DroidFDR: Automatic Classification of Android Malware Using Model Checking
Abstract
:1. Introduction
- Being first to model the Jimple code with CSP, whose few statements and simple forms facilitate a quick and accurate formal modeling;
- Capturing the characteristics of malicious code such as control flow, data flow, procedure calls, and API calls, which makes it possible for a more comprehensive behavior analysis with a higher accuracy;
- An automatic property extraction algorithm for malware family, which significantly improves the efficiency and avoids the possibility of human error;
- Explaining the family behavior to reveal its working mechanism, thus supporting the evaluation and analysis of malicious code.
2. Related Work
3. Preliminaries
3.1. CSP
3.2. Soot
3.3. Jimple
4. System Design
4.1. Code Conversion
4.2. Formal Modeling
4.3. Property Abstraction
4.4. Model Checking
5. Formal Modeling with CSP
5.1. Core Statements
5.1.1. NopStmt
5.1.2. IdentityStmt
5.1.3. AssignStmt
5.2. Statements for Intraprocedural Control Flow
5.2.1. IfStmt
5.2.2. GotoStmt
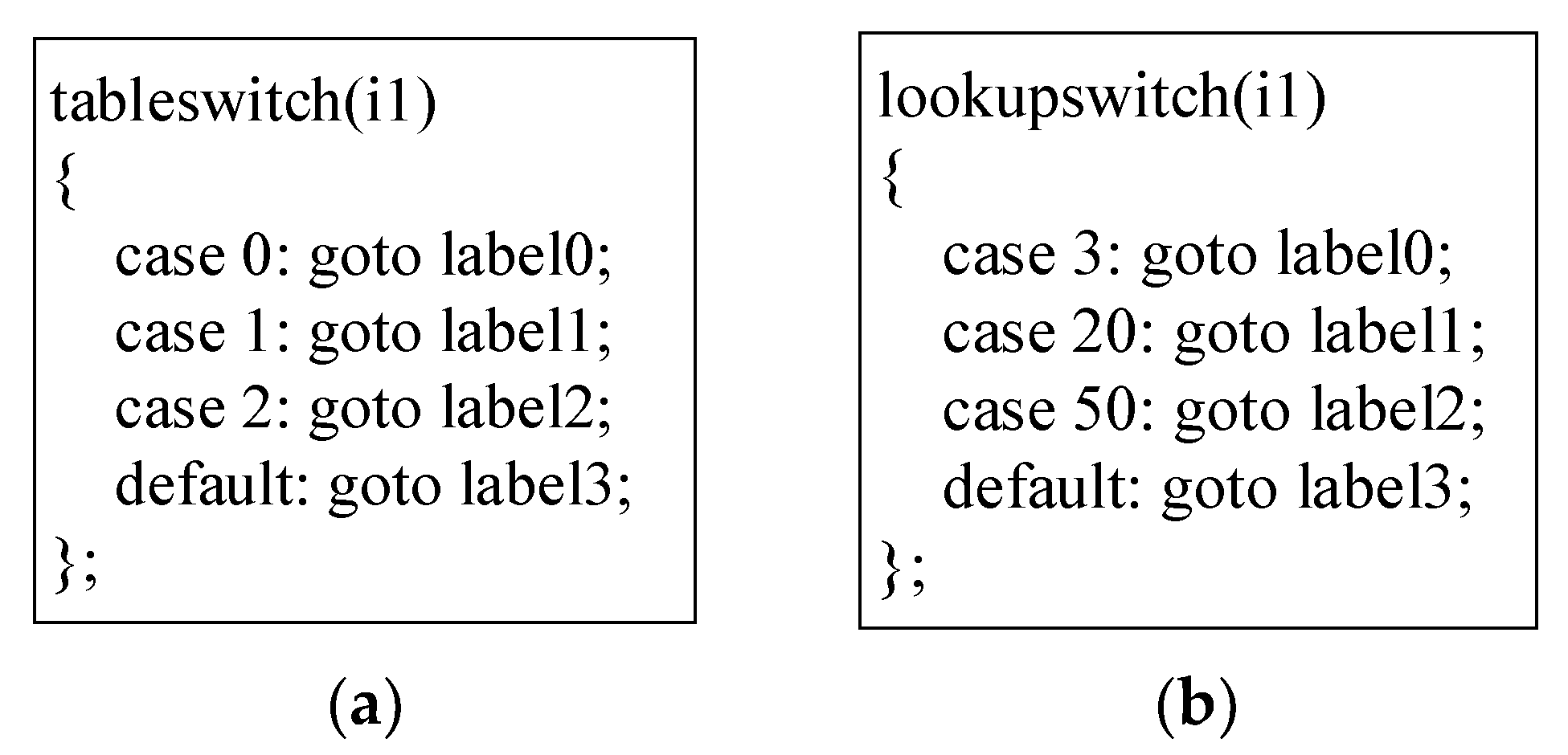
5.2.3. TableSwitchStmt
5.2.4. LookupSwitchStmt
5.3. Statements for Interprocedural Control Flow
5.3.1. InvokeStmt
val.method?val→return.method→Pi+1,r0,i0,…)
5.3.2. ReturnStmt
5.3.3. ReturnVoidStmt
turn.method→SYNM_method)
5.4. Other Statements
5.4.1. ThrowStmt
5.4.2. RetStmt
5.4.3. MonitorStmt
5.5. Modeling of Application
- The processes of all methods in the program, denoted by method1, method2…, are responsible for the execution of the respective method.
- The synchronization process of method calls, SYNM, is responsible for the exclusive call to methods.
- The processes of all classes in the program, denoted by class1, class2…, are responsible for the management of static member variables and static variables of the member methods in the respective class.
- The process used to simulate the main method of the program, denoted by Dummymain, is responsible for modeling the application entries. Since an Android application may have multiple entry points, we refer to FlowDroid to customize a dummy main method for each application, and the processes of the other methods will be executed only when they are called.
- The synchronization process of the objects, SYNO, is responsible for the exclusive access to monitored objects.
