Vulnerability Analysis to Maximize the Resilience of Power Systems Considering Demand Response and Distributed Generation
Abstract
1. Introduction
1.1. Motivation
1.2. Literature Review
1.3. Contributions and Paper Organization
- It complements previous works reported in the specialized literature regarding the solution of the EGIP by considering AC modeling of the problem as well as simultaneous attacks on lines and generators.
- New metrics are proposed for the assessment of power system resiliency under deliberate attacks.
- Enhancement of grid resiliency is proposed by introducing the effect of DERs as a reaction strategy of the system operator.
2. Outline of the EGIP
2.1. Normal Operative Conditions
- The resources that the network operator allocates for the protection of lines and generators in the system are known to the disruptive agent.
- The disruptive agent is aware of the bilateral agreements for voluntary load shedding.
- The attacks performed on the system are 100% effective.
- The network operator considers DR to be a mechanism for immediate mitigation of the attack plan and reduction of network operating costs.
2.2. Scenarios for the Case Study
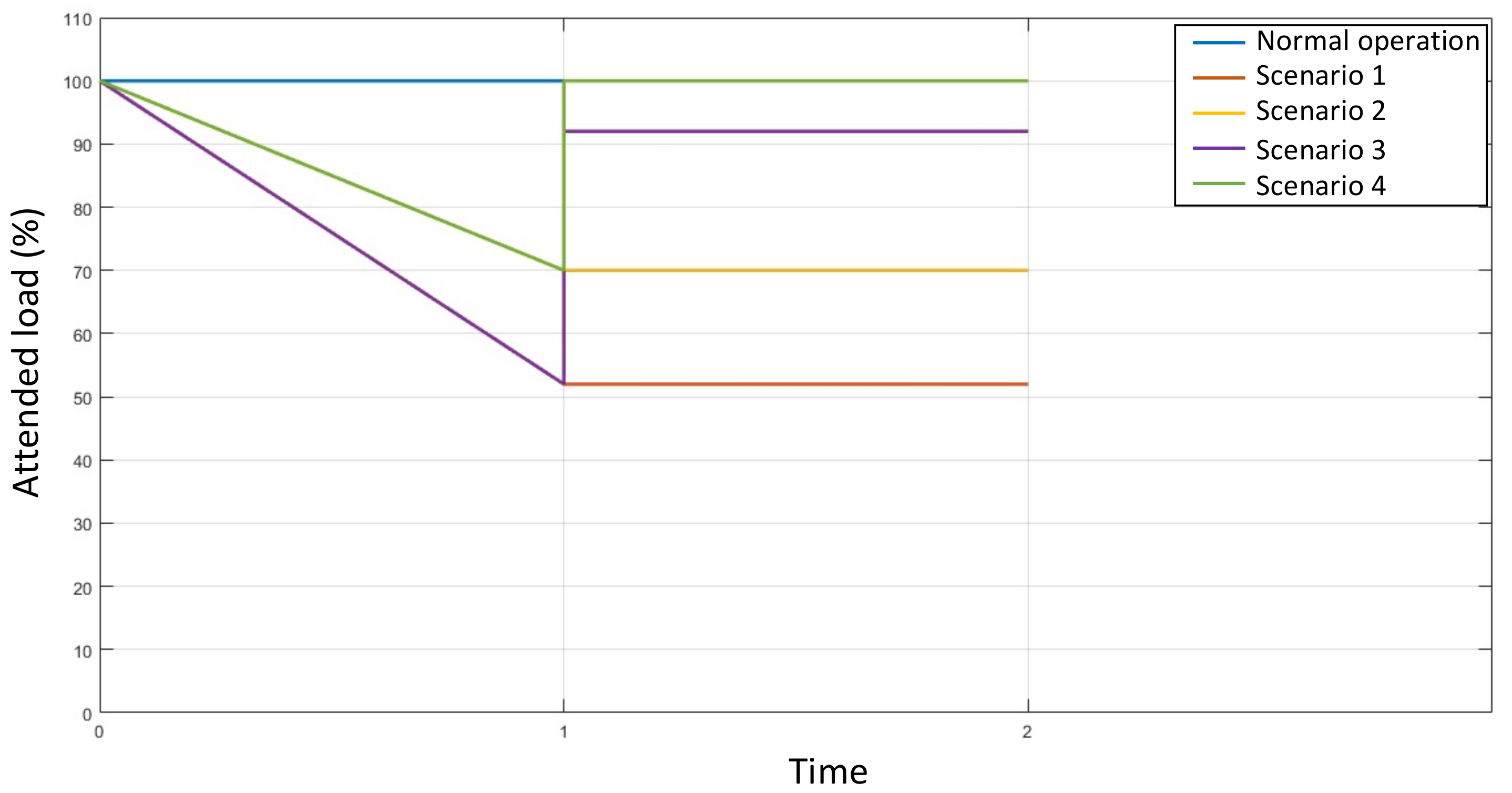
- Scenario 1: There is no agreement for voluntary load shedding. Under this condition, the most severe attack plan of the vulnerability analysis is executed without taking mitigation actions by the network operator.
