Abstract
Safety application systems in Vehicular Ad-hoc Networks (VANETs) require the dissemination of contextual information about the scale of neighbouring vehicles; therefore, ensuring security and privacy is of utmost importance. Vulnerabilities in the messages and the system’s infrastructure introduce the potential for attacks that lessen safety and weaken passengers’ privacy. The purpose of short-lived anonymous identities, called “pseudo-identities”, is to divide the trip into unlinkable short passages. Researchers have proposed changing pseudo-identities more frequently inside a pre-defined area, called a cryptographic mix-zone (CMIX) to ensure enhanced protection. According to ETSI ITS technical report recommendations, the researchers must consider the low-density scenarios to achieve unlinkability in CMIX. Recently, Christian et al. proposed a Chaff-based CMIX scheme that sends fake messages under the consideration of low-density conditions to enhance vehicles’ privacy and confuse attackers. To accomplish full unlinkability, in this paper, we first show the following security and privacy vulnerabilities in the Christian et al. scheme: Linkability attacks outside the CMIX may occur due to deterministic data sharing during the authentication phase (e.g., duplicate certificates for each communication). Adversaries may inject fake certificates, which breaks Cuckoo Filters’ (CFs) updates authenticity, and the injection may be deniable. CMIX symmetric key leakage outside the coverage may occur. We propose a VPKI-based protocol to mitigate these issues. First, we use a modified version of Wang et al.’s scheme to provide mutual authentication without revealing the real identity. To this end, the messages of a vehicle are signed with a different pseudo-identity “certificate”. Furthermore, the density is increased via the sending of fake messages in low traffic periods to provide unlinkability outside the mix-zone. Second, unlike Christian et al.’s scheme, we use the Adaptive Cuckoo Filter (ACF) instead of CF to overcome the false positives’ effect on the whole filter. Moreover, to prevent any alteration of the ACFs, only RUSs distribute the updates, and they sign the new fingerprints. Third, the mutual authentication prevents any leakage from the mix zones’ symmetric keys by generating a fresh one for each communication through a Diffie–Hellman key exchange.
1. Introduction
Intelligent transportation systems (ITS), particularly Vehicular Ad Hoc Networks (VANETs), are constantly growing in importance. Efficiency and security are achieved in VANETs mainly through safety applications and non-safety applications such as entertainment and internet access. In safety applications, beaconing services are necessary because they are essential for ITS effectiveness; otherwise, accidents can occur. Open networks that are accessible by any node are characteristic of VANETs. In general, the two types of communication performed by VANETs are Vehicle to Vehicle (V2V) and Vehicle to Infrastructure (V2I), which communicate through the latest Radio Access Technology (RAT) IEEE 802.11bd for Dedicated Short Range Communications (DSRC) and New Radio NR-V2X for Cellular-V2X (C-V2X). They reduce the packet collisions [1] and they can work in tunnels and confined areas [2]. The On-Board Units (OBUs) of vehicles must transmit Cooperative Awareness Messages (CAMs) as safety messages due to their high mobility, providing real-time information on velocity, location, and heading [3]. In compliance with international standards (i.e., IEEE 1609.2 WG [4] and the European Telecommunications Standards Institute (ETSI) ITS [5]), to ensure the integrity, non-repudiation and authenticity of messages, vehicles and Roadside Units (s) are formed with public and private key pairs, in addition to digital signatures. Furthermore, established safety requirements based on Vehicle Public Key Infrastructure (VPKI) require multiple Certificate Authorities (CAs) to administer certificates for the underlying bodies [6,7]. These CAs permit long-term certificates for vehicles and s after registration. Later, they grant certificates based on pseudo-identities and “anonymous credentials” to deter some types of road attacks. However, the standard ETSI [8] body also suggests changing pseudo-identities in combination with modifying all communication stack layer identifiers, such as the Network Access Control (MAC) and the Internet Protocol (IP) addresses [9]. Nevertheless, a passive attacker who gathers information from these CAMs can comfortably perform location tracking by syntactic linking attack, referring to the old and new vehicle pseudo-identities. Additionally, adversaries can link pseudo-identities by analysing signed messages’ contents, and the adversary can accurately determine the next location of the car. This is defined as a Semantic linking attack [10]. We should note that the semantic link attack is more powerful than the syntactic link attack because the adversary produces an attack based on the details included in the security messages used to link the pseudo-identities, which produces better results [11]. Various research works have focused on managing the pseudo-identity change to solve these linking attacks over the last few years. For example, some techniques recommend that vehicles set up a silent period, i.e., their transmitters stay off (do not send messages) for a specific duration after changing their pseudo-identities, although they can still accept and process incoming messages [8]. Nonetheless, while this tends to make tracking very difficult, safety applications may be impaired because vehicles cannot send safety messages during this time. As a consequence, the probability of collision rises for such techniques. An alternative is the idea of a mix-zone, which is pre-defined as a geographic region (bound to the coverage) in which vehicles exchange messages, except for position-related messages since they are in the same place, and they change pseudo-identities within that region. Researchers have suggested improving the privacy strategy for pseudo-identity transition techniques in Cooperative-ITS (C-ITS) [12]. Freudiger et al. [13] suggested encrypting the exchanged messages inside the mix-zone and called it the CMIX strategy. This relies on a symmetric key to share safety messages within the mix-zone, which ensures that all vehicles can use the same key to avoid linkability within the mix-zone, whereby the provides the symmetric key to all vehicles within the mix-zone [8]. Christian et al. later considered the density and suggested a CMIX based on Chaff, believing that it would provide location privacy and irresistible security [14]. However, the filter used in Christians et al.’s scheme to differentiate between real and fake messages is weak, and an internal adversary may expose the hash table to malicious injections. Additionally, the filter performance disrupts the Chaff messages’ concept, which may break the system and make it vulnerable to linking attacks. We believe that the authentication of the transmitted messages and senders’ identities must be improved significantly for safety applications to address these problems. Therefore, in our scheme, entities might prove the possession of some secret information preloaded in the OBU of the vehicle.
