UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies
Abstract
1. Introduction
Contributions of the Paper
- A comparison of varied drone forensic analysis.
- Address varied forensics tools capabilities related to the reliability, integrity, and recoverability of digital evidence.
- Explore digital evidence structure recovered from the two selected UAV models.
- Apply a three-dimensional (3D) visualization technique on the recovered flight trajectories for interpretation purposes.
2. Related Work
3. Methodology
4. Findings
4.1. Digital Forensic Tools Evaluation
4.2. Technical Investigative Challenges
4.3. Digital Evidence Integrity Using Open-Source Tools
5. Discussion
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- FAA. UAS by the Numbers. Available online: https://www.faa.gov/uas/resources/by_the_numbers/ (accessed on 13 February 2021).
- INTERPOL to Issue Drone Guidelines for First Responders. Available online: https://www.interpol.int/en/News-and-Events/News/2018/INTERPOL-to-issue-drone-guidelines-for-first-responders (accessed on 2 October 2020).
- Watson, S. Drone Forensic Program. Available online: https://dfrws.org/wp-content/uploads/2019/06/pres_drone_forensics_program.pdf (accessed on 15 March 2021).
- Clark, D.R.; Meffert, C.; Baggili, I.; Breitinger, F. DROP (DRone Open source Parser) your drone: Forensic analysis of the DJI Phantom III. Digit. Investig. 2017, 22, S3–S14. [Google Scholar] [CrossRef]
- Azhar, M.; Barton, T.E.A.; Islam, T. Drone forensic analysis using open source tools. J. Digit. Forensics Secur. Law 2018, 13, 6. [Google Scholar] [CrossRef][Green Version]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.K. RPAS forensic validation analysis towards a technical investigation process: A case study of yuneec typhoon H. Sensors 2019, 19, 3246. [Google Scholar] [CrossRef] [PubMed]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.; Al-Hazemi, F. Drone disrupted denial of service attack (3DOS): Towards an incident response and forensic analysis of remotely piloted aerial systems (RPASs). In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 704–710. [Google Scholar]
- Jain, U.; Rogers, M.; Matson, E.T. Drone forensic framework: Sensor and data identification and verification. In Proceedings of the IEEE Sensors Applications Symposium (SAS), Glassboro, NJ, USA, 13–15 March 2017; pp. 1–6. [Google Scholar]
- Kao, D.Y.; Chen, M.C.; Wu, W.Y.; Lin, J.S.; Chen, C.H.; Tsai, F. Drone Forensic Investigation: DJI Spark Drone as A Case Study. Procedia Comput. Sci. 2019, 159, 1890–1899. [Google Scholar] [CrossRef]
- Roder, A.; Choo, K.K.R.; Le-Khac, N.A. Unmanned aerial vehicle forensic investigation process: Dji phantom 3 drone as a case study. arXiv 2018, arXiv:1804.08649. [Google Scholar]
- Yu, Y.; Barthaud, D.; Price, B.A.; Bandara, A.K.; Zisman, A.; Nuseibeh, B. LiveBox: A Self-Adaptive Forensic-Ready Service for Drones. IEEE Access 2019, 7, 148401–148412. [Google Scholar] [CrossRef]
- Mirza, M.M.; Karabiyik, U. Enhancing IP Address Geocoding, Geolocating and Visualization for Digital Forensics. In Proceedings of the International Symposium on Networks, Computers and Communications (ISNCC): Trust, Security and Privacy (ISNCC-2021 TSP), Dubaï, United Arab Emirates, 1–3 June 2021. Manuscript Under Review. [Google Scholar]
- Horsman, G. Unmanned aerial vehicles: A preliminary analysis of forensic challenges. Digit. Investig. 2016, 16, 1–11. [Google Scholar] [CrossRef]
- Salamh, F.E.; Karabiyik, U.; Rogers, M.K. Constructive DIREST Threat Model and Threat Assessment Framework for Drone as a Service (DaaS). J. Digit. Forensics Secur. Law 2021, 16, 2. [Google Scholar]
- He, D.; Chan, S.; Guizani, M. Drone-Assisted Public Safety Networks: The Security Aspect. IEEE Commun. Mag. 2017, 55, 218–223. [Google Scholar] [CrossRef]
- Ma, C.; Yang, J.; Chen, J.; Qu, Z.; Zhou, C. Effects of a navigation spoofing signal on a receiver loop and a UAV spoofing approach. GPS Solut. 2020, 24, 1–13. [Google Scholar]
- Vasconcelos, G.; Carrijo, G.; Miani, R.; Souza, J.; Guizilini, V. The Impact of DoS Attacks on the AR.Drone 2.0. In Proceedings of the XIII Latin American Robotics Symposium and IV Brazilian Robotics Symposium (LARS/SBR), Recife, Brazil, 8–12 October 2016; pp. 127–132. [Google Scholar] [CrossRef]
- NIST: Drone Data Set. Available online: https://www.cfreds.nist.gov/drone-images.html (accessed on 15 March 2021).
- Technology, B. Autopsy—Basis Technology. Available online: https://www.basistech.com/autopsy/ (accessed on 13 February 2021).
- Forensics, M. Software and Downloads. Available online: https://support.magnetforensics.com/s/software-and-downloads (accessed on 13 February 2021).
- Cellebrite. Products—Cellebrite. Available online: https://www.cellebrite.com/en/product/ (accessed on 13 February 2021).
- V3 .CSV Column Descriptions. Available online: https://datfile.net/DatCon/fieldsV3.html. (accessed on 15 February 2021).
