IoDM: A Study on a IoT-Based Organizational Deception Modeling with Adaptive General-Sum Game Competition
Abstract
:1. Introduction
1.1. Background of Cyber Deception
1.2. Problem Statement and Related Limitation
- Unconceptualized deception strategies by various IoT domains: Existing defensive deception studies have conceptually formalized some of the operational characteristics and domain scopes of the target topology according to common vul-nerabilities and exploits (CVE) labeling in the national vulnerability database (NVD) for each IoT or non-IoT-based host. Accordingly, the related defense efficiency for each IoT-enabled deception strategy was derived. However, these studies were conducted only within a limited range, focusing on general-purpose fields such as WiFi-based smart home IoT and wireless sensor networks. In other words, it is reported that no systematic defensive deception strategy has been established for special domains such as medical IoT or industrial control systems.
- Unquantified organizational unique characteristics and IoT operation strategies: Previous studies have statically or less dynamically defined attack and defense goals, equilibrium states, decision weights, and state-transition probabilities based on common vulnerability scoring systems (CVSS) for IoT or non-IoT systems when constructing scenarios and deception sequences. Accordingly, the related effectiveness and utility of the defender’s deception based on the vulnerable contact points and attack vectors were calculated. However, the domain definition for the target IoT was limited only based on the related CVE vulnerability of the IoT device belonging to the topology. In addition, interactions between IoT devices, feedback, sequences, transmission/reception processes, and the organization’s unique IoT operation strategy concept were not taken into account.
- Low flexibility and scalability issues of existing deception techniques: The naive MTD of previous studies was constructed to secure proactive defense by concentrating only on avoidance through mobility properties. In addition, it did not conceptually consider the reactive response for each threat that evaded the naive MTD scheme with sophisticated attackers. Other related studies with decoys have also not improved the scalability of the concept of deceptive perturbation by combining decoys with organization-specific characteristics.
- Unconsidered standardization of general sum game-based IoT deception strategies: Most of the defensive deception techniques applied in IoT, especially the strategic studies conducted to improve the defense efficiency by optimizing the MTD, have reached equilibrium states based on a zero-sum game. However, all cyber-attack defenses in the real world cannot be simulated solely on the basis of a zero-sum game. Accordingly, by introducing the concept of general sum game competition, preemptive normalization and optimization of non-zero-sum-based IoT-enabled MTD are also required.
- High dynamicity and real-time concepts that have not been applied: All deceptive disturbances and contingencies within an IoT network with defensive deception affect the organization’s security posture and radically change the attack–defense environment. However, previous studies did not consider these factors and modeled the relationship between defender and attacker sequentially, mainly based on a simple leader and follower. For this reason, the proposed game models do not accurately characterize the real-time performance change of the actual IoT network attack–defense process and do not take into account the noise that can potentially affect the reward in each episode. In addition, even when performing steps to achieve goals for each actor within the game model, it is also impossible to dynamically calculate suboptimal deception strategies against incompletely perceived opponents according to sequential consumption of episodes for equilibrium [41,42].
1.3. Research Goal and Key Contributions
- General sum-based IoT deception strategies can be additionally formulated: From the perspective of macroscopic strategization of defensive deception for IoT security, a general sum game-based competition concepts endowed with PBNE, BSSG, and partial signaling can be formed. That is, to expand the security of real IoT devices, systems, and networks, the concepts of IoT-enabled MTD and decoys optimized for non-zero-sum games that were not reflected in existing zero-sum games can be compared and verified.
- Deception efficiency can be calculated by IoT domain and scenario: Through the topology templates configured for general purposes based on smart home IoT, cyber–physical system IoT, and medical IoT and related general sum game foreground components, real-time attack–defense competitive acts within an IoT organization with limited resources can be simulated and a multi-step spatiotemporal deceptive decision-making process configured. Furthermore, through the POMDP background components, the views not agreed upon between the attackers and the defenders by episode, the attack-exploration surfaces, and the concept of initiative can be also simulated. Moreover, IoT defenders can push disinformation behaviors for certain IoT devices and systems with the possibility of initial intrusion and final occupation according to a pre-calculated indicator of vulnerability (IoV) based on signaling. Furthermore, IoT defenders can dominantly conceptualize the cognition disturbance and social-engineering additionally defined in IoT-enabled MTD and decoys.
- A lightweight independent IoT deception defense concept can be established: When responding to specialized attackers, a concept of defensive deception can operate independently of the interconnected IoT systems without separately considering the deployment and management of dedicated protocols or additional solutions while minimizing resource usage and performance degradation and improving security can be defined based on IoT domains, scenarios, sequences, metrics, and major simulation parameters.
- Following the calculation of deceptive intensity, optimized deception strategies in the IoT domain can be produced: By subdividing functional parameters related to MTD and decoy performance (e.g., mutation target and period, shuffling, sampling scheme, decoy element, decoy properties, decoy path, maximum CKC permissible stage, target points by actor, and quantified main purpose), the most appropriate deception processes can be configured. In addition, an optimization strategy that can respond to the overhead problem and resource allocation issue of the existing IoT deception study cases where the concept of defensive deception was naively applied only for the purpose of simply improving security can be presented.
1.4. Structure of Paper
2. Related Work
2.1. Game-Enabled Defensive Deception Techniques with MTD
2.2. MTD-Based Defensive Deception Techniques for IoT
2.3. Taxonomy Analysis by Previous Studies for Proposed Model
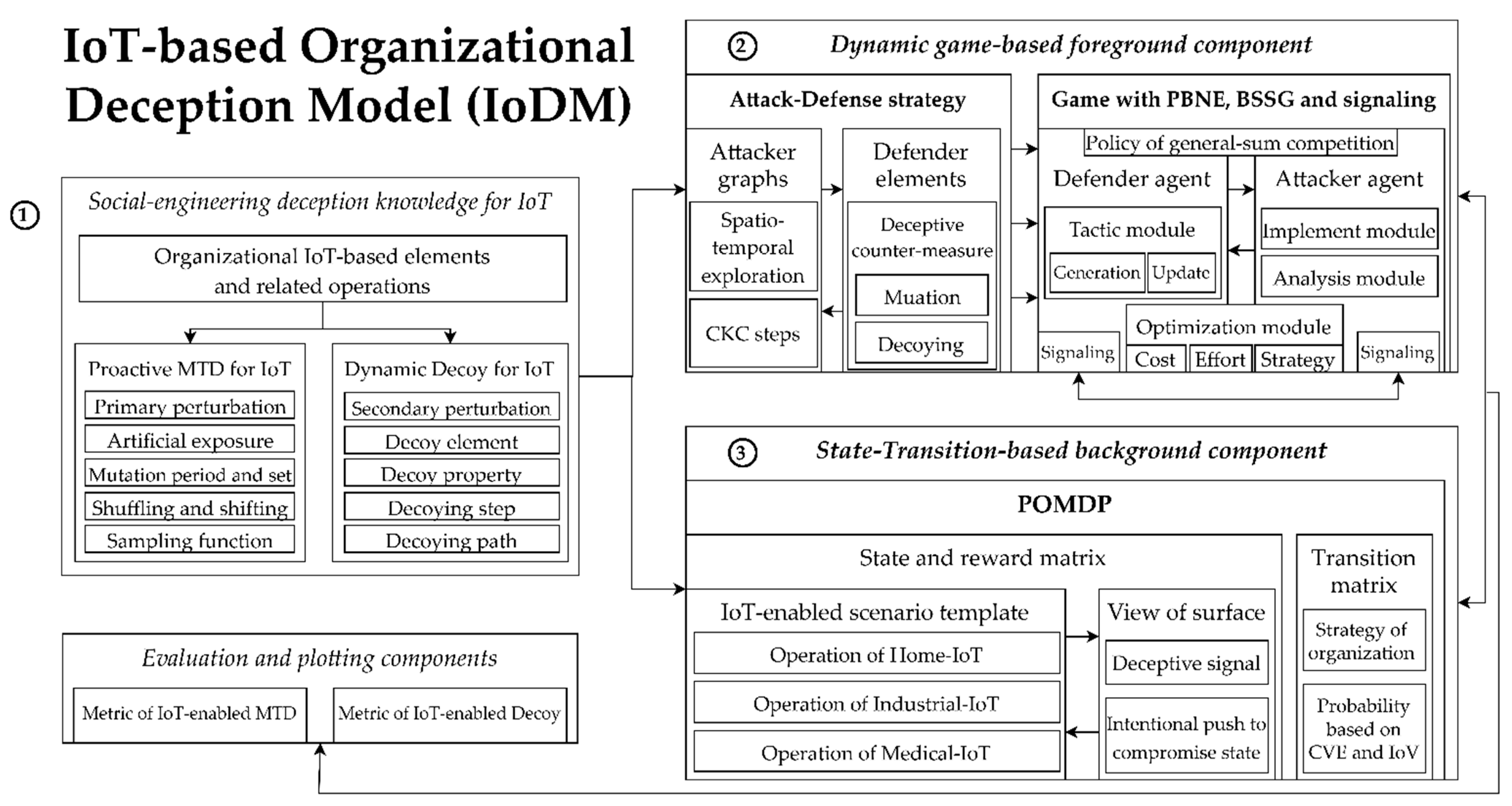
3. Proposed Organizational Deceptive Modeling for IoT and Related Strategies
3.1. Design Principle
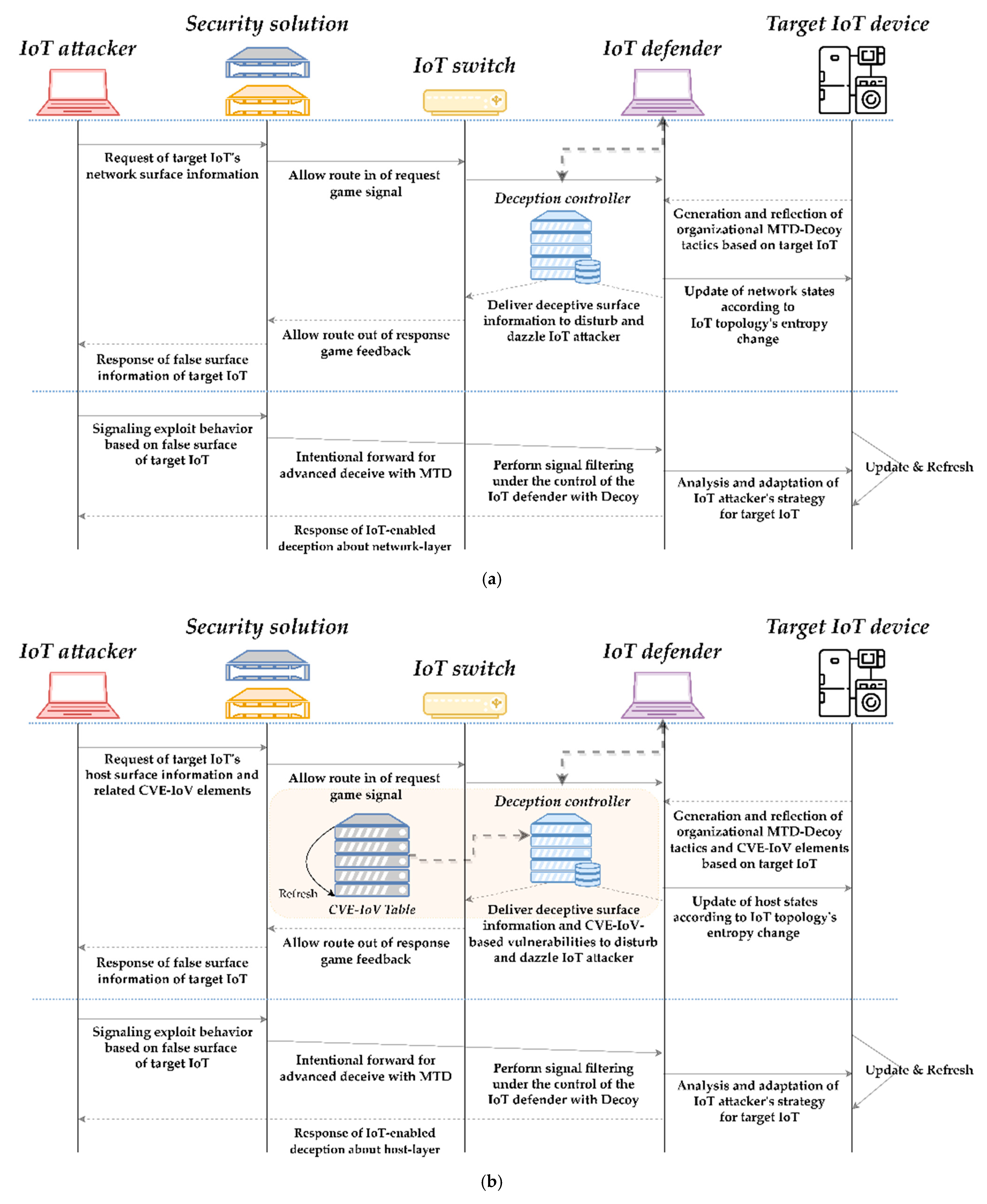
3.2. IoT-Enabled MTD and Decoy-Based Deception Process
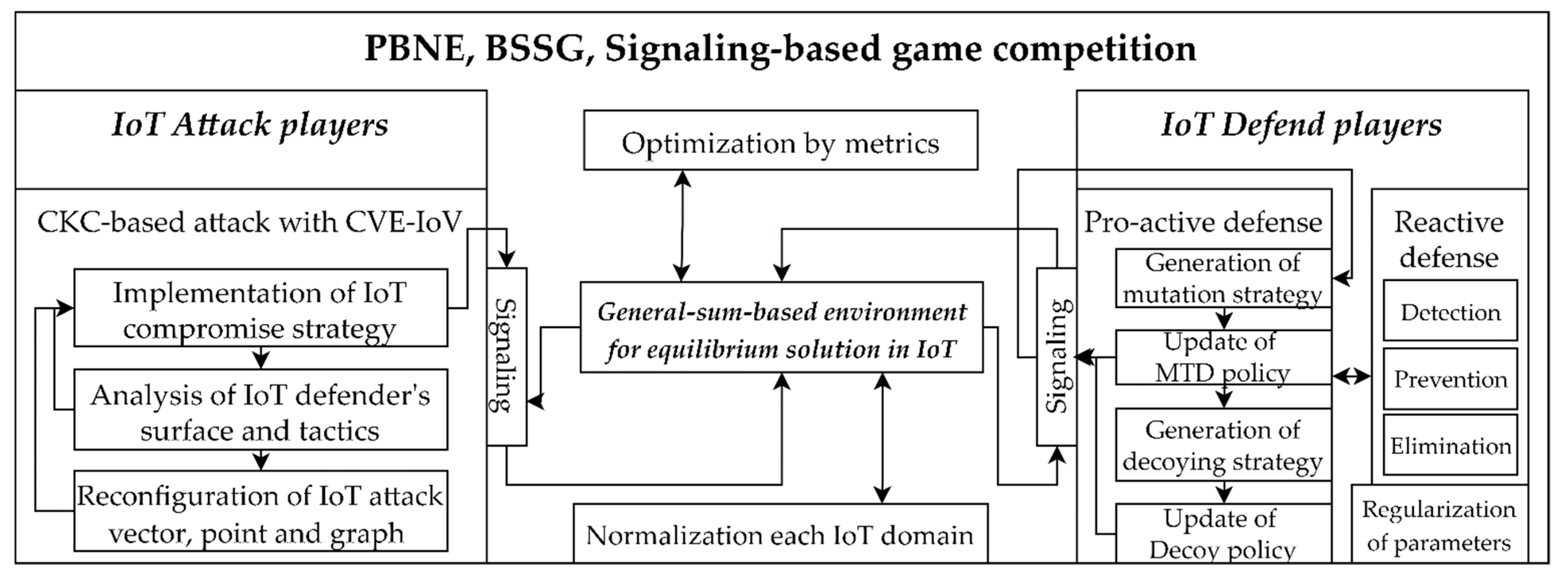
3.3. Construction of Deceptive Game Architecture with IoT-Based Organizational Network
3.3.1. Regularization of General-Sum Game Mechanisms
- is a set of actors, where is an IoT attacker, and is an IoT defender. In this case, payoffs and signaling by the actor and the leader–follower relationship are defined differently depending on each IoT scenario and the present situation of the development of detailed episodes.