1.1. Our Contributions
In this paper, we first revisit the Christian et al.’s CMIX-based scheme [14] and then point out the following security and privacy issues: (1) Linkability attacks during the communication outside the mix-zone, (2) unreliable Cuckoo Filters’ (CFs) updates (in the low-density of the traffic), which breaks the privacy and safety of the whole system, and (3) mix-zones’ encryption key leakage, which allows any compromised vehicle to break the safety of the system. We then propose an improved version that is resistant to these issues. To comply with Christian et al.’s scheme, we utilise a modified version of [15] by replacing digital certificates with an Identity-Based Signature. In summary, our scheme provides the following features:
- We use Adaptive Cuckoo Filter(ACF) instead of CF, as in [14], to mitigate the effect of false positives that may impact the performance of the filter; this enhances the system in sending Chaff messages to confuse eavesdropping adversaries that exploit traffic flow to breach unlinkability. We also use the pseudo-identity generation concept from [15], which has non-malleability to hide the certificates of actual vehicles.
- We provide unforgeability and non-repudiation by adding an signature and timestamp in each message, in particular, on the new fingerprinted Chaff messages before inserting them into the ACF. Hence, to preclude any possibility of malicious injections, we also remove the ACFs forwarding task from vehicles, like in [14]; in our scheme, s are the sole authority to distribute them.
- We modify the mutual authentication between s and vehicles based on certificates instead of IDs, as in [15], before generating the symmetric key of a mix-zone, as the generation of a shared key follows the Diffie–Hellman key exchange method to provide confidentiality and privacy by preventing any key leakage.
These features allow our protocol to achieve unlinkability, unforgeability, and mutual authentication.
1.2. Roadmap
The rest of the paper is structured as follows: Section 2 presents the VANETs architecture and our scheme’s design goals. Section 3 reviews the related work on location privacy that aims to achieve unlinkability. In Section 4, we present the security and privacy model of the improved Chaff-based CMIX. In Section 5, we introduce our improved CMIX scheme. Section 6 gives a comprehensive security analysis. Section 7 is dedicated to a comparison between our scheme and similar schemes in the literature. Finally, Section 8 concludes the paper.
2. Background
2.1. VPKI Architecture
The heterogeneous VANET architecture primarily consists of three bodies, i.e., vehicles, s and CAs. The vehicle is also called an OBU, a transceiver board placed on the vehicle to exchange information with CAs, s and other vehicles. Each and vehicle has credentials and private keys for safe and secure communication. CAs register and certify the public keys to vehicles and s. s are used to monitor road traffic and minimise accidents. They also provide access points for vehicles and other s to disseminate information securely and effectively. Although s use wire-based communication, vehicles use wireless communication between each other and with s. Note that this protocol can be executed in tunnels and other confined areas due to these communications features; see Figure 1 for a standard VANET architecture. In general, the VPKI should have the following list of CAs [8,14]:
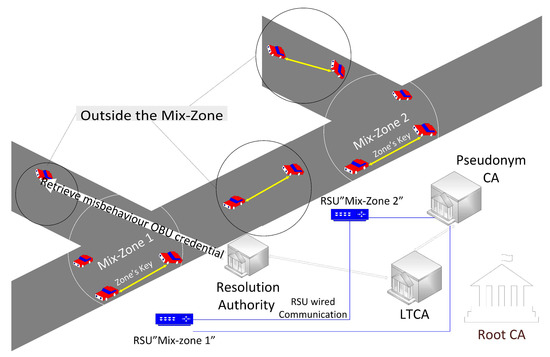
Figure 1.
Our C-ITS PKI High-Level Architecture: (1) RCA is a government entity, and it is responsible for managing all subordinate CAs. (2) is responsible for entity registration and issuing certificates. (3) RA is responsible for retrieving misbehaving entities’ credentials. (4) is responsible for pseudonym issuance. Moreover, s are responsible for vehicles entering/leaving the mix-zones. There are two types of communication: (1) through a shared key that is distributed by s inside the mix-zone [8]. (2) Anonymous communication, which is performed outside the mix-zone.
