1. Introduction
As a result of rapid advancements in the field of micro-electro-mechanical systems (MEMS), small sensor nodes have become inexpensive and self-sufficient [
1]. These sensor nodes can sense and monitor the environment, analyze and aggregate data, and communicate data to one other or to a central point, commonly known as the sink. Sensor nodes can be interconnected to serve an application-specific purpose through the use of wireless sensor networks (WSN) [
2,
3].
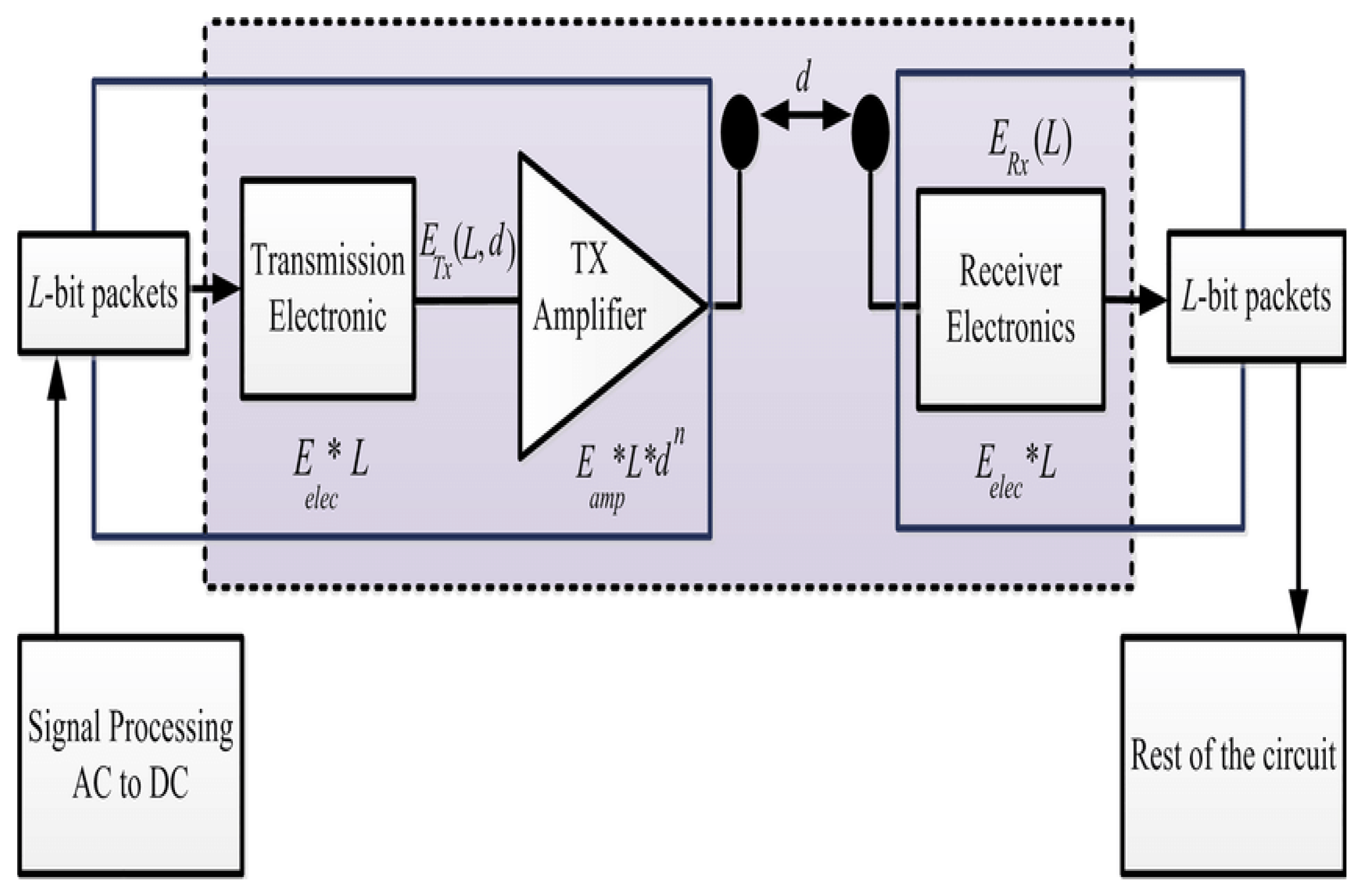
Sensor nodes have a certain amount of battery power, and these batteries are rarely rechargeable. Sensor nodes often use the most energy for their communication functions [
4]. When a node’s energy source runs out, the node is declared dead and is no longer useful. WSNs can be used in a wide variety of real-world situations. They are employed in a variety of fields, including agriculture, industry, health care, surveillance, target tracking, and security management, in both the civilian and military sectors [
5,
6,
7].
