An Exploratory Study of Cognitive Sciences Applied to Cybersecurity
Abstract
:1. Introduction
- A text mining process to identify challenges in the field of cybersecurity and analyze the impact of cyberattacks and the future direction of cybersecurity solutions based on cognitive science;
- A Systematic Literature Review (SLR) to identify the contributions of applied cognitive sciences in cybersecurity as alternatives for proactive strategies. The main contribution of this study is the definition of a cognitive cybersecurity model supported by the findings of a literature review in this research area based on the PRISMA methodology.
2. Background
2.1. Adversarial and User Analysis
- Cultural characteristics;
- Behavior patterns;
- Types of attacks.
2.2. Cognitive Sciences
2.3. Cognitive Process
2.4. Cognitive Security
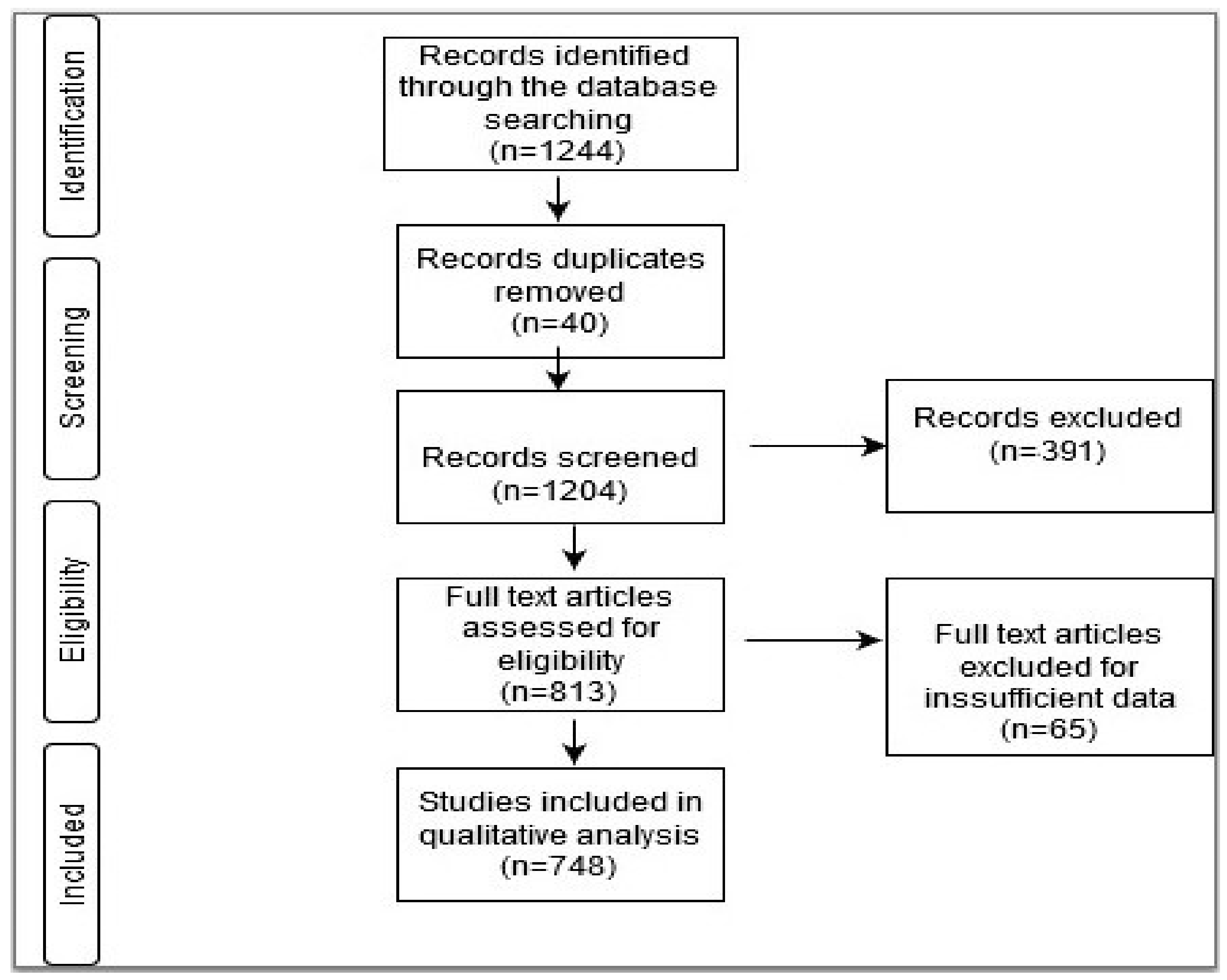
2.5. Prisma Methodology
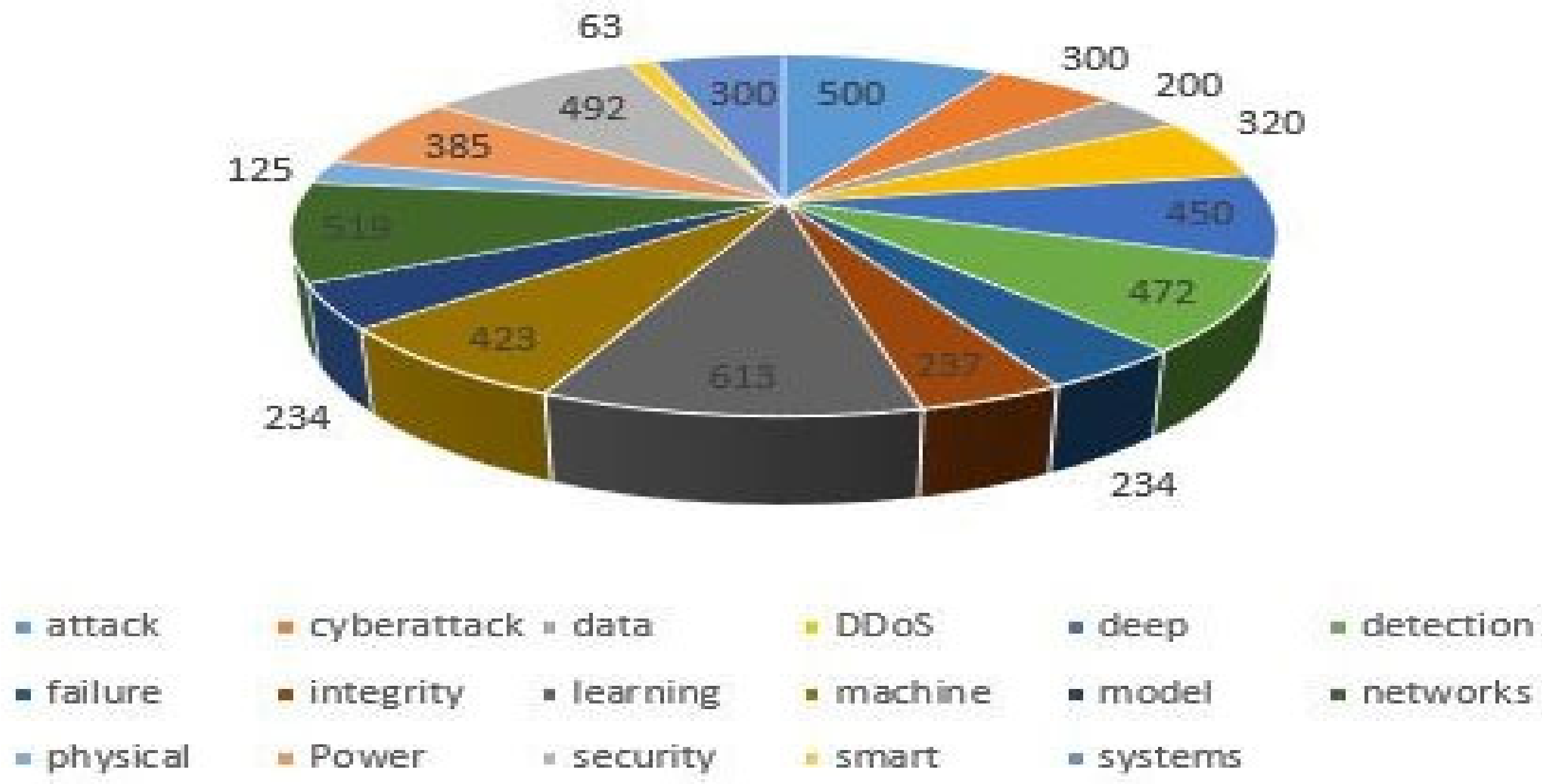
2.6. Text Mining
3. Methods
- “Cybersecurity” AND “Attacks” AND “Trends”;
- “Cybersecurity” AND “Trends” AND “Challenges”.
| Algorithm 1 Pseudo-code of R script to word cloud process |
| wordcloud ⇐ function(group, df) print(group) wordcloud(words = dftoken, freq = dffrequency max.words = 400, random.order = FALSE, rot.per = 0.35, color = brewer.pal(8,”Dark2”)) |
- Physical security, two-way authentication, security protocol, and privacy;
- Security medical devices and legacy software.
