Blockchain Applications to Improve Operation and Security of Transportation Systems: A Survey †
Abstract
:1. Introduction
- The importance of future CAV applications in our day-to-day convenience, safety, security, and growth is illustrated.
- The current obstacles that hinder the public acceptance and development of CAVs, like safety, security, and speed concerns, are discussed.
- The common applications and attributes of blockchain technology and how they have been used for numerous projects in the past are included.
- The benefits for the implementation of blockchain technology in the transportation system’s development are presented.
2. Background
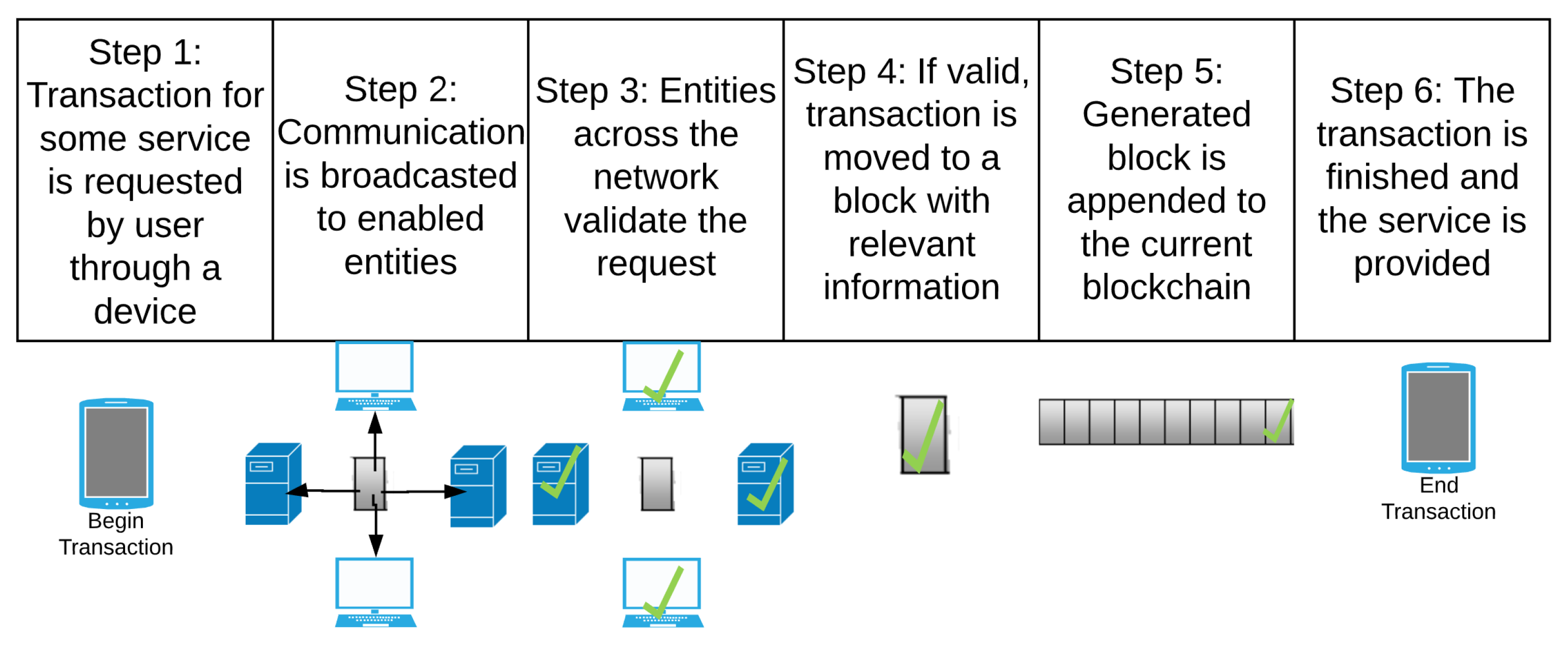
2.1. Ledger
2.2. Block
2.3. Proof-of-Work (PoW) and Hashes
2.4. Scalability
2.5. Privacy, Anonymity, and Keys
2.6. Re-Purposing
3. Blockchain and Transportation
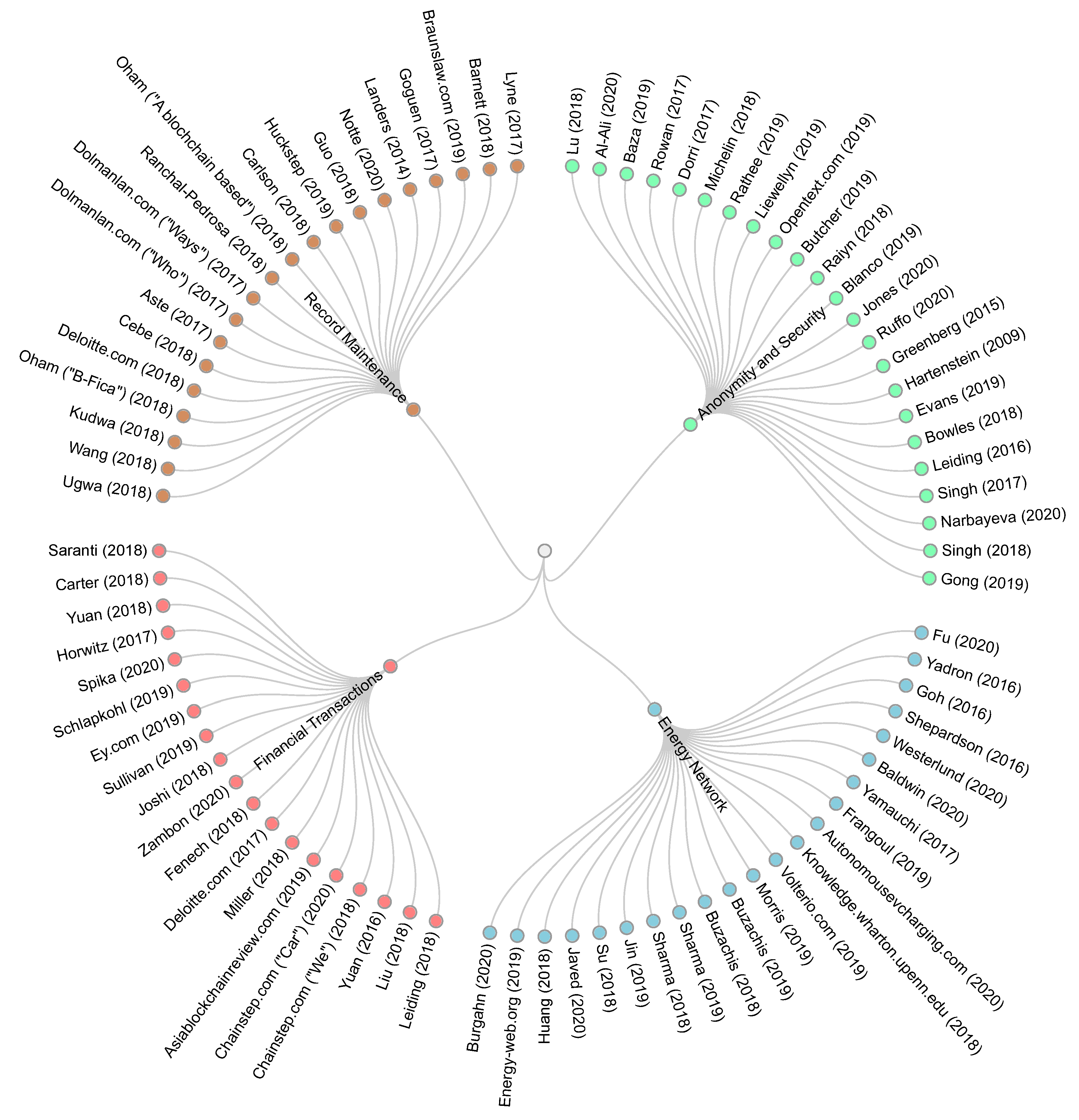
3.1. Anonymity and Security
3.2. Financial Transactions and Enhanced Services
3.3. Driving Record Maintenance
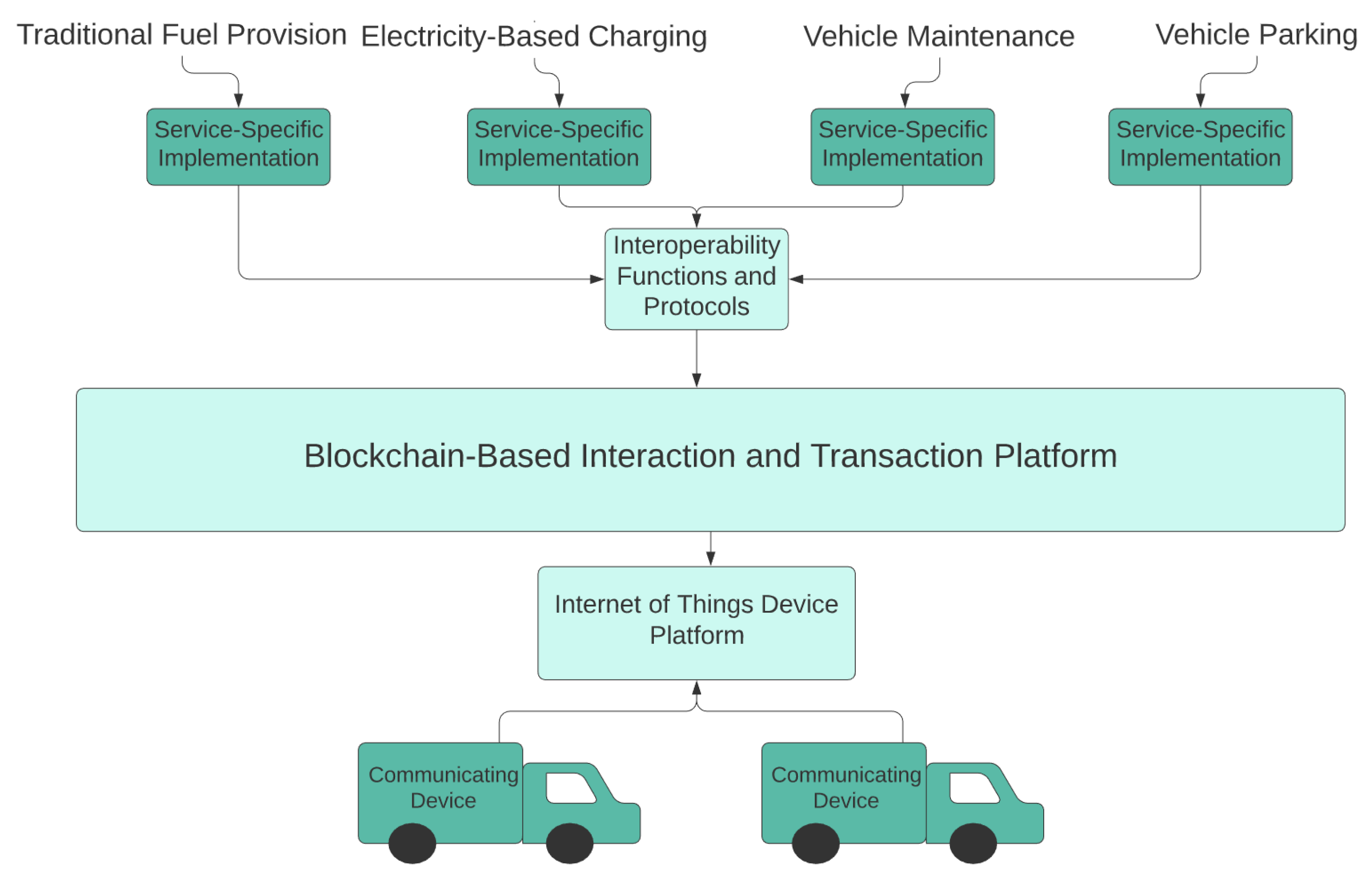
3.4. Improved CAVs Operation and Energy Network Functionality
4. Application of Blockchain in Collective Decision
5. Future Research Directions, Challenges and Barriers
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Madrigal, A.C. 7 Arguments Against the Autonomous-Vehicle Utopia. 2018. Available online: theatlantic.com (accessed on 1 September 2020).
- Siddiqui, F.; Silicon Valley Pioneered Self-Driving Cars. But Some of Its Tech-Savvy Residents Don’t Want Them Tested in Their Neighborhoods. 2019. Available online: washingtonpost.com (accessed on 1 September 2020).
- Top 5 Dangers of Self-Driving Cars. 2019. Available online: technology.org (accessed on 1 September 2020).
- Top 3 Possible Dangers of Self-Driving Cars. Available online: vesttech.com (accessed on 1 September 2020).
- Deign, J. Why Self-Driving Cars Might Make Traffic Worse. 2020. Available online: https://www.greentechmedia.com/articles/read/why-a-world-with-self-driving-cars-might-not-be-such-a-great-idea (accessed on 1 September 2020).