- , , and are the sets of elements uniquely possessed by actors. is defined as the deceptive private information element of IoT defender . is defined as the attack graph-tree-based private information element of IoT attacker . The elements are combined or divided according to the changed payoffs by the actor, and unlike the defender, the attacker dynamically composes the element with , which is the effectiveness of the IoT attack surface at the present time point.
- , , and are the sets of decision strategies for general sum competition between IoT attacker and IoT defender , which are also configured according to the payoffs and signaling by the actor and the leader–follower relationship. is the deceptive strategy possessed by the defender. is the defender surface information possessed by the attacker, and is defined as an attack graph-tree and intelligence-based strategy.
- , , and are the sets of the signals of IoT attacker and IoT defender , respectively, and are selected according to the signaling initiatives given by the actor. has , which is a set of attack signals to achieve the goal of intrusion, and has , which is a set of proactive–reactive defense signals for achieving the protection of all IoT devices, systems, and networks.
- is a signal attenuation factor that determines the degree of attenuation of the ) of IoT defender according to the progress of the episode.
- , , and are the sets of general sum-based game beliefs of IoT attacker . is the set of prior beliefs of and is the set of posterior beliefs of produced through Bayes’ rule after received normal signals or deceptive signals spoofed based on the of IoT defender .
- is a set of and -based finite states in a general sum-based dynamic game component, which defines the multi-level nature and transferability of attack–defense competition along with actions.
- , , and are the sets of finite actions of IoT attacker and IoT defender for . defines the defender’s proactive–reactive deceptive and defensive actions to as transition relations. defines the attacker’s CKC actions to such as reconnaissance and search, vulnerability and fingerprint-based exploits, initial occupation and lateral movement, final invasion through privilege escalation and takeover and occupation.
- is a probability distribution function used to calculate the possibility for the IoT attacker and IoT defender to arrive at when IoT attacker carries out the action termed and IoT defender carries out the action termed at in the current episode.
- is a function used to calculate the reward obtainable within the current episode in when IoT attacker and IoT defender carry out the actions termed and at , respectively. IoT actors compete toward the maximization of reward until entering general sum-based game equilibrium.
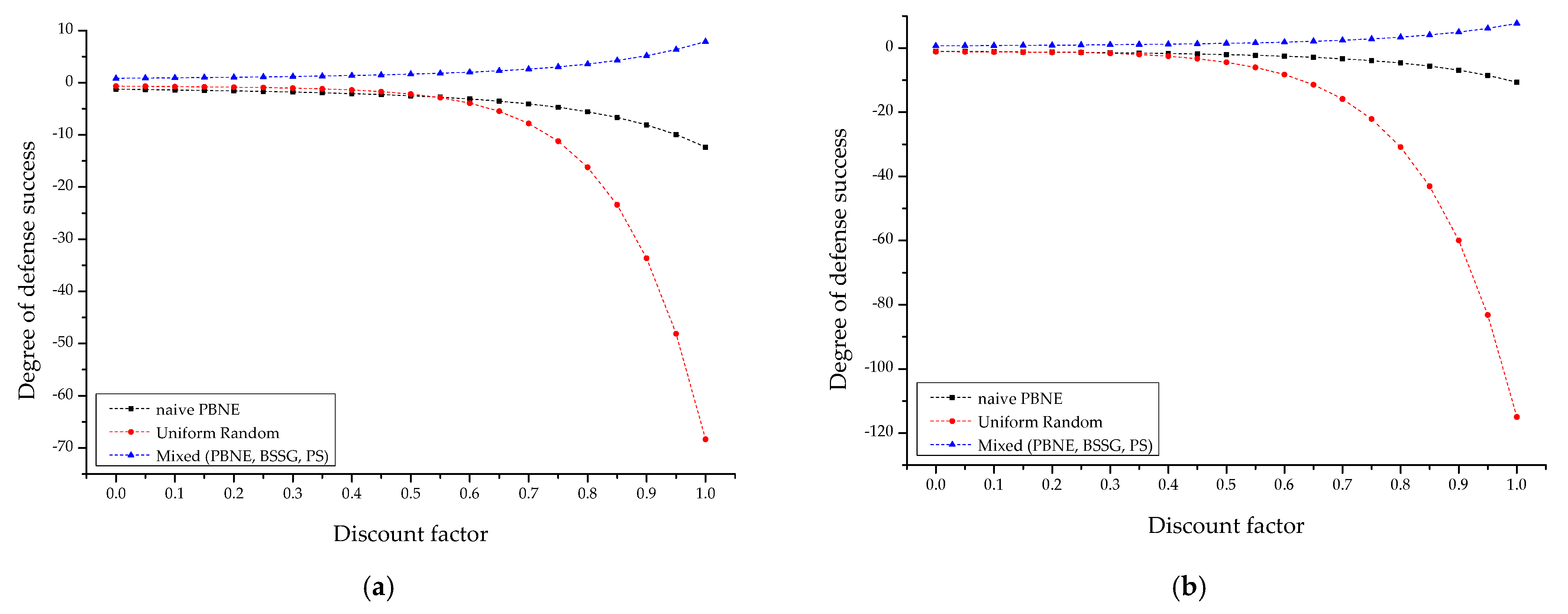
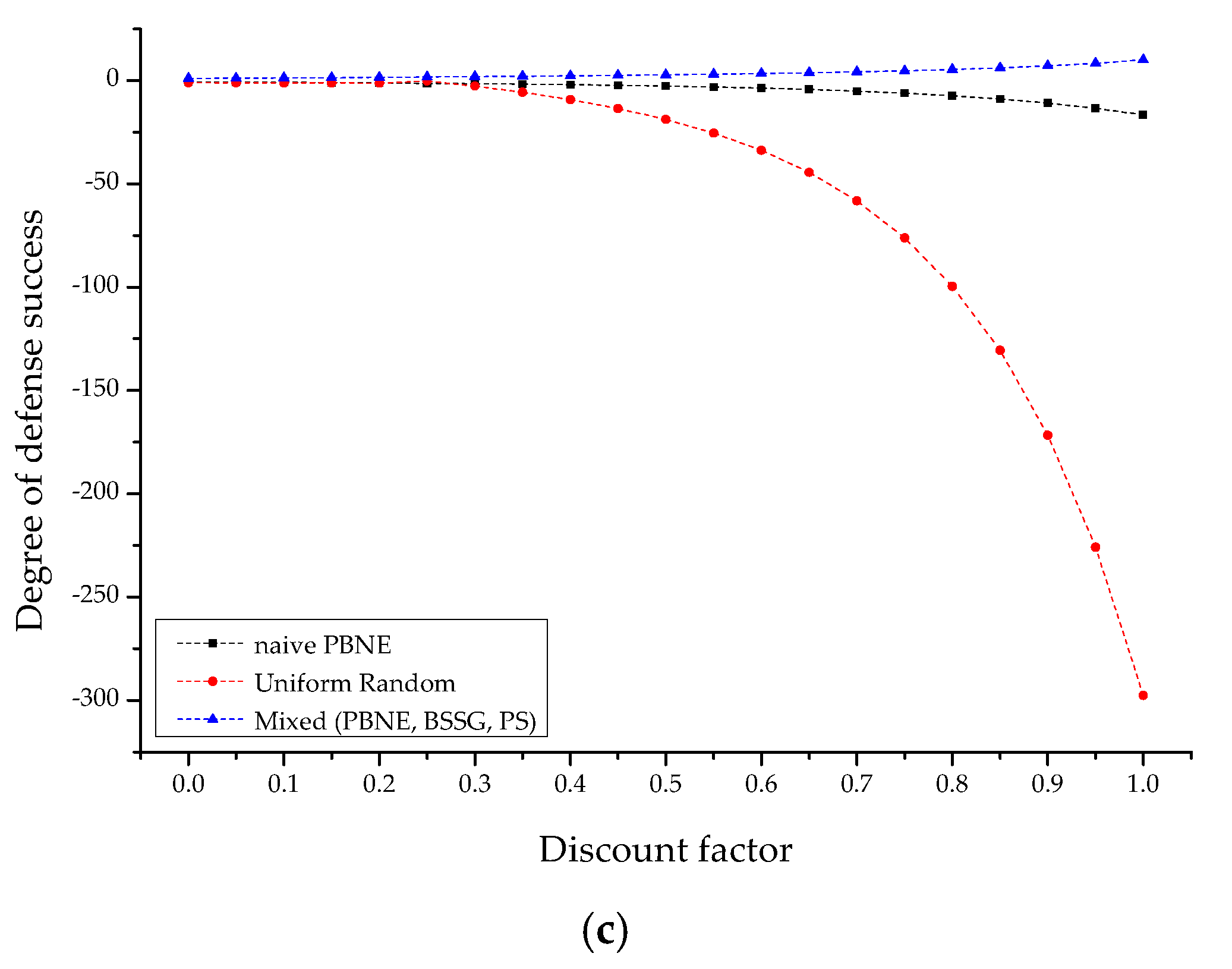
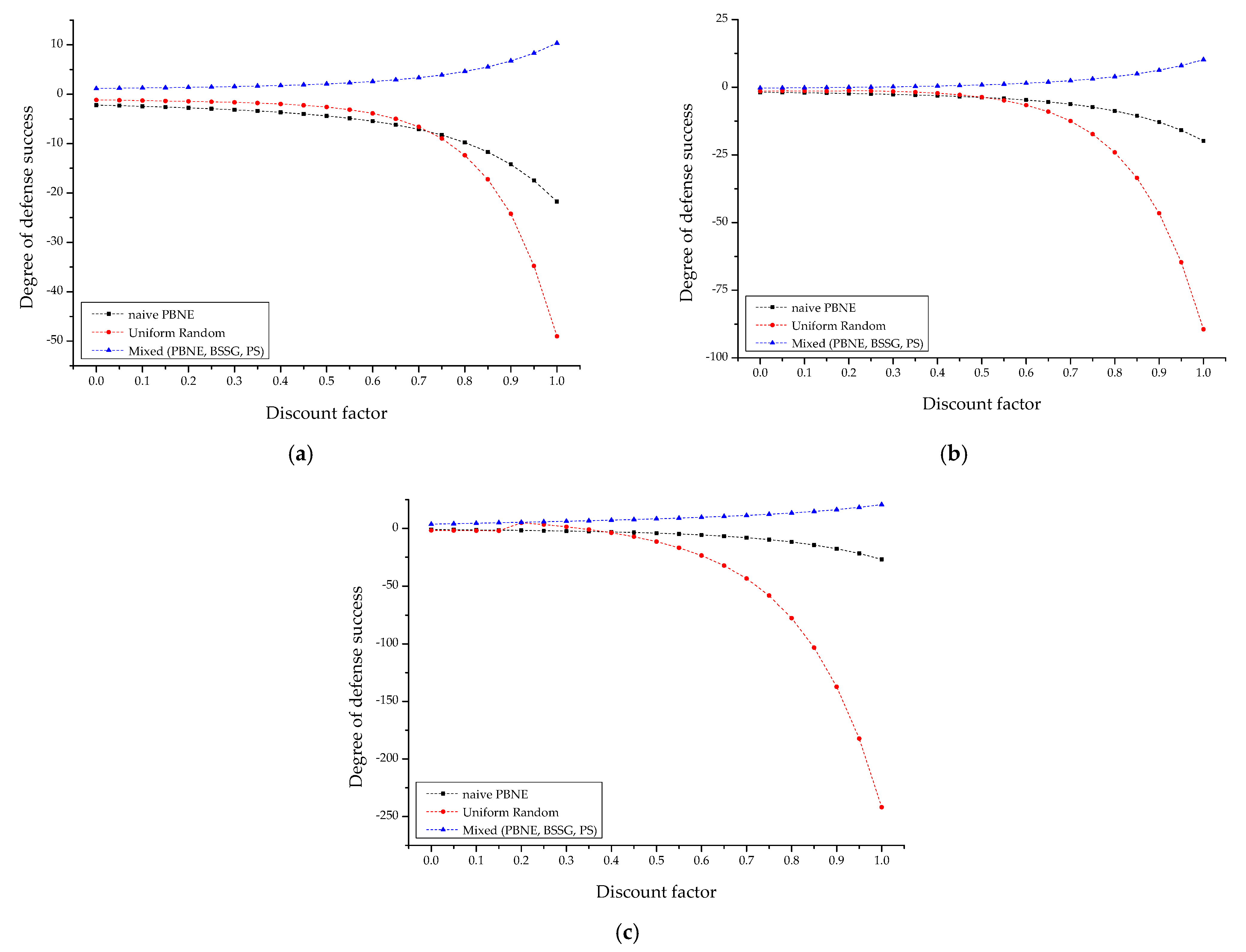
- is a discount factor function that cuts off the judgment ranges by the actor within [0,1] to force a quick judgment while also reducing the solution space required for optimization. In addition, it defines leader–follower-based ex-ante/ex-post competitive strategy judgments such as the limitation of surface information by an actor that can be observed at the present time, intelligence distortion, disinformation, and artificial disclosure so that they can be indirectly simulated.
