1. Introduction
In a harsh mobile network environment, where stable routing paths from source mobile nodes to destination mobile nodes are not available, mainly due to the nonexistence of infrastructure and sparse density of mobile nodes, conventional self-organizing networks based on the existence of stable routing paths, such as mobile ad hoc networks (MANET) [
1], are not suitable to deliver messages from source nodes to destination nodes efficiently. In these networks, if a routing path is broken for a long time, the communication session between a source node and a destination node is disconnected, and messages are removed from the buffer memory of nodes. Therefore, a new communication model is needed to cope with the unstable connectivity problem, and delay-tolerant networking (DTN) [
2,
3,
4,
5] was proposed for this purpose. In DTN, a node has a bundle layer, which is located between a transport layer and an application layer, and messages can be stored for a long time at the buffer storage with the help of the bundle layer. Then, if a mobile node with messages in its buffer contacts another mobile node opportunistically while moving, it can forward messages to a contact node, and the forwarded messages are stored in the buffer of the receiving node. By using a series of opportunistic contacts between nodes, messages can be delivered to a destination node successfully in DTN, even though the delivery latency may be increased, compared to conventional self-organizing routing protocols based on stable routing paths, such as MANET.
DTN has its application mainly in deep space networks or military networks, since stable routing path between nodes is not available due to the long distance between nodes or sparse node density. Extensive work has been carried out for DTN routing protocols [
2,
3,
4,
5,
6,
7,
8]. Epidemic protocol [
6] is a flooding-based protocol, and a node forwards messages whenever it contacts another node, if the contact node does not have the messages already. It is simple but has significant traffic overload. In a Spray and Wait routing protocol [
7], the total number of message copies in a network is limited to L for each generated message. When a message is generated at a source node originally, it forwards L − 1 copies of messages to L − 1 contact nodes in the Spray phase until L nodes including the source node has exactly one copy of the message. In the Wait phase, the message is forwarded to a destination node only. Although the Spray and Wait routing protocol can alleviate the high overload problem of an Epidemic protocol, it is a blinded forwarding protocol basically, since messages are forwarded to L − 1 contact nodes blindly without any efficient forwarding criteria. In a PRoPHET protocol [
8], delivery predictability (DP) between any two nodes is calculated based on the contact history between nodes. If the delivery predictability between two nodes is higher, it is more probable to deliver messages between them. Therefore, if two nodes contact, they compare delivery predictability for the destination nodes of stored messages, and a message is forwarded to a contact node if a contact node has a higher delivery predictability to a destination node for the considered message. The PRoPHET protocol was standardized as an Internet Research Task Force (IRTF) request for comments (RFC) [
8] by the DTN research group [
9]. In [
10], the authors define quality of node, which is a weighted sum of message handling capacity and the improved delivery predictability. Then, they proposed an adaptive Spray and Wait routing protocol based on quality node by adaptively allocating the number of message copies based on the quality of the node in the Spray phase. In the Wait phase, a message is forwarded only if the contact node has a higher improved delivery predictability. In [
11], the authors proposed a vehicular DTN routing protocol, where the message forwarding decision is based on the encounter probability comparison in the PRoPHET protocol, and the number of message replications at forwarding is controlled based on the Spray and Wait protocol in the vehicular DTN networks.
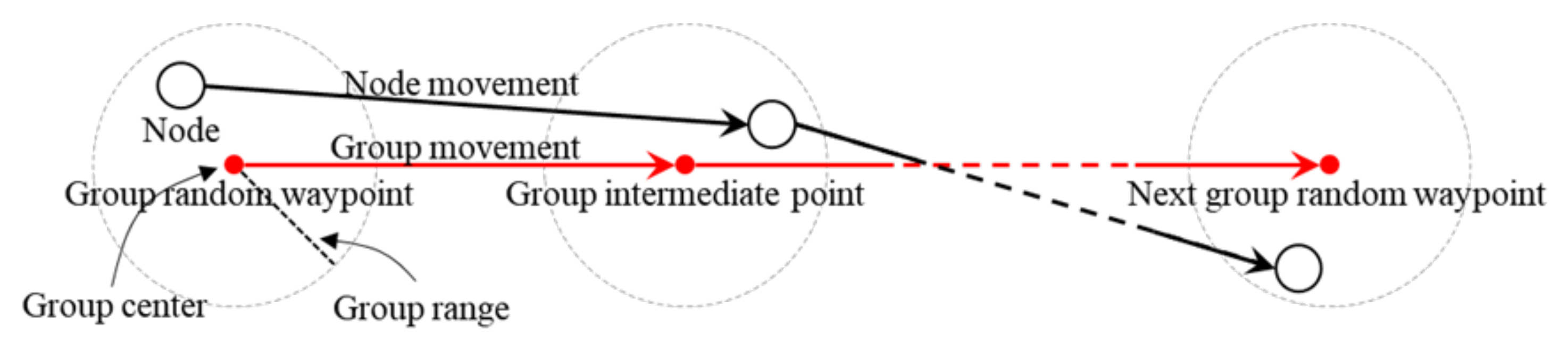
In some network environments, such as military networks, nodes movement follows a group mobility model [
12,
13,
14]. A group consists of a number of member nodes, and they move together based on an assumed group mobility model. In [
12], a reference point group mobility model (RPGM) was proposed. In an RPGM, there is a logical center in each group and the mobility of group members follows the movement of the logical center, which includes location, speed, direction, acceleration, etc. Group members are distributed uniformly within the geographic scope of a group. A reference point is assigned to each group member by following the group movement, and a group member is located in the neighborhood of its assigned reference point randomly at each movement. In [
13], an RPGM was extended by considering the velocity of groups and group members, and it was called as a reference velocity group mobility model (RVGM). In an RVGM, the mobility of each group is modeled by group velocity, and group members have velocities close to the group velocity, but the velocities have a slight deviation from group velocity. In [
14], the authors proposed an ellipse group mobility (EGM) model for tactical MANET, where nodes in a group located in an elliptic region and compared the performance of the EGM model with that of the RPGM. The results showed that the EGM model is better for intergroup communication and worse for intragroup communication.