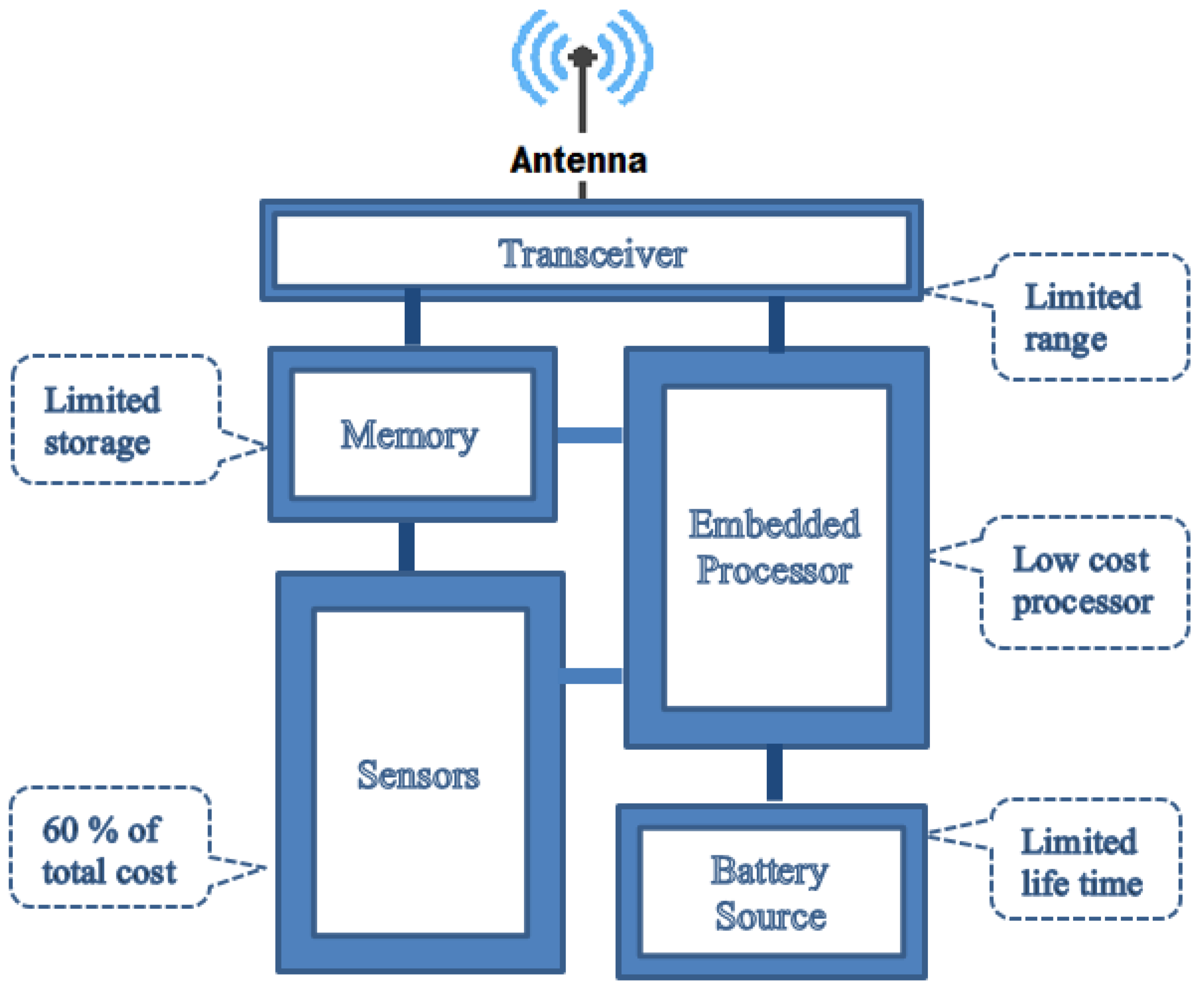
Figure 1 shows a typical sensor node block diagram [
8].
