A Secure Personal Health Record Sharing System with Key Aggregate Dynamic Searchable Encryption
Abstract
:1. Introduction
1.1. Motivation, Methodology, and Contributions
- We propose a secure PHR sharing system that ensures patients’ authority over their personal records by suggesting a key aggregate dynamic searchable encryption. Thus, patients can manage and regulate access to their own PHRs.
- We provide dynamic searches for allowing users to obtain specific PHRs with low computational costs. We support dynamic searches using LSSS. In the proposed scheme, users can generate a trapdoor with various keywords at the same time to acquire a PHR.
- The proposed scheme utilizes a blockchain to provide data integrity and prevent the single point of failure. In addition, we utilize a smart contract to realize the secure and effective keyword searches and trapdoor verification.
- We store PHRs using an IPFS, which is a decentralized data storage system. Since the IPFS is a content-addressable protocol generating unique hash values for stored PHRs, it ensures the security of PHRs and avoids duplications.
1.2. Organization
2. Related Works
3. Preliminaries
3.1. System Models
3.1.1. Network Model
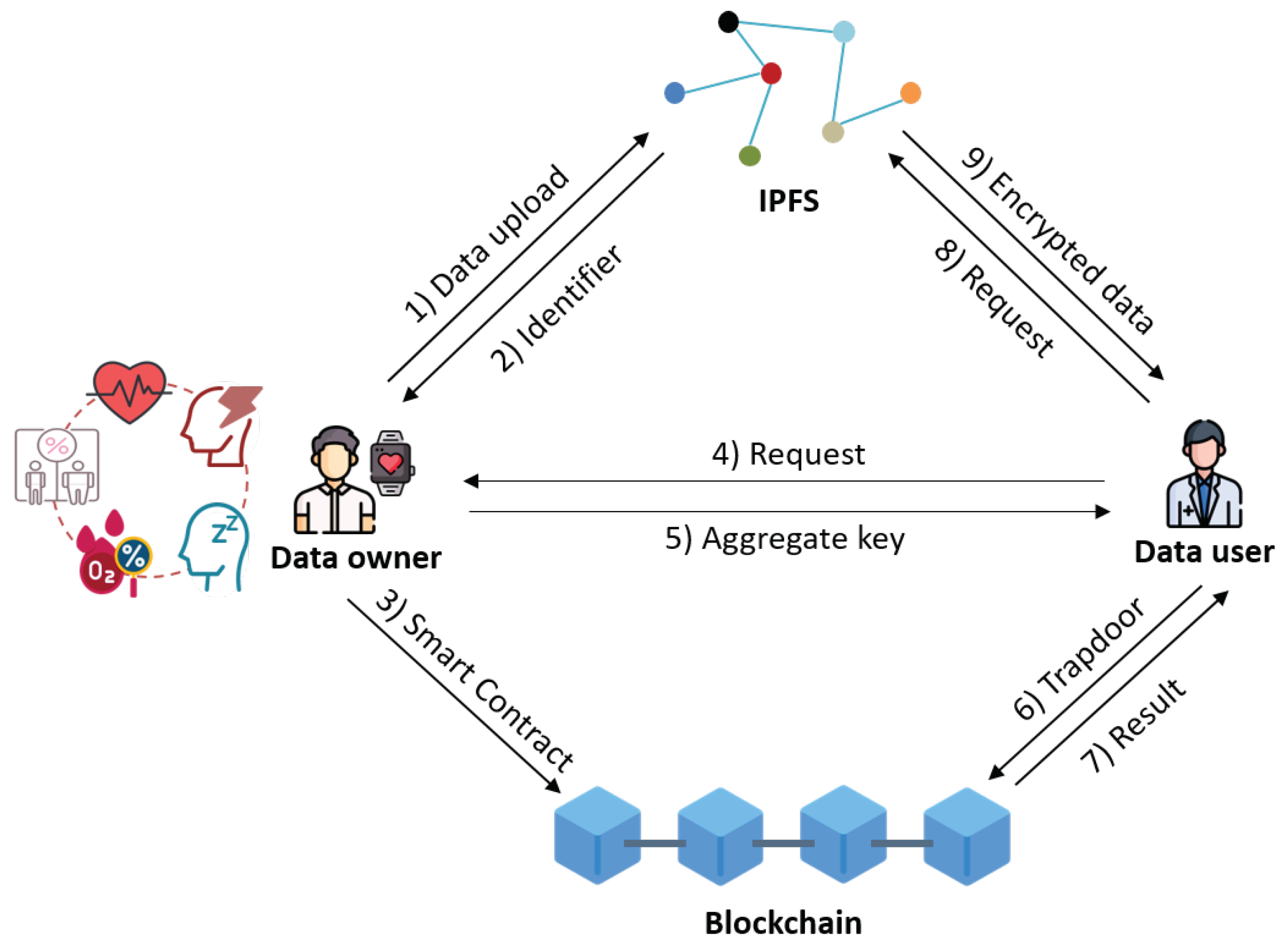
- Data owner (DO): The manages his/her own PHR for self-directed health care. The generates the system parameters for his/her own PHR and controls the access rights of the using an aggregate key. The uploads the encrypted PHR to the IPFS and generates and uploads the smart contract to the blockchain for realizing the secure verification of the trapdoor.
