Secure Mimo Communication System with Frequency Hopping Aided OFDM-DCSK Modulation
Abstract
:1. Introduction
- 1.
- We propose to use FH-OFDM-DCSK to improve the security of the MIMO communication system. The initial values of chaotic sequences and the method of generating FH module are shared only between legitimate users. Thus, eavesdroppers or malicious users can not recover the received unknown information. Thus, the scheme proposed in this paper can improve the security of the MIMO communication system.
- 2.
- We analyze the theoretical BER and secrecy capacity for the proposed scheme. Then, simulation results are provided to verify the effectiveness of the scheme proposed in this paper and that the proposed MIMO communication system can achieve higher secrecy capacity.
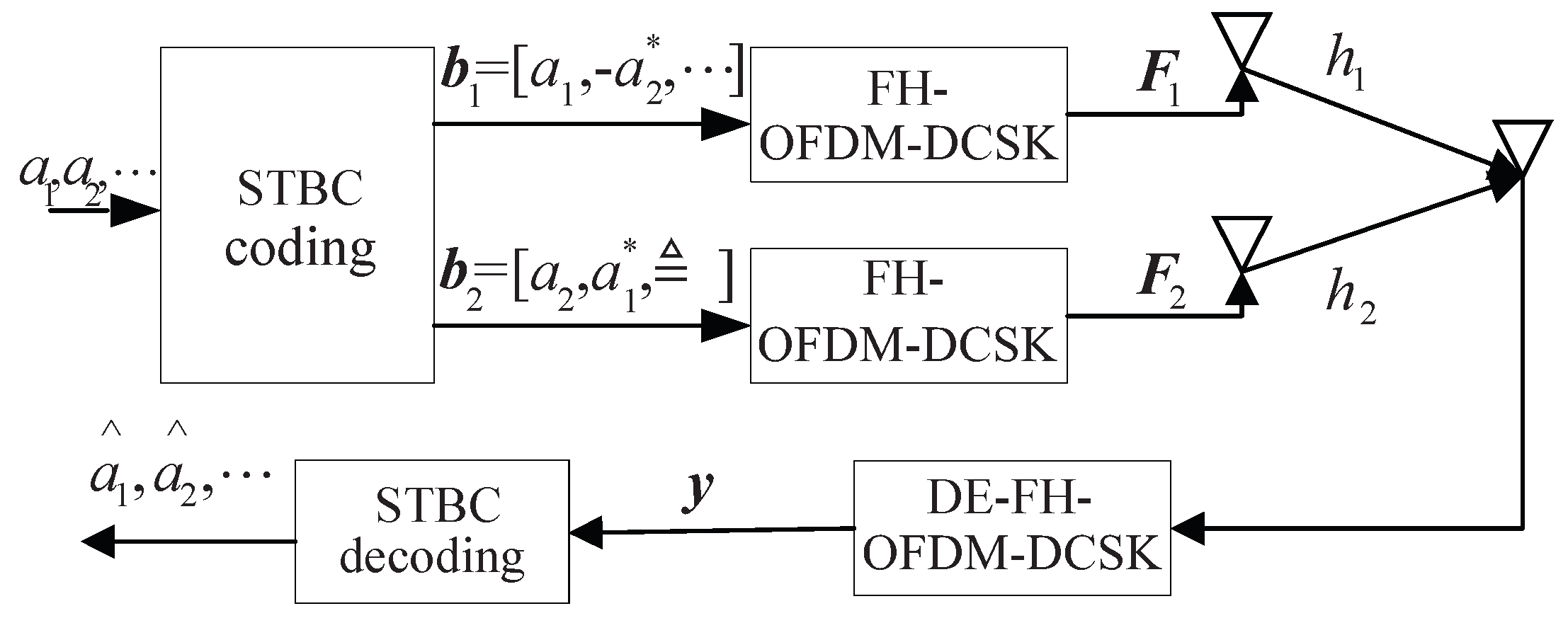
2. MIMO-FH-OFDM-DCSK System
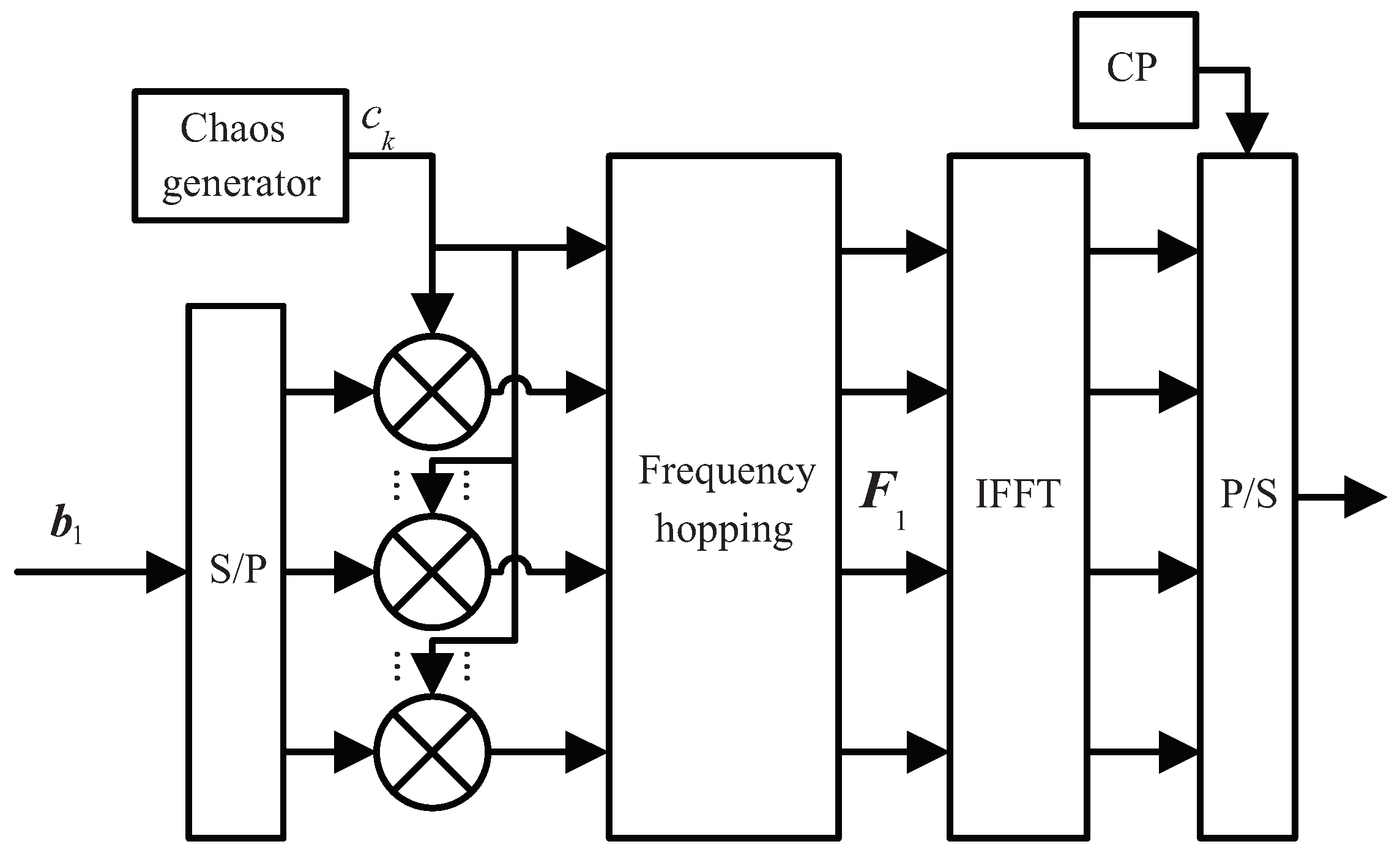
2.1. Transmitter
2.2. Receiver
3. Performance Analysis
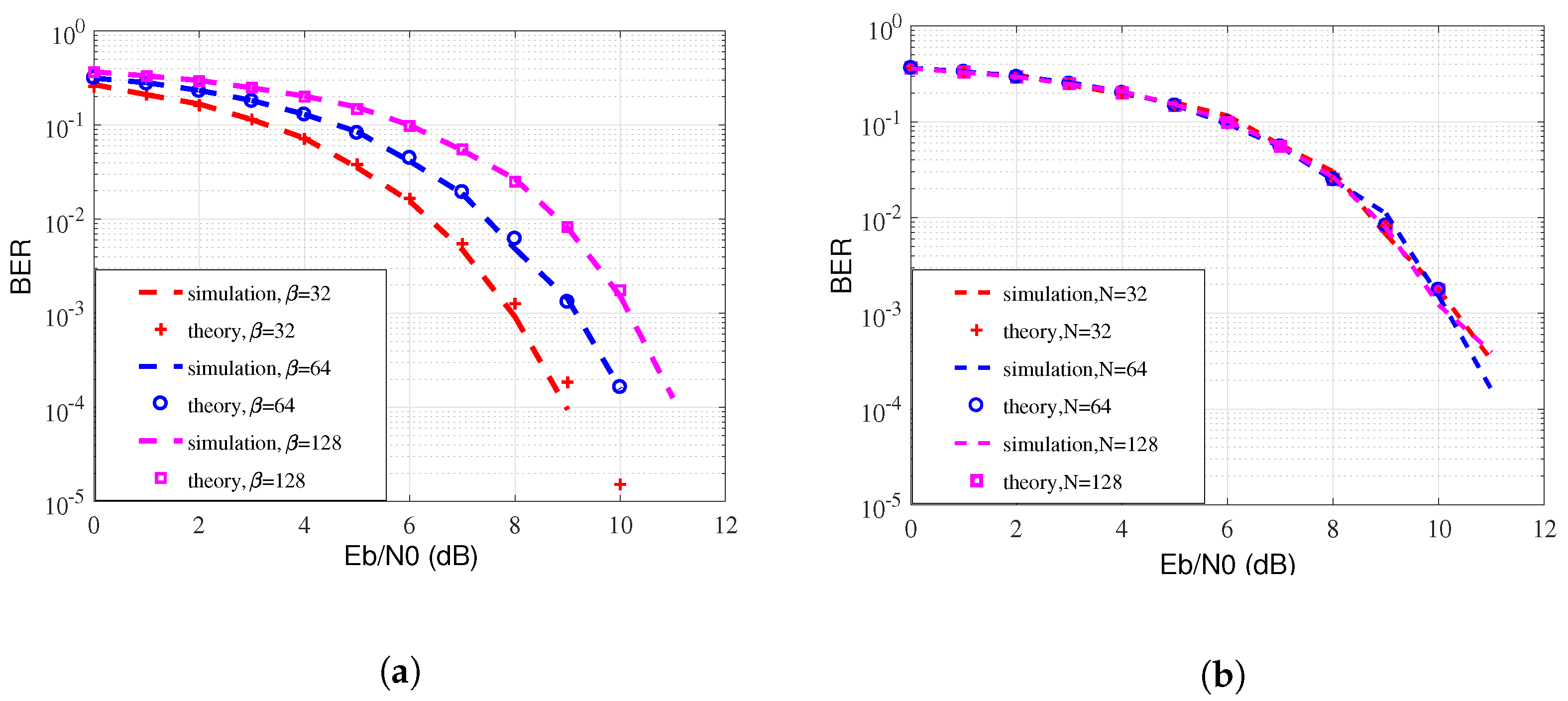
3.1. Ber Performance
3.2. Secrecy Capacity
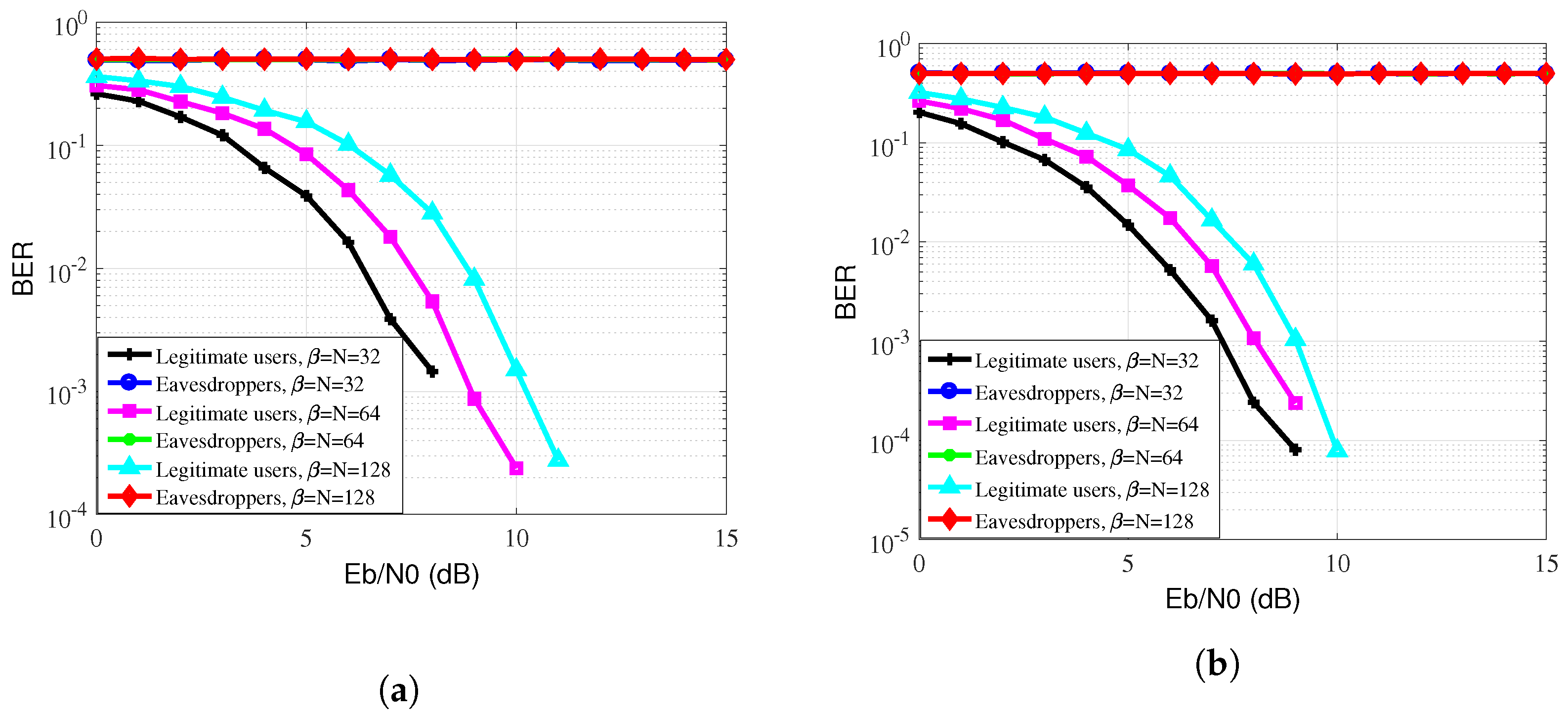
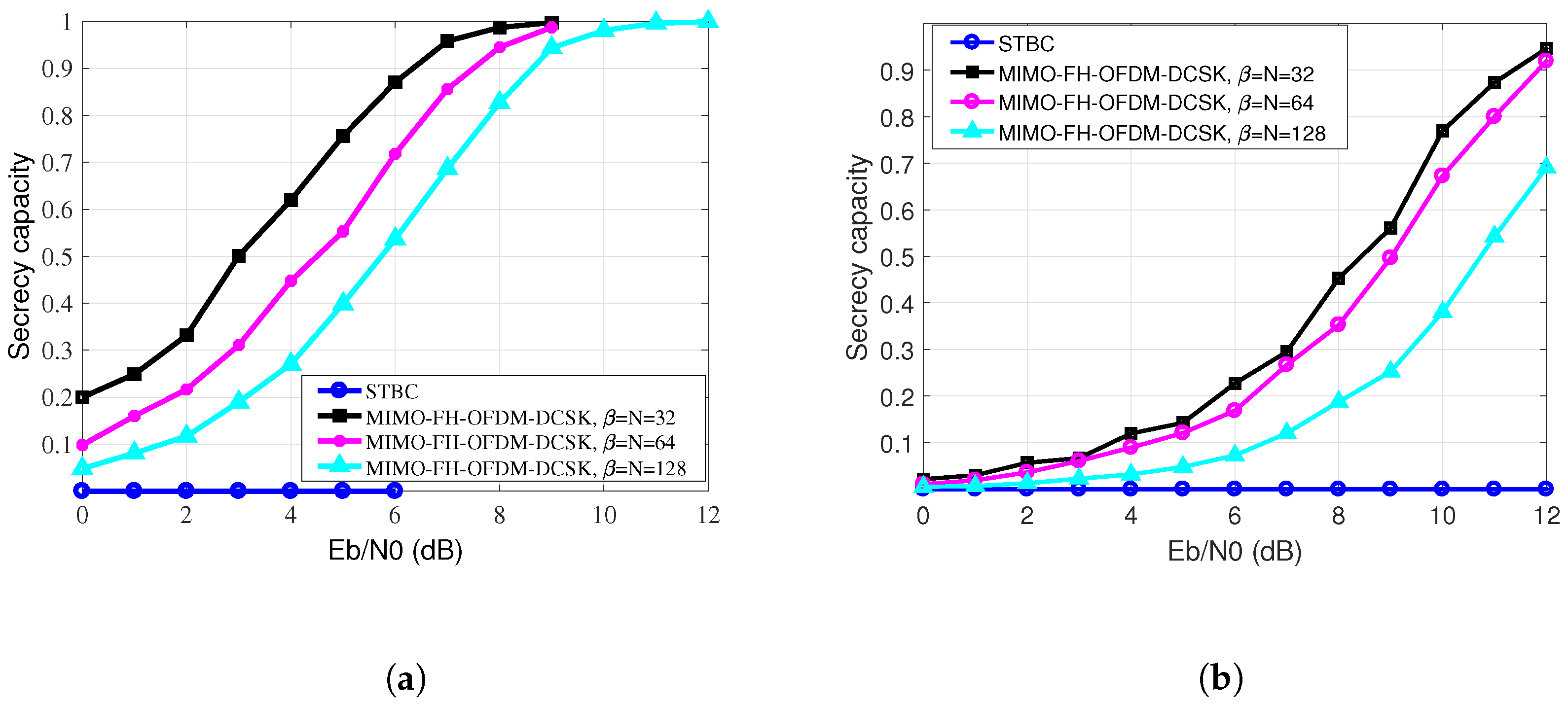
4. Simulation Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Lau, C. Performance of MIMO Systems Using Space Time Block Codes (STBC). Open J. Appl. Sci. 2021, 11, 273–286. [Google Scholar] [CrossRef]