- Ahram, T.; Sargolzaei, A.; Sargolzaei, S.; Daniels, J.; Amaba, B. Blockchain technology innovations. In Proceedings of the 2017 IEEE Technology & Engineering Management Conference (TEMSCON), Santa Clara, CA, USA, 8–10 June 2017; pp. 137–141. [Google Scholar]
- Daniel, J.; Sargolzaei, A.; Abdelghani, M.; Sargolzaei, S.; Amaba, B. Blockchain Technology, Cognitive Computing, and Healthcare Innovations. J. Adv. Inf. Technol. 2017, 8, 194–198. [Google Scholar] [CrossRef]
- Zheng, Z.; Xie, S.; Dai, H.N.; Wang, H. Blockchain challenges and opportunities: A survey. Int. J. Web Grid Serv. 2018, 14, 352–375. [Google Scholar] [CrossRef]
- Kyriakidis, M.; Happee, R.; de Winter, J.C. Public opinion on automated driving: Results of an international questionnaire among 5000 respondents. Transp. Res. Part F Traffic Psychol. Behav. 2015, 32, 127–140. [Google Scholar] [CrossRef]
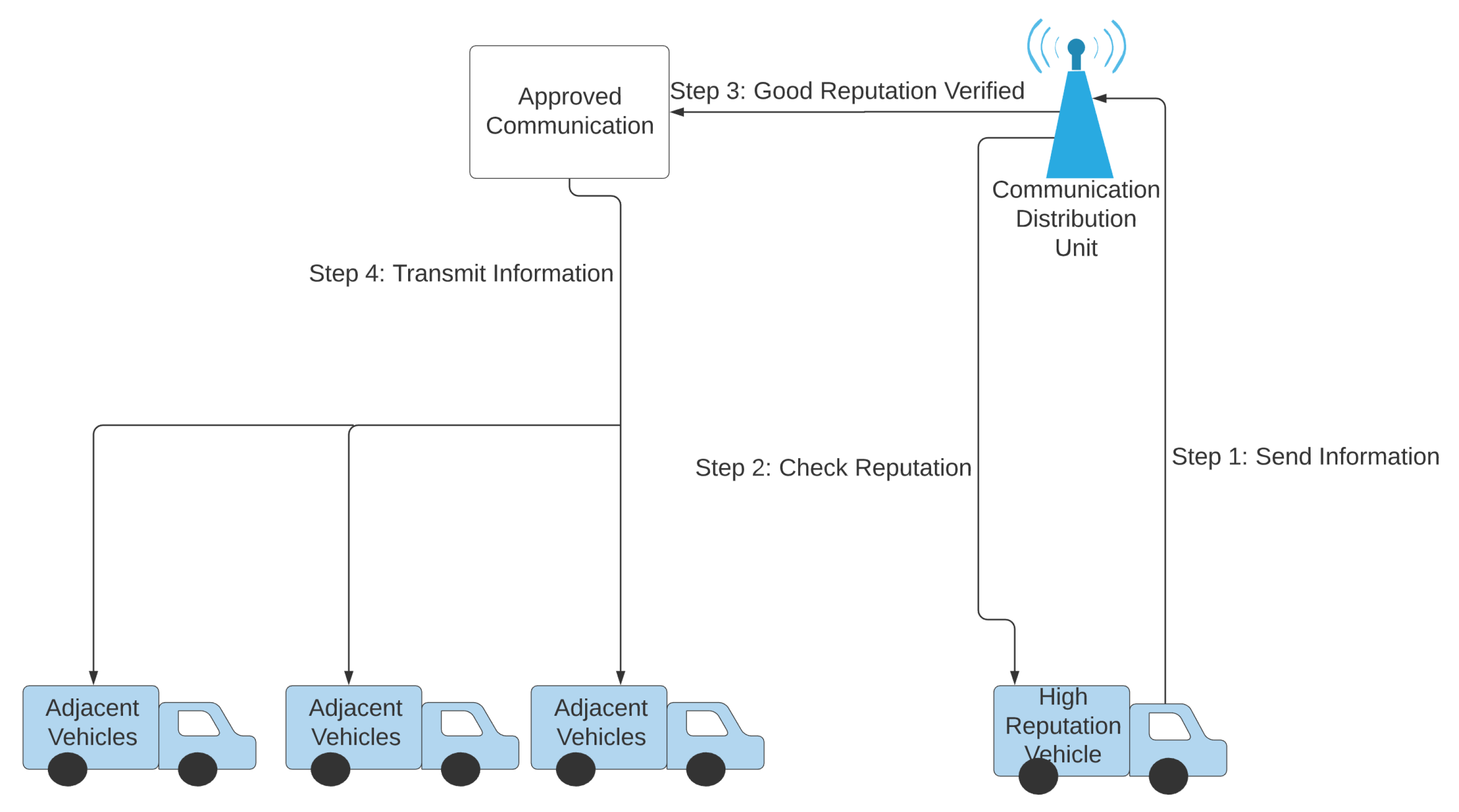
- Lu, Z.; Wang, Q.; Qu, G.; Liu, Z. Bars: A blockchain-based anonymous reputation system for trust management in vanets. In Proceedings of the 2018 17th IEEE International Conference on Trust, Security And Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering (TrustCom/BigDataSE), New York, NY, USA, 1–3 August 2018; pp. 98–103. [Google Scholar]
- Cao, Y.; Morley Mao, Z. Autonomous Vehicles can be Fooled to ‘See’ Nonexistent Obstacles. Available online: https://theconversation.com/autonomous-vehicles-can-be-fooled-to-see-nonexistent-obstacles-129427#:~:text=BystrategicallyspoofingtheLiDAR,blockingtrafficorbrakingabruptly (accessed on 1 September 2020).
- Al-Ali, M.S.; Al-Mohammed, H.A.; Alkaeed, M. Reputation Based Traffic Event Validation and Vehicle Authentication using Blockchain Technology. In Proceedings of the 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), Doha, Qatar, 2–5 February 2020; pp. 451–456. [Google Scholar]
- Dorri, A.; Steger, M.; Kanhere, S.S.; Jurdak, R. Blockchain: A distributed solution to automotive security and privacy. IEEE Commun. Mag. 2017, 55, 119–125. [Google Scholar] [CrossRef] [Green Version]
- Baza, M.; Nabil, M.; Lasla, N.; Fidan, K.; Mahmoud, M.; Abdallah, M. Blockchain-based Firmware Update Scheme Tailored for Autonomous Vehicles. In Proceedings of the 2019 IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 15–18 April 2019; pp. 1–7. [Google Scholar]
- Rowan, S.; Clear, M.; Gerla, M.; Huggard, M.; Goldrick, C.M. Securing Vehicle to Vehicle Communications using Blockchain through Visible Light and Acoustic Side-Channels. arXiv 2017, arXiv:1704.02553. [Google Scholar]
- Nakamoto, S. Bitcoin: A peer-to-peer electronic cash system. Available online: https://bitcoin.org/en/bitcoin-paper (accessed on 1 September 2020).
- Michelin, R.A.; Dorri, A.; Lunardi, R.C.; Steger, M.; Kanhere, S.S.; Jurdak, R.; Zorzo, A.F. SpeedyChain: A framework for decoupling data from blockchain for smart cities. arXiv 2018, arXiv:1807.01980. [Google Scholar]
- Saranti, P.G.; Chondrogianni, D.; Karatzas, S. Autonomous Vehicles and Blockchain Technology Are Shaping the Future of Transportation. In The 4th Conference on Sustainable Urban Mobility; Springer: Berlin/Heidelberg, Germany, 2018; pp. 797–803. [Google Scholar]
- Ranchal-Pedrosa, A.; Pau, G. ChargeltUp: On Blockchain-based technologies for Autonomous Vehicles. In Proceedings of the 1st Workshop on Cryptocurrencies and Blockchains for Distributed Systems, Munich, Germany, 15 June 2018; pp. 87–92. [Google Scholar] [CrossRef] [Green Version]
- Rathee, G.; Sharma, A.; Iqbal, R.; Alogaily, M.; Jablan, N.; Kumar, R. A Blockchain Framework for Securing Connected and Autonomous Vehicles. Sensors 2019, 19, 3165. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Carter, C.; Koh, L.D. Blockchain Disruption in Transport: Are You Decentralised Yet? Available online: https://trid.trb.org/view/1527923 (accessed on 1 September 2020).
- Fadhil, M.; Owenson, G.; Adda, M. A Bitcoin Model for Evaluation of Clustering to Improve Propagation Delay in Bitcoin Network. In Proceedings of the 2016 IEEE Intl Conference on Computational Science and Engineering (CSE) and IEEE Intl Conference on Embedded and Ubiquitous Computing (EUC) and 15th Intl Symposium on Distributed Computing and Applications for Business Engineering (DCABES), Paris, France, 24–26 August 2016; pp. 468–475. [Google Scholar] [CrossRef]
- Horwitz, L. Data Center-Impact of Driverless Cars Could Broaden with Blockchain. Available online: https://www.cisco.com/c/en/us/solutions/data-center/blockchain-driverless-cars.html (accessed on 1 September 2020).
- Juričić, V.; Radošević, M.; Fuzul, E. Optimizing the Resource Consumption of Blockchain Technology in Business Systems. Bus. Syst. Res. J. 2020, 11, 78–92. [Google Scholar] [CrossRef]
- Ghosh, E.; Das, B. A Study on the Issue of Blockchain’s Energy Consumption. In Proceedings of International Ethical Hacking Conference 2019, eHaCON 2019, Kolkata, India, 2020; Springer: Singapore, Singapore; pp. 63–75. [CrossRef]
- Fu, Y.; Li, C.; Yu, F.R.; Luan, T.H.; Zhang, Y. An Autonomous Lane Changing System with Knowledge Accumulation and Transfer Assisted by Vehicular Blockchain. IEEE Internet Things J. 2020, 7, 1–14. [Google Scholar] [CrossRef]
- Choncholas, J.; Bhardwaj, K.; Gavrilovska, A. GeoENS: Blockchain-based Infrastructure for Service Discovery at the Edge. Available online: https://www.usenix.org/conference/hotedge20/presentation/choncholas (accessed on 1 September 2020).
- Anatomy of Autonomous Vehicles: Is GIS Really Under the Hood of Self-Driving Cars? Available online: https://gisgeography.com/autonomous-vehicles-gis-self-driving-cars/ (accessed on 1 September 2020).
- Petrovskaya, A.; Thrun, S. Model Based Vehicle Tracking for Autonomous Driving in Urban Environments; MIT Press: Cambridge, MA, USA, 2008. [Google Scholar] [CrossRef]
- Sharp, C.; Schaffert, S.; Woo, A.; Sastry, N.; Karlof, C.; Sastry, S.; Culler, D. Design and Implementation of a Sensor Network System for Vehicle Tracking and Autonomous Interception. In Proceedings of the Second European Workshop on Wireless Sensor Networks, Istanbul, Turkey, 31 January–2 February 2005; pp. 93–107. [Google Scholar]
- Westerlund, R. Decentralized Reservation of Spatial Volumes by Autonomous Vehicles: Investigating the Applicability of Blockchain and Smart Contracts. Available online: https://www.diva-portal.org/smash/get/diva2:1437488/FULLTEXT01.pdf (accessed on 1 September 2020).
- Zadobrischi, E.; Cosovanu, L.M.; Dimian, M. Traffic Flow Density Model and Dynamic Traffic Congestion Model Simulation Based on Practice Case with Vehicle Network and System Traffic Intelligent Communication. Available online: https://www.mdpi.com/2073-8994/12/7/1172 (accessed on 1 September 2020).
- Van Arem, B.; Van Driel, C.J.; Visser, R. The Impact of Cooperative Adaptive Cruise Control on Traffic-Flow Characteristics. IEEE Trans. Intell. Transp. Syst. 2006, 7, 429–436. [Google Scholar] [CrossRef] [Green Version]
- Yakub Abualhoul, M. Visible Light and Radio Communication for Cooperative Autonomous Driving: Applied to Vehicle Convoy. Ph.D. Thesis, Mines ParisTech, Paris, France, 2016. [Google Scholar] [CrossRef]
- Kent, T.; Pipe, A.; Richards, A.; Hutchinson, J.; Schuster, W. A Connected Autonomous Vehicle Testbed: Capabilities, Experimental Processes and Lessons Learned. Automation 2020, 1, 17–32. [Google Scholar] [CrossRef]
- Sichitiu, M.; Kihl, M. Inter-vehicle communication systems: A survey. IEEE Commun. Surv. Tutorials 2008, 10, 88–105. [Google Scholar] [CrossRef] [Green Version]
- Luo, J.; Hubaux, J.P. A Survey of Inter-Vehicle Communication. 2004. Available online: core.ac.uk (accessed on 1 September 2020).
- Jameel, F.; Awais Javed, M.; Zeadally, S.; Jantti, R. Efficient Mining Cluster Selection for Blockchain-based Cellular V2X Communications. IEEE Trans. Intell. Transp. Syst. 2020, 1–9. [Google Scholar] [CrossRef]
- Jawhar, I.; Mohamed, N.; Zhang, L. Inter-vehicular Communication Systems, Protocols and Middleware. In Proceedings of the 2010 IEEE Fifth International Conference on Networking, Architecture, and Storage, Macau, China, 15–17 July 2010; pp. 282–287. [Google Scholar]
- Takatori, Y.; Hasegawa, T. Quantitative Performance Evaluation of Predictive Collision Warning System based on Inter-Vehicle Communication. Int. J. lTS Res. 2007, 4, 13–20. [Google Scholar]
- Lin, F.; Wang, K.; Zhao, Y.; Wang, S. Integrated Avoid Collision Control of Autonomous Vehicle Based on Trajectory Re-Planning and V2V Information Interaction. Sensors 2020, 20, 1079. [Google Scholar] [CrossRef] [Green Version]
- Reichardt, D.; Shick, J. Collision Avoidance in Dynamic Environments Applied to Autonomous Vehicle Guidance on the Motorway. In Proceedings of the Intelligent Vehicles ’94 Symposium, Paris, France, 24–26 October 1994; pp. 74–78. [Google Scholar] [CrossRef]
- Funke, J.; Brown, M.; Erlien, S.M.; Gerdes, J.C. Collision Avoidance and Stabilization for Autonomous Vehicles in Emergency Scenarios. IEEE Trans. Control. Syst. Technol. 2017, 25, 1204–1216. [Google Scholar] [CrossRef]
- Wang, P.; Gao, S.; Li, L.; Sun, B.; Cheng, S. Obstacle Avoidance Path Planning Design for Autonomous Driving Vehicles Based on an Improved Artificial Potential Field Algorithm. Energies 2019, 12, 2342. [Google Scholar] [CrossRef] [Green Version]
- Gupta, R.; Tanwar, S.; Kumar, N.; Tyagi, S. Blockchain-based security attack resilience schemes for autonomous vehicles in industry 4.0: A systematic review. Comput. Electr. Eng. 2020, 86, 106717. [Google Scholar] [CrossRef]
- Chattopadhyay, A.; Lam, K.Y.; Tavva, Y. Autonomous Vehicle: Security by Design. IEEE Trans. Intell. Transp. Syst. 2020, 1–15. [Google Scholar] [CrossRef]
- Zelle, D.; Rieke, R.; Plappert, C.; Kraus, C.; Levshun, D.; Chechulin, A. SEPAD-Security Evaluation Platform for Autonomous Driving. In Proceedings of the 2020 28th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP), Västerås, Sweden, 11–13 March 2020; IEEE Computer Society: Los Alamitos, CA, USA, 2020; pp. 413–420. [Google Scholar] [CrossRef]
- Ferdowsi, A.; Challita, U.; Saad, W.; Mandayam, N.B. Robust Deep Reinforcement Learning for Security and Safety in Autonomous Vehicle Systems. In Proceedings of the 2018 21st International Conference on Intelligent Transportation Systems (ITSC), Maui, HI, USA, 4–7 November 2018; pp. 307–312.