- Data user (DU): The is the person that wants to access the PHR of the . To obtain the read rights of the PHR, the requests the aggregate key from the . The can obtain the aggregate key by mutual authentication with the . The can request and receive the PHR by communicating with the blockchain and IPFS. For the PHR decrypted using the aggregate key, the can verify the integrity through the received verification value from the blockchain.
- IPFS: IPFS is a P2P decentralized database. In the proposed system, the IPFS stores the encrypted PHR of the and returns a unique hash address for the stored PHR as an identifier. In addition, when the requests the PHR through the identifier, the IPFS returns the corresponding results to the .
- Blockchain: The architecture of the blockchain is a public permissionless blockchain since all network parties can access the smart contract in the blockchain. The proposed system employs the Practical Byzantine Fault Tolerance (PBFT) consensus algorithm for the validation of transactions and generation of blocks. The blockchain implements the stored smart contract when the sends the trapdoor. Then, the blockchain transmits the identifier and verification value as a result.
- 1
- The generates the system parameters for his/her own PHR and the and generate their own public and private key pairs with the system parameters. Then, the encrypts the PHR and uploads it to the IPFS.
- 2
- The IPFS stores the received PHR. Then, the IPFS generates and sends an unique hash address as an identifier for the received PHR to the . The calculates the keyword ciphertexts corresponding to the PHR and verification values. Then, the generates the smart contract using the keyword, identifier, and verification value, and uploads the smart contract to the blockchain.
- 3
- The requests the aggregate key for reading the ’s PHR by sending the ’s credentials.
- 4
- The verifies the ’s credentials, and if the is valid, the generates and sends the aggregate key and secret value to the .
- 5
- The generates the trapdoor using the keyword and received secret value. Then, the sends the trapdoor to the blockchain to obtain the identifier and verification value for the encrypted PHR.
- 6
- The blockchain checks the validity of the , and if the is validated, the blockchain sends the corresponding PHR’s identifier and verification values to the as a result.
- 7
- The sends a request for the PHR to the IPFS using the received identifier.
- 8
- The IPFS sends the encrypted PHR to the by matching the identifier in the database. The decrypts the received PHR using the aggregate key. Then, the checks whether the PHR is the data of the using the verification value. If it is correct, the process is successfully completed.
3.1.2. Threat Model
3.1.3. Security Model
- Data privacy: The PHR contains the sensitive information of the . If the PHR is leaked, the ’s life life could be put in danger or compromised. The PHR ciphertext does not reveal any information about the plaintext to the adversary. Thus, data confidentiality and integrity must be ensured in the PHR sharing system. We prove data privacy using the IND-CPA model.
- Ciphertext privacy: The keyword ciphertext does not expose any information about the corresponding keywords to the adversary who is the unauthorized user. We prove ciphertext privacy using the IND-CKA model.