Work on routing protocols by considering group mobility models have been carried out, too [
15,
16,
17,
18,
19,
20,
21]. In [
15], a DTN network for the military battlefield is considered, where nodes move in a group according to the reference point established by the leader node. Then, the authors compared the delay of the group mobility model with that of an entity mobility model using an Epidemic routing protocol. It was shown that the group mobility model has lower delay. In [
16], the authors considered a group mobility model and compared the performance of three MANET routing protocols, such as destination sequence distance vector (DSDV), ad hoc on-demand distance vector (AODV), and dynamic source routing (DSR) by considering an RPGM model and by varying pause time and mobility speed in a single group environment and the connection ratio between intra- and intergroup communications in a multiple group environment. In [
17], the authors proposed a novel group mobility model in tactical MANET, where wedge formation was used as the basic movement technique. The authors analyzed the effect of the dynamics of network connectivity of the proposed mobility model on the performance by assuming an AODV routing protocol. In [
18], a group Epidemic routing (G-ER) was proposed. In the G-ER, an AODV protocol was used for intragroup routing and an Epidemic protocol was used for intergroup routing. Additionally, the authors proposed a buffer sharing mechanism inside each group. In [
19], the authors analyzed the performance of an RPGM for MANET from the aspects of average throughput, energy consumption, and average end-to-end delay. They considered a network with a static node and a network with an RPGM model and applied AODV protocol and an ad hoc on-demand multipath distance vector (AOMDV) protocol to these networks. Analysis results showed that the AOMDV with an RPGM model was more appropriate when higher throughput or lower energy consumption was required. On the other hand, an AODV with an RPGM model was more appropriate when less delay was required. In [
20], the authors studied the feasibility of applying DTN architecture into an aircraft cluster network in order to cope with the intermittent communication links problem between aircraft—from the aspects of routing protocol, transport layer protocol, and safety issues. In [
21], the authors considered a future tactical-battlefield network, where ground nodes formed several small groups and an unmanned aerial vehicle (UAV) was used to enlarge coverage and increase connectivity among small groups. Then, they formulated a group connectivity optimization problem and data slot allocation optimization problem. A UAV positioning mechanism was proposed to maximize group connectivity and a dynamic slot allocation mechanism was proposed to maximize group connectivity utility.
In most of the work mentioned above, however, a MANET protocol was mainly assumed as the basic routing protocol for group mobility. In [
18], although a DTN protocol was assumed for intergroup routing, a MANET protocol was assumed for intragroup routing. In this paper, we consider a DTN protocol for both intra- and intergroup routing, since connectivity between group members in the same group may be broken due to the mobility and the destruction of nodes in a battlefield environment, and thus, a MANET routing protocol cannot work well, even for intragroup routing. Then, we propose an efficient DTN routing protocol with overload control for group mobility, which is an extension of our preliminary work in [
22]. The group mobility model and the basic idea of using group delivery predictability in addition to individual delivery predictability are similar to our preliminary work in [
22], but the work in this paper significantly extends the previous work in [
22]. Our proposed work’s main novelty and major contributions, which include a major extension from our preliminary work, are summarized as follows:
The proposed group mobility model was elaborated.
A proactive overload control protocol with overload control table was proposed in order to reduce the message forwarding of a message delivered to a node in the same group with a destination node.
A message forwarding condition and overload control protocol were efficiently combined for an efficient routing protocol with overload control for group mobility.
The performance of the proposed routing protocol with overload control was compared with comparing protocols, and the effectiveness of the proposed protocol was validated from the aspects of delivery ratio and overhead ratio.
The remaining part of this paper is organized as follows. In
Section 2, we propose a group mobility model and group delivery predictability model. In
Section 3, we describe an algorithm of the proposed protocol in detail using examples. In
Section 4, we analyze the performance of the proposed protocol extensively by using simulation. Finally, we conclude this work in
Section 5.
3. A Proposed Routing Protocol with Overload Control for Group Mobility
In this paper, we propose a routing protocol for group mobility. Depending on the relationship of the group of contact node , the group of contact node , and the group of destination node of a considered message, the message forwarding condition of the proposed protocol is classified as Cases 1, 2, 3, 4, and 5. Then, the forwarding of the proposed protocol operates as follows:
Case 1. If contact nodes and belong to the same group and also destination node belongs to the same group , a message is forwarded to node if .
Case 2. If contact nodes and belong to the same group but destination node belongs to different group , a message is forwarded to node if .
Case 3. If contact nodes and belong to groups and , respectively, and destination node belongs to the same group with node , a message is forwarded to node if , where the message dissemination promotion threshold, , is generally set as a small value to promote the dissemination of a message.
Case 4. If contact nodes and belong to groups and , respectively, and destination node belongs to group , a message is forwarded to node if , where the message dissemination restriction threshold, , is generally set as a large value to restrict the dissemination of a message.