6. Abstraction of Family Property
6.1. Composition Structure of Behavior in Property
6.1.1. Sequential Structure
6.1.2. Selective Structure
6.1.3. Parallel Structure
6.1.4. Iterative Structure
6.1.5. Conditional Control Structure
6.2. Algorithm for Extracting Family Properties
7. Model Checking in FDR
| Algorithm 1 Extracting the property of a malware family f |
| Input: |
| Sampf1, Sampf2, … Sampfn ——The processes that express the behavior of test samples in the malware family f |
| SEf ——The sensitive event set of malware family f |
| Output: |
| Specf ——The process that abstracts the property of malware family f |
| Procedure Family_PropertyExtraction |
| begin |
| P1←Simplify(Sampf1, SEf) |
| Specf := P1 |
| for(i = 1, i < n+1, i ++) do |
| begin |
| Pi←Simplify(Sampfi, SEf) |
| if(traces(Specf) ⊆ traces(Pi)) Specf := Pi |
| else if(traces(Pi) ⊆ traces(Specf)) continue |
| else Specf := Specf|Pi |
| end |
| end |
8. Experimental Analysis
8.1. Dataset
- AndroZoo (note: https://androzoo.uni.lu/, accessed on 14 May 2022), a growing collection of Android Applications collected from several sources, whose malware has been analyzed by tens of different AntiVirus products, and
- VirusShare (note: https://virusshare.com/, accessed on 15 May 2022), a continuously updated malware database for share.
8.2. Experimental Results
- Fifty samples of the family that are not involved in the property extraction process,
- Three-hundred malicious samples belonging to other families, and
- Fifty benign applications
- LEILA directly models Java bytecode, whereas DroidFDR converts APK files into an intermediate representation, i.e., Jimple, with fewer types of statements and simpler forms, which is conducive to fast and accurate formal modeling.
- LEILA focuses on capturing sensitive API calls when defining family properties, whereas DroidFDR also considers sensitive string information and sensitive data flow to make the expression of the properties more comprehensive, thus yielding a better detection performance.
- The temporal logic formulae for the property are defined by manually inspecting a few samples from each family in LEILA, whereas DroidFDR includes an automatic property extraction algorithm, which significantly improves the efficiency and avoids the possibility of human error.
