Abstract
Focusing on the fine-grained access control challenge of multi-user searchable encryption, we propose a hierarchical searchable encryption scheme using blockchain-based indexing (HSE-BI). First, we propose a hierarchical search index structure based on a DAG-type access policy and a stepwise hierarchical key derivation mechanism; which we outsourced to the blockchain network to achieve reliable hierarchical search. We design a dynamic append-only update protocol for the blockchain-based index to deal with adding and deleting files. Secondly, we propose a hierarchical authorization mechanism based on broadcast encryption to achieve fine-grained search permission granting and revoking, which can prevent a malicious server from colluding with corrupted users. The security and complexity analysis shows that HSE-BI achieves optimal search time while satisfying adaptive secure and revocation secure. Our experimental results are encouraging, e.g., compared with the traditional multi-user searchable encryption schemes, HSE-BI’s hierarchical search policy does not impact the search performance visually. The growth rate of the search latency decreases with the increasing number of hierarchical users, which can act as an efficient crypto tool to open up venues for other applications. We demonstrate that HSE-BI is more suitable for actual applications with fine-grained access requirements and can act as an efficient crypto tool to open up venues for other applications.
1. Introduction
1.1. Background and Motivation
As the demand for outsourced data storage and distributed computing grows, data privacy is becoming one of the primary considerations. Encryption can ensure the security of outsourced data, but how to effectively search and share outsourced encrypted data has become a new challenge. To that end, searchable encryption (SE) [1,2] is a family of cryptographic protocols that allow a data owner to outsource the encrypted data to a cloud server maintaining the server’s search capability. In recent years, multi-user searchable encryption (MUSE) [3,4,5] has been one crucial research line in searchable encryption. Compared with the majority of works in SE, the architecture in MUSE is more complicated, where not only the original data owner but a constant number of entities have the ability to send the server a search query for (part of) data. MUSE opens up avenues for other applications, such as collaborative data sharing. For example, all employees can be authenticated in an enterprise to access the company’s outsourced encrypted files for subsequent collaboration.
A typical design challenge of multi-user searchable encryption is achieving flexible access control for users [6,7]. Most MUSE schemes from the literature consider the case that authenticated users always have unrestricted access to the entire dataset. However, in the real-world data-sharing scenario, an organization often consists of a pyramid-shaped hierarchical access control strategy. Users in different hierarchies are assigned different access permissions. The sensitive data in the real world is likely to be hierarchical and different users should have different access rights. However, there are relatively few works in MUSE considering this situation.
In addition, another problem in MUSE is that the server is often treated as a semi-honest-but-curious party [5,8], which is assumed to store and search the secure index correctly and does not attend to learning user’s extra information. However, this assumption is too strong for many applications where the server is malicious. As most recent research shows [9,10], the existing verification approaches for MUSE do not provide efficient verification for search results over multiple users, and few works achieve a hierarchical verifiable search. Therefore, it is an urgent challenge to design a solution for the above problems.
In recent years, with the popularity of cryptocurrencies and decentralized applications, blockchain technology has received much attention from various industries. It has been a critical technology in constructing distributed storage platforms, such as Bigchain DB [11] and Bluzelle [12]. Therefore, a blockchain data structure offers a possible solution to the above problems in MUSE research. Some recent works have already considered building MUSE schemes on top of a blockchain network. However, most of them treat blockchain as a trusted third party to ensure reliable searches through consensus protocols [13,14,15], but few works achieve hierarchical search. In this work, we take advantage of a blockchain data structure to build a hierarchical searchable encryption scheme. Our design goal is to make HSE-BI achieve fine-grained access control and ensure the search results are reliable by the consistency and immutability of the blockchain-based index.
1.2. Our Contributions
We propose a hierarchical searchable encryption scheme using blockchain-based indexing (HSE-BI) to focus on the above challenges in MUSE. Our contributions are as follows:
- (Blockchain-based index) First, to achieve a multi-user hierarchical search, we explore the construction of a secure hierarchical index via a blockchain network. The index is built on a DAG-type access structure oriented real-world information flow policy. We deploy the blockchain network to collaboratively manage the index to achieve index immutability, aiming to make the search results reliable with no extra verification work on the user side. We further propose an append-only index update mechanism oriented in the blockchain index when adding/deleting is applied to outsourced files.
- (Hierarchical search control) Secondly, we propose a dynamic user authorization mechanism that realizes fine-grained search permission control through hierarchical key derivation. Based on this, authorized users have the right to search for the files under their hierarchies. By deploying broadcast encryption and a hierarchical key derivation strategy, HSE-BI can dynamically grant/revoke users’ search rights without updating other users’ keys. Each user only needs to store its secret key locally, which requires constant-size user storage.
- (Formal analysis evaluation) We give a formal security definition for HSE-BI, including adaptive secure and revocation secure, and show that HSE-BI satisfies them. We also implement HSE-BI and compare it with other related schemes. It shows that HSE-BI’s hierarchical search policy does not impact the search performance visually. The growth rate of the search latency decreases with the increasing number of hierarchical users, which can act as an efficient crypto tool to open up avenues for other applications.
The rest of the paper is summarized below: Section 2 is the literature review, which describes the related work, followed by a description of the proposed HSE-BI model in Section 3. Section 4 presents the concrete constructions of HSE-BI. Section 5 and Section 6 discuss HSE-BI’s security and theoretical complexity analysis, respectively. Section 6 shows the experimental investigations. Finally, the paper is concluded in Section 7.
