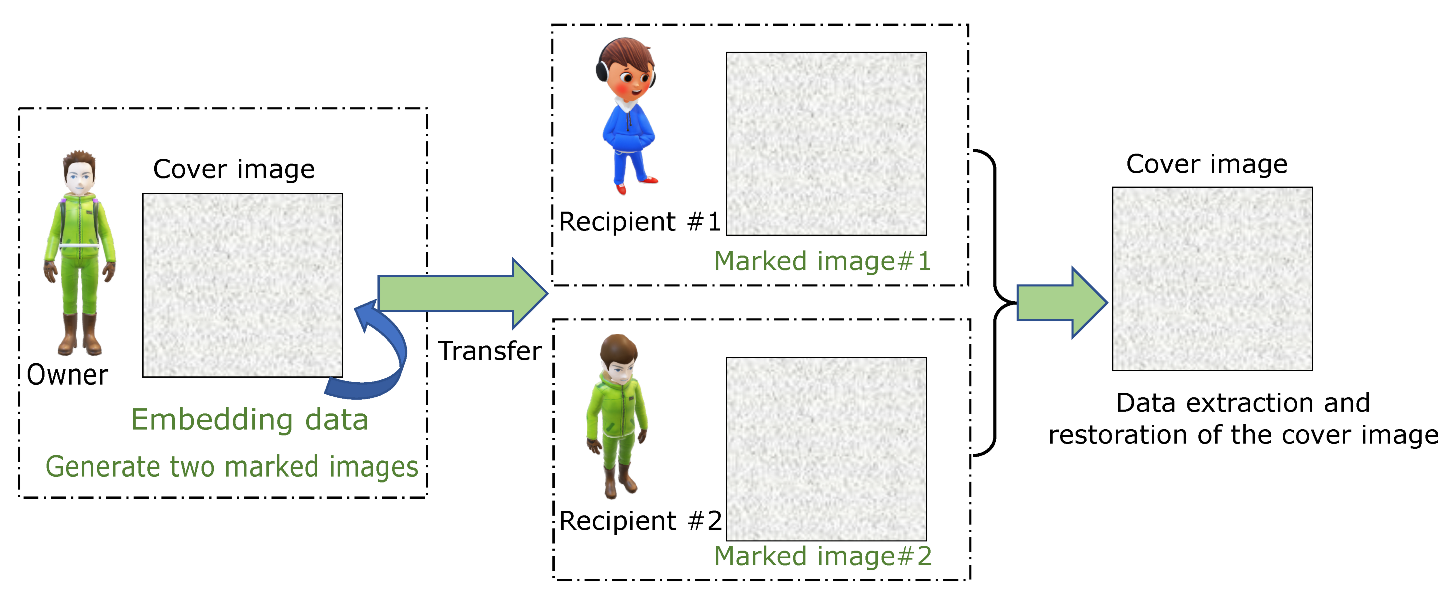
Dual Reversible Data Hiding Based on AMBTC Using Hamming Code and LSB Replacement
Abstract
1. Introduction
2. Preliminary Knowledge
2.1. AMBTC
2.2. Hamming Code
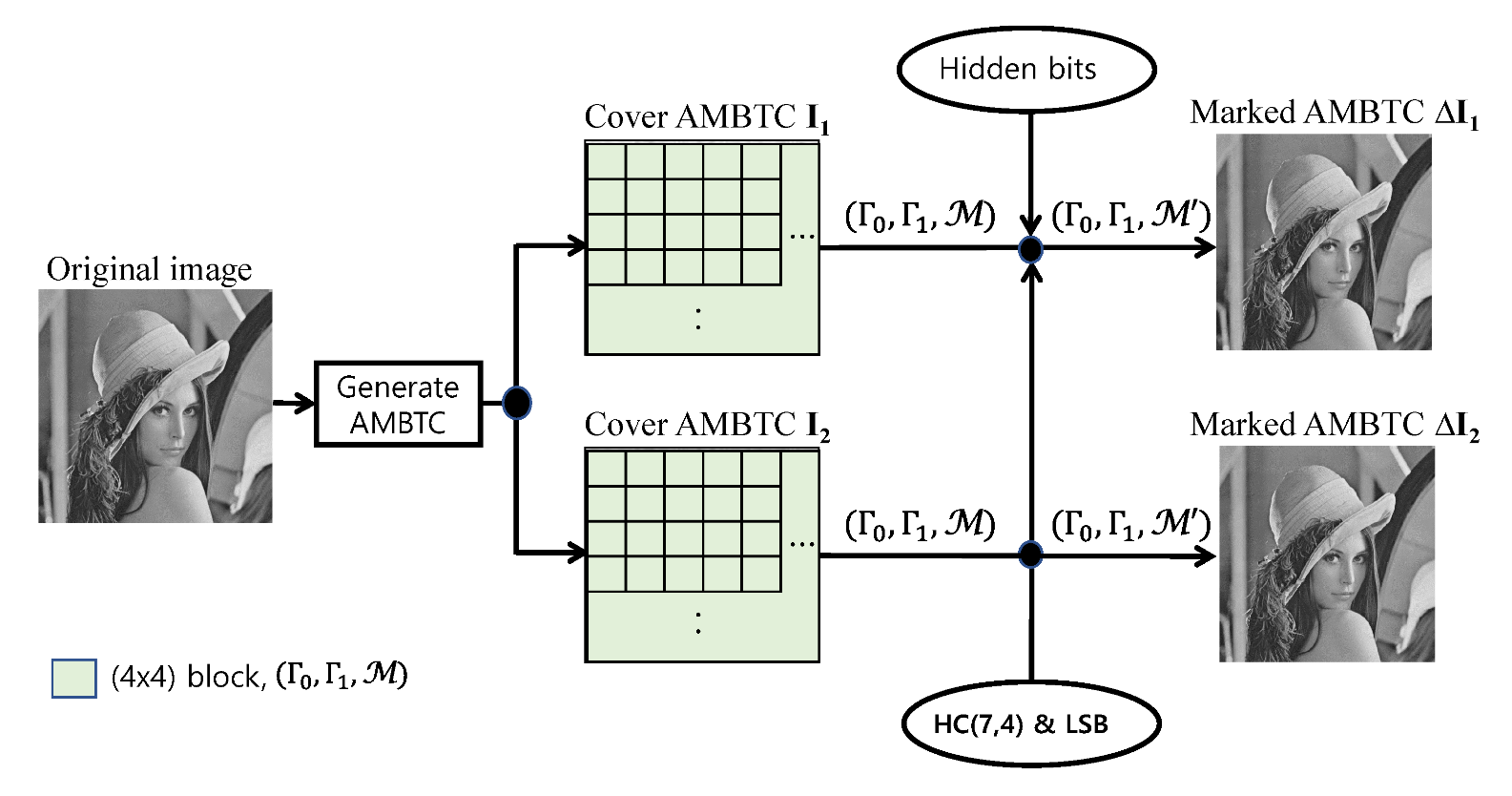
3. Proposed Scheme
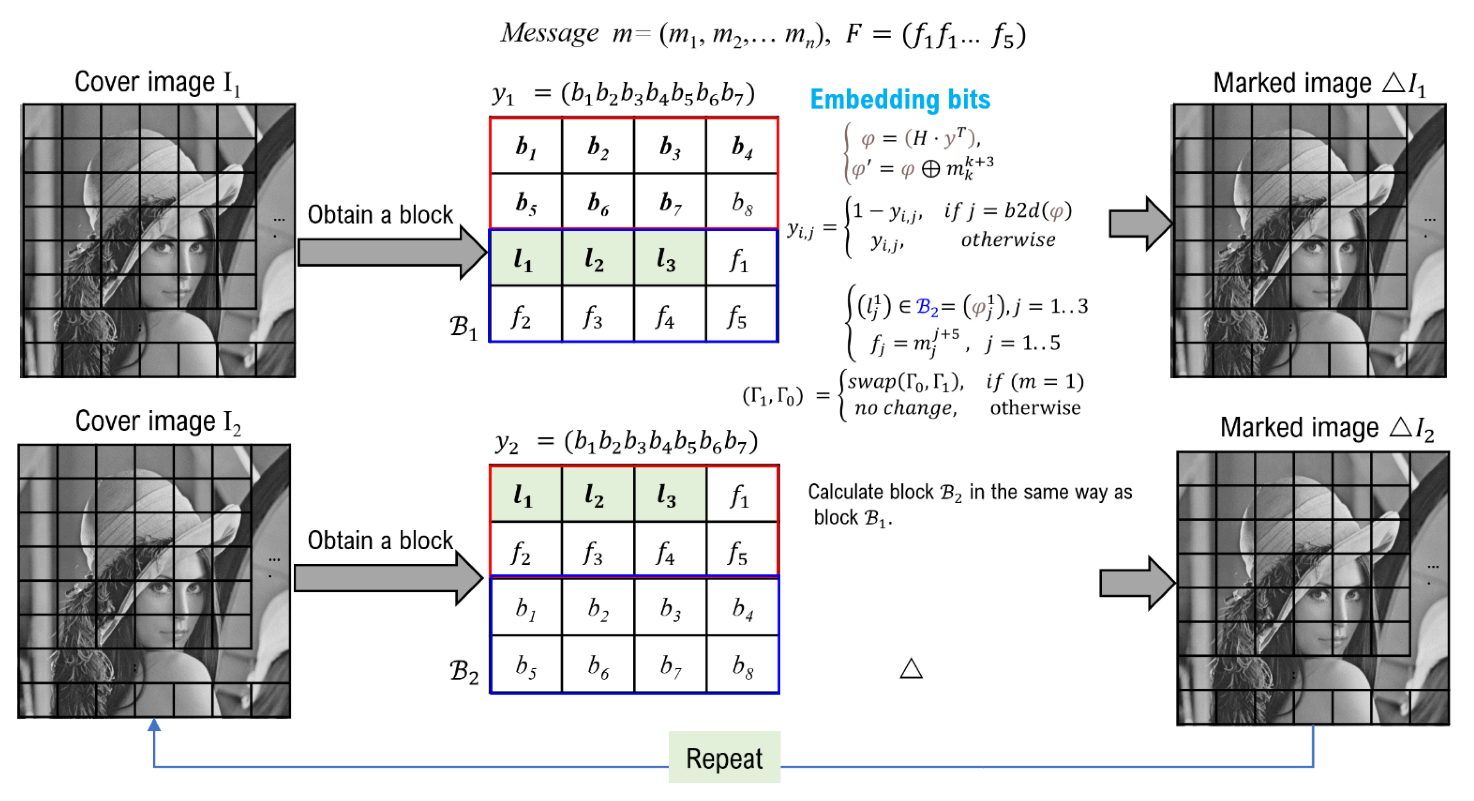
3.1. Data Embedding Procedure
- Step 1:
- The size of two images is and the variable i denotes .
- Step 2:
- Read a sized block and of two cover AMBTC and , respectively.
- Step 3:
- A codeword is constructed with 7 bits each of blocks and . That is, and .
- Step 4:
- Equation (6) is applied to codeword to calculate the syndrome for data hiding, i.e., . The result of XOR operation on the syndrome and 3-bit m is assigned to , i.e., . If the result of converting to a decimal number is not zero, it is calculated as in Equation (7). Assign the syndrome to of block (Figure 3), where is a function that converts a binary number to a decimal number.
- Step 5:
- Step 6:
- For of blocks and , respectively, data are hidden by directly replacing bits with the bitmap. That is, and .
- Step 7:
- A bit of m is hidden using the order of the two quantization levels. If 1 bit of m is ‘0’, the order of the two quantization levels is not changed. If ‘1’, the order of the two quantization levels (Equation (8)) is changed to .
- Step 8:
- If variable i is less than , go to Step 2.
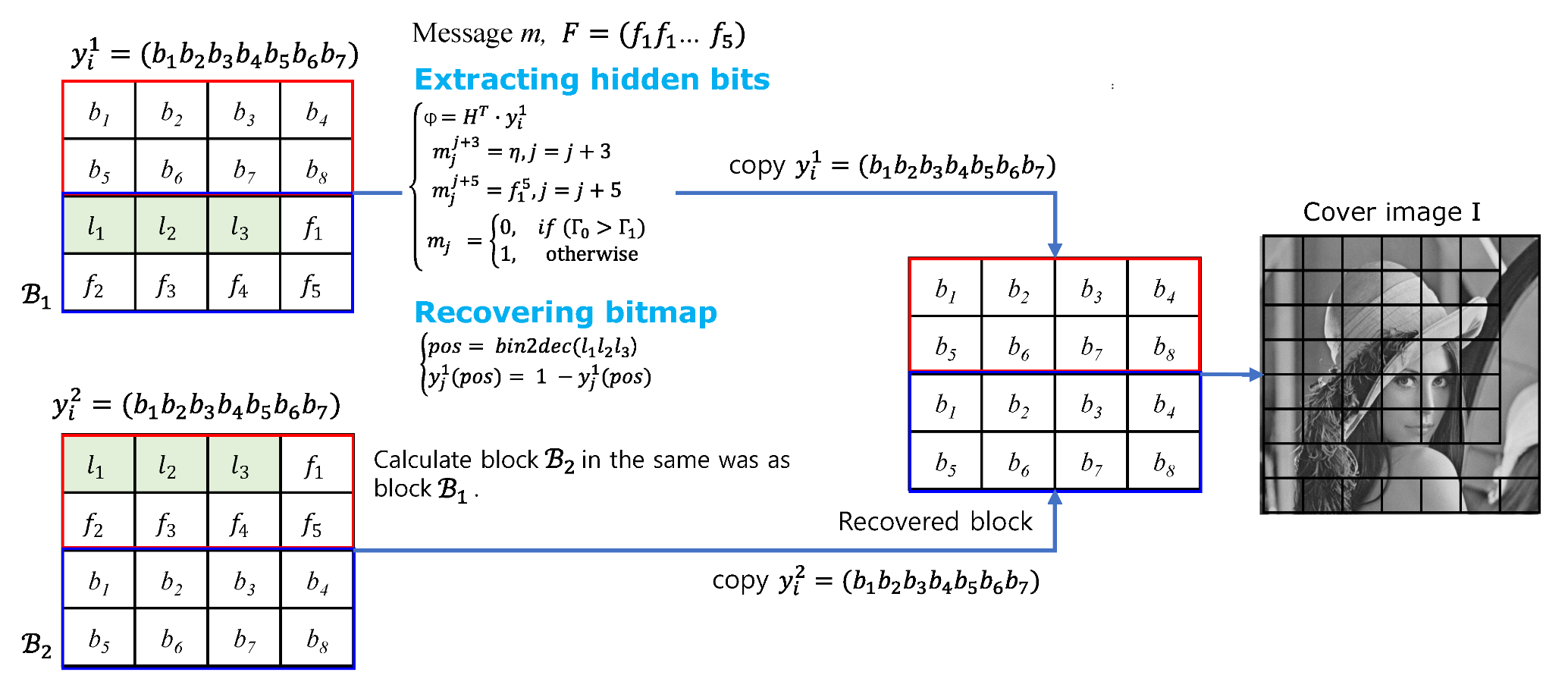
3.2. Data Extraction and Recovering Procedure
- Step 1:
- The size of two images is and the variable i is the block index, i.e., . The variable j is initialized to one.
- Step 2:
- Read a block and of two marked AMBTC and , respectively.
- Step 3:
- A codeword is constructed with 7 bits each of blocks and . That is, and .
- Step 4:
- In order to extract three hidden bits m in the block , the syndrome is calculated for the codeword by Equation (6). Put the extracted bits into m, i.e., .
- Step 5:
- To extract three hidden bits m in the block , the syndrome is calculated for the codeword using Equation (6). Put the extracted bits into m, i.e., .