Case 5. If contact nodes and belong to groups and , respectively, and destination node belongs to group , a message is forwarded to node if .
The basic rationale of the proposed forwarding condition is to use both individual delivery predictability and group delivery predictability together to make a forwarding decision efficiently if the group of a destination node is different from either a group of contact node
or a group of contact node
. Additionally, when a group of contact node
and a group of contact node
are different from each other, if a group of destination node
is the same as the group of contact node
only, the message dissemination is promoted. On the other hand, if a group of destination node
is the same as the group of contact node
only, the message dissemination is restricted.
Table 1 summarizes the forwarding conditions of the proposed protocol for Cases 1 to 5.
In addition to forwarding conditions proposed above, overload control is newly proposed in this paper. In DTN, messages are forwarded through opportunistic contacts and forwarding nodes are not aware of whether the generated message was delivered to a destination node successfully or not. Therefore, unnecessary forwarding of messages may occur even though the messages are delivered to destination nodes successfully already. To reduce this unnecessary forwarding of messages after successful delivery, a
vaccine scheme was proposed in [
24], where if a message is delivered to a destination node, an anti-packet for the delivered message is generated at a forwarding node. Then, the forwarding node does not receive the same message anymore, and it shares the anti-packet information with all contact nodes, and contact nodes remove the already delivered messages if they have them. Otherwise, they do not receive the message anymore. In this paper, we adopt an approach of the vaccine scheme [
24] for overload control and extend the approach to reduce overload further.
Firstly, if a message is delivered to a destination node, the “delivery state of a message to a destination node”, which acts similarly as an anti-packet in [
24], is recorded at the overload control table of the forwarding node as “delivered”. Then, this delivery information is shared with future contact nodes, and the already delivered message is removed from the buffer of the contact nodes in order to reduce unnecessary forwarding of already delivered messages, which is similar to the vaccine scheme [
24]. This protocol is called reactive overload control (OC) in this paper. The concept of reducing unnecessary forwarding of already delivered messages to a destination node in reactive overload control is similar to the work in our previous work [
25], where the concept of the anti-packet [
24] was also applied for multiple requesters and multiple caching nodes environment in DTN for information-centric networking (ICN) by defining a satisfaction flag for a pair of delivered data and requester.
Secondly, in order to carry out the overload control more proactively, we propose a proactive overload control. In the proactive overload control, if a message is delivered to a node that belongs to the same group as the destination node of the message, the “delivery state of the message to a node in the same group as the destination node” is recorded as “delivered” at the overload control table of the forwarding node additionally. Then, the message that is delivered to any node in the same group as the destination node can be delivered to a destination node only, i.e., direct delivery, without forwarding to any other nodes to reduce overload.
The rationale of the proposed proactive protocol is to use the direct delivery by the receiving node within the same group as the destination node for intragroup delivery, which may have higher delivery probability. The delivery state information is shared with future contact nodes, and a contact node with the already delivered message to a node in the same group as a destination node does not forward the message to any other nodes, except the destination node, too. We note that the message delivered to a node in the same group as a destination node is not removed from the buffer of contact nodes, although it is not permitted to forward the message any further since it is not still guaranteed that the message is delivered to a destination node yet, and thus, it is safe not to remove the message at the buffer of future contact nodes.
In the proactive overload control, if a message is delivered to a destination node of the message, the “delivery state of the message to a destination node” is recorded as “delivered” at the overload control table of the forwarding node, too, as in reactive overload control. Then, this information is shared with contact nodes to reduce unnecessary forwarding of already delivered messages to destinations, and the delivered message is removed from the buffer of the contact node.
Reducing message forwarding for delivered a message to a node that belongs to the same group as the destination node of the message in proactive overload control is different from that in [
24,
25], since message forwarding is restricted proactively; although, a message is not delivered to a destination node but is only delivered to a node that belongs to the same group as the destination node of the message for more active overload control. Additionally, a message delivered to a node in the same group as a destination node is not removed from the buffer of contact nodes, different from that in [
24,
25], but direct delivery is only allowed for the message at the contact node.