2. Literature Review
Multi-User Searchable Encryption The concept of “multi-user searchable encryption (MUSE)” was proposed by Curtmola et al. by combining a single-user SE model with broadcast encryption [3]. In 2015, Li et al. proposed a self-authorized multi-user searchable encryption scheme, which allows group users to be authorized to perform keyword searches by generating shared keys to realize data sharing on mobile terminals [4]. In 2017, Deng et al. designed a multi-user searchable encryption scheme based on a non-collusive dual-server model, where the anti-revoking user and cloud server conspired [5] and constructed an access policy combining search keywords and user attributes.
In the last decade, many related works have combined hierarchical access with multi-user searchable encryption. In 2011, Hattori et al. [8] proposed a role-based multi-user searchable encryption scheme. In their scheme, the roles of users are mapped to policy vectors and associated with secure indexes; however, in this scheme, the authenticated user group is static, and the adversary must declare its corruption initially. In 2014, Kaci et al. [16] proposed a multi-user searchable encryption scheme based on attribute-based encryption to realize flexible access control but still retain the ability to update data dynamically. In 2017, Ye et al. [17] designed a dynamic, searchable cloud storage scheme with multiple access hierarchies using ciphertext policy-attribute-based encryption; it constructed an access tree for each file, which caused an exponential extra storage overhead. In 2018, Hamlin et al. [18] designed a multi-user searchable encryption scheme via ORAM-based proxy re-encryption, which allows data to be shared from multiple data owners to multi-level users for the searching of single keywords; its main limitation is that the search time is linear in the total number of files. Alderman et al. [19] proposed a multi-level searchable encryption that allows multiple users differential access control, but it is restricted to non-practical access policies where the set of access rights is totally ordered.
In 2019, Blomer et al. [9] proposed a verifiable multi-user searchable encryption scheme that realized the efficient verifiable search; however, at the same time, the search operation disclosed the attributes of users. Wang et al. [20] proposed a multi-user searchable encryption scheme that hides access policies that ensure the privacy of a user’s attributes, which takes the cost of too much computation and communication above the addition and deletion of users. When the user group changes, the scheme needs to re-perform the setup algorithm to generate a series of new parameters, and re-generate and distribute all users’ keys. In 2021, Chamani et al. [21] designed a multi-user searchable encryption scheme based on a multi-server model and an oblivious data structure to resist the collusion of revoked users and cloud servers. In 2022, Li et al. [22] considered the real-world application of MUSE and proposed a hierarchical multi-user searchable encryption scheme for a medical electronic sharing data scenario.
Blockchain-Assisted Searchable Encryption In recent years, several pioneering works have considered building searchable encryption schemes (especially multi-user searchable encryption) on top of the blockchain network. In 2018, Hu et al. designed the first searchable encryption scheme based on a blockchain, where the search interaction process is between the data owner and the blockchain. In 2018, Cai et al. [10] proposed the design of a blockchain-assisted encrypted database with expressive content search capabilities, assuring the trustworthiness of search results returned by various service providers. In 2019, Chen et al. [13] proposed a searchable encryption scheme for EHR (electronic health record), and Niu et al. [14] proposed an electronic health record-sharing scheme on the blockchain. In 2021, Guptaet al. [15] deployed blockchain-assisted searchable encryption into a cloud-based healthcare cyber-physical system. The above works [13,14,15] all treated blockchain as a trusted third party, which enforces the generalized solutions of theoretical crypto constructions in real-life scenarios. In 2022, Han et al. [6] formalized a flexible and privacy-preserving framework for MUSE by orienting blockchain and attribute-based encryption, which achieves fine-grained access control.
3. The Proposed Model
We present the model of the HSE-BI scheme in this section. We start by giving the architecture of the HSE-BI scheme in Section 3.1 and define its syntax in Section 3.2. We will use the notations from Table 1 throughout the rest of the paper.

Table 1.
Notations.
3.1. Architecture
HSE-BI is designed to be executed among: a data owner , n users , a server and a blockchain network . The scheme model is illustrated in Figure 1:
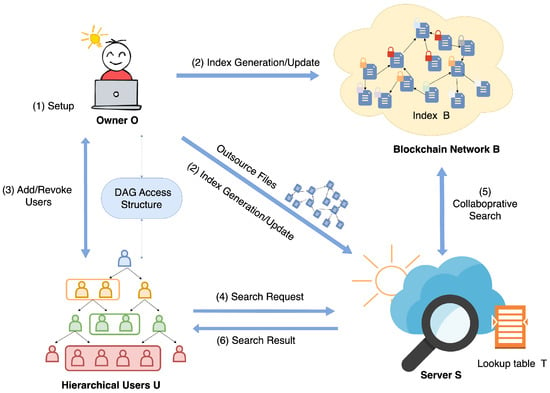
Figure 1.
The architecture.
- Data owner develops a hierarchical DAG search structure and outsources encrypted files to .
- Each user can be mapped to a search hierarchy in by and has hierarchical search rights to the files in their hierarchy.
- Server is an untrusted entity that stores encrypted files and answers search queries from with the collaboration of .
- Blockchain network is organized by a network of peer nodes, which manage the index and acts as a collaborator for searching.
