1. Introduction
Creating adversarial profiles and activities requires good intelligence reports for mitigating and defending security strategies. Indicators of compromise (IoCs) [
1] are when data that suggests a cyber-attack may have compromised a computer are referred to as IOCs, which should exist in the report but start to depreciate from the time of the report or the compromise. As per IBM, Threat hunting is a proactive approach to identify non-remediated and unknown threats inside an organization. Crowdstrike defines threat hunting as the process of proactive search for cyber threats hiding undetected inside enterprise networks. Consistent adversarial behavior helps defend against attacks better than using standard operating procedures (SOPs) [
2] and defense skillsets. Threat hunting has gained tremendous traction within the cyber security community [
3]. Organizations have realized that while traditional security controls and analysis have served as a cornerstone for an organization’s cyber security compliance, they are no longer sufficient to mitigate operational risks. This is especially true given the ever-increasing attack surfaces of these organizations and the increase in the number and capability of cyber adversaries. This reality has necessitated a paradigm shift from reactive to proactive security, and as a result, organizations increasingly focus on threat hunting to fill this realized gap. However, despite this increase in demand for processes, people, and technologies to enable hunts across environments, many organizations continue to struggle with the establishment of sustainable threat hunting capabilities which can operate in a rigorous and repeatable manner. This struggle is often fed by a litany of business and technical challenges, some of which are unique to threat hunting but many of which are common to security practices.
At its simplest, threat hunting is an iterative and proactive process whereby threat hunters seek out anomalous activity, artefacts, and behaviors within an environment to identify previously unknown and undetected threats. Threat hunting or hyber-threat hunt proactively identifies ongoing or previously unknown non-remediated attacks and threats inside the organization’s network. Initially, hunts began with a hypothesis based on triggers which serve as springboards for deep investigations. Threat intel reports further provide specific IoCs for threat hunting models—structured [
4] and unstructured [
5] threat hunting. Rather of depending solely on automated systems like SIEMs, threat hunting involves manual or machine-assisted techniques. Although alerting is critical, it cannot be the sole priority of a detection tool. Threat hunting increases automated detection by innovative manual and machine learning techniques that aid in identifying malicious and anomalous behaviors. These are translated into valuable information for the detection and investigation of attacks. Different threat hunting models are adopted as:
Intel-driven [
6] reports and feeds ingested on emerging threat vectors, malware, or vulnerabilities. These are often tailored to validate compromise type of efforts based on targeted knowledge similar in the environment. This helps identify gaps.
Situational awareness [
7] is useful if the cyber-defence analyst has a deep understanding knowledge of internal risks and critical assets and has spent a long time in the organization. This can be gained if the teams are in the same environment long enough. These are often tailored to scenarios hypothesized around controls and processes that adversaries would exploit and utilize if they entered the environment.
Analytics-driven [
8] visualizes telemetry in the environment, baselining the environment knowing what is normal and what an anomaly is. These are tailored to abnormal human behavior changes and rabbit home tracing.
Hybrid [
9] is the most mature level, and this is a blend of all the above.
Structured hunting is a crucial topic to understand when businesses investigate the usage of threat hunting tactics (sometimes referred to as hypothesis-based threat hunting). Most businesses underutilize this sort of hunting. Still, mature organizations may reap some of the most significant benefits from their efforts by including structured threat hunting into their threat hunting efforts. Unstructured threat hunts are usually haphazard and ad hoc activities that rely heavily on data from internal log sources. Hunters sift through logs on the fly, using basic data manipulation techniques such as pivot tables or other ways by analysts, and they frequently rely on investigative tactics such as the principle of least seen to find abnormalities in the data. Structured threat hunting is in contrast to the more common practice of unstructured threat hunting (also known as ad hoc or data-driven hunting).
Table 1 below describes the differences between the types of threat hunting.
From a business perspective, one of the most critical challenges organizations are faced with is skills shortages for threat hunting. This means that many organizations are unable to locate resources to stand up a threat hunting capability, and, for organizations that can conduct threat hunting operations, their programs are largely reliant on only a few highly skilled and technical resources. This often means that any fluctuation in manning can have direct operational impacts. Skill shortage, however, is not the only business-related challenge to threat hunting. Another challenge organizations grapple with is the inherently uncertain nature of threat hunting. This uncertainty can often make it a challenge to appropriately measure the value that threat hunting brings to security operations, which in turn can make it difficult to realize the return-on-investment (ROI) for organizations. With ongoing skills shortages for most organizations and the challenge in measuring ROI for organizations, a common outcome of this is that threat hunting teams are often seconded to or forgone altogether in favor of ongoing traditional security operations. From a technical perspective, the number of impediments organizations face to establishing a threat hunting capability are considerable. One of the most common technical challenges is a so-called data deficit. Organizations, dependent upon their current security operations maturity, often find that the depth, breadth, quality, and quantity of their data is insufficient to support threat hunting operations. This challenge can be compounded as security teams come to their existing security controls may not provide sufficient coverage to support more advanced threat hunting. The ongoing skill shortage also manifests itself as a technical issue for organizations, especially true as the number of resources with the depth of experience to develop operational capabilities and conduct threat hunting operations continues to remain very low. The result is often a lack of direction and focuses for threat hunting operations which typically results in a lack of defined processes, as well as ineffective and unreliable hunts. Despite these significant challenges that organizations continue to encounter, there are both demands and a need for mature, reliable, repeatable, and robust hunting capabilities in many organizations.
The highlights of this threat hunting research are as follows:
Design and implement an online threat hunting platform;
Perform threat hunting based on behavioral patterns instead of using IOCs;
Propose a new threat hunting process using the threat intelligence report;
Capture threat information and artefacts from logs.
This research is organized into different sections.
Section 2 reviews the previous research works and implementations from various journals.
Section 3 presents the research methodology with the threat intel report to research as per the proposed behavior-based threat hunting framework.
Section 4 presents the implementation and platforms used in the form of Elastic instance and network traffic logs, and alsopresents the bad behavior-based filtering and searches for malicious artifacts as per the intel report.
Section 5 presents the results obtained as the artifacts and information regarding the attack, and finally, the conclusion with the future scope in
Section 6.
2. Literature Survey
Recent years have seen an increase in cyberattacks that affect small, medium, and large enterprises, prompting the creation of solutions to help with risk mitigation. Organizations today receive a lot of threat data from many sources due to the rise in cyberattacks, which has to be ingested, processed, and assessed in order to give useful mitigation insights. Based on research keywords for behavior-based threat hunting, such as IoCs, threat hunting, threat intelligence, structured threat hunting, unstructured threat hunting. the authors categorized and classified the papers as the first level of review. The authors then organized to search 243 research papers and after four-stage process 22 relevant papers are shortlisted from literature as presented in
Table 2.
Ajmal et al. [
10] proposed a unique hybrid approach for identifying offensive security strategies, techniques, and processes, especially threat hunting using adversary emulation. The suggested method is based on a unique method for introducing adversary emulation (mapping each step) into the threat hunting process. The experimental results reveal that the suggested technique leverages adversary simulation to hunt advanced-level threats and has opposing impacts. Furthermore, the suggested approach’s threat detection capability requires few resources. The suggested method may be utilized to create an offensive security-aware environment for businesses for discovering sophisticated threat and attack methods and evaluate their capacity for detecting attacks.
The ability of system security for detecting the growing threats is mismatched. Anti-malware, anti-virus and endpoint detection are reactive security systems that are ineffective against attacks that are extremely slow and stealthy. The need of the hour is for a proactive strategy, such as threat hunting. Cyber Deception and Cyber-Kill Chain with threat hunting have contradictory impacts on identifying and mitigating threats, according to Ajmal et al. [
11]. The authors adopted the approach of decoy farms, in which attacks are engaged. Unknown risks were the subject of a revolutionary threat detection and prevention strategy. The research introduced a new simulated network to examine the effectiveness of the strategy by simulating multiple industrial systems running Linux and Windows-based assaults. The authors found that the suggested technique discovered and blocked attackers before utilizing the present reactive approach and security mechanism for heterogeneous devices, resulting in increased protection. The suggested threat hunting technique has greatly increased the threat detection capabilities, according to the results and testing.