- Amoozadeh, M.; Raghuramu, A.; Chuah, C.N.; Ghosal, D.; Michael Zhang, H.; Rowe, J.; Levitt, K. Security Vulnerabilities of Connected Vehicle Streams and Their Impact on Cooperative Driving. IEEE Commun. Mag. 2015, 53, 126–132. [Google Scholar] [CrossRef] [Green Version]
- Pokhrel, S.; Choi, J. A Decentralized Federated Learning Approach For Connected Autonomous Vehicles. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Seoul, Korea, 6–9 April 2020. [Google Scholar] [CrossRef]
- Lam, A.Y.; Leung, Y.W.; Chu, X. Autonomous-Vehicle Public Transportation System: Scheduling and Admission Control. IEEE Trans. Intell. Transp. Syst. 2016, 17, 1210–1226. [Google Scholar] [CrossRef] [Green Version]
- Llewellyn, P. Cybersecurity and Autonomous Vehicle Technology. Available online: aertech.com (accessed on 1 September 2020).
- Autonomous Vehicles: What Are the Security Risks? Available online: opentext.com (accessed on 1 September 2020).
- Butcher, L. Increased Security for Autonomous and Connected Vehicles. Available online: autonomousvehicleinternational.com (accessed on 1 September 2020).
- Raiyn, J. Data and Cyber Security in Autonomous Vehicle Networks. Transp. Telecommun. J. 2018, 19, 325–334. [Google Scholar] [CrossRef] [Green Version]
- Blanco, S. Data Security For Autonomous Vehicles Can And Should Be Treated With Respect. Available online: forbes.com (accessed on 1 September 2020).
- Jones, M. Tesla Personal Data Oversight Highlights Autonomous Vehicle Data Privacy Issue. Available online: techhq.com (accessed on 1 September 2020).
- Henrique Ruffo, G. Tesla Data Leak: Components With Personal Info Find Their Way On eBay. Available online: insideevs.com (accessed on 1 September 2020).
- Greenberg, A. Hackers Remotely Kill a Jeep on the Highway-With Me in It. Available online: wired.com (accessed on 1 September 2020).
- Evans, S. Unsafe at Any Connection: Autonomous Vehicles Lacking in Privacy, Security Protections. Available online: sharaevans.com (accessed on 1 September 2020).
- Bowles, J. Autonomous Vehicles and the Threat of Hacking. Available online: cpomagazine.com (accessed on 1 September 2020).
- Hartenstein, H.; Laberteaux, K. VANET: Vehicular Applications and Inter-Networking Technologies; John Wiley & Sons: Hoboken, NJ, USA, 2009; Volume 1. [Google Scholar]
- Leiding, B.; Memarmoshrefi, P.; Hogrefe, D. Self-managed and blockchain-based vehicular ad-hoc networks. In Proceedings of the 2016 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Heidelberg, Germany, 12–16 September 2016; pp. 137–140. [Google Scholar] [CrossRef]
- Singh, M.; Kim, S. Blockchain Based Intelligent Vehicle Data sharing Framework. arXiv 2017, arXiv:1708.09721. [Google Scholar]
- Narbayeva, S.; Bakibayev, T.; Abeshev, K.; Makarova, I.; Shubenkova, K.; Pashkevich, A. Blockchain Technology on the Way of Autonomous Vehicles Development. Transp. Res. Procedia 2020, 44, 168–175. [Google Scholar] [CrossRef]
- Singh, M.; Kim, S. Branch Based Blockchain Technology in Intelligent Vehicle. Comput. Netw. 2018, 145, 219–231. [Google Scholar] [CrossRef]
- Gong, S.; Tcydenova, E.; Jo, J.; Lee, Y.; Park, J. Blockchain-Based Secure Device Management Framework for an Internet of Things Network in a Smart City. Sustainability 2019, 11, 3889. [Google Scholar] [CrossRef] [Green Version]
- The Impact of Blockchain on Banks & Financial Institution. Available online: asiablockchainreview.com (accessed on 1 September 2020).
- Spilka, D. Blockchain and the Unbanked: Changes Coming to Global Finance. Available online: ibm.com (accessed on 1 September 2020).
- Schlapkohl, K. Central Bank Digital Currency Explained. Available online: ibm.com (accessed on 1 September 2020).
- Blockchain in Financial Services. Available online: ey.com (accessed on 1 September 2020).
- Sullivan, M. The Future of Blockchain in Financial Services. Available online: blocktelegraph.io (accessed on 1 September 2020).
- Joshi, N. Autonomous Vehicles and Blockchain. Available online: bbntimes.com (accessed on 1 September 2020).
- Zambon, A. Autonomous Vehicles and Blockchain. Available online: octotelematics.com (accessed on 1 September 2020).
- Fenech, G. The Link Between Autonomous Vehicles and Blockchain. Available online: forbes.com (accessed on 1 September 2020).
- Blockchain @ Auto Finance: How Blockchain Can Enable the Future of Mobility. Available online: deloitte.com (accessed on 1 September 2020).
- Miller, D. Blockchain and the Internet of Things in the Industrial Sector. IT Prof. 2018, 20, 15–18. [Google Scholar] [CrossRef]
- Yuan, Y.; Wang, F.Y. Blockchain and Cryptocurrencies: Model, Techniques, and Applications. IEEE Trans. Syst. Man Cybern. Syst. 2018, 48, 1421–1428. [Google Scholar] [CrossRef]
- Car Ewallet: Make Your Car a Wallet. Available online: chainstep.com (accessed on 1 September 2020).
- We built Car eWallet on blockchain to securely facilitate machine-to-machine transactions. Available online: chainstep.com (accessed on 1 September 2020).
- Mine, A. Blockchain based car wallet Car eWallet. Available online: gaiax-blockchain.com (accessed on 1 September 2020).
- Yuan, Y.; Wang, F.Y. Towards blockchain-based intelligent transportation systems. In Proceedings of the 2016 IEEE 19th International Conference on Intelligent Transportation Systems (ITSC), Rio de Janeiro, Brazil, 1–4 November 2016; pp. 2663–2668. [Google Scholar]
- Liu, H.; Zhang, Y.; Yang, T. Blockchain-Enabled Security in Electric Vehicles Cloud and Edge Computing. IEEE Netw. 2018, 32, 78–83. [Google Scholar] [CrossRef]
- Leiding, B.; Vorobev, W.V. Enabling the Vehicle Economy Using a Blockchain-Based Value Transaction Layer Protocol for Vehicular Ad-Hoc Networksguo. 2018. Available online: uploads-ssl.webflow.com (accessed on 1 September 2020).
- Steps You Can Take to Correct a Mistake in the Police Report After Your Car Accident. Available online: braunslaw.com (accessed on 1 September 2020).
- Goguen, D. Checklist of Records to Gather After a Car Accident. Available online: nolo.com (accessed on 1 September 2020).
- Landers, D. Tips for Settling a Car Accident Claim. Available online: nolo.com (accessed on 1 September 2020).
- Ways to Investigate the Cause of a Car Accident. Available online: dolmanlaw.com (accessed on 1 September 2020).
- Who is Responsible for Your Car Accident. Available online: dolmanlaw.com (accessed on 1 September 2020).
- Huckstep, R. Four Ways Autonomous Vehicles Will Change Auto Insurance. Available online: the-digital-insurer.com (accessed on 1 September 2020).
- Carlson, D. The Autonomous Vehicle Revolution: How Insurance Must Adapt. Available online: marsh.com (accessed on 1 September 2020).
- Lyne, A. Driverless Cars and the Insurance Industry. Available online: capsicumre.com (accessed on 1 September 2020).
- Barnett, D. Autonomous Cars and Auto Insurance: What’s Going to Happen. Available online: atlantainsurance.com (accessed on 1 September 2020).
- Notte, J. How Do Self-Driving Safety Features Affect Your Car Insurance? Available online: thesimpledollar.com (accessed on 1 September 2020).
- Guo, H.; Meamari, E.; Shen, C.C. Blockchain-inspired Event Recording System for Autonomous Vehicles. In Proceedings of the 2018 1st IEEE International Conference on Hot Information-Centric Networking (HotICN), Shenzhen, China, 15–17 August 2018; pp. 218–222. [Google Scholar]
- Aste, T.; Tasca, P.; Di Matteo, T. Blockchain Technologies: The Foreseeable Impact on Society and Industry. Computer 2017, 50, 18–28. [Google Scholar] [CrossRef] [Green Version]
- Oham, C.; Kanhere, S.S.; Jurdak, R.; Jha, S. A Blockchain Based Liability Attribution Framework for Autonomous Vehicles. arXiv 2018, arXiv:1802.05050. [Google Scholar]
- Cebe, M.; Erdin, E.; Akkaya, K.; Aksu, H.; Uluagac, S. Block4Forensic: An Integrated Lightweight Blockchain Framework for Forensics Applications of Connected Vehicles. arXiv 2018, arXiv:1802.00561. [Google Scholar] [CrossRef] [Green Version]
- Ugwu, M.C.; Okpala, I.C.; Oham, C.I.; Nwakanma, C.I. A Tiered Blockchain Framework for Vehicular Forensics. Int. J. Netw. Secur. Its Appl. IJNSA 2018. [Google Scholar] [CrossRef]
- Wang, A. The Future of Blockchain in Insurance. Available online: genre.com (accessed on 1 September 2020).
- Kudwa, A.S. Blockchain: Life and Vehicle Insurance. Available online: mindtree.com (accessed on 1 September 2020).
- Oham, C.; Jurdak, R.; Kanhere, S.S.; Dorri, A.; Jha, S.K. B-FICA: BlockChain based Framework for Auto- Claim and Adjudication. In Proceedings of the IEEE International Conference on Internet of Things (iThings) and IEEE Green Computing and Communications (GreenCom) and IEEE Cyber, Physical and Social Computing (CPSCom) and IEEE Smart Data (SmartData), Halifax, NS, Canada, 30 July–3 August 2018; pp. 1171–1180. [Google Scholar]
- Accelerating Techonlogy Disruption in the Automotive Market: Blockchain in the Automotive Industry. Available online: deloitte.com (accessed on 1 September 2020).
- Autonomous Car Crashes: Who-or What-Is to Blame. Available online: knowledge.wharton.upenn.edu (accessed on 1 September 2020).
- Goh, B.; Shirouzu, N. Chinese Man Blames Tesla Autopilot Function for Son’s Crash. Available online: reuters.com (accessed on 1 September 2020).
- Shepardson, D. Google Says it Bears ‘Some Responsibility’ After Self-Driving Car Hit Bus. Available online: reuters.com (accessed on 1 September 2020).
- Yadron, D.; Tynan, D. Tesla Driver Dies in First Fatal Crash While Using Autopilot Mode. Available online: theguardian.com (accessed on 1 September 2020).
- Baldwin, R. Driver in Fatal Tesla Model X Crash Had Complained About Autopilot. Available online: caranddriver.com (accessed on 1 September 2020).
- Yamauchi, M. How Will Autonomous Vehicles Charge Themselves? Available online: pluglesspower.com (accessed on 1 September 2020).
- Frangoul, A. VW Subsidiary to Help with Pilot of Robotic Charging Stations for Self-Driving Vehicles. Available online: cnbc.com (accessed on 1 September 2020).
- EZ-Linck Beats Tesla with Its Completely Cable-Less Charging. Available online: autonomousevcharging.com (accessed on 1 September 2020).
- Redefining Charging: Automatic Conductive Connection Device. Available online: volterio.com (accessed on 1 September 2020).
- Morris, C. What’s the Best Way to Grow Electric Vehicle Charging Infrastructure? Available online: evannex.com (accessed on 1 September 2020).
- Buzachis, A.; Filocamo, B.; Fazio, M.; Ruiz, J.A.; Sotelo, M.; Villari, M. Distributed Priority Based Management of Road Intersections Using Blockchain. In Proceedings of the 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, 29 June–3 July 2019; pp. 1159–1164. [Google Scholar]
- Buzachis, A.; Celesti, A.; Galletta, A.; Fazio, M.; Villari, M. A Secure and Dependable Multi-Agent Autonomous Intersection Management (MA-AIM) System Leveraging Blockchain Facilities. In Proceedings of the IEEE/ACM International Conference on Utility and Cloud Computing Companion (UCC Companion), Zurich, Switzerland, 17–20 December 2018; pp. 226–231. [Google Scholar] [CrossRef]
- Sharma, V. An energy-efficient transaction model for the blockchain-enabled internet of vehicles (IoV). IEEE Commun. Lett. 2018, 23, 246–249. [Google Scholar] [CrossRef] [Green Version]
- Su, Z.; Wang, Y.; Xu, Q.; Fei, M.; Tian, Y.C.; Zhang, N. A Secure Charging Scheme for Electric Vehicles with Smart Communities in Energy Blockchain. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef] [Green Version]
- Javed, M.U.; Javaid, N.; Aldegheishem, A.; Alrajeh, N.; Tahir, M.; Ramzan, M. Scheduling Charging of Electric Vehicles in a Secured Manner by Emphasizing Cost Minimization Using Blockchain Technology and IPFS. Sustainability 2020, 12, 5151. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, Y.; Li, D.; Han, L. An optimal scheduling algorithm for hybrid EV charging scenario using consortium blockchains. Future Gener. Comput. Syst. 2018, 91. [Google Scholar] [CrossRef]
- Energy Web Foundation Launches Worlds First Public, Open-Source, Enterprise-Grade Blockchain Tailored to the Energy Sector. Available online: energyweb.org (accessed on 1 September 2020).
- Burgahn, C. Launch of the Open Charging Network. Available online: shareandcharge.com (accessed on 1 September 2020).