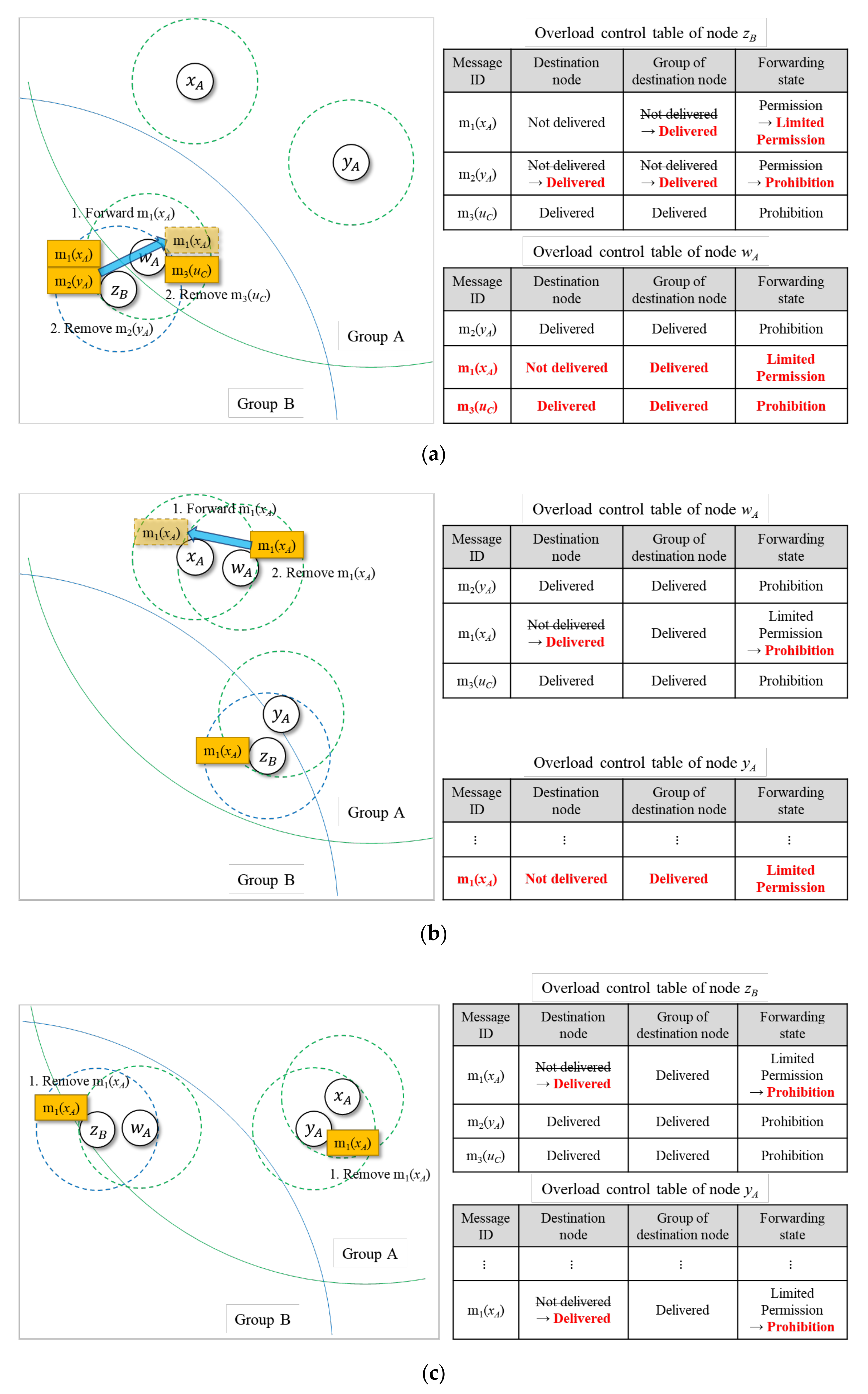
Table 2 shows examples of the overload control table in the proposed proactive overload control protocol. The message
, where
is the message ID and
is the destination node of the message
, has not been delivered to a destination node or a node in the same group of a destination node yet. Therefore, the state of forwarding permission is stored as “permission”. The message
has not delivered to a destination node yet, but it was delivered to a node in the same group of a destination node already. Thus, the status of forwarding permission is stored as “limited permission”, since forwarding is only permitted to a destination node only. The message
has been delivered to a destination node already, and the status of forwarding permission is stored as “prohibition”, and it is not permitted to forward to any node anymore.
At contact with another node, a node in the proposed proactive protocol makes a forwarding decision based on the forwarding condition using the group delivery predictability defined in
Table 1, and overload control is applied if a message is delivered to either a node in a group of a destination node or a destination node.
Figure 3 shows examples of the overload control table, where information before contact is printed in black color and information after contact is printed in red color for illustration purposes. Message ID (destination node), delivery state to a destination node, delivery state to a node in the same group as a destination node, and state of forwarding permission in
Table 2 are denoted as message ID, destination node, group of destination node, and forwarding state, respectively, for brevity.
In
Figure 3a, nodes
,
, and
belong to group
, and node
belongs to group
. Node
is in contact with
now. Before contact, node
has
and
in its buffer and has delivery state and forwarding state information of
in its overload control table. Node
has
in its buffer and has delivery state and forwarding state information of
in its overload control table before contact. At contact, it is assumed that
in the buffer of
is forwarded to
according to the forwarding condition defined in
Table 1. As shown in overload control table of node
,
was already delivered to destination node
. Additionally,
was already delivered to destination node
, as shown in overload control table of node
. Using this information,
is removed from the buffer of
, and the delivery state and forwarding state of
are updated appropriately in the overload control table of node
after contact. In addition, the delivery state and forwarding state of
are updated in overload control table of
after contact. After contact,
is removed from the buffer of node
. Then, the delivery state and forwarding state of
and
are updated appropriately in the overload control table of node
.
In
Figure 3b,
is in contact with
and
is in contact with
now. Since
is the destination node of
,
is delivered to
from
at contact, and
is removed from the buffer of
after contact. The delivery state and forwarding state of
are updated in overload control table of node
. After contact of
and
,
receives delivery state and forwarding state information for
and delivery state and forwarding state information of
are created newly in the overload control table of node
.
In
Figure 3c,
is in contact with
and
is in contact with
now. Before contact with
,
has information of successful delivery state to destination
, as shown in
Figure 3b. Thus, this information is shared with
, and
is removed from the buffer of
and information on delivery state and forwarding state are updated in overload control table of
. Since
successfully received
before contact with
already,
is removed from the buffer of
after contact with
. Then, information on delivery state and forwarding state are updated appropriately in the overload control table of
.
