Abstract
In this paper, we designed a beacon-based hybrid routing protocol to adapt to the new forms of intelligent warfare, accelerate the application of unmanned vehicles in the military field, and solve the problems such as high maintenance cost, path failure, and repeated routing pathfinding in large-scale unmanned vehicle network communications for new battlefields. This protocol used the periodic broadcast pulses initiated by the beacon nodes to provide synchronization and routing to the network and established a spanning tree through which the nodes communicated with each other. An NS3 platform was used to build a dynamic simulation environment of service data to evaluate the network performance. The results showed that when it was used in a range of 5 ~ 35 communication links, the beacon-based routing protocol’s PDR was approximately 10% higher than that of AODV routing protocol. At 5 ~ 50 communication links, the result was approximately 20% higher than the DSDV routing protocol. The routing load was not related to the number of nodes and communication link data and the protocol had better performance than traditional AODV and DSDV routing protocol, which reduced the cost of the routing protocol and effectively improved the stability and reliability of the network. The protocol we designed is more suitable for the scenarios of large-scale unmanned vehicle network communication in the future AI battlefield.
1. Introduction
A modern battlefield considers large-scale unmanned vehicle network (LUVN) operations, with a single unmanned vehicle (UV) as the basic task unit. That is, the individual low intelligence is coupled into swarm intelligence, which could execute wide area target searches, target continuous mission coverage, and perform other complex tasks that could not be achieved with traditional vehicles [1]. An unmanned vehicle network (UVN) is a cluster network composed of multiple UV communication systems in which the vehicle is capable of information sharing and dynamic allocation. In large-scale specific application scenarios, the network could stably and reliably execute information interaction [2,3]. Instructions for UVs and information exchange among them mainly rely on wireless networks. Considering LUVN communication in future military applications, it is particularly important to design a network routing protocol that can satisfy the requirements of a large-scale network of 100 or more nodes while maintaining good network performance with the topology of the network changing rapidly. Figure 1 illustrates the scheme diagram of LUVN.
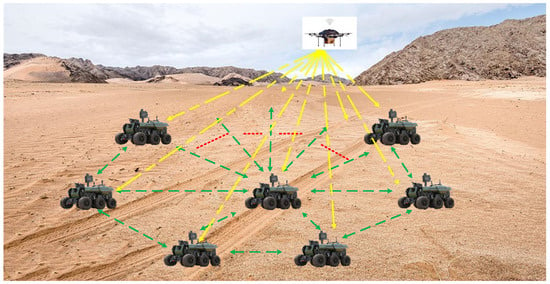
Figure 1.
Schematic diagram of large-scale unmanned vehicle networking.
Currently, according to the network routing discovery policy, there are active routes, on-demand routes, and hybrid routes [4]. In the active routing protocol, all nodes maintain network topology information. Whether or not the network topology changes, its updated information will be transmitted throughout the entire network. In addition, the active routing protocol would generate a large amount of control overhead in the network, which consumes more bandwidth resources in the data transmission process. The nodes of an on-demand routing protocol trigger the path search process only when there is demand for service data. Route maintenance is executed on demand in the process of data transmission, that is, once the demand of service data stops, route maintenance will also be terminated, and the control cost can be reduced to some extent [5]. With the application of traditional protocols such as destination sequence distance vector (DSDV) and ad hoc on-demand distance vector (AODV) routing protocols in more scenarios, more obvious problems are exposed, mainly in the network overhead of active routing protocols and the long end-to-end transmission delay of data packets of on-demand routing protocols [6]. These problems are not suitable for LUVN scenarios.
In network routing protocols, literature [7] comprehensively analyzed and simulated typical AODV, DSDV, and OLSR protocols, but has not proposed a routing protocol with higher efficiency according to the differences obtained by simulation. Literature [8] introduced a clustering algorithm into the DSDV protocol and modified the criterion of link quality in the protocol so as to improve the network throughput. However, this method still used the method of flooding in the process of maintenance and path discovery, and the problems of transmission delay were not solved. Another study [9] adopted the frequency-based policy to maintain routing to improve the AODV protocol, which effectively reduced the transmission delay of the protocol. Literature [10] used ant colony algorithm to discover paths, which solved the single path problem in AODV protocol and improved the network stability. Literature [11] modified the AODV routing protocols to reduce the number of route request (RREQ) and route reply (RREP) messages by adding direction parameters and two-step filtering. The two-step filtering process reduced the number of RREQ and RREP packets, reduced the packet overhead, and helped select the stable route. Literature [12] improved the MPR algorithm of the OLSR protocol and selected the MPR path to the left or right of the source node according to the destination node location, so as to reduce the network overhead and improve the network throughput. Literature [13] proposed a service-based multipath routing protocol; this protocol was based on the quality of service (QoS) requirements of various services, considering hop count, average connection, and minimum bandwidth as comprehensive reference conditions, and the optimal path based on the QoS requirements of this service was selected.