Sensor nodes have the ability to send their collected data straight to the sink node [
9], but this consumes more energy and leads to the premature death of the node; as a result, other issues are introduced into the network, such as the coverage/hole problem [
10]. Using clustering, sensor nodes can be balanced in terms of energy consumption. Clustering is based on putting together nodes that are near each other or have similar characteristics or functions. Cluster heads (CH) and member nodes (MN) are the two types of nodes that make up a cluster. MNs gather information from the environment and send it to the CH. Additionally, CHs collect, compress, and send data to the sink node.
Direct communication between CH and sink node is possible, as well as communication involving multiple hops [
11]. In general, CHs use more energy than MNs. The CH role must be rotated between network nodes in order to maintain a stable overall network energy level while also extending the network’s life span [
12]. For the creation, operation, and maintenance of clusters, numerous protocols have been designed. A number of them, such as low energy adaptive clustering hierarchy (LEACH) and stable election protocol (SEP), can be found in the literature [
13]. Clustering and routing protocols in WSNs have a problem in that they cannot reduce the overall network energy and balance energy consumption among sensor nodes over the network’s lifetime [
11]. In some cases, a significant reduction in the overall energy consumption of the network is achieved at the expense of unequal remaining energies among sensor points. In other cases, balancing the remaining energies of sensor nodes is achieved at the expense of increasing the overall energy consumed by the network.
WSNs use meta-heuristics algorithms, which are also known as nature-inspired algorithms, or intelligent optimization algorithms, to balance energy consumption among sensor nodes while also reducing overall energy consumption [
14,
15]. This trade-off has proven to be successful. There are four types of meta-heuristic algorithms: bio-inspired, human-inspired, geography-inspired, and physics-inspired. The biological system is the source of inspiration for the vast majority of nature-inspired algorithms. The bio-inspired algorithms are further classified into three categories, namely evolutionary, swarm-based and plant-based [
16,
17]. The genetic algorithm (GA) is a meta-heuristic, bio-inspired and evolutionary technique, which is widely used in WSNs to solve fundamental problems, such as sensor node localization, energy efficient clustering, data aggregation and optimal coverage [
18]. With GA, the number of clusters in the network can be optimized, and sensor node energy consumption can be balanced, allowing the WSN to operate for longer time periods. In lieu of two-dimensional WSN (2D-WSN), three-dimensional WSN (3D-WSN) is being researched because it is more realistic than 2D-WSN since the third dimension is crucial in determining the WSN’s lifespan [
5].
GA is made up of three main components: selection, crossover, and mutation. The selection operator is responsible for the production of the next generation; crossover and mutation are responsible for the manipulation of the selected individuals to form the next generation. The mechanism of selection determines which individuals are selected for reproduction (mating) and how many offspring each selected individual produces. The selection strategy’s core principle is that the better an individual is, the greater the likelihood that it will be a parent. As a rule of thumb, crossover and mutation expand the search area, while selection narrows the search area within a population by eliminating poor solutions [
19].
This study has the following contributions: First, the central dynamic clustering protocol based on GA for extending the 3D WSN stability period is proposed. Second, six GA selection operators are utilized, evaluated and compared for better reliability and maximum network life time. Three, a new GA fitness function is used to optimize the number of clusters in the network, which essentially includes information about the type of connections that MNs establish with CHs in a cluster and CHs establish with the sink in the network.
The rest of the paper is organized as follows:
Section 2 overviews the related work.
Section 3 describes the GA operators’ details. In
Section 4, the simulation setup and configuration are provided. The simulation results are explained in
Section 5. Finally, we conclude our research and provide some future work in
Section 6.