- Trapdoor privacy: For secure PHR sharing, only the authorized can access the PHR, i.e., the trapdoor with the received secret values can be generated. The trapdoor does not disclose any information about the corresponding keywords to the adversary who is not authorized by the . Using the IND-KGA model, we demonstrate that the proposed scheme ensures trapdoor privacy.
- Init.Adversary selects a challenge set that wants to attack.
- Setup.Simulator executes the setup phase and sends the public parameters to .
- Phase 1. queries the aggregate key for set to . Then, performs the aggregate key request phase and sends to .
- Challenge. picks two plaintext and , where , from a set of possible plaintexts belonging to class and submits them to . flips the coin , encrypts in the data upload phase and sends the ciphertext to .
- Phase 2. repeatsPhase 1for , that is, the aggregate sets that contain data classes apart from those in the target set .
- Guess. outputs a guess of δ to . If , wins the game.
- Init.Adversary chooses a challenge set that wants to attack.
- Setup.Simulator executes the setup phase and returns the public parameters to .
- Phase 1.First, sends an aggregate key request query to . implements the aggregate key request phase and returns to . Then, transmits the trapdoor query for the keyword . If , executes the data request phase and responds with the trapdoor.
- Challenge. chooses two keywords and , where and of a challenge set , to . flips the coin and responds with the ciphertext for in the data upload phase to .
- Phase 2. repeatsPhase 1with the restriction that neither nor are used.
- Guess. outputs a guess of δ to . If , wins the game.
- Init.Adversary gives to the simulator a challenge set .
- Setup. executes the setup phase and returns the results to .
- Phase 1. first sends an aggregate key request query to . executes the aggregate key request phase and sends to . Then, sends the ciphertext query for the keyword . If , executes the data upload phase and responds with the ciphertext.
- Challenge. submits two equal-length keywords and to within . flips the coin and responds with the trapdoor for in the data request phase to .
- Phase 2. repeatsPhase 1with the restriction that neither nor are used.
- Guess. outputs a guess of δ to . If , wins the game.
3.2. Bilinear Maps
- Bilinearity: For and , we have .
- Non-degeneracy: , .
- Computability: , can be computed in polynomial time.
3.3. Linear Secret-Sharing Scheme (LSSS)
- For each party, the shares of a secret form a vector over .
- There is an matrix called the share-generating matrix on and a function that maps each row of to a specific party in . During the generation of the shares, we give consideration to the column vector , where . Then, l shares a vector of s, which is equal to . In addition, the share belongs to , where is the jth row of .
3.4. Computational Assumption
3.4.1. Decisional Diffie–Hellman (DDH) Assumption
3.4.2. Decisional Bilinear Diffie–Hellman (DBDH) Assumption
3.5. Blockchain
- Public permissionless blockchain: every node can participate in the consensus process, read and write the transactions, and maintain the ledgers.
- Public permissioned blockchain: the nodes are permitted to read or convert the state of the ledger with approved performing consensus, that is, only authorized nodes in the network can write in the ledger.
- Private permissionless blockchain: only authorized nodes are allowed to participate; the read and write abilities are owned by authorized nodes; all transactions can be conducted privately, and if necessary, the transaction can be opened for verification.
- Private permissioned blockchain: only authorized nodes can access, perform operations over the distributed ledger, and participate in the consensus process.
3.6. InterPlanetary File Systems
4. Proposed Scheme
4.1. Setup Phase
4.2. Key Generation Phase
4.3. Data Upload Phase
- Step 1:
- The generates and computes , , for the . Then, the sends to the IPFS.
- Step 2:
- The IPFS stores in the database and computes the identifier . Then, the IPFS sends to the .
- Step 3:
- The selects , where , and matrix . The computes , and calculates , , for , where is the number of keywords about . Then, the generates the smart contract using and uploads it to the blockchain.
4.4. Aggregate Key Request Phase
- Step 1:
- The generates and . The computes , , , , , . Then, the sends to the through a public channel.
- Step 2:
- After receiving the message, the checks . Then, the computes , , and checks . If it is correct, the computes , , , , , , , , . Then, the sends to the .
- Step 3:
- Upon receiving the message, the checks . Then, the computes , , , and checks whether and . If it is valid, the obtains the secret values by computing .