- Cerf, M.; Matz, S.; Berg, A. Using Blockchain to Improve Decision Making That Benefits the Public Good. Front. Blockchain 2020, 3, 13. [Google Scholar] [CrossRef]
- Singh, P.; Singh, R.; Nandi, S.; Ghafoor, K.; Rawat, D.B.; Nandi, S. An Efficient Blockchain-Based Approach for Cooperative Decision Making in Swarm Robotics. Internet Technol. Lett. 2019, 3, e140. [Google Scholar] [CrossRef] [Green Version]
- Abbaspour, A.; Mokhtari, S.; Sargolzaei, A.; Yen, K.K. A Survey on Active Fault-Tolerant Control Systems. Electronics 2020, 9, 1513. [Google Scholar] [CrossRef]
- Mokhtari, S.; Abbaspour, A.; Yen, K.K.; Sargolzaei, A. A Machine Learning Approach for Anomaly Detection in Industrial Control Systems Based on Measurement Data. Electronics 2021, 10, 407. [Google Scholar] [CrossRef]
- Nair, M.; Sutter, D. The Blockchain and Increasing Cooperative Efficacy. Indep. Rev. 2018, 22, 529–550. [Google Scholar]
- Khan, A.T.; Cao, X.; Li, S.; Milosevic, Z. Blockchain Technology with Applications to Distributed Control and Cooperative Robotics: A Survey. Int. J. Robot. Control 2019, 2, 36. [Google Scholar] [CrossRef] [Green Version]
- Hexmoor, H.; Alsamaraee, S.; Almaghshi, M. BlockChain for Improved Platoon Security. Int. J. Inf. 2018, 7, 1–6. [Google Scholar]
- Ledbetter, B.; Wehunt, S.; Rahman, M.A.; Manshaei, M.H. LIPs: A Protocol for Leadership Incentives for Heterogeneous and Dynamic Platoons. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; Volume 1, pp. 535–544. [Google Scholar] [CrossRef]
- Ying, Z.; Yi, L.; Ma, M. BEHT: Blockchain-Based Efficient Highway Toll Paradigm for Opportunistic Autonomous Vehicle Platoon. Wirel. Commun. Mob. Comput. 2020, 2020, 1–13. [Google Scholar] [CrossRef]
- Saiáns-Vázquez, J.V.; Ordóñez-Morales, E.F.; López-Nores, M.; Blanco-Fernández, Y.; Bravo-Torres, J.F.; Pazos-Arias, J.J.; Gil-Solla, A.; Ramos-Cabrer, M. Intersection Intelligence: Supporting Urban Platooning with Virtual Traffic Lights over Virtualized Intersection-Based Routing. Sensors 2018, 18, 4054. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Regnath, E.; Steinhorst, S. CUBA: Chained Unanimous Byzantine Agreement for Decentralized Platoon Management. In Proceedings of the 2019 Design, Automation Test in Europe Conference Exhibition (DATE), Florence, Italy, 25–29 March 2019; pp. 426–431. [Google Scholar] [CrossRef]
- Pashayev, I. Reducing Computational Waste: Space and Usefulness. Available online: https://crypto.stanford.edu/cs359c/17sp/projects/IskandarPashayev.pdf (accessed on 1 September 2020).
- How to Determine the Cost of Blockchain Implementation? Available online: https://www.leewayhertz.com/cost-of-blockchain-implementation/ (accessed on 1 September 2020).
- Blockchain Solution Implementation. Available online: https://www.tpptechnology.com/blog/blockchain-solutions-implementation-how-much-does-it-cost-in-2020/ (accessed on 1 September 2020).
- Sedlmeir, J.; Buhl, H.; Fridgen, G.; Keller, R. The Energy Consumption of Blockchain Technology: Beyond Myth. Bus. Inf. Syst. Eng. 2020, 62. [Google Scholar] [CrossRef]
- K, A.; Verma, P.; Southernwood, J.; Massey, B.; Corcoran, P. Blockchain in Energy Efficiency: Potential Applications and Benefits. Energies 2019, 12, 3317. [Google Scholar] [CrossRef] [Green Version]
- Zhou, Q.; Huang, H.; Zheng, Z. Solutions to Scalability of Blockchain: A Survey. IEEE Access 2020. [Google Scholar] [CrossRef]
- Hazari, S.; Mahmoud, Q. Improving Transaction Speed and Scalability of Blockchain Systems via Parallel Proof of Work. Future Internet 2020, 12, 125. [Google Scholar] [CrossRef]
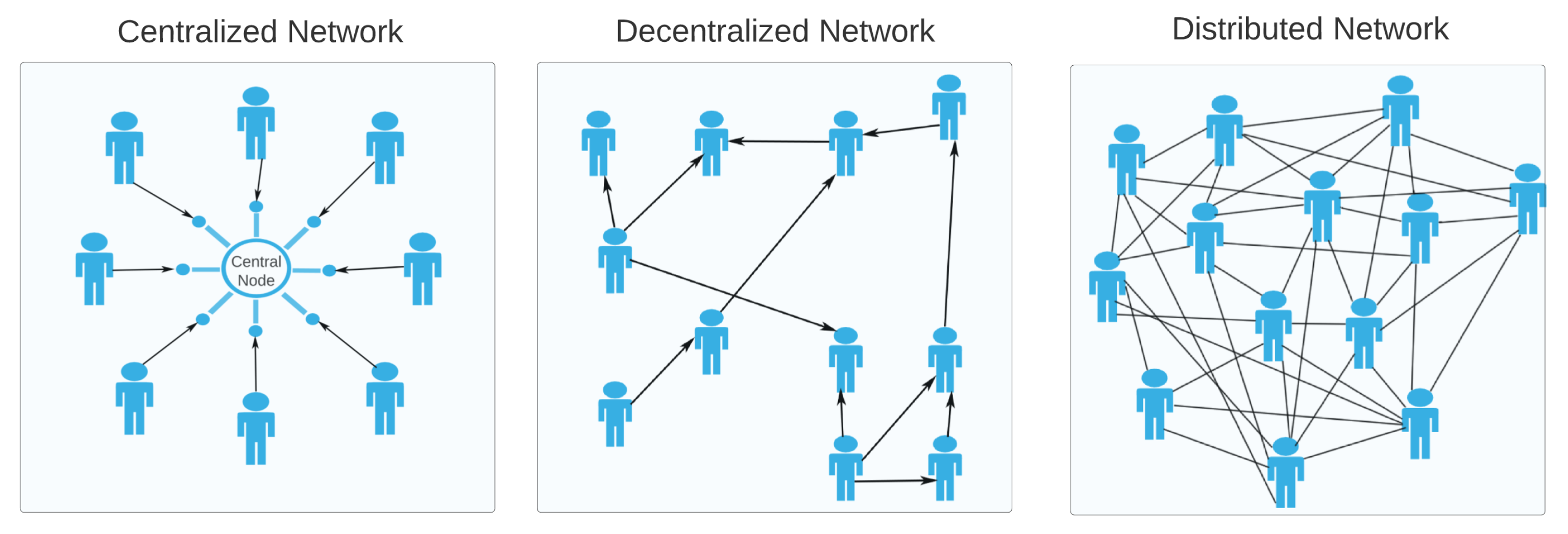
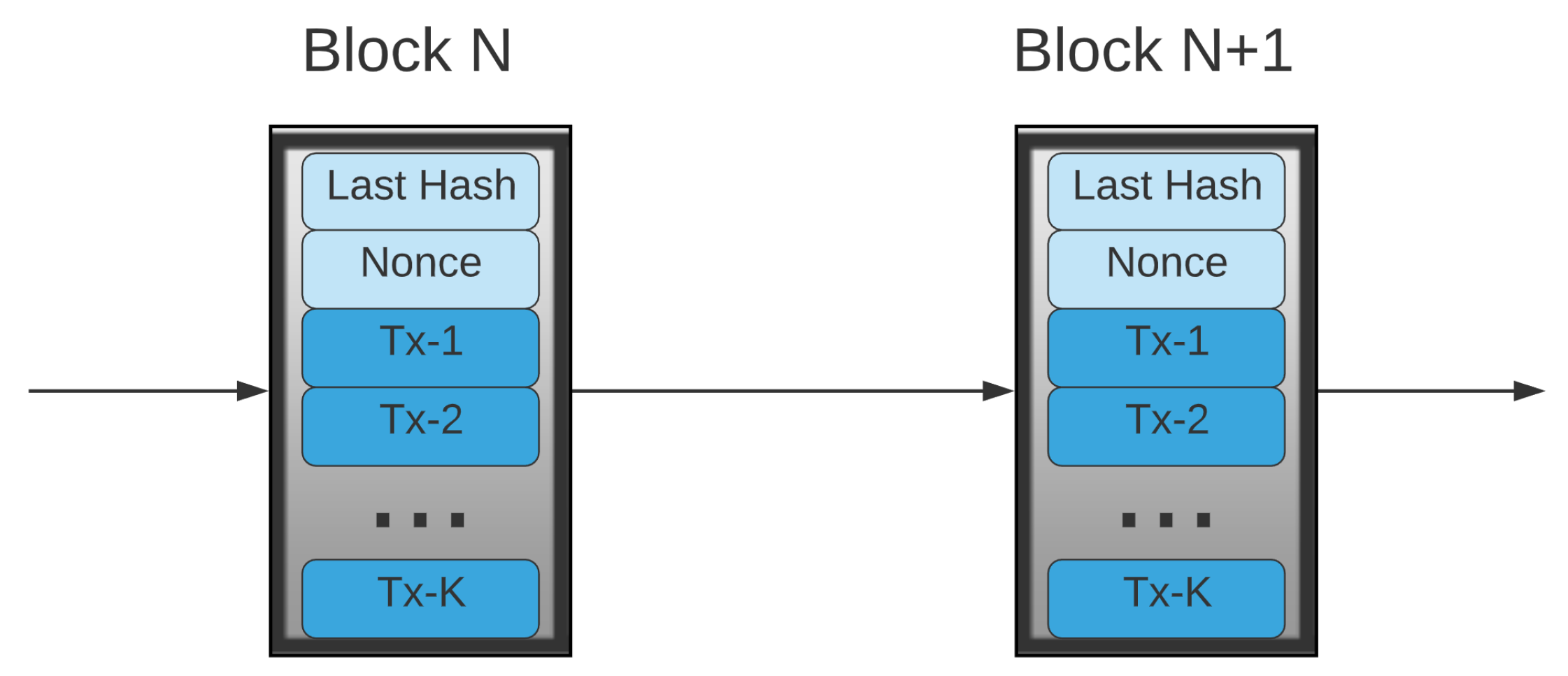
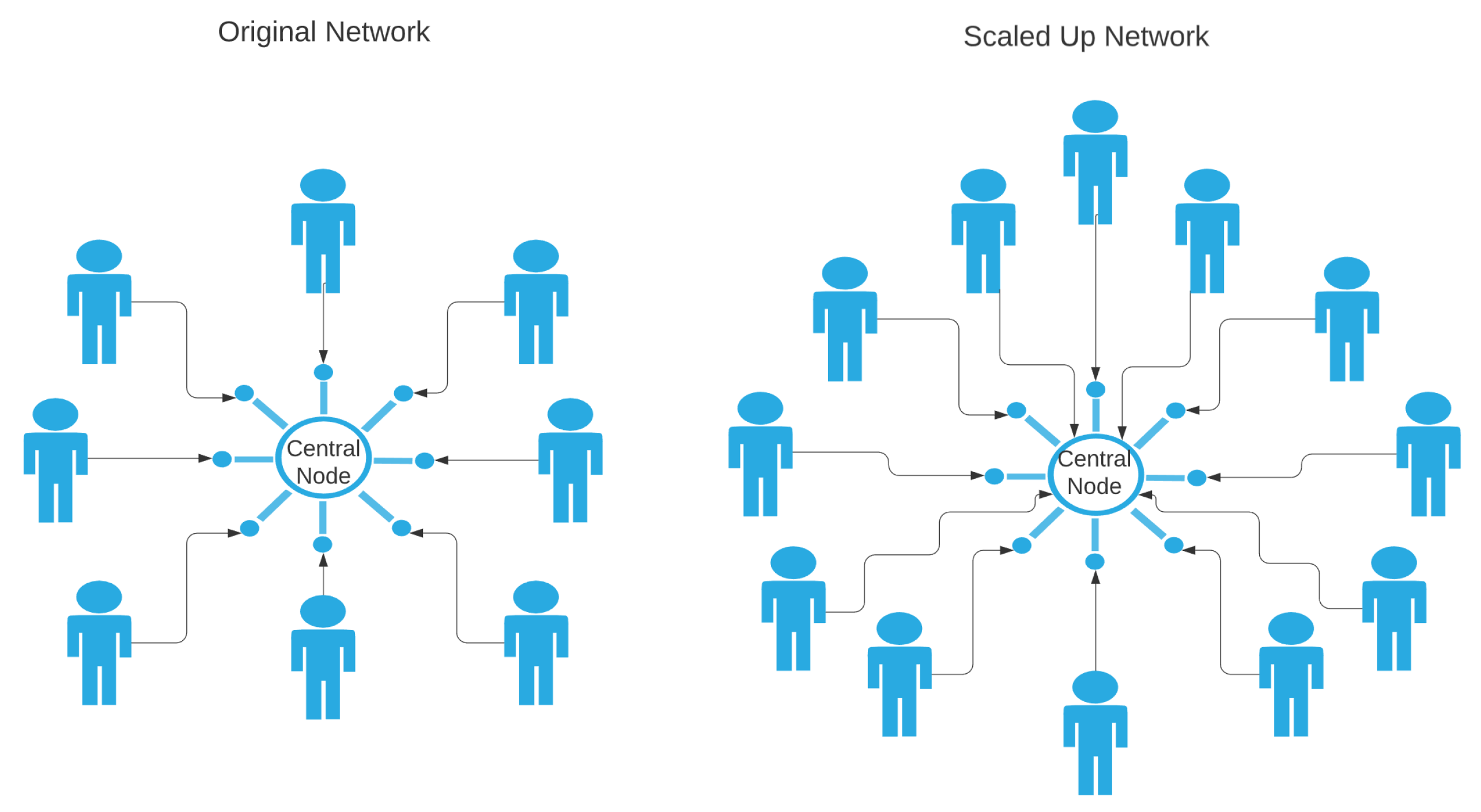
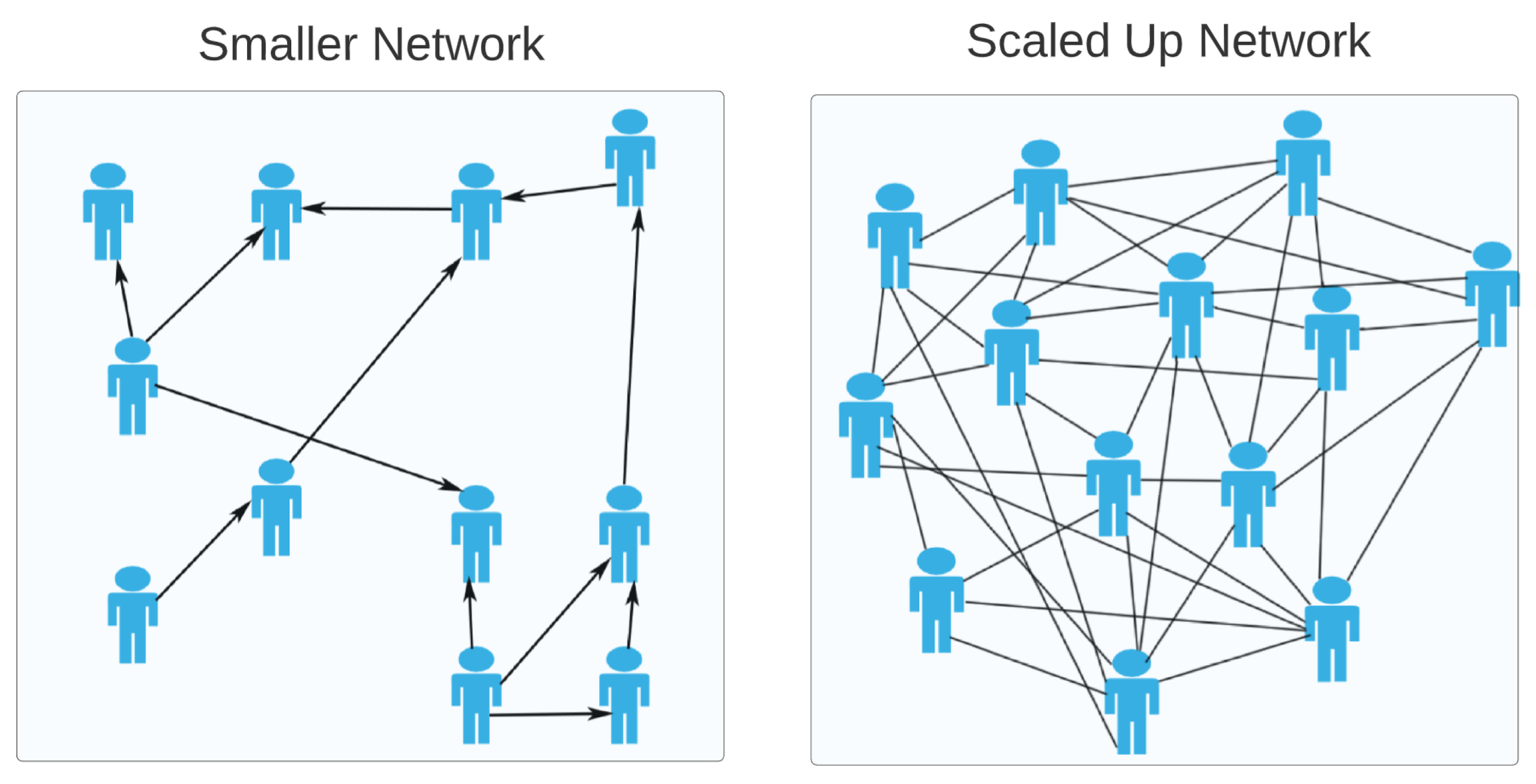
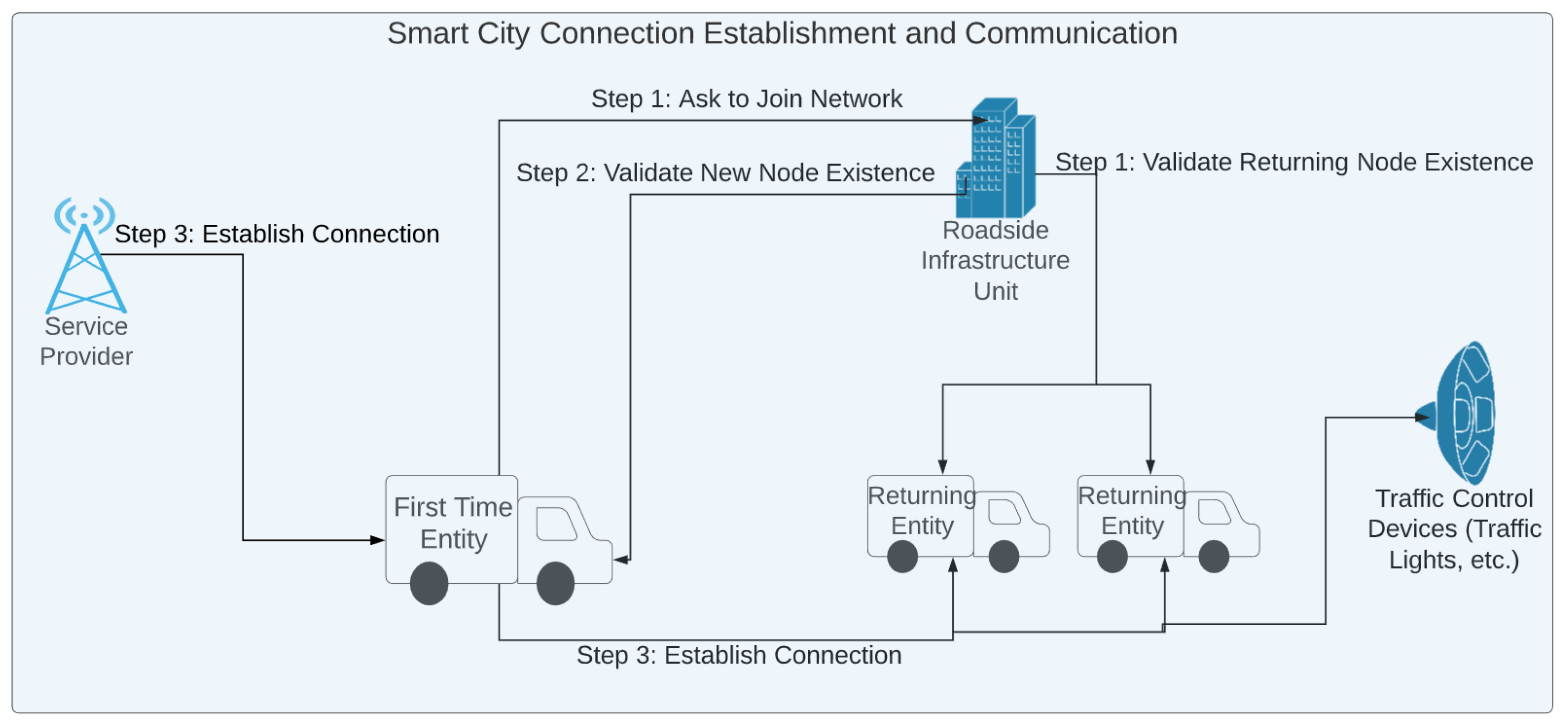
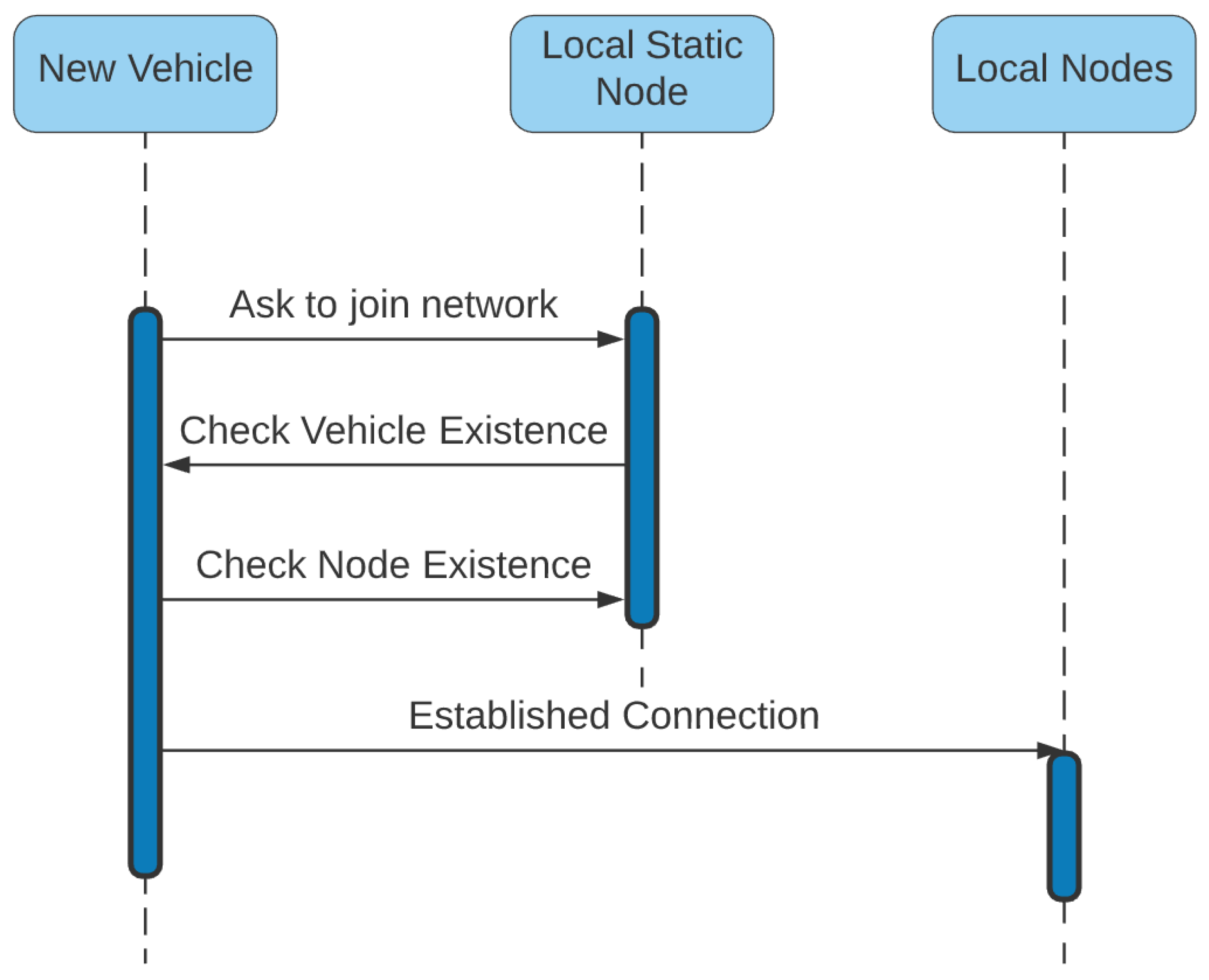
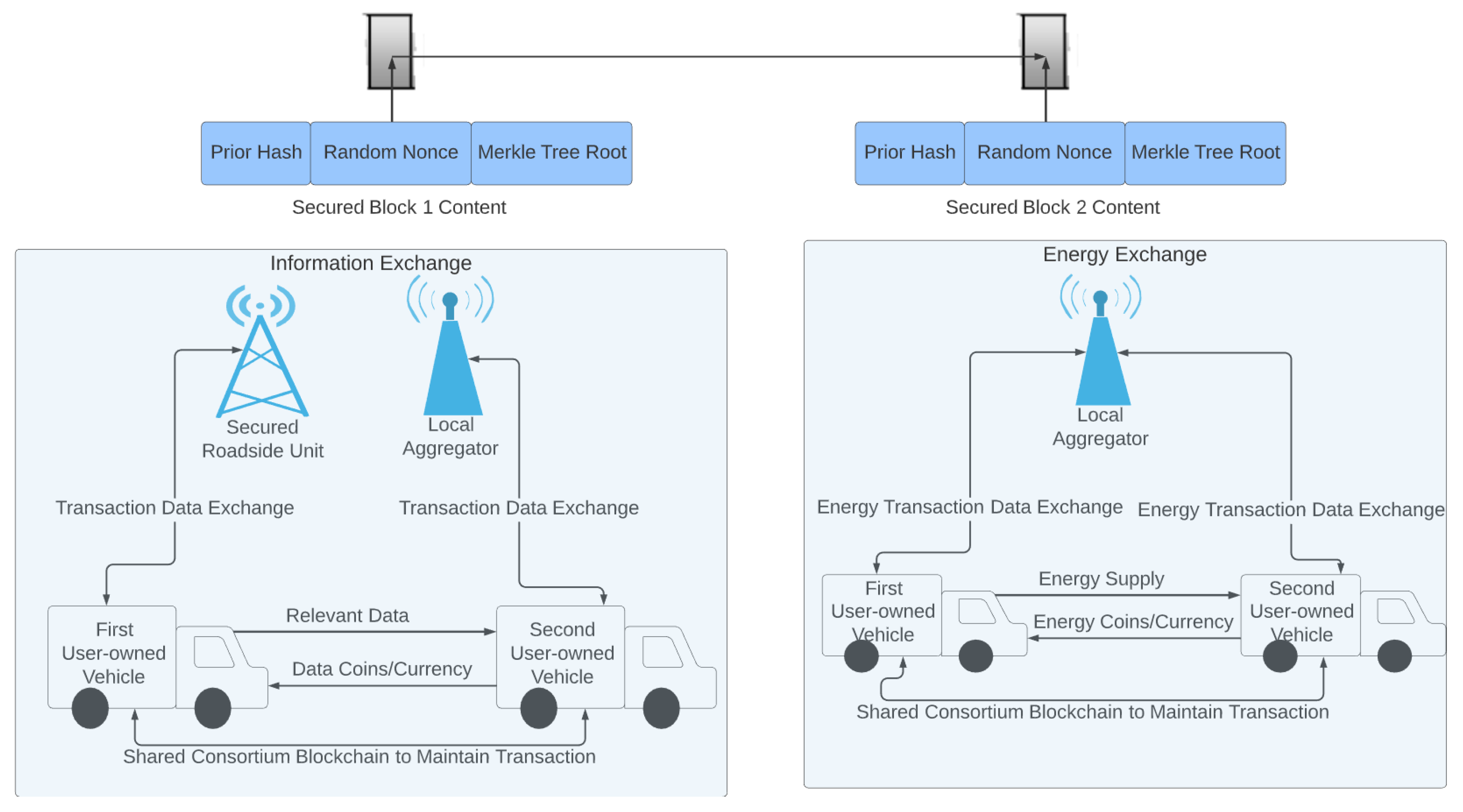


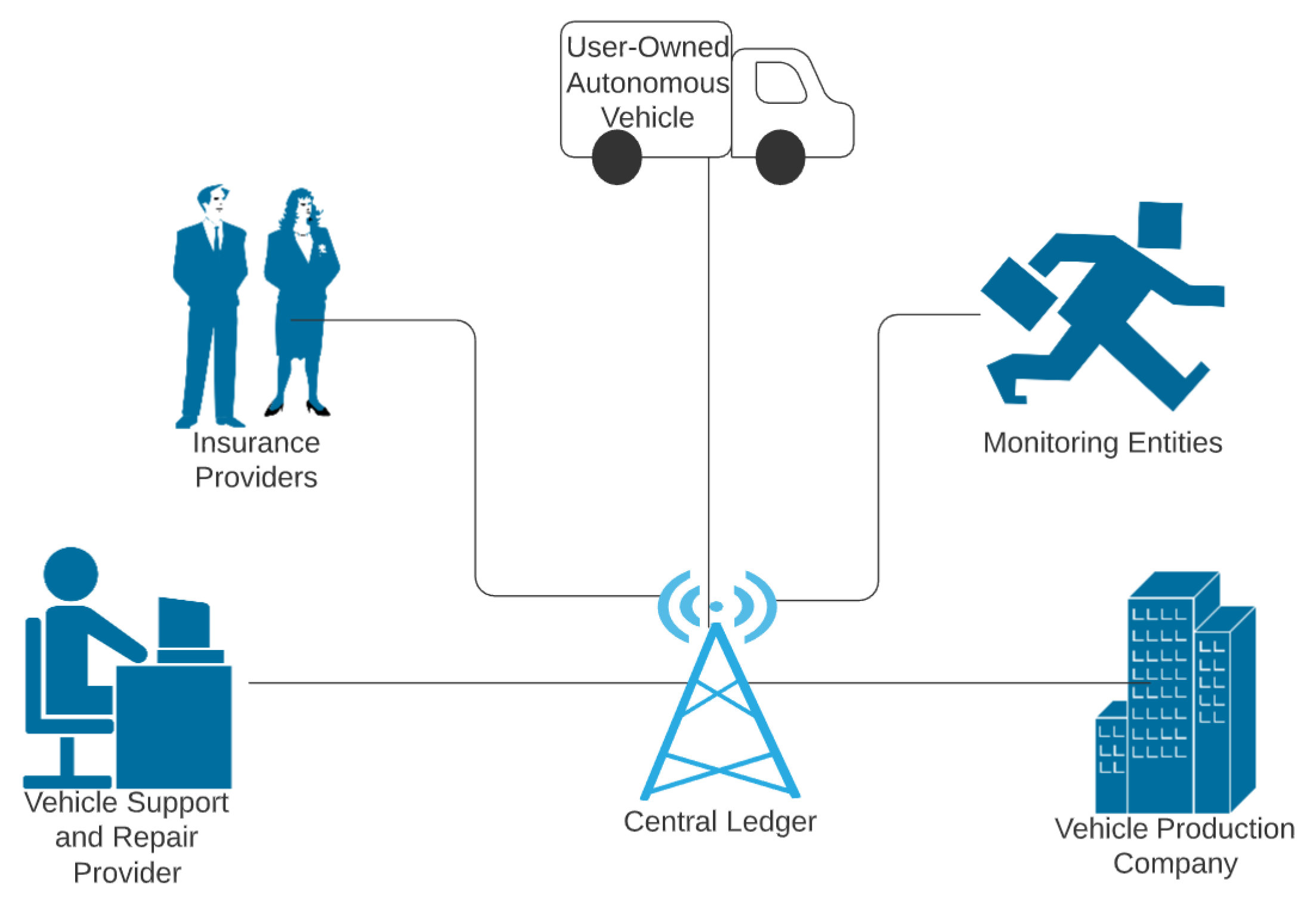
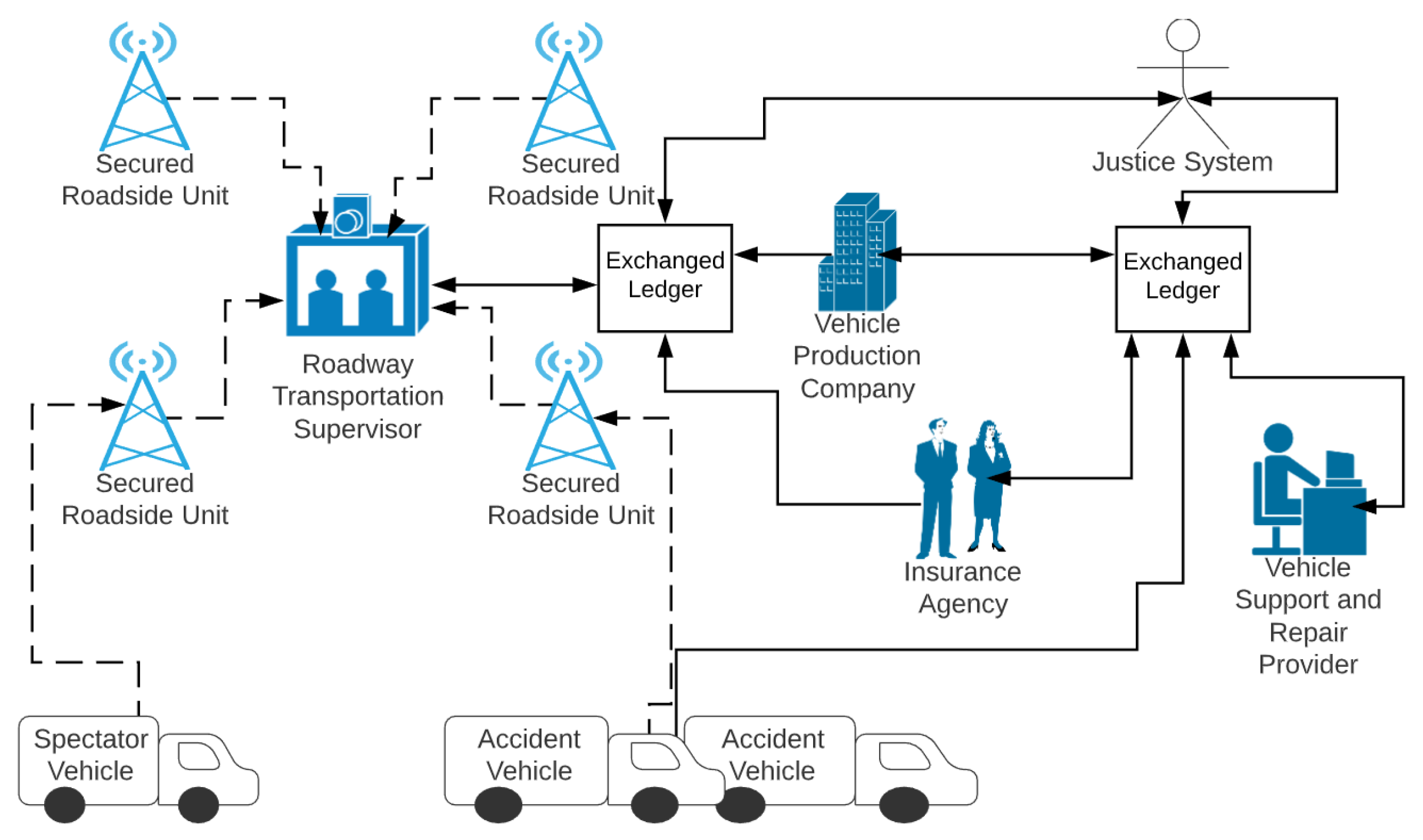
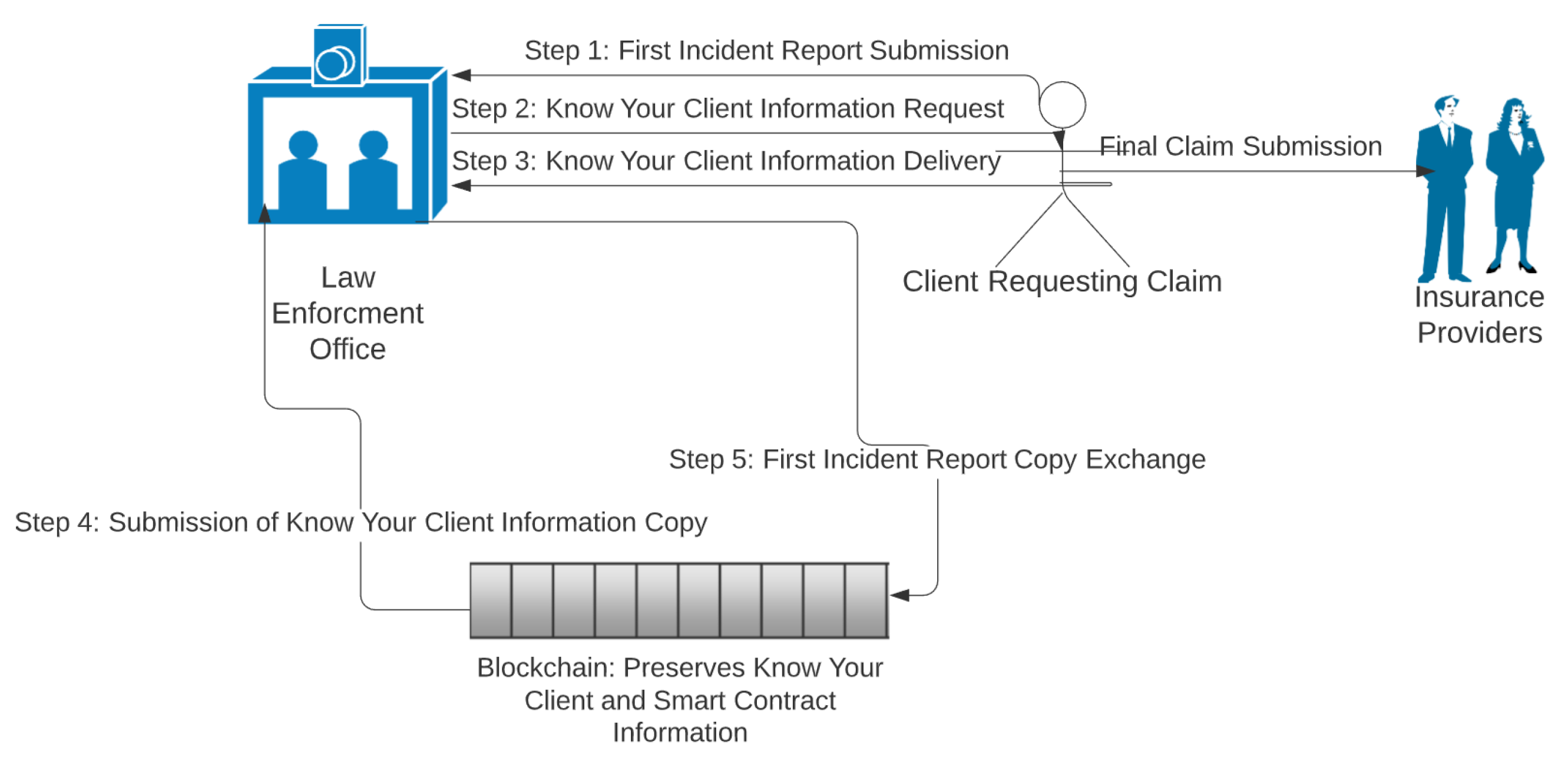
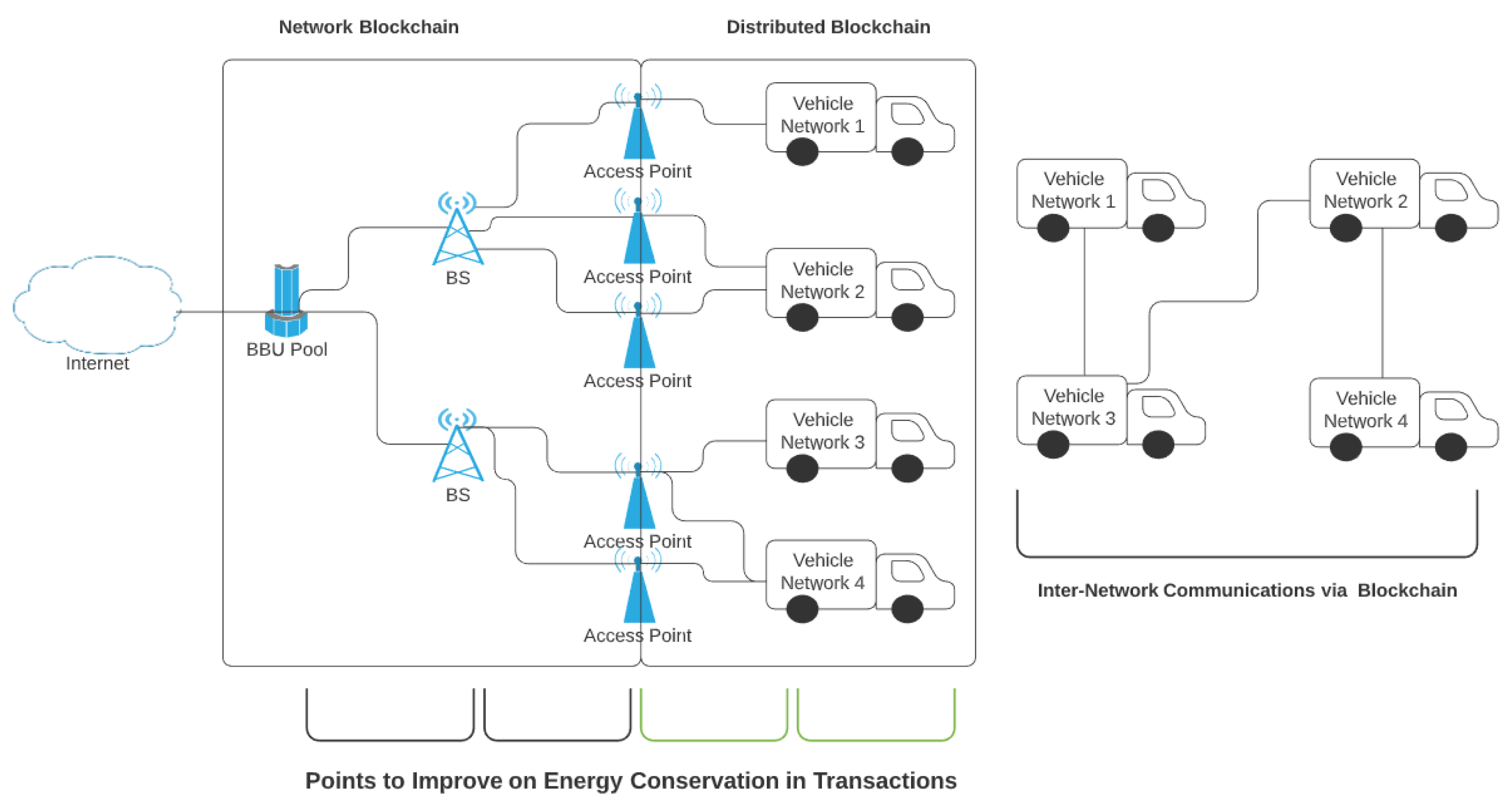
| Centralized Problems | Blockchain Solutions |
|---|---|
| Requires Trusted Authority | Trustless System |
| Scalability Issues | System Scales with New Users |