The architecture is illustrated in Figure 1. To initialize the system, the data owner constructs a hierarchical search index based on a DAG-type authentication structure , encrypts the index by hierarchical keys and outsources it to the blockchain network , stored as index BC. also initializes a look-up table T outsourced to the server for encrypted searches. A user u can interact with to obtain the search authority under some hierarchy . To search the files that include the keyword w, the authorized user can submit search tokens to that contain the masked information of the searched keyword w and its hierarchy . interacts with the blockchain network to conduct the encrypted search according to the search token , and obtains search result R, which contains the matched file id under hierarchy . is able to change any user’s hierarchy or revoke a user’s search right at any time. can also interact with to dynamically update the index BC when adding/deleting files.
3.2. Syntax
The scheme HSE-BI (Setup, IndexGen, AddU, Search, RevokeU, Update) consists of six algorithms/protocols:
- : On input, the security parameter k and the authentication structure , computes , where is ’s key, is ’s key and is ’s state.
- : On input, ’s key , the file set and the authentication structure , computes the hierarchical index and , sends to and sends to .
- : On input, ’s key, the authentication structure , the user’s identity u and computes the user’s key , the updated user group and ’s state .
- : To search for files contains w, a user u executes this protocol with on input of w and , interacts with to query on input . The final output for the user is R.
- : On input, ’s key, file f, the authentication structure , executes this protocol with and to compute the updated index and .
- : On input, ’s key and the revoked user’s identity u, computes the updated user group and ’s current state .
4. HSE-BI Constructions
4.1. Design Challenge
Before we present HSE-BI’s detailed concrete constructions, we need to describe our design challenge for the explicit algorithms. Since HSE-BI is designed for hierarchical searches, how do we build a hierarchical index structure to achieve this goal? Notice first that in a blockchain data structure, the transactions can be linked by storing the addresses of previous transactions in current transactions. Therefore, we organize the hierarchical DAG-type index as a constant number of sorted arrays; each array includes l nodes. To link the nodes in the same array that stores in different transactions together as a virtual link list, we insert each node with the transaction addresses of the previously connected nodes in such a way that can make the index achieve hierarchical and parallel searches. Secondly, recall that the blockchain is an append-only data store, i.e., once a block is created, it is final. It is not possible to subsequently delete or modify the index. How can the dynamic update can be applied to the secure index corresponding to the update of the actual outsourced files? To achieve dynamic update, we propose an append-only index update mechanism to support update operations on the encrypted blockchain-based index structure.
4.2. Concrete Constructions
Let k be a public parameter, be the data owner, be the authenticated users, be a server and be the blockchain network. Let be the file set, and be the keyword dictionary. Let F and P be two pseudo-random functions of fixed length [15], G be a full-domain pseudo-random function and H be a collision-resistant hash function . HSE-BI also makes black-box use of crypto primitives: a private key encryption scheme SKE = (Gen, Enc, Dec) [23], a CPA-secure broadcast encryption scheme BE = (KeyGen, Join, Enc, Dec) [24] and a blockchain data store [25]. Consider that HSE-BI works as follows:
4.2.1. Setup
To initialize the system, the data owner constructs the hierarchical authentication structure as a directed acyclic graph . contains l vertices , each of which represents an access hierarchy in . The directed edge set represents the affiliations among hierarchies. If there exists , then the hierarchy of is directly afflicted by the hierarchy of . Any authenticated user or file can be mapped to a vertex in : and . A user u can access file f if and only if is afflicted by , which means that is reachable from in . After is established, the data owner generates the hierarchy keys as l triples of k-bit strings . also initializes the authenticated user group , and computes their master key by for enrolling users. Then inserts server into . It also computes the server’s key by and generates a k-bit string as the authentication key by , encrypts as the current server state by . Finally, sends to , and stores its key as at local. This algorithm is shown in Algorithm 1.
| Algorithm 1Setup |
|
4.2.2. IndexGen
Data owner constructs a hierarchical secure index BC outsourced to blockchain network and a look-up table T outsourced to server . This algorithm is shown in Algorithm 2.
- The index BC consists of keyword-guided hierarchy-sorted arrays . Each array contains l nodes . At a high level, the information stored in should at least include the identities of files in hierarchy that contain the keyword w. These nodes should be linked in the sorted arrays to generate a hierarchical DAG index. To outsource the index to the blockchain network, interacts with to initialize BC using . To connect different nodes in , besides the above information stores in , inserts with additional address information —the transaction address of the connected nodes in , where is directly affiliated by : .To guarantee confidentiality and hierarchical search control, should mask the information stored in each node. We define the structure of the masked node as , where is the file set that contains the keyword w and corresponds to the hierarchy , is the address of node where is directly afflicted by : , is the key to decrypt the masked node . then encrypts each node in an orderly way from to , inserts as a transaction into the blockchain index BC by , and receives the transaction address . Specifically, for , the tail node in , there is no node for the lower hierarchy in the ordered array , computes the masked as .