4.5. Data Retrieval Phase
- Step 1:
- The generates and , and computes , for , where is the number of search keywords. Then, the sends to the blockchain, where .
- Step 2:
- With the received message, the blockchain checks and implements the smart contract. The blockchain computes satisfying and checks whether . If it is correct, the blockchain sends all matched and to the .
4.6. Data Request Phase
- Step 1:
- The sends the identifier to the IPFS for the PHR that the wants.
- Step 2:
- The IPFS finds the encrypted document, which is matched with . Then, the IPFS sends to the .
- Step 3:
- After receiving the message, the computes . Then, the checks whether . If it is valid, the obtains the right PHR, and the process of the proposed PHR sharing system is successfully completed.
5. Informal Security Analysis
5.1. Impersonation Attack
5.2. Replay Attack
5.3. Man-in-the-Middle (MITM) Attack
5.4. Insider Attack
5.5. Correctness
5.5.1. Dynamic Keyword
5.5.2. PHR
5.6. Perfect Forward Secrecy
5.7. Anonymity
5.8. Mutual Authentication
6. Formal Security Analysis
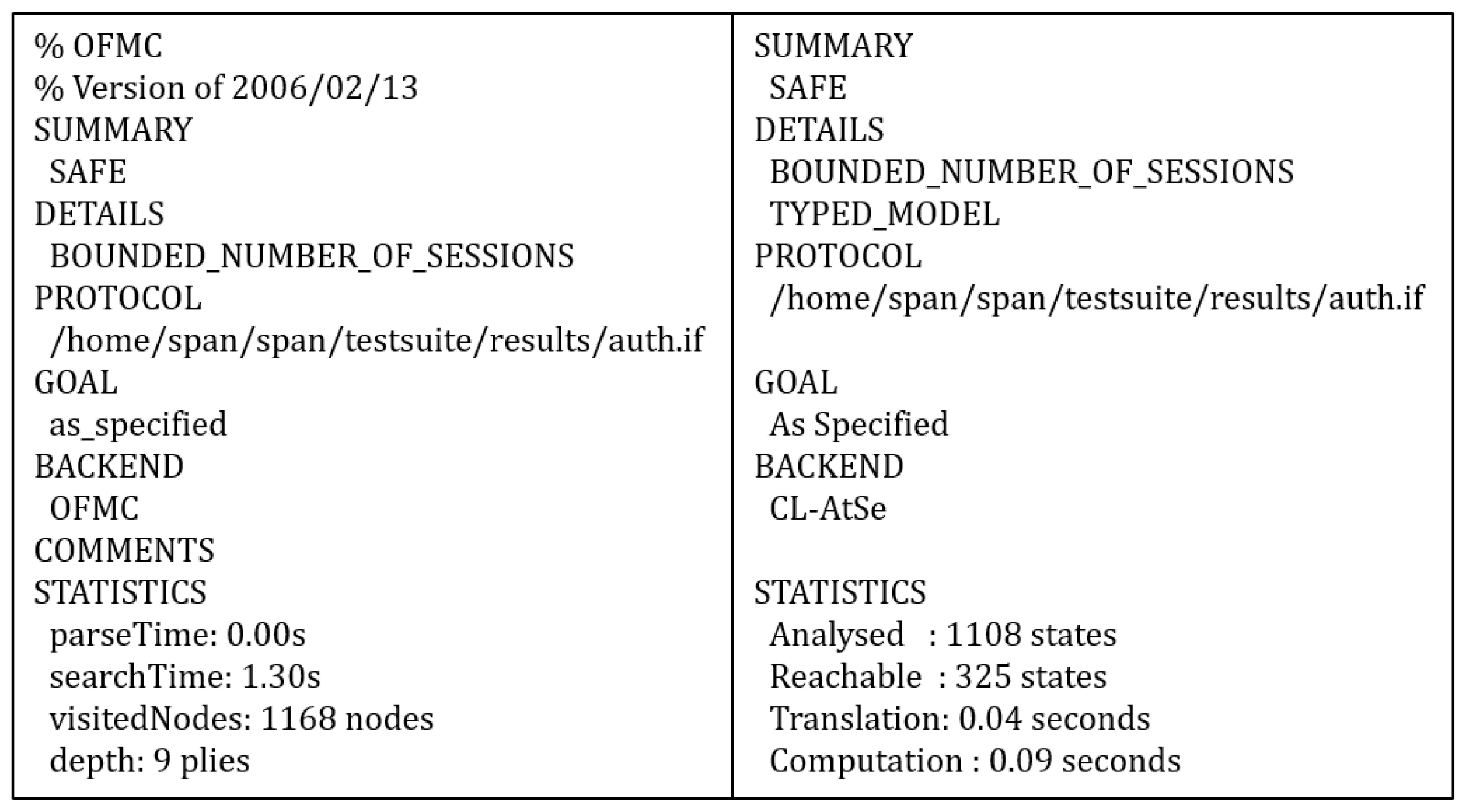
6.1. AVISPA Simulation Tool
6.2. Formal Security Analysis using BAN Logic
6.2.1. Rules
- Message meaning rule ():
- Nonce verification rule ():
- Jurisdiction rule ():
- Freshness rule ():
- Belief rule ():
6.2.2. Goals
- Goal 1:
- Goal 2:
- Goal 3:
- Goal 4:
6.2.3. Idealized Forms
- :
- :
6.2.4. Assumptions
- :
- :
- :
- :
- :
- :
6.2.5. Proof
- Step 1:
- can be obtained from .
- Step 2:
- can be obtained by applying the with .
- Step 3:
- can be gained from the with and .