| Information is Modifiable | Immutable Blocks Using Hashes |
| Identities are not Anonymous | Cryptographic Keys as Pseudo-Identifiers |
| Security against Known Exploits | Focused Validation Protocols |
|---|---|
| Low Communication Complexity | Vehicle Integrity Checks |
| Minimal Latency | Dynamic Node Tolerance |
| Resistant to DoS Attacks | Faulty Node Tolerance |
| Low Energy Cost | High Scalability |
| Consensus Finality | Fast Error Handling |
| Model Proposed | Blockchain Type | Advantages | Drawbacks |
|---|---|---|---|
| BARS [10] | Certificate-based blockchain (CerBC) and revoked public key blockchain (RevBC) | Security and trust, authentication, low time/space overhead, anonymity and privacy. | Few results and performance analysis from few experiments and no large implementation. |
| Self-managed VANET [63] | Ethereum | Decentralized network, fast and reliable operation, no single failure point, secure communications, allowed user applica-tion use. | Customers charged fees for commu-nication and app use in Ethereum-gas, they pay for network. |
| Intelligent Vehicle Framework Model using Blockchain [64] | - | Security and privacy, IV-TP for speed. Records of communication, tamper-resistant, well-defined layering system for model. | No tests carried out, beyond system analysis, no results or space or time analysis. |
| Blockchain-based Connected CAV Framework [20] | - | Appropriate data hiding, transparency, data verification. Improvement in attack mitigation from previous methods due to blockchain. | Results from simulations only. No time/space analysis. Approach works well only after certain time interval. Many attackers can still compromise network. |
| Elliptic Curve Digital Signature Algorithm Based Approach [65] | Exonum | ECDSA securely inputs and validates information, blockchain secures vehicle state data. | No testable system, vague imple-mentation. ECDSA relies on users, but users can be unreliable. |
| Proof-of-Event VANET [12] | - | Higher success rate in attack detection and decision speed. Secured and pri-vate communications, but verifiable from transparency. | Performance is compromised when few vehicles are in an area. Physical tests not done. |
| Blockchain-Based Firmware Update Scheme [14] | Ethereum | Update scheme is peer-to-peer and hard to attack, many sources for fast updates, users are rewarded to maintain network. Effective and fast security, validity. Over- load prevented through peer-to-peer ar-chitecture. | No working model, so no tests done to see performance in real world. Users may not have update soon: some far from distributors. |
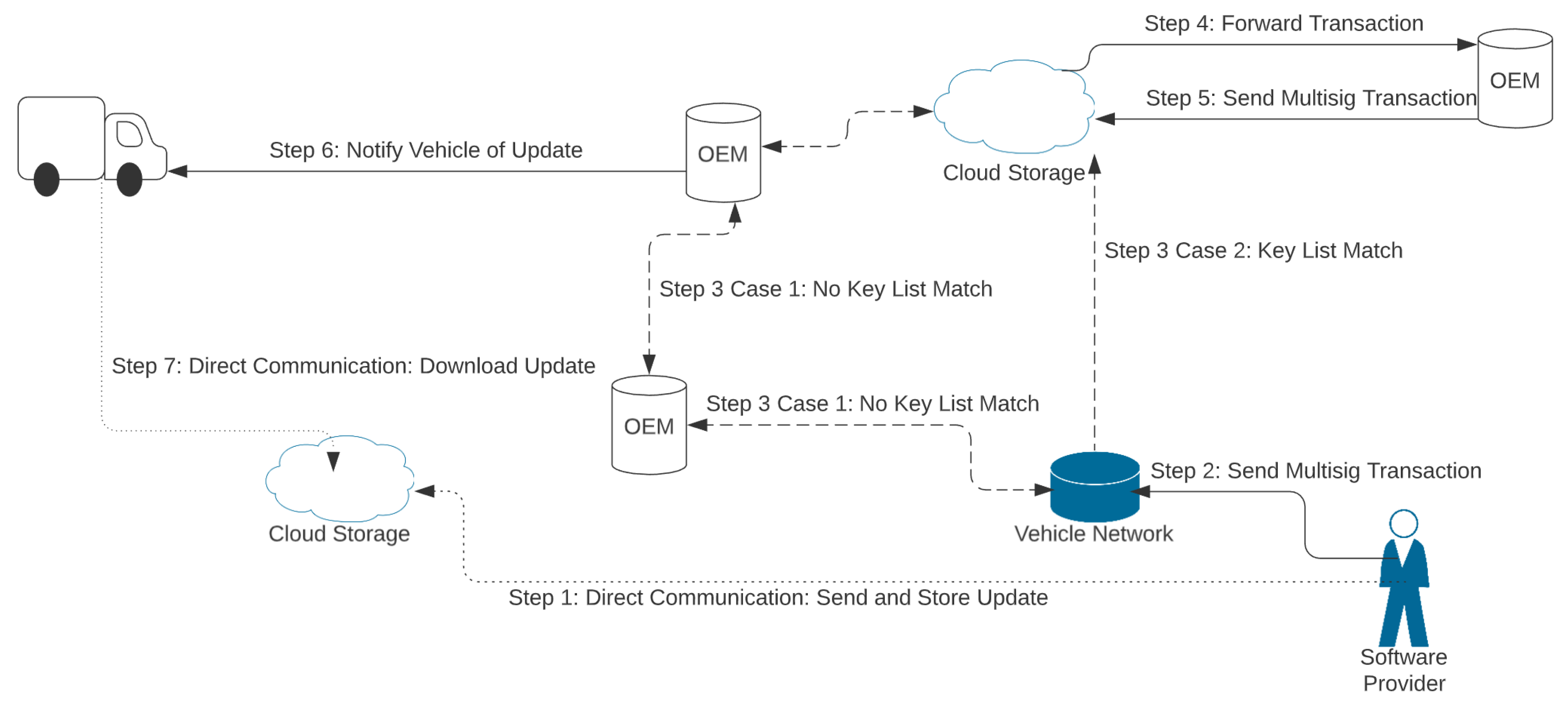
| Blockchain-Based Cloud Update Scheme [13] | Lightweight Scalable Blockchain (LSB) | Access to updates through cloud storage, updates verified for security and integrity, providers safely send updates to users, privacy, hash function prevents malicious node access. DDoS attacks are impossible. | Large overhead through various operations to check update security before download, cloud provides all software, which may compromise. No tests or implementation. |
| Side-Channel Blockchain- Based Security [15] | Bitcoin | Side-channels with blockchain have many protections, if one is compromised, other is used. Physical security allows direct communications with nearby vehicles, can be applied to ensure features between vehicles, like proper spacing. Side-channel protects against wireless transmission interception. | Side-channels lost from outside conditions, causes insecurity. Low performance and speed. No extensive system testing. Vague implementation details. |
| Blockchain-Based Vehicle to Vehicle and Vehicle to Infrastructure Communications [66] | Branch-Based (Local dynamic and main blockchain combination) | Security in communications, user trust promotion by blockchain use. Branching is more lightweight than most blockchain, vehicles operate in real-time. | Test results are simulated. Vague implementation structure. |