- Hardware failure;
- Software failure;
- Data encryption;
- Loss of backup power;
- Accidental user error;
- External security breach;
- Physical security;
- Accidental user error;
- External security breach.
- Mobile devices;
- Embedded systems;
- Consumer technologies;
- Operational systems.
- Energy trading;
- Cryptocurrency, crypto-jacking, money laundering;
- Public organization;
- Decentralized consensus decision-making (DCDM);
- Fuzzy static Bayesian game model (FSB-GM);
- Internet of Things, smart contracts;
- Electronic health records.
- Malicious web pages;
- Malicious Mobil Apps;
- Malicious Emails messages;
- Misinformation and fake news;
- Security and privacy.
- Security intelligence systems;
- Perimeter controls;
- Encryption technologies;
- Data loss prevention;
- Governance risk;
- Automated policy management.
- Software-based defense approaches;
- User education.
- The heterogeneity of IoT solutions;
- The expansion of the attack surface by IoT and Machine Learning;
- Attacks on Cloud infrastructures;
- Cognitive hacking.
- Deep learning;
- Deep reinforcement learning;
- Deep transfer learning.
- Deep learning;
- Machine learning;
- Deep Convolutional Neural Network (CNN);
- Genetic algorithms;
- Game theory;
- PCA;
- Large-Scale System (LSS.)
- Deep learning for word embedding;
- Natural language processing and sentiment analysis on online social networks.
4. Results and Discussion
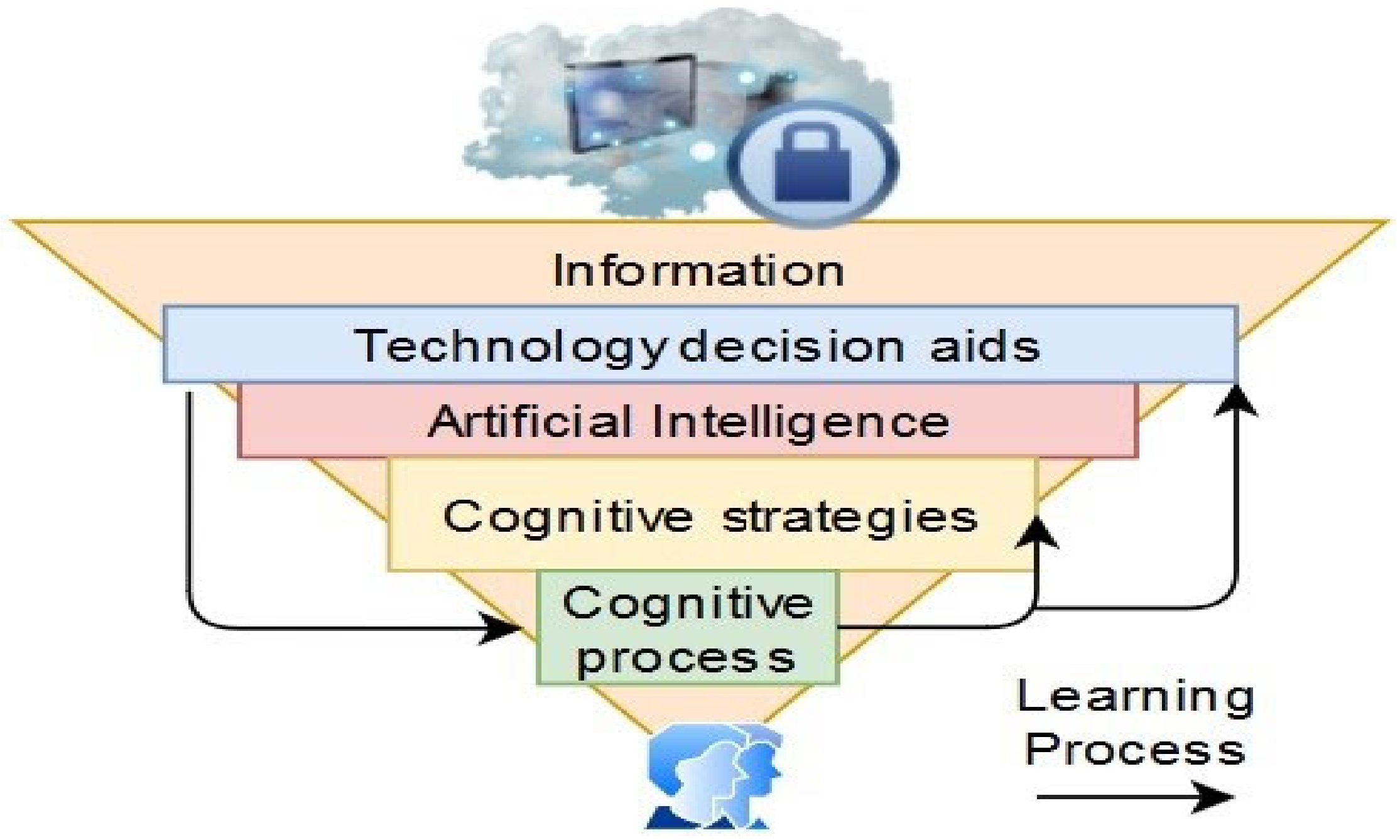
Cognitive Cybersecurity Model
- OSSEC is an open-source HIDS for data gathering;
- Snort is an intrusion Prevention System (IPS) to detect malicious network activity;
- Suricata is an open-source system for real-time intrusion detection (IDS) and intrusion prevention (IPS);
- Security Onion is open-source used for threat hunting, security monitoring, and log management;
- OpenWIPS-NG is an intrusion prevention system (IPS), preferred for wireless packet tracking;
- Fail2ban is a software that scans log files and bans IPs that show malicious activity. Procedures used for adversaries could be based on Command and Control (C2) frameworks. Following, we list some C2 frameworks:
- ▪
- FudgeC2 is a campaign-orientated Powershell C2;
- ▪
- Callidus is an open-source C2 framework that leverages Outlook, OneNote, Microsoft Teams for command and control;
- ▪
- APfell is a cross-platform, OPSEC aware, red teaming, post-exploitation C2 framework;
- ▪
- DaaC2: is an open-source C2 framework that makes use of Discord as a C2;
- ▪
- Koadic is an open-source for post-exploitation;
- ▪
- TrevorC2 is a client/server model for masking command and control through web browsers
5. Discussion
- Security intelligence systems;
- Perimeter controls;
- Encryption technologies;
- Data loss prevention;
- Governance risk;
- Automated policy management.
- Malicious web pages;
- Malicious Mobile Apps;
- Malicious Email messages;
- Misinformation and fake news;
- Security and privacy.
- Implementation of infrastructure for handling a large volume of data;
- Incorporation of cognitive sciences in security strategies such as artificial intelligence, machine learning, data analytics, and psychology;
- Cognitive model design based on:
- Cognitive processes Observe–Orient–Decide–Act model (OODA);
- the Monitor–Analyze–Plan–Execute model (MAPE-K).
- Identification of cognitive processes:
- Users’ or analysts’ cognitive processes;
- The adversary’s behavioral characteristics.
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- WEF: Word Economic Forum. The Global Risks Report 2021. Available online: https://www.weforum.org/reports/the-global-risks-report-2021 (accessed on 21 May 2021).