8.3. Performance Analysis
8.4. Analysis of Typical Malicious Behaviors
8.4.1. Root Privilege Escalation
process(String, String, String, int[])!“/system/bin/sh”→channel?str→if member(str,
“chmod 777”) then java_io_FileOutputStream_write(int)!str
8.4.2. Access to Sensitive Information
droid.provider.telephony.SMS_RECEIVED”→android_telephony_SmsMes
sage_getOriginatingAddress()?x1→android_telephony_SmsMessage_getDis
playMessageBody()?x2→android_telephony_SmsMessage_getTimestampMil
lis()?x3→android_content_Context_openFileOutput(String, FileCrea
tionMode)!“zjsms.txt”→channel?str→if member(str, x1) then
if member(str, x2) then if member(str, x3) then java_io_FileOutputStream_write(int)!str
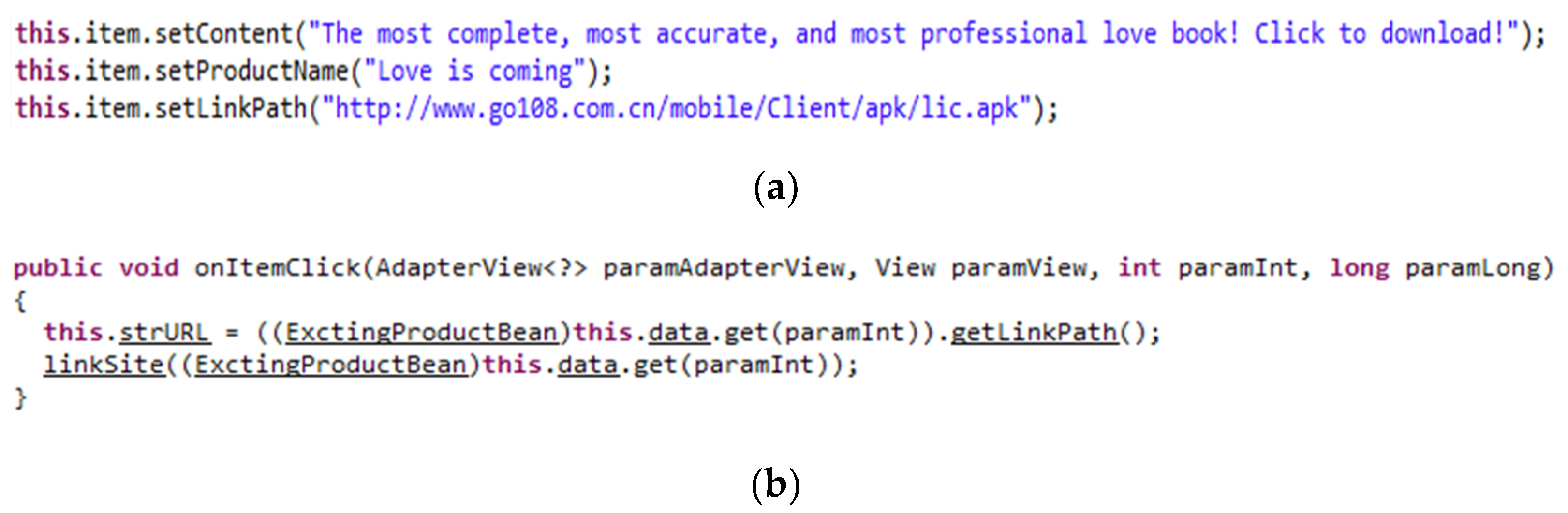
8.4.3. In-App Package Installation
most accurate, and most professional love book! Click to download!”→com_talk
web_comm_ExctingProductBean_setProductName(String)!“Love is coming”→
com_talkweb_comm_ExctingProductBean_setLink
Path(String)!“http://www.go108.com.cn/mobile/Client/apk/lic.apk”→
java_net_URL_openConnection().begin→android_os_Environment_getExternal
StorageDirectory()?x→channel?str→if member(str, x) then if member(str,
“/go108/apk”) then java_io_File_init(String)!str→java_io_File_createNew
File().begin→java_io_FileOutputStream_init(File).begin→android_content_In
tent_SetAction(String)!“android.intent.action.VIEW”→android_content_Intent_Set
DataAndType (Uri, String)!“application/vnd.android.package-archive”→an
droid_app_Activity_StartActivity(Intent).begin
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Xu, J.; Yuan, Q. LibRoad: Rapid, online, and accurate detection of TPLs on Android. IEEE Trans. Mob. Comput. 2022, 21, 167–180. [Google Scholar] [CrossRef]
- Senanayake, J.; Kalutarage, H.; Al-Kadri, M. Android mobile malware detection using machine learning: A systematic review. Electronics 2021, 10, 1606. [Google Scholar] [CrossRef]
- Arp, D.; Spreitzenbarth, M.; Hübner, M.; Gascon, H.; Rieck, K. Drebin: Effective and explainable detection of android malware in your pocket. In Proceedings of the 21st Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Avdiienko, V.; Kuznetsov, K.; Gorla, A.; Zeller, A.; Arzt, S.; Rasthofer, S.; Bodden, E. Mining apps for abnormal usage of sensitive data. In Proceedings of the 37th IEEE/ACM International Conference on Software Engineering (ICSE), IEEE, Florence, Italy, 16–24 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 426–436. [Google Scholar]
- Xu, K.; Li, Y.; Deng, R.H. ICCDetector: ICC-based malware detection on android. IEEE Trans. Inf. Foren. Sec. 2016, 11, 1252–1264. [Google Scholar] [CrossRef]
- Fan, M.; Liu, J.; Luo, X.; Chen, K.; Tian, Z.; Zheng, Q.; Liu, T. Android malware familial classification and representative sample selection via frequent subgraph analysis. IEEE Trans. Inf. Foren. Sec. 2018, 13, 1890–1905. [Google Scholar] [CrossRef]
- Han, Q.; Subrahmanian, V.; Xiong, Y. Android malware detection via (somewhat) robust irreversible feature transformations. IEEE Trans. Inf. Foren. Sec. 2020, 15, 3511–3525. [Google Scholar] [CrossRef]