- Scenario 2: There is a bilateral agreement between the network operator and some system loads to voluntarily disconnect a percentage of the total load. From this condition, the disruptive agent executes the most severe attack of the vulnerability analysis. In the post-attack stage, the network operator takes no action to decrease load shedding.
- Scenario 3: There is no agreement for voluntary load shedding. Under this condition, the most severe attack plan of the vulnerability analysis is executed. In the post-attack stage, the network operator optimizes the location and sizing of distributed generators to reduce load shedding.
- Scenario 4: There is a bilateral agreement between the network operator and some system loads to voluntarily disconnect a percentage of the total load. From the condition, the disruptive agent executes the most severe attack of the vulnerability analysis. In the post-attack stage, the network operator optimizes the location of distributed generators and reallocates demand response to reduce load shedding.
3. Mathematical Modeling and Solution Approach
3.1. Vulnerability Analysis
3.1.1. Genetic Algorithm
3.1.2. Upper-Level Optimization Problem
3.1.3. Lower-Level Optimization Problem
3.2. Allocation of Costs in Loads
3.3. Resilience of an Electrical Power System
3.4. Strategies for Maximizing Network Resilience Following a Disruptive Event
4. Tests and Results
4.1. Results with a 5-Bus Power System
4.1.1. Normal Operation and Disruptive Event
4.1.2. Disruptive Event with DR
4.1.3. DG Allocation to Increase Resiliency without DR
4.1.4. Location and Sizing of DG along with DR to Improve Resiliency
4.1.5. Quantification of Resilience in Terms of Operating Cost and Percentage of the Total Load
4.2. Results with the IEEE RTS-24 Bus Power System
5. Discussion of Results
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Acronyms and Abbreviations
| AC | Alternating Current |
| DC | Direct Current |
| DERs | Distributed Energy Resources |
| DG | Distributed Generation |
| DR | Demand Response |
| EPS | Electric Power Systems |
| GA | Genetic Algorithm |
| PSO | Particle Swarm Optimization |
Nomenclature
| Indices and sets | |
| L | Set of lines |
| G | Set of generators |
| Total resources of the attacker | |
| Set of buses | |
| Set of buses with demand response | |
| Set of generators connected to node n | |
| Set of demands connected to node n | |
| Set of lines connected to node n | |
| Parameters and constants | |
| Cost of the power delivered by generator g | |
| Cost of the dispatchable load at node n | |
| Cost of load shedding at node m | |
| Cost of attacking a line | |
| Cost of attacking a generator | |
| c2 | Uncertainty costs |
| Cost of demand | |
| Power demanded | |
| Variables | |
| Power delivered | |
| Power demand response at node n | |
| Power Load shedding at node m | |
| Reactive power delivered by generator g | |
| Interdiction vector for the set of lines | |
| Interdiction vectors for the set of generators | |
| Active power demand | |
| Reactive power demand | |
| Apparent power flow in line | |
| Wn | Power scheduled for generator n |
| x1, x2 | Power demanded |
| m1, m2 | Cost operation results and minimum and maximum power at the loads |
| μ1 | Represents the ability of the system to adequately manage the optimal power flow to meet the demand |
| μ2 | Shows that the power grid has mechanisms to minimize mandatory load shedding as the worst case scenario for the network operator and the loads |
| μ | Quantify respectively a fully resilient and a zero resilient network |
| Voltage magnitude at bus n | |
References
- Zang, T.; Gao, S.; Liu, B.; Huang, T.; Wang, T.; Wei, X. Integrated fault propagation model based vulnerability assessment of the electrical cyber-physical system under cyber attacks. Reliab. Eng. Syst. Saf. 2019, 189, 232–241. [Google Scholar] [CrossRef]
- Corredor, P.H.; Ruiz, M.E. Mitigating the Impact of Terrorist Activity on Colombia’s Power System. IEEE Power Energy Mag. 2011, 9, 59–66. [Google Scholar] [CrossRef]
- Salmeron, J.; Wood, K.; Baldick, R. Analysis of electric grid security under terrorist threat. IEEE Trans. Power Syst. 2004, 19, 905–912. [Google Scholar] [CrossRef]
- Arroyo, J.M.; Galiana, F.D. On the solution of the bilevel programming formulation of the terrorist threat problem. IEEE Trans. Power Syst. 2005, 20, 789–797. [Google Scholar] [CrossRef]
- Delgadillo, A.; Arroyo, J.M.; Alguacil, N. Analysis of electric grid interdiction with line switching. IEEE Trans. Power Syst. 2010, 25, 633–641. [Google Scholar] [CrossRef]
- Upme, C. Recursos Energéticos Distribuidos Acciones Para la Integración. 2020; pp. 1–83. Available online: https://pigccme.minenergia.gov.co/public/uploads/web_documentos/5f47f3963eac5.pdf (accessed on 27 January 2021).