- Step 6:
- Extract hidden bits from directly , i.e., , and , respectively.
- Step 7:
- According to the order of the two quantization levels, 1 bit is extracted by using Equation (9), and then put into .
- Step 8:
- of is a syndrome for , which is converted to a decimal number, i.e., and then the pixel corresponding to is restored to the original pixel using Equation (10).
- Step 9:
- of is a syndrome for , which is converted to a decimal number, and then the pixel corresponding to is restored to the original pixel by using Equation (10).
- Step 10:
- The restored bitmap block is completed by copying of and of to the bitmap block , and then copied to the corresponding positions of I.
- Step 11:
- If variable index i is less than , go to Step 2.
4. Experimental Results and Discussions
5. Conclusions
Funding
Conflicts of Interest
Abbreviations
| AMBTC | Absolute Moment Block Truncation Coding. |
| BTC | Block Truncation Coding. |
| DH | Data Hiding. |
| RDH | Reversible Data Hiding. |
| Dual RDH | Dual Reversible Data Hiding. |
| HC | Hamming Code. |
| Cover Image 1. | |
| Cover Image 2. | |
| Marked Image 1. | |
| Marked Image 2. | |
| m | Secret bits. |
| A block of the cover image. | |
| y | A codeword. |
| A function that converts a binary number to decimal number. | |
| Syndrome. | |
| x | A pixel. |
| Average pixel value. | |
| and | Two quantization levels. |
| A parity check matrix. |
References
- Suryawanshi, P.; Padiya, P.; Mane, V. Detection of Contrast Enhancement Forgery in Previously and Post Compressed JPEG Images. In Proceedings of the 2019 IEEE 5th International Conference for Convergence in Technology (I2CT), Bombay, India, 29–31 March 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Bender, W.; Gruhl, D.; Morimote, N.; Lu, A. Techniques for data hiding. IBM Syst. J. 1996, 35, 313–336. [Google Scholar] [CrossRef]
- Shi, Y.Q.; Li, X.; Zhang, X.; Wu, H.-T.; Ma, B. Reversible data hiding: Advances in the past two decades. IEEE Access 2016, 4, 3210–3237. [Google Scholar] [CrossRef]