- is a utility function for resources and costs incurred when performing competitive actions. is the utility function of IoT attacker , and is the utility function of IoT defender .
3.3.2. Optimization of Attack-Defense Competition with Game Equilibrium
4. Experiments
4.1. Configuration of Organizational IoT-Enabled Scenarios and Detailed Simulation Parameters
- IoT attacker’s action standard: An attacker intrudes an IoT-based organizational network from the outside and carries out attacks on the internal IoT sensor device, system, security solution, and sub-farm network. The final intrusion target points are selected as single or multiple IoT nodes, and the intrusion continues according to the CKC stages until the state of equilibrium is reached or the permitted attack time expires. As the episode unfolds, the intrusion target is changed according to the collected defender’s vulnerable contact points, attack surface information, and the effectiveness of the discount factor-based intelligence, and an attack chain is formed toward the production of the highest microscopic reward by time point
- IoT attacker’s APT attack strategy: The attacker considers finally occupying the target point defined in the current episode as the top priority strategy, and fans out all possible attacks based on the attack graph and attack tree defined outside before the initial intrusion to optimize the attack gains. In cases where the rate of success in achieving the first priority goal is lower than the possessed threshold, the attack strategy changes to select and occupy the next best attack target. This is done by changing the attack origins by episode or activating the tactics of lateral movement in a different direction of movement. However, if the attacker makes an error in judgment due to changes in the defender’s IoT network or deceiving acts, then the actual initiative of the attacker in the competitive relation may disappear as the attacker’s initial perception is biased toward defender dominance.
- IoT defender action standard: The defender monitors all IoT device units, security solutions, and sub-farm networks. However, due to the limited resources, the security solutions protecting the affiliated IoT nodes cannot be operated in a timely manner in all cases. The defensive deception signaling strategies by internal IoT sensor devices are not optimized based on the resources or the attenuation ratio of deceptive signals increases. Therefore, in cases where the defense contact point for countermeasures is selected wrongfully, the defense for the corresponding IoT device, farm network, and security solution will fail, and consequently, microscopic defense gains will decrease and the ripple effect of chain attacks in the CKC subsequent stages will increase. The defender’s goals are differently configured according to the importance levels by affiliated IoT nodes and the possibility of expression of vulnerabilities. However, they are aimed at proactively avoiding attacks on all IoT nodes and immediately defending against detected attackers for as long as possible. In the case of critical system-based IoT scenarios, the sub-farm networks composed of VLANs by IoT sensor devices are interconnected, or all periodic snapshots, restorations, and sandboxing isolation actions are carried out to improve safety.
- IoT defender’s deception strategy: The defender performs MTD- and decoy-based defensive deceptive actions for all affiliated IoT nodes in the topology based on leading signaling to disrupt and mislead the attacker’s judgment. However, since such deception alone cannot completely block intruding IoT attackers, reactive defense is also carried out. Since the defender’s reactive response is only possible on the basis of a single IoT device and a sub-farm network, an appropriate prevention point or response point deployment strategy should be produced depending on the available resources.
- Definition of scenario compensation: The concept of compensation that determines actions in the general sum game in IoDM is made into a constant based on CVE and CVSS related to the IoT sensor device. However, it can be dynamically increased or decreased according to the attacker’s APT level and present situation of intrusion, the level of defender deception-response, and the state of occupation rates by the actor, etc. so that they become variables
- Calculation of scenario compensation: IoT attackers by episode win rewards when they succeeded in CKC stages, while the defender wins rewards when they succeeded in proactive–reactive defense against the attacker’s CKC intrusion act. The reward values are differently defined in relation to the importance levels, correlations, ripple effects, and vulnerabilities of IoT nodes, and microscopic reward values are determined accordingly. When the final simulation has ended, each IoT actor calculates the microscopic reward value.
- Definition of episode discount factor: A concept of discount factors was introduced to force quick decisions by IoT actors and prevent the fixation of the macroscopic equilibrium. That is, attackers and defenders cannot postpone microscopic decisions at the present time unlimitedly for more than a hundred episodes, and the MILP solution space to obtain maximum rewards is also limited by the cut-off.
- Simulation termination condition: With reference to an attacker, this is when the attacker reaches the intrusion target point configured at the present time point, carried out gradual exploitation based on the vulnerable point of contact, and thereafter occupies it based on the action of the object (AoO). With reference to a defender, it is when the defender neutralizes the detected attacker’s CKC-based act of intrusion and expels the attacker by completely depleting the resources. After the simulation ends, along with the reward values optimized by episode, the probability values related to the main metrics based on the efforts, costs, and utilities of the attacker and the defender are finally returned.
- Addition of the concept of security solutions dedicated to IoT: UTM is a primary security terminal that combines intrusion detection system (IDS) and intrusion prevention system (IPS) functions. IDS and IPS functions are performed to identify, detect, and block threats from IoT attackers. Then, the firewall is an access control within an IoT-based organizational network and operates as a secondary security terminal that distinguishes the validity of legitimate users and authorizes them. Depending on the scenarios, these security solutions are diversified horizontally and become double-modular-redundant or triple-modular-redundant vertically. In this case, the potential vulnerability is only assumed as a hole-based vulnerable contact point for external IoT attackers to bypass, and unlike the affiliated IoT nodes, the attacker’s act of occupation through remote code execution, privilege escalation, etc. are limited or not performed.
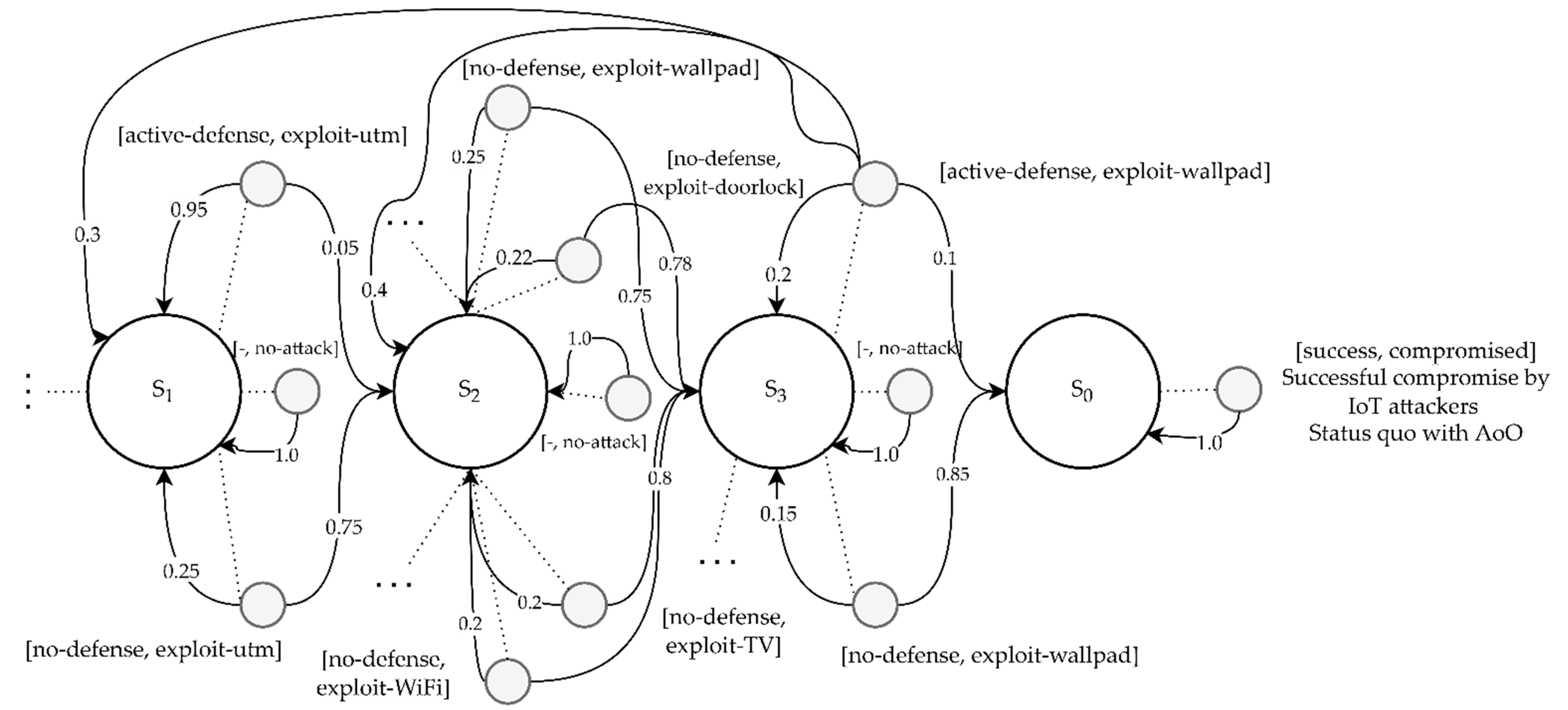
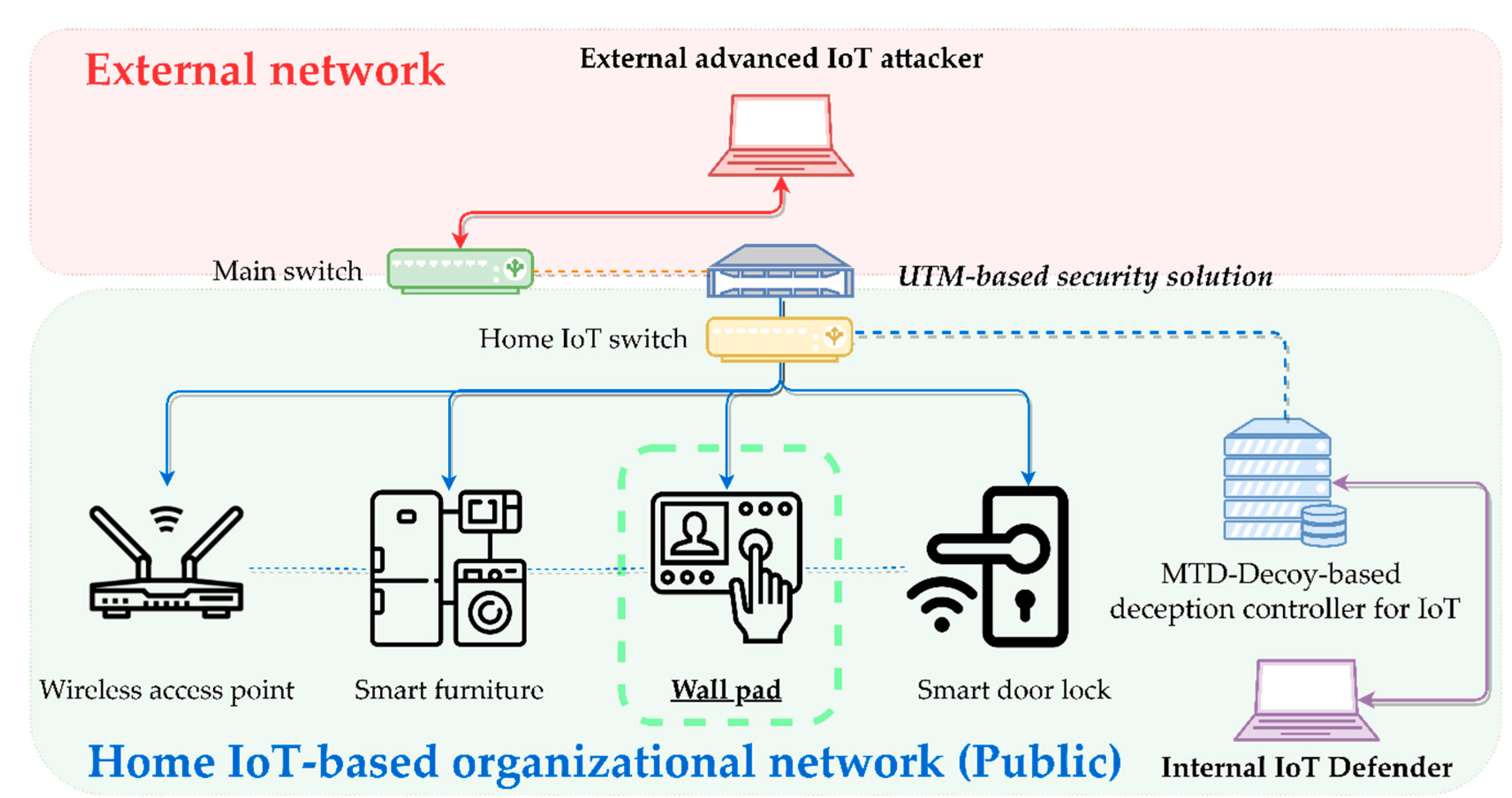
- Scenario 1 (Figure 4): ‘Smart home IoT-Based open organizational network topology’.