Defenders battling APTs must identify an adversary’s propagation region as rapidly as feasible, employing incident response operations and threat hunting to locate attackers within a compromised network. From both the attacker and defender viewpoints, Berady et al. [
12] established a formal attack model. An infinitely powerful actor can compare the differences in knowledge and perception between defenders and attackers using this model, enabling defenders for improving Threat hunting quality by identification of false-positives and adapt log policy to be investigation-oriented. The authors described an assault campaign that imitated the actual threat known as APT29 in an MITRE-designed model. The quality of the defensive architecture is next thoroughly examined.
Jadidi et al. [
13] highlighted missing solutions for unified hunting for integrated IT and OT networks, proposing a threat hunting framework that focused on the detection of cyber threats against industrial devices in the initial stages of the incident lifecycle. Threat hunting, triggers, and cyber threat intelligence as the three steps of the proposed framework. The threat hunting trigger stage detects occurrences or external resources that may cause the hunting stage to be triggered. To establish a hunting hypothesis and predict the adversary’s future behavior, the hunting stage employs a mix of the MITRE ATT&CK Matrix and a diamond model of intrusion analysis. The validity of this hypothesis was verified by analyzing diamond threat action models. Finally, the cyber threat intelligence stage is in charge of producing IoCs for future threat hunting. The SWaT dataset, Black Energy 3 malware, and PLC-Blaster malware were employed in this research to examine the effectiveness of the proposed framework.
Jahromi et al. [
14] provided a deep recurrent neural network approach as a stacked long short-term memory, using global and short input dependencies as a normalization method to avoid random network initialization. The authors were able to eliminate random initialization and increase the accuracy and resilience of malware threat hunting by using pre-training. In comparison to the stacked approach, the proposed method reduced the length of malware OpCode or bytecode sequences, and accelerated convergence. As a result, the concluding method’s complexity was lowered. In comparison to a typical model with identical detection time, this resulted in increased accuracy. Smart IoT devices integrated into human life have become routes for hackers’ malicious activities as the Internet of Things (IoT) age has expanded. IoT devices use a variety of Unix-based architectures that conform to the standard binary file specification of the executable and linked format. Raju et al. [
15] focused on presenting an overview of the recent advances in merged IoT malware detection and classification methods. The authors addressed the feature representations, feature extraction strategies, and machine learning models using modern taxonomy. This study emphasised on the practical issues of tracking down cross-architectural IoT malware threats and discussed several possibilities for future research. Industrial IoT devices are now becoming increasingly targeted, owing to their wide use in a variety of applications, including home and corporate environments. Using the grey wolves’ optimization approach, Haddadpajouh et al. [
16] suggested a multi-kernel support vector machine for IoT cloud-edge gateway virus hunting. At the IoT cloud-edge gateway, this meta-heuristic technique is utilized to determine the best attributes for identifying malicious and benign applications. The model is trained using the IoT malware Opcode and Bytecode training data set, which included both benign and malicious samples, and assessed using the k-fold cross-validation approach. In terms of accuracy, the proposed multi-kernel SVM strategy beats DNNs and fuzzy-based IoT malware hunting strategies while also reducing the computing cost and training time.
Crypto ransomware has radically altered the threat-landscape. By encrypting critical data on victims’ systems, crypto-ransomware disables data custodian access and demands a ransom payment to restore custodian access by decrypting data. The speed and accuracy with which system logs can be mined to hunt for anomalies and eliminate ransomware depend a lot on how fast and accurately it can be detected. Homayoun et al. [
17] set up an environment to capture activity logs for the ransomware strains Locky, Cerber, and TeslaCrypt. The authors utilized sequential pattern mining to uncover MFPs of behaviors. The suggested approach was 96.5 percent accurate in determining the family of a given ransomware sample and 99 percent accurate in detecting ransomware cases from goodware samples. The results showed that applying pattern mining approaches to the detection of favorable traits for ransomware hunting is both beneficial and practicable. This research revealed various ransomware families with distinct features and common patterns that could be evaluated to identify ransomware sample families and create knowledge about threat actors and the threat profile of a specific target.
Unmanned underwater vehicles (UUVs) have become vital in today’s maritime environment. Underwater reconnaissance and surveillance, underwater mine hunting, and anti-submarine warfare are only a few of the activities that represent a major and hazardous threat to humans. UUV has emerged as the leading technology for completing such missions. Yao et al. [
18] suggested a technique for evaluating the UUV in an underwater hazard situation based on dynamic Bayesian network modeling. The researchers classified the hazards posed by UUVs into three categories: environmental, platform, and mission factors. The authors performed factor extraction and set up the prior probability based on the features for each of these categories. The incorporation of state transition probability and the creation of a model for assessing the dynamic Bayesian threat scenario were required to set up the static Bayesian network. The dynamic Bayesian simulation was shown to be superior when the results of the static and dynamic Bayesian simulations were compared. Furthermore, by studying the sensitivity, we were able to identify the most serious present danger and, as a result, develop the best UUV countermeasures. The findings revealed that the dynamic Bayesian technique has a lot of practical usefulness in threat assessment. The integration of industry 4.0 and intelligent IoT technologies has enhanced the vulnerability of industrial cyber-physical systems (ICPS) to a diverse variety of network attacks. Assessing cyber threats with intelligent threat detection is a difficult undertaking since it involves interacting with large-scale, sophisticated, and diverse ICPS. Abdel-Basset et al. [
19] presented a novel model based on federated deep learning to perform threat hunting against ICPS that captured network data in both temporal and geographical representations. The authors proposed an innovative framework to deploy as Micro-services on relevant edge servers while ensuring adequate resource orchestration using container-based industrial edge computing. An experimental micro-services placement methodology was developed to allow improved micro-services deployment depending on the computational capacity of the participants to resolve the latency issue of an ICSP. The efficiency of the proposed techniques in terms of high accuracy and f1-scores was evaluated by simulated results obtained from two public benchmarks.
By correlating multi-source data, Ju et al. [
20] proposed a multi-layer data fusion approach to detect cyber-attacks. The researchers proposed multi-correlation analysis, which included correlation of events, pattern-knowledge, alert, and alert-context for identifying anomalous traffic, alert-based known attack, pattern-based attack, and alert-pattern attack, respectively. Despite the simple suggested framework, they were unable to demonstrate real-world outcomes from it, and they still believe that manual analysis is the best way to track down threat analysts.
Almohannadi et al. [
21] proposed cyber threat analysis based on three threat intelligence components: attack, pattern, and behavior, utilizing a viable open-source elastic search engine. This research however, focused only on honeypot traffic based on the incident, and not the threat’s history and behavior.
Gao et al. [
22] recommended using open-source cyber threat intelligence to do realistic threat hunting based on system auditing frameworks (OSCTI). The proposed architecture utilized the OSCTI report to extract threat behavior by converting it to a threat behavior graph, which is then ingested into query-based threat hunting to generate a system auditing report as threats are being found. The suggested system’s performance and threat detection accuracy are strongly reliant on the richness of OSCTI text and/or derived threat information, from which a threat behavior pattern was generated.
By mapping the Microsoft Advanced Threat Analytics data to the diamond model and Kill Chain model, Ertaul et al. [
23] were able to detect intrusions. The mapping that resulted emphasized the complexity of an incursion, its phases, and the linkages between the attacker, victim, capacity, and infrastructure. During threat hunting in system memory, Javeed et al. [
24] stressed the significance of additional memory forensics processes to confirm the presence of malware in the host under study. During the research of network log collection, the investigation overlooked significant artifacts that may have led to the discovery of undiscovered threat patterns.
Dietrich et al. [
25] investigated logs from a range of perimeter security devices, including firewall and intrusion detection systems, which were gathered and ingested into the elastic stack for analysis. Outgoing packets are filtered, displayed, and pro-active threat hunting is used to identify unknown threats and validate them using memory forensics.
3. Research Methodology
This research focuses on a threat intelligence report [
26] received against the use case involving an IT services organization, employing 7000 engineers and staff in over 50 customer locations on-site. The customers include enterprise organizations that are technology, energy, manufacturing, and government agencies as well as service engineers delivering support to remote offices and locations. The threat intelligence report mentions an advanced persistent threat (APT) [
27] activity discovered 3 months prior, targeting such service organizations. The activities are seen over networks using common protocols and service applications. From the initial reading, the threat targets most probably the organization we are concerned about, the attack had been in action for the prior 3 months, so a lot of time has already passed and IoCs could have changed over time. The threat intelligence report summary presents indicators of compromise as sender addresses, malicious attachments, hashes, and file names, as illustrated in
Figure 1.