- Kim, C.; Shin, D.-K.; Yang, C.-N.; Leng, L. Hybrid data hiding based on AMBTC using enhanced Hamming code. Appl. Sci. 2020, 10, 5336. [Google Scholar] [CrossRef]
- Yang, C.N.; Wu, S.Y.; Chou, Y.S.; Kim, C. Enhanced stego-image quality and embedding capacity for the partial reversible data hiding scheme. Multimed. Tools Appl. 2019, 78, 18595–18616. [Google Scholar] [CrossRef]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef]
- Wu, D.C.; Tsai, W.H. A steganographic method for images by pixel-value differencing. Pattern Recognit. Lett. 2013, 24, 1613–1626. [Google Scholar] [CrossRef]
- Alattar, A.M. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Process. 2004, 13, 1147–1156. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Tsai, P.Y.; Hu, Y.C.; Yeh, H.L. Reversible image hiding scheme using predictive coding and histogram shifting. Signal Process. 2009, 89, 1129–1143. [Google Scholar] [CrossRef]
- Zhang, W.; Wang, H.; Hou, D.; Yu, N. Reversible Data Hiding in Encrypted Images by Reversible Image Transformation. IEEE Trans. Multimed. 2016, 18, 1469–1479. [Google Scholar] [CrossRef]
- Cao, X.; Du, L.; Wei, X.; Meng, D.; Guo, X. High Capacity Reversible Data Hiding in Encrypted Images by Patch-Level Sparse Representation. IEEE Trans. Cybern. 2016, 46, 1132–1143. [Google Scholar] [CrossRef]
- Ke, Y.; Zhang, M.; Zhang, X.; Liu, J.; Su, T.; Yang, X. A Reversible Data Hiding Scheme in Encrypted Domain for Secret Image Sharing Based on Chinese Remainder Theorem. IEEE Trans. Circuits Syst. Video Technol. 2021, 32, 2469–2481. [Google Scholar] [CrossRef]
- Chang, C.C.; Kieu, T.D.; Chou, Y.C. Reversible data hiding scheme using two steganographic images. In Proceedings of the IEEE Region 10 International Conference (TENCON), Taipei, Taiwan, 30 October–2 November 2007; pp. 1–4. [Google Scholar]
- Chang, C.C.; Chou, Y.C.; Kieu, T.D. Information hiding in dual images with reversibility. In Proceedings of the 3rd International Conference on Multimedia and Ubiquitous Engineering, Qingdao, China, 4–6 June 2009; pp. 145–152. [Google Scholar]