- (1)
- IoT node configuration: IEEE 802.11 WiFi device (‘Wireless access point’), smart TV (‘Smart furniture’), wall pad (‘Wall pad’), smart door lock (‘Smart door lock’).
- (2)
- IoT security solution configuration: Single IoT-enabled UTM device with some user access control and authorization functions.
- (3)
- IoT attacker’s intrusion goal: The best goal is to obtain firmware authority for the smart door lock through contamination of input factors of an unauthenticated external IoT attacker, and then achieve improper unlocking. When it seems impossible to acquire the authority for the target smart door lock, the target is changed into a WiFi device that has more vulnerable contact points and a wide attack surface to achieve suboptimal intrusion, and then differentially carry out chain attack actions of pivoting with a wall pad, etc. in parallel.
- (4)
- IoT defender’s defense goal: While performing MTD and decoy-based proactive evasion and deception for all IoT nodes and security solutions, depleting all utilities related to the validity of the defender intelligence possessed by a professional IoT attacker and an attempt to enter the CKC stage to completely achieve reactive blocking of remote intrusion within the IoT network.
- (5)
- Attacker’s major intrusion path and fanout tactic: Outside the IoT network → attempt to intrude inside → bypass IoT-enabled UTM’s access control and detection policy → carry out an immediate search for and access to a smart door lock with a vulnerability in privilege elevation due to parameter contamination. When continuing access or attack seems impossible, progressively carry out differential intrusion, pivoting, occupation, and search by IoT node according to other vulnerabilities → finally achieve the intrusion into and occupation of the smart door lock.
- (6)
- Defender’s major defense sequences and normalization strategy: Perform MTD based on the shuffling of the entire organizational networks by IoT and host layer information. Decoying based on dynamic sandboxing is also performed in parallel. Configure proactive deception process → carry out UTM-based real-time monitoring according to limited resources → detect the intruding attacker and control the access of the attacker, and carry out reactive blocking → force the attackers to make inferior judgments and maximize the required costs → achieve complete expulsion to the outside.
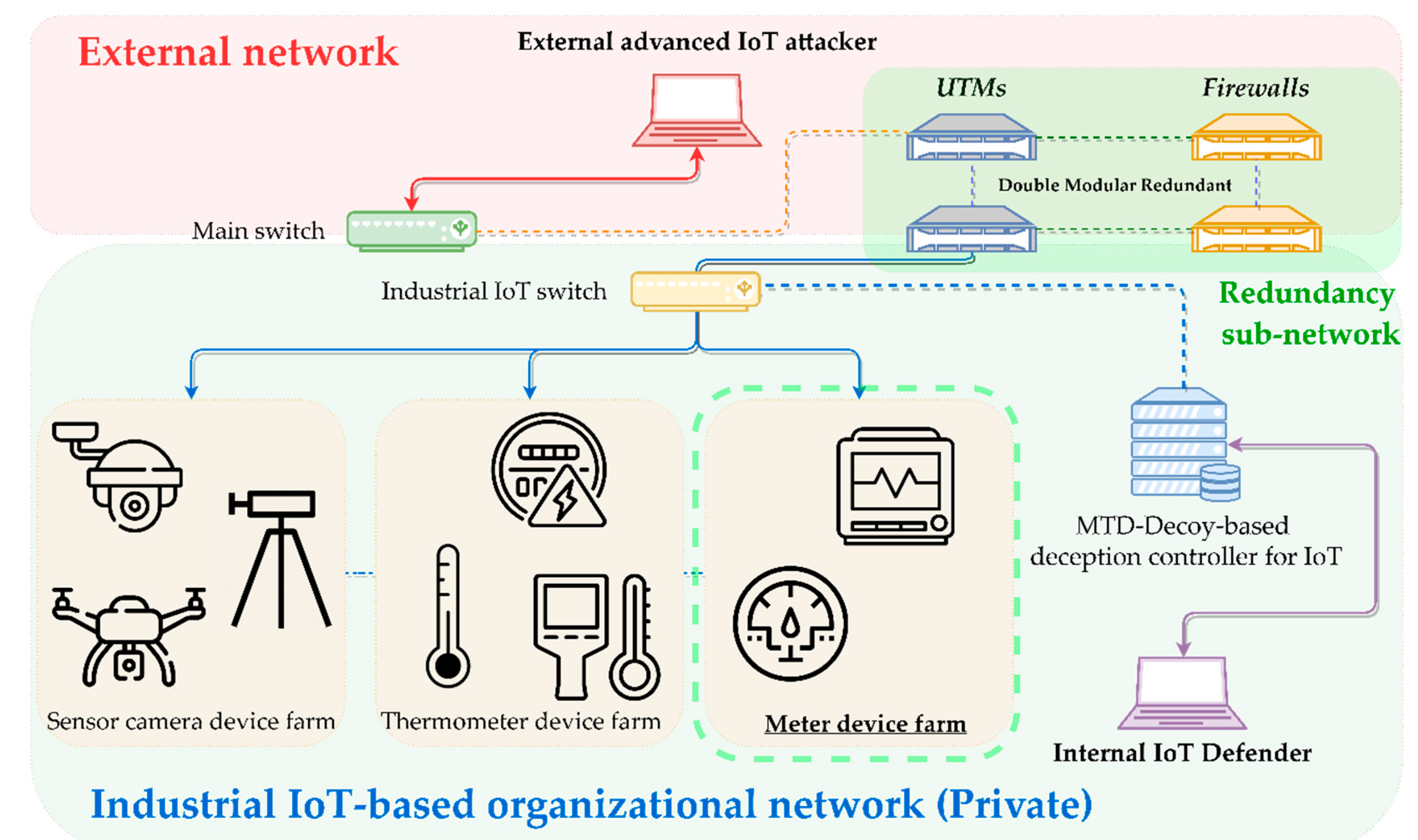
- Scenario 2 (Figure 5): ‘Closed organizational network topology based on the industrial IoT applied with a dual modular redundancy (DMR) security solution dedicated to IoT’.
- (1)
- IoT node configuration: multiple industrial sensor camera device-based farm networks (‘Sensor camera device farm’), multiple industrial thermometer-based farm networks (‘Thermometer device farm’), multiple industrial meter-based farm networks (‘Meter device farm’).
- (2)
- IoT security solution configuration: Two UTMs and two firewalls horizontally interconnected and vertically DMRed.
- (3)
- IoT attacker’s intrusion goal: The best goal is to obtain power meter firmware authority through remote code execution based on stack-based buffer over-flow of the web application, and then to achieve the securing of a second intrusion vector for other interconnected industrial IoT devices. When it seems impossible to obtain the authority for a single target meter or the relevant farm network, achieve the sub-optimal intrusion by damaging the thermometer that can cause very large human-property losses or damaging the confidentiality of protected resources based on visual images and changing the target into an industrial sensor camera device from which meaningful real-time information can be taken over. Pivoting is carried out in parallel in the affiliated sub-farm network from the initially occupied node as a starting point.
- (4)
- IoT defender’s defense goal: Same as that in Scenario 1
- (5)
- Attacker’s major intrusion path and fanout tactic attacker: Outside of IoT network → attempt to intrude → bypass the policy of DMRed IoT-enabled UTM and firewall → carry out an immediate search for and access to the power meter that has vulnerabilities in the execution of remote codes and privilege escalation due to buffer overflow. When continuing the search and the access or attack seem impossible, carry out pivoting to another meter within the same sub-farm network or change the intrusion route to another farm network → achieve the intrusion into the power meter and final occupation.
- (6)
- Defender’s major defense sequences and normalization strategy: Force defender dominant deceiving, disturbing, and isolating actions with MTD based on shuffling by each of the entire IoT nodes and decoying based on multitenancy sandbox → carry out reinforced monitoring and detection of multiplexed UTM and firewall → carry out reactive blocking and expulsion of the IoT attacker that intruded any sub-farm network in parallel → achieve complete expulsion from the upper network.