- The root CA (RCA) Figure 1 is at the top of the hierarchy, serving as a governance body that certifies other intermediate authorities.
- The long-term CA () Figure 1 is an intermediary authority that is responsible for vehicle registration and long-term certificate issuance for vehicles and s.
- The resolution authority (RA) Figure 1 is a central authority that can address a pseudo-identity and thereby validate the long-term identity of the vehicle in the event of a fraudulent act by communicating with the and the .
- The pseudo-identity CA () Figure 1 is an intermediary authority responsible for issuing pseudo-identities for registered vehicles.
In addition, the RCA manages various domains through cross-certification. There is only one in each domain, and vehicles must register in the home domain. However, they may cross domains and communicate with foreign s to gain pseudo-identities. As far as the is concerned, it may be involved in one or even several domains. Therefore, if the vehicle requires a pseudo-identity, the can only offer one authentication ticket per vehicle, and the authorisation will be with the certificate gained from the . In PKI-based systems, even though the use of pseudo-identities as anonymised certificates guarantees the anonymity of the identity [16], it cannot guarantee the privacy of the position. For example, a vehicle has to change its pseudo-identity during its trip. However, the eavesdropping monitor with two observation points in the same road will link the changing of a moving vehicle’s pseudo-identity.
2.2. Design Goals
The proposed work should satisfy security and privacy preservation through the following goals:
- Authentication: There are two forms of authentication: mutual authentication and message authentication. Mutual authentication demands the ability of two entities to identify each other at a specified session. Message authentication confirms the integrity of the messages and proves that they are generated from authorised vehicles and have not been unmodified through the transmission.
- Nonrepudiation: This property applies to a case in which the recipient is willing to show to a third party that the sender cannot dispute responsibility for the messages’ generation. It prevents the attacker from forging messages with other identities.
In a particular scenario of VANET low density, we aim to achieve essential properties.
- Unlinkability: The certificate and information in the messages have to be unlinkable for privacy protection, even if identical vehicles change certificates or the exact vehicle sends new messages with new data, so that an adversary can never discover shared properties in several messages and then link them to a specific vehicle and trace its location. The change time to time in each communication and in the mix-zone on pseudo-identity rather than real identity. In addition, certificates in the communication have a relation with the pseudo-identity.
3. Related Work
Several types of research have been published on pseudo-identity unlinkability and vehicle privacy in ITS. This section includes our review of the most recent works on location privacy, which is also a significant element that needs to be considered [17], as well as pseudo-identity change management in VANETs. Due to the data transmission in VANETs for safety applications and the amplification in broadcasting technology, messages can be made open to adversaries; thus, it is easy to listen to the correspondence channels via the ITS infrastructure [18,19,20]. In this context, researchers have attempted to prevent the attacks related to linking the communications’ information. Various studies have focused on unlinkability accomplishment by optimising the pseudo-identity change management mechanism to retain vital details, such as position and trajectory. However, we are now seeing that various literature schemes suffer from a vulnerability to linkability attacks that breach privacy.
Note that the following parameters are listed in the ETSI ITS technical report [8] on pseudo-identity change management as not adequate for different reasons, namely: (1) fixed parameters, (2) silent period, (3) randomness, and (4) CMIX. Eckhoff et al. [21] suggested allowing a pool of pseudo-identities for each vehicle to use within one week, whereby each pseudo-identity will be valid for ten minutes without overlapping, which is a fixed parameters scheme. It will deter attacks, such as Sybil attacks, and address the trade-off between privacy and safety. However, the use of fixed parameters is straightforward, and this allows the adversary to know the parameter values of a given vehicle, making it easier to trace them. Choosing randomness dependent on fixed parameters, such as randomly changing the pseudo-identity every five minutes plus or minus one minute, helps deter the attacker from detecting a change in the pseudo-identity. However, it is still possible to link attacks when a few vehicles change their pseudo-identities while others retain their old ones. Furthermore, an attacker can track vehicles effortlessly by using trajectory predictability algorithms, such as Kalman filters [22], especially when the density is not high or when a few vehicles change their pseudo-identities while others maintain theirs [8]. Some researchers propose shutting off the wireless transmitter at an unspecified point and changing pseudo-identities during the silent period [10,23,24,25,26,27]. Vehicles would have adequate protection during this time, but this would dramatically limit protection due to the non-broadcasting series of CAMs, which would lead to an increase in vehicle accidents.