- Shimaponda-Nawa, M.; Achari, S.; Jayakody, D.N.K.; Cheng, L. Visible Light Communication System Employing Space Time Coded Relay Nodes and Imaging Receivers. SAIEE Afr. Res. J. 2020, 111, 56–64. [Google Scholar] [CrossRef]
- Naser, S.; Bariah, L.; Muhaidat, S.; Al-Qutayri, M.; Uysal, M.; Sofotasios, P.C. Space-Time Block Coded Spatial Modulation for Indoor Visible Light Communications. IEEE Photonics J. 2022, 14, 1–11. [Google Scholar] [CrossRef]
- Guo, J.N.; Zhang, J.; Zhang, Y.Y.; Xin, G.; Li, L. Constant Weight Space-Time Codes for Dimmable MIMO-VLC Systems. IEEE Photonics J. 2020, 12, 1–15. [Google Scholar] [CrossRef]
- Ren, H.; Xu, W.; Wang, L. Multiple-Mode Orthogonal Time Frequency Space with Index Modulation. Electronics 2022, 11, 2600. [Google Scholar] [CrossRef]
- Deka, K.; Thomas, A.; Sharma, S. OTFS-SCMA: A Code-Domain NOMA Approach for Orthogonal Time Frequency Space Modulation. IEEE Trans. Commun. 2021, 69, 5043–5058. [Google Scholar] [CrossRef]
- Surabhi, G.D.; Chockalingam, A. Low-complexity Linear Equalization for 2×2 MIMO-OTFS Signals. In Proceedings of the 2020 IEEE 21st International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Atlanta, GA, USA, 26–29 May 