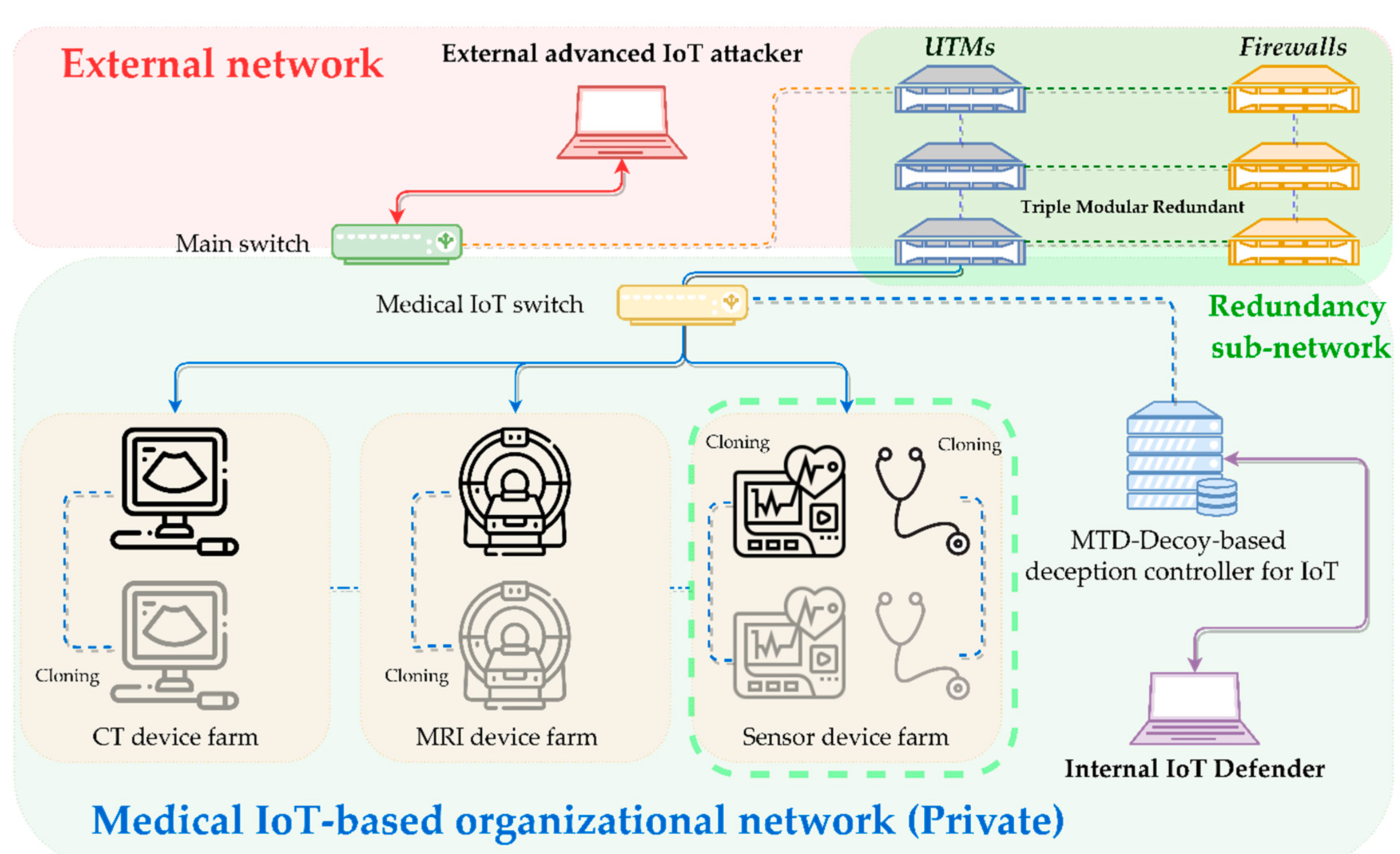
- Scenario 3 (Figure 6): ‘Closed organizational network topology based on Medical IoT applied with a triple modular redundant (TMR) security solution dedicated to IoT’.
- (1)
- IoT node configuration: farm network including CT device and duplexed virtual clone device (‘CT device farm’), farm network including MRI device and duplexed virtual clone device (‘MRI device farm’), farm network including in the fusion pump, electrosurgical unit-based medical sensor device, and, respectively, duplexed virtual clone devices (‘Sensor device farm’).
- (2)
- IoT security solution configuration: Vertically TMRed integrated IoT-enabled UTMs and three firewalls.
- (3)
- IoT attacker’s intrusion goal: The best goal is to obtain the sensitive data of a medical infusion pump applied with inappropriate privilege handling routines, seize the administrator privilege, and achieve the possibility of a direct threat to human life through lateral movement to similar IoT devices within the same farm network. When it seems impossible to gain control over a single-target infusion pump or electrosurgical unit or the relevant farm network, change the target into CT and MRI devices that can threaten the lives of many patients with a greater scope of malfunction while taking over the patients’ sensitive personal information thereby achieving suboptimal intrusion. Pivoting is carried out in parallel in the affiliated sub-farm network from the initially occupied node as a starting point.
- (4)
- IoT defender’s defense goal: Same as that in Scenario 2.
- (5)
- Attacker’s major intrusion route and fanout tactics: Outside the IoT network → attempt to intrude inside → bypass the policy of TMRed IoT-enabled UTM and firewall → carry out an immediate search for and access to a medical injection pump sensor device with vulnerability in privilege escalation due to sensitive data disclosure. When it seems impossible to continue the attack, carry out pivoting to another medical sensor device in the same sub-farm network or change the intrusion route into another farm network → carry out intrusion into the drug infusion pump and neutralization and destruction of the backed up image → achieve the final occupation.
- (6)
- Defender’s major defense sequences and normalization strategy: Perform MTD and Decoy-based proactive deception process → carry out triplication-based additional monitoring while ensuring snapshot-based IoT node image integrity in parallel → Detect IoT attacker intrusion, reactively block and expel the attacker, and carry out restoration to normal states with random snapshots → achieve complete expulsion to the outside
4.2. Results
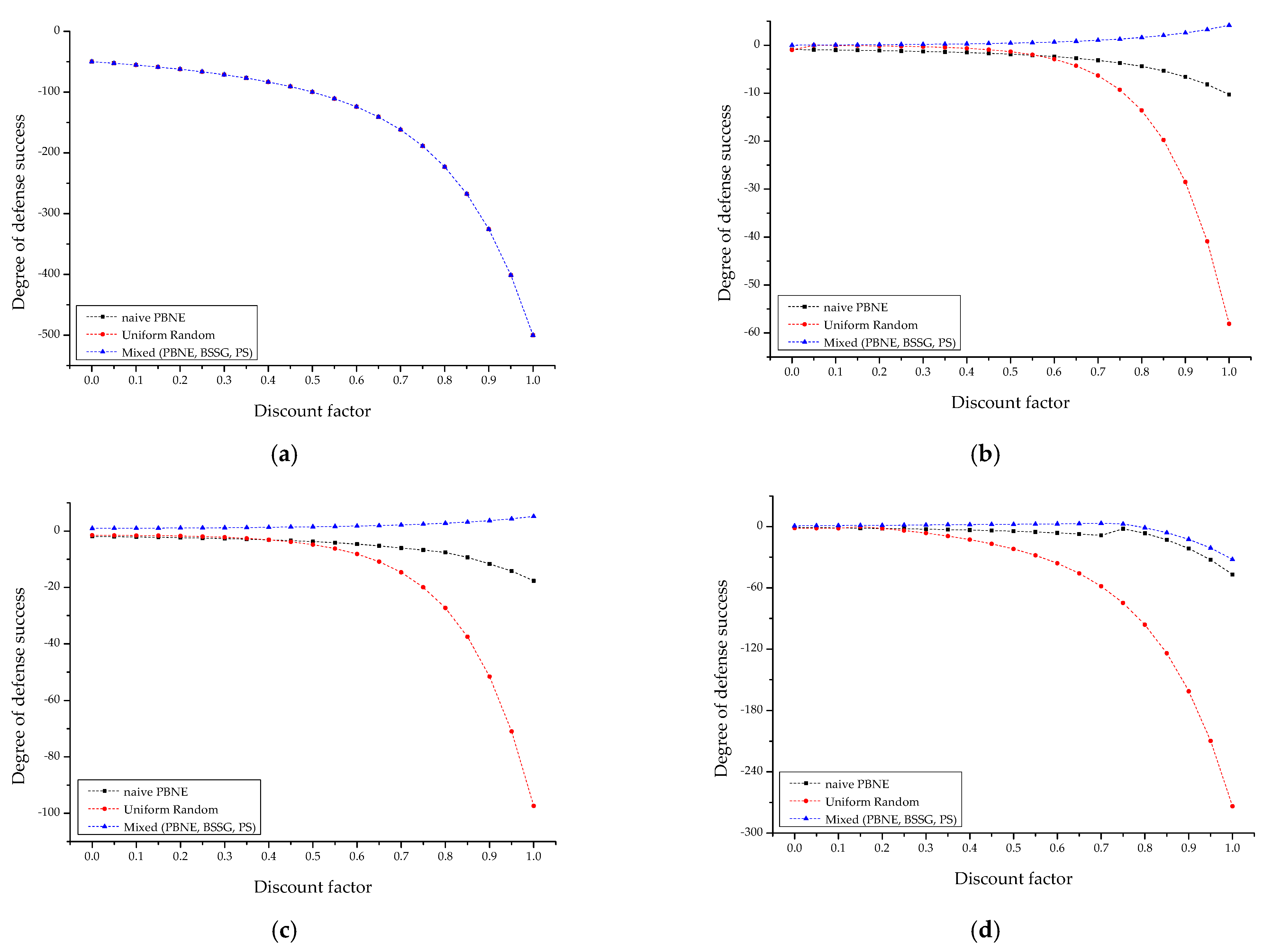
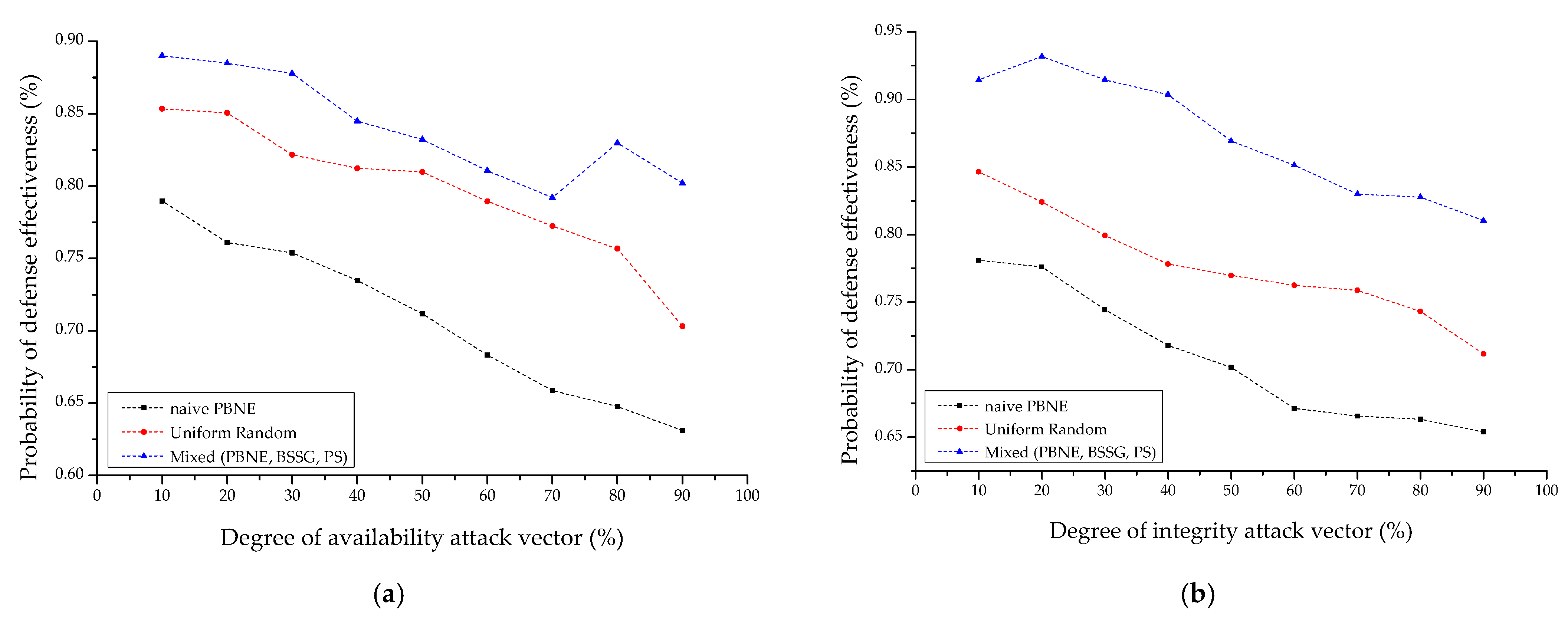
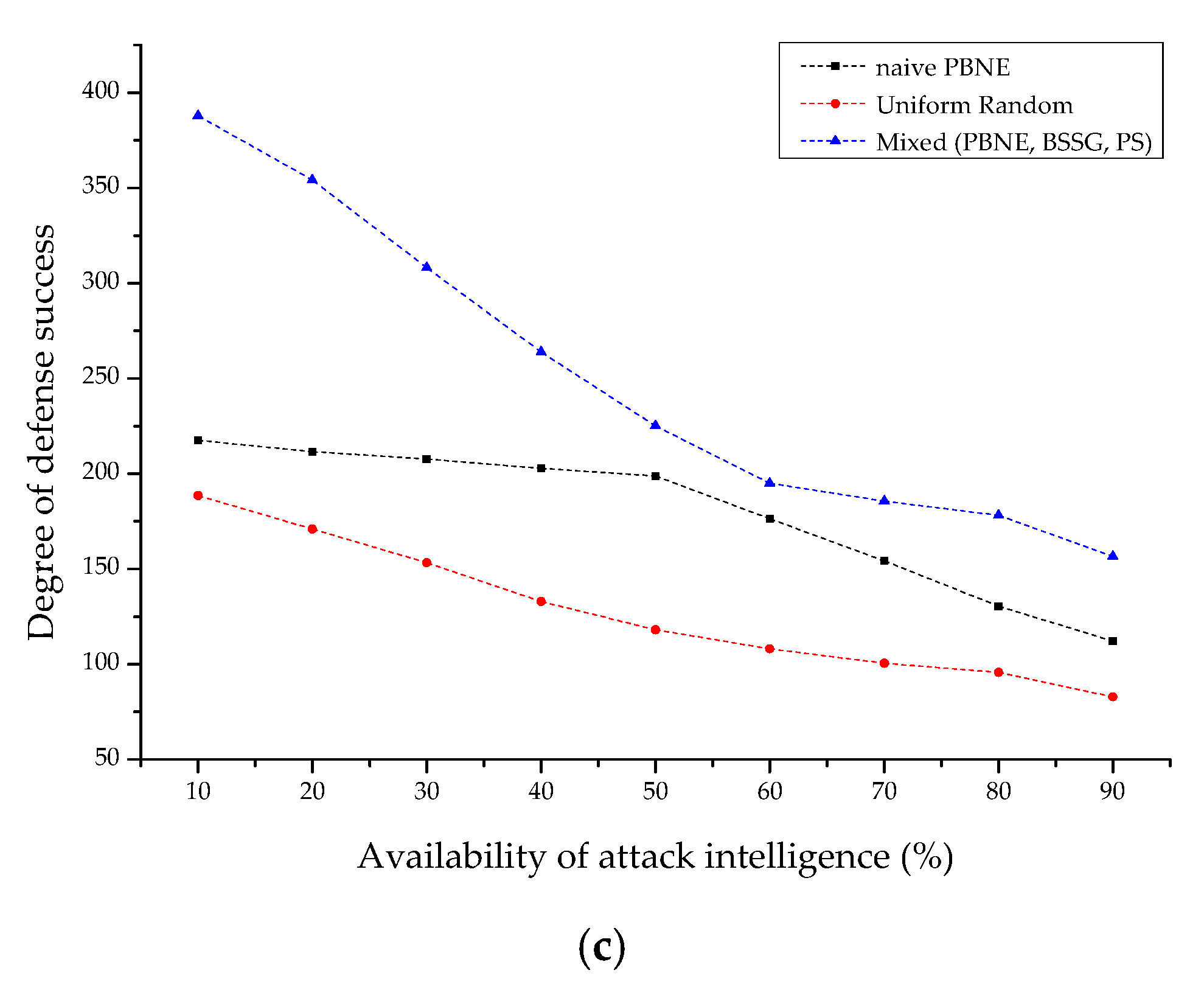
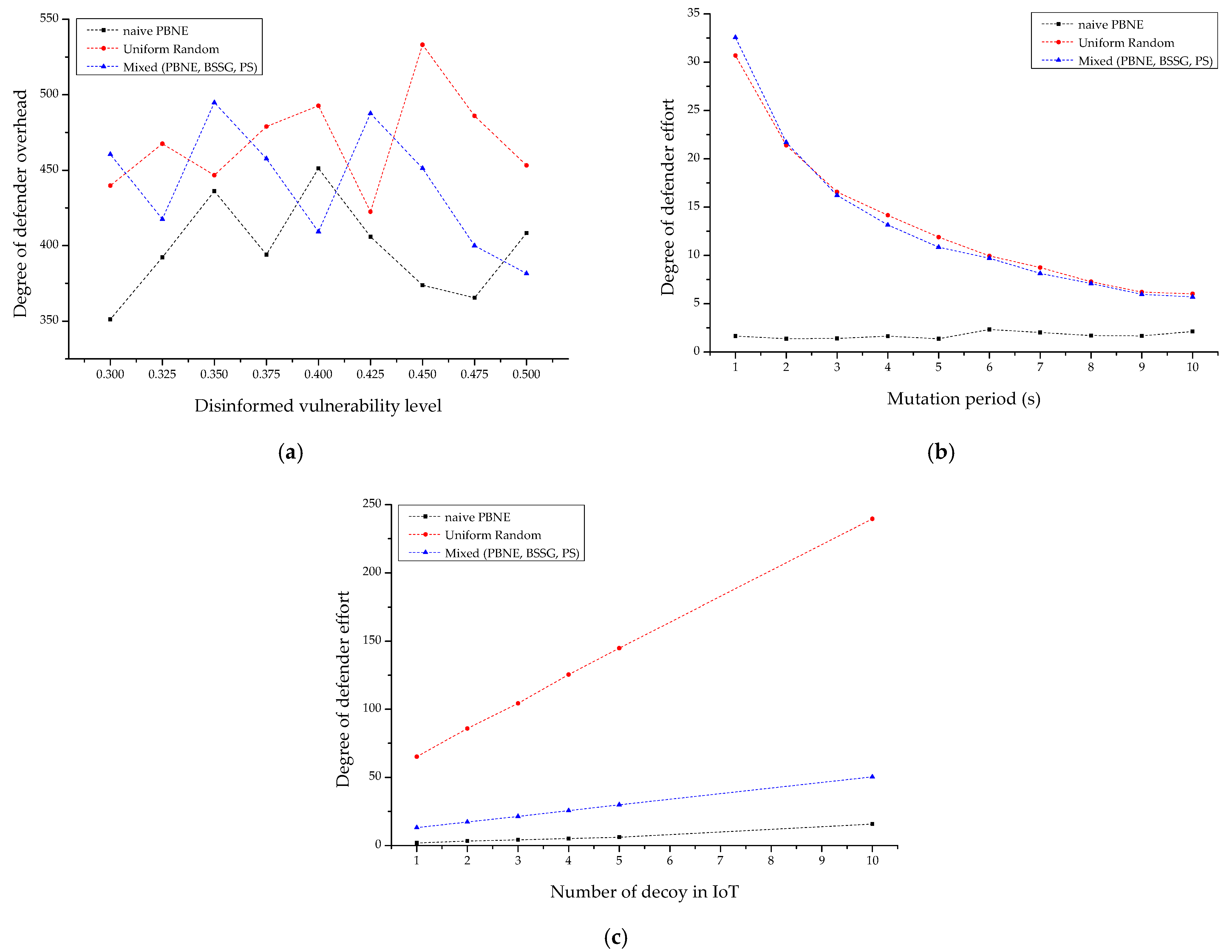
4.2.1. Comparative Analysis of Each IoT-Based Scenario
4.2.2. Sensitivity Analysis with Decision Strategy
5. Discussion
- The issue of demand for strategization due to the limited range of decisions: In an actual IoT system and network environment, attack–defense actors subjectively process asymmetric information available at the present time and decide on actions after making incomplete judgments. This proves that a simple naive game strategy that models dynamic decision-making under the premise that actors in an uncertain situation have a consistent view is not generalizable. This study tried to mitigate the problem by conceptualizing disinformation-based