In addition to the silent period, Buttyan et al. propose changing the pseudo-identity when the vehicle’s speed is less than 30 km/h [26]; however, this does not take into account low-density situations that lead to linking attacks. On the other side, Boualouache et al. in [10] suggested a Vehicular Location Privacy Zone (VLPZ) to regulate service stations (e.g., diesel, fuel and charging stations or toll booths). However, syntactic linking attacks can easily occur due to the lack of coordination caused by the silent period [28], and the attackers may track the pseudo-identity change [22]. Additionally, the link attack’s impact worsens in low-density situations due to the simplicity of analysing a low number of vehicles. Conversely, the mix-zones concept does not need to limit the feasibility of safety applications. Initially, the mix-zone approach was proposed by Beresford et al. [12], leading to the use of a pre-defined geographical region to change pseudo-identities. These zones have a CA hierarchy, and the semi-honest s dominate the mix-zone. Freudiger et al. enhanced the scheme by inserting a symmetric key to encrypt messages among vehicles within the mix-zone and called it a CMIX [13]. While CMIX-based systems are sensitive to linking attacks, they depend heavily on vehicle traffic, vehicle arrival, speeds, and probable vehicle movements through mixed zones. These schemes are also vulnerable to linking attacks in low-density [8] scenarios. Lu et al. [29] proposed changing pseudo-identities at social spots, i.e., a public space, which gives the benefit of traffic to confuse the attacker. For example, vehicles stopped at traffic lights can change their pseudo-identities when these turn green, and in shopping mall parking, vehicles can change their pseudo-identities before they exit. However, this scheme is simplistic and inadequate to guarantee unlinkability because high density does not guarantee that certificates can be linked and traced back to identity. The authors in [30] proposed a context-based system to use credibility scores sent in order to cause synchronous pseudo-identity changes; those scores are part of the periodic safety beacons, thus increasing the anonymity set. With the same, i.e., context-based, approach Liu et al. [31] presented another pseudo-identity change management technique, which is an entirely uncoordinated pseudo-identities change in distributed networks after a random delay to allow regular and unlinkable changes, whereby they suppose that the anonymity can be accomplished at trivial throughput loss is in large networks. Zhao et al. [32] proposed a pseudo-identity changing game that is mixed-context and was developed by examining the relationship between changing the pseudo-identity, expense, and privacy. Moreover, Zeng and Xu [33] suggested pseudo-identity changing privacy preservation authentication based on a mixed-context. However, attackers can easily threaten these systems if the density is low, as with traffic-based techniques.
Furthermore, a dynamic zone-based pseudo-identity change management [34] has recently been proposed to set up a temporary on-demand swap zone in which a vehicle will randomly pick and exchange a pseudo-identity with another vehicle without a group manager. This change adapts to reduce the contact cost of establishing pseudo-identity swap zones based on the environment.
Benarous et al.’s [35] is proposal based on two main factors: the strategies of “hiding inside the crowd” and “location obfuscation”. When the vehicle either exits a particular geographical area or the pseudo-identity reaches its expiry, it must change it. This change management holds the count of the neighbouring vehicles, and if the pre-defined neighbour threshold matches the current neighbours, then it changes pseudo-identity with other vehicles cooperatively. Otherwise, for the vehicle to change its pseudo-identity, the vehicle obfuscates its location and turns the speed to zero. The downside is that the unreliable broadcasting of speed and location information poses questions regarding safety applications. In 2018, Christian et al. [14] introduced a development for CMIX by adding Chaff messages (representing vehicles on the road) to stabilise the density in low-density scenarios in CMIX. Hence, the Chaff-based CMIX protocol alleviates Freudiger et al.’s CMIX scheme’s weaknesses in low-density situations by confusing the attacker to strengthen the CMIX scheme. As ETSI ITS confirmed the importance of considering the low density as mentioned in their report “the higher the density of vehicles, the more efficient the mix-zone is against tracking.” [8]. Moreover, this scenario is possible in the peak and off peak hours daily. Furthermore, the lockdown of the Coronavirus Disease of 2019 (COVID-19) pandemic raises the chances of low-density scenarios in different countries. In fact, this emphasises the value of Christian et al.’s scheme. However, their Chaff-based CMIX scheme has some issues that could break the system.
4. Security and Privacy Issues of Christian et al.’s Chaff-Based CMIX Scheme
Christian et al. [14] proposed a protocol using Chaff messages in low-density scenarios to increase the number of fake vehicles which prevents linkability attacks. However, there is a security vulnerability in their protocol which is run outside the mix-zone. More concretely, the signature and the certificate are not encrypted in the following message which allows attackers to break the unlinkability:
where is the pseudo-identity of the j-th vehicle , is the public key of while denotes message encryption with the specified key, is the symmetric key of the r-th mix-zone, is the CF of the r-th mix-zone, is the ’s certificate, and , denote ’s and ’s signatures. In addition, the message contains non-encrypted values, namely the timestamp , the sender’s signature , and the certificate . Nevertheless, sending these messages outside the mix-zone leads to the following security issues:
- The privacy of vehicles can be compromised. Vehicles update their pseudo-identity once they move from one mix-zone to another. However, outside mix-zones, while they communicate with other vehicles securely, they also send and separately. Therefore, it is trivial for the adversary to link the old and the new pseudo-identities, meaning they can identify the sender, which breaks the unlinkability property.