Figure 4 shows a flowchart of the proposed algorithm. When node x and node y contact, they update individual and group delivery predictabilities by exchanging summary vectors, which includes information of messages in their buffer and delivery predictability. Then, they update the overload control table. Node x checks if there is any message for forwarding to node y. If there is any, node x checks the overload control table to check if it is permitted to forward. Then, if it is, the message is forwarded based on the forwarding condition, as proposed in
Table 1. If node x receives a message from node y, it firstly checks if it is the destination node z of the message. If it is, the corresponding entry in the overload control table is updated. Otherwise, node x checks if it is located within the same group as the destination node z of the message. If it is, the corresponding entry in the overload control table is updated.
4. Simulation Results
The performance of the proposed protocol was analyzed through simulation using an opportunistic network environment (ONE) simulator [
26,
27], which is one of the most widely used simulators for the DTN protocol—from the aspects of delivery ratio, overhead ratio, and delivery latency, as defined in Equations (8)–(10) as follows:
Table 3 shows parameter values used in the simulation. In this paper, we consider a traffic scenario, where all messages generated at mobile nodes are delivered to a single mobile node, such as a mobile sink node in delay-tolerant wireless sensor networks [
28], since in a battlefield environment, which is one of the main application areas of the proposed group mobility, it is likely that messages generated at mobile units of each group would be delivered to a single command center node.
For performance comparison, we considered three comparable protocols in simulation.
Table 4 compares the proposed protocol and three comparable protocols. In the individual DP protocol, forwarding conditions of the original PRoPHET protocol with individual delivery predictability were modified appropriately by using the forwarding conditions in
Table 1 for fair comparison. Group DP protocol was the protocol proposed in our preliminary work [
22]. Group DP + Reactive OC protocol is a combination of Group DP protocol [
22] and the reactive overload control protocol, where overload control is enabled only when the message is delivered to a final destination node, as in [
24]. Group DP + Proactive OC protocol is a combination of Group DP protocol and the proposed proactive overload control protocol, and we refer to this as the proposed protocol in numerical examples.
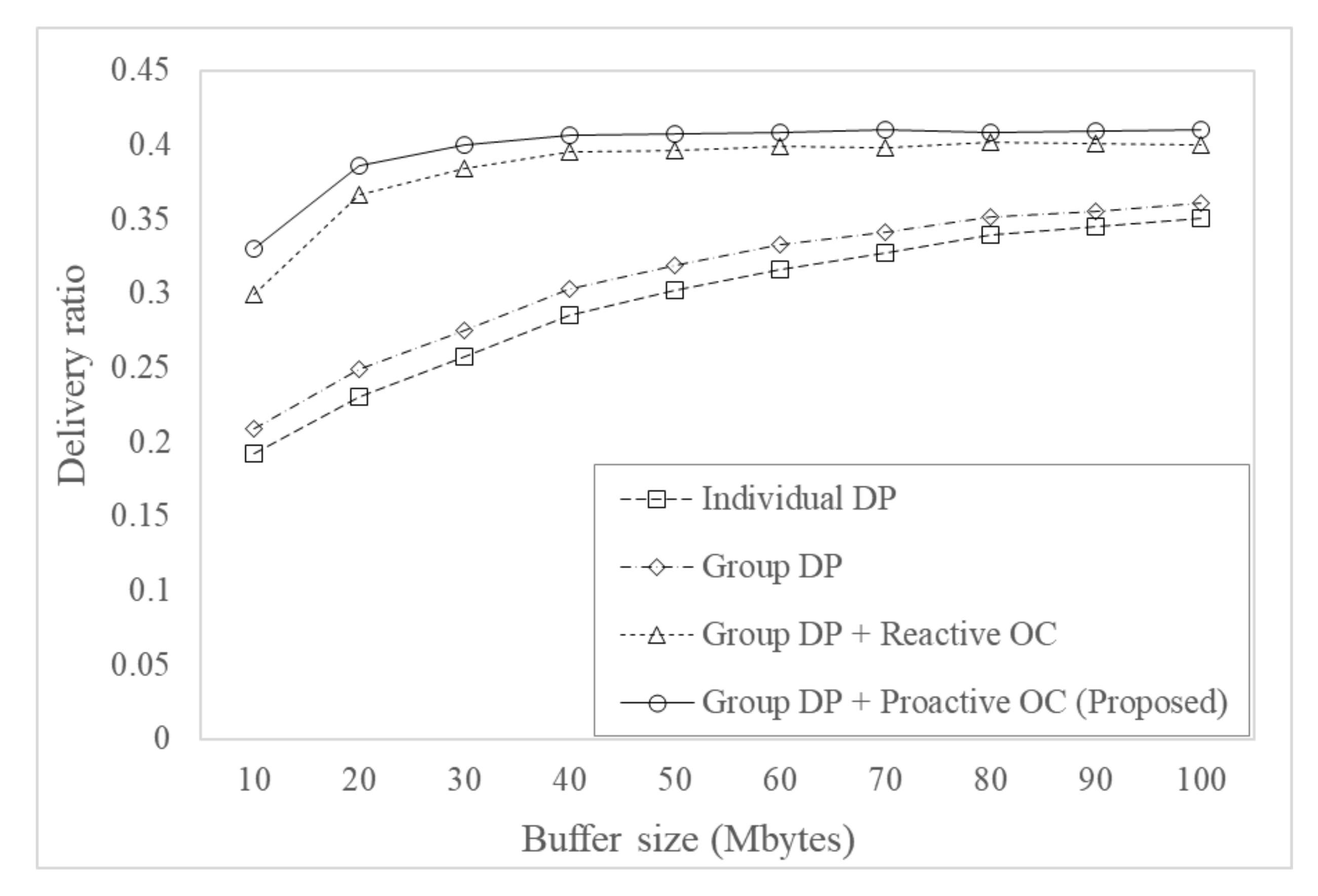
Figure 5 shows the delivery ratio for varying buffer size. Delivery ratios of all the considered protocols increased as buffer size increased but it saturated as the buffer size increased to accommodate messages sufficiently. Routing protocols with overload control had a significantly higher delivery ratio, since they efficiently reduced unnecessary message forwarding. The proposed protocol using group delivery predictability and proactive overload control had a higher delivery ratio by proactively reducing messages that were delivered to a node within the same group as the destination nodes of the messages.