- Lee, C.F.; Huang, Y.L. Reversible data hiding scheme based on dual stegano-images using orientation combinations. Telecommun. Syst. 2013, 52, 2237–2247. [Google Scholar] [CrossRef]
- Chang, C.C.; Lu, T.C.; Horng, G.; Huang, Y.H.; Hsu, Y.M. A high payload data embedding scheme using dual stego-images with reversibility. In Proceedings of the 3rd International Conference on Information, Communications and Signal Processing, Islamabad, Pakistan, 16–18 December 2013; pp. 1–5. [Google Scholar]
- Lin, J.Y.; Chen, Y.; Chang, C.C.; Hu, Y.C. Dual-image with integrity verification using exploiting modification direction. Multimed. Tools Appl. 2019, 78, 25855–25872. [Google Scholar] [CrossRef]
- Lu, T.C.; Wu, J.H.; Huang, C.C. Dual-image-based reversible data hiding method using center folding strategy. Signal Process. 2015, 115, 195–213. [Google Scholar] [CrossRef]
- Lu, T.C.; Tseng, C.Y.; Wu, J.H. Dual imaging-based reversible hiding technique using LSB matching. Signal Process. 2015, 108, 77–89. [Google Scholar] [CrossRef]
- Jana, B.; Giri, D.; Mondal, S.K. Dual image based reversible data hiding scheme using (7,4) hamming code. Multimed. Tools Appl. 2018, 77, 763–785. [Google Scholar] [CrossRef]
- Yao, H.; Qin, C.; Tang, Z.; Tian, Y. Improved dual-image reversible data hiding method using the selection strategy of shiftable pixels’ coordinates with minimum distortion. Signal Process. 2017, 135, 26–35. [Google Scholar] [CrossRef]
- Liu, Y.; Chang, C.C. A turtle shell-based visual secret sharing scheme with reversibility and authentication. Multimed. Tools Appl. 2018, 77, 25295–25310. [Google Scholar] [CrossRef]
- Chen, X.; Hong, C. An efficient dual-image reversible data hiding scheme based on exploiting modification direction. J. Inf. Secur. Appl. 2021, 58, 102702. [Google Scholar] [CrossRef]
- Sun, Y.X.; Li, Q.; Yan, B.; Pan, J.S.; Yang, H.M. Reversible data hiding in dual encrypted halftone image using matrix embedding, Multimed. Tools Appl. 2020, 79, 27659–27682. [Google Scholar] [CrossRef]