- Unreliable CFs update. To update the CF, vehicles forward the as a new version in a ciphertext; Christian et al. argue that the signature of is attached to prevent forgery attacks. It is possible for malicious vehicles to inject real pseudo-identities and send them to the inside the mix-zone or other vehicles, subsequently denying this malicious activity. Moreover, if an adversary compromises the and tries to tamper with the CF, the vehicles will discard messages from these fingerprinted pseudo-identities, which leads to accidents by affecting safety applications.
- The secret key of the mix-zones can cause leakage. The ciphertext C contains the encryption key , which must only be used in the specified area. The receiving of this key outside the mix-zone by an external unauthorised vehicle (i.e., the mix-zone is compromised) threatens the security of the communication. Hence, an attacker would be able to communicate maliciously with honest vehicles outside the specified area, which would break the system’s safety.
Moreover, we should note here that Mitzenmacher et al. [36] specified a drawback that may affect the CF’s performance. In particular, they suggested that the false positives that can occur in a CF may affect the search for an element inside these hash tables. To fix this, they proposed a technique that identified the element that caused false positives, then removed it and re-inserted it again differently. Then, if they searched for that element, it would be found. Undoubtedly, the performance of the filter in a Chaff-based scheme plays a vital role. Thus, we are using ACF rather than CF in our scheme.
5. Our Improved Chaff-Based CMIX Scheme
We are now ready to describe our VPKI-based scheme. We utilise a modified version of Wang et al.’s Identity Based Signature (IBS) construction by replacing IDs with certificates to comply with Christian et al.’s protocol [15]. The setup is as follows:
5.1. Setup
Let , be cyclic groups of prime order q, and be generators of , , respectively. Let also be hash functions where
is a keyspace, and ℓ is a security parameter while is the multiplicate group (which is a list of integers modulo q and are co-prime with q). Let also and be the long-term identities of the i-th and the j-th vehicle, respectively. Furthermore, denote for the pseudo-identity of the j-th vehicle. Let be a public and private key pair, and be the master secret key of . During the setup of and vehicle, first chooses and computes , and . maintains a public list and a private list for and . As we describe below, is going to maintain for mutual authentication, while is going to maintain for tracking the authentication details of registered vehicles. Next, we describe the setup of the and vehicles:
- RSU setup: generates from in and sends it to . also generates , where is the public key with respect to . then computes and , where , and stores the tuple for later to securely communicate with the vehicles entering the mix-zone.
- Vehicle Setup: Whenever a vehicle enters a new region, first generates from in and sends it to . also generates , where is the public key with respect to . stores . also incorporates the tuple into in and into List that is accessible for , and when expires in each, forces the vehicles to refresh their authentication keys. The also loads existing s’ certificates to the vehicle. Next,
- picks and then computes its authentication key = , where is the timestamp.
- computes , , and sends to , where . The authentication key is saved in .
- generates a challenge and a dynamic password , where . The challenge is sent to , which stores it locally.
- maintains the tuple , where is the expiration date.
- PCA Setup: generates from in and sends it to . also generates , where is the public key with respect to . In addition, sends and to . Then, generates the public parameters .
- RA Setup: sends , and the registered s identities to , while sends and . Therefore, these values help to detect any malicious vehicles or s.
Note that obligates vehicles to update their authentication keys if is expired.
5.2. Mutual Authentication
The authentication between s and vehicles starts once the vehicles are in the transmission range of the s. In the following, we describe the protocol between and vehicles.
- broadcasts = , where , where along is the timestamp and is used to generate symmetric keys and is the ACF of .
- A vehicle entering the transmission range receives and validates the signature . If not verified, it aborts the protocol. Otherwise, stores .
- next computes
- (a)
- and .
- (b)
- and , where .
- (c)
- , where and sends C to .
- now computes the symmetric key and decrypts C. Next,
- (a)
- First validates the signature , and aborts if it is not valid.
- (b)
- Aborts the protocol if , where .
- (c)
- Verifies and aborts if it is not valid.
- (d)
- Searches for a tuple in , where .
- (e)
- Aborts the validation if the tuple is expired or it is not in , or it has more than one tuple.
- (f)
- Computes .
- (g)
- If then will be authenticated to without revealing its identity.
5.3. Privacy Preservation: Pseudo-Identity Generation and Updating Authentication Key
Our scheme provides privacy preservation by focusing on pseudo-identity generation to achieve untraceability and the update of the authentication key to accomplish full unlinkability.
5.3.1. Pseudo-Identity Generation for Vehicles
To preserve privacy and untraceability between vehicles, they need to use pseudo-identities rather than their real identities. As mentioned previously, s are responsible for pseudo-identity generation. After is in the transmission range of , the vehicle generates pseudo-identity as follows:
- computes the pseudo-identity of itself as , where and (note that the pseudo-identity of is equal to the encryption of through the Cramer–Shoup encryption scheme [37], which is non-malleable and secure against adaptive chosen-ciphertext attack (CCA2)).