- To support the search, we design a look-up table T at the server side to store the masked tail address of each virtual hierarchy-sorted array in BC. The entries in T contain each masked pair, which does not point to the address of the initial node in each , but to the masked address of the tail node of in the blockchain BC. For example, to retrieve array in hierarchy , we should only retrieve its sub-array from the blockchain BC. Since the search can not traverse back through the encrypted virtual link list, the available search results are the identifiers for the files that both contain the keyword w and are affiliated by hierarchy , as required by DAG structure. Therefore, for each , generates the entry in T, which points to the masked address : . Finally, sends T to server .
| Algorithm 2 |
|
4.2.3. AddU/RevokeU
A user u can interact with the data owner to obtain the search authority under their hierarchy . Data owner adds the user id u to the authenticated user group as , and generates the user’s key by . Since group is updated, should also refresh as a new k-bit string by SKE.Gen() and encrypts as a new server state by . Finally, sends the user’s key to u and sends to server .
If the data owner would like to revoke u’s search right at any time, they need to delete the user id u from the authenticated user group as . should also refresh as a new k-bit string by SKE.Gen(), and encrypt as the current server state by . Finally, sends to . AddU and RevokeU algorithms are shown in Algorithms 3 and 4.
| Algorithm 3 |
|
| Algorithm 4 |
|
4.2.4. Search
To search the files that contain the keyword w, the authorized user can submit search token to server , which contains the masked information of the search keyword w and its hierarchy . interacts with the blockchain network to conduct an encrypted search according to the search token . The specific process is as follows:
User u first retrieves the server’s current state , uses their key to decrypt as r by running and generates the search token as , then sends to server . first runs to decrypt as and uses to decrypt as . If is decrypted successfully, that means ; then the token sender u is an authorized user. then initializes an empty search result set R, and parses as , uses as the entry to retrieve , which points to the masked address of the tail node of in the blockchain B, uses to decrypt the address as that stores masked —the tail node of the hierarchy-sorted in BC. interacts with to obtain the transaction with address , uses to decrypt , and sets . If , then is the transaction addresses set of , where each is affiliated directly with . adds to the result set R as , and continues the above process parallel to retrieve the nodes by addresses in until . After has retrieved all the nodes in , search result R then contains those identifiers for files containing w, and the hierarchy is affiliated with , as required by the DAG structure. Finally, sends the result R to u. This algorithm is shown in Algorithm 5.
| Algorithm 5 |
|
4.2.5. Update
When adding or deleting file f in hierarchy with keywords , data owner should update the secure index BC and T accordingly. For , interacts with and runs to get the transaction that stores masked . decrypts it as . If file f is added, computes the updated as . If file f is deleted, computes as . Then inserts as a new transaction into BC, and receives its new address by .
For each q from to 1, interacts with and runs to get the transaction that stores the masked . decrypts as , computes , inserts a new transaction that stores masked into and runs as to get the transaction address , masks with and generates . parses the update token , where and . Finally, sends to . updates the lookup table T by setting as . This algorithm is shown in Algorithm 6.
| Algorithm 6 |
|
5. Security Analysis
We present the security analysis for HSE-BI in this section. The notions of security focus on two aspects: (1) User’s view: for each user with hierarchy , it cannot learn any information for the files whose hierarchy is higher than . (2) Server’s view: although it can conclude with some revoked or relegated users, it cannot provide a valid search token.
We formalize the security required in HSE-BI. Suppose is an adversary with pseudo-random polynomial time (PPT) computation ability, who is given the security parameter k. In that case, the search policy is , and the server key is , also provided is access to the following oracles, where · denotes the parameters that are provided by themselves.
- -
- : can send index generation to this oracle, which runs by the input provided by . The oracle outputs .
- -
- : can send an add user request to this oracle, which runs by the input provided by . If , then the oracle outputs ⊥.
- -
- : can send a revoke request to this oracle, who runs Revoke by the input provided by . If , then the oracle outputs ⊥.
- -
- : can send a search request for keyword w to this oracle. generates a search token and sends it to which runs Search and outputs the search result to .
Definition 1 (Adaptive Secure).
The security definition of adaptive secure requires that the execution of the scheme in the real-world, Real , is indistinguishable from an ideal-world, Ideal . In Real , the protocols between and execute just as in the real scheme. In Ideal , there exist a simulator that can obtain the leakage information from the oracles above and try to simulate the execution of in Real . HSE-BI achieves adaptive secure if, for all polynomial times of , there exists a polynomial time simulator such that the following two distribution ensembles are computationally indistinguishable: .
Theorem 1.
If SKE is CPA secure, and functions and H are pseudo-random, let HSE-BI be the hierarchical searchable symmetric encryption scheme with a blockchain-based index, then HSE-BI satisfies adaptive secure, which is defined in Definition 1.
Proof Sketch.
To show adaptive secure we reduce the security to that of the indistinguishability of the output of SKE.Enc and functions and H are indistinguishable from the output of a truly random function. We assume the possibility of an adversary that is able to break the adaptive secure property of HSE-BI, then we build a distinguisher that is able to use as a sub-routine to distinguish between the output of SKE.Enc and functions and a truly random function with non-negligible probability. □
Definition 2 (Revocation Secure).
Consider , which is interactively executed by a challenger and an adversary who have the ability to add and revoke users in the real scheme. After a polynomial number of queries, revokes all users that are queried to the oracle but are not subsequently queried to (i.e., all users for which holds their valid user keys). generates a search token τ in the Search protocol. If the output of the Search is not ⊥, then it returns 1, otherwise, it returns 0. After several rounds of queries, if ’s probability of winning the revocation secure experiment with PPT computation ability is negligible, then we can say that HSE-BI satisfies revocation secure.