- Huang, Y.; Li, X.; Qiao, M.; Tang, K.; Zhang, C.; Gui, H.; Wang, P.; Liu, F. Android-SEM: Generative adversarial network for Android malware semantic enhancement model based on transfer learning. Electronics 2022, 11, 672. [Google Scholar] [CrossRef]
- Qiu, J.; Zhang, J.; Luo, W.; Pan, L.; Nepal, S.; Xiang, Y. A survey of Android malware detection with deep neural models. ACM Comput. Surv. 2021, 53, 1–36. [Google Scholar] [CrossRef]
- Dahl, G.E.; Stokes, J.W.; Deng, L.; Yu, D. Large-scale malware classification using random projections and neural networks. In Proceedings of the 38th IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Vancouver, BC, Canada, 26–30 May 2013; pp. 3422–3426. [Google Scholar]
- Huang, W.; Stokes, J.W. MtNet: A multi-task neural network for dynamic malware classification. In Proceedings of the 13th International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment (DIMVA), San Sebastián, Spain, 7–8 July 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 399–418. [Google Scholar]
- Tobiyama, S.; Yamaguchi, Y.; Shimada, H.; Ikuse, T.; Yagi, T. Malware detection with deep neural network using process behavior. In Proceedings of the IEEE 40th Annual Computer Software and Applications Conference (COMPSAC), IEEE, Atlanta, GA, USA, 10–14 June 2016; pp. 577–582. [Google Scholar]
- Wu, B.; Chen, S.; Gao, C.; Fan, L.; Liu, Y.; Wen, W.; Lyu, M. Why an android app is classified as malware: Toward malware classification interpretation. ACM Trans. Softw. Eng. Meth. 2021, 30, 1–29. [Google Scholar] [CrossRef]
- Nix, R.; Zhang, J. Classification of android apps and malware using deep neural networks. In Proceedings of the International Joint Conference on Neural Networks (IJCNN), IEEE, Anchorage, AK, USA, 14–19 May 2017; pp. 1871–1878. [Google Scholar]
- McLaughlin, N.; Rincon, J.M.; Kang, B.; Yerima, S.; Miller, P.; Sezer, S.; Safaei, Y.; Trickel, E.; Zhao, Z.; Doupe, A.; et al. Deep android malware detection. In Proceedings of the 7th ACM Conference on Data and Application Security and Privacy (CODASPY), Scottsdale, AZ, USA, 22–24 March 2017; ACM: New York, NY, USA, 2017; pp. 301–308. [Google Scholar]
- Karunanayake, N.; Rajasegaran, J.; Gunathillake, A.; Seneviratne, S.; Jourjon, G. A multi-modal neural embeddings approach for detecting mobile counterfeit apps: A case study on Google Play store. IEEE Trans. Mob. Comput. 2022, 21, 16–30. [Google Scholar] [CrossRef]
- Yuan, Z.; Lu, Y.; Wang, Z.; Xue, Y. Droid-Sec: Deep learning in android malware detection. In Proceedings of the ACM Conference on SIGCOMM, Chicago, IL, USA, 17–22 August 2014; ACM: New York, NY, USA, 2014; pp. 371–372. [Google Scholar]
- Yuan, Z.; Lu, Y.; Xue, Y. DroidDetector: Android malware characterization and detection using deep learning. Tsinghua Sci. Technol. 2016, 21, 114–123. [Google Scholar] [CrossRef]
- Xu, L.; Zhang, D.; Jayasena, N.; Cavazos, J. HADM: Hybrid analysis for detection of malware. In Proceedings of the 2nd SAI Intelligent Systems Conference (IntelliSys), Amsterdam, The Netherlands, 2–3 September 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 702–724. [Google Scholar]