| SpeedyChain [17] | SpeedyChain | Security with blockchain, integrity through hash functions and condition records. User privacy through timed key changes. System is immune to Sybil attacks and data tampering with SpeedyChain. Performance higher than that in Bitcoin blockchains, and others reliant on PoW. | Limited testing, no space and time analysis. Speed increases a lot with transactions when many vehicles are in a system. |
| Blockchain-Based Device Management Framework for Smart Cities [67] | Private Blockchain, similar to Ethereum | Data integrity and scalability through blockchain. Management system is applicable to any device type so each is secured. Energy use lowered with proof-of-stake to manage smart contracts. Outline detailed and accounts for many attacks. | No testing or estimated performance in real-world. |
| Model Proposed | Blockchain Type | Advantages | Drawbacks |
|---|---|---|---|
| Blockchain-Aided Transport Transaction System [18] | - | Public, accessible transport via CAV through an app, high availability in any location. Blockchain eases transactions, and can be applied to parking and tolls. Blockchain can also add security to transactions, peer-to-peer based. | Vague description, no real system details. Mentioned privacy, security, and ethical concerns with no exact solution. No time/space analysis. |
| Autonomous Transaction System [77] | - | A structure outlining a unique approach for each feature integration, ensuring no lax measures in optimizing each. Features contribute to ease of operating vehicles and increased accessibility to users who are not confident driving or performing actions relating to vehicles. | Very vague outline, no implementation detail. No time/space analysis, only base features. |
| Vehicle Transaction System [78] | - | Defined, comprehensive layered blockchain to cover all functions, blockchain allows new functions, like financial transactions for parking or wi-fi. | Vague outline, no implementation detail. No time/space analysis, just potential. |
| Car eWallet [79,80] | Hyperledger | Transactions are possible, service and good detection by vehicle, actions can be performed with little user effort, present use, testing, and implementation with great success. Security and records through blockchain. | The technology has not been very widely implemented yet, and many of its promised features have yet to be incorporated. |
| Decentralized Transport Network [21] | - | Comprehensive discussion of past implementation, different types of blockchain, and use in securing and allowing transport-based transactions. Predictions for future use and how it could be implemented, focus on decentralization. | Vague implementation detail, more a list of desired features, future growth, and potential based on past use. |
| Blockchain-Based ITS [82] | Ethereum | Intensive model to handle all operation of blockchain, discussion of past blockchain use and application, like decentralization, trust, and network device security. Decentralization greatly benefits potential services offered. | No actual implementation of model, no tests, and no time/space analysis. More focus on potential and under-lying blockchain than how it will be implemented with CAVs. |
| Blockchain-Aided EVCE [83] | Consortium | Defined resource-sharing models to further peer-to-peer transaction availability between cars. Encouragement of user contribution of data and energy. Decentralized, enhanced services, multiple security outlines. | No tests or implementation, and no time/ space analysis. |
| Chorus V2X Model [84] | Ethereum | Prototype implementation and testing. Blockchain use for security, blockchain enables service and good transactions, like transport or maintenance. Unified platform insures compatibility between networks. Flexibility in transaction details and execution. Requirement analysis. | No full system implementation, no time/space analysis, no testing carried out. |
| Model Proposed | Blockchain Type | Advantages | Drawbacks |
|---|---|---|---|
| Event Record System [95] | N/A | Invulnerability to many common attacks, detailed outline of system to maintain driving record information, accessible in case of accidents or calculating insurance information. Data can not be altered and is accurate based on information from several parties. | No simulated or real-world testing done. When no witness or verifier is present, the system does not record accidents. No time/space analysis. |