- Pep, S.; Carrasco, A. Agrecación de Recursos Energéticos Distribuidos (DER) Obstáculos y Recomendaciones Para un Desarrollo Íntegro del Mercado Barcelona, Diciembre de 2017. Available online: http://acco.gencat.cat/web/.content/80_acco/documents/arxius/actuacions/20180406-Agregacio-de-recursos-eneregetics-distribuits_esp.pdf (accessed on 27 January 2021).
- Brown, R.E. Cost-Benefit Analysis of the Deployment of Utility Infrastructure Upgrades and Storm Hardening Programs. Satell. Commun. 2009, 3021, 1–108. [Google Scholar]
- Gil-González, W.; Garces, A.; Montoya, O.D.; Hernández, J.C. A mixed-integer convex model for the optimal placement and sizing of distributed generators in power distribution networks. Appl. Sci. 2021, 11, 627. [Google Scholar] [CrossRef]
- Shu, J.; Guan, R.; Wu, L.; Han, B. A Bi-Level Approach for Determining Optimal Dynamic Retail Electricity Pricing of Large Industrial Customers. IEEE Trans. Smart Grid 2019, 10, 2267–2277. [Google Scholar] [CrossRef]
- Costa, A.; Georgiadis, D.; Ng, T.S.; Sim, M. An optimization model for power grid fortification to maximize attack immunity. Int. J. Electr. Power Energy Syst. 2018, 99, 594–602. [Google Scholar] [CrossRef]
- López-Lezama, J.M.; Cortina-Gómez, J.; Muñoz-Galeano, N. Assessment of the Electric Grid Interdiction Problem using a nonlinear modeling approach. Electr. Power Syst. Res. 2017, 144, 243–254. [Google Scholar] [CrossRef]
- Cortina, J.J.; López-Lezama, J.M.; Muñoz-Galeano, N. Modelo de interdicción de sistemas de potencia considerando el efecto de la respuesta a la demanda. Inf. Tecnol. 2017, 28, 197–208. [Google Scholar] [CrossRef]
- Biswas, R.; Sen Pal, A.; Werho, T.; Vittal, V. A Graph Theoretic Approach to Power System Vulnerability Identification. IEEE Trans. Power Syst. 2021, 36, 923–935. [Google Scholar] [CrossRef]
- Yang, S.; Chen, W.; Zhang, X.; Liang, C.; Wang, H.; Cui, W. A Graph-Based Model for Transmission Network Vulnerability Analysis. IEEE Syst. J. 2020, 14, 1447–1456. [Google Scholar] [CrossRef]
- Liu, B.; Li, Z.; Chen, X.; Huang, Y.; Liu, X. Recognition and Vulnerability Analysis of Key Nodes in Power Grid Based on Complex Network Centrality. IEEE Trans. Circuits Syst. II Express Briefs 2018, 65, 346–350. [Google Scholar] [CrossRef]
- Beyza, J.; Garcia-Paricio, E.; Ruiz, H.F.; Yusta, J.M. Geodesic Vulnerability Approach for Identification of Critical Buses in Power Systems. J. Mod. Power Syst. Clean Energy 2021, 9, 37–45. [Google Scholar] [CrossRef]
- Luo, L.; Han, B.; Rosas-Casals, M. Network hierarchy evolution and system vulnerability in power grids. IEEE Syst. J. 2018, 12, 2721–2728. [Google Scholar] [CrossRef]
- Pu, C.; Wu, P.; Xia, Y. Vulnerability Assessment of Power Grids against Link-Based Attacks. IEEE Trans. Circuits Syst. II Express Briefs 2020, 67, 2209–2213. [Google Scholar] [CrossRef]
- Fang, J.; Su, C.; Chen, Z.; Sun, H.; Lund, P. Power system structural vulnerability assessment based on an improved maximum flow approach. IEEE Trans. Smart Grid 2018, 9, 777–785. [Google Scholar] [CrossRef]
- López-Lezama, J.M.; Galeano, J.C.C.; Trujillo, E.R. Assessment of the electric grid interdiction problem considering different network models. J. Appl. Sci. Eng. 2020, 23, 175–183. [Google Scholar] [CrossRef]
- República de Colombia, Ministerio de Minas y Energía, Comisión de Regulación de Energía y Gas. 2015. Available online: http://apolo.creg.gov.co/Publicac.nsf/1c09d18d2d5ffb5b05256eee00709c02/84e16439657b002b05257e52005011b5?OpenDocument (accessed on 23 March 2021).