2. Related Work
Energy conservation in WSN is critical for extending the lifetime and ensuring the smooth operation of resource-constrained nodes in the network. Many techniques are proposed in the literature to increase the lifespan and reliability of WSNs. Clustering/routing, mobile relays and sinks, optimal node deployment, data correlation, energy harvesting, beamforming, and various optimization techniques are among them [
20,
21]. In the following sections, we limit our related work to optimization techniques that use nature-inspired algorithms, specifically the GA. There are numerous studies that used meta-heuristic algorithms to extend the life of WSNs. GA has demonstrated a wide range of applicability and solutions in WSNs. An energy-efficient clustering protocol (GAEEC) was proposed by the authors in [
22], which divided the network into optimal numbers of clusters using GA before using GA again to select the appropriate node within a cluster as a CH, depending on its fitness function per algorithm round. They found that their protocol outperformed the current renowned LEACH protocol in terms of network throughput and stability. The authors in [
23] proposed GAECH, a GA-based energy-efficient clustering hierarchy protocol whose goal is to reduce overall network energy consumption while also extending the network’s lifespan. When the sink node is located outside the network area, their results show a significant increase in network life time compared to other well-known clustering protocols. Using genetic algorithms for energy-efficient clustering and routing in 3D WSNs, the authors in [
8] proposed PEGASIS protocol variants. GA was used to create data transmission chains with a remarkably short overall length. An improved method for devising CHs that takes distance and remaining energy into account was developed. Their results showed that the normal PEGASIS protocol was superior in terms of the first-node-die (FND) metric, compared to other well-known protocols. The fuzzy C-means genetic algorithm (FCM-GA) protocol was proposed by the authors in [
24]. Two phases make up the protocol. First, clustering is done using FCM based on three objectives: the appropriate distribution of online energy among each cluster, the distances within each cluster, and the separation between each CH and the sink. As compared to other protocols, such as direct transmission, SH-MEER, and MH-FEER, the FCM-GA results show significant gains in terms of both network throughput and life span. In [
25], the authors proposed an improved version of the LEACH protocol (O-LEACH). When determining the best route, O-LEACH relies on GA for selecting the best route. As a result, their energy usage was reduced by
.
To the best of our knowledge, no research has been done on the impact of using different GA selection operators on 3D-WSN reliability, lifetime and energy conservation. The following studies looked at and compared the outcomes of using GA selection operators in other domains. Using different parent selection strategies, the authors in [
26] compared the GA’s performance in solving the traveling salesman problem (TSP). The results show that the tournament selection strategy outperforms proportional roulette wheel and rank-based roulette wheel selections, achieving the best solution quality with the lowest computing times, in several TSP tests. The results also show that tournament and proportional roulette wheel selection can be superior to rank-based roulette wheel selection only for smaller problems and can become susceptible to premature convergence as the problem size increases. To solve the network topology design problem, the authors in [
27] employed three different selection strategies: tournament, ranking, or the use of a roulette wheel. They were compared in terms of quality of solution and computation time. For a 10-node network, tournament selection yielded the best solution in terms of quality and computation time, while ranking and scaling delivered the worst solution in terms of quality and computation time. The solution quality of ranking and scaling was equal to that of tournament selection for networks with 21 and 36 nodes, but tournament outperformed ranking and scaling when it came to computation time.
3. Genetic Algorithm Overview
GA is a stochastic, meta-heuristic optimization algorithm. GA is made up of three different operators: selection, crossover, and mutation. The GA solution is encoded in a binary string known as chromosome. The elements of a chromosome are referred to as genes. The number of genes on each chromosome should be the same. An objective function is used to assess a chromosome’s fitness value. The term population refers to a grouping of chromosomes [
19].
GA is an iterative process. It uses the three operators at each run to find new chromosomes that may produce a better solution; see Algorithm 1. The GA operators are as follows:
Selection operator: Parents with higher fitness values are chosen to produce the next generation’s offspring. Some examples of selection operators include roulette wheel, tournament, and stochastic universal sampling.
Crossover operator: To produce new offspring, the genes of the two chosen parents are merged. In this phase, uniform-point, single-point, and double-point methods are used separately or collectively.
Mutation operator: To diversify the search space, single or multiple gene modifications are applied to newly produced chromosomes.
Algorithm 1 shows a typical execution of a simple GA.
| Algorithm 1 Simple GA process. |
- 1:
Set parameters - 2:
Choose encode method - 3:
Generate the initial population - 4:
while & do - 5:
Fitness calculation - 6:
Selection - 7:
Crossover - 8:
Mutation - 9:
end while - 10:
Decode the individual with max. fitness - 11:
Return the best solution
|
The selection operator has the most effect in directing the GA toward the optimal solution and narrowing the search space. Moreover, it aims to exploit the best characteristics of good candidate solutions in order to improve these solutions over generations. This should, in theory, guide the GA to converge to an acceptable and satisfactory solution of the optimization problem at hand. However, despite decades of research, there are no general guidelines or theoretical support for how to choose a good selection method for each problem. This can be a serious issue because a poor selection operator can lead to poor performance of the GA in terms of both speed and reliability [
28].