- Amera, E.; El-Sappagh, S. Robust deep learning early alarm prediction model based on the behavioural smell for android malware. Comput. Secur. 2022, 116, 102670. [Google Scholar] [CrossRef]
- Xu, J.; Li, Y.; Deng, R.; Xu, K. SDAC: A slow-aging solution for Android malware detection using semantic distance based API clustering. IEEE Trans. Dependable Secur. Comput. 2022, 19, 1149–1163. [Google Scholar] [CrossRef]
- Huang, Y.; Lin, C.; Guo, Y.; Lo, K.; Sun, Y.; Chen, M. Open source intelligence for malicious behavior discovery and interpretation. IEEE Trans. Dependable Secur. Comput. 2022, 19, 776–789. [Google Scholar] [CrossRef]
- Enck, W.; Gilbert, P.; Chun, B.G.; Cox, L.P.; Jung, J.; McDaniel, P.; Sheth, A.N. TaintDroid: An information-flow tracking system for realtime privacy monitoring on smartphones. ACM Trans. Comput. Syst. 2014, 32, 1–29. [Google Scholar] [CrossRef]
- Arzt, S.; Rasthofer, S.; Fritz, C.; Bodden, E.; Bartel, A.; Klein, J.; Traon, Y.L.; Octeau, D.; McDaniel, P. FlowDroid: Precise context, flow, field, object-sensitive and lifecycle-aware taint analysis for android apps. In Proceedings of the 35th ACM SIGPLAN Conference on Programming Language Design and Implementation (PLDI), Edinburgh, UK, 9–14 June 2014; ACM: New York, NY, USA, 2014; pp. 259–269. [Google Scholar]
- Wei, F.; Roy, S.; Ou, X. Amandroid: A precise and general inter-component data flow analysis framework for security vetting of android apps. ACM Trans. Priv. Secur. 2018, 21, 1329–1341. [Google Scholar] [CrossRef]
- Li, L.; Bartel, A.; Bissyande, T.F.; Klein, J.; Traon, Y.L.; Arzt, S.; Rasthofer, S.; Bodden, E.; Octeau, D.; McDaniel, P. IccTA: Detecting inter-component privacy leaks in android apps. In Proceedings of the 37th IEEE/ACM International Conference on Software Engineering (ICSE), IEEE, Florence, Italy, 16–24 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 280–291. [Google Scholar]
- Bianchi, A.; Corbetta, J.; Invernizzi, L.; Fratantonio, Y.; Kruegel, C.; Vigna, G. What the app is that? Deception and countermeasures in the android user interface. In Proceedings of the 36th IEEE Symposium on Security and Privacy (SP), IEEE, San Jose, CA, USA, 17–21 May 2015; pp. 931–948. [Google Scholar]
- Zhao, Q.; Zuo, C.; Dolan-Gavitt, B.; Pellegrino, G.; Lin, Z. Automatic uncovering of hidden behaviors from input validation in mobile apps. In Proceedings of the 41th IEEE Symposium on Security and Privacy (SP), IEEE, San Francisco, CA, USA, 18–20 May 2020; pp. 1106–1120. [Google Scholar]
- Yang, Z.; Yuan, Z.; Jin, S.; Chen, X.; Sun, L.; Du, X.; Li, W.; Zhang, H. FSAFlow: Lightweight and fast dynamic path tracking and control for privacy protection on Android using hybrid analysis with state-reduction strategy. In Proceedings of the 43rd IEEE Symposium on Security and Privacy (SP), IEEE, San Francisco, CA, USA, 23–25 May 2022; pp. 721–736. [Google Scholar]
- Zhang, J.; Tian, C.; Duan, Z. An efficient approach for taint analysis of Android applications. Comput. Secur. 2021, 104, 102161. [Google Scholar] [CrossRef]