- Bie, Z.; Lin, Y.; Li, G.; Li, F. Battling the Extreme: A Study on the Power System Resilience. Proc. IEEE 2017, 105, 1253–1266. [Google Scholar] [CrossRef]
- Calvete, H.I.; Galé, C.; Mateo, P.M. A new approach for solving linear bilevel problems using genetic algorithms. Eur. J. Oper. Res. 2008, 188, 14–28. [Google Scholar] [CrossRef]
- Li, H.; Jiao, Y.; Zhang, L. Orthogonal genetic algorithm for solving quadratic bilevel programming problems. J. Syst. Eng. Electron. 2010, 21, 763–770. [Google Scholar] [CrossRef][Green Version]
- Wang, G.M.; Wang, X.J.; Wan, Z.P.; Jia, S.H. An adaptive genetic algorithm for solving bilevel linear programming problem. Appl. Math. Mech. 2007, 28, 1605–1612. [Google Scholar] [CrossRef]
- Arroyo, J.M.; Fernández, F.J. A genetic algorithm for power system vulnerability analysis under multiple contingencies. Stud. Comput. Intell. 2013, 482, 41–68. [Google Scholar] [CrossRef]
- Lezama, J.M.L.; Cuestas, B.J.R.; Valencia, J.P.H.A. Bilevel Attacker-Defender Model for Enhancing Power Systems Resilience with Distributed Generation. Sci. Tech. 2020, 25, 540–547. [Google Scholar] [CrossRef]
- Wang, G.; Wan, Z.; Wang, X.; Lv, Y. Genetic algorithm based on simplex method for solving linear-quadratic bilevel programming problem. Comput. Math. Appl. 2008, 56, 2550–2555. [Google Scholar] [CrossRef]
- Smith, J.E. Self-adaptation in evolutionary algorithms for combinatorial optimisation. Stud. Comput. Intell. 2008, 136, 31–57. [Google Scholar] [CrossRef]
- Zimmerman, R.D.; Murillo-Sánchez, C.E.; Thomas, R.J. MATPOWER: Steady-state operations, planning, and analysis tools for power systems research and education. IEEE Trans. Power Syst. 2011, 26, 12–19. [Google Scholar] [CrossRef]
- Amirioun, M.H.; Aminifar, F.; Lesani, H.; Shahidehpour, M. Metrics and quantitative framework for assessing microgrid resilience against windstorms. Int. J. Electr. Power Energy Syst. 2019, 104, 716–723. [Google Scholar] [CrossRef]
- Panteli, M.; Mancarella, P.; Trakas, D.N.; Kyriakides, E.; Hatziargyriou, N.D. Metrics and Quantification of Operational and Infrastructure Resilience in Power Systems. IEEE Trans. Power Syst. 2017, 32, 4732–4742. [Google Scholar] [CrossRef]
- Henry, D.; Emmanuel Ramirez-Marquez, J. Generic metrics and quantitative approaches for system resilience as a function of time. Reliab. Eng. Syst. Saf. 2012, 99, 114–122. [Google Scholar] [CrossRef]
- Chalishazar, V.; Poudel, S.; Hanif, S.; Mana, P.T. Power System Resilience Metrics Augmentation for Critical Load Prioritization. Available online: https://www.pnnl.gov/main/publications/external/technical_reports/PNNL-30837.pdf (accessed on 2 December 2020).