Theorem 2.
If BE is CPA secure, let HSE-BI be the hierarchical searchable symmetric encryption scheme with a blockchain-based index, then HSE-BI satisfies revocation secure, which is defined in Definition 2.
Proof Sketch.
Assuming the advantage of winning is negligible, we can construct an adversary , who can break the CPA secure of BE with assistance from . If has a non-negligible advantage in , then we can construct an adversary that uses as a subroutine to break the CPA secure of BE. Since BE is proven to be CPA secure [6]; there exists no to produce a valid search token, even though it does not hold a non-revoked key that can win with non-negligible probability, and HSE-BI satisfies revocation secure as defined in Definition 2. □
6. Theoretical Analysis
We give the theoretical analysis of HSE-BI in this section. Table 2 presents a detailed complexities analysis of HSE-BI. In the Setup phase, the computation and storage complexity of data owner is linear with the number of hierarchies l, since needs to generate the keys for all hierarchies. The IndexGen phase, as shown in Section 4.2.2, needs the data owner to construct the search index into: (1) keyword-guided arrays with l nodes , which need O() operations; (2) a look-up table T contains all masked pairs as entries with O() operations. The arrays are outsourced to , and T is outsourced to , so their storage overheads are O() and O(), respectively. To search for , a user sends a constant size token to , interacts with to perform works to operate XOR functions from the array in the subtree-rooted , as presented in Section 4.2.4. Therefore, we require that the computational complexities included user-side and -side are O(1) and , respectively, which are both independent in the number of files that contain .

Table 2.
Complexity.
Moreover, HSE-BI also achieves a constant-time computation and storage cost to add/delete user. The owner can dynamically add or revoke users by updating the state parameter. Each user only needs to store their secret key locally, which requires constant user storage O(1). The search and update complexities is related to the concrete instance of the DAG-type index, which can be formalized as a full and complete binary tree. To update the index for a file f of hierarchy with keywords , adds new transactions as newer versions of in all subtrees rooted from to , which is described in Section 4.2.5, which needs to update -related entries in T with O() operations.
Table 3 shows the complexities and property comparisons of HSE-BI with the existing related multi-user searchable encryption schemes [16,18,19,20]. From the figure, we can see that the search and update complexities in HSE-BI are less than other schemes, which does not depend on the number of files. The DAG authentication structure makes the search complexity depend on the user’s search hierarchy, while in [18], the number of data items searched for is linear with the user’s rights and the files contain keywords; further, searching in [16,18,20] requires traversing all files. The index storage complexity in HSE-BI is linear with the size of the keyword dictionary and the hierarchy number. It is comparable with [19], the index of which is designed specifically for partial order access. Compared with [19], the size of the server’ storage overload of HSE-BI is about times larger, where l is the number of access hierarchies and m is the total file number. The hierarchical search property of HSE-BI will not significantly affect the index generation and search complexity. In terms of other properties, compared with the existing schemes, HSE-BI is secure from attacks from adaptive adversaries and supports the efficient updating for index and users while satisfying the revocation secure.

Table 3.
Comparison.
7. Experimental Evaluation
We implement HSE-BI in C++ and Python. In the simulation experiments, security parameter k is 256 bits, and the key length of broadcast encryption is 1024 bits. The experiment uses OpenSSL library [26] to implement basic cryptography algorithms, such as AES-CBC-256 for private-key encryption and SHA256 for hash and pseudo-random functions. Since running experiments on the blockchain main net is expensive, we simulate the blockchain network on Ropsten’s testnet [27], which provides custom transaction input of up to 1 KB, which we use to store the index BC. We fund our wallet using Ropsten’s faucet. In addition, we use BGW2 [24] to realize broadcast encryption. We use the U.S. National Science Foundation (NSF) Research Awards Abstracts 1990–2003 [28] as the hierarchical file collection. The experiment simulates a hierarchical DAG authentication structure on top of the collection containing 10 hierarchies. The hierarchy affiliation, number of files and users in each hierarchy is illustrated in Figure 2.
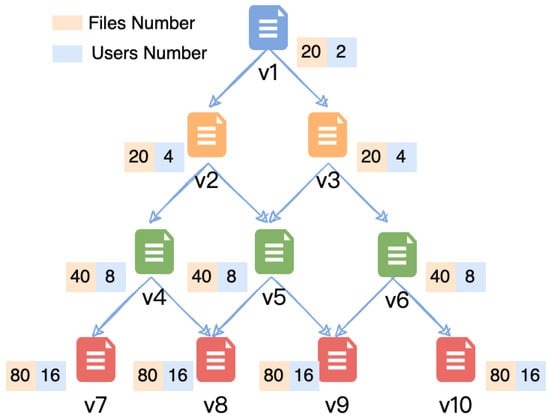
Figure 2.
The Simulated Authentication Structure.
7.1. Search Performance
We analyzed the search performance for answering requests from users of different hierarchies. The search is performed by the server, and the process includes querying and communicating with the blockchain network to obtain transaction data. The search latency and communication overhead for the different hierarchy is presented in Figure 3 and Figure 4.