- Donevski, M.; Zia, T. A survey of anomaly and automation from a cybersecurity perspective. In Proceedings of the 2018 IEEE Globecom Workshops (GC Wkshps), Abu Dhabi, United Arab Emirates, 9–13 December 2018; pp. 1–6. [Google Scholar] [CrossRef]
- Yang, Q.; Jia, X.; Li, X.; Feng, J.; Li, W.; Lee, J. Evaluating Feature Selection and Anomaly Detection Methods of Hard Drive Failure Prediction. IEEE Trans. Reliab. 2020, 70, 749–760. [Google Scholar] [CrossRef]
- Alrashdi, I.; Alqazzaz, A.; Aloufi, E.; Alharthi, R.; Zohdy, M.; Ming, H. AD-IoT: Anomaly Detection of IoT Cyberattacks in Smart City Using Machine Learning. In Proceedings of the IEEE 9th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 7–9 January 2019; pp. 0305–0310. [Google Scholar] [CrossRef]
- Andrade, R.; Torres, J. Self-awareness as an enabler of cognitive security. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 701–708. [Google Scholar] [CrossRef]
- Leung, H. An integrated decision support system based on the human ooda loop. In Proceedings of the 2018 IEEE 17th International Conference on Cognitive Informatics Cognitive Computing (ICCI*CC), Berkeley, CA, USA, 16–18 July 2018; p. 1. [Google Scholar] [CrossRef]
- Shaukat, K.; Luo, S.; Varadharajan, V.; Hameed, I.A.; Xu, M. A Survey on Machine Learning Techniques for Cyber Security in the Last Decade. IEEE Access 2020, 8, 222310–222354. [Google Scholar] [CrossRef]
- Brückner, M.; Scheffer, T. Stackelberg games for adversarial prediction problems. In Proceedings of the 17th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, New York, NY, USA, 21–24 August 2011; pp. 547–555. [Google Scholar] [CrossRef] [Green Version]
- Andrade, R.; Torres, J. Enhancing intelligence soc with big data tools. In Proceedings of the 2018 IEEE 9th Annual Information Technology, Electronics and Mobile Communication Conference (IEMCON), Vancouver, BC, Canada, 1–3 November 2018; pp. 1076–1080. [Google Scholar] [CrossRef]
- Le, D.C.; Zincir-Heywood, N. Exploring adversarial properties of insider threat detection. In Proceedings of the 2020 IEEE Conference on Communications and Network Security (CNS), Avignon, France, 29 June–1 July 2020; pp. 1–9. [Google Scholar] [CrossRef]
- Rajivan, P.; Gonzalez, C. Creative Persuasion: A Study on Adversarial Behaviors and Strategies in Phishing Attacks. Front. Psychol. 2018, 9, 135. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Andrade, R.; Yoo, S.G. Cognitive security: A comprehensive study of cognitive science in cybersecurity. J. Inf. Secur. Appl. 2019, 48, 102352. [Google Scholar] [CrossRef]
- Alqahtani, H.; Kavakli-Thorne, M. Exploring factors affecting user’s cybersecurity behaviour by using mobile augmented reality app (cybar). In Proceedings of the 2020 12th International Conference on Computer and Automation Engineering. ICCAE, Sydney, NSW, Australia, 14–16 February 2020; Association for Computing Machinery: New York, NY, USA; pp. 129–135. [CrossRef]
- Kakkad, V.; Shah, H.; Patel, R.; Doshi, N. A Comparative study of applications of Game Theory in Cyber Security and Cloud Computing. Procedia Comput. Sci. 2019, 155, 680–685. [Google Scholar] [CrossRef]
- Andrade, R.O.; Ortiz-Garces, I.; Cazares, M. Cybersecurity attacks on smart home during covid-19 pandemic. In Proceedings of the Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2021; pp. 398–404. [Google Scholar] [CrossRef]
- Orunsolu, A.; Sodiya, A.; Akinwale, A. A predictive model for phishing detection. J. King Saud Univ. Comput. Inf. Sci. 2022, 34, 232–247. [Google Scholar] [CrossRef]
- Schubert, A.-L.; Frischkorn, G.T.; Hagemann, D.; Voss, A. Trait Characteristics of Diffusion Model Parameters. J. Intell. 2016, 4, 7. [Google Scholar] [CrossRef] [Green Version]
- Simmons, C.; Ellis, C.; Shiva, S.; Dasgupta, D.; Wu, C. Avoidit: A cyber attack taxonomy. In Proceedings of the 9th Annual Symposium on Information Assurance (ASIA’14), Albany, NY, USA, 3–4 June 2014. [Google Scholar]
- Venkatesan, S.; Sugrim, S.; Izmailov, R.; Chiang, C.J.; Chadha, R.; Doshi, B.; Hoffman, B.; Allison Newcomb, E.; Buchler, N. On detecting manifestation of adversary characteristics. In Proceedings of the MILCOM 2018—2018 IEEE Military Communications Conference (MILCOM), Los Angeles, CA, USA, 29–31 October 2018; pp. 431–437. [Google Scholar] [CrossRef]
- Andrade, R.O.; Yoo, S.G.; Tello-Oquendo, L.; Ortiz-Garces, I. A Comprehensive Study of the IoT Cybersecurity in Smart Cities. IEEE Access 2020, 8, 228922–228941. [Google Scholar] [CrossRef]
- Zambrano, P.; Torres, J.; Tello-Oquendo, L.; Jacome, R.; Benalcazar, M.E.; Andrade, R.; Fuertes, W. Technical Mapping of the Grooming Anatomy Using Machine Learning Paradigms: An Information Security Approach. IEEE Access 2019, 7, 142129–142146. [Google Scholar] [CrossRef]
- Lebiere, C.; Morrison, D.; Abdelzaher, T.; Hu, S.; Gonzalez, C.; Buchler, N.; Veksler, V. Cognitive models of prediction as decision aids. In Proceedings of the 14th International Conference on Cognitive Modeling, University Park, PA, USA, 4–6 August 2016. [Google Scholar]
- Cassenti, D.; Veksler, V. Using cognitive modeling for adaptive automation triggering. In Proceedings of the AHFE 2017 International Conference on Human Factors in Simulation and Modeling, Los Angeles, CA, USA, 17–21 July 2017; pp. 378–390. [Google Scholar] [CrossRef]
- Cameron, L.; Jago, L. Cognitive Strategies; Springer: New York, NY, USA, 2013; p. 453. [Google Scholar] [CrossRef]
- Mengist, W.; Soromessa, T.; Legese, G. Method for conducting systematic literature review and meta-analysis for environmental science research. MethodsX 2019, 7, 100777. [Google Scholar] [CrossRef]
- Andrade, R.O.; Yoo, S.G. A Comprehensive Study of the Use of LoRa in the Development of Smart Cities. Appl. Sci. 2019, 9, 4753. [Google Scholar] [CrossRef] [Green Version]
- Antons, D.; Grünwald, E.; Cichy, P.; Salge, T.O. The application of text mining methods in innovation research: Current state, evolution patterns, and development priorities. R&D Manag. 2020, 50, 329–351. [Google Scholar] [CrossRef] [Green Version]
- Lee, C.; Cheng, C.; Zeleke, A. Can text mining technique be used as an alternative tool for qualitative research in education? In Proceedings of the 15th IEEE/ACIS International Conference on Software Engineering, Artificial Intelligence, Networking and Parallel/Distributed Computing (SNPD), Las Vegas, NV, USA, 30 June–2 July 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Ceron, J.C.A.; Gomez, L.J.P.; Ceballos, H.G.; Cantu-Ortiz, F.J. Twitter data analysis on the topic: Tec de monterrey. In Proceedings of the 2020 3rd International Conference on Computer Applications Information Security (ICCAIS), Riyadh, Saudi Arabia, 19–21 March 2020; pp. 1–6. [Google Scholar] [CrossRef]
- USDJ. New York Man Pleads Guilty to Cyberstalking after Harassing and Sextorting Multiple Victims. 2021. Available online: https://www.justice.gov/usao-mdfl/pr/new-york-man-pleads-guilty-cyberstalking-after-harassing-and-sextorting-multiple (accessed on 25 May 2021).
- CISA. Ransomware Activity Targeting the Healthcare and Public Health Sector. 2021. Available online: https://us-cert.cisa.gov/ncas/alerts/aa20–302a (accessed on 25 May 2021).