- Li, F. Rui Bo DCOPF-Based LMP simulation: Algorithm, comparison with ACOPF, and sensitivity. Conf. Paper IEEE Trans. Power Syst. 2008, 22, 1475–1485. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, C.C.; Schneider, K.P.; Ton, D.T. Toward a resilient distribution system. IEEE Power Energy Soc. Gen. Meet. 2015, 1–5. [Google Scholar] [CrossRef]
- Panteli, M.; Mancarella, P. Influence of extreme weather and climate change on the resilience of power systems: Impacts and possible mitigation strategies. Electr. Power Syst. Res. 2015, 127, 259–270. [Google Scholar] [CrossRef]







| Resiliency Degree | |
|---|---|
| None | |
| Deficient | |
| Poor | |
| Regular | |
| Good | |
| Excellent |
| Bus | Type | P Load (MW) | Q Load (MVAR) | Voltage (p. u) |
|---|---|---|---|---|
| 1 | PV | 0 | 0 | 1.07 |
| 2 | PQ | 300 | 98.61 | 1.08 |
| 3 | PV | 300 | 98.61 | 1.09 |
| 4 | Slack | 400 | 131.47 | 1.06 |
| 5 | PV | 0 | 0 | 1.06 |
| Generator | Pg (MW) | Qg (MVAR) | Cost (USD/MWh) |
|---|---|---|---|
| G1 | 40 | 30 | 14 |
| G2 | 170 | 127.5 | 15 |
| G3 | 324.5 | 390 | 30 |
| G4 | 0 | −10.8 | 40 |
| G5 | 470.69 | −165 | 10 |
| Resource | Costs of Attacking Elements, DR, and Load Shedding |
|---|---|
| Cost of attacking a line (USD/line) | 50 |
| Cost of attacking a generator (USD/generator) | 100 |
| Total resources of the attacker (USD) | 300 |
| Load shedding costs buses 2, 3, 4 (USD/MWh) | 100, 100, 400 |
| DR at buses 2, 3, 4 (%) | 0, 50, 25 |
| Cost of DR at buses 2, 3, 4 (USD/MWh) | 0, 50, 50 |
| Attack | Attacked Lines | Attacked Generators | Operation Cost × 105 (USD) | % of Load Served |
|---|---|---|---|---|
| 1 | L1, L2, L5, L6 | G4 | 1.8365 | 52 |
| 2 | L2, L3, L5, L6 | G4 | 1.7485 | 60 |
| 3 | L2, L4, L5, L6 | G4 | 1.7203 | 60 |
| 4 | L2, L5, L6 | G4 | 1.7013 | 60 |
| 5 | L1, L2, L6 | G3 | 1.4800 | 20 |
| 6 | L1, L2, L3, L6 | G3 | 1.4800 | 20 |
| 7 | L1, L2, L4, L6 | G3 | 1.4800 | 20 |
| 8 | L1, L2, L5, L6 | G3 | 1.4800 | 20 |
| 9 | L1, L2 | G3, G4 | 1.3287 | 22.34 |
| 10 | L2, L3, L4, L6 | G3 | 1.3023 | 40.88 |
| Bus | Generation (MW) | Generation Cost (USD) | Served Load (MW) | Served Load (%) | Cost of Load Shedding (USD) |
|---|---|---|---|---|---|
| 1 | 0 | 0 | - | - | - |
| 2 | - | - | 220 | 73.33 | 8000 |
| 3 | 520 | 15,600 | 300 | 100 | 0 |
| 4 | 0 | 0 | 0 | 0 | 160,000 |
| 5 | 0 | 0 | - | - | - |
| Attacked Elements | Operation Cost (USD) | Served Load (MW) |
|---|---|---|
| L1, L2, L5, L6, G4 | 14,464 | 700 |
| Node | Power Supplied (MW) | DR (MW) | Load Shedding (MW) | Cost (USD) | Served Load (%) |
|---|---|---|---|---|---|
| 2 | 300 | 0 | 0 | 0 | 100 |
| 3 | 220 | 80 | 0 | 4000 | 100 |
| 4 | 0 | 100 | 300 | 125,000 | 25 |
| Type | Pmax (MW) | Cost (USD/MW) |
|---|---|---|
| 1 | 100 | 45 |
| 2 | 300 | 45 |
| Location DG-Type | Power Generated (MW) | Operation Cost (USD) | Served Load (MW) | Load Supplied (%) |
|---|---|---|---|---|
| 4(1), 4(2) | 100, 300 | 41,648 | 920 | 92 |