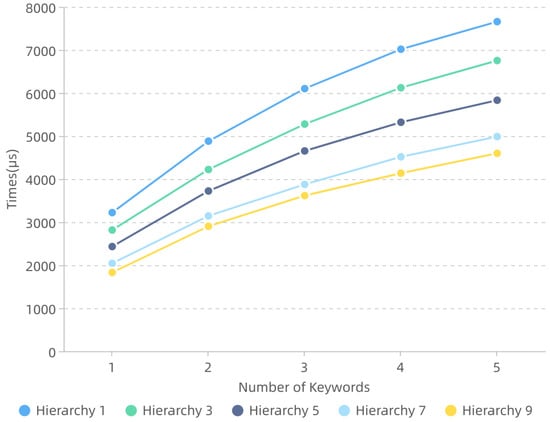
Figure 3.
The Relationship of Search Times and Hierarchies.
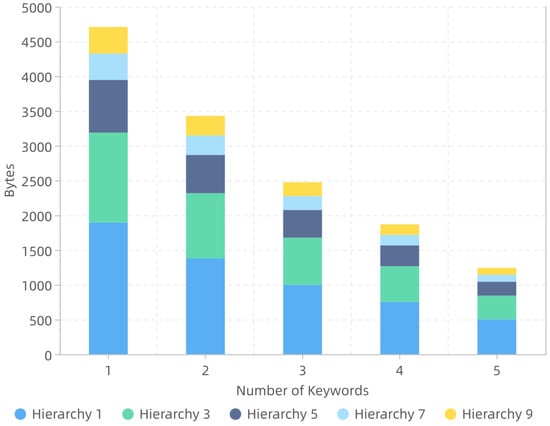
Figure 4.
The Relationship of Communication Sizes and Hierarchies.
To analyze the search latency, we performed a keyword search with different hierarchies. Figure 3 plots the average search latency per 50 searches for 1, 2, 3, 4 and 5 independent keywords with 1, 3, 5, 7 and 9 hierarchies. From the figure, we can learn that, with the hierarchy of search users increasing, the search latency decreases with a smooth and orderly curve, i.e., the search times for three keywords are about 0.61, 0.53, 0.47, 0.39 and 0.36 ms with 1, 3, 5, 7 and 9 hierarchies, respectively. We identified the main efficiency bottleneck to be the on-chain processing. In fact, as long as enough transaction data size is deployed in transactions, the broadcast transactions will be mined and processed efficiently. The XOR operation and the PRF evaluation for the transaction data are related to the hierarchy directly, which decreases as the hierarchy increases. Therefore, from the performance shown in Figure 3, we observe that Search in HSE-BI is efficient, and the search latency (around a few milliseconds) is acceptable.
In terms of communication, we mainly analyze the amount of data transformed between the search user and the server. Figure 4 plots the average communication overhead between them per 50 searches when we have performed 1, 2, 3, 4 and 5 independent keywords, with 1, 3, 5, 7 and 9 hierarchies. We do not record the blockchain network communication overhead since it depends on the real-time network connection condition. From the figure, we can see the communication size decreases with the increasing hierarchy of search users, i.e., to search for three keywords, the communication sizes are 0.99, 0.68, 0.40, 0.21 and 0.20 kb for 1, 3, 5, 7 and 9 hierarchies, respectively, and each search only needs one round of interaction, which is tolerable with bandwidth latency. It is worth mentioning that as the hierarchy gets lower, the communication size slows down due to the specific DAG-type access structure shown in Figure 2. In general, from the performance shown in Figure 4, we can observe that the communication overhead is acceptable and is consistent with the theoretical analysis.
7.2. Comparison
We also implement schemes [18,19] and compare their experimental results with HSE-BI. We analyzed the influence of search users’ hierarchies and the number of users on the search latency of the three schemes. We assume that the number of searched keywords in the above schemes are all set to three. Figure 5 plots the relationship between search times and hierarchies. Figure 6 plots the relationship between the number of users and the search times. It should be mentioned that we implemented multiple user searches by deploying several hosts acting as users to submit search requests to the server host simultaneously. Each user host stores one user’s private information locally and interacts with the server independently.
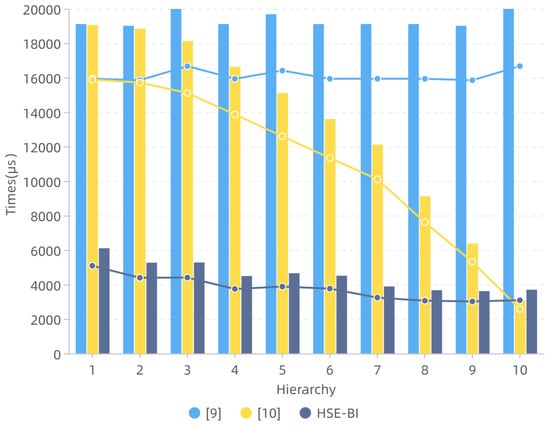
Figure 5.
The Relationship between Hierarchy and Search Time.
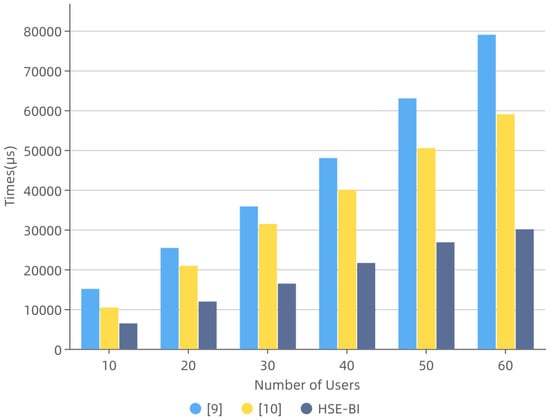
Figure 6.