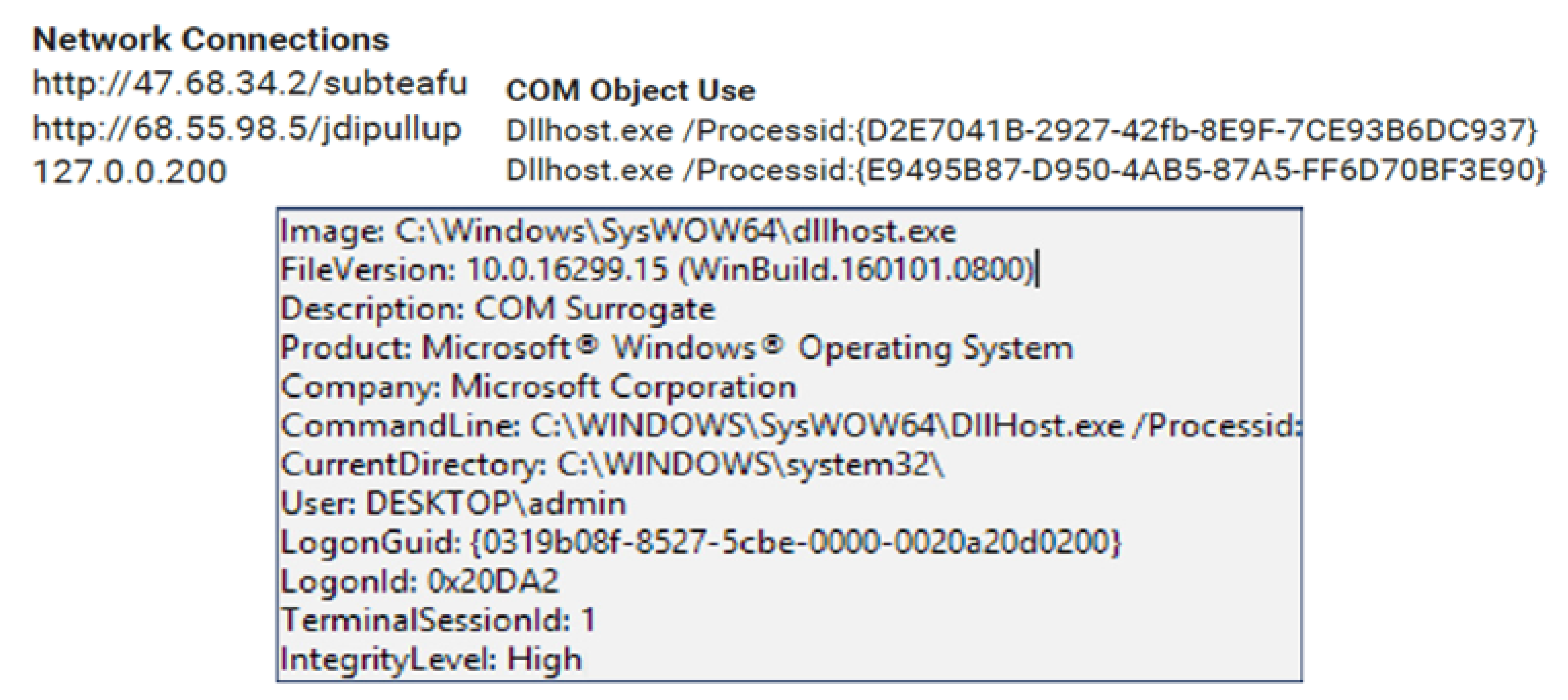
The initial compromise could most likely be using phishing with geopolitical references to US and Antarctica on global warming. The report provides evidence of IOCs on activities using VB script execution, these malicious attachments are being sent as macro-enabled Microsoft Office Excel documents through emails. On opening these email attachments, some Visual Basic scripts execute the payload. This constitutes the behavior. The report further cites the abuse and execution of COM-based objects as presented in
Figure 2. The attack allows standard system mechanics to execute malicious processes under different mandates or contexts that enable privilege escalations.
The payloads are also observed to be executing as native Windows Defense software, such techniques are used to blend in and use living-off-the-land (LOTL) binaries, which are legitimate executables in the operating system. The payloads mask themselves as components of the Windows Defender framework. Maintaining persistence by the malicious payload is done by utilizing the ‘RUN’ keys in the local registry hive, which allows execution of the malware even after the system is rebooted. ‘\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Updater’ is the hive location to maintain elevated privileges for the malicious payload. From the threat intelligence report, the LOTL binaries enumerate the host and environment-saving the output in text files and utilize covert channels to communicate the information to the attacker’s command and control (C&C) server [
28] using HTTP and ICMP protocols. On using standard security processes for identifying and analyzing the breach, no IoCs seem to match. This motivated the researchers to design and implement a behavior-based Threat hunting framework named BTH. The setup is configured to report threat hunting based on adversarial activity profiles to defend and build security strategies. IOCs in the threat intelligence reports start to depreciate from the time of report or the compromise. Consistent threat intelligence differs from report to report, so adversarial behavior related to their standard operating procedures, skill set, and habits is focused on in this research.
4. BTH: Behavior-Based Threat Hunting
The research setup involves hardware with a 4-Core CPU, 8 GB memory, and 50 GB disk running the 64-bit Ubuntu operating system. The software tools involved Elastic instance [
29] and Kibana services managed by Docker accessed over web browsers. After the hardware and software components were implemented to run the Elastic instance, threat logs are ingested using Python code. The logs are initially verified in the Kibana instance for different data and time ranges. The hunting platform uses the MITRE attack framework to analyze the hunts in this research [
30,
31,
32,
33,
34,
35,
36]. The focus of this threat hunting research is to find IoCs based on behavior using the elastic instance searching from top-down searching for malicious documents being sent to senders as attachments in form of macro-enabled Microsoft Excel documents (.xlsm) embedded with VB script which pull and download payloads and executes them, which indicates a phishing attack [
37,
38,
39,
40,
41,
42,
43,
44].
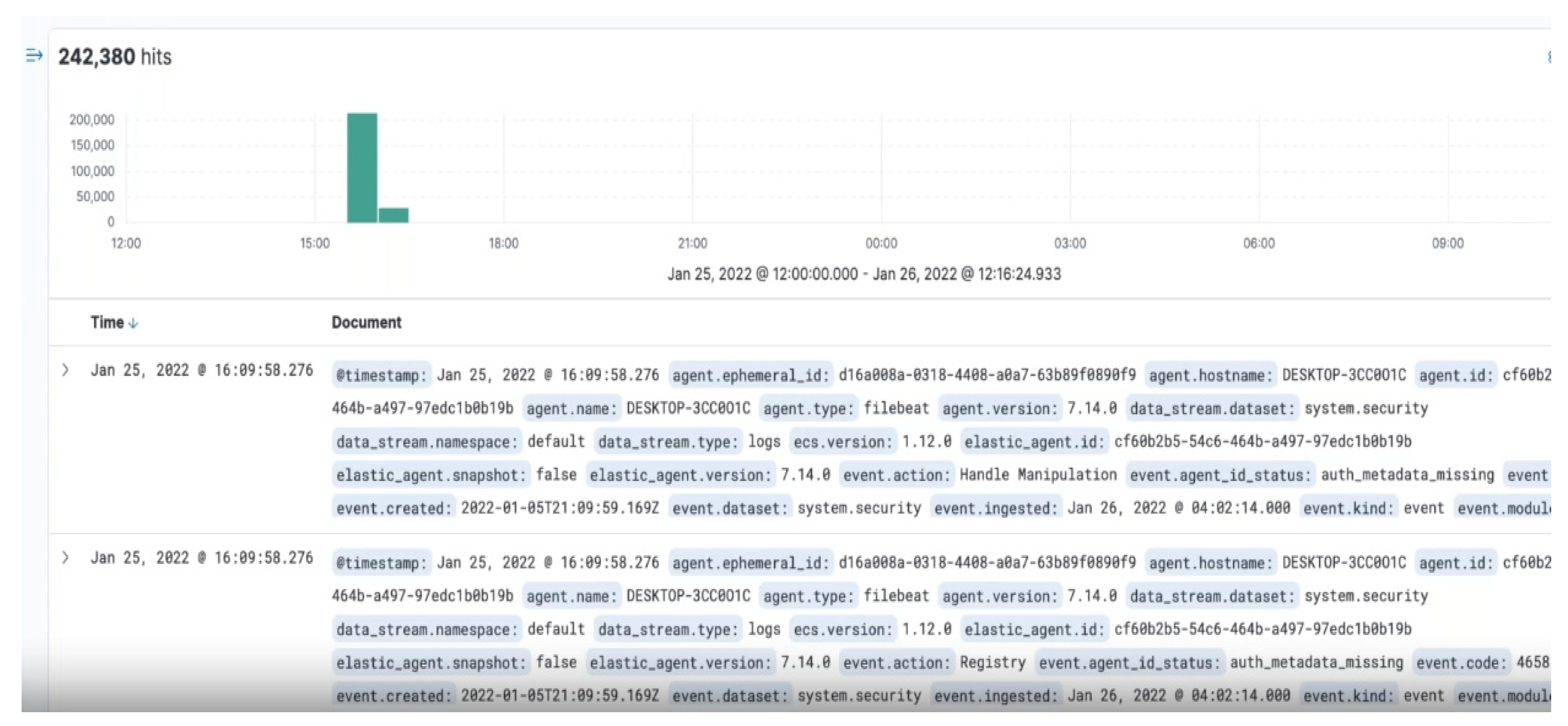
Elastic Instance is ingested with 242,380 threat logs to analyze as illustrated in
Figure 3.