- FBI. Fraudsters Prey on Emotions and Bank Accounts in Money Mule Schemes. 2021. Available online: https://www.fbi.gov/contact-us/field-offices/elpaso/news/press-releases/fraudsters-prey-on-emotions-and-bank-accounts-in-money-mule-schemes (accessed on 25 May 2021).
- Al-Mohannadi, H.; Mirza, Q.; Namanya, A.; Awan, I.; Cullen, A.; Disso, J. Cyber-attack modeling analysis techniques: An overview. In Proceedings of the 2016 IEEE 4th International Conference on Future Internet of Things and Cloud Workshops (FiCloudW), Vienna, Austria, 22–24 August 2016; pp. 69–76. [Google Scholar] [CrossRef] [Green Version]
- ENISA. Threat Landscape. 2020. Available online: https://www.enisa.europa.eu/topics/threat-risk-management/threats-and-trends (accessed on 12 February 2021).
- Singh, C. Meenu: Phishing website detection based on machine learning: A survey. In Proceedings of the 2020 6th International Conference on Advanced Computing and Communication Systems (ICACCS), Coimbatore, India, 6–7 March 2020; pp. 398–404. [Google Scholar] [CrossRef]
- Athulya, A.; Praveen, K. Towards the detection of phishing attacks. In Proceedings of the 2020 4th International Conference on Trends in Electronics and Informatics (ICOEI) (48184), Tirunelveli, India, 15–17 June 2020; pp. 337–343. [Google Scholar] [CrossRef]
- Chapla, H.; Kotak, R.; Joiser, M. A machine learning approach for url based web phishing using fuzzy logic as classifier. In Proceedings of the 2019 International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 17–19 July 2019; pp. 383–388. [Google Scholar] [CrossRef]
- Zubair Hasan, K.M.; Hasan, M.Z.; Zahan, N. Automated prediction of phishing websites using deep convolutional neural network. In Proceedings of the 2019 International Conference on Computer, Communication, Chemical, Materials and Electronic Engineering (IC4ME2), Rajshahi, Bangladesh, 11–12 July 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Kunju, M.V.; Dainel, E.; Anthony, H.C.; Bhelwa, S. Evaluation of phishing techniques based on machine learning. In Proceedings of the 2019 International Conference on Intelligent Computing and Control Systems (ICCS), Madurai, India, 15–17 May 2019; pp. 963–968. [Google Scholar] [CrossRef]
- Zheng, K.; Wu, T.; Wang, X.; Wu, B.; Wu, C. A Session and Dialogue-Based Social Engineering Framework. IEEE Access 2019, 7, 67781–67794. [Google Scholar] [CrossRef]
- Joshi, C.; Aliaga, J.R.; Insua, D.R. Insider Threat Modeling: An Adversarial Risk Analysis Approach. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1131–1142. [Google Scholar] [CrossRef]
- Duncan, A.; Creese, S.; Goldsmith, M. A combined attack-tree and kill-chain approach to designing attack-detection strategies for malicious insiders in cloud computing. In Proceedings of the 2019 International Conference on Cyber Security and Protection of Digital Services (Cyber Security), Oxford, UK, 3–4 June 2019; pp. 1–9. [Google Scholar] [CrossRef]
- Khan, A.Y.; Latif, R.; Latif, S.; Tahir, S.; Batool, G.; Saba, T. Malicious Insider Attack Detection in IoTs Using Data Analytics. IEEE Access 2019, 8, 11743–11753. [Google Scholar] [CrossRef]
- Alshamrani, A.; Myneni, S.; Chowdhary, A.; Huang, D. A Survey on Advanced Persistent Threats: Techniques, Solutions, Challenges, and Research Opportunities. IEEE Commun. Surv. Tutor. 2019, 21, 1851–1877. [Google Scholar] [CrossRef]
- Su, Y. Research on apt attack based on game model. In Proceedings of the 2020 IEEE 4th Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chongqing, China, 12–14 June 2020; Volume 1, pp. 295–299. [Google Scholar] [CrossRef]
- Khosravi, M.; Ladani, B.T. Alerts Correlation and Causal Analysis for APT Based Cyber Attack Detection. IEEE Access 2020, 8, 162642–162656. [Google Scholar] [CrossRef]
- Sajal, S.Z.; Jahan, I.; Nygard, K.E. A survey on cyber security threats and challenges in modem society. In Proceedings of the 2019 IEEE International Conference on Electro Information Technology (EIT), Brookings, SD, USA, 20–22 May 2019; pp. 525–528. [Google Scholar] [CrossRef]
- Park, J.; Cho, D.; Lee, J.K.; Lee, B. The Economics of Cybercrime. ACM Trans. Manag. Inf. Syst. 2019, 10, 1–23. [Google Scholar] [CrossRef]
- Cao, M.; Badihi, S.; Ahmed, K.; Xiong, P.; Rubin, J. On benign features in malware detection. In Proceedings of the 35th IEEE/ACM International Conference on Automated Software Engineering ASE’20, Virtual Event, Australia, 21–25 December 2020; Association for Computing Machinery: New York, NY, USA; pp. 1234–1238. [Google Scholar] [CrossRef]
- Samantray, O.P.; Tripathy, S.N.; Das, S.K. A study to understand malware behavior through malware analysis. In Proceedings of the 2019 IEEE International Conference on System, Computation, Automation and Networking (ICSCAN), Pondicherry, India, 29–30 March 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A survey of DDoS attacking techniques and defence mechanisms in the IoT network. Telecommun. Syst. 2019, 73, 3–25. [Google Scholar] [CrossRef]
- Liang, X.; Znati, T. An empirical study of intelligent approaches to ddos detection in large scale networks. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 821–827. [Google Scholar] [CrossRef]
- Priya, S.S.; Sivaram, M.; Yuvaraj, D.; Jayanthiladevi, A. Machine learning based ddos detection. In Proceedings of the 2020 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 12–14 March 2020; pp. 234–237. [Google Scholar] [CrossRef]
- Nandi, S.; Phadikar, S.; Majumder, K. Detection of ddos attack and classification using a hybrid approach. In Proceedings of the 2020 Third ISEA Conference on Security and Privacy (ISEA-ISAP), Guwahati, India, 27 February–1 March 2020; pp. 41–47. [Google Scholar] [CrossRef]
- Rohit, M.H.; Fahim, S.M.; Khan, A.H.A. Mitigating and detecting ddos attack on iot environment. In Proceedings of the 2019 IEEE International Conference on Robotics, Automation, Artificial-intelligence and Internet-of-Things (RAAICON), Dhaka, Bangladesh, 29 November–1 December 2019; pp. 5–8. [Google Scholar] [CrossRef]
- Agrawal, N.; Tapaswi, S. Defense Mechanisms Against DDoS Attacks in a Cloud Computing Environment: State-of-the-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2019, 21, 3769–3795. [Google Scholar] [CrossRef]
- Bijitha, C.V.; Sukumaran, R.; Nath, H.V. A survey on ransomware detection techniques. In Secure Knowledge Management in Artificial Intelligence Era; Sahay, S.K., Goel, N., Patil, V., Jadliwala, M., Eds.; Springer: Singapore, 2020; pp. 55–68. [Google Scholar]
- Alzahrani, A.; Alshahrani, H.; Alshehri, A.; Fu, H. An intelligent behavior-based ransomware detection system for android platform. In Proceedings of the 2019 First IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (TPS-ISA), Los Angeles, CA, USA, 12–14 December 2019; pp. 28–35. [Google Scholar] [CrossRef]
- Adamov, A.; Carlsson, A. Reinforcement learning for anti-ransomware testing. In Proceedings of the 2020 IEEE East-West Design Test Symposium (EWDTS), Varna, Bulgaria, 4–7 September 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Bahrani, A.; Bidgly, A.J. Ransomware detection using process mining and classification algorithms. In Proceedings of the 2019 16th International ISC (Iranian Society of Cryptology) Conference on Information Security and Cryptology (ISCISC), Mashhad, Iran, 28–29 August 2019; pp. 73–77. [Google Scholar] [CrossRef]
- Shahpasand, M.; Hamey, L.; Vatsalan, D.; Xue, M. Adversarial attacks on mobile malware detection. In Proceedings of the 2019 IEEE 1st International Workshop on Artificial Intelligence for Mobile (AI4Mobile), Hangzhou, China, 24 February 2019; pp. 17–20. [Google Scholar] [CrossRef]
- Tahtaci, B.; Canbay, B. Android malware detection using machine learning. In Proceedings of the 2020 Innovations in Intelligent Systems and Applications Conference (ASYU), Istanbul, Turkey, 15–17 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Mbaziira, A.V.; Diaz-Gonzales, J.; Liu, M. Deep learning in detection of mobile malware. J. Comput. Sci. Coll. 2020, 36, 80–88. [Google Scholar]
- Diaz-Gonzalez, J.; Mbaziira, A.V.; Liu, M. An exploratory deep learning approach to mobile malware detection. J. Comput. Sci. Coll. 2019, 35, 219. [Google Scholar]
- Allen, J.; Yang, Z.; Landen, M.; Bhat, R.; Grover, H.; Chang, A.; Ji, Y.; Perdisci, R.; Lee, W. Mnemosyne: An effective and efficient postmortem watering hole attack investigation system. In Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security, CCS’20, Virtual Event, USA, 9–13 November 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 787–802. [Google Scholar] [CrossRef]
- Research CP. CYBER ATTACK TRENDS: 2020 MID-YEAR REPORT—Check Point Research. 2021. Available online: https://research.checkpoint.com/2020/cyber-attack-trends-2020-mid-year-report/ (accessed on 21 May 2021).