The Relationship between Number of Users and Search Time.
Search Latency The experimental results in Figure 5 demonstrate that HSE-BI spends much less time searching than that of [18,19], where 10 users with the same hierarchy submit search requests simultaneously in the three schemes. In detail, compared to [18], the search time of which does not change visibly and remains approximately 19 ms, the search time of HSE-BI is maintained in [3 ms, 6 ms], which is significantly better. One reason is the search operation in [18] needs to traverse the whole index and is independent of the hierarchies of users. Another reason is that searching operations in HSE-BI is not as complicated as [18], where the latter needs to traverse more of the index for the same hierarchy and consists of ORAM operations, which are not very efficient since ORAM incurs heavy computational and communication costs.
Compared with [19], the search performance of HSE-BI is less affected by hierarchy, while that in [19] has a stable, approximately linear relationship with the number of hierarchies. In detail, we observe that the HSE-BI’s search time for hierarchy 10 is 0.37 ms, which is slightly more than that in [19] (0.31 ms). Still, from hierarchy 9 to hierarchy 1, HSE-BI’s search performance is better than [19]. The increasing rate of efficiency is improved by 73% (for hierarchy 9) to 110% (for hierarchy 1), and as the hierarchy gets lower, the search latency in [19] considerably increases, more steeply than HSE-BI. One important reason is that HSE-BI supports parallel searches with a hierarchical index (especially the specific DAG-type access structure in Figure 2).
Scalability We also compared the scalability of the three schemes, which is the impact of the increasing number of users on search performance. We recorded the search times for 10, 20, 30, 40, 50 and 60 users who submitted search requests simultaneously to the server in the three schemes and plotted the relationship between the number of users and the search time, as illustrated in Figure 6. We observe that, for the same number of search users, the search performance of HSE-BI is better than others. In detail, the search time in HSE-BI is 38–49% less than [19] and 35–62% less than [18], where the curves in [18,19] are stably linear with the number of users. It is essential to notice that, in HSE-BI, the increase in search time slows down with the growing number of search users. Therefore, in the case of a large number of users, the growing number of search users has a weaker impact on the time consumption of the search protocol than [18,19]; that is, the number of users that the scheme can carry has an extensible space to meet the actual scalability requirements of hierarchical multi-user search.
8. Conclusions
In this paper, we propose a hierarchical searchable encryption scheme using blockchain-based indexing (HSE-BI). We focus on fine-grained access control policy, which is a crucial aspect for multi-user searchable encryption, but there are relatively few works considering this research area. We designed a hierarchical search index structure based on stepwise hierarchical key derivation and outsourced it to the blockchain network to achieve search reliability. We also propose a hierarchical user authorization mechanism based on broadcast encryption to achieve efficient user permission granting and revoking while preventing the malicious server from colluding with corrupted users. The security and performance analysis show that HSE-BI is adaptive secure and revocation secure. Our experimental results are encouraging in that HSE-BI’s hierarchical search policy does not impact the search performance visually, which is more suitable for actual complex application scenarios with fine-grained access requirements.
Author Contributions
Conceptualization, Y.L.; methodology, Y.L.; software, D.J. and Z.X.; validation, Z.X. and D.J.; formal analysis, Y.L. and F.Z.; data curation, D.J.; writing—original draft preparation, Y.L.; writing—review and editing, Y.L. and F.Z.; funding acquisition, Y.L. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by Northeastern University Annual Basic Scientific Research Funding grant number 02190022121006.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Song, D.X.; Wagner, D.; Perrig, A. Practical techniques for searches on encrypted data. In Proceedings of the 2000 IEEE Symposium on Security and Privacy, S & P 2000, Berkeley, CA, USA, 14–17 May 2000; pp. 44–55. [Google Scholar]
- Kamara, S.; Papamanthou, C.; Roeder, T. Dynamic searchable symmetric encryption. In Proceedings of the 2012 ACM Conference on Computer and Communications Security, Raleigh, NC, USA, 16–18 October 2012; pp. 965–976. [Google Scholar]
- Curtmola, R.; Garay, J.; Kamara, S.; Ostrovsky, R. Searchable Symmetric Encryption: Improved Definitions and Efficient Constructions. In Proceedings of the 13th ACM Conference on Computer and Communications Security, ACM, Alexandria, VA, USA, 30 October–3 November 2006; pp. 79–88. [Google Scholar]
- Li, Z.; Jiang, H.; Zhao, M. A Discretionary Searchable Encryption Scheme in Multi-User Settings. J. Comput. Res. Dev. 2015, 52, 2313–2322. [Google Scholar]
- Deng, Z.; Li, K.; Li, K.; Zhou, J. A multi-user searchable encryption scheme with keyword authorization in a cloud storage. Future Gener. Comput. Syst. 2017, 72, 208–218. [Google Scholar] [CrossRef]
- Han, J.; Li, Z.; Liu, J.; Wang, H.; Xian, M.; Zhang, Y.; Chen, Y. Attribute-Based Access Control Meets Blockchain-Enabled Searchable Encryption: A Flexible and Privacy-Preserving Framework for Multi-User Search. Electronics 2022, 11, 2536. [Google Scholar] [CrossRef]
- Van Rompay, C.; Molva, R.; Önen, M. Secure and scalable multi-user searchable encryption. In Proceedings of the 6th International Workshop on Security in Cloud Computing, Incheon, Republic of Korea, 4 June 2018; pp. 15–25. [Google Scholar]
- Hattori, M.; Hirano, T.; Ito, T.; Matsuda, N.; Mori, T.; Sakai, Y.; Ohta, K. Ciphertext-policy delegatable hidden vector encryption and its application to searchable encryption in multi-user setting. In Proceedings of the IMA International Conference on Cryptography and Coding, Oxford, UK, 16–18 December 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 190–209. [Google Scholar]
- Blomer, J.; Loken, N. Dynamic searchable encryption with access control. In Proceedings of the International Symposium on Foundations and Practice of Security, Toulouse, France, 5–7 November 2019; Springer: Cham, Switzerland, 2019; pp. 308–324. [Google Scholar]
- Cai, C.; Weng, J.; Yuan, X.; Wang, C. Enabling Reliable Keyword Search in Encrypted Decentralized Storage with Fairness. IEEE Trans. Dependable Secur. Comput. 2018, 18, 131–144. [Google Scholar] [CrossRef]
- Bigchain DB. Available online: https://www.bigchaindb.com/ (accessed on 9 September 2022).