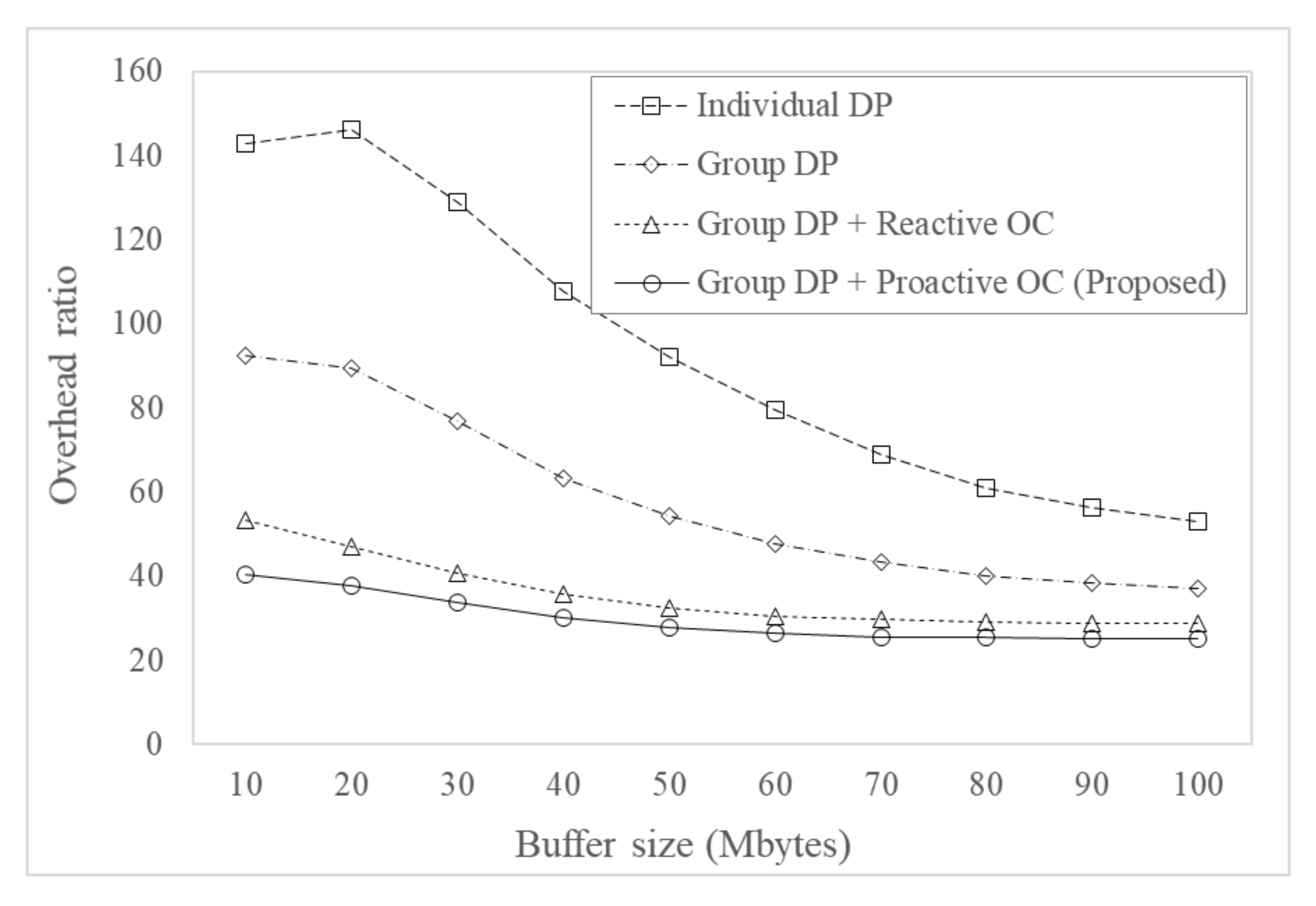
Figure 6 shows the overhead ratio for varying buffer size. Overhead ratios of all the considered protocols decreased as buffer size increased. This is because delivery ratio increases as buffer size increases due to the increase of the number of successfully delivered messages, as shown in Equation (9). As can be expected, routing protocols with overload control had significantly lower overhead ratio, since they efficiently reduced unnecessary message forwarding by overload control. The proposed protocol using group delivery predictability and proactive overload control had a lower overhead ratio by proactively reducing messages that were delivered to a node within the same group as the destination nodes of the messages.
Figure 7 shows the delivery latency for varying buffer size. Delivery latencies of all the considered protocols increased as buffer size increased, since a large buffer accommodates more messages, and thus more time is needed to deliver a message to a destination node through transmission with limited bandwidth and limited contact time. Since protocols with overload control had smaller copies of messages for a given buffer size, more time was needed for them to be delivered to the destination node using a smaller number of forwarded messages. The proposed protocol had the largest delivery latency due to proactive overload control.