partial signaling game tactics and adaptively changing the state-transition probability according to changes in the attack–defense state in the modeling related to conflicts of interest between the IoT attack–defense actors; however, potential side effects will still remain. Accordingly, the hyper game theory [41], which is an unbalanced metagame, should be quantitatively utilized to formulate the inferior decision-making flow when the actors in competitive relationships by episode are ‘induced’ to select the best strategy due to subjective or false beliefs, differences in information and view, misperception, and perceived uncertain judgment, etc. In addition, various solution spaces for the relevant modeling of conflicts and methods to produce optimal solutions configured based on the uniqueness of the IoT domain (e.g., frequent additional interventions by unspecified internal and external actors, impossibility to cut off decision strategies due to explosive increases in interconnected channels, etc.) should be processed. Furthermore, approaches such as FlipIt games [67,68,69] and other various game theories [70] should be considered.
- Substantiality of IoDM and optimization problem: The IoT organizational characteristics intellectualized in the game in this IoDM were quantified as based conditions for sequential entries into the game equilibrium state through the calculation of the state-transition probability in POMDP and reward values after preprocessing the CVEs or related IoVs disclosed. However, they will be different from the unique policies or beliefs related to the actual organization that operates the IoT device-system-network and will show clear practical differences from the network-separated IoT organization environment according to the range of disclosure of vulnerable information and the IoT domain classification. In addition, since the defined IoT-based CVEs and IoVs were simply limited to CVSS scoring-based parameterization rather than considering the correlation or ripple effect between IoT device-system-network specifications, additional augmentation and normalization should be also considered.
- The scalability problem of the IoT deception model: Since this study carried out experiments to reduce the attack-exploration surface through defense actors’ performance of IoT-enabled MTD and decoy-based deceptive actions and performance optimization within the scope of scenarios configured in the IoT domain, we did not consider scenarios or other domains other than the ones described. In addition, since the IoT specifications emulated in the game are also formulated as attack–defense probability values based on random scenario configurations, the probability values should be abstracted at a more stratified organizational IoT domain classification level and the appropriate IoT operation process should be conceptualized.
- IoT-enabled MTD and decoy applicability problem: The main experimental results were derived using MTD metrics based on mutation period and intensity, candidate target, and sampling and decoy metrics based on decoying elements, properties, and paths. However, an improved solution set should be produced by securing a wider solution space. An approach to hierarchically modeling complex correlations between IoT systems is required. Therefore, it is necessary to improve the approach based on reinforcement learning, deep neural network, and graph neural network [71], which have been actively studied recently in the field of deception.