- Shannon, C.E. A mathematical theory of communication. Bell Syst. Tech. J. 1948, 27, 379–423. [Google Scholar] [CrossRef]

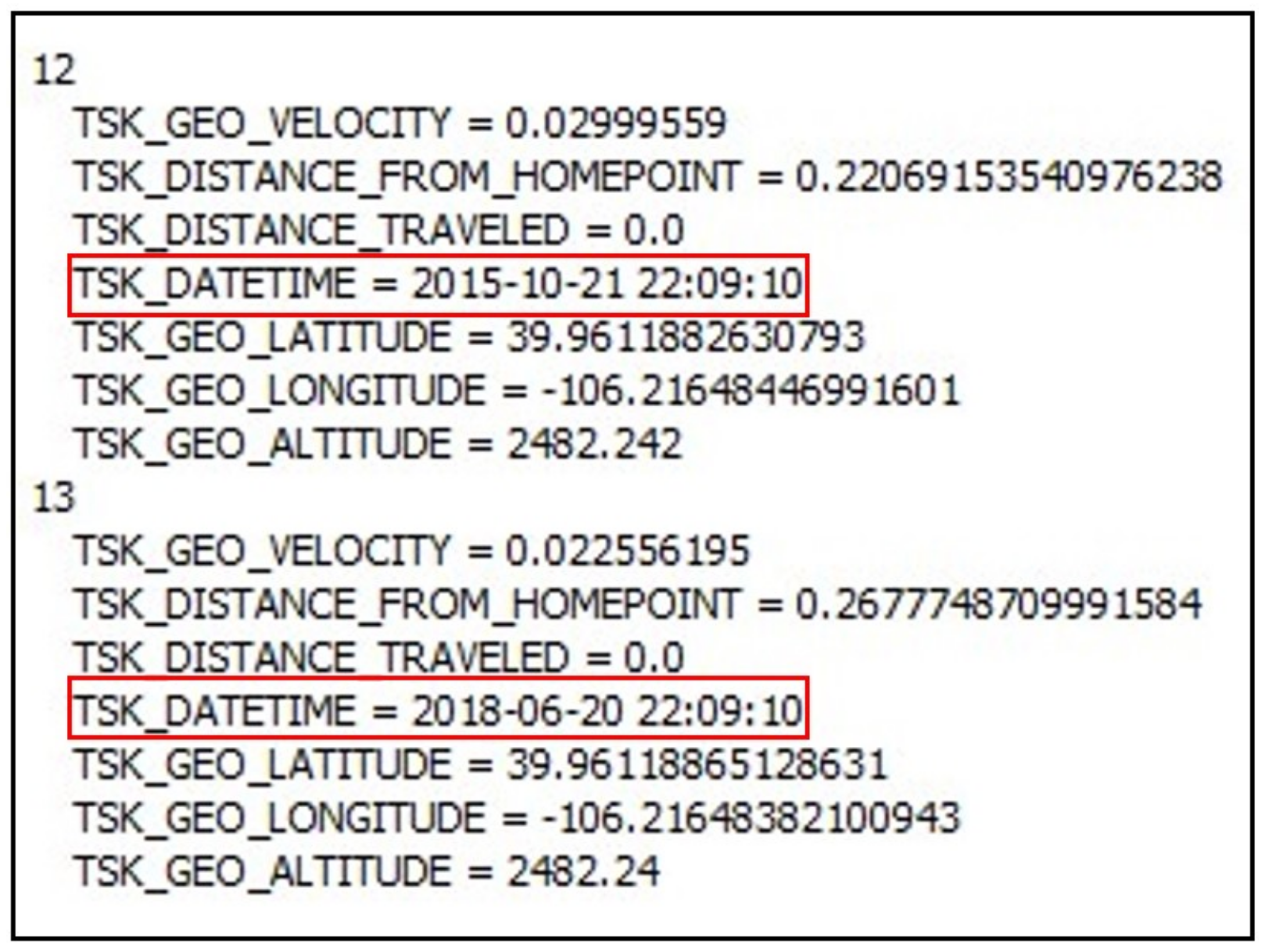
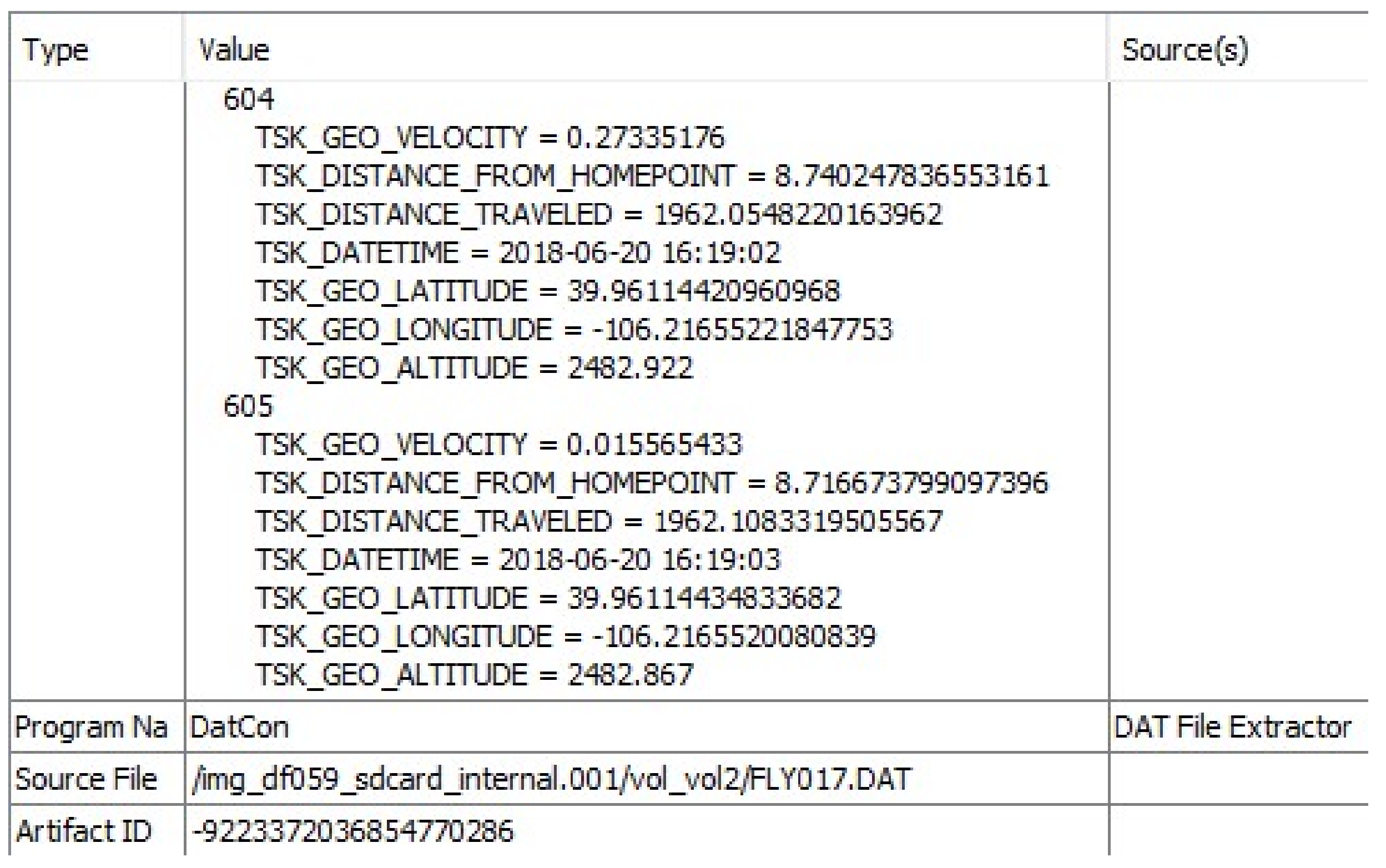
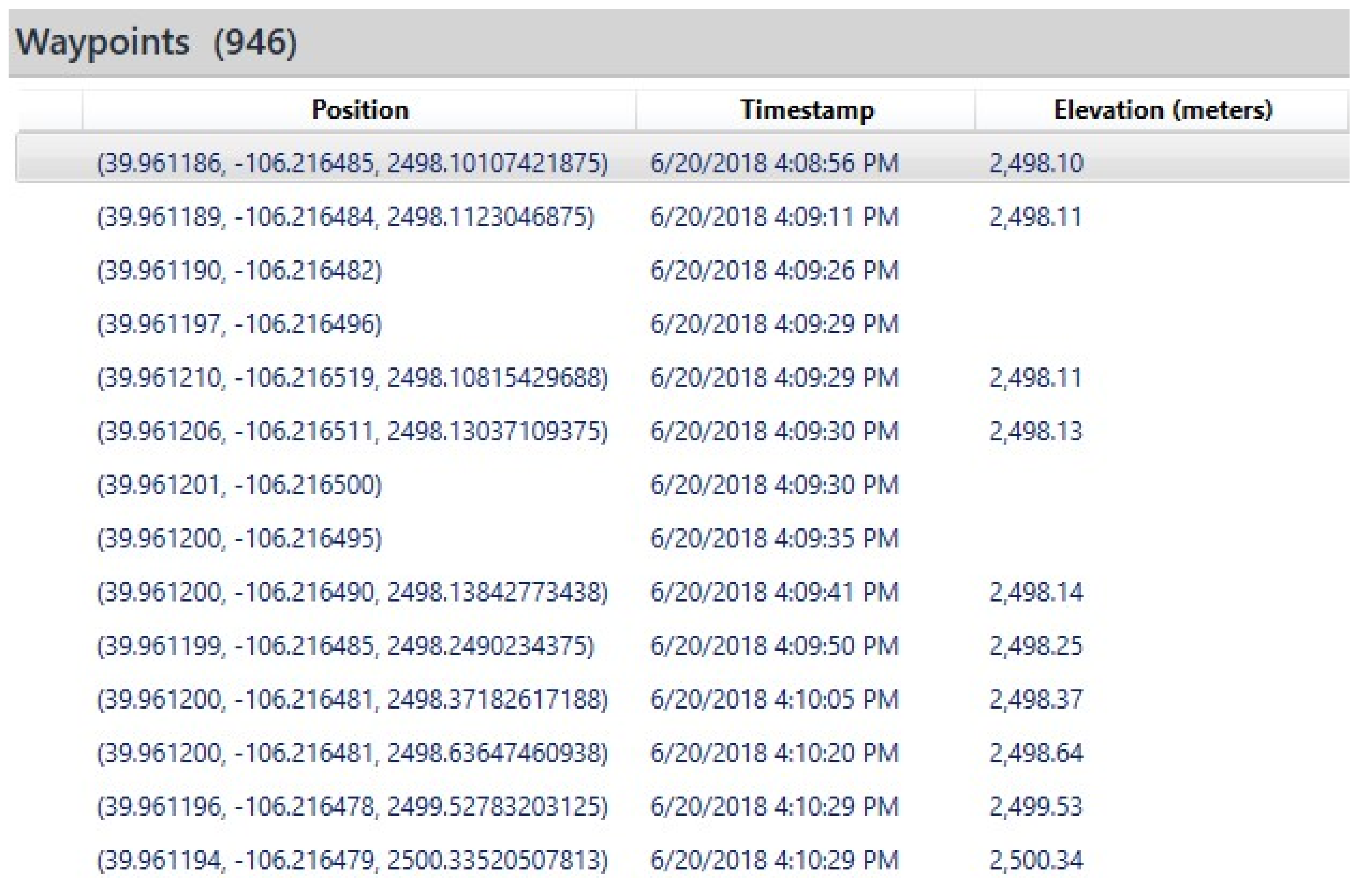
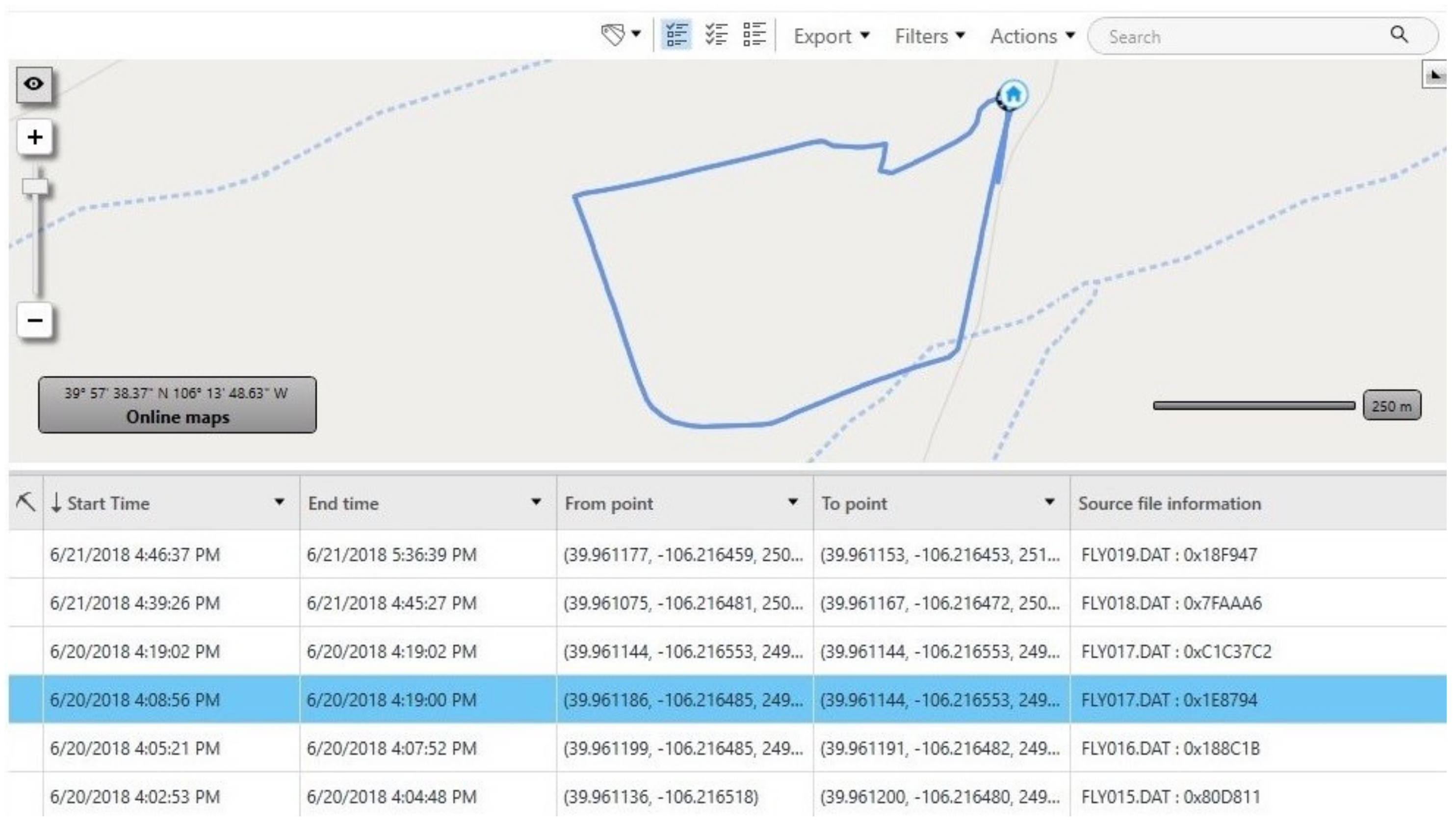
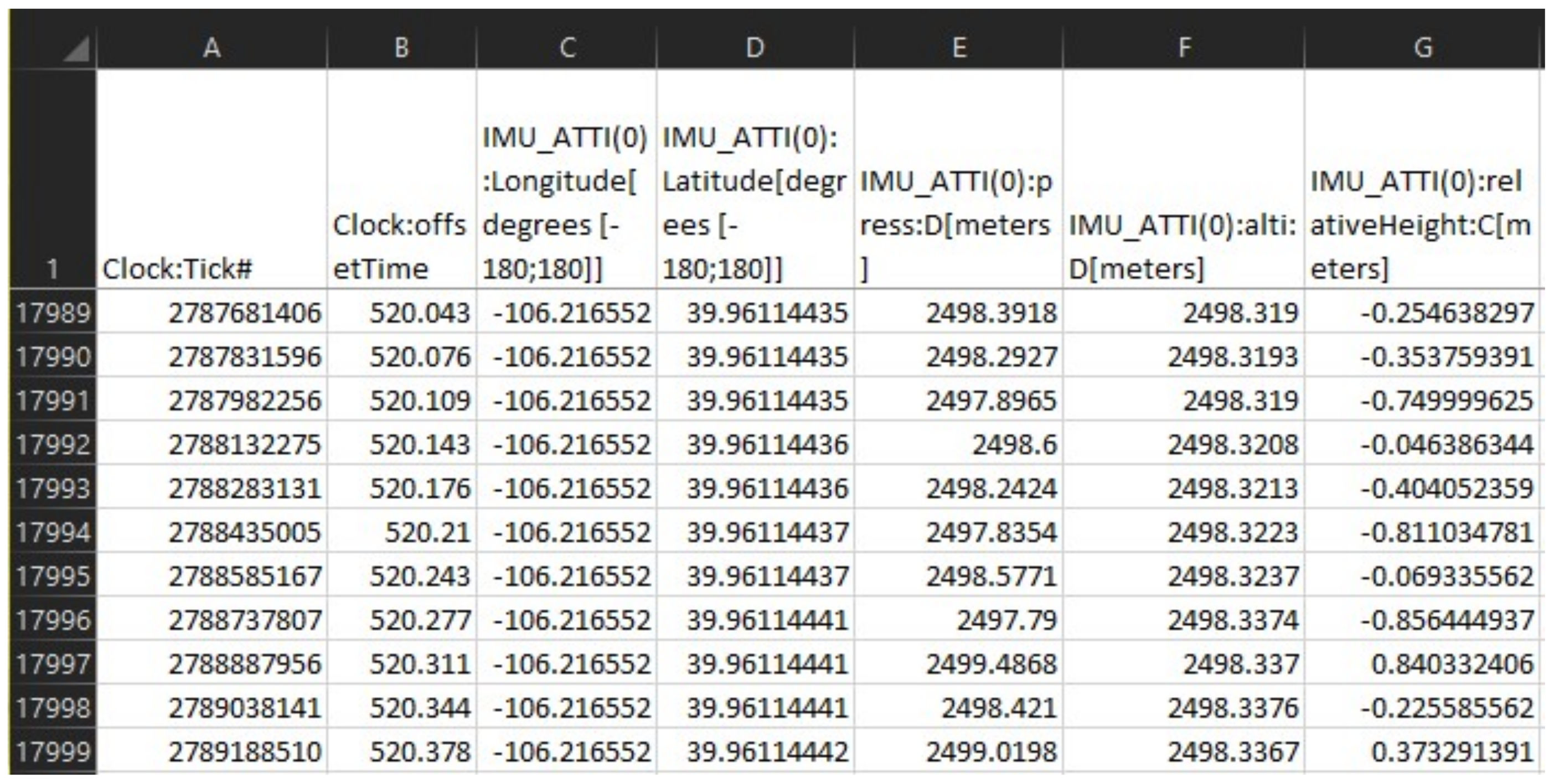
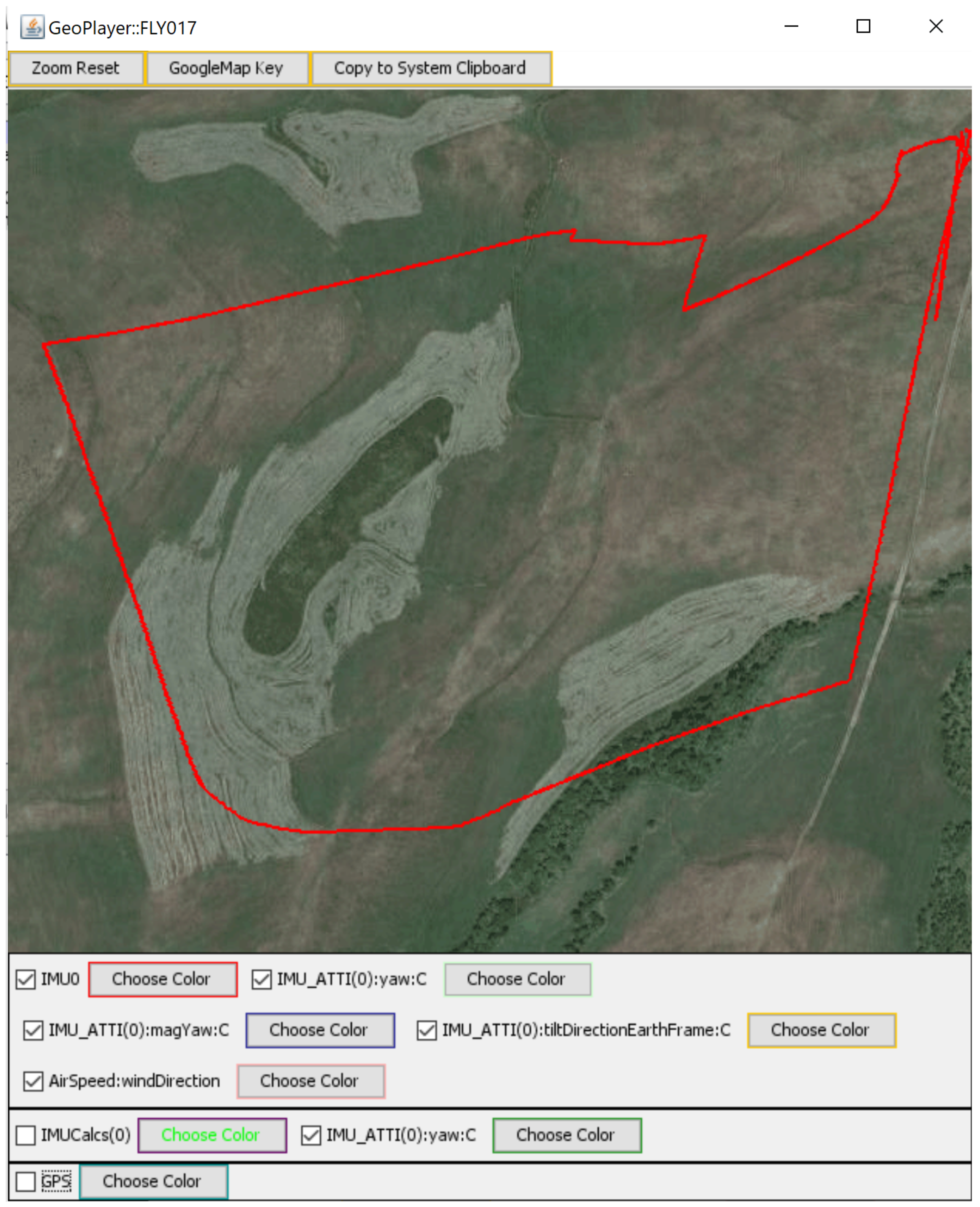
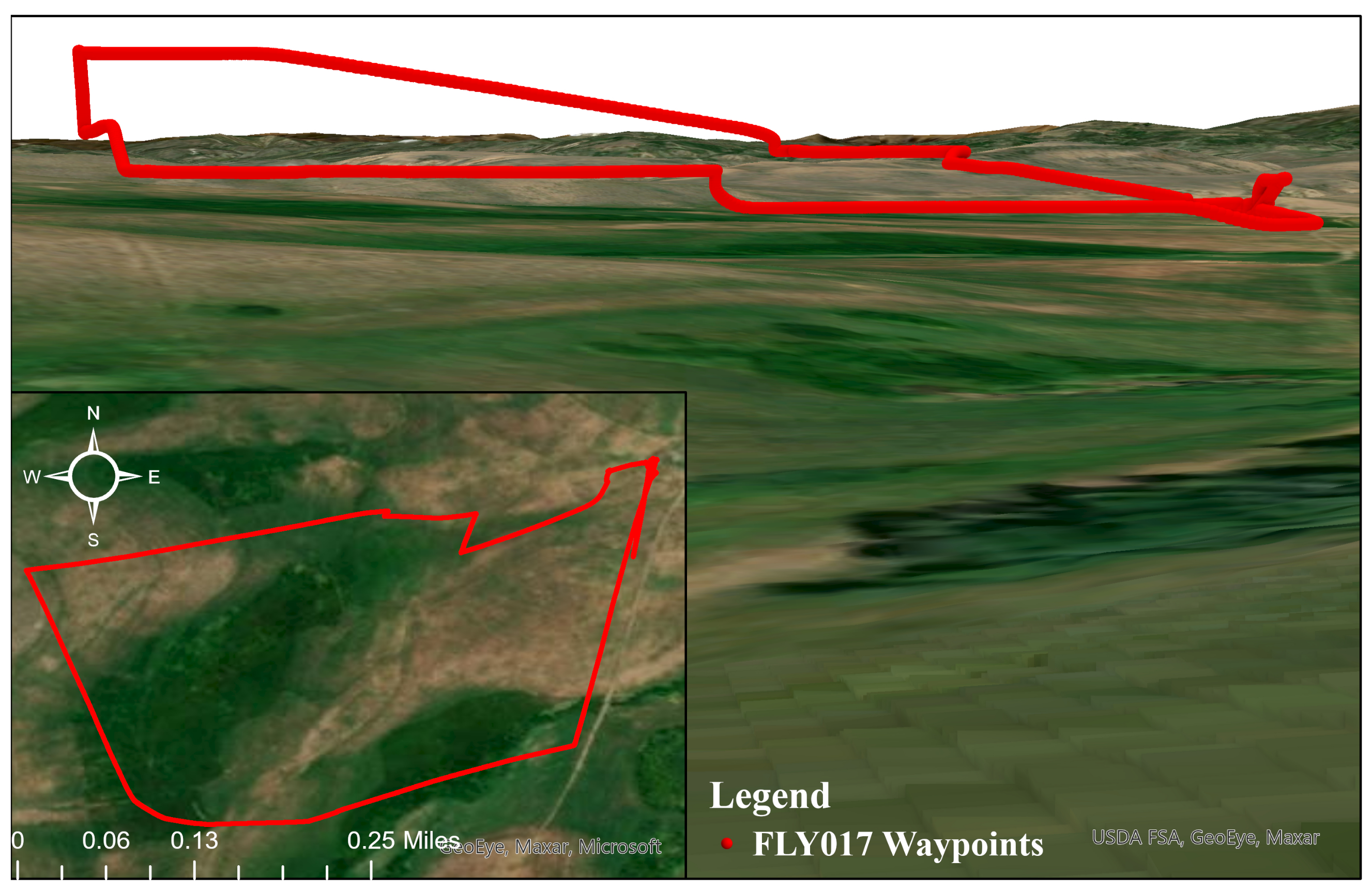

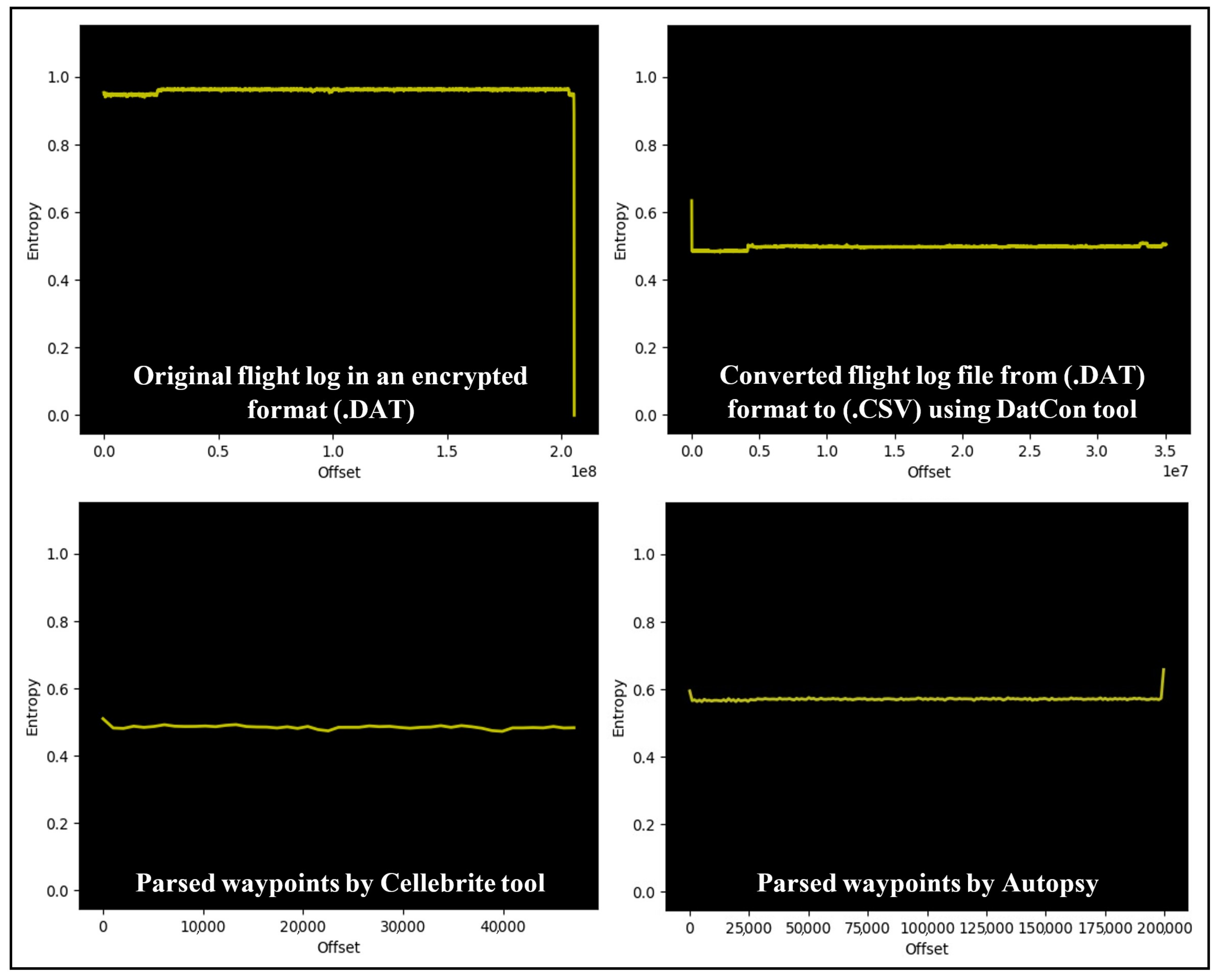
| Purpose | Software | Version | Availability |
|---|---|---|---|
| Forensic examination | Autopsy | 4.17.0 | Open-source |