- Dasgupta, D.; Akhtar, Z.; Sen, S. Machine learning in cybersecurity: A comprehensive survey. J. Déf. Model. Simul. Appl. Methodol. Technol. 2020, 19, 57–106. [Google Scholar] [CrossRef]
- Brewer, J.N.; Dimitoglou, G. Evaluation of attack vectors and risks in automobiles and road infrastructure. In Proceedings of the 2019 International Conference on Computational Science and Computational Intelligence (CSCI), Las Vegas, NV, USA, 5–7 December 2019; pp. 84–89. [Google Scholar] [CrossRef]
- Li, T.; Wang, K.; Horkoff, J. Towards effective assessment for social engineering attacks. In Proceedings of the 2019 IEEE 27th International Requirements Engineering Conference (RE), Jeju, Korea, 23–27 September 2019; pp. 392–397. [Google Scholar] [CrossRef]
- Tandale, K.D.; Pawar, S.N. Different types of phishing attacks and detection techniques: A review. In Proceedings of the 2020 International Conference on Smart Innovations in Design, Environment, Management, Planning and Computing (ICSIDEMPC), Aurangabad, India, 30–31 October 2020; pp. 295–299. [Google Scholar] [CrossRef]
- Badami, C.; Kettani, H. On Malware Detection in the Android Operating System. In Proceedings of the 4th International Conference on Algorithms, Computing and Systems, Rabat, Morocco, 6–8 January 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 45–50. [Google Scholar] [CrossRef]
- George, R.; Jalal, R.; Raju, R.M.; Sunny, S.S.; Hari, M. High responsive plug-in for malicious url detection. In Proceedings of the 2019 3rd International Conference on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, 23–25 April 2019; pp. 357–359. [Google Scholar] [CrossRef]
- Song, X.; Chen, C.; Cui, B.; Fu, J. Malicious JavaScript Detection Based on Bidirectional LSTM Model. Appl. Sci. 2020, 10, 3440. [Google Scholar] [CrossRef]
- Dogaru, D.I.; Dumitrache, I. Cyber security of smart grids in the context of big data and machine learning. In Proceedings of the 2019 22nd International Conference on Control Systems and Computer Science (CSCS), Bucharest, Romania, 28–30 May 2019; pp. 61–67. [Google Scholar] [CrossRef]
- Spanakis, E.G.; Bonomi, S.; Sfakianakis, S.; Santucci, G.; Lenti, S.; Sorella, M.; Tanasache, F.D.; Palleschi, A.; Ciccotelli, C.; Sakkalis, V.; et al. Cyber-attacks and threats for healthcare—A multi-layer thread analysis. In Proceedings of the 2020 42nd Annual International Conference of the IEEE Engineering in Medicine Biology Society (EMBC), Montreal, QC, Canada, 20–24 July 2020; pp. 5705–5708. [Google Scholar] [CrossRef]
- Pilz, M.; Naeini, F.B.; Grammont, K.; Smagghe, C.; Davis, M.; Nebel, J.-C.; Al-Fagih, L.; Pfluegel, E. Security attacks on smart grid scheduling and their defences: A game-theoretic approach. Int. J. Inf. Secur. 2019, 19, 427–443. [Google Scholar] [CrossRef] [Green Version]
- Canaan, B.; Colicchio, B.; Abdeslam, D.O. Microgrid Cyber-Security: Review and Challenges toward Resilience. Appl. Sci. 2020, 10, 5649. [Google Scholar] [CrossRef]
- Tervoort, T.; De Oliveira, M.T.; Pieters, W.; Van Gelder, P.; Olabarriaga, S.D.; Marquering, H. Solutions for Mitigating Cybersecurity Risks Caused by Legacy Software in Medical Devices: A Scoping Review. IEEE Access 2020, 8, 84352–84361. [Google Scholar] [CrossRef]
- Fatima, K.; Nawaz, S.; Mehrban, S. Biometric authentication in health care sector: A survey. In Proceedings of the 2019 International Conference on Innovative Computing (ICIC), Lahore, Pakistan, 1–2 November 2019; pp. 1–10. [Google Scholar] [CrossRef]
- Kazemi, Z.; Fazeli, M.; Hely, D.; Beroulle, V. Hardware security vulnerability assessment to identify the potential risks in a critical embedded application. In Proceedings of the 2020 IEEE 26th International Symposium on On-Line Testing and Robust System Design (IOLTS), Napoli, Italy, 13–15 July 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Kotenko, I.; Saenko, I.; Kushnerevich, A.; Branitskiy, A. Attack detection in iot critical infrastructures: A machine learning and big data processing approach. In Proceedings of the 2019 27th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Pavia, Italy, 13–15 February 2019; pp. 340–347. [Google Scholar] [CrossRef]
- Sen, S.; Jayawardena, C. Analysis of cyber-attack in big data iot and cyber-physical systems—A technical approach to cybersecurity modeling. In Proceedings of the 2019 IEEE 5th International Conference for Convergence in Technology (I2CT), Bombay, India, 29–31 March 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Gressl, L.; Steger, C.; Neffe, U. Consideration of security attacks in the design space exploration of embedded systems. In Proceedings of the 2019 22nd Euromicro Conference on Digital System Design (DSD), Kallithea, Greece, 28–30 August 2019; pp. 530–537. [Google Scholar] [CrossRef]