An initial search on the threat hunting platform for Microsoft office and one of the packages displays information about various attack methods for Windows scripting and executing malicious payload programs is shown in
Figure 4.
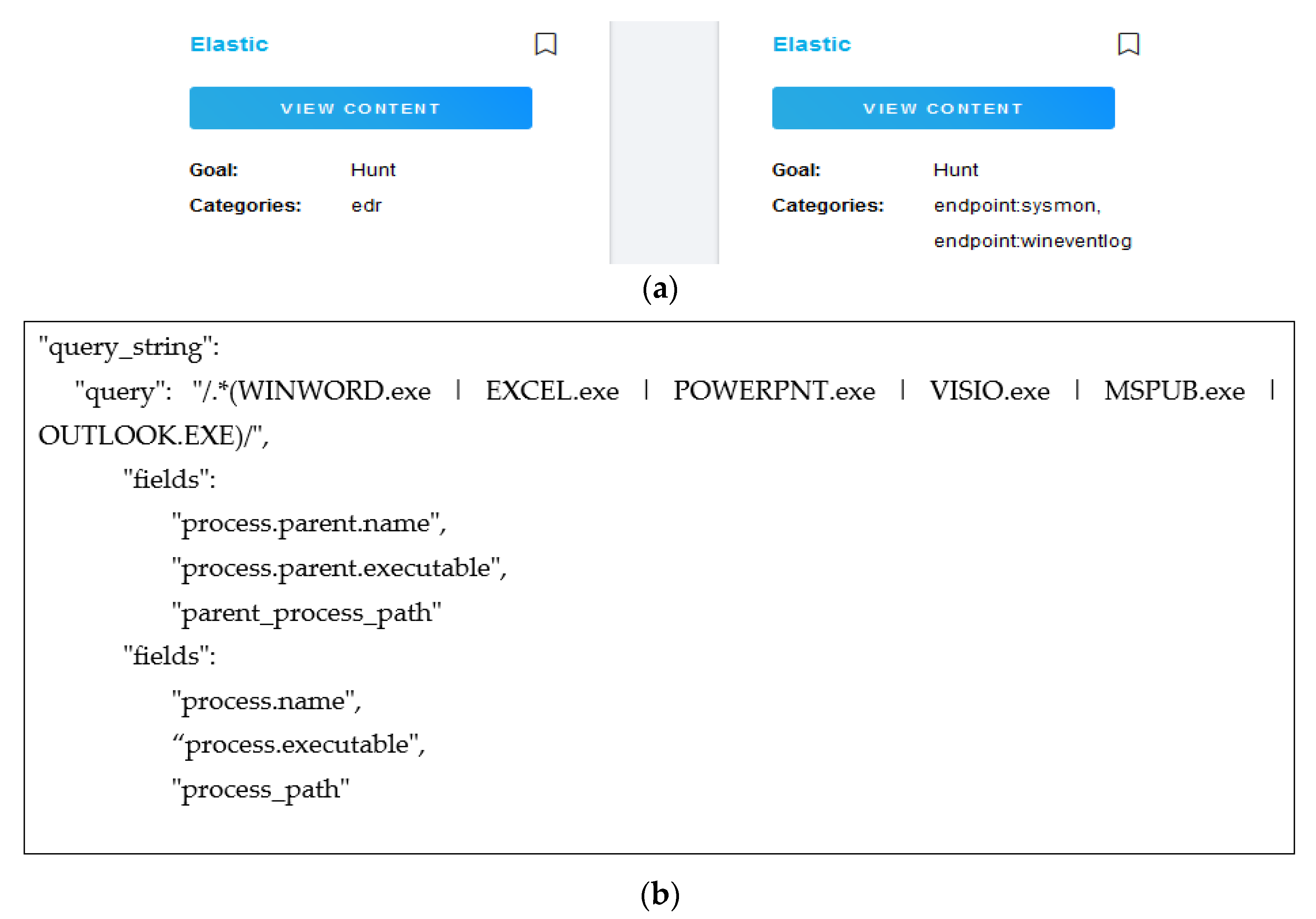
The platform provides details of real-world attack executions related to ‘Microsoft Office’ and Excel documents to Elastic and so the focus is on the Endpoint Sysmon category as presented in
Figure 5 which provides the actual script to query the Elastic Instance having the attack logs.
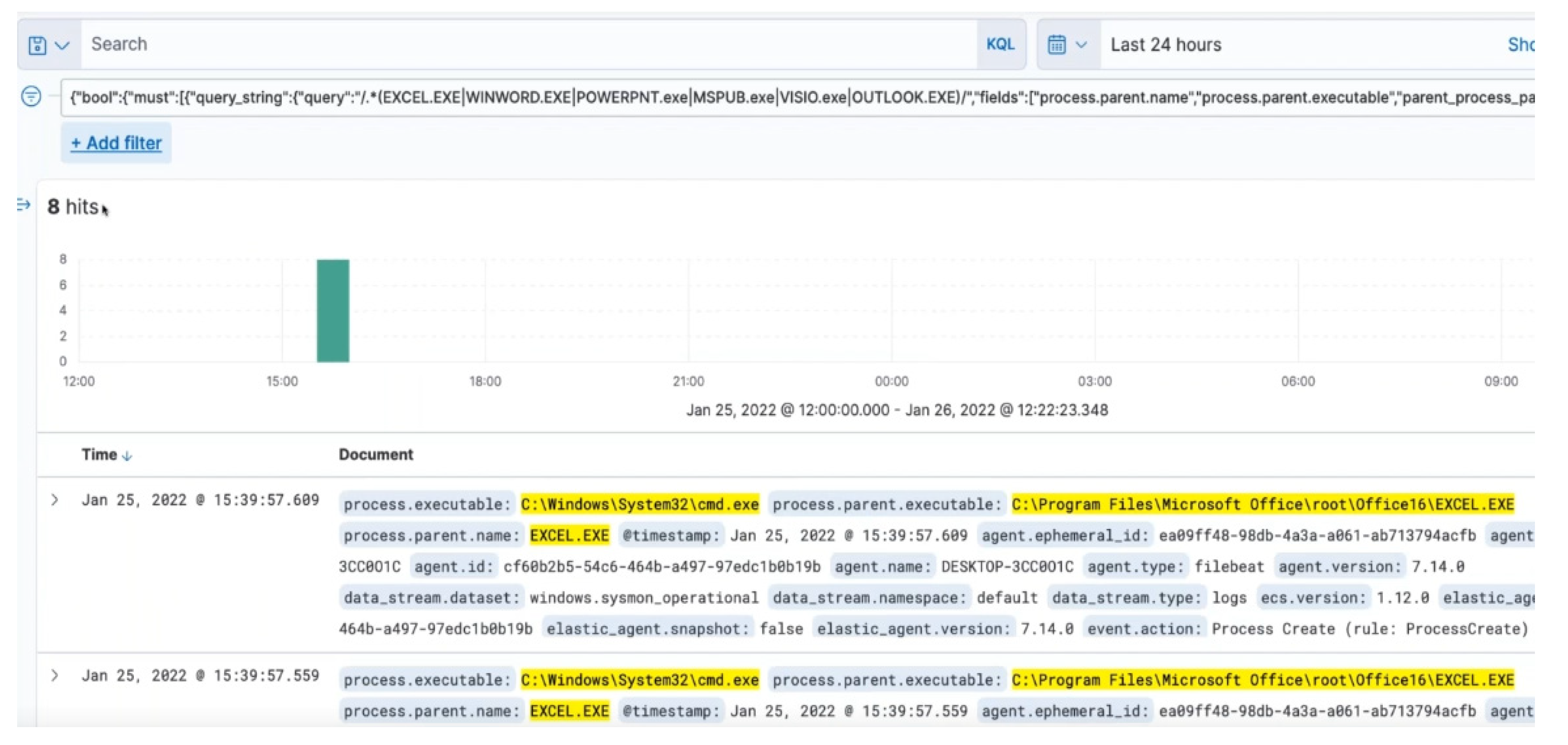
On executing the script on the threat hunt platform, some hits are reported immediately, highlighting some of the threat activities as illustrated in
Figure 6. The next step is to verify if these activities are associated with the threat report.