- manages the generation of fake pseudo-identities and fingerprints them and signs them before inserting them into the ACFs. Then, signs the whole ACF to provide non-depuration and distributes it to the vehicles.
can detect the real identity of the vehicle if it has malicious activities, as follows. Let be a malicious vehicle and its pseudo-identity be . The obtains and computes . It then checks whether . The pseudo-identity is invalid if they are not equal. Otherwise, computes . If is valid in and , then attempts to find the from its database and learns the real identity of . For privacy reasons, the real identity of the vehicle must be hidden from other s and vehicles.
5.3.2. Unlinkability through Updating Authentication Key
In order to provide unlinkability, the system must update the authentication key and the ACF regularly. Assume that the tuple has expired based on the expiration date . Here below, to update the authentication key, and the vehicle run the protocol.
- (a)
- First generates a pseudo-identity for vehicle , where .
- (b)
- Computes , where . is used for the targeted vehicle , is used for , and is used to generate a shared key.
- (c)
- Computes a signature , where generated from and , and is a timestamp.
- (d)
- Broadcasts .
- (a)
- Receives .
- (b)
- Validates the signature using .
- (c)
- Checks the freshness of the timestamp .
- (d)
- Checks if , where with being the authentication key. Note that only the that holds can compute this pseudo-identity.
- (e)
- Updates the authentication key by computing and , where .
- (f)
- Sends , , where to .
- (a)
- First decrypts and obtains , , where .
- (b)
- Validates .
- (c)
- Aborts if .
- (d)
- Computes and aborts if .
- (e)
- Computes and updates with in , where the expiration time is .
- (f)
- The tuple is updated with in .
- (g)
- Computes , where ,
- (h)
- Broadcasts , where is a timestamp and .
- receives and checks the validity of the message. If the signature is valid and the timestamp is fresh, then it computes .
- aborts if . Otherwise, the current authentication key and challenge are replaced with and , respectively.
6. Security Analysis
We are now ready to provide a security analysis of our scheme.
6.1. Mutual Authentication
During the mutual authentication, the vehicle validates and which are received from the broadcast message by , i.e., = . Therefore, authentication is provided through signatures and certificates as long as is honest. Next, to be able to generate a shared key, first computes its and , where is sent by . Then, the can recover from in the list . Hence, even if and given to other entities, to generate valid and they must know either of or of . However, since these private values are only known by and certificates are used for authentication, no adversary can compute the shared key due to the underlying Computational Diffie–Hellman (CDH) problem. Therefore, our scheme provides the message confidentially inside the mix-zone.
6.2. Non-Repudiation
Every message generated by the vehicle or uses the digital signature as evidence of non-repudiation. Moreover, digital certificates, which are issued by , contain an expiration date. Therefore, already involves the timestamp and the receiver checks whether the is valid or not for the pseudo-identity . Thus, if or behaves maliciously, can easily detect and revoke their certificates. Hence, non-repudiation is guaranteed.
6.3. Unlinkability
Our scheme preserves privacy by signing the messages with different pseudo-identities. The real identity is secretly hidden in these messages because is computed by the authentication key where . Note that this key is only accessible by . For accountability reasons, can compute for the vehicle where because the public parameters are known by all the certificate authorities , , and . Hence, no adversaries can obtain the real identity from the ciphertext . Moreover, we also prevent information leakage by providing mutual authentication and sending Chaff messages on the road to mitigate the risk of linkability attacks by eavesdropping adversaries due to the low-density traffic. Therefore, our scheme provides unlinkability.
6.4. Defence against Compromised
In the proposed system, we assume that the CAs are fully trusted while the s and the vehicles are semi-trusted which means that they are trusted but cannot know some sensitive and private data of the vehicles. Thus, generates the private key and the based on its master key. Therefore, if s corrupted, it can be detected through the credentials generated by which can immediately revoke the ’s certificate. Moreover, the corrupted can also manipulate the . This manipulation impairs the safety application and can cause accidents. However, in our scheme, signs the fingerprinted Chaff , which helps to detect the in case it has malicious activities.
7. A Comparison of Proposed and Existing Schemes
In the previous section, we focused on three desired properties, namely mutual authentication, non-repudiation and unlinkability. Furthermore, it is also essential to show that our scheme is robust against low density. Note that previous studies have not given much attention to low density scenario. The comparison in Table 1 shows more factors related to existing VANETs’ location privacy schemes. Moreover, it summarises that our scheme overcomes the vulnerabilities of [14] which are presented in Section 4. Here we illustrate a security and privacy vulnerabilities in related existing schemes:

Table 1.
A Comparison of the proposed and existing schemes.
- Unlinkability: The fixed parameters schemes like [21] or schemes using the randomness such as [31] are vulnerable to linkability attacks. In addition, most of the existing works does not consider the traffic variability, which may help the attackers to break the unlinkability.