- Step 4:
- can be acquired by applying the with and .
- Step 5:
- can be obtained from .
- Step 6:
- can be gained from with and .
- Step 7:
- can be obtained by applying with and .
- Step 8:
- can be obtained from with and .
- Step 9:
- and can be obtained from and since .(Goal 3)(Goal 4)
- Step 10:
- and can be obtained by applying from , , , and .(Goal 1)(Goal 2)
6.3. IND-CPA Security
6.4. IND-CKA Security
6.5. IND-KGA Security
7. Security and Performance Analysis
7.1. Security Features
7.2. Computational Costs
7.3. Communication Costs
8. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- ISO. Health Informatics—Capacity-Based eHealth Architecture Roadmap—Part 2: Architectural Components and Maturity Model; Technical Report (ISO/TRTR14639-2); ISO: Geneva, Switzerland, 2014; Available online: https://www.iso.org/standard/54903.html (accessed on 13 April 2022).
- Deng, F.; Wang, Y.; Peng, L.; Xiong, H.; Geng, J.; Qin, Z. Ciphertext-policy attribute-based signcryption with verifiable outsourced designcryption for sharing personal health records. IEEE Access 2018, 6, 39473–39486. [Google Scholar] [CrossRef]
- MTBC PHR: Personal Health Records for Patients. Available online: https://phr.mtbc.com/phrdefault.aspx (accessed on 13 April 2022).
- Capzule PHR: Your Family Health Data in One App. (Personal Medical/Health Records). Available online: https://www.capzule.com/ (accessed on 13 April 2022).
- My Medical—The Personal Medical Record for You, The Patient. Available online: http://mymedicalapp.com/ (accessed on 13 April 2022).