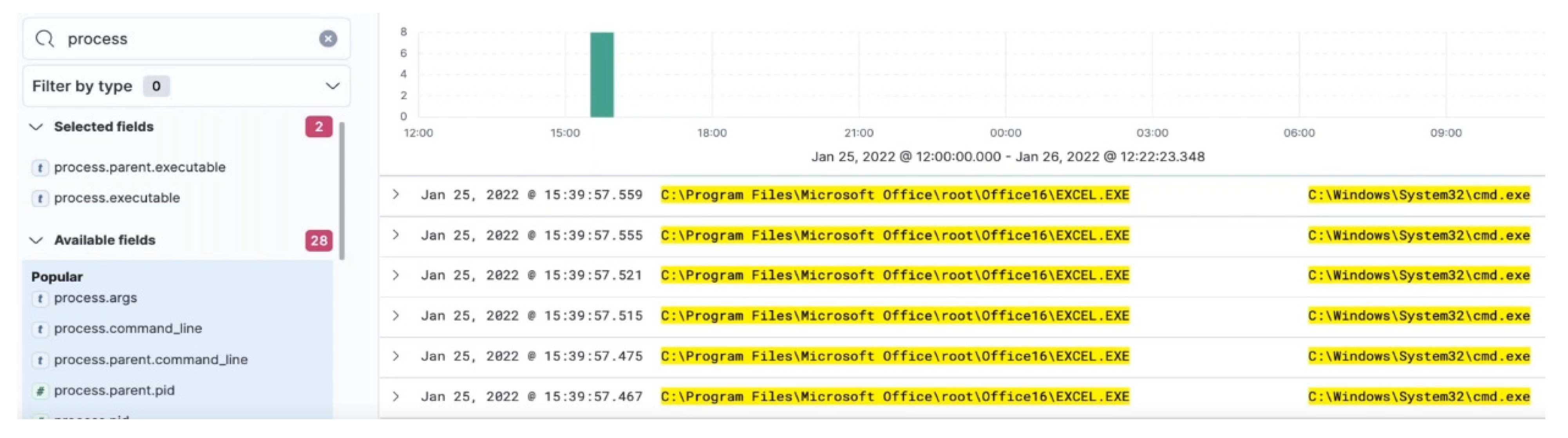
To validate the findings, on filtering two variables ‘process.parent.executable’ and ‘process.executable’ and
Figure 7 illustrates Microsoft Excel launching multiple Windows command line terminals.
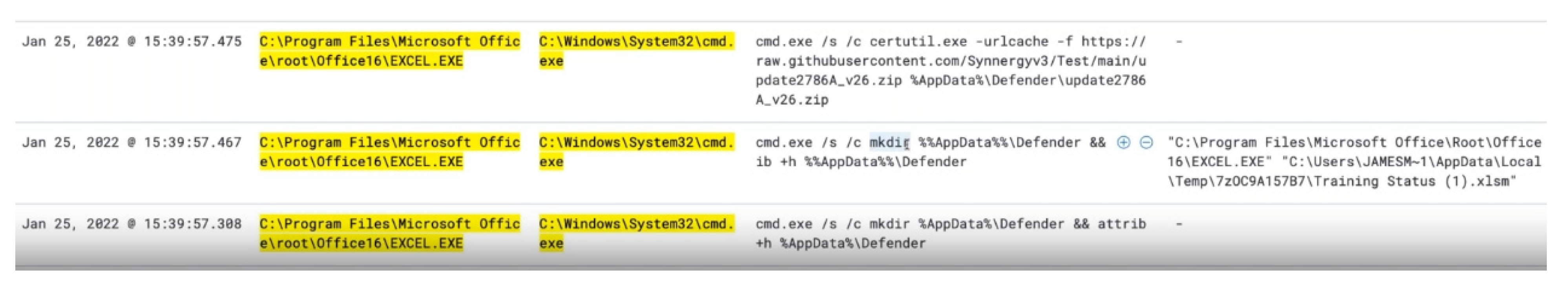
On further filtering and adding ‘process.command_line’ and ‘process.parent.command_line’ variables,
Figure 8 illustrates that Microsoft Excel calls the command line, creating hidden directories in %AppData% \Defender and uses a temporary macro-enabled Excel document from the user folder—this is a similar theme that has been reported in the threat intelligence report.
On reviewing more logs, this utiliutilisesutil.exe which is a Microsoft binary and part of certificate services to dump and display keys and certificates. However, this utility is being used to download a ZIP file from Github URL and copying to the hidden folder that was initially created. On unzipping this, contains several payload executables as presented in
Figure 9.
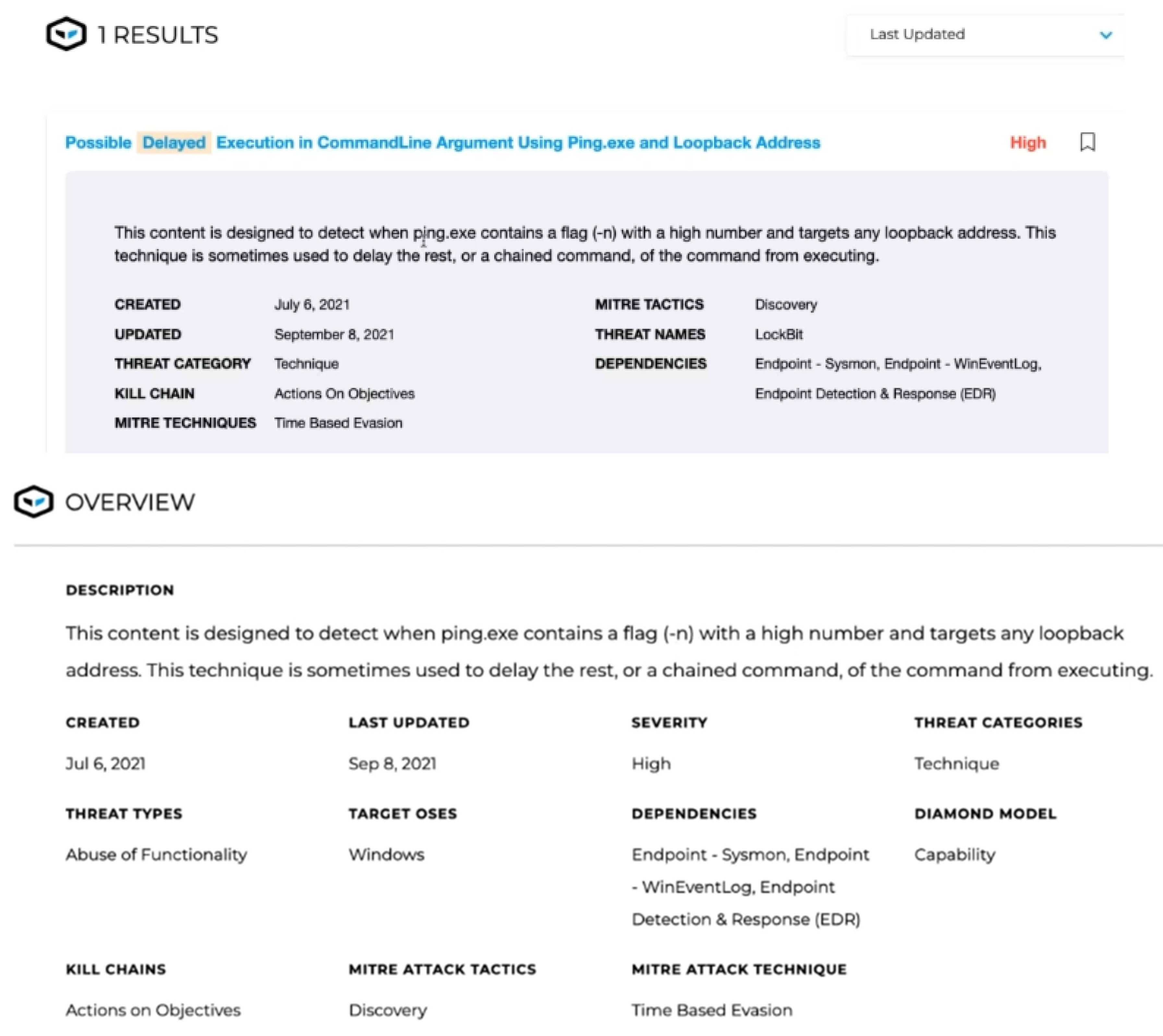
A threat Intelligence report in
Figure 10 also mentions scripts being executed from the attachments and different methods for delayed execution—which seems to be a bad behavior.