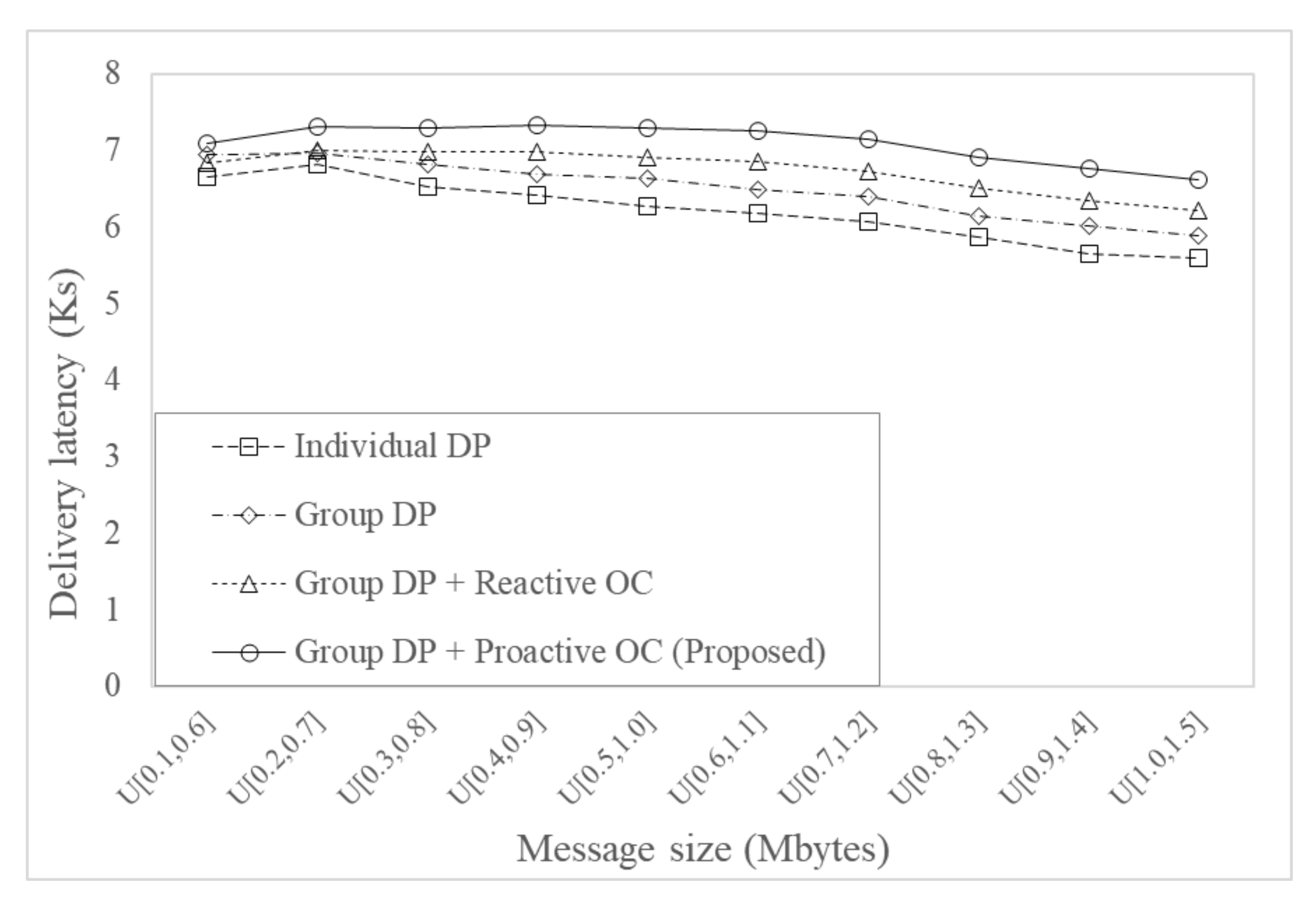
Figure 8 shows the delivery ratio for varying the message size with a buffer size of 50 Mbytes. The delivery ratios of all the considered protocols decreased as message size increased. This is because higher messages size generates more message drop due to buffer overflow, and thus results in a lower delivery ratio. The protocols with overload control had a significantly higher delivery ratio than those without overload control by efficiently reducing unnecessary message forwarding. The proposed protocol using group delivery predictability and proactive overload control had a higher delivery ratio by proactively controlling overload.
Figure 9 shows the overhead ratio for varying message size with a buffer size of 50 Mbytes. Overhead ratios of all the considered messages increased as message size increased due to the decreased number of successfully delivered messages. Routing protocols with overload control had a significantly lower overhead ratio. The proposed protocol using group delivery predictability and proactive overload control had a lower overhead ratio because of proactive overload control.
Figure 10 shows the delivery latency for varying message size with a buffer size of 50 Mbytes. The delivery latencies of all the considered protocols decreased as message size increased. This is because when the message size increases, the average number of messages stored in buffer decreases, and thus each message has a higher chance for forwarding and results in a lower delivery latency. For a given message size, delivery latency of overload control protocols was higher since they had smaller copies of messages and there was a smaller chance of message delivery. The proposed protocol had the largest delivery latency due to proactive overload control.