| Forensic examination | Magnet AXIOM Process | 4.9.1.23338 | Proprietary |
| Forensic examination | Magnet AXIOM Examine | 4.9.1.23338 | Proprietary |
| Forensic examination | Cellebrite Physical Analyzer | 7.42.0.50 | Proprietary |
| Forensic examination | Cellebrite Reader | 7.42.0.50 | Proprietary |
| Data comparison | HxD | 2.4.0.0 | Freeware |
| Entropy measurement | Binwalk | 2.1.2 | Open-source |
| Flight log decoder | DatCon | 4.0.5 | Open-source |
| Flight log visualizer | CsvView PC | 4.0.5 | Open-source |
| Reading Exif data | ExifTool | 12.16 | Open-source |
| Timestamps decoder | DCode | 5.2.20195.4 | Open-source |
| Visualization | Google Earth Web | online | Freeware |
| 3D visualization | ArcGIS Pro | 2.7.1 | Proprietary |
| Symbol | Explanation |
|---|---|
| Y | Artifacts were found |
| No | Artifacts were not found |
| * | Artifacts were partially recovered, and it is missing relevant data |
| P | Geolocations were found not a complete track |
| E | Artifacts were found but encrypted |
| A | Autopsy tool |
| C | Cellebrite tool |
| M | Magnet AXIOM tool |
| Artifacts | PII | GPS Tracks | Videos | Pictures | Logs | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Tools | A | C | M | A | C | M | A | C | M | A | C | M | A | C | M | |
| Drone Model | Drone Component | |||||||||||||||
| DJI Matrice 210 | External SD Card | * | * | * | N | P | P | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| Internal SD Card | * | * | * | * | * | E | N | N | N | N | N | N | * | * | * | |
| eMMC Chip Off | * | * | N | N | P | N | N | N | N | N | * | N | N | N | N | |