- Palit, T.; Moon, J.; Monrose, F.; Polychronakis, M. DynPTA: Combining static and dynamic analysis for practical selective data protection. In Proceedings of the 42rd IEEE Symposium on Security and Privacy (SP), IEEE, San Francisco, CA, USA, 24–27 May 2021; pp. 1919–1937. [Google Scholar]
- Yang, W.; Xiao, X.; Andow, B.; Li, S.; Xie, T.; Enck, W. AppContext: Differentiating malicious and benign mobile app behaviors using context. In Proceedings of the 37th IEEE/ACM International Conference on Software Engineering (ICSE), IEEE, Florence, Italy, 16–24 May 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 303–313. [Google Scholar]
- Rasthofer, S.; Arzt, S.; Bodden, E. A machine-learning approach for classifying and categorizing android sources and sinks. In Proceedings of the 21st Annual Network and Distributed System Security Symposium (NDSS), San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Shen, F.; Vecchio, J.D.; Mohaisen, A.; Ko, S.Y.; Ziarek, L. Android malware detection using complex-flows. IEEE Trans. Mobile Comput. 2019, 18, 1231–1245. [Google Scholar] [CrossRef]
- Song, F.; Touili, T. Model-checking for android malware detection. In Proceedings of the 12th Asian Symposium on Programming Languages and Systems (APLAS), Singapore, 17–19 November 2014; Springer: Berlin/Heidelberg, Germany, 2014; pp. 216–235. [Google Scholar]
- Bai, G.; Ye, Q.; Wu, Y.; Botha, H.; Sun, J.; Liu, Y.; Dong, J.S.; Visser, W. Towards model checking android applications. IEEE Trans. Software Eng. 2018, 44, 595–612. [Google Scholar] [CrossRef]
- Mercaldo, F.; Nardone, V.; Santone, A.; Visaggio, C.A. Ransomware steals your phone. Formal methods rescue it. In Proceedings of the 36th International Conference on Formal Techniques for Distributed Objects, Components, and Systems (FORTE), Crete, Greece, 6–9 June 2016; Springer: Berlin/Heidelberg, Germany, 2016; pp. 212–221. [Google Scholar]
- Mercaldo, F.; Nardone, V.; Santone, A.; Visaggio, C.A. Download malware? No, thanks. How formal methods can block update attacks. In Proceedings of the 4th FME Workshop on Formal Methods in Software Engineering (FormaliSE), Austin, TX, USA, 15 May 2016; ACM: New York, NY, USA, 2016; pp. 22–28. [Google Scholar]
- Battista, P.; Mercaldo, F.; Nardone, V.; Santone, A. Identification of android malware families with model checking. In Proceedings of the 2nd International Conference on Information Systems Security and Privacy (ICISSP), Rome, Italy, 19–21 February 2016; pp. 542–547. [Google Scholar]
- Martinelli, F.; Mercaldo, F.; Nardone, V.; Santone, A.; Vaglinid, G. Model checking and machine learning techniques for HummingBad mobile malware detection and mitigation. Simul. Model. Pract. Theory 2020, 105, 102169. [Google Scholar] [CrossRef]
- Canfora, G.; Martinelli, F.; Mercaldo, F.; Nardone, V.; Santone, A.; Visaggio, C.A. LEILA: Formal tool for identifying mobile malicious behavior. IEEE Trans. Software Eng. 2019, 45, 1230–1252. [Google Scholar] [CrossRef]
- Hoare, C.A.R. Communicating Sequential Processes; Prentice Hall: Upper Saddle River, NJ, USA, 1985. [Google Scholar]