- Bluzelle. Available online: https://bluzelle.com/ (accessed on 9 September 2022).
- Chen, L.; Lee, W.K.; Chang, C.C.; Choo, K.K.R.; Zhang, N. Blockchain based searchable encryption for electronic health record sharing. Future Gener. Comput. Syst. 2019, 95, 420–429. [Google Scholar] [CrossRef]
- Niu, S.; Chen, L.; Wang, J.; Yu, F. Electronic Health Record Sharing Scheme with Searchable Attribute-Based Encryption on Blockchain. IEEE Access 2020, 8, 7195–7204. [Google Scholar] [CrossRef]
- Gupta, B.B.; Li, K.C.; Leung, V.C.; Psannis, K.E.; Yamaguchi, S. Blockchain-assisted secure fine-grained searchable encryption for a cloud-based healthcare cyber-physical system. IEEE/CAA J. Autom. Sin. 2021, 8, 1877–1890. [Google Scholar]
- Kaci, A.; Bouabana-Tebibel, T.; Challal, Z. Access Control Aware Search on the Cloud Computing. In Proceedings of the 2014 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Delhi, India, 24–27 September 2014; pp. 1258–1264. [Google Scholar]
- Ye, J.; Wang, J.; Zhao, J.; Shen, J.; Li, K.C. Fine-Grained Searchable Encryption in Multi-User Setting. Soft Comput. 2017, 21, 6201–6212. [Google Scholar] [CrossRef]
- Hamlin, A.; Shelat, A.; Weiss, M.; Wichs, D. Multi-key searchable encryption, revisited. In Proceedings of the IACR International Workshop on Public Key Cryptography, Rio de Janeiro, Brazil, 25–29 March 2018; Springer: Cham, Switzerland, 2018; pp. 95–124. [Google Scholar]
- Alderman, J.; Martin, K.M.; Renwick, S.L. Multi-level access in searchable symmetric encryption. In Proceedings of the International Conference on Financial Cryptography and Data Security, Sliema, Malta, 7 April 2017; Springer: Cham, Switzerland, 2017; pp. 35–52. [Google Scholar]
- Wang, H.; Ning, J.; Huang, X.; Wei, G.; Poh, G.S.; Liu, X. Secure fine-grained encrypted keyword search for e-healthcare cloud. IEEE Trans. Dependable Secur. Comput. 2019, 18, 1307–1319. [Google Scholar] [CrossRef]
- Gharehchamani, J.; Wang, Y.; Papadopoulos, D.; Zhang, M.; Jalili, R. Multi-User Dynamic Searchable Symmetric Encryption with Corrupted Participants. IEEE Trans. Dependable Secur. Comput. 2021. [Google Scholar] [CrossRef]
- Li, W.; Xu, L.; Wen, Y.; Zhang, F. Conjunctive multi-key searchable encryption with attribute-based access control for EHR systems. Comput. Stand. Interfaces 2022, 82, 103606. [Google Scholar] [CrossRef]
- Katz, J.; Lindell, Y. Introduction to Modern Cryptography; CRC Press: London, UK, 2014. [Google Scholar]
- Boneh, D.; Gentry, C.; Waters, B. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 14–18 August 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 258–275. [Google Scholar]
- Adkins, D.; Agarwal, A.; Kamara, S.; Moataz, T. Encrypted blockchain databases. In Proceedings of the 2nd ACM Conference on Advances in Financial Technologies, New York, NY, USA, 21–23 October 2020; pp. 241–254. [Google Scholar]
- The OpenSSL Project. OpenSSL: The Open Source toolkit for SSL/TLS [EB/OL]. 2015. Available online: http://www.openssl.org/ (accessed on 15 August 2022).
- Ethereum Community. Etherscan Ropsten Testnet Network. 2019. Available online: https://ropsten.etherscan.io/ (accessed on 9 September 2022).
- NSF Research Awards Abstracts 1990–2003. 2013. Available online: http://kdd.ics.uci.edu/databases/nsfabs/nsfawards.html (accessed on 9 September 2022).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).