The routing protocols in the above studies mainly reduced the routing cost to a certain extent. However, the broadcast mode was used to discover routes and maintain routing tables. As the number of network nodes increased, the network maintenance load increased exponentially. Therefore, it was difficult to support large-scale networks. In the multi-unmanned vehicle network, with each unmanned vehicle as a node, the task required strong mobility performance, resulting in the network topology changing dramatically. The node moving speed was fast, therefore data transmission had strong interference, and the communication link stability and reliability were low. As shown in Figure 2, the original 0-1-2-3 path was interrupted due to node movement and a new 0-4-3 path was generated. However, the routing protocol in the above literature could not actively perceive the change of routing path. When the path failed, the failed path was still used for communication or repeated routing path finding, which eventually led to data loss and seriously affected the communication quality.
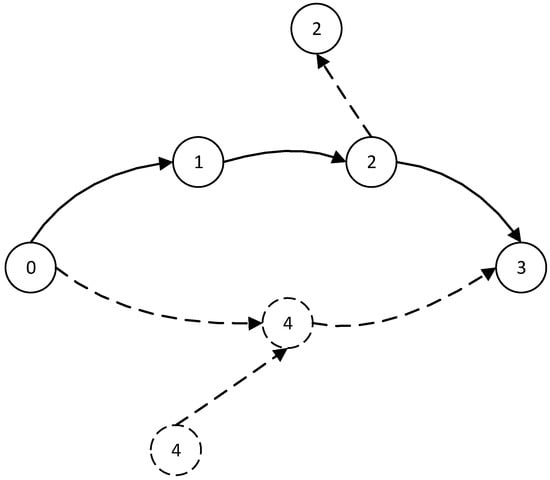
Figure 2.
Schematic diagram of node path changes.
Based on the above analysis, a more efficient beacon-based hybrid routing protocol was proposed for the LUVN scenarios. In this protocol, a periodic beacon pulse was used to actively discover and maintain the path tree of the node, and the path was built from the source node to the destination on demand. At the same time, active paths were maintained under the guidance of periodic beacon pulses, so as to reduce the cost of routing protocols and improve the stability and reliability of routing network paths. An NS3 platform was used to build a dynamic service data simulation environment to verify the network performance. The simulation results showed that this protocol can solve the problems of path failure, repeated path finding, and excessive cost in route maintenance when using traditional AODV and DSDV routing protocols, which effectively improved the stability and reliability of the network. The protocol was more suitable for future AI battlefield LUVN scenarios.
The major contributions of this paper follow:
- In this protocol, a periodic beacon pulse was used to actively discover and maintain the path tree of the node, and the path was built from the source node to the destination on demand, which reduced the cost of routing protocols.
- Active paths were maintained under the guidance of periodic beacon pulses, so as to improve the stability and reliability of routing network paths.
- In the beacon-based hybrid routing protocol for LUVAN, a pulse cycle was the basic unit. A pulse cycle was divided into four phases, each of which was executed in a fixed time and the cost controlled by the routing protocol was only related to the time allocated in the first three phases.
This paper is organized as follows:
- In Section 1, the implementation method of beacon-based hybrid routing protocol is introduced.
- In Section 2, the effectiveness of beacon-based hybrid routing protocol is analyzed.
- In Section 3, an NS3 network simulation platform is used to compare and analyze the performance of beacon-based hybrid routing protocol, DSDV protocol and AODV protocol.
- Finally, the conclusion of this paper is in Section 4.