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Hamamreh, J.M.; Furqan, H.M.; Arslan, H. Classifications and Applications of Physical Layer Security Techniques for Confidentiality: A Comprehensive Survey. IEEE Commun. Surv. Tutorials 2019, 21, 1773–1828. [Google Scholar] [CrossRef]
- Probst, A.; Marko, M.; Kmetko, L.; Gershenson, C. Chaos-Based Digital Communication Systems. In Digital Communications with Chaos; Elsevier Science: Amsterdam, The Netherlands, 2003; pp. 11–31. [Google Scholar]
- Ma, W.; Du, J.; Xue, H. Design of reverse-DCSK for chaos based communication system. In Proceedings of the 2017 3rd IEEE International Conference on Computer and Communications (ICCC), Chengdu, China, 13–16 December 2017; pp. 743–747. [Google Scholar] [CrossRef]
- Herceg, M.; Kaddoum, G.; Vranjes, D.; Soujeri, E. Permutation Index DCSK Modulation Technique for Secure Multi-User High-Data-Rate Communication Systems. IEEE Trans. Veh. Technol. 2017, 67, 2997–3011. [Google Scholar] [CrossRef]
- Cai, H.; Hua, Z.; Huang, H. A Novel Differential-Chaos-Shift-Keying Secure Communication Scheme. In Proceedings of the 2018 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Miyazaki, Japan, 7–10 October 2018; pp. 1794–1798. [Google Scholar] [CrossRef]