- Chauhan, V.; Arora, G. A review paper on cryptocurrency portfolio management. In Proceedings of the 2019 2nd International Conference on Power Energy, Environment and Intelligent Control (PEEIC), Greater Noida, India, 18–19 October 2019; pp. 60–62. [Google Scholar] [CrossRef]
- Shahnaz, A.; Qamar, U.; Khalid, A. Using Blockchain for Electronic Health Records. IEEE Access 2019, 7, 147782–147795. [Google Scholar] [CrossRef]
- Gong, X.; Liu, E.; Wang, R. Blockchain-based iot application using smart contracts: Case study of m2m autonomous trading. In Proceedings of the 2020 5th International Conference on Computer and Communication Systems (ICCCS), Shanghai, China, 15–18 May 2020; pp. 781–785. [Google Scholar] [CrossRef]
- Chen, Y.-W.; Sheu, J.-P.; Kuo, Y.-C.; Van Cuong, N. Design and implementation of iot ddos attacks detection system based on machine learning. In Proceedings of the 2020 European Conference on Networks and Communications (EuCNC), Dubrovnik, Croatia, 15–18 June 2020; pp. 122–127. [Google Scholar] [CrossRef]
- Ahmed, Z.; Danish, S.M.; Qureshi, H.K.; Lestas, M. Protecting iots from mirai botnet attacks using blockchains. In Proceedings of the 2019 IEEE 24th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Limassol, Cyprus, 11–13 September 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Sambangi, S.; Gondi, L. A machine learning approach for ddos (distributed denial of service) attack detection using multiple linear regression. Proceedings 2020, 63, 51. [Google Scholar]
- Sai, A.M.V.V.; Li, Y. A Survey on Privacy Issues in Mobile Social Networks. IEEE Access 2020, 8, 130906–130921. [Google Scholar] [CrossRef]
- Hijji, M.; Alam, G. A Multivocal Literature Review on Growing Social Engineering Based Cyber-Attacks/Threats During the COVID-19 Pandemic: Challenges and Prospective Solutions. IEEE Access 2021, 9, 7152–7169. [Google Scholar] [CrossRef] [PubMed]
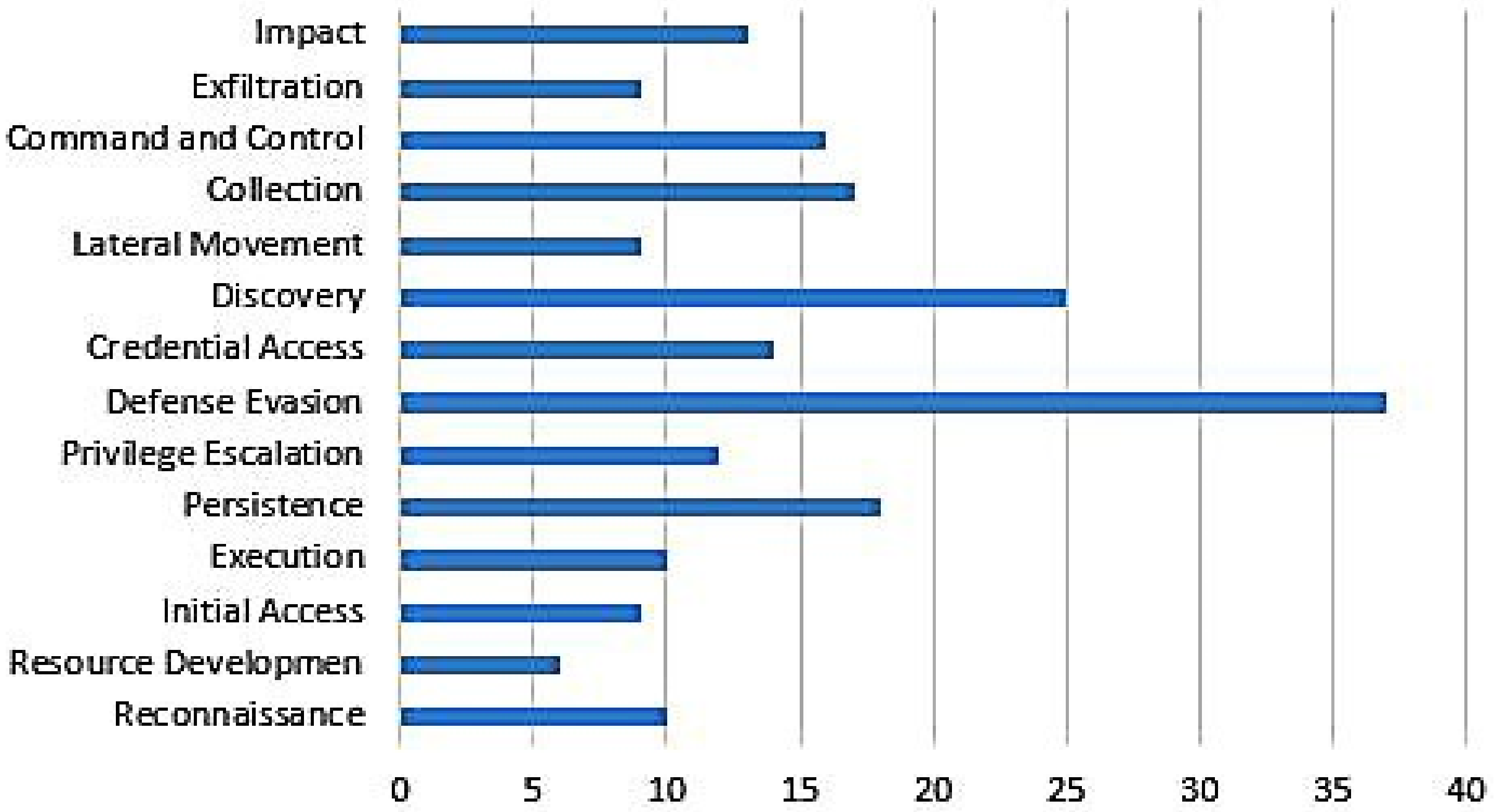
- MITRE. Enterprise Attacks Techniques MITRE. 2021. Available online: https://attack.mitre.org/techniques/enterprise/ (accessed on 25 May 2021).
- Wankhede, S.B. Anomaly detection using machine learning techniques. In Proceedings of the 2019 IEEE 5th International Conference for Convergence in Technology (I2CT), Bombay, India, 29–31 March 2019; pp. 1–3. [Google Scholar] [CrossRef]
- Wollaber, A.; Peñna, J.; Blease, B.; Shing, L.; Alperin, K.; Vilvovsky, S.; Trepagnier, P.; Wagner, N.; Leonard, L. Proactive cyber situation awareness via high performance computing. In Proceedings of the 2019 IEEE High Performance Extreme Computing Conference (HPEC), Waltham, MA, USA, 24–26 September 2019; pp. 1–7. [Google Scholar] [CrossRef]
- Iqbal, A.; Gunn, L.J.; Guo, M.; Babar, M.A.; Abbott, D. Game Theoretical Modelling of Network/Cybersecurity. IEEE Access 2019, 7, 154167–154179. [Google Scholar] [CrossRef]
- Zhou, X.; Cheng, S.; Liu, Y. A Cooperative Game Theory-Based Algorithm for Overlapping Community Detection. IEEE Access 2020, 8, 68417–68425. [Google Scholar] [CrossRef]
- Kwiatkowska, M.; Norman, G.; Parker, D.; Santos, G. Prism-games 3.0: Stochastic game verification with concurrency, equilibria and time. In Computer Aided Verification; Lahiri, S.K., Wang, C., Eds.; Springer: Cham, Switzerland, 2020; pp. 475–487. [Google Scholar]
- Bitzer, S.; Park, H.; Blankenburg, F.; Kiebel, S.J. Perceptual decision making: Drift-diffusion model is equivalent to a Bayesian model. Front. Hum. Neurosci. 2014, 8, 102. [Google Scholar] [CrossRef] [Green Version]
- Dale, S. Heuristics and biases: The science of decision-making. Bus. Inf. Rev. 2015, 32, 93–99. [Google Scholar] [CrossRef]
- Nikolić, J. Biases in the decision-making process and possibilities of overcoming them. Èkon. Horiz. 2018, 20, 45–59. [Google Scholar] [CrossRef] [Green Version]
- Trueblood, J.S.; Holmes, W.R.; Seegmiller, A.C.; Douds, J.; Compton, M.; Szentirmai, E.; Woodruff, M.; Huang, W.; Stratton, C.; Eichbaum, Q. The impact of speed and bias on the cognitive processes of experts and novices in medical image decision-making. Cogn. Res. Princ. Implic. 2018, 3, 28. [Google Scholar] [CrossRef]
- Smith, P.; Ratcliff, R. An introduction to the diffusion model of decision making. In An Introduction to Model-Based Cognitive Neuroscience; Springer: New York, NY, USA, 2015; pp. 49–70. [Google Scholar] [CrossRef]
- Nishiguchi, Y.; Sakamoto, J.; Kunisato, Y.; Takano, K. Linear Ballistic Accumulator Modeling of Attentional Bias Modification Revealed Disturbed Evidence Accumulation of Negative Information by Explicit Instruction. Front. Psychol. 2019, 10, 2447. [Google Scholar] [CrossRef] [Green Version]