2. Beacon-Based Multi-Agent Network Hybrid Routing Algorithm
In a beacon-based hybrid routing protocol for a large-scale unmanned vehicle ad hoc network (LUVAN), the beacon node was the control center of the whole network; other nodes in the network took the pulse message sent by the beacon node as the time origin of the routing operation and established the optimal path tree to the beacon node. According to the optimal path tree, path discovery and maintenance and data transmission services were then completed.
2.1. Pulse Message
In the beacon-based hybrid routing protocol for LUVAN, a pulse cycle was the basic unit. As shown in Figure 3, a pulse cycle was divided into four phases, each of which was executed in a fixed time and the cost controlled by the routing protocol was only related to the time allocated in the first three phases.
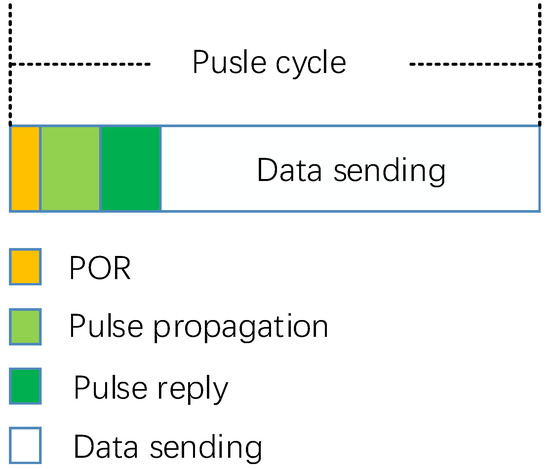
Figure 3.
Schematic diagram of pulse unit.
Power on Reset (POR): In order to avoid the time error of different nodes, nodes can start receiving in advance and wait for receiving pulse messages.
Pulse Propagation: Pulse node periodically broadcasted pulse messages, other nodes received pulse messages and established the optimal path tree (OPT) to the pulse node.
Pulse Reply: For the routing request node, after receiving the pulse message, it would reply to the message in the form of unicast pulse along the OPT to the pulse node and request the path to the pulse node.
Data Sending: After the optimal path from pulse node to the destination node was established, the pulse node sent data along the OPT and sent the data to the destination node through forwarding to the nodes along the OPT.
In the beacon-based routing protocol, the non-beacon node would actively maintain the OPT pointing to the beacon node and establish the path to the destination node through the OPT.
When the non-beacon nodes received the pulse messages sent by the beacon node, they would create an OPT from non-beacon nodes to the beacon node. Because the beacon node sent pulse messages periodically, the non-beacon nodes could maintain an OPT to the beacon node in real time to ensure the real-time effectiveness of the OPT.
The beacon node sent pulse messages in a fixed period. Pulse messages included time information for time synchronization of non-beacon nodes.
The non-beacon node determined the time of the next POR state according to the pulse interval received last time and entered the receiving state at the specified time while remaining in the inactive state at other times. This node could enter the hibernation state to save power.
After receiving the pulse message, the non-beacon node would judge it according to the serial number and link metric of the pulse message. When the pulse number was the latest or the pulse number was the same as the stored pulse number but the link measure was small, the path was saved and the pulse message was forwarded at the same time. At this time, the node would establish an optimal path data to reach the beacon node.
After the beacon node sent a pulse message, all nodes in the network would create a path tree to the beacon source node, as shown in Figure 4.
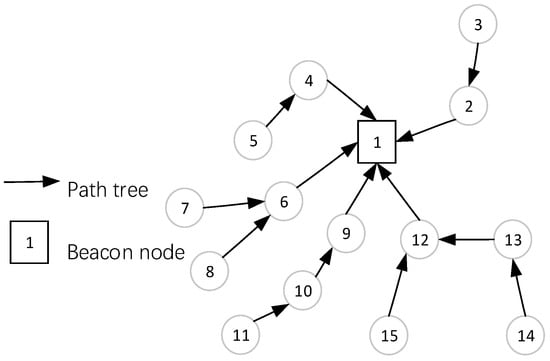
Figure 4.
Schematic diagram of spanning tree.