- Garg, N.; Wazid, M.; Das, A.K.; Singh, D.P.; Rodrigues, J.J.P.C.; Park, Y. BAKMP-IoMT: Design of blockchain enabled authenticated key management protocol for internet of medical things deployment. IEEE Access 2020, 8, 95956–95977. [Google Scholar] [CrossRef]
- Morales-Sandoval, M.; Cabello, M.H.; Marin-Castro, H.M.; Compean, J.L.G. Attribute-based encryption approach for storage, sharing and retrieval of encrypted data in the cloud. IEEE Access 2020, 8, 170101–170116. [Google Scholar] [CrossRef]
- Banerjee, S.; Roy, S.; Odelu, V.; Das, A.K.; Chattopadhyay, S.; Rodrigues, J.J.P.C.; Park, Y. Multi-authority CP-ABE-based user access control scheme with constant-size key and ciphertext for IoT deployment. J. Inf. Secur. Appl. 2020, 53, 102503. [Google Scholar] [CrossRef]
- Cui, B.; Liu, Z.; Wang, L. Key-aggregate searchable encryption (KASE) for group data sharing via cloud storage. IEEE Trans. Comput. 2016, 65, 2374–2385. [Google Scholar] [CrossRef]
- Kim, M.; Lee, J.; Oh, J.; Park, K.; Park, Y.; Park, K. Blockchain based energy trading scheme for vehicle-to-vehicle using decentralized identifiers. Appl. Energy 2022, 322, 119445. [Google Scholar] [CrossRef]
- Chen, CM.; Tie, Z.; Wang, E.K.; Khan, M.K.; Kumar, S.; Kumari, S. Verifiable dynamic ranked search with forward privacy over encrypted cloud data. Peer-to-Peer Netw. Appl. 2021, 14, 2977–2991. [Google Scholar] [CrossRef]
- Yu, S.; Park, Y. A robust authentication protocol for wireless medical sensor networks using blockchain and physically unclonable functions. IEEE Internet Things J. 2022, 9, 20214–20228. [Google Scholar] [CrossRef]
- Chattaraj, D.; Bera, B.; Das, A.K.; Rodrigues, J.J.P.C.; Park, Y. Designing fine-grained access control for software-defined networks using private blockchain. IEEE Internet Things J. 2022, 9, 1542–1559. [Google Scholar] [CrossRef]
- Chen, CM.; Deng, X.; Kumar, S.; Kumari, S.; Islam, S.K. Blockchain-based medical data sharing schedule guaranteeing security of individual entities. J. Ambient Intell. Humaniz. Comput. 2021. [Google Scholar] [CrossRef]
- Park, K.; Lee, J.; Das, A.K.; Park, Y. BPPS: Blockchain-enabled privacy-preserving scheme for demand-response management in smart grid environments. IEEE Trans. Dependable Secur. Comput. 2022; Early access. [Google Scholar]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, R.; Srivastava, G.; Gupta, G.P.; Tripathi, R.; Gadekallu, T.R.; Xiong, N.N. PPSF: A privacy-preserving and secure framework using blockchain-based machine-learning for IoT-driven smart cities. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2326–2341. [Google Scholar] [CrossRef]
- Kim, M.; Yu, S.; Lee, J.; Park, Y.; Park, Y. Design of Secure Protocol for Cloud-Assisted Electronic Health Record System Using Blockchain. Sensors 2020, 20, 2913. [Google Scholar] [CrossRef] [PubMed]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and secure sharing of personal health records in cloud computing using attribute-based encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef] [Green Version]
- Liu, J.; Huang, X.; Liu, J.K. Secure sharing of personal health records in cloud computing: Ciphertext-policy attribute-based signcryption. Future Gener. Comp. Syst. 2015, 52, 67–76. [Google Scholar] [CrossRef]
- Rao, Y. A secure and efficient ciphertext-policy attribute-based signcryption for personal health records sharing in cloud computing. Future Gener. Comp. Syst. 2017, 67, 133–151. [Google Scholar] [CrossRef]
- Zhang, W.; Lin, Y.; Xiao, S.; Wu, J.; Zhou, S. Privacy preserving ranked multi-keyword search for multiple data owners in cloud computing. IEEE Trans. Comput. 2016, 65, 1566–1577. [Google Scholar] [CrossRef]