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| State | Probability of Transition in Scenario 2 | Reward Value for Defender |
|---|---|---|
| State | Probability of Transition in Scenario 3 | Reward Value for Defender |
|---|---|---|
| Scenario | CVE ID | Vulnerability and Related Weakness 1 | Related Node | Exploitability Score in CVSS 2.0 |
|---|---|---|---|---|
| Home IoT-based organizational network (Scenario 1) | CVE-2018-3953 | OS command injection | Wi-Fi | 8.0 |
| CVE-2021-34991 | Remote code execution with overflow | Wi-Fi | 6.5 | |
| CVE-2021-44632 | Remote code execution with overflow | Wi-Fi | 10.0 | |
| CVE-2020-9759 | Privilege escalation | TV | 10.0 | |
| CVE-2018-4082 | Remote code execution with overflow, Memory corruption, Denial-of-service | TV | 8.6 | |
| CVE-2021-30780 | Privilege escalation | TV | 8.6 | |
| CVE-2019-19163 | Remote code execution | Wall pad | 6.5 | |
| CVE-2019-13143 | Privilege escalation with parameter pollution | Door lock | 10.0 | |
| CVE-2019-12944 | Missing authorization | Door lock | 8.6 | |
| CVE-2020-25223 | Remote code execution | UTM | 10.0 | |
| CVE-2020-17352 | OS command injection | Firewall | 8.0 | |
| Industrial IoT-based organizational network (Scenario 2) | CVE-2016-9155 | Improper access control | Sensor camera | 10.0 |
| CVE-2018-10661 | Bypass of restriction | Sensor camera | 10.0 | |
| CVE-2017-3209 | Incorrect default permissions and missing authentication | Sensor camera | 6.5 | |
| CVE-2019-3944 | Incorrect default permissions with deauthentication | Sensor camera | 10.0 | |
| CVE-2013-4860 | Incorrect default permissions | Thermometer | 6.5 | |
| CVE-2018-11315 | Bypass of restriction and related permissions | Thermometer | 6.5 | |
| CVE-2017-9944 | Improper privilege management | Meter device | 10.0 | |
| CVE-2021-44165 | Remote code execution with overflow | Meter device | 10.0 | |
| CVE-2018-0101 | Remote code execution with double-free | UTM | 10.0 | |
| CVE-2021-34787 | Bypass of restriction | Firewall | 8.6 | |
| Medical IoT-based organizational network (Scenario 3) | CVE-2018-8857 | Hard-coded credentials | CT device | 3.9 |
| CVE-2020-25175 | Weak encryption of protected credentials | CT device | 10.0 | |
| CVE-2021-26262 | Improper access control | MRI device | 10.0 | |
| CVE-2020-25179 | Obtain credentials | MRI device | 10.0 | |
| CVE-2019-13543 | Hard-coded credentials | Medical sensor | 10.0 | |
| CVE-2020-12041 | Incorrect permission assignment | Medical sensor | 10.0 | |
| CVE-2020-25165 | Improper authentication | Medical sensor | 10.0 | |
| CVE-2021-36807 | Remote code execution with SQL injection | UTM | 8.0 | |
| CVE-2022-1040 | Remote code execution with bypass | Firewall | 10.0 |
| MTD Parameter | Value | Decoy Parameter | Value |
|---|---|---|---|
| Time slot length for periodic mutation (s) | 1–86,400 | Activation time (s) | 0–518,000 |
| Mutation batch pool size | 32–2048 | Number of decoying hosts | 1–5 |
| Bellman-based mutation sampling size | 8–2048 | Number of decoying services | 1–10 |
| Mutation shuffling tactic [61] | Random, GeneticHeuristic | Number of decoying vulnerabilities | 1–10 |
| Mutation period decision scheme [61] | Random, Adaptive, Hybrid | Number of decoying beacons | 1–20 |
| Number of false surface views in topology | 0–24 | Number of decoying signals | 1–10 |
| Maximum number of branches in attack graph-tree | 23 | Level of attack severity with vulnerability | L-M-H |
| Maximum number of deceptive signaling | 0–25 | Maximum number of compromised decoys | 0–5 |
| Mutation range of security solutions | 0–24 | Maximum number of sandboxing holes | 0–1 |
| Mutation range of IPv4 addresses | 28–236 | Feedback rate for adaptation each episode (%) | 10−4–10−2 |
| Mutation range of port numbers | 210–216 | Probability of interaction each attack step (%) | 0–100 |
| Mutation range of OS fingerprints | 0–24 | Probability of cloning (%) | 1–90 |
| Mutation range of protocol services | 0–24 | Probability of mimicking (%) | 1–80 |
| Mutation range of vulnerabilities | 21–24 | Probability of enticingness in decoy (%) | 30–100 |
| Probability of disinformation (%) | 1–100 | Probability of conspicuousness in decoy (%) | 50–100 |
| Probability of artificial disclosure (%) | 1–100 | Probability of variability in decoy (%) | 10–100 |
| Probability of reliability of deceptive signal (%) | 1–100 | Probability of differentiability in decoy (%) | 70–100 |
| Parameter | Value |
|---|---|
| Simulation time (s) | 7200–518,000 |
| Number of simulation run for Monte Calro | 100 |
| Attack time (s) | 3600–518,000 |
| Defense time (s) | 3600–518,000 |
| Number of scenarios | 3 (Home IoT, Industrial IoT, Medical IoT) |
| Number of real IoT devices each node | 1 |
| Switch mode | Virtual local area network (VLAN) |
| Number of CKC phases with IoT attacker | 4–7 |
| Validity of attak surface (%) | 10–90 |
| Efficiency of packet drop attacks (%) | 10–90 |
| Efficiency of packet modify attacks (%) | 10–90 |
| Discount factor (%) | 0–100 |
| Number of vulnerability and weakness each node | 1–4 |
| Methodology of constructing attack paths | Attack graph, attack tree |
| Operating system | Windows 10 |
| Language | Python 3.7.5 (Anaconda) |
| MILP-based general-sum game solver | Gurobi optimizer 9.0 |
References
- Wang, S.; Shi, H.; Hu, Q.; Lin, B.; Cheng, X. Moving Target Defense for Internet of Things Based on the Zero-Determinant Theory. IEEE Internet Things J. 2020, 7, 661–668. [Google Scholar] [CrossRef]
- Soussi, W.; Christopoulou, M.; Xilouris, G.; Gur, G. Moving Target Defense as a Proactive Defense Element for beyond 5G. IEEE Commun. Stand. Mag. 2021, 5, 72–79. [Google Scholar] [CrossRef]
- Saputro, N.; Tonyali, S.; Aydeger, A.; Akkaya, K.; Rahman, M.A.; Uluagac, S. A Review of Moving Target Defense Mechanisms for Internet of Things Applications. In Modeling and Design of Secure Internet of Things; John Wiley & Sons: New York, NY, USA, 2020; pp. 563–614. [Google Scholar]
- Seo, S.; Han, S.; Kim, D. D-CEWS: DEVS-Based Cyber-Electronic Warfare M&S Framework for Enhanced Communication Effectiveness Analysis in Battlefield. Sensors 2022, 22, 3147. [Google Scholar] [CrossRef]
- Majid, M.; Habib, S.; Javed, A.R.; Rizwan, M.; Srivastava, G.; Gadekallu, T.R.; Lin, J.C.W. Applications of Wireless Sensor Networks and Internet of Things Frameworks in the Industry Revolution 4.0: A Systematic Literature Review. Sensors 2022, 22, 2087. [Google Scholar] [CrossRef]
- Zhu, M.; Anwar, A.H.; Wan, Z.; Cho, J.-H.; Kamhoua, C.; Singh, M.P. Game-Theoretic and Machine Learning-based Approaches for Defensive Deception: A Survey. arXiv 2021, arXiv:2101.10121. [Google Scholar]
- Fraunholz, D.; Anton, S.D.; Lipps, C.; Reti, D.; Krohmer, D.; Pohl, F.; Tammen, M.; Schotten, H.D. Demystifying deception technique: A survey. arXiv 2018, arXiv:1804.06196. [Google Scholar]
- Mohan, P.V.; Dixit, S.; Gyaneshwar, A.; Chadha, U.; Srinivasan, K.; Seo, J.T. Leveraging Computational Intelligence Techniques for Defensive Deception: A Review, Recent Advances, Open Problems and Future Directions. Sensors 2022, 22, 2194. [Google Scholar] [CrossRef]
- Heckman, K.E.; Stech, F.J.; Thomas, R.K.; Schmoker, B.; Tsow, A.W. Cyber Denial, Deception and Counter Deception. In Advances in Information Security; Springer International Publishing: New York, NY, USA, 2015; ISBN 978-3-319-25131-8. [Google Scholar]
- Heckman, K.E.; Stech, F.J.; Schmoker, B.S.; Thomas, R.K. Denial and Deception in Cyber Defense. Computer 2015, 48, 36–44. [Google Scholar] [CrossRef]
- Al Amin, M.A.R.; Shetty, S.; Njilla, L.; Tosh, D.K.; Kamhoua, C. Hidden markov model and cyber deception for the prevention of adversarial lateral movement. IEEE Access 2021, 9, 49662–49682. [Google Scholar] [CrossRef]
- Cho, J.H.; Sharma, D.P.; Alavizadeh, H.; Yoon, S.; Ben-Asher, N.; Moore, T.J.; Kim, D.S.; Lim, H.; Nelson, F.F. Toward Proactive, Adaptive Defense: A Survey on Moving Target Defense. IEEE Commun. Surv. Tutor. 2020, 22, 709–745. [Google Scholar] [CrossRef] [Green Version]
- Pawlick, J.; Colbert, E.; Zhu, Q. A game-theoretic taxonomy and survey of defensive deception for cybersecurity and privacy. ACM Comput. Surv. 2019, 52, 1–28. [Google Scholar] [CrossRef] [Green Version]
- Park, K.; Woo, S.; Moon, D.; Choi, H. Secure cyber deception architecture and decoy injection to mitigate the insider threat. Symmetry 2018, 10, 14. [Google Scholar] [CrossRef] [Green Version]
- Cohen, F. The Use of Deception Techniques: Honeypots and Decoys Deception. Handb. Inf. Secur. 2006, 3, 646–655. [Google Scholar]
- Manadhata, P.K.; Wing, J.M. An attack surface metric. IEEE Trans. Softw. Eng. 2011, 37, 371–386. [Google Scholar] [CrossRef]
- Li, H.; Zheng, Z. Optimal Timing of Moving Target Defense: A Stackelberg Game Model. In Proceedings of the MILCOM 2019—2019 IEEE Military Communications Conference (MILCOM), Norfolk, VA, USA, 12–14 November 2019; pp. 1–6. [Google Scholar]
- Xie, Y.-X.; Ji, L.-X.; Li, L.-S.; Guo, Z.; Baker, T. An adaptive defense mechanism to prevent advanced persistent threats. Conn. Sci. 2021, 33, 359–379. [Google Scholar] [CrossRef]
- Ferguson-Walter, K.; Mauger, J.; Fugate, S.; Major, M. Game theory for adaptive defensive cyber deception. In Proceedings of the 6th Annual Symposium on Hot Topics in the Science of Security, Nashville, TN, USA, 1–3 April 2019; pp. 1–8. [Google Scholar]
- Hu, H.; Liu, J.; Tan, J.; Liu, J. SOCMTD: Selecting Optimal Countermeasure for Moving Target Defense Using Dynamic Game. KSII Trans. Internet Inf. Syst. 2020, 14, 4157–4175. [Google Scholar]
- Lei, C.; Ma, D.H.; Zhang, H.Q. Optimal strategy selection for moving target defense based on markov game. IEEE Access 2017, 5, 156–169. [Google Scholar] [CrossRef]
- Xiong, X.L.; Yang, L.; Zhao, G.S. Effectiveness Evaluation Model of Moving Target Defense Based on System Attack Surface. IEEE Access 2019, 7, 9998–10014. [Google Scholar] [CrossRef]
- Zheng, J.; Siami Namin, A. A Markov Decision Process to Determine Optimal Policies in Moving Target. In Proceedings of the 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, ON, Canada, 15–19 October 2018; pp. 2321–2323. [Google Scholar]
- Maleki, H.; Valizadeh, S.; Koch, W.; Bestavros, A.; Van Dijk, M. Markov modeling of moving target defense games. In Proceedings of the 2016 ACM Workshop on Moving Target Defense, Vienna, Austria, 24 October 2016; pp. 81–92. [Google Scholar]
- Sengupta, S.; Kambhampati, S. Multi-agent Reinforcement Learning in Bayesian Stackelberg Markov Games for Adaptive Moving Target Defense. arXiv 2020, arXiv:2007.10457. [Google Scholar]
- Sengupta, S.; Chakraborti, T.; Kambhampati, S. MTDeep: Boosting the Security of Deep Neural Nets Against Adversarial Attacks with Moving Target Defense. arXiv 2019, arXiv:1705.07213v3. [Google Scholar]
- Qian, Y.; Shao, Q.; Wang, J.; Lin, X.; Guo, Y.; Gu, Z.; Wang, B.; Wu, C. EI-MTD:Moving Target Defense for Edge Intelligence against Adversarial Attacks. arXiv 2020, arXiv:2009.10537. [Google Scholar]
- Amich, A.; Eshete, B. Morphence: Moving Target Defense against Adversarial Examples. In Proceedings of the Annual Computer Security Applications Conference, Austin, TX, USA, 6–10 December 2021; pp. 61–75. [Google Scholar]
- Xu, X.; Hu, H.; Liu, Y.; Tan, J.; Zhang, H. Moving target defense of routing randomization with deep reinforcement learning against eavesdropping attack. Digit. Commun. Networks. 2022, 8, 1–19. [Google Scholar] [CrossRef]
- Song, Q.; Yan, Z.; Tan, R. DeepMTD: Moving Target Defense for Deep Visual Sensing against Adversarial Examples. ACM Trans. Sens. Networks 2021, 18, 5. [Google Scholar] [CrossRef]
- Yoon, S.; Cho, J.H.; Kim, D.S.; Moore, T.J.; Free-Nelson, F.; Lim, H. DESOLATER: Deep Reinforcement Learning-Based Resource Allocation and Moving Target Defense Deployment Framework. IEEE Access 2021, 9, 70700–70714. [Google Scholar] [CrossRef]
- Huang, Y.; Huang, L.; Zhu, Q. Reinforcement Learning for feedback-enabled cyber resilience. Annu. Rev. Control 2022, 1–52. [Google Scholar] [CrossRef]
- Kim, S.; Yoon, S.; Cho, J.H.; Kim, D.S.; Moore, T.J.; Free-Nelson, F.; Lim, H. DIVERGENCE: Deep Reinforcement Learning-based Adaptive Traffic Inspection and Moving Target Defense Countermeasure Framework. IEEE Trans. Netw. Serv. Manag. 2021, 1–14. [Google Scholar] [CrossRef]
- Kim, S.; Yoon, S.; Lim, H. Deep Reinforcement Learning-Based Traffic Sampling for Multiple Traffic Analyzers on Software-Defined Networks. IEEE Access 2021, 9, 47815–47827. [Google Scholar] [CrossRef]
- Lockheed Martin. GAINING THE ADVANTAGE, Applying Cyber Kill Chain Methodology to Network Defense. Available online: https://www.lockheedmartin.com/content/dam/lockheed-martin/rms/documents/cyber/Gaining_the_Advantage_Cyber_Kill_Chain.pdf (accessed on 15 April 2022).