2.2. Path Discovery and Maintenance
2.2.1. Path Discovery
When the data node had a data sending request, if there was no routing path to the destination node, the path establishment process as shown in Algorithms 1 and 2.
| Algorithm 1. Source node path request process. | |
| 1 | Tp: Pulse Propagation time |
| 2 | Tr:Pluse Reply time |
| 3 | Td:Data Sending time |
| 4 | If T > Tp and T < Tr |
| 5 | Source node send a pulse reply message along the OPT. |
| 6 | OPT node unicast reply message. |
| 7 | Elif T > Tr and T < Td |
| 8 | Source node send data along the path tree. |
| 9 | Else |
| 10 | Wait until the time reaches Tr. |
| 11 | End if |
| Algorithm 2. Beacon node path request process. | |
| 1 | Pt: Path information table |
| 2 | Pd: Path to the destination address |
| 3 | Tp: Pulse Propagation time |
| 4 | Becaon node received the pulse reply message: |
| 5 | If Pd is in Pt: |
| 6 | Becaon node created a reverse path to the source node. |
| 7 | Else: |
| 8 | Becaon node created a reverse path to the source node. |
| 9 | If T < Tp: |
| 10 | Becaon node send a pulse message with the destination address. |
| 11 | |
| 12 | Else: |
| 13 | Wait until next pulse cycle. |
| 14 | End if |
| 15 | End if |
(1) Path creation process of data node:
① The node judged whether it was in the pulse reply state. If it was, it would send the pulse reply along the OPT, reaching the beacon node.
② If it was not in the pulse reply state, the node then judged whether it was in the data transmission state. If it was, data would be sent directly along the OPT reaching the beacon node. If not, it would wait until the data sending state.
(2) Node of OPT:
① The node in the OPT would create a reverse path to the source node after receiving the pulse reply message with the destination address, as shown in red arrows 6-7 in Figure 5a.
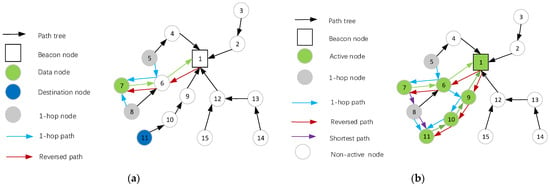
Figure 5.
(a) Schematic diagram of source node path establishment process. (b) Schematic diagram of destination nodepath establishment process.
② The node in the OPT forwarded the pulse reply message with the destination address until it reached the beacon node.
(3) 1-hop node around the OPT:
When 1-hop node around the OPT received a pulse reply message with the destination address, a reverse path to the source node was established, as shown in the blue arrows 5-6-7 and 8-7 in Figure 5a.
The 1-hop node around the OPT did not forward the pulse reply message to avoid unnecessary routing cost.
(4) Beacon node:
① After the beacon node received a pulse reply request from the source node, a reverse path to the source node would be created, as shown by the red arrow 1-6-7 in Figure 5a.
② The beacon node judged if there was a path to the destination node. If not, it would send a pulse message with the destination address in the next pulse cycle for path addressing.
Subsequently, the beacon node, the source nodes in the OPT from the source node to the beacon source node, and the 1-hop nodes around the OPT would all create a reverse path to the source node.
When the destination node received the pulse message with the destination address, the node would send the pulse reply message to the beacon node along the OPT pointing to the beacon source node. The process for each type of node is illustrated Algorithm 1 and Algorithm 2. After the message reached the beacon node, the path 1-9-10-11 from the beacon node to the destination node as shown in Figure 5b was established. Node 8 around the path tree established reverse paths from 8 to 11 to the destination node.
2.2.2. Optimal Path Creation
As shown in Figure 5b, the source node would send data to the destination node along the newly established path tree. The initial possible path was 7-6-9-10-11, which was obviously not the optimal path.
During the path creation process, 1-hop nodes (nodes 5 and 8) of the path tree would monitor the pulse reply message sent by the source node and the destination node. If the node found a fast path existed, it would send a message to the corresponding node and declared that a fast path existed. The optimal path 7-8-11 shown in the purple arrow in Figure 5b would then be created.
The source node and destination node would actively respond to the pulse message broadcast by the beacon node to ensure the real-time validity of the communication link. The non-source node and destination node would not respond to the pulse message to reduce the route cost.
2.3. Beacon-Based Hybrid Routing Protocol
In active DSDV, the cost of maintaining N paths per node is O (N). The maintenance cost of each link is O (N/T), where N is the number of nodes and T is the lifetime of a link. Therefore, the total cost of maintaining links for N nodes in the network is O (N2/T).