- Peng, T.; Lin, Y.; Yao, X.; Zhang, W. An efficient ranked multi-keyword search for multiple data owners over encrypted cloud data. IEEE Access 2018, 6, 21924–21933. [Google Scholar] [CrossRef]
- Sun, J.; Hu, S.; Nie, X.; Walker, J. Efficient ranked multi-keyword retrieval with privacy protection for multiple data owners in cloud computing. IEEE Syst. J. 2020, 14, 1728–1739. [Google Scholar] [CrossRef]
- Liu, Z.; Liu, Y.; Fan, Y. Searchable attribute-based signcryption scheme for electronic personal health record. IEEE Access 2018, 6, 76381–76394. [Google Scholar] [CrossRef]
- Xu, C.; Wang, N.; Zhu, L.; Sharif, K.; Zhang, C. Achieving searchable and privacy-preserving data sharing for cloud-assisted e-healthcare system. IEEE Internet Things J. 2019, 6, 8345–8356. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, D.; Zhang, Y. Blockchain-based personal health records sharing scheme with data integrity verifiable. IEEE Access 2019, 7, 102887–102901. [Google Scholar] [CrossRef]
- Zhang, J.; Yang, Y.; Liu, X.; Ma, J. An efficient blockchain-based hierarchical data sharing for Healthcare Internet of Things. IEEE Trans. Ind. Inform. 2022, 18, 7139–7150. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, T.; Wu, Q.; Mu, Y.; Rezaeibagha, F. Secure decentralized attribute-based sharing of personal health records with blockchain. IEEE Internet Things J. 2022, 9, 12482–12496. [Google Scholar] [CrossRef]
- Madine, M.M.; Salah, K.; Jayaraman, R.; Yaqoob, I.; Al-Hammadi, Y.; Ellahham, S.; Calyam, P. Fully decentralized multi-party consent management for secure sharing of patient health records. IEEE Access 2020, 8, 225777–225791. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, A.; Zhang, P.; Qu, Y.; Yu, S. Security-aware and privacy-preserving personal health record sharing using consortium blockchain. IEEE Internet Things J. 2022, 9, 12014–12028. [Google Scholar] [CrossRef]
- Wu, G.; Wang, S.; Ning, Z.; Li, J. Blockchain-enabled privacy-preserving access control for data publishing and sharing in the internet of medical things. IEEE Internet Things J. 2022, 9, 8091–8104. [Google Scholar] [CrossRef]
- Hussien, H.M.; Yasin, S.M.; Udzir, N.I.; Ninggal, M.I.H. Blockchain-based access control scheme for secure shared personal health records over decentralised storage. Sensors 2021, 21, 2462. [Google Scholar] [CrossRef] [PubMed]
- Niu, J.; Li, X.; Gao, J.; Han, Y. Blockchain-based anti-key-leakage key aggregation searchable encryption for IoT. IEEE Internet Things J. 2020, 7, 1502–1518. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wazid, M.; Das, A.K.; Choo, K.-K.R.; Park, Y. SCS-WoT: Secure communication scheme for web of things deployment. IEEE Internet Things J. 2022, 9, 10411–10423. [Google Scholar] [CrossRef]
- Oh, J.; Lee, J.; Kim, M.; Park, Y.; Park, K.; Noh, S. A secure data sharing based on key aggregate searchable encryption in fog-enabled IoT environment. IEEE Trans. Netw. Sci. Eng. 2022; Early access. [Google Scholar]
- Beimel, A. Secure Schemes for Secret Sharing and Key Distribution; Technion-Israel Institute of Technology, Faculty of Computer Science: Haifa, Israel, 1996. [Google Scholar]
- Hunhevicz, J.J.; Hall, D.M. Do you need a blockchain in construction? Use case categories and decision framework for DLT design options. Adv. Eng. Inform. 2020, 45, 101094. [Google Scholar] [CrossRef] [Green Version]
- Tan, W.K.A.; Sundarakani, B. Assessing blockchain technology application for freight booking business: A case study from technology acceptance model perspective. J. Glob. Oper. Strateg. Sourc. 2021, 14, 202–223. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2. Available online: https://firstmonday.org/ojs/index.php/fm/article/view/548 (accessed on 13 April 2022). [CrossRef]
- IPFS is the Distributed Web. Available online: https://ipfs.io/ (accessed on 13 April 2022).