- Yang, H.; Jiang, G.; Xia, L.; Tu, X. Reference-shifted DCSK modulation scheme for secure communication. In Proceedings of the 2017 International Conference on Computing, Networking and Communications (ICNC), Silicon Valley, CA, USA, 26–29 January 2017; pp. 1073–1076. [Google Scholar] [CrossRef]
- Liu, Z.; Zhang, L.; Wu, Z. Reliable and Secure Pre-Coding OFDM-DCSK Design for Practical Cognitive Radio Systems with the Carrier Frequency Offset. IEEE Trans. Cogn. Commun. Netw. 2020, 6, 189–200. [Google Scholar] [CrossRef]
- Zhang, H.; Zhang, L.; Jiang, Y.; Wu, Z. Reliable and Secure Deep Learning-Based OFDM-DCSK Transceiver Design without Delivery of Reference Chaotic Sequences. IEEE Trans. Veh. Technol. 2022, 71, 8059–8074. [Google Scholar] [CrossRef]
- Zhang, L.; Zheng, J.; Chen, B.; Wu, Z. Reliable Low-Rank Approximation of Matrices Detection Aided Multicarrier DCSK Receiver Design. IEEE Syst. J. 2021, 15, 5277–5288. [Google Scholar] [CrossRef]
- Chen, Z.; Zhang, L.; Wang, W.; Wu, Z. A Pre-Coded Multi-Carrier M-Ary Chaotic Vector Cyclic Shift Keying Transceiver for Reliable Communications. IEEE Trans. Wirel. Commun. 2022, 21, 1007–1021. [Google Scholar] [CrossRef]