In on-demand routing protocols, such as AODV and dynamic source routing (DSR), the routing cost is reduced by maintaining active links on demand; the cost of maintaining active links for N nodes is O (NF), where F is the number of active links on each node. However, the on-demand routing protocol still uses the method of flooding in the process of path transmission, and the broadcast cost of node flooding is O (N). Therefore, the total number of maintenance links of N nodes in the network is O (FN2/T).
The beacon-based hybrid routing protocol uses single path tree to discover and maintain links; only the beacon node in the network periodically send a flooding. Therefore, the maintenance cost of the link is O(N/T), and T is the pulse period of the beacon-based protocol.
In active and on-demand routing protocols, when the number of nodes increases in a large scale, the cost of routing protocols increases exponentially, which is not suitable for large-scale networking scenarios. The beacon-based routing protocol uses the single path tree method to effectively solve the problem of flooding in the network. The routing cost and the number of nodes increase linearly, which reduces the cost of network maintenance.
3. Results
3.1. Simulation Environment
The NS3 simulation platform was used to build a dynamic simulation environment of service data to evaluate the routing protocol we designed. The MAC layer in the NS3 simulation environment uses the IEEE802.11 standard. Table 1 shows the basic simulation parameters. Table 2 shows the beacon-based hybrid routing protocol parameters.

Table 1.
Simulation parameters.

Table 2.
Protocol parameters.
In this simulation, in order to verify the performance of multi-node concurrent network communication, the node access time is limited. The node access time is required to be randomly selected between simulation start time (communication start time/s) and active link data. That is, the network access time in this experiment was between 80 s + 5 s ~ 50 s, so that it can guarantee concurrent communication with multiple links at the same time in the active link time.
According to the above simulation parameters, 50 nodes were randomly distributed in the simulation environment with a range of 1000 m × 1000 m, moving randomly at the speed of 5 m/s, and 5 to 50 groups of active communication links were randomly generated in the network. AODV and DSDV were selected as comparisons to the proposed beacon-based routing protocol. The performance of the routing protocol was estimated by comparing the simulation results.
3.2. Results and Analysis
This paper mainly compared and analyzed the packet delivery rate and routing load. In order to ensure the randomness of node positions during the test, the nodes were in the stage of random movement before the 80 s of simulation, then communication links were established randomly from the 80 s to 170 s, in which the number of active links varied from 5 to 50. The results are discussed as follows.
(1) Packet Delivery Rate (PDR)
PDR is the ratio of packets received by the target node to packets sent by the source node. It is a statistical measure of correctly transmitted packets. This index mainly examines the reliability and communication quality of the network. The higher the successful packet delivery rate, the higher the network reliability and the better the communication quality.
The PDR of the beacon-based routing protocol and the AODV and DSDV protocols varied with the number of active links in the network, as shown in Figure 6. When the beacon-based routing protocol was used in a range 5–35 communication links, the PDR was approximately 10% higher than that of AODV routing protocol. At 5–50 communication links, the PDR was approximately 20% higher than the DSDV routing protocol. The overall PDR of the beacon-based routing protocol was better than that of the two traditional routing protocols. The beacon-based routing protocol adopted the active maintenance path tree and active link mode, which was more suitable for sensing path changes in advance and avoiding path failures and repeated path finding. Therefore, it had high reliability after networking.
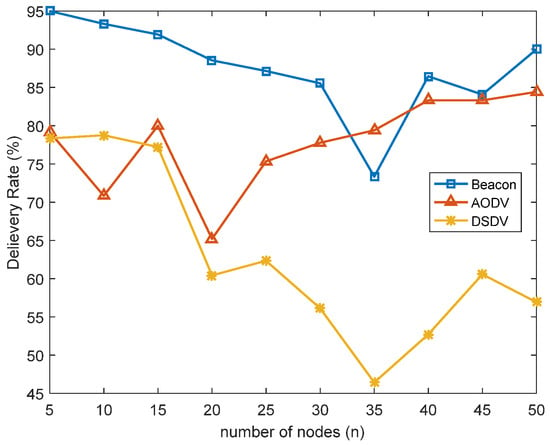
Figure 6.
Delivery ratios of beacon routing protocol and AODV, DSDV protocols.