| Bus | Active Power (MW) | Load Shedding (MW) | Cost (USD) | Load Supplied (%) |
|---|---|---|---|---|
| 2 | 300 | 0 | 0 | 100 |
| 3 | 220 | 80 | 8000 | 73.33 |
| 4 | 400 | 0 | 0 | 100 |
| Location DG-Type | DR Location | DR | Operation Cost (USD) | Load Supplied (MW) |
|---|---|---|---|---|
| 4-(1), 4-(2) | 3 | 80 | 37,645 | 1000 |
| Served Load (MW) | Operation Cost (USD) | Load Shedding Cost (USD) | |
|---|---|---|---|
| Scenario 1 | 520 | 183,650 | 168,000 |
| Scenario 2 | 700 | 144,645 | 120,000 |
| Scenario 3 | 920 | 41,648 | 8000 |
| Scenario 4 | 1000 | 37,645 | 0 |
| Resilience | ||||
|---|---|---|---|---|
| Scenario 1 | 0.52 | 0.0852 | 0.3026 | Poor |
| Scenario 2 | 0.70 | 0.1703 | 0.4351 | Poor |
| Scenario 3 | 0.92 | 0.8079 | 0.8639 | Good |
| Scenario 4 | 1 | 1 | 1 | Excellent |
| Attacked Lines | Attacked Generators | DG (Bus-Type) | DR (Bus) | |
|---|---|---|---|---|
| Scenario 1 | 1, 7, 10, 15, 17, 18, 19, 25, 26, 28, 36, 37 | G21, G22 | - | - |
| Scenario 2 | 1, 2, 3, 8, 10, 11, 18, 20, 21, 23, 27, 29, 36 | G23 | - | 6, 8, 9, 11, 14, 20 |
| Scenario 3 | 1, 7, 10, 15, 17, 18, 19, 25, 26, 28, 36, 37 | G21, G22 | 6-1, 9-1, 12-1, 14-2, 19-2, 24-2 | - |
| Scenario 4 | 1, 2, 3, 8, 10, 11, 18, 20, 21, 23, 27, 29, 36 | G23 | 6-1, 9-1, 12-1, 14-2, 19-2, 24-2 | 6, 8, 9, 11, 14, 20 |
| Load Served (MW) | Load Served (%) | Load Shedding Cost (USD) | |
|---|---|---|---|
| Scenario 1 | 1094.5 | 38.40 | 336,464 |
| Scenario 2 | 1527.2 | 53.58 | 218,736 |
| Scenario 3 | 1318.0 | 46.24 | 255,394 |
| Scenario 4 | 1750.7 | 61.42 | 184,442 |
| Resiliency | ||||
|---|---|---|---|---|
| Scenario 1 | 0.3840 | 0.052211 | 0.21812 | Deficient |
| Scenario 2 | 0.5359 | 0.131355 | 0.33360 | Poor |
| Scenario 3 | 0.4625 | 0.078019 | 0.27023 | Poor |
| Scenario 4 | 0.6142 | 0.147741 | 0.38095 | Poor |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mosquera Palacios, D.J.; Trujillo, E.R.; López-Lezama, J.M. Vulnerability Analysis to Maximize the Resilience of Power Systems Considering Demand Response and Distributed Generation. Electronics 2021, 10, 1498. https://doi.org/10.3390/electronics10121498
Mosquera Palacios DJ, Trujillo ER, López-Lezama JM. Vulnerability Analysis to Maximize the Resilience of Power Systems Considering Demand Response and Distributed Generation. Electronics. 2021; 10(12):1498. https://doi.org/10.3390/electronics10121498
Chicago/Turabian StyleMosquera Palacios, Darin Jairo, Edwin Rivas Trujillo, and Jesús María López-Lezama. 2021. "Vulnerability Analysis to Maximize the Resilience of Power Systems Considering Demand Response and Distributed Generation" Electronics 10, no. 12: 1498. https://doi.org/10.3390/electronics10121498
APA StyleMosquera Palacios, D. J., Trujillo, E. R., & López-Lezama, J. M. (2021). Vulnerability Analysis to Maximize the Resilience of Power Systems Considering Demand Response and Distributed Generation. Electronics, 10(12), 1498. https://doi.org/10.3390/electronics10121498