On searching the hunting platform for ‘delayed execution’ which provides a result as illustrated in
Figure 11. This presents the command line, Ping, and Loopback as the possible vectors.
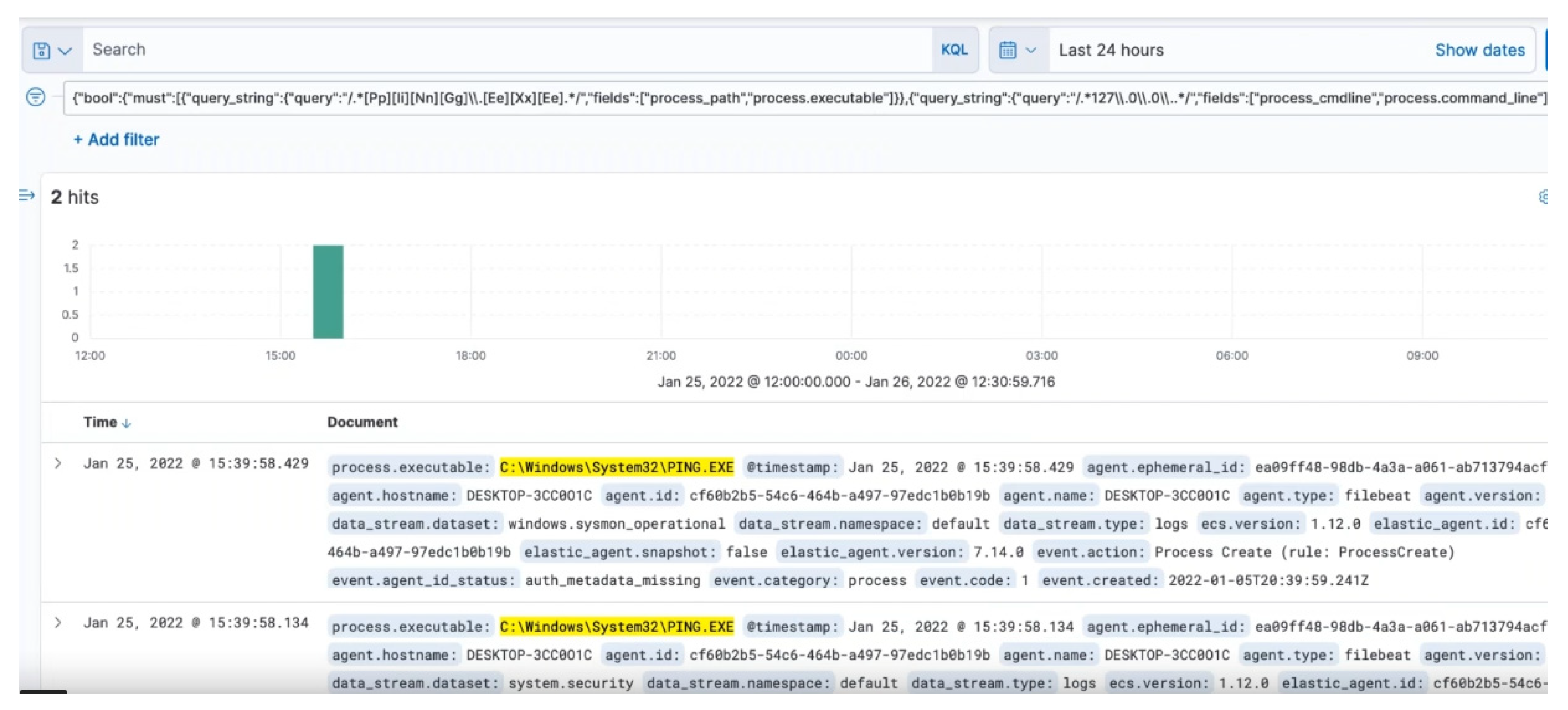
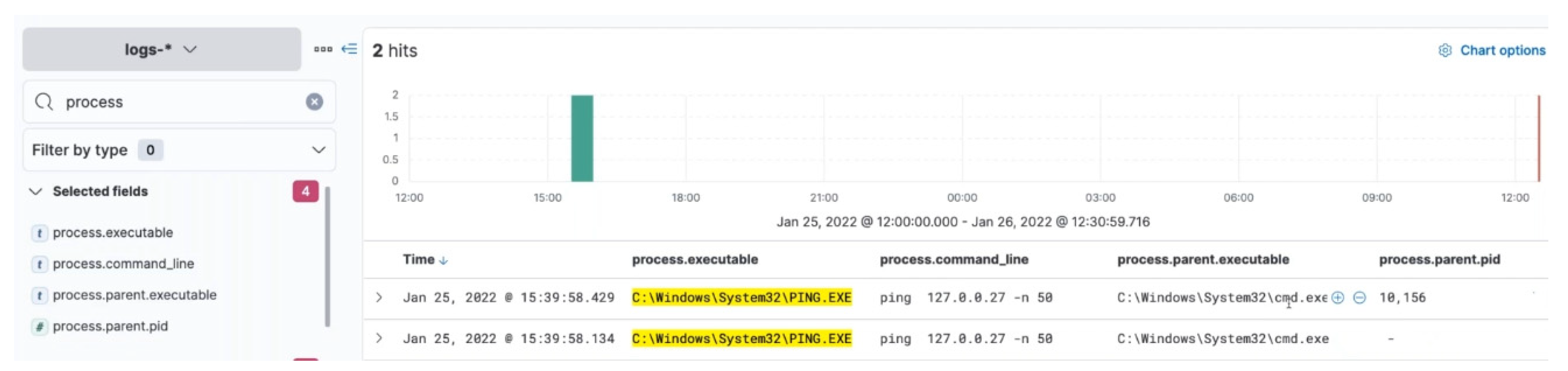
On running the script query for these vectors, two results are obtained as presented in
Figure 12.
On further filtering of the reported findings for ‘process.executable’, ‘process.command_line’, ‘process.parent.executable’, and ‘process.partent_pid’—two results are obtained, as illustrated in
Figure 13. These validate the threat reports of Ping being utilized and the loopback report, which mentioned 127.0.0.200, instead of 127.0.0.27, pinging 50 times—this is a case of using loopback with a slightly different variation to have the same impact, which indicates the attacker’s behavior.