| Crash Data Record System [97] | Permissioned | High security, tamper-resistant, crash data collected and verified by several parties. Extensive security analysis and model outline. Accurate records for use by authorized parties. | No simulated or real-world testing done. No time/space analysis. |
| Vehicular Digital Forensics System [98] | Permissioned | High security and privacy. Mitigates space concerns by storing hash data. Maintains driving records for authorized parties in case of accident or insurance, which are accurate and assured by vehicle systems. | No simulated or real-world testing done. No time analysis, and hash value use means records are deleted after a time depending on storage in devices. |
| Layered Vehicular Crash Data System [99] | Permissioned | Well-defined, layered blockchain system to manage crash information, several vehicle reports used to figure out event, class separation of parties improves organization and efficiency of system. High security and reliability of data, conversation records kept between devices. | No simulated or real-world testing done, no time or space analysis. |
| Several Insurance-Based Blockchain Systems [101] | - | There are several different future applications discussed, like vehicle insurance claims submission and damage reports, with step-based outlines of how they work. | No actual full outline, more loose concepts on potential applications and a basic outline of how they work. Very few specific details. |
| Autonomous Insurance Claim Management System [102] | Permissioned | High security, tamper-resistant data, improved operation time, high data reliability. Working simulation with promising results. | Results gained from simulation only, no real-world testing. No space analysis or consideration. |
| Delivery Recording System [103] | - | Several different applications of blockchain in autonomous vehicle systems discussed, particularly in event record keeping. Extensive information on future uses and how blockchain helps. | No full system outline, more ideas on how blockchain can expand with vague application details. |
| Transport-Based Transaction System [19] | Ethereum | Architectural outline for full transport-based service providing network. Secure communication, fast execution time, method for privacy of users, and availability of communications that can be applied to let users buy transport-related services. | No simulated or real-life testing done. There are attacks it can be hit by, like overwhelming state channels by having a large user close all of its channels simultaneously or mass ignorance of certain communications by users. |
| Model Proposed | Blockchain Type | Advantages | Drawbacks |
|---|---|---|---|
| Hyperledger-Based Intersection-Traversal Algorithm [114] | Hyperledger | Working logic to determine priority and order, peer-to-peer structure to avoid overload or single failure point. Secure transactions and communications. | Operation time is too slow for real-time response, and unusable as a result. |
| Multi-Agent Autonomous Intersection Management System [115] | Private Hyperledger | Secured communications between vehicles and other vehicles or infrastructure-governing devices, in-depth explanation of how intersections are controlled to avoid collisions. | No tests or working implementation yet, no time/space analysis with roadway conditions. |
| Blockchain-Based Collision Avoidance [31] | Ethereum | Extensive testing and traffic reduction, and in turn, greater safety for drivers. Relatively high security and acceptable time and space use. | No real-life testing, only results are from simulations. Plaintext private keys, and anonymity is not ensured. |
| Blockchain-Based Collective Learning for Lane Changing [26] | - | Secure communications and group-based information retrieval, high malicious node detection and information reliability, higher lane change success rate, improved execution time and space. | There is greater difficulty in finding malicious nodes when they comprise a larger part of the network, so performance slightly degrades. All tests are simulated, there have been no real-world tests. No full execution time/space analysis. |