- Shamir, A. How to share a secret. Commun. Assoc. Comput. Mach. 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Naor, M.; Shamir, A. Visual cryptography. In Advances in Cryptology—EUROCRYPT’94, Perugia, Italy, 9–12 May 1994; De Santis, A., Ed.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 1995; Volume 950. [Google Scholar]
- Delp, E.; Mitchell, O. Image compression using block truncation coding. IEEE Trans. Commun. 1979, 27, 1335–1342. [Google Scholar] [CrossRef]
- Lema, M.D.; Mitchell, O.R. Absolute moment block truncation coding and its application to color images. IEEE Trans. Commun. 1984, 32, 1148–1157. [Google Scholar] [CrossRef]
- Chuang, J.C.; Chang, C.C. Using a simple and fast image compression algorithm to hide secret information. Int. J. Comput. Appl. 2006, 28, 329–333. [Google Scholar]
- Ou, D.; Sun, W. High payload image steganography with minimum distortion based on absolute moment block truncation coding. Multimed. Tools Appl. 2015, 74, 9117–9139. [Google Scholar] [CrossRef]
- Chen, J.; Hong, W.; Chen, T.S.; Shiu, C.W. Steganography for BTC compressed images using no distortion technique. Imaging Sci. J. 2013, 58, 177–185. [Google Scholar] [CrossRef]
- Sun, W.; Lu, Z.M.; Wen, Y.C.; Yu, F.X.; Shen, R.J. High Performance Reversible Data Hiding for Block Truncation Coding Compressed Images. Signal Image Video Process. 2013, 7, 297–306. [Google Scholar] [CrossRef]
- Chang, C.C.; Chen, T.S.; Wang, Y.K.; Liu, Y.J. A reversible data hiding scheme based on absolute moment block truncation coding compression using exclusive OR operator. Multimed. Tools Appl. 2018, 77, 9039–9053. [Google Scholar] [CrossRef]
- Hong, W.; Zhou, X.Y.; Weng, S.W. Joint adaptive coding and reversible data hiding for AMBTC compressed images. Symmetry 2018, 10, 254. [Google Scholar] [CrossRef]
- Rurik, W.; Mazumdar, A. Hamming codes as error-reducing codes. In Proceedings of the 2016 IEEE Information Theory Workshop (ITW), Cambridge, UK, 11–14 September 2016; pp. 404–408. [Google Scholar]