Six different selection operators are utilized in this research to evaluate the performance of 3D WSN, namely [
19]: the roulette wheel selection (RWS), the linear rank selection (LRS), the exponential rank selection (ERS), the stochastic universal sampling (SUS), the tournament selection (TOS), and the truncation selection (TRS). All of the algorithms steps are shown in MATLAB as pseudo-code.
Roulette wheel selection (RWS): The distinguishing feature of this selection method is that it assigns a probability
of selection to each chromosome
i in the current population, proportional to its fitness value
as shown in the following expression.
The population size is denoted by n. Algorithm 2 shows the RWS pseudo-code.
It should be noted that a well-known disadvantage of this technique is the risk of the GA converging to a local optimum too soon, due to the presence of a dominant individual who always wins the competition and is chosen as a parent.
Linear rank selection (LRS): This is variant of RWS that attempts to overcome the disadvantage of the premature convergence of the GA to a local optimum. It is based on a chromosome’s rank rather than its fitness. The best chromosome receives rank
n, while the worst individual receives rank 1. As a result, each chromosome has the probability of being chosen given by the following expression:
Algorithm 3 shows the LRS pseudo-code.
Exponential rank selection (ERS): It is based on the same principle as the LRS, but it varies slightly from the LRS in terms of the probability of selecting each individual. This probability is given by the expression