- Einarsso, A.; Nielsen, J.D. A Survivor’s Guide to Java Program Analysis with Soot; Version 1.1; BRICS, Department of Computer Science, University of Aarhus: Aarhus, Denmark, 2008. [Google Scholar]
- Gardiner, P.; Goldsmith, M.; Hulance, J.; Jackson, D.; Roscoe, B.; Scattergood, B.; Armstrong, P. Failures-Divergence Refinement: FDR2 User Manual; FDR Version 2.82; Formal Systems (Europe) Ltd.: Oxford, UK, 2005. [Google Scholar]
- Milner, R. Communication and Concurrency; Prentice Hall: Upper Saddle River, NJ, USA, 1989. [Google Scholar]
- Barbuti, R.; Francesco, N.D.; Santone, A.; Vaglini, G. Selective mu-calculus and formula-based equivalence of transition systems. J. Comput. Syst. Sci. 1999, 59, 537–556. [Google Scholar] [CrossRef] [Green Version]
- Iadarola, G.; Martinelli, F.; Mercaldo, F.; Santone, A. Call graph and model checking for fine-grained Android malicious behaviour detection. Appl. Sci. 2020, 10, 7975. [Google Scholar] [CrossRef]
- Cimino, M.; Francesco, N.; Mercaldo, F.; Santone, A.; Vaglini, G. Model checking for malicious family detection and phylogenetic analysis in mobile environment. Comput. Secur. 2020, 90, 101691. [Google Scholar] [CrossRef]
- Zhou, Y.; Jiang, X. Dissecting android malware: Characterization and evolution. In Proceedings of the 33rd IEEE Symposium on Security and Privacy (SP), IEEE, San Francisco, CA, USA, 24–25 May 2012; pp. 95–109. [Google Scholar]
- Andersen, J.R.; Andersen, N.; Enevoldsen, S.; Hansen, M.M.; Larsen, K.G.; Olesen, S.R.; Srba, J.; Wortmann, J.K. CAAL: Concurrency workbench, Aalborg edition. In Proceedings of the 12th International Colloquium on Theoretical Aspects of Computing (ICTAC), Cali, Colombia, 29–31 October 2015; ACM: New York, NY, USA, 2015; pp. 573–582. [Google Scholar]
- Zhou, Z. Machine Learning; Tsinghua University Press: Beijing, China, 2016. [Google Scholar]









| Category | Examples | Features | Interpretability | Family Classification |
|---|---|---|---|---|
| ML-based detection | [3] | Components, intent filters, permissions, API calls | Only provide the top features that contribute to the classification as a behavioral explanation | Y |
| [13] | Permissions, API calls | Produce the semantic order of selected key features, while the order rule is made manually | Y | |
| [22] | API calls | Select explanation template from OSINT, which also requires a lot of manual support | Y | |
| [5,6,7,10,11,12,14,15,20,21] | One or more of the features of components, intent filters, intent, API calls | Not supported | Y | |
| [8,16,17,18,19] | One or more of the features of components, intent filters, permissions, API/function calls, annotations | Not supported | N | |
| Information flow analysis | [23,24,25,26,27,28,29,30,31] | data flows | Not supported | N |
| [4,32,34] | data flows | Not supported | Y | |
| Formal methods | [41,47,48] | API calls, control flows function call | Output fine-grained behavior descriptions, but express family properties manually | Y |
| Ours | API calls, control flows, function call, and data flows | Output fine-grained behavior descriptions, and extract family properties from samples automatically | Y |
| Malware Family | Precision (%) | Recall (%) | F1 Score (%) | Accuracy (%) | AUC | |||||