- Liu, Z.; Zhang, L.; Wu, Z.; Bian, J. A Secure and Robust Frequency and Time Diversity Aided OFDM-DCSK Modulation System Not Requiring Channel State Information. IEEE Trans. Commun. 2020, 68, 1684–1697. [Google Scholar] [CrossRef]
- Holla, N.; Sudha, K.L. Performance Analysis of MIMO System with the Combination of Different Types of STBC and DCSK. In Proceedings of the 2020 2nd PhD Colloquium on Ethically Driven Innovation and Technology for Society (PhD EDITS), Bangalore, India, 8 November 2020; pp. 1–2. [Google Scholar] [CrossRef]
- Ma, H.; Fang, Y.; Tao, Y.; Chen, P.; Li, Y. A Novel Differential Chaos Shift Keying Scheme with Transmit Diversity. IEEE Commun. Lett. 2022, 26, 1668–1672. [Google Scholar] [CrossRef]
- Fang, Y.; Han, G.; Chen, P.; Lau, F.C.M.; Chen, G.; Wang, L. A Survey on DCSK-Based Communication Systems and Their Application to UWB Scenarios. IEEE Commun. Surv. Tutor. 2016, 18, 1804–1837. [Google Scholar] [CrossRef]
- Kaddoum, G.; Mai, V.; Gagnon, F. Performance analysis of differential chaotic shift keying communications in MIMO systems. In Proceedings of the IEEE International Symposium on Circuits & Systems, Rio de Janeiro, Brazil, 15–18 May 2011. [Google Scholar]
- Deng, H.; Li, T.; Wang, Q.; Li, H. A Novel Chaotic Slow FH System Based on Differential Space-Time Modulation. In Proceedings of the 2008 International Conference on Embedded Software and Systems Symposia, Chengdu, China, 29–31 July 2008; pp. 380–385. [Google Scholar] [CrossRef]