- Quayyum, F.; Cruzes, D.S.; Jaccheri, L. Cybersecurity awareness for children: A systematic literature review. Int. J. Child Comput. Interact. 2021, 30, 100343. [Google Scholar] [CrossRef]
- Cheung, K.-F.; Bell, M.G.; Bhattacharjya, J. Cybersecurity in logistics and supply chain management: An overview and future research directions. Transp. Res. Part E: Logist. Transp. Rev. 2021, 146, 102217. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Wang, Z.; Zhu, H.; Sun, L. Social Engineering in Cybersecurity: Effect Mechanisms, Human Vulnerabilities and Attack Methods. IEEE Access 2021, 9, 11895–11910. [Google Scholar] [CrossRef]
- Rahman, A.U.; Williams, L. Software Security in DevOps: Synthesizing Practitioners’ Perceptions and Practices. In Proceedings of the 2016 IEEE/ACM International Workshop on Continuous Software Evolution and Delivery (CSED), Austin, TX, USA, 14–15 May 2016; pp. 70–76. [Google Scholar]
- Maglaras, L.; Drivas, G.; Chouliaras, N.; Boiten, E.; Lambrinoudakis, C.; Ioannidis, S. Cybersecurity in the Era of Digital Transformation: The case of Greece. In Proceedings of the 2020 International Conference on Internet of Things and Intelligent Applications (ITIA), Zhenjiang, China, 27–29 November 2020; pp. 1–5. [Google Scholar] [CrossRef]
- Sharma, R.; Dangi, S.; Mishra, P. A Comprehensive Review on Encryption based Open Source Cyber Security Tools. In Proceedings of the 2021 6th International Conference on Signal Processing, Computing and Control (ISPCC), Solan, India, 7–9 October 2021; pp. 614–619. [Google Scholar] [CrossRef]




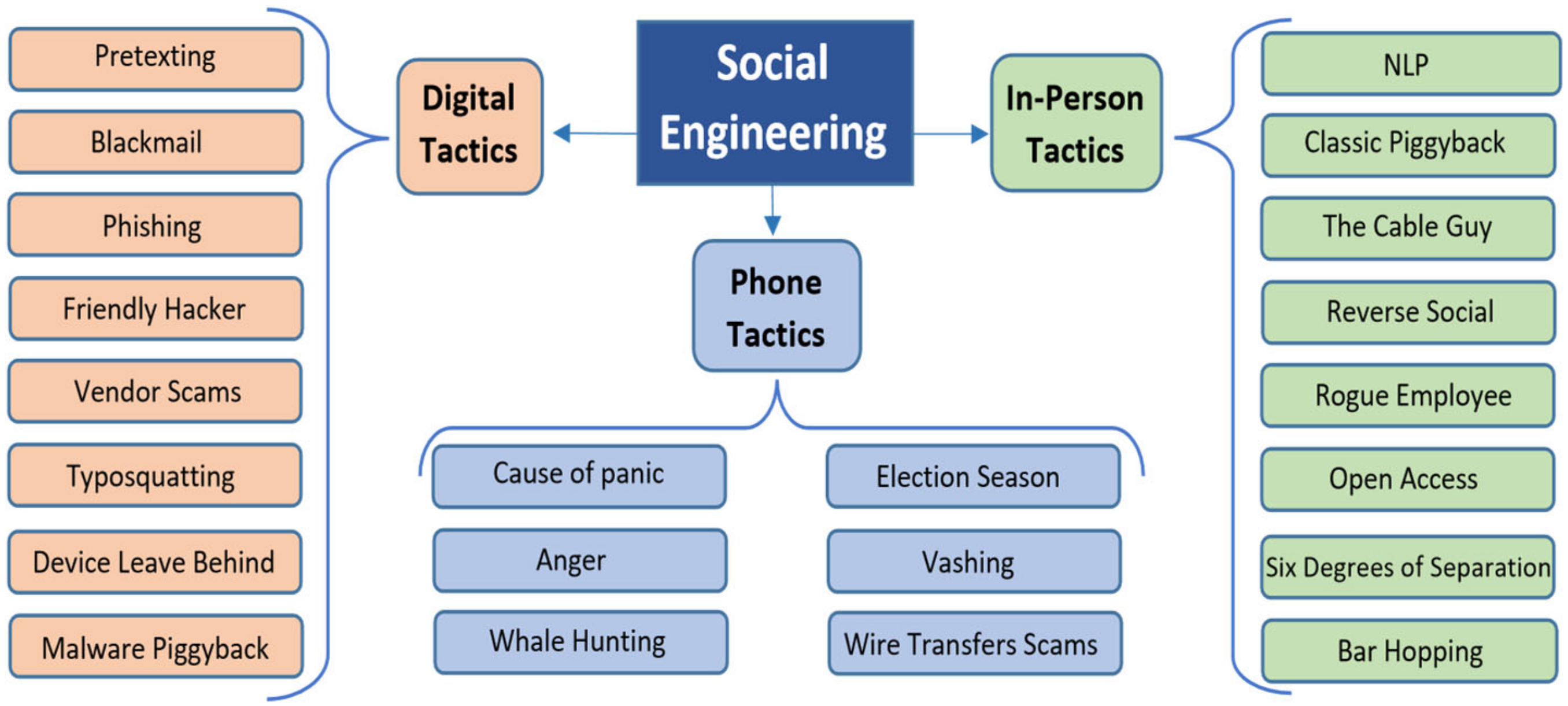


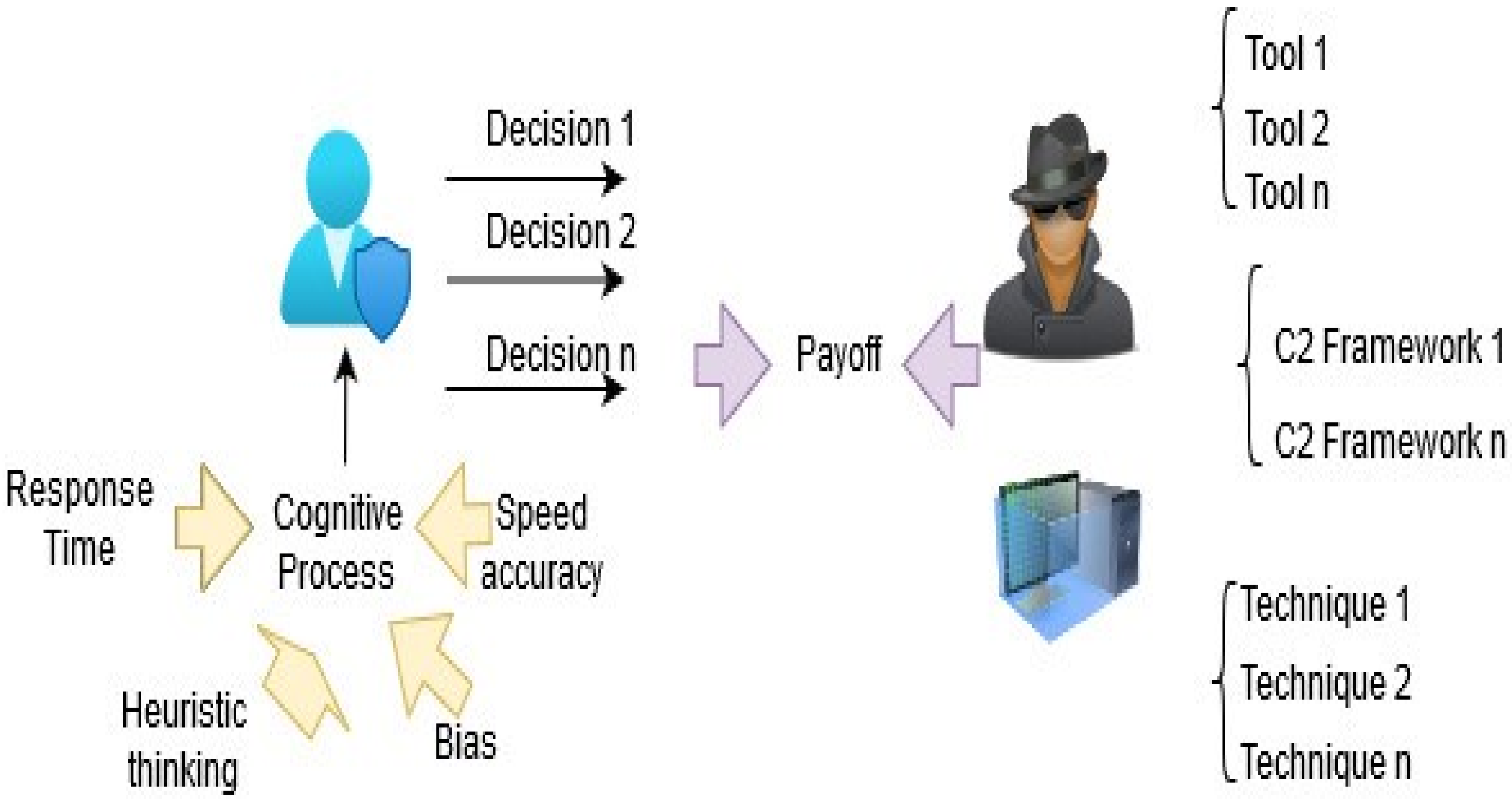
| Role | Techniques | IT Resources | Information |
|---|---|---|---|
| User | Empirical Knowledge | Office or Home Desktop | No information related to the adversaries |
| Organization | Tactics, Techniques, and Procedures (TTP) Ofensive/Defensive approaches | Perimetral security (Firewall, IPS, IDS) Security Event Management (SIEM) | No or low information related to adversaries. Adversaries could use VPN or deep network to hide their information and maintain anonymity. |
| Adversaries | Offensive approaches (hacking, vulnerability scans, deep network) MITRE ATT&CK defines 245 techniques of attacks, distributed in 14 categories. | Vulnerability tools Exploit tools Obfuscation tools Lateral Movement Frameworks Remote access trojans | Data from Social networks (Facebook, Instagram, twitter) Data from personal or enterprise blogs or web pages. Data for deep network. |
| 5G | Cloud Security | Microgrid |
|---|---|---|
| AC microgrids | Data integrity attack (DIA.) | Multistate model |
| Advanced metering | Deep learning | Offensive Security |
| Artificial intelligence (AI.) | Distributed resilient control | Open software |
| Battery pack | DevOps Security | Plug-in electric vehicles |
| Blockchain | Digital transformation | Robust algorithm |
| Call detail record (CDR.) | Event-triggered mechanism | Smart contract |
| Cybersecurity awareness | Energy security | Smart sensor |
| Cyberattacks | False data injection attacks | Smart meters |
| Cyberattack detection | Human Security | Smart City |
| Cyber-physical systems (CPS.) | Internet of Things (IoT) | Software-defined architecture |
| Cyber power network | Machine learning | Supply chain management |
| Type | Description | Reference |
|---|---|---|
| Phishing | Is a malicious and deliberate attempt of sending fake messages that appear to come from a reputable source | [35,36,37,38,39,40] |
| Insider threats | Are encountered in international security, geopolitics, business, trade, and cybersecurity. Insider threats could be considered more damaging than outsider attacks | [41,42,43] |
| APT | Are designed to steal corporate or national secrets. | [44,45,46] |
| Cybercrime | Criminal activity either targets or uses a computer, a computer network, or a networked device. | [47,48] |
| Malware | Malicious software designed to infiltrate a device without knowledge | [49,50] |
| DDoS | Denial of service attack on a computer system or network that causes a service or resource tobe inaccessible to legitimate users | [51,52,53,54,55] |
| Ransomware | A type of malicious program that restricts access to certain parts of files of the infected operating system and demands a ransom in exchange for removing this restriction | [56,57,58,59,60] |
| Mobile malware | Its name suggests malicious software that targets explicitly the operating systems on mobile phones | [61,62,63,64] |