- Moon, T.K. Error Correction Coding—Mathematical Methods and Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 2005; pp. 2001–2006. [Google Scholar]
- Image Databases. Available online: https://www.imageprocessingplace.com/root_files_V3/image_databases.htm (accessed on 5 May 2022).
- Horé, A.; Ziou, D. Image Quality Metrics: PSNR vs. SSIM. In Proceedings of the 20th International Conference on Pattern Recognition, Istanbul, Turkey, 23–26 August 2010; pp. 2366–2369. [Google Scholar] [CrossRef]
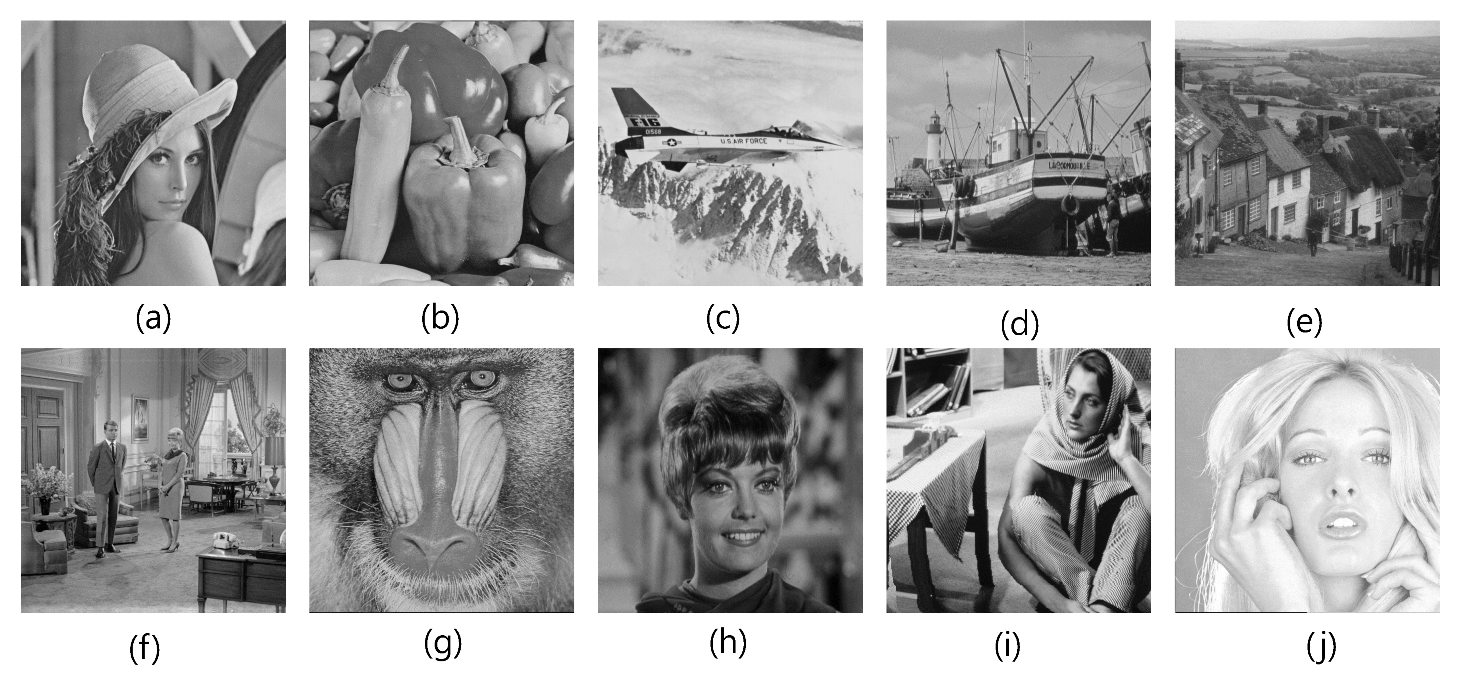
| Images | EC | #1 | #2 | #1 | #2 | ||
|---|---|---|---|---|---|---|---|
| Lena | 33.6556 | 0.9468 | 148705 | 45.2557 | 45.2875 | 33.3654 | 33.3702 |
| Pepper | 34.0968 | 0.9395 | 114593 | 45.7492 | 45.7017 | 33.8055 | 33.8068 |
| Airplane | 32.0372 | 0.9504 | 168193 | 45.7197 | 45.756 | 31.8562 | 31.8587 |
| Boat | 31.5700 | 0.9388 | 142865 | 46.603 | 46.6046 | 31.4365 | 31.4365 |
| Goldhill | 32.836 | 0.9208 | 67537 | 50.1685 | 50.1580 | 32.7545 | 32.7551 |
| Couple | 31.2567 | 0.9241 | 70193 | 48.8354 | 48.8542 | 31.1806 | 31.1809 |
| Baboon | 26.9765 | 0.8872 | 34449 | 57.7565 | 57.494 | 26.9726 | 26.9726 |
| Zelda | 36.6537 | 0.9476 | 123201 | 45.1824 | 45.1478 | 36.0805 | 36.075 |
| Barbara | 27.0756 | 0.9248 | 89553 | 48.9218 | 48.9832 | 27.0478 | 27.0477 |
| Tiffany | 35.6576 | 0.9473 | 147521 | 45.1695 | 45.1695 | 35.1957 | 35.206 |
| Average | 31.8235 | 0.9311 | 106588 | 48.2436 | 48.2208 | 31.6111 | 31.6115 |
| Original Image I | Threshold T | EC | PSNR | PSNR | Avg. PSNR |
|---|---|---|---|---|---|
| Lena | 5 | 148,705 | 33.3654 | 33.3702 | 33.3678 |
| 10 | 206865 | 32.8208 | 32.8335 | 32.8271 | |
| 15 | 232545 | 32.2292 | 32.2542 | 32.2417 | |
| 20 | 247313 | 31.6594 | 31.699 | 31.6792 | |
| Boat | 5 | 142865 | 31.4365 | 31.4365 | 31.4365 |
| 10 | 174529 | 31.2241 | 31.2172 | 31.2206 | |
| 15 | 199249 | 30.8229 | 30.8091 | 30.816 | |