- Alamouti, S. A simple transmit diversity technique for wireless communications. IEEE J. Sel. Areas Commun. 1998, 16, 1451–1458. [Google Scholar] [CrossRef]
- Dawa, M.; Kaddoum, G.; Sattar, Z. A Generalized Lower Bound on the Bit Error Rate of DCSK Systems over Multi-Path Rayleigh Fading Channels. IEEE Trans. Circuits Syst. II Express Briefs 2018, 65, 321–325. [Google Scholar] [CrossRef]
- Li, H.; Wang, X.; Zou, Y. Dynamic Subcarrier Coordinate Interleaving for Eavesdropping Prevention in OFDM Systems. IEEE Commun. Lett. 2014, 18, 1059–1062. [Google Scholar] [CrossRef]



| Secrecy Capacity | ||||
|---|---|---|---|---|
| MIMO-FH-OFDM-DCSK | Alimouti | |||
| Eb/N0 (dB) | ||||
| 2 | 0.332 | 0.217 | 0.117 | 0.000 |
| 3 | 0.501 | 0.311 | 0.190 | 0.000 |
| 4 | 0.620 | 0.448 | 0.271 | 0.000 |
| 5 | 0.756 | 0.553 | 0.399 | 0.000 |
| 6 | 0.870 | 0.718 | 0.537 | 0.000 |
| Secrecy Capacity | ||||
|---|---|---|---|---|
| MIMO-FH-OFDM-DCSK | Alimouti | |||
| Eb/N0 (dB) | ||||
| 8 | 0.453 | 0.353 | 0.188 | 0.000 |
| 9 | 0.561 | 0.496 | 0.252 | 0.000 |
| 10 | 0.769 | 0.673 | 0.380 | 0.000 |
| 11 | 0.873 | 0.800 | 0.543 | 0.000 |