- Viganò, L. Automated security protocol analysis with the AVISPA tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef] [Green Version]
- Lee, J.; Yu, S.; Park, K.; Park, Y.; Park, Y. Secure three-factor authentication protocol for multi-gateway IoT environments. Sensors 2019, 19, 2358. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.; Guo, Z.; Ma, J.; Song, Y. A secure authentication scheme for wireless sensor networks based on DAC and Intel SGX. IEEE Internet Things J. 2022, 9, 3533–3547. [Google Scholar] [CrossRef]
- Kwon, D.; Park, Y.; Park, Y. Provably secure three-factor-based mutual authentication scheme with PUF for wireless medical sensor networks. Sensors 2021, 21, 6039. [Google Scholar] [CrossRef] [PubMed]
- Shashidhara, R.; Nayak, S.K.; Das, A.K.; Park, Y. On the design of lightweight and secure mutual authentication system for global roaming in resource-limited mobility networks. IEEE Access 2021, 9, 12879–12895. [Google Scholar] [CrossRef]
- Chen, CM.; Deng, X.; Gan, W.; Chen, J.; Islam, S.K. A secure blockchain-based group key agreement protocol for IoT. J. Supercomput. 2021, 77, 9046–9068. [Google Scholar] [CrossRef]
- Lee, J.; Kim, G.; Das, A.K.; Park, Y. Secure and efficient honey list-based authentication protocol for vehicular ad hoc networks. IEEE Trans. Netw. Sci. Eng. 2021, 8, 2412–2425. [Google Scholar] [CrossRef]
- MIRACL Cryptographic SDK: Multiprecision Integer and Rational Arithmetic Cryptographic Library. Available online: https://github.com/miracl/MIRACL (accessed on 13 April 2022).




| Notation | Description |
|---|---|
| , | Data owner/data user |
| Data owner’s private key and public key | |
| Data user’s private key and public key | |
| n | Maximum number of PHRs |
| m | Maximum number of keywords |
| W | Keyword set for document |
| Search keyword set | |
| I | Index of search keyword set |
| i-th PHR | |
| w | Keyword |
| Random number | |
| Timestamp | |
| Maximum transmission delay | |
| Aggregate key | |
| Trapdoor | |
| e | Bilinear map |
| h | One-way hash function |
| Concatenation operator | |
| ⊕ | Bitwise exclusive-or operator |
| Notation | Description |
|---|---|
| Secret key | |
| Kbelieves statement Y | |
| Statement Y is fresh | |
| Kreceives statement Y | |
| K once said Y | |
| Kcontrols statement Y | |
| Statement Y is combined with secret statement S | |
| Statement Y is masked by | |
| K and Q share to communicate with each other |
| Security Features | Liu et al. [25] | Zhang et al. [28] | Wang et al. [31] | Ours |
|---|---|---|---|---|
| ∘ | ∘ | ∘ | ∘ | |
| ∘ | ∘ | ∘ | ∘ | |
| ∘ | ∘ | ∘ | ∘ | |
| ∘ | ∘ | ∘ | ∘ | |
| × | × | × | ∘ | |
| − | ∘ | ∘ | ∘ | |
| × | × | × | ∘ | |
| ∘ | ∘ | ∘ | ∘ | |
| ∘ | ∘ | ∘ | ∘ | |
| ∘ | ∘ | ∘ | ∘ | |
| × | × | × | ∘ | |
| × | × | × | ∘ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Oh, J.; Lee, J.; Kim, M.; Park, Y.; Park, K.; Noh, S. A Secure Personal Health Record Sharing System with Key Aggregate Dynamic Searchable Encryption. Electronics 2022, 11, 3199. https://doi.org/10.3390/electronics11193199
Oh J, Lee J, Kim M, Park Y, Park K, Noh S. A Secure Personal Health Record Sharing System with Key Aggregate Dynamic Searchable Encryption. Electronics. 2022; 11(19):3199. https://doi.org/10.3390/electronics11193199
Chicago/Turabian StyleOh, Jihyeon, JoonYoung Lee, MyeongHyun Kim, Youngho Park, KiSung Park, and SungKee Noh. 2022. "A Secure Personal Health Record Sharing System with Key Aggregate Dynamic Searchable Encryption" Electronics 11, no. 19: 3199. https://doi.org/10.3390/electronics11193199
APA StyleOh, J., Lee, J., Kim, M., Park, Y., Park, K., & Noh, S. (2022). A Secure Personal Health Record Sharing System with Key Aggregate Dynamic Searchable Encryption. Electronics, 11(19), 3199. https://doi.org/10.3390/electronics11193199