where
w is the exponent base, a typical value of
. Algorithm 4 shows the ERS pseudo-code.
Stochastic universal sampling (SUS): SUS is roughly equivalent to RWS. The only difference is that instead of a single fixed point, we have several fixed points. As a result, all of the parents are chosen at random from a single spin of the wheel based on their fitness value. Furthermore, such a setup encourages the most highly fit chromosome to be chosen at least once in a spin. Algorithm 5 shows the SUS pseudo-code.
Tournament selection (TOS): This is a type of ranking-based selection method. Its basic idea is to pick a group of k chromosomes at random. These chromosomes are then ranked based on their relative fitness, with the fittest being chosen for reproduction. TOS is a popular method of selection in evolutionary algorithms. It works well for a wide range of problems, it is easy to implement, and it is parallelizable. Algorithm 6 shows the TOS pseudo-code.
Truncation selection (TRS): The TRS method sorts chromosomes based on their fitness value. Only the best chromosomes are chosen to be the parents of the next new population. The main parameter for truncation selection is the TRS threshold. It denotes the specified proportion of the population to be chosen as parents, with values ranging from to . Individuals who fall below the TRS threshold do not reproduce and are discarded. Algorithm 7 shows the TRS pseudo-code.
| Algorithm 2 GA RWS technique. |
- 1:
n: number of chromosomes in the population - 2:
c: vector of chromosomes’ fitness values - 3:
- 4:
- 5:
- 6:
- 7:
- 8:
▹ - 9:
- 10:
|
| Algorithm 3 GA LRS technique. |
- 1:
n: number of chromosomes in the population - 2:
c: vector of chromosomes’ fitness values - 3:
▹ vector of ranks - 4:
- 5:
- 6:
- 7:
- 8:
- 9:
- 10:
|
| Algorithm 4 GA ERS technique. |
- 1:
n: number of chromosomes in the population - 2:
c: vector of chromosomes’ fitness values - 3:
▹ vector of ranks - 4:
- 5:
- 6:
- 7:
- 8:
- 9:
- 10:
|
| Algorithm 5 GA SUS technique. |
- 1:
n: number of chromosomes in the population - 2:
c: vector of chromosomes’ fitness values - 3:
m: # of fixed points - 4:
- 5:
- 6:
- 7:
- 8:
- 9:
▹ vector of m values
|
| Algorithm 6 GA TOS technique. |
- 1:
n: number of chromosomes in the population - 2:
c: vector of chromosomes’ fitness values - 3:
m: # of parents to choose - 4:
q: # of selected parents - 5:
- 6:
- 7:
- 8:
- 9:
▹ vector of q values
|
| Algorithm 7 GA TRS technique. |
- 1:
n: number of chromosomes in the population - 2:
c: vector of chromosomes’ fitness values - 3:
: TRS threshold ▹ ranges from to - 4:
- 5:
- 6:
- 7:
▹ vector of values
|
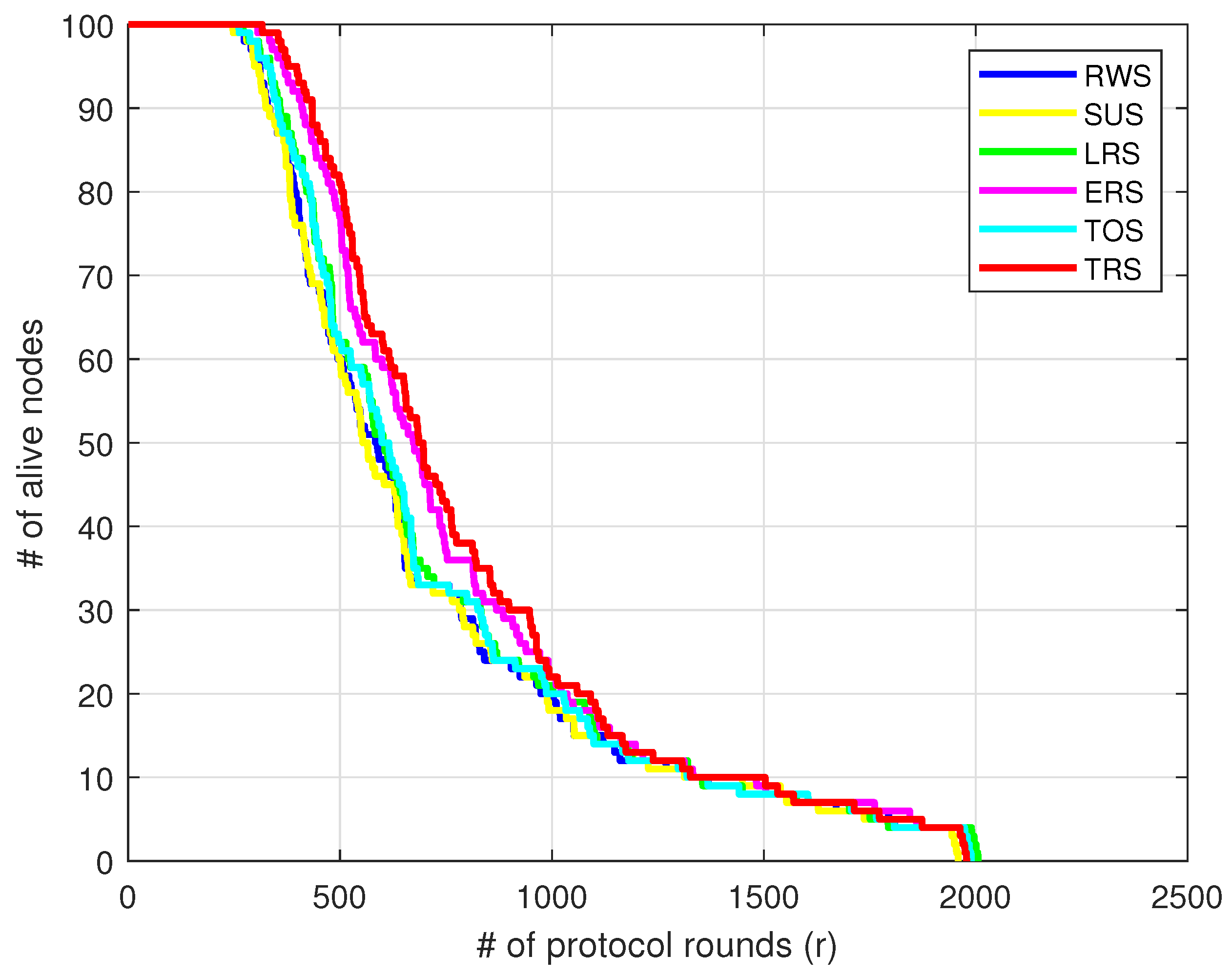
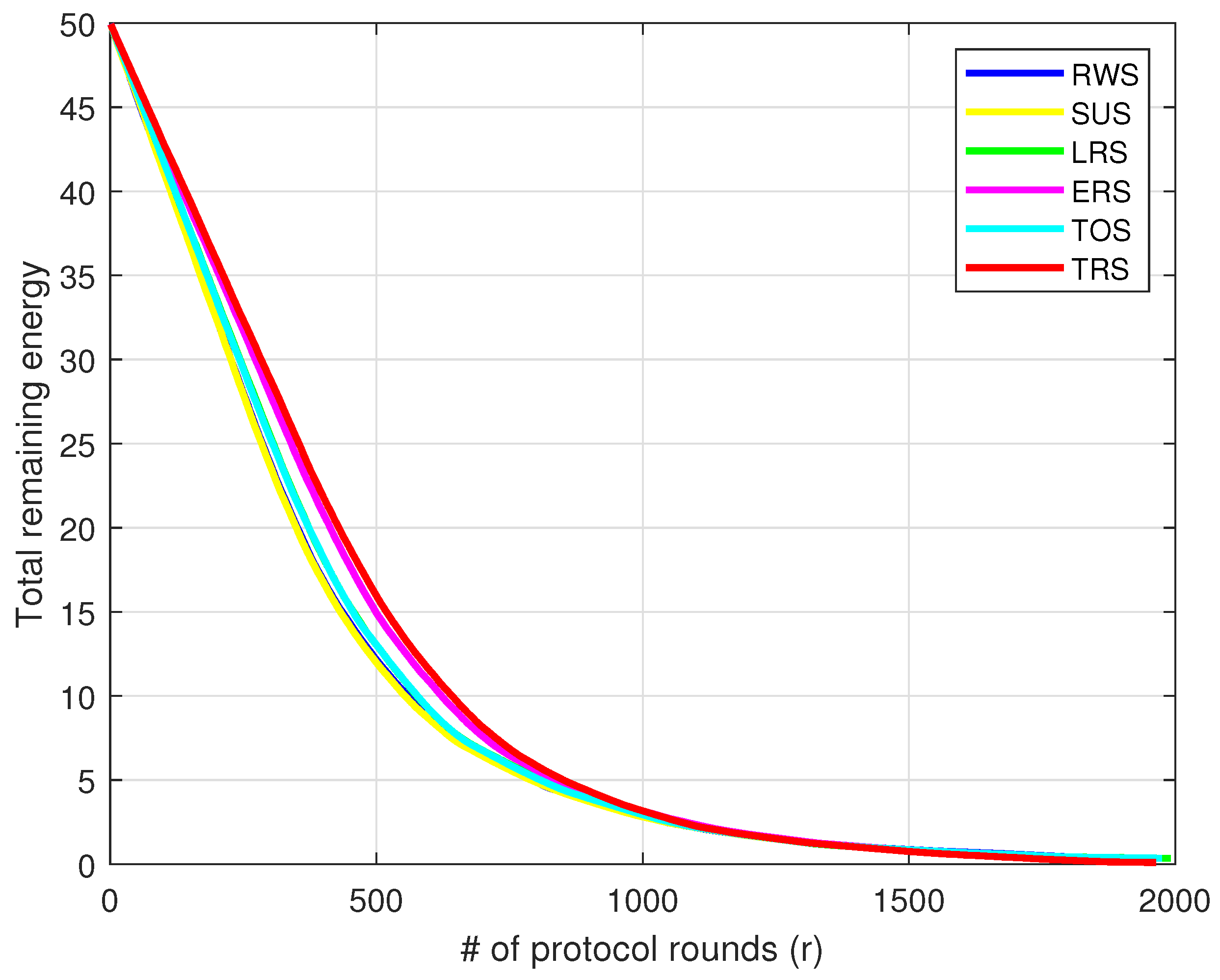
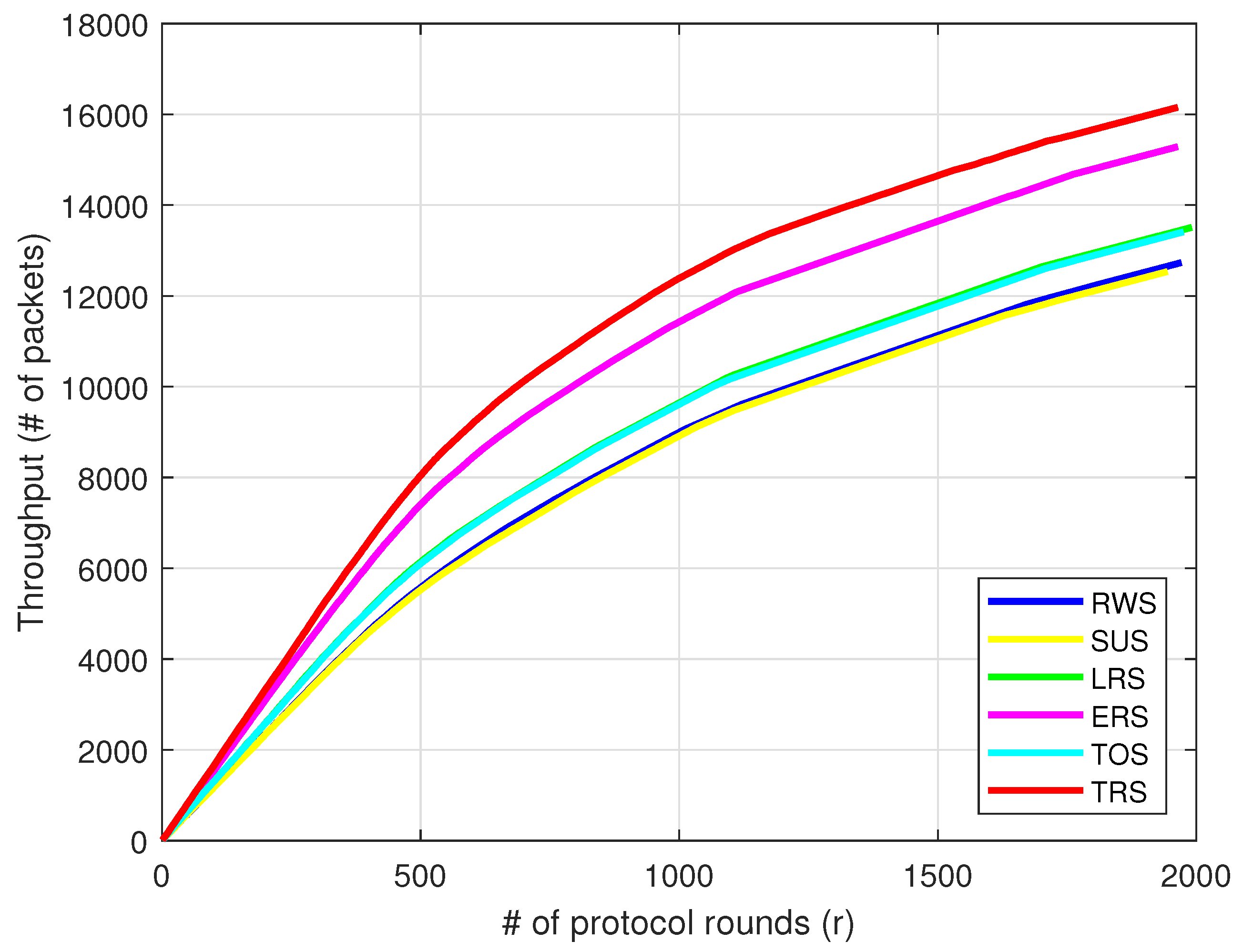
6. Conclusions and Future Work
This paper proposes a central dynamic clustering protocol based on GA for extending the 3D-WSN stability period. The GA algorithm makes use of six parental selection operators. Furthermore, in order to find the best solution, the performance of these operators is evaluated and compared in terms of network stability period and reliability, total remaining energy, and data throughput. The truncation operator is found to have the greatest impact on network stability period and reliability, followed by the exponential ranking operator. The truncation operator outperforms other selection operators, particularly the well-known and widely used roulette wheel operator, in the stability period and cumulative throughput at the sink node by and by , respectively. A number of challenges can be investigated for future work: First, a comparative study of different nature-inspired optimization algorithms, viz. ant colony optimization (ACO), particle swarm optimization (PSO), with the GA approach utilized in this paper to identify which optimization algorithm extends the network reliability and life time more. Second, the impact of different GA selection and crossover techniques can be studied to identify which selection/crossover techniques can be combined to further extend the network reliability and life time. Finally, the same research can be carried out in heterogeneous WSN. Nodes in this WSN have varying structures, capabilities, computational power, and energy storage. A new fitness function can be proposed to take advantage of these properties in order to increase the reliability and life time of heterogeneous WSNs.