| 12 | 0.946 | 0.919 | 0.690 | 0.000 |
| Secrecy Capacity | ||||
|---|---|---|---|---|
| MIMO-FH-OFDM-DCSK | STBC-DCSK | |||
| Eb/N0 (dB) | ||||
| 4 | 0.627 | 0.423 | 0.287 | 0.000 |
| 5 | 0.777 | 0.569 | 0.366 | 0.000 |
| 6 | 0.910 | 0.722 | 0.553 | 0.000 |
| 7 | 0.956 | 0.871 | 0.685 | 0.000 |
| 8 | 0.987 | 0.952 | 0.846 | 0.000 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Qiu, W.; Yang, Y.; Feng, Y.; Zhang, L.; Wu, Z. Secure Mimo Communication System with Frequency Hopping Aided OFDM-DCSK Modulation. Electronics 2022, 11, 3029. https://doi.org/10.3390/electronics11193029
Qiu W, Yang Y, Feng Y, Zhang L, Wu Z. Secure Mimo Communication System with Frequency Hopping Aided OFDM-DCSK Modulation. Electronics. 2022; 11(19):3029. https://doi.org/10.3390/electronics11193029
Chicago/Turabian StyleQiu, Wenduo, Yimu Yang, Yan Feng, Lin Zhang, and Zhiqiang Wu. 2022. "Secure Mimo Communication System with Frequency Hopping Aided OFDM-DCSK Modulation" Electronics 11, no. 19: 3029. https://doi.org/10.3390/electronics11193029
APA StyleQiu, W., Yang, Y., Feng, Y., Zhang, L., & Wu, Z. (2022). Secure Mimo Communication System with Frequency Hopping Aided OFDM-DCSK Modulation. Electronics, 11(19), 3029. https://doi.org/10.3390/electronics11193029