|---|---|---|---|---|---|---|---|---|---|---|
| LEILA | DroidFDR | L | D | L | D | L | D | L | D | |
| Opfake | 92.00 | 94.12 | 92.00 | 96.00 | 92.00 | 95.05 | 98.00 | 98.75 | 0.9543 | 0.9757 |
| GingerMaster | 95.92 | 95.92 | 94.00 | 94.00 | 94.95 | 94.95 | 98.75 | 98.75 | 0.9671 | 0.9671 |
| FakeInstaller | 84.21 | 96.15 | 96.00 | 100.00 | 89.72 | 98.04 | 97.25 | 99.50 | 0.9671 | 0.9971 |
| Plankton | 100.00 | 96.08 | 100.00 | 98.00 | 100.00 | 97.03 | 100.00 | 99.25 | 1.00 | 0.9871 |
| Average | 93.03 | 95.57 | 95.50 | 97.00 | 94.12 | 96.27 | 98.50 | 99.06 | 0.9721 | 0.9818 |
| Malware Family | # Family Sample | # Other Malware | # Benign Applications | Total Number |
|---|---|---|---|---|
| AnserverBot | 187 | 706 | 300 | 1193 |
| BaseBridge | 122 | 771 | 300 | 1193 |
| DroidKungFu3 | 309 | 584 | 300 | 1193 |
| DroidKungFu4 | 96 | 797 | 300 | 1193 |
| Geinimi | 69 | 824 | 300 | 1193 |
| KMin | 52 | 841 | 300 | 1193 |
| Pjapps | 58 | 835 | 300 | 1193 |
| Adrd | 91 | 802 | 300 | 1193 |
| DroidDream | 81 | 812 | 300 | 1193 |
| FakeDoc | 132 | 761 | 300 | 1193 |
| Dowgin | 100 | 793 | 300 | 1193 |
| Wooboo | 100 | 793 | 300 | 1193 |
| Malware Family | Sample Number | Precision (%) | Recall (%) | F1 Score (%) | Accuracy (%) | AUC |
|---|---|---|---|---|---|---|
| AnserverBot | 187 | 97.30 | 96.26 | 96.77 | 98.91 | 0.9783 |
| BaseBridge | 122 | 95.87 | 95.08 | 95.47 | 99.08 | 0.9731 |
| DroidKungFu3 | 309 | 97.72 | 97.09 | 97.40 | 98.66 | 0.9815 |
| DroidKungFu4 | 96 | 96.81 | 94.79 | 95.79 | 99.33 | 0.9726 |
| Geinimi | 69 | 95.65 | 95.65 | 95.65 | 99.50 | 0.9769 |
| KMin | 52 | 94.32 | 96.15 | 95.24 | 99.58 | 0.9795 |
| Pjapps | 58 | 91.52 | 93.10 | 92.31 | 99.25 | 0.9633 |
| Adrd | 91 | 96.74 | 97.80 | 97.27 | 99.58 | 0.9876 |
| DroidDream | 81 | 95.18 | 97.53 | 96.34 | 99.50 | 0.9859 |
| FakeDoc | 132 | 99.23 | 98.48 | 98.85 | 99.66 | 0.9882 |
| Dowgin | 100 | 97.06 | 99.00 | 98.02 | 99.66 | 0.9936 |
| Wooboo | 100 | 96.04 | 97.00 | 96.52 | 99.41 | 0.9832 |
| Phase | Code Conversion | Formal Modeling | Property Abstraction | Model Checking |
|---|---|---|---|---|
| Time (s) | 10.94 | 5.97 | 1505.32 | 268.23 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yang, Z.; Chao, F.; Chen, X.; Jin, S.; Sun, L.; Du, X. DroidFDR: Automatic Classification of Android Malware Using Model Checking. Electronics 2022, 11, 1798. https://doi.org/10.3390/electronics11111798
Yang Z, Chao F, Chen X, Jin S, Sun L, Du X. DroidFDR: Automatic Classification of Android Malware Using Model Checking. Electronics. 2022; 11(11):1798. https://doi.org/10.3390/electronics11111798
Chicago/Turabian StyleYang, Zhi, Fan Chao, Xingyuan Chen, Shuyuan Jin, Lei Sun, and Xuehui Du. 2022. "DroidFDR: Automatic Classification of Android Malware Using Model Checking" Electronics 11, no. 11: 1798. https://doi.org/10.3390/electronics11111798
APA StyleYang, Z., Chao, F., Chen, X., Jin, S., Sun, L., & Du, X. (2022). DroidFDR: Automatic Classification of Android Malware Using Model Checking. Electronics, 11(11), 1798. https://doi.org/10.3390/electronics11111798