| 20 | 219425 | 30.2416 | 30.2505 | 30.246 | |
| Pepper | 5 | 114593 | 33.8055 | 33.8068 | 33.8061 |
| 10 | 213985 | 32.8545 | 32.8637 | 32.8591 | |
| 15 | 241681 | 32.2336 | 32.2521 | 32.2428 | |
| 20 | 254593 | 31.7156 | 31.7641 | 31.7398 | |
| Goldhill | 5 | 67537 | 32.7545 | 32.7551 | 32.7548 |
| 10 | 141073 | 32.0922 | 32.0991 | 32.0956 | |
| 15 | 195777 | 31.0982 | 31.1116 | 31.1049 | |
| 20 | 225857 | 30.2253 | 30.2423 | 30.2338 | |
| Zelda | 5 | 123201 | 36.0805 | 36.075 | 36.0777 |
| 10 | 226369 | 34.5375 | 34.5615 | 34.5495 | |
| 15 | 253425 | 33.6805 | 33.6865 | 33.6835 | |
| 20 | 267457 | 32.9338 | 32.9668 | 32.9503 | |
| Barbara | 5 | 89553 | 27.0478 | 27.0477 | 27.0477 |
| 10 | 135969 | 26.9345 | 26.9329 | 26.9337 | |
| 15 | 158497 | 26.7962 | 26.7973 | 26.7967 | |
| 20 | 267457 | 26.6557 | 26.6545 | 26.6551 | |
| Airplane | 5 | 168193 | 31.8562 | 31.8587 | 31.8574 |
| 10 | 208545 | 31.5844 | 31.584 | 31.5842 | |
| 15 | 227873 | 31.232 | 31.2363 | 31.2341 | |
| 20 | 240625 | 30.8257 | 30.8355 | 30.8306 | |
| Couple | 5 | 70193 | 31.1806 | 31.1809 | 31.1807 |
| 10 | 143009 | 30.7385 | 30.7422 | 30.7403 | |
| 15 | 180721 | 30.1983 | 30.1906 | 30.1944 | |
| 20 | 205217 | 29.6088 | 29.6046 | 29.6067 | |
| Tiffany | 5 | 147521 | 35.1957 | 35.206 | 35.2008 |
| 10 | 211825 | 34.3111 | 34.3197 | 34.3154 | |
| 15 | 240433 | 33.4334 | 33.4311 | 33.4322 | |
| 20 | 255985 | 32.6425 | 32.6755 | 32.659 | |
| Baboon | 5 | 34449 | 26.9726 | 26.9726 | 26.9726 |
| 10 | 70481 | 26.8768 | 26.8781 | 26.8774 | |
| 15 | 104593 | 26.664 | 26.6665 | 26.6652 | |
| 20 | 128225 | 26.4056 | 26.4056 | 26.4056 |
| Images | Sun et al. [33] | Chang et al. [34] | W. Hong et al. [35] | The Proposed | ||||||
|---|---|---|---|---|---|---|---|---|---|---|
| EC | PSNR | EC | PSNR | EC | PSNR | EC | PSNR | PSNR | Avg. PSNR | |
| Baboon | 64,008 | 26.98 | 151439 | 26.34 | 64516 | 26.98 | 128225 | 26.4056 | 26.4056 | 26.4056 |
| Boats | - | - | 166786 | 31.16 | 64516 | 31.12 | 219425 | 30.2416 | 30.2505 | 30.2460 |