In Figure 6, the packet transmission rate of beacon-based routing protocol suddenly drops at node 35, mainly because the simulation startup time of six active communication links is basically the same, and the source node and destination node addresses of these six links are the same. The path query and maintenance of beacon-based routing protocol is limited to the first three stages of 140 ms.
As a result, when there are multiple data requests from the same node at the same time, the path query and maintenance cannot be completed within 140 ms. To solve this problem, we conducted the following experiment. In the experiment, the time of node access to the network was not limited and the time of node access to the network was randomly distributed within 80 s ~ 180 s (Beacon 2) and 80 s ~ 300 s (Beacon 3). The comparison between the delivery rate and the network entry time distribution of the original experiment in the 80 s + 5 s ~ 50 s (Beacon 1) is shown in Figure 7.
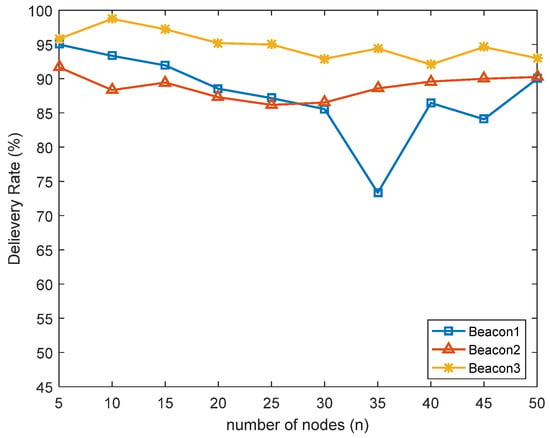
Figure 7.
Delivery ratios of beacon routing protocol at different inbound times.
As shown in the figure above, the more dispersed the network time distribution of nodes is, the better the protocol delivery rate is. At the same time, there is no concurrent communication between multiple nodes at node 35, so there is no problem as shown in Figure 6.
(2) Routing Load (RL)
RL indicates the number of frames or packets borne by a communication device within a unit time. Ideally, the forwarding capability/rate should increase linearly with the increase in load. In practice, as the load increases, the processing capability decreases. Packet congestion leads to packet loss. As a result, the forwarding rate drastically decreases. Therefore, the RL is closely related to the system stability after networking.
Figure 8 showed the changes of RL of the beacon-based routing protocol and the AODV and DSDV protocols with the number of active links in the network. The result show that the cost of the RL of the beacon-based routing protocol had always been in a stable state and was unrelated to the data of the active communication link in the link, which was consistent with the original intention of the design.
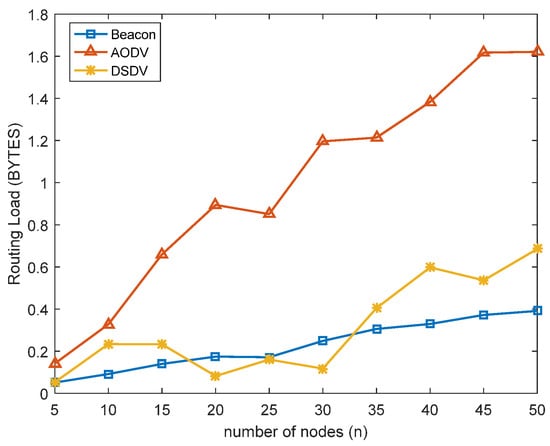
Figure 8.
Routing load of beacon-based routing and the AODV and DSDV protocols.
The RL of the beacon-based routing protocol was only related to the time allocated to the first three phases of the pulse unit and unrelated to the number of nodes and communication link data. Therefore, using the beacon-based routing protocol for network unmanned equipment was more stable and suitable for the LUVN scenario.
(3) Effect of Pulse Cycle on the Network
In the beacon-based routing protocol, periodic flooding was used to create and maintain the OPT for nodes in the network to reach the beacon node. At the same time, nodes in the network completed path establishment and data transmission according to the guidance of the path tree. The sending period of the pulse message of the beacon node determined the network entry time and path update maintenance time of nodes in the network. The sending period of the pulse message should be selected according to the number of nodes in the network, the network access time, communication bandwidth, and other parameters required by the network. Figure 9 and Figure 10 were the simulation comparison of PDR and RL when the pulse cycle was 1.5 s, 2 s, 2.5 s, and 3 s, respectively, under the configuration parameters in Table 1.