| Watering hole | Refers to a tactic used during targeted attack campaigns where the APT is distributed through a trusted website that is usually visited by employees of the target company or entity | [65,66] |
| Attack | Americas | Europa | Asia |
|---|---|---|---|
| DDoS | 13% | 17% | 23% |
| Ransomware | 3% | 4% | 6% |
| Mobile malware | 15% | 15% | 25% |
| Phishing | 7% | 11% | 14% |
| Type | Human | Machine |
|---|---|---|
| Phishing | X | - |
| Insider threats | X | X |
| Web Based Attacks | - | X |
| Advanced persistent threat (APT) | - | X |
| Spam | X | X |
| Identity theft | X | X |
| Data breach | X | X |
| Botnets | - | X |
| Physical manipulation | X | - |
| Cybercrime | X | X |
| Malware | X | X |
| DDoS | - | X |
| Ransomware | - | X |
| Mobile malware | X | X |
| Watering hole | X | X |
| Information leakage | X | X |
| Services | Description | Reference |
|---|---|---|
| Financial services | Financial institutions are exposed due to their network dependence. Financial services include payment systems or trading platforms. An example of an attacker on financial services is accessing SWIFT credentials to send fraudulent payment orders. | [38] |
| The energy | The energy sector is vulnerable to attacks because they need real-time operations. Cyberattacks can generate failure or breakdown of generation, transmission, distribution, or substation systems | [51] |
| Healthcare | The prime target is the theft of medical information. Cyber-criminals’ medical information is more valuable than personal financial information. Ransomware attacks are growing on medical devices | [52] |
| Energy Systems | Cybersecurity Scope | Applied Mechanism |
|---|---|---|
| Cyber-physical power system (CPPS) | Intrusion detection | Temporal-topological correlation |
| Distribution systems | Anomaly detection | Multi-agent system |
| Electric drive system | Attack pattern | Fuzzy feature analysis |
| Industrial system | Cyberattack monitoring and detection | Frequent pattern tree |
| Smart distribution networks | Situation awareness | State estimation |
| Networked control system | Resilience control | Markov chain |
| Steam turbines | Active defense | k-connected graph |
| Microgrids | Quantization effect | Ruin probability |
| Smart grid | Sequential false data injection attacks | |
| Power outage | ||
| Stealthy attack | ||
| False data injection (FDI) | ||
| Denial-of-service (DoS) |
| The Mechanism Applied Based on | IoT Cybersecurity Context |
|---|---|
| Data analysis | IoT attack classification |
| ANN | Attack–defense trees |
| Graph neural nets | DDoS attacks |
| Cognitive packet network | Botnet |
| Random neural networks | Attack countermeasures |
| Home security threat | |
| Identification anomaly |
| Cybersecurity Context | Scope | Applied Mechanism |
|---|---|---|
| Cyber-physical power system (CPPS) | Behavior pattern | Multiagentsystems (MASs) |
| Internet of Things | Attack pattern | Honeypots |
| Connected and automated vehicles (CAVs) | Anomaly detection | Convolution neural network (CNN) |
| Smart home | Anomaly identification | Dimensionality reduction |
| Intelligent transportation system (ITS) | Attack pattern | Principal component analysis |
| Learning Techniques | Cybersecurity Application Context |
|---|---|
| Decision Tree | Cryptojacking |
| k-nearest neighbors | Internet of things |
| Random Forest | Advanced persistent threat |
| Naive Bayes | Collaborative attacks |
| Recurrent Neural Networks (RNNs) | Traffic flow monitoring |
| Generative adversarial networks | Distributed denial-of-service attacks |
| Deep learning | Malicious javascript detection |
| Deep reinforcement learning | Intruder detection |
| Deep transfer learning |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Andrade, R.O.; Fuertes, W.; Cazares, M.; Ortiz-Garcés, I.; Navas, G. An Exploratory Study of Cognitive Sciences Applied to Cybersecurity. Electronics 2022, 11, 1692. https://doi.org/10.3390/electronics11111692
Andrade RO, Fuertes W, Cazares M, Ortiz-Garcés I, Navas G. An Exploratory Study of Cognitive Sciences Applied to Cybersecurity. Electronics. 2022; 11(11):1692. https://doi.org/10.3390/electronics11111692
Chicago/Turabian StyleAndrade, Roberto O., Walter Fuertes, María Cazares, Iván Ortiz-Garcés, and Gustavo Navas. 2022. "An Exploratory Study of Cognitive Sciences Applied to Cybersecurity" Electronics 11, no. 11: 1692. https://doi.org/10.3390/electronics11111692
APA StyleAndrade, R. O., Fuertes, W., Cazares, M., Ortiz-Garcés, I., & Navas, G. (2022). An Exploratory Study of Cognitive Sciences Applied to Cybersecurity. Electronics, 11(11), 1692. https://doi.org/10.3390/electronics11111692