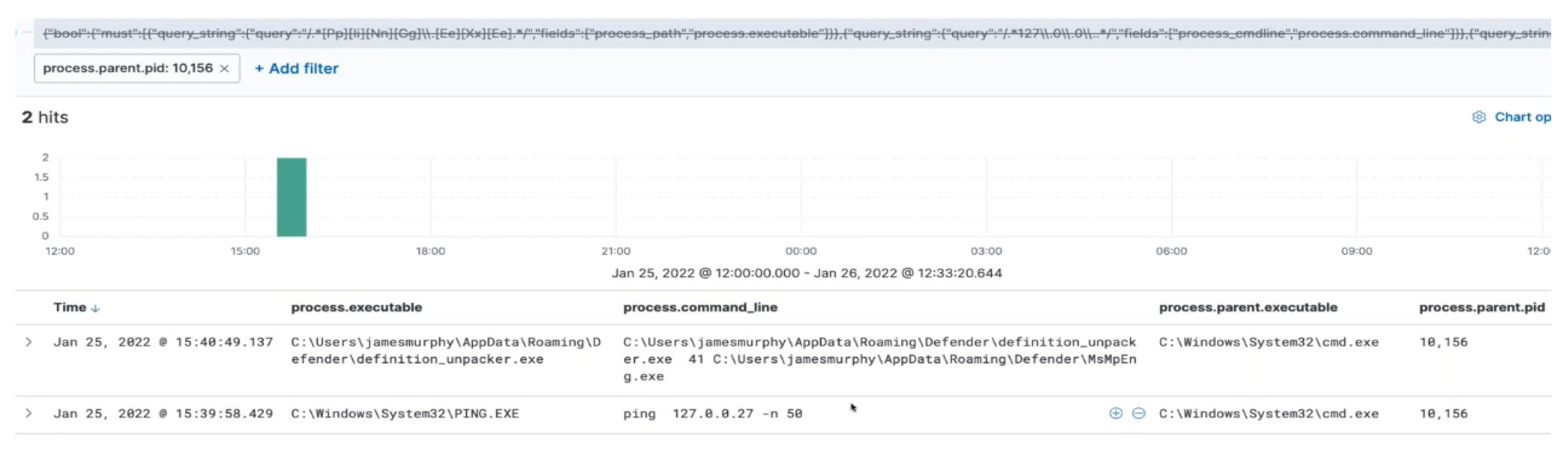
This validates the case being a behavior-based hunt with the cmd.exe executing via process ID 10 and 156. On disabling the initial query and searching for those PIDs,
Figure 14 illustrates process.executable kicked an executable in the folder that further executed ‘msmpeg.exe’.
On looking at the whole context of the filtering and execution and searching for only the process IDs 10, and 156, the logs present the Excel document in
Figure 15.
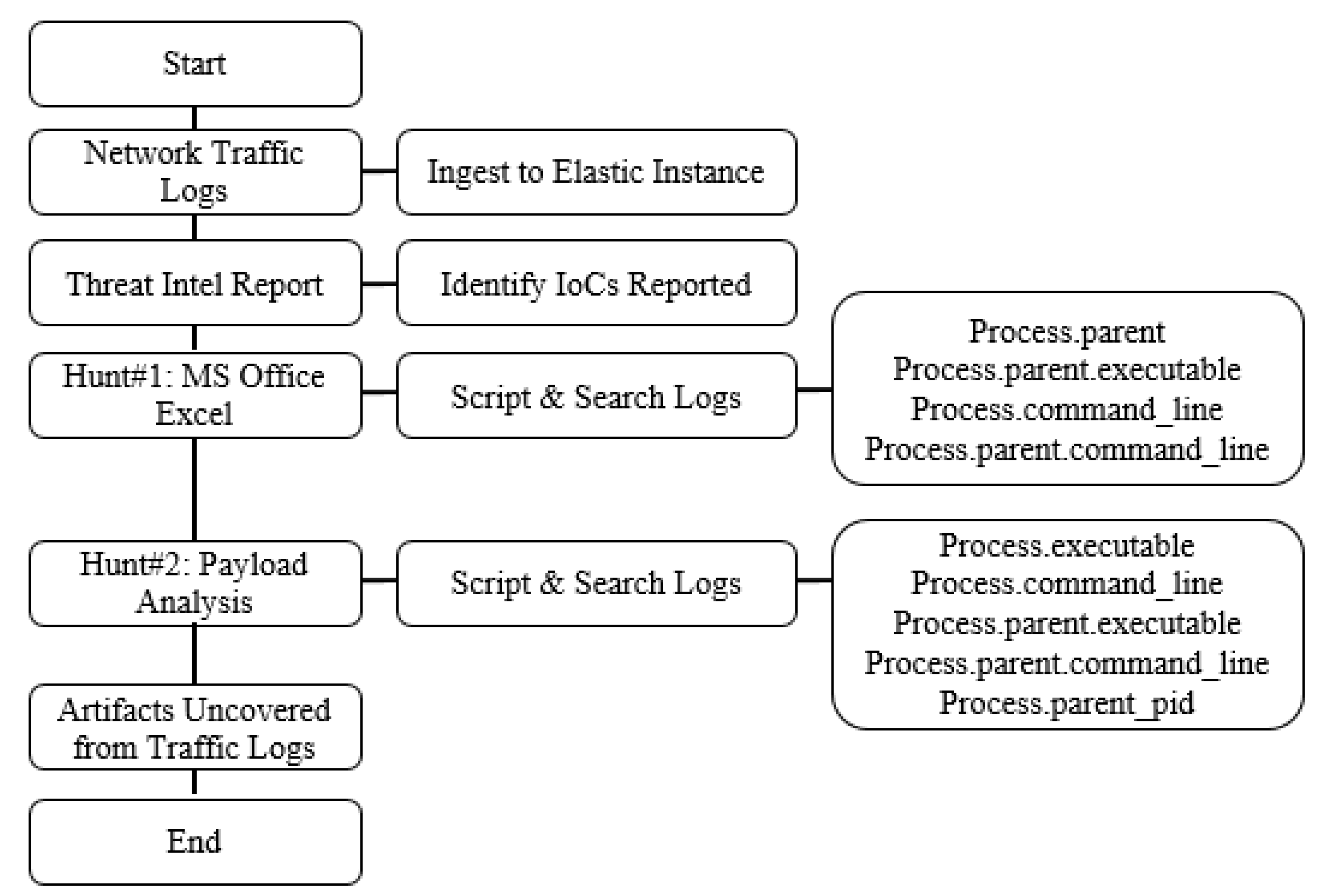
The proposed framework, aptly named BTH—Behavior-based Threat Hunting, referred to the threat intel report, ingested the network traffic logs into the Elastic Instance and then searched and filtered for various IoCs in the hunt platform and then validated artifact and details obtained and discussed in the next section.
5. Results Obtained
Organizations often rely on threat hunters for their ability to detect previously unknown and unidentified threats; threat hunting also serves as an invaluable input and resource for organizations’ existing security operations. To that end, threat hunting should serve as a rising tide that lifts all boats within an organization and not remain a lake of knowledge. The proposed implemented framework automatically tailors and deploys a threat hunting package as per the organization’s unique environment on the SIEM and EDR platforms. Each package includes guided hunt plans and run books for the security teams, this provides actionable threat intelligence, analyst-focused remediation, and cyber threat emulation. This helps in detecting advanced adversaries while maximizing the value of the existing security solutions by transforming traditional CIT into advanced actionable CTI; see the proposed framework playbook in
Figure 16.