| DJI Phantom 4 | External SD Card | * | * | * | N | P | P | Y | Y | Y | Y | Y | Y | Y | Y | Y |
| Internal SD Card | * | * | * | * | * | E | N | N | N | N | N | N | * | * | * | |
| Chip Off IC Flash Top Chip | * | * | * | N | P | N | N | N | N | N | * | * | Y | Y | Y | |
| Variable | Explanation |
|---|---|
| H | Shannon Entropy |
| Fraction of population composed of a single species i | |
| ln | Natural log |
| S | Encountered species |
| Sum of species 1 to S |
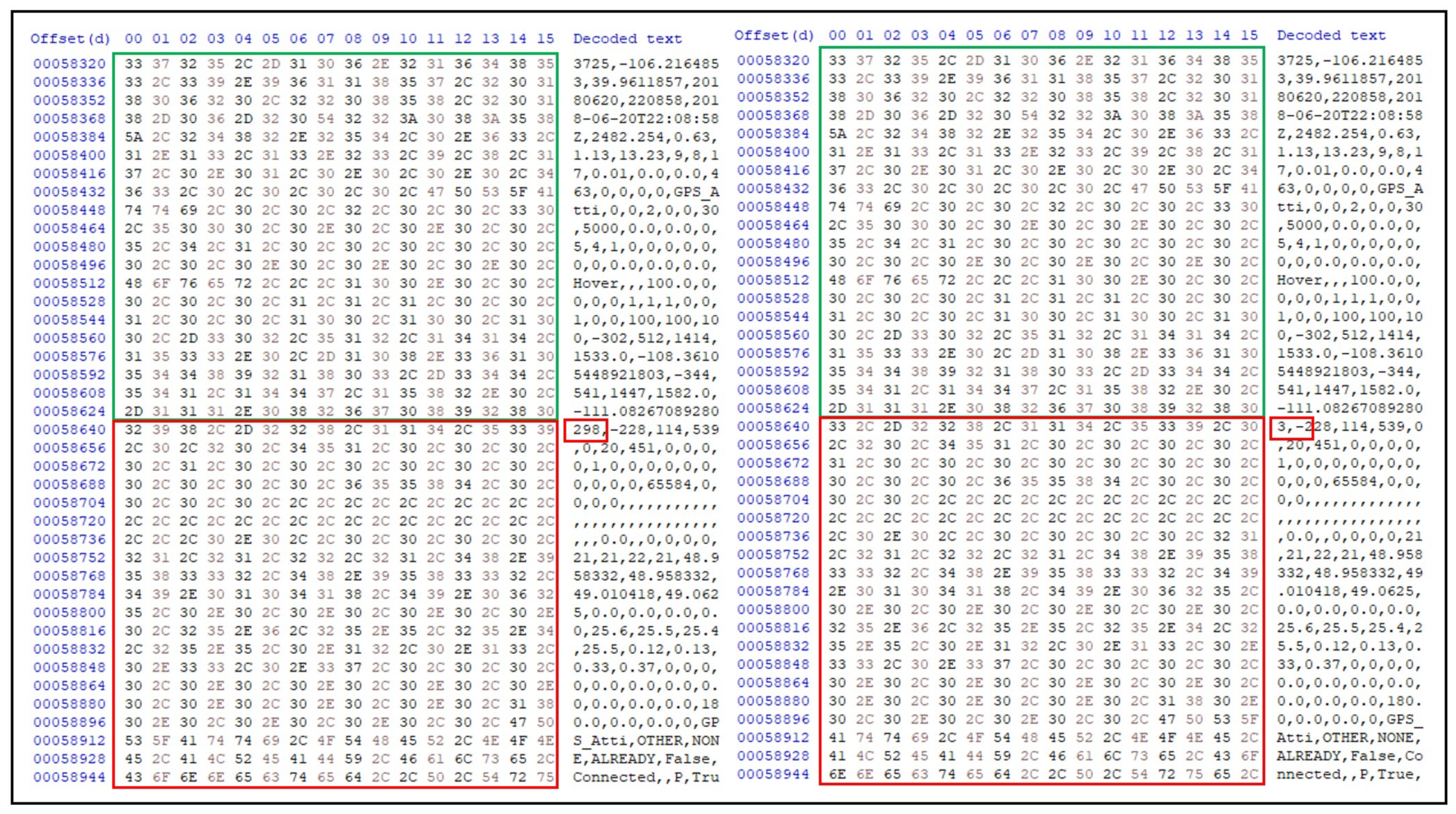
| File Name | File Size (Bytes) | MD5 Hash Value |
|---|---|---|