- Non-repudiation: Some schemes rely on identity changes after a random delay, if malicious vehicles do not change the pseudo-identity intentionally, then they will break the system. The randomness and the delay will break the non-repudiation. Moreover, this whas also the case in [35] which is based on location obfuscation and hiding in the silent period. The location obfuscation means the vehicle can turn its speed to zero and obfuscate the position while changing the pseudo-identity. Hence, it affects the safety applications. Thus, if a malicious vehicle tried to harm those applications purposely, it can deny it because the location obfuscation is part of the system. The non-repudiation issues of [14] are related to the quality of that can breach the system. Furthermore, the scheme in [15], considers the fully trusted; without a digital signature in the communication, it can deny any malicious activities.
- CMIX: The schemes tending to the CMIX are [13,14] and our scheme. The concept of cryptography in a mix-zone around is efficient, but it is associated with road density. The higher the density, the better the effect against tracking.
- No interference with safety application: The necessity of updating the information via messages without any interruption, like silent period, assures the safety application quality. Scheme such as [10,35] using the silent period with different structure. However, this threatens the safety application technologies as reported in [8] technical report. Furthermore, other schemes like [14] that added filter for Chaff messages may weaken the safety application technologies if the filter has been corrupted. In addition, in [15] that relies on , if it is compromised, it will be easy to abuse the safety application and jeopardise the passengers’ safety.
Christian et al. [14] evaluated the performance of their system using three metrics: chaff pseudonym pool size, the number of simultaneously active chaff pseudonyms, and the RSU signature generation overhead. We are consume more overhead because our system requires mutual authentication as we are using DDH. However, they did not measure the overhead of the filter’s hash tables. Our scheme uses which also uses hash functions while it has a lower false-positive rate compared to . The can find the elements that caused the false-positives after they occur, delete and re-insert them again in the hash table. Hence, it will help to find them in the search more efficiently than [36].
8. Conclusions
In this paper, we investigated Christian et al.’s Chaff-based CMIX scheme [14] that concentrated on low-density situations as essential and possible daily scenarios. However, their scheme is not sound in achieving security and privacy. Furthermore, the scheme cannot resist linkability attacks in vehicles communication, CF malicious injections, which affect safety applications, and the leakage of mix-zones’ symmetric keys to unauthorised vehicles. To overcome the weaknesses of Christian et al.’s scheme, we utilised a version of [15] by using certificates instead of IDs to accomplish mutual authentication to enhance the security and privacy of the legitimate entities. Furthermore, we accomplish unlinkability by preventing low-density exploitation via increasing the density securely and by generating unlinkable pseudo-identities for each message based on an unexampled secret authentication key. Moreover, we increase the efficiency of the Chaff messages by using ACF to overcome the CF disadvantages. To prevent malicious injection in ACFs, the signs the new fingerprinted Chaff pseudo-identities and keeps the distribution for s only. We apply a Diffie–Hellman key exchange method after the mutual authentication to prevent unauthorised vehicles from symmetric key access to mitigate any leakage of the mix-zone symmetric key. In future work, we believe that we have to evaluate our scheme and provide performance evaluation results to make the work more convincing. In addition, we will investigate our scheme efficiency in tunnels and confined area.
Author Contributions
M.S.A.-M. is the principal author of this article as part of his PhD thesis, A.H.A.-B., M.S.K. were involved in planning and supervised the work. M.S.A.-M. The specific contribution made by each author are as follows: Conceptualization, M.S.A.-M., A.H.A.-B. and M.S.K.; methodology, M.S.A.-M.; validation, M.S.A.-M., A.H.A.-B. and M.S.K.; formal analysis, M.S.A.-M.; investigation, M.S.A.-M.; M.S.A.-M.; writing—original draft preparation, M.S.A.-M.; writing—review and editing, M.S.A.-M., A.H.A.-B. and M.S.K.; visualization, M.S.A.-M.; supervision, A.H.A.-B., M.S.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Naik, G.; Choudhury, B.; Park, J.-M. IEEE 802.11 bd & 5G NR V2X: Evolution of Radio Access Technologies for V2X Communications. IEEE Access 2019, 7, 70169–70184. [Google Scholar]