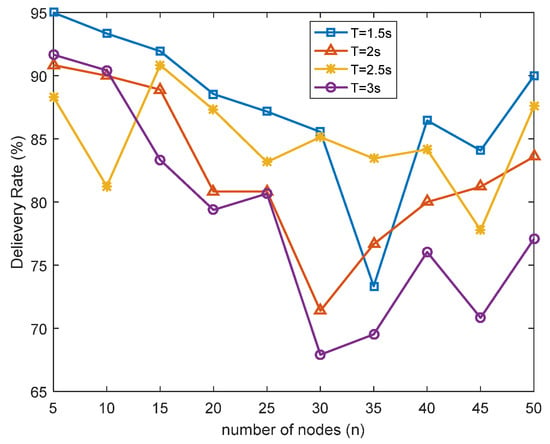
Figure 9.
Comparison of pulse cycle delivery rate of beacon routing protocol.
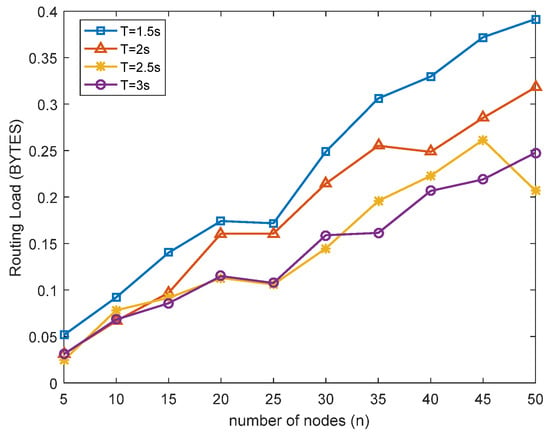
Figure 10.
Comparison of pulse cycle routing load of beacon routing protocol.
As shown in Figure 9, the four curves represented the PDR of beacon-based routing protocols with pulse cycle of 1.5 s, 2 s, 2.5 s, and 3 s. The result showed that the PDR of the beacon-based routing protocol was the most stable when the pulse cycle was 1.5 s, and the performance would gradually decrease with increasing time.
The simulation result showed that the active link continuously sent data in the active time; due to constant motion of the node in the path, path failure would occur. Therefore, the shorter the time interval of the pulse cycle, the better the perception of the change of link path failure can be. Therefore, the delivery rate is the best when the pulse cycle is 1.5 s, and the delivery rate decreases gradually with the increase in time. The beacon-based routing protocol made full use of the periodic pulse message, completing the path reconstruction and path addressing operation within a pulse cycle, which effectively avoided the problems of path failure and repeated path finding.
As shown in Figure 10, the four curves represented the RL of beacon-based routing protocols with pulse periods of 1.5 s, 2 S, 2.5 s, and 3 s. The simulation result showed that with the increase in pulse cycle, the RL decreased gradually, which was also consistent with the design idea of this paper. Theoretically, the RL of the beacon-based routing protocol is only related to the time allocated to the first three phases of the pulse unit and unrelated to the number of nodes and communication link data. The simulation verified this: the larger the pulse cycle, the smaller the proportion of time occupied by the route load; the smaller the route load, the larger the effective data bandwidth.
4. Conclusions
Aiming at the problems of path failure, repeated routing path finding, and excessive cost of route maintenance in the networking of large-scale unmanned equipment using traditional routing protocol, combining the characteristics of active and on-demand routing protocols, we proposed a beacon-based hybrid routing protocol for LUVAN. In this beacon-based routing protocol, the path tree of each node pointing to the beacon node was used as guidance. Nodes were periodically maintained for OPT. Source nodes used unicast mode to create paths as required. Active nodes actively maintained routing paths in the network, maximized routing control commands, and limited the route load to a fixed time. Therefore, the cost of route maintenance in unmanned equipment network is reduced and the problems of path failure and repeated path finding are solved.
The simulation results showed that the PDR and RL performance of the beacon-based routing protocol were better than the network with traditional AODV and DSDV routing protocols. When they were used in a range 5–35 communication links, the beacon-based routing protocol PDR was approximately 10% higher than that of AODV routing protocol. At 5 ~ 50 communication links, result was approximately 20% higher than the DSDV routing protocol. The beacon-based routing protocol with different pulse cycles were compared. The RL of the beacon-based routing protocol were unrelated to the number of nodes and communication link data in the LUVN, which effectively improved the stability and reliability of the network. The beacon-based routing protocol we designed is more suitable for future LUVN battlefields.