| Goldhill | - | - | 168185 | 33.72 | 64516 | 32.83 | 225857 | 30.2253 | 30.2423 | 30.2338 |
| Airplane | 64,008 | 31.97 | 177814 | 33.29 | 64516 | 31.97 | 240625 | 30.8257 | 30.8355 | 30.8306 |
| Lena | 64,008 | 33.24 | 175145 | 33.72 | 64516 | 33.24 | 247313 | 31.6594 | 31.6990 | 31.6792 |
| Peppers | 64,008 | 33.42 | 174222 | 34.10 | 64516 | 33.42 | 254593 | 31.7156 | 31.7641 | 31.7398 |
| Tiffany | 64,008 | 35.77 | - | - | 64516 | 35.77 | 255985 | 32.6425 | 32.6755 | 32.6590 |
| Average | 64,008 | 32.28 | 168932 | 32.06 | 64516 | 32.19 | 224575 | 30.5308 | 30.5500 | 30.5400 |
| Images | File Size | Lee et al. [15] | Liu et al. [23] | Lin et al. [18] | The Propose | |
|---|---|---|---|---|---|---|
| ER | ER | ER | File Size | ER | ||
| Baboon | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Barbara | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Lena | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Pepper | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Goldhill | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Airplane | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Boat | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Couple | 258 KB | 1.09 | 1 | 1.07 | 64 KB | 0.56 |
| Zela | 258 KB | 1.09 | 0.99 | 1.07 | 64 KB | 0.56 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, C. Dual Reversible Data Hiding Based on AMBTC Using Hamming Code and LSB Replacement. Electronics 2022, 11, 3210. https://doi.org/10.3390/electronics11193210
Kim C. Dual Reversible Data Hiding Based on AMBTC Using Hamming Code and LSB Replacement. Electronics. 2022; 11(19):3210. https://doi.org/10.3390/electronics11193210
Chicago/Turabian StyleKim, Cheonshik. 2022. "Dual Reversible Data Hiding Based on AMBTC Using Hamming Code and LSB Replacement" Electronics 11, no. 19: 3210. https://doi.org/10.3390/electronics11193210
APA StyleKim, C. (2022). Dual Reversible Data Hiding Based on AMBTC Using Hamming Code and LSB Replacement. Electronics, 11(19), 3210. https://doi.org/10.3390/electronics11193210