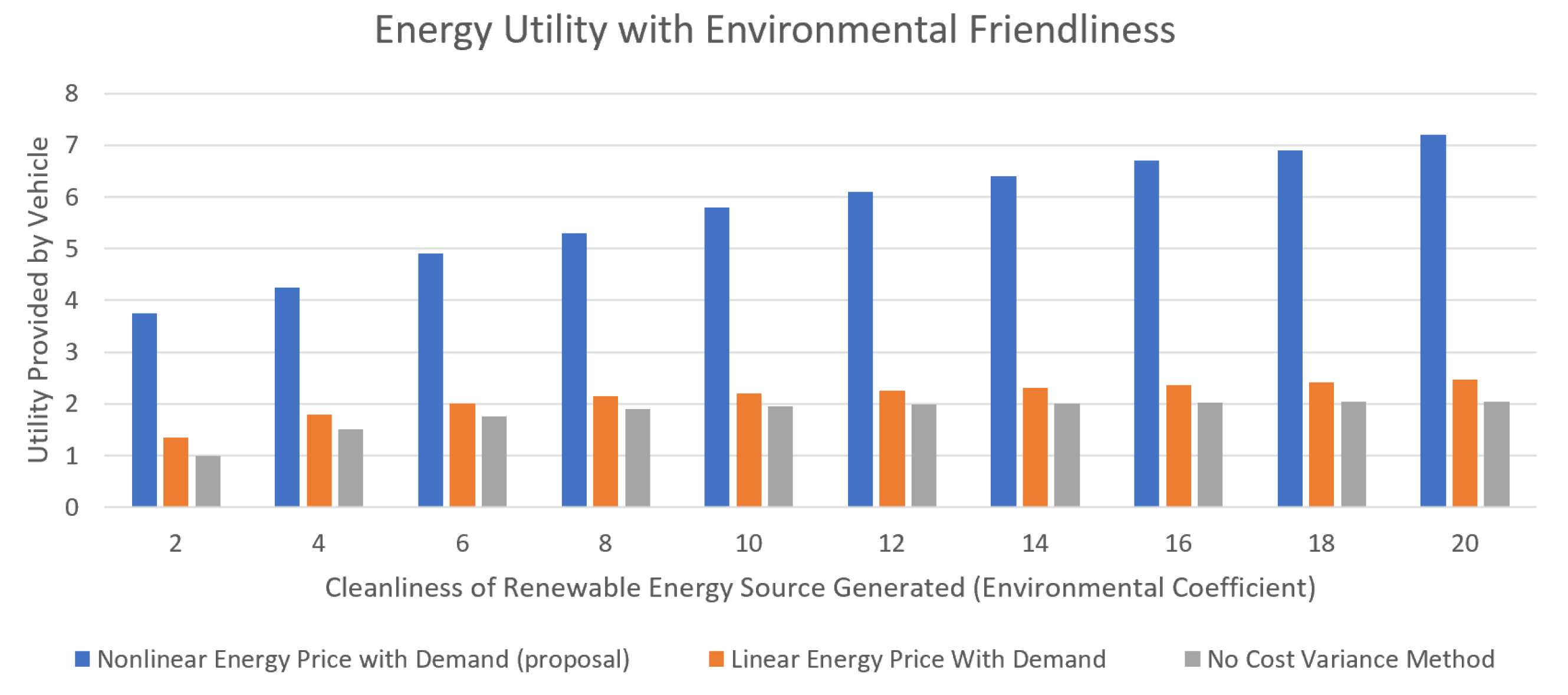
| Energy-Optimized Blockchain System [116] | - | Improved energy use, and reduced transaction number with no performance loss. Less network strain and high security in transactions. Extensive resource-use and performance consideration. | Limited testing, all results thus far are simulated, wide-scale testing is needed. |
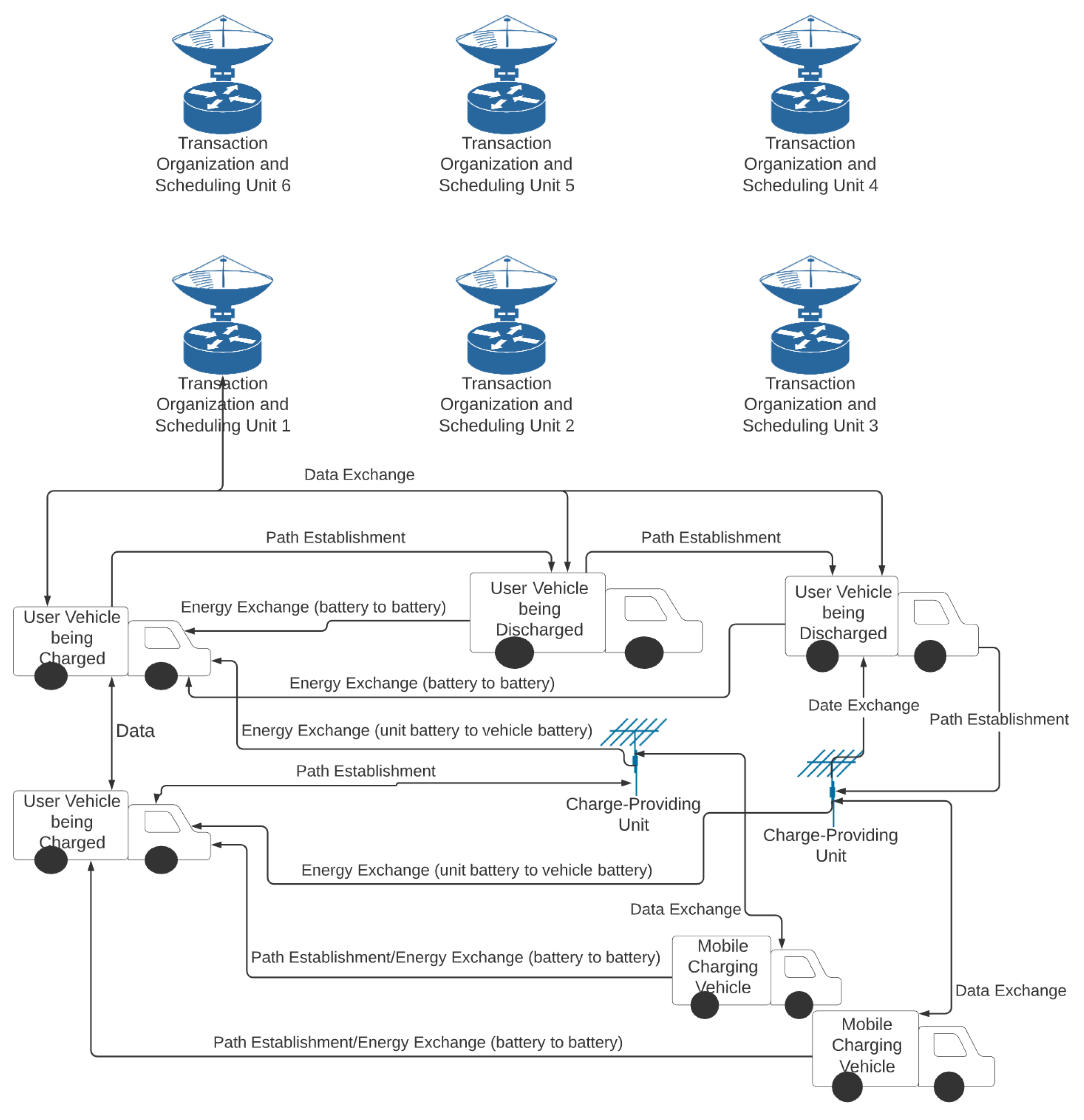
| Blockchain-Based Energy Trading Network | Ethereum | Well-outlined energy management and exchange system outline and simulation testing. Ability for several different transaction types for energy, like bidding and offering in auctions. Decentralized network to avoid overload and single failure point. High security and trust. | All testing done through simulations, no real-world condition test. No considera-tion for how full network will operate, just individual energy-providing units in it. |
| Permissioned Energy Blockchain [117] | - | Improved energy management through use and demand analysis, decentralized network. High security, consensus, and information reliability through reputation analysis. Optimized charge station utility, and overall optimized use in turn. | Little testing has been carried out on this model, no real-world implementation, all results are simulated so far. |
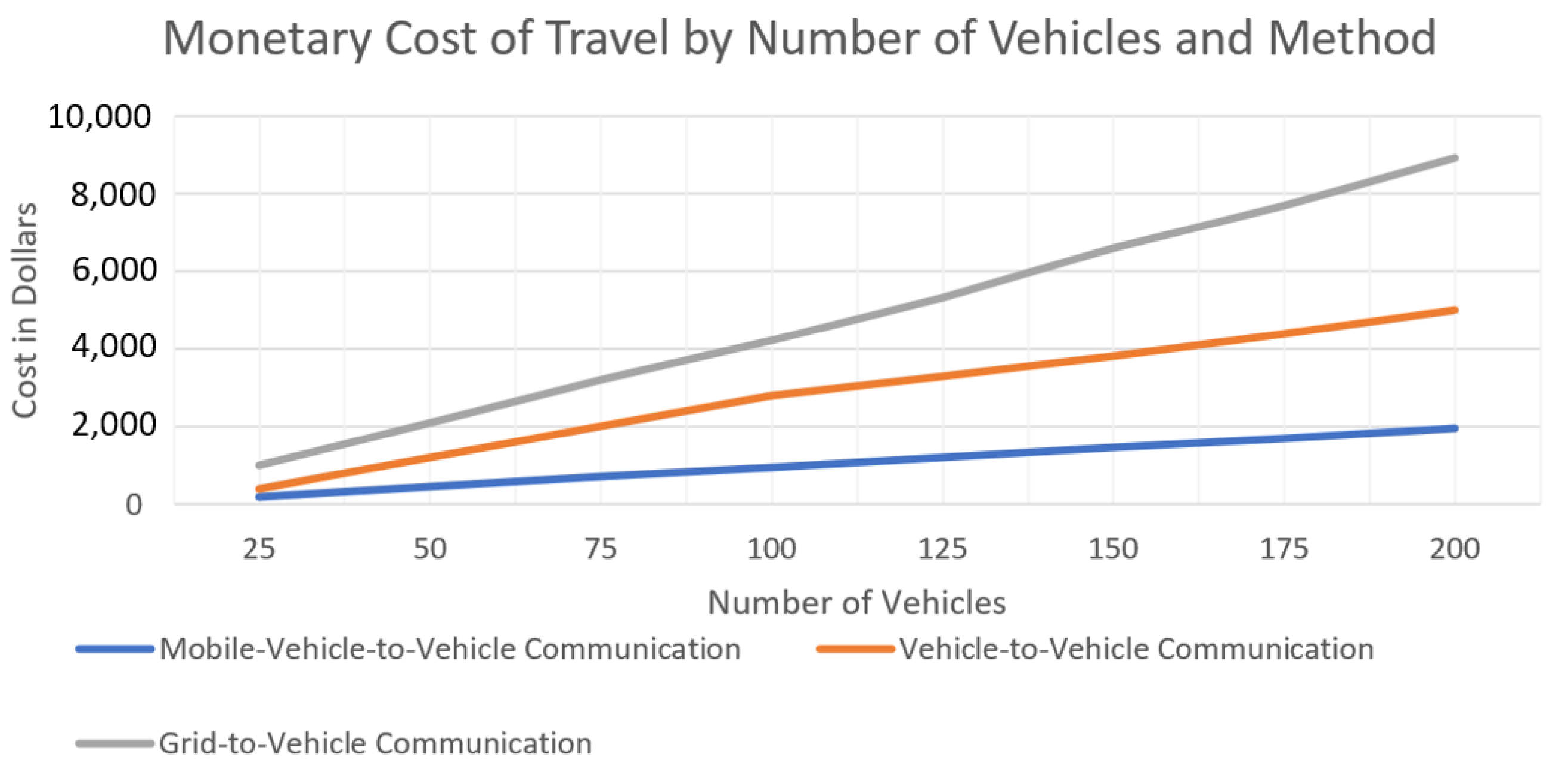
| Energy-Exchange System [118] | Consortium | Decentralized system, reduced cost, and improved utility of charging systems through optimized charge schedule. Blockchain ensures security and trust, rewards given for active participation in network, and lowest distance from vehicle to charging system is calculated when needed. | All tests are simulated, may be inaccurate to real-world results. The model is not optimized, and presents concerns of high resource use that may drain the network or compromise security. Security can still be improved, as mentioned. |
| Scheduled Charge System [119] | Consortium | Improved operation of charge stations through charge schedule algorithm. High security and privacy, user benefits through demand and location considerations in determining a price, as well as hybrid architecture allowing for charge for all vehicle types. | All testing is done through simulation, no real-world analysis. No space analysis for proposed system. |
| Blockchain-Based Energy Network [120] | Ethereum | Implemented energy system, high security, detection of malicious nodes, energy efficiency and high scalability, accessible and cost-optimized energy for users. Open-source implementation for increased user access. | Limited implementation to a few company systems, not available to the public on a wide scale. Fairly new, so there is limited testing and performance analysis. |
| Blockchain-Based Open Charge Network [121] | Ethereum | Implemented network to charge user vehicles, open-source and highly available to users. High security, scalability, and lack of unnecessary additional middle parties in carrying out transactions. Fairly large-scale public implementation. | Limited use and test results due to it being a relatively new technology. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Khoshavi, N.; Tristani, G.; Sargolzaei, A. Blockchain Applications to Improve Operation and Security of Transportation Systems: A Survey. Electronics 2021, 10, 629. https://doi.org/10.3390/electronics10050629
Khoshavi N, Tristani G, Sargolzaei A. Blockchain Applications to Improve Operation and Security of Transportation Systems: A Survey. Electronics. 2021; 10(5):629. https://doi.org/10.3390/electronics10050629
Chicago/Turabian StyleKhoshavi, Navid, Gabrielle Tristani, and Arman Sargolzaei. 2021. "Blockchain Applications to Improve Operation and Security of Transportation Systems: A Survey" Electronics 10, no. 5: 629. https://doi.org/10.3390/electronics10050629
APA StyleKhoshavi, N., Tristani, G., & Sargolzaei, A. (2021). Blockchain Applications to Improve Operation and Security of Transportation Systems: A Survey. Electronics, 10(5), 629. https://doi.org/10.3390/electronics10050629