Author Contributions
Conceptualization, Y.M. and Z.L.; methodology, W.M.; software, G.L.; validation, W.M., R.W. and Z.L.; formal analysis, W.M.; investigation, Y.L.; resources, Y.M.; data curation, Z.L.; writing—original draft preparation, W.M. and Y.M.; writing—review and editing, Z.L.; visualization, R.W.; supervision, G.L.; project administration, Y.L.; funding acquisition, Y.M. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key Research and Development Program under Grant 2018YFE0204302, This research was funded by NSFC, grant number 51979261 and Intelligent Unmanned System Key Technology Cutting-Edge Tracking Research, grant number 4142Z17.
Data Availability Statement
All data can be requested from the corresponding author.
Acknowledgments
Authors acknowledge the technical support given by Youchun Xu.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Tahir, A.; Böling, J.; Haghbayan, M.H.; Toivonen, H.; PLoSila, J. Swarms of unmanned aerial vehicles—A survey. J. Ind. Inf. Integr. 2019, 16, 100106. [Google Scholar] [CrossRef]
- Adiguzel, F.; Mumcu, T.V. Robust discrete-time nonlinear attitude stabilization of a quadrotor UAV subject to time-varying disturbances. Elektron. Elektrotechnika 2021, 27, 4–12. [Google Scholar]
- Ulku, E.; Dogan, B.; Demir, O.; Bekmezci, I. Sharing location information in multi-UAV systems by common channel multi-token circulation method in FANETs. Elektron. Elektrotechnika 2019, 25, 66–71. [Google Scholar] [CrossRef] [Green Version]
- Ramanathan, R.; Redi, J. A brief overview of ad hoc networks: Challenges and directions. IEEE Commun. Mag. 2002, 40, 20–22. [Google Scholar] [CrossRef]
- Basci, A.; Can, K.; Orman, K.; Derdiyok, A. Trajectory tracking control of a four rotor unmanned aerial vehicle based on continuous sliding mode controller. Elektron. Elektrotechnika 2017, 23, 12–19. [Google Scholar] [CrossRef]
- Zafar, S.; Tariq, H.; Manzoor, K. Throughput and delay analysis of AODV, DSDV and DSR routing protocols in mobile ad hoc networks. Int. J. Comput. Netw. Appl. 2016, 3, 1–7. [Google Scholar]
- Shafiq, M.; Ashraf, H.; Ullah, A.; Masud, M.; Azeem, M.; Jhanjhi, N.; Humayun, M. Robust cluster-based routing protocol for IoT-assisted smart devices in WSN. Comput. Mater. Contin. 2021, 67, 3505–3521. [Google Scholar] [CrossRef]
- Godfrey, D.; Kim, B.; Miao, H.; Shah, B.; Hayat, B.; Khan, I.; Kim, K. Q-learning based routing protocol for congestion avoidance. Comput. Mater. Contin. 2021, 68, 3671. [Google Scholar] [CrossRef]
- Del-Valle-Soto, C.; Mex-Perera, C.; Aldaya, I.; Lezama, F.; Nolazco-Flores, J.; Monroy, R. New detection paradigms to improve wireless sensor network performance under jamming attacks. Sensors 2019, 19, 2489. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Sharma, A.; Dongsoo, S. Energy efficient multipath ant colony based routing algorithm for mobile ad hoc networks. Ad Hoc Netw. 2021, 113, 102396. [Google Scholar] [CrossRef]
- Ahamed, A.; Vakilzadian, H. Impact of direction parameter in performance of modified AODV in VANET, J.J. Sens. Actuator Netw. 2020, 9, 40. [Google Scholar] [CrossRef]
- Kumar, P.; Verma, S. Implementation of modified OLSR protocol in AANETs for UDP and TCP environment. J. King Saud Univ. -Comput. Inf. Sci. 2019. [Google Scholar] [CrossRef]
- Wahid, I.; Ullah, F.; Ahmad, M.; Khan, A.; Uddin, M.; Alharbi, A.; Alosaimi, W. Quality of service aware cluster routing in vehicular Ad Hoc Networks. Comput. Mater. Contin. 2021, 67, 3949–3965. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).