- Potteiger, B.; Zhang, Z.; Cheng, L.; Koutsoukos, X. A Tutorial on Moving Target Defense Approaches within Automotive Cyber-Physical Systems. Front. Futur. Transp. 2022, 2, 792573. [Google Scholar] [CrossRef]
- Kanellopoulos, A.; Vamvoudakis, K.G. A Moving Target Defense Control Framework for Cyber-Physical Systems. IEEE Trans. Automat. Contr. 2020, 65, 1029–1043. [Google Scholar] [CrossRef]
- Brown, R.; Marti, A.; Jenkins, C.; Shannigrahi, S. Dynamic Address Validation Array (DAVA): A Moving Target Defense Protocol for CAN bus. In Proceedings of the 7th ACM Workshop on Moving Target Defense, Virtual Event, USA, 9 November 2020; pp. 11–19. [Google Scholar]
- Woo, S.; Moon, D.; Youn, T.Y.; Lee, Y.; Kim, Y. CAN ID Shuffling Technique (CIST): Moving Target Defense Strategy for Protecting In-Vehicle CAN. IEEE Access 2019, 7, 15521–15536. [Google Scholar] [CrossRef]
- Liu, H.; Wang, S.; Li, Y. Event-Triggered Control and Proactive Defense for Cyber-Physical Systems. IEEE Trans. Syst. Man, Cybern. Syst. 2022, 1–9. [Google Scholar] [CrossRef]
- Wan, Z.; Cho, J.-H.; Zhu, M.; Anwar, A.H.; Kamhoua, C.; Singh, M.P. Foureye: Defensive Deception based on Hypergame Theory Against Advanced Persistent Threats. arXiv 2021, arXiv:2101.02863. [Google Scholar] [CrossRef]
- Huang, S.; Zhang, H.; Wang, J.; Huang, J. Markov Differential Game for Network Defense Decision-Making Method. IEEE Access 2018, 6, 39621–39634. [Google Scholar] [CrossRef]
- Zhu, Q.; Basar, T. Game-theoretic approach to feedback-driven multi-stage moving target defense. In Proceedings of the International Conference on Decision and Game Theory for Security, Fort Worth, TX, USA, 11–12 November 2013; pp. 246–263. [Google Scholar]
- Ge, L.; Yu, W.; Shen, D.; Chen, G.; Pham, K.; Blasch, E.; Lu, C. Toward effectiveness and agility of network security situational awareness using moving target defense (MTD). In Sensors and Systems for Space Applications VII, Proceedings of the SPIE DEFENSE + SECURITY, Baltimore, MD, USA, 5–9 May 2014; SPIE: Bellingham, WA, USA, 2014; Volume 9085, pp. 1–9. [Google Scholar]
- Mireles, J.D.; Ficke, E.; Cho, J.H.; Hurley, P.; Xu, S. Metrics towards measuring cyber agility. IEEE Trans. Inf. Forensics Secur. 2019, 14, 3217–3232. [Google Scholar] [CrossRef] [Green Version]
- Neti, S.; Somayaji, A.; Locasto, M.E. Software diversity: Security, entropy and game theory. In Proceedings of the 7th USENIX conference on Hot Topics in Security, Bellevue, WA, USA, 7 August 2012; pp. 1–6. [Google Scholar]
- Wright, M.; Venkatesan, S.; Albanese, M.; Wellman, M.P. Moving Target Defense against DDoS Attacks. In Proceedings of the 2016 ACM Workshop on Moving Target Defense, Vienna, Austria, 24 October 2016; pp. 93–104. [Google Scholar]
- Carter, K.M.; Riordan, J.F.; Okhravi, H. A game theoretic approach to strategy determination for dynamic platform defenses. In Proceedings of the Conference on Computer and Communications Security, Scottsdale, AZ, USA, 3–7 November 2014; pp. 21–30. [Google Scholar]
- Colbaugh, R.; Glass, K. Predictability-oriented defense against adaptive adversaries. In Proceedings of the 2012 IEEE International Conference on Systems, Man, and Cybernetics (SMC), Seoul, Korea, 14–17 October 2012; pp. 2721–2727. [Google Scholar]
- Hasan, M.M.; Rahman, M.A. Protection by Detection: A Signaling Game Approach to Mitigate Co-Resident Attacks in Cloud. In Proceedings of the 2017 IEEE 10th International Conference on Cloud Computing (CLOUD), Honololu, HI, USA, 25–30 June 2017; pp. 552–559. [Google Scholar]
- Feng, X.; Zheng, Z.; Cansever, D.; Swami, A.; Mohapatra, P. A signaling game model for moving target defense. In Proceedings of the IEEE INFOCOM 2017-IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar]
- Zhu, Q.; Clark, A.; Poovendran, R.; Basar, T. Deceptive routing games. In Proceedings of the 2012 IEEE 51st IEEE Conference on Decision and Control (CDC), Maui, HI, USA, 10–13 December 2012; pp. 2704–2711. [Google Scholar]
- Sengupta, S.; Vadlamudi, S.G.; Kambhampati, S.; Doupé, A.; Zhao, Z.; Taguinod, M.; Ahn, G.J. A game theoretic approach to strategy generation for moving target defense in web applications. In Proceedings of the 16th International Conference on Autonomous Agents and Multiagent Systems, AAMAS 2017, Sao Paulo, Brazil, 8–12 May 2017; Volume 1, pp. 178–186. [Google Scholar]
- Sengupta, S.; Chowdhary, A.; Huang, D.; Kambhampati, S. General Sum Markov Games for Strategic Detection of Advanced Persistent Threats Using Moving Target Defense in Cloud Networks. In International Conference on Decision and Game Theory for Security; Springer: New York, NY, USA, 2019; pp. 492–512. [Google Scholar]
- Li, H.; Shen, W.; Zheng, Z. Spatial-Temporal Moving Target Defense: A Markov Stackelberg Game Model. arXiv 2020, arXiv:2002.10390. [Google Scholar]
- Seo, S.; Kim, D. OSINT-based LPC-MTD and HS-decoy for organizational defensive deception. Appl. Sci. 2021, 11, 3402. [Google Scholar] [CrossRef]
- Seo, S.; Kim, D. SOD2G: A Study on a Social-Engineering Organizational Defensive Deception Game Framework through Optimization of Spatiotemporal MTD and Decoy Conflict. Electronics 2021, 10, 3012. [Google Scholar] [CrossRef]
- Manadhata, P.K. Game Theoretic Approaches to Attack Surface Shifting. In Moving Target Defense II; Springer: New York, NY, USA, 2013; pp. 1–13. [Google Scholar]
- Zhang, H.; Zheng, K.; Wang, X.; Luo, S.; Wu, B. Strategy selection for moving target defense in incomplete information game. Comput. Mater. Contin. 2020, 62, 763–786. [Google Scholar] [CrossRef]
- Navas, R.E.; Cuppens, F.; Boulahia Cuppens, N.; Toutain, L.; Papadopoulos, G.Z. Physical resilience to insider attacks in IoT networks: Independent cryptographically secure sequences for DSSS anti-jamming. Comput. Netw. 2021, 187, 107751. [Google Scholar] [CrossRef]
- Ge, M.; Cho, J.H.; Kim, D.S.; Dixit, G.; Chen, I.R. Proactive defense for internet-of-Things: Integrating moving target defense with cyberdeception. arXiv 2020, arXiv:2005.04220. [Google Scholar] [CrossRef]
- Nizzi, F.; Pecorella, T.; Esposito, F.; Pierucci, L.; Fantacci, R. IoT security via address shuffling: The easy way. IEEE Internet Things J. 2019, 6, 3764–3774. [Google Scholar] [CrossRef] [Green Version]
- Zeitz, K.; Cantrell, M.; Marchany, R.; Tront, J. Changing the game: A micro moving target IPv6 defense for the internet of things. IEEE Wirel. Commun. Lett. 2018, 7, 578–581. [Google Scholar] [CrossRef]
- Navas, R.E.; Sandaker, H.; Cuppens, F.; Cuppens, N.; Toutain, L.; Papadopoulos, G. IANVS: A moving target defense framework for a resilient Internet of Things. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–6. [Google Scholar]
- Kyi, W.; Oo, K. A Framework of Moving Target Defenses for the Internet of Things. Bull. Netw. Comput. Syst. Softw. 2019, 8, 104–107. [Google Scholar]
- Mercado-Velazquez, A.A.; Escamilla-Ambrosio, P.J.; Ortiz-Rodriguez, F. A Moving Target Defense Strategy for Internet of Things Cybersecurity. IEEE Access 2021, 9, 118406–118418. [Google Scholar] [CrossRef]
- Van Dijk, M.; Juels, A.; Oprea, A.; Rivest, R.L. FlipIt: The game of “stealthy takeover”. J. Cryptol. 2013, 26, 655–713. [Google Scholar] [CrossRef] [Green Version]
- Tan, J.L.; Tan, J.L.; Zhang, H.W.; Zhang, H.W.; Zhang, H.Q.; Zhang, H.Q.; Lei, C.; Lei, C.; Jin, H.; Jin, H.; et al. Optimal Timing Selection Approach to Moving Target Defense: A FlipIt Attack-Defense Game Model. Secur. Commun. Netw. 2020, 2020, 3151495. [Google Scholar] [CrossRef]
- Tan, J.; Zhang, H.; Zhang, H.; Hu, H.; Lei, C.; Qin, Z. Optimal temporospatial strategy selection approach to moving target defense: A FlipIt differential game model. Comput. Secur. 2021, 108, 102342. [Google Scholar] [CrossRef]
- Singh, R.; Dwivedi, A.D.; Srivastava, G.; Wiszniewska-Matyszkiel, A.; Cheng, X. A game theoretic analysis of resource mining in blockchain. Cluster Comput. 2020, 23, 2035–2046. [Google Scholar] [CrossRef] [Green Version]
- Zhou, J.; Cui, G.; Hu, S.; Zhang, Z.; Yang, C.; Liu, Z.; Wang, L.; Li, C.; Sun, M. Graph neural networks: A review of methods and applications. AI Open 2020, 1, 57–81. [Google Scholar] [CrossRef]
| Approach | Specific Technique | Advantages | Disadvantages |
|---|---|---|---|
| Game-Enabled Defensive Deception Techniques with MTD [43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59] | General game, Bayesian Stackelberg game, Stochastic game | Formalizing the interactions between attackers and defenders and providing methodologies for estimating deception effectiveness and security. Determining the optimal MTD strategy based on learning and realizing the decision model. | Not working the best strategy devised by defender for the irrational attacker. Requires very high number of deriving computational resources for the optimal solution space. Causing uncertainty because of interpreting the same game differently depending on their subjective perception of different players. Difficulty in modeling cybersecurity and defensive cyber deception issues in real-world and practical environments. |
| MTD-based Defensive Deception Techniques for IoT [60,61,62,63,64,65,66] | Definition of IoT-enabled MTD strategy, Construction of IoT framework with MTD scheme | Securing an avoidance-based, independent-adaptive mobility-type countermeasure for attenuation of the explosively increased attack-detection surfaces in heterogeneous IoT networks. Breaking down the spatiotemporal dominance of attackers in static and passive IoT systems. Reducing organizational operating costs for deploying security solutions dedicated to IoT. Adopted as the most core security game-changer for special IoT domains with insecure communication channels | MTD performance constraints occur due to limited and non-uniform resource allocation within IoT-based organizational environments. Due to the characteristics of interconnected heterogeneous IoT communications, the consistency of the efficiency of MTD-based proactive defense cannot be maintained. Not suitable for extremely lightweight IoT communication domains. Not mapped to free IoT node joining and leaving processes |
| IoDM |
| Description and Improvement | |
| The IoT-enabled organizational MTD is the concept of using an MTD strategy to select appropriate mutation periods and intensities, and targets by IoT domain. Furthermore, this MTD determines the sampling techniques and shuffling schemes with the advantage of the defender. Through the definition of these adaptive IoT-enabled MTD, optimized MTD strategies can be secured by IoT domain and related mutation metric, and reactive tactics within the MTD for the defender to carry out in-depth deception can be realized. The IoT-enabled organizational decoy is a concept of induction of CKC attacker cognitive disturbance consisting of layered false organizational information based on certified IoT CVE and IoV information, which standardizes the decoy elements, properties, and targets based on unique characteristics by IoT domain, and optimizes the decoy induction pathways allowable values. Through the definition of active IoT-enabled decoys, the usability and scalability of the decoy sandbox in the IoT environment can also be improved. The organizational IoDM model is a two IoT player competitive game mainly composed of PBNE, BSSG, partial signaling-based general sun game foreground components, and POMDP state-transition background components and a real-time attack–defense process within an IoT organization operating environment with limited resources was representatively configured as multi-staged spatiotemporal deception decision-making. | |||
| State | Probability of Transition 1 in Scenario 1 | Reward Value for Defender |
|---|---|---|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Seo, S.; Kim, D. IoDM: A Study on a IoT-Based Organizational Deception Modeling with Adaptive General-Sum Game Competition. Electronics 2022, 11, 1623. https://doi.org/10.3390/electronics11101623
Seo S, Kim D. IoDM: A Study on a IoT-Based Organizational Deception Modeling with Adaptive General-Sum Game Competition. Electronics. 2022; 11(10):1623. https://doi.org/10.3390/electronics11101623
Chicago/Turabian StyleSeo, Sang, and Dohoon Kim. 2022. "IoDM: A Study on a IoT-Based Organizational Deception Modeling with Adaptive General-Sum Game Competition" Electronics 11, no. 10: 1623. https://doi.org/10.3390/electronics11101623
APA StyleSeo, S., & Kim, D. (2022). IoDM: A Study on a IoT-Based Organizational Deception Modeling with Adaptive General-Sum Game Competition. Electronics, 11(10), 1623. https://doi.org/10.3390/electronics11101623