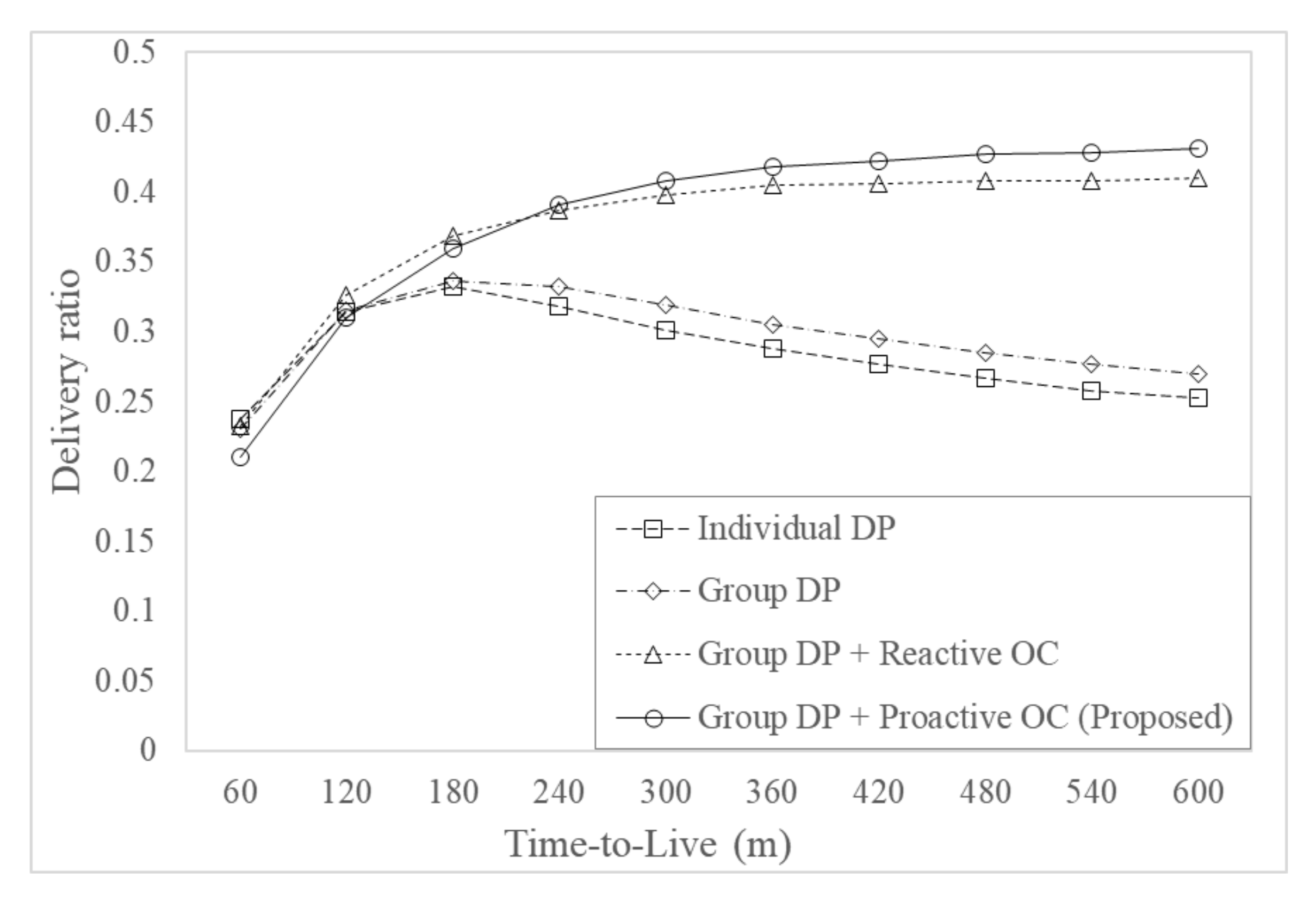
Figure 11 shows the delivery ratio for varying time-to-live (TTL) with a buffer size of 50 Mbytes. The delivery ratio of protocols without overload control increased as TTL value increased from 60 m to 180 m, but it decreased as TTL value increased from 180 m to 600 m. Since the number of message copies increased as TTL increased, thus the delivery ratio also increased because of more message dissemination by increasing the TTL value for small values of TTL. However, if TTL increases for large values of TTL, it is highly likely that more messages are dropped due to buffer overflow at fixed buffer size, since fewer messages are removed because of TTL expiration, and thus delivery ratio decreases. The delivery ratio of protocols with overload control increased as TTL values increased, since the number of message copies could be controlled efficiently using overload control. The proposed protocol had the largest delivery ratio in most of the considered TTL values, except for small TTL values, where the protocol with reactive overload control had a higher delivery ratio than the proposed protocol because of the effect of more message dissemination in small TTL values.
Figure 12 shows the overhead ratio for varying TTL with a buffer size of 50 Mbytes. The overhead of all the protocols increased as TTL values increased due to more message forwarding. The overhead of the protocols with overload control was significantly smaller than those without overload control. Especially, the overhead ratio of the proposed protocol was the smallest due to proactive overload control.
Figure 13 shows delivery latency for varying TTL with a buffer size of 50 Mbytes. The delivery latencies of all considered protocols increased as TTL values increased, since more time was needed to deliver a message to the destination node for large values of TTL using limited transmission speed because of more message copies in the buffer. The proposed protocol had the largest delivery latency, since the proposed protocol proactively removed message copies if they were delivered to any node in the same group of the destination node, and thus more time was needed to deliver a message to a destination node.