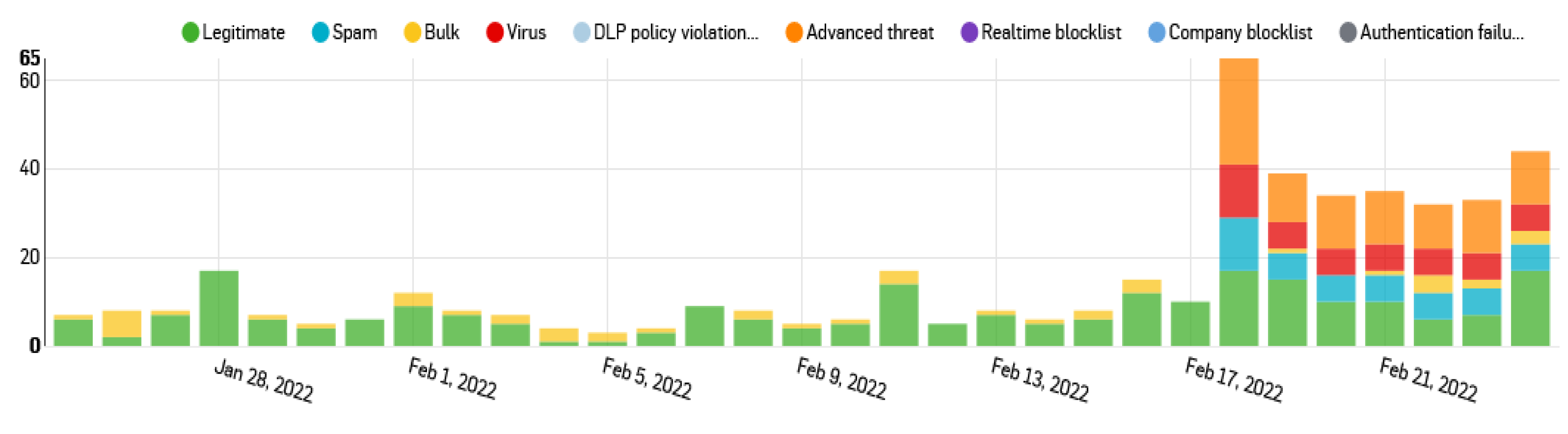
The authors propose first performing alert-based investigations with behavior-based threat hunting aligned with the MITRE matrix. Behaviors include misbehaving Windows OS power-shell, HTTP User-agent string that may download additional toolsets or malware scripts, unknown process IDs and command line process executions, DNS tunneling or logs related to lateral movement resulting in privilege escalation. On reviewing emails received by the organizations, viruses, DLP policy violations, and advanced threats are revealed, which point to the reason for the Email Excel attachment attack, as illustrated in
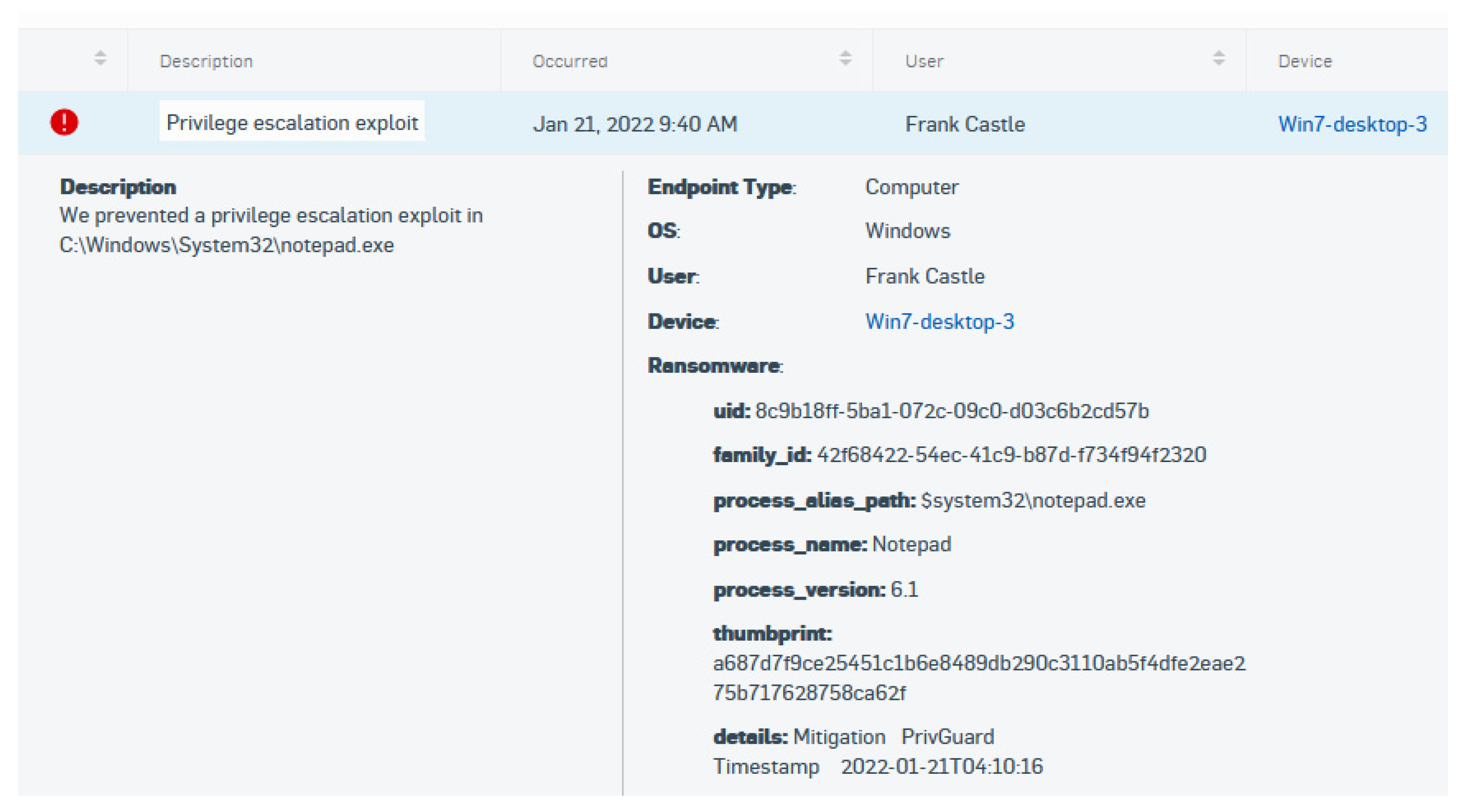
Figure 17.
Figure 18 further confirms the detection of the specific machine and user whose account faced the privilege escalation attack.
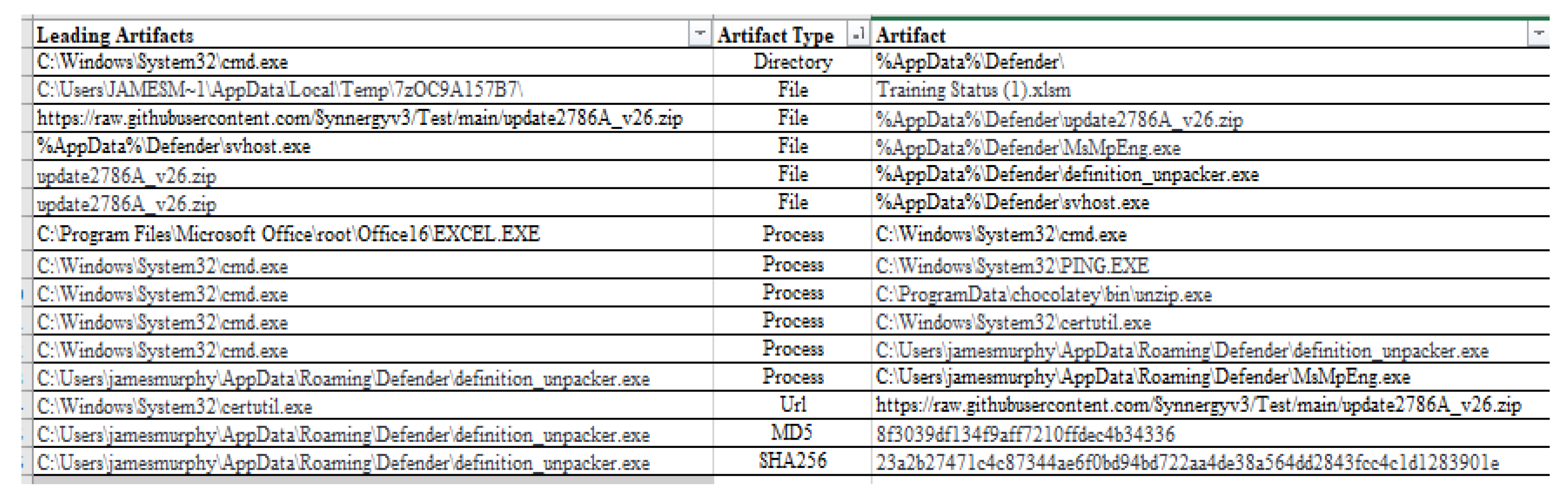
From the above hunts,
Figure 19 illustrates the threat information uncovered and artifacts, which includes leading indicators, types, and the actual artifacts investigated as part of the initial report to escalate and build indicators to investigate further.
As illustrated in this research, behavior-based threat hunting with synthesized criteria to rank order three threat hunt detection profiles and confirm the findings to recognize and consider successful threat hunting capability and measure how far or close organizations are to an ideal or fully mature threat hunting program. The accuracy of behavior-based threat hunting depends on the quantity and quality of data collected, methods and capabilities to visualize and analyze data of varying sources and types, as well as the types of analytics which can be applied to the data to enhance hunters’ insights into said data. An organization utilizing the behavior-based threat hunt would largely address hidden threats in logs. As a result, such organizations are able not only to develop their hunting content and queries but are also able to keep pace with the ancillary tasks associated with threat hunting, especially in the development of threat detection content.
The authors validated the results using machine learning algorithms for the alternate hypothesis with synthesized criteria and enabling rank ordering of three threat hunt detection profiles. The hunting success is based on five criteria for hunt accuracy detection as presented in
Table 3 with criteria as C1 to C5 with accepted values in the range and weight columns representing the percentage values per the scenarios and requirements of the methods.
Table 4 presents the pattern sigma detected and unknown threat patterns, using binary outputs using three different traffic logs.
Table 5 illustrates the different enterprise threat hunting levels, which initially created the hypothesis to drive the organization’s efforts for threat hunting, the use of threat intel to hypothesize threats discovered and executed in the network and systems and behavior-based hunting.