| FLY017.DAT | 205,496,320 | 42FDBE67089FDE01B5F1C4F27AF97F44 |
| FLY017.CSV | 35,070,466 | 44196203416EB2E0F0A71D6AD3AFF436 |
| FLY017.DAT | 205,496,320 | 42FDBE67089FDE01B5F1C4F27AF97F44 |
| FLY017.CSV | 35,070,451 | 4A088109155A13796DD5456C5E7BB890 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Salamh, F.E.; Mirza, M.M.; Karabiyik, U. UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies. Electronics 2021, 10, 733. https://doi.org/10.3390/electronics10060733
Salamh FE, Mirza MM, Karabiyik U. UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies. Electronics. 2021; 10(6):733. https://doi.org/10.3390/electronics10060733
Chicago/Turabian StyleSalamh, Fahad E., Mohammad Meraj Mirza, and Umit Karabiyik. 2021. "UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies" Electronics 10, no. 6: 733. https://doi.org/10.3390/electronics10060733
APA StyleSalamh, F. E., Mirza, M. M., & Karabiyik, U. (2021). UAV Forensic Analysis and Software Tools Assessment: DJI Phantom 4 and Matrice 210 as Case Studies. Electronics, 10(6), 733. https://doi.org/10.3390/electronics10060733