- Chehri, A.; Chehri, H.; Hakim, N.; Saadane, R. Realistic 5.9 GHz DSRC vehicle-to-vehicle wireless communication protocols for cooperative collision warning in underground mining. In Smart Transportation Systems 2020; Springer: Singapore, 2020. [Google Scholar]
- Doukha, Z.; Moussaoui, S. An SDMA-Based Mechanism for Accurate and Efficient Neighborhood-Discovery Link-Layer Service. IEEE Trans. Veh. 2015, 65, 603–613. [Google Scholar] [CrossRef]
- Technology, I.V. Intelligent Transportation Systems ITS. In IEEE Standard for Wireless Access in Wireless Access in Vehicular Environments (WAVE)– Networking Services; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- ETSI; TCITS. Intelligent transport systems (its); vehicular communications; basic set of applications; definitions. Tech. Rep. ETSI TR 2009, 102, 6382009. [Google Scholar]
- ETSI, T. Intelligent transport systems (its); Security; Trust and Privacy Management; Definitions. Tech. Spec. ETSI 2012, 102, 9412012. [Google Scholar]
- Technology, I.V. Intelligent Transportation Systems ITS. In IEEE Standard for Wireless Access in Vehicular Environments Security Services for Applications and Management Messages; IEEE: Piscataway, NJ, USA, 2013. [Google Scholar]
- ETSI. Intelligent transport systems (its); Pre-Standardization Study on Pseudonym Change Management. Tech. Rep. ETSI 2018, 103, 4152018. [Google Scholar]
- Papadimitratos, P.; Buttyan, L.; Hubaux, J.-P.; Kargl, F.; Kung, A.; Raya, M. Architecture for Secure and Private Vehicular Communications. In Proceedings of the 2007 7th IEEE International Conference on ITS Telecommunications, Sophia Antipolis, France, 6–8 June 2007; pp. 1–6. [Google Scholar]
- Boualouache, A.; Senouci, S.-M.; Moussaoui, S. VLPZ: The vehicular Location Privacy Zone. Procedia Comput. Sci. 2016, 83, 369–376. [Google Scholar] [CrossRef]
- Boualouache, A.; Senouci, S.-M.; Moussaoui, S. A Survey on Pseudonym Changing Strategies for Vehicular Ad-Hoc Networks. IEEE Commun. Surv. Tutor. 2017, 20, 770–790. [Google Scholar] [CrossRef]
- Beresford, A.R.; Stajano, F. Location Privacy in Pervasive Computing. IEEE Pervasive Comput. 2003, 2, 46–55. [Google Scholar] [CrossRef]
- Freudiger, J.; Raya, M.; Falegyhazi, M.; Papadimitratos, P.; Hubaux, J.-P. Mix-Zones for Location Privacy in Vehicular Networks. In Proceedings of the ACM Workshop on Wireless Networking for Intelligent Transportation Systems (WiN-ITS), Vancouver, BC, Canada, 14–17 August 2007. [Google Scholar]
- Vaas, C.; Khodaei, M.; Papadimitratos, P.; Martinovic, I. Nowhere to hide? Mix-Zones for Private Pseudonym Change using Chaff Vehicles. In Proceedings of the 2018 IEEE Vehicular Networking Conference (VNC), Taipei, Taiwan, 5–7 December 2018; pp. 1–8. [Google Scholar]
- Wang, B.; Wang, Y.; Chen, R. A Practical Authentication Framework for VANETs. Secur. Commun. Netw. 2019, 2019. [Google Scholar] [CrossRef]
- Yang, Z.; Yang, K.; Lei, L.; Zheng, K.; Leung, V.C. Blockchain-based decentralized trust management in vehicular networks. IEEE Internet Things J. 2018, 6, 1495–1505. [Google Scholar] [CrossRef]
- Huang, J.; Fang, D.; Qian, Y.; Hu, R.Q. Recent advances and challenges in security and privacy for v2x communications. IEEE Open J. Veh. Technol. 2020, 1, 244–266. [Google Scholar] [CrossRef]
- Bellatti, J.; Brunner, A.; Lewis, J.; Annadata, P.; Eltarjaman, W.; Dewri, R.; Thurimella, R. Driving Habits Data: Location Privacy Implications and Solutions. IEEE Secur. Priv. 2017, 15, 12–20. [Google Scholar] [CrossRef]
- Narain, S.; Vo-Huu, T.D.; Block, K.; Noubir, G. Inferring User Routes and Locations Using Zero-Permission Mobile Sensors. In Proceedings of the IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016; pp. 397–413. [Google Scholar]
- Gao, X.; Firner, B.; Sugrim, S.; Kaiser-Pendergrast, V.; Yang, Y.; Lindqvist, J. Elastic Pathing: Your Speed is Enough to Track You. In Proceedings of the 2014 ACM International Joint Conference on Pervasive and Ubiquitous Computing, Seattle, WA, USA, 13–17 September 2014; pp. 975–986. [Google Scholar]
- Eckhoff, D.; Sommer, C. Readjusting the Privacy Goals in Vehicular Ad-Hoc Networks: A Safety-Preserving Solution Using Non-Overlapping Time-Slotted Pseudonym Pools. Comput. Commun. 2018, 122, 118–128. [Google Scholar] [CrossRef]
- Emara, K.; Woerndl, W.; Schlichter, J. CAPS: Context-Aware Privacy Scheme for VANET Safety Applications. In Proceedings of the 8th ACM Conference on Security & Privacy in Wireless and Mobile Networks, New York, NY, USA, 24–26 June 2015; pp. 1–12. [Google Scholar]
- Sampigethaya, K.; Huang, L.; Li, M.; Poovendran, R.; Matsuura, K.; Sezaki, K. CARAVAN: Providing Location Privacy for VANET; AD-a459 198; Washington Univ Seattle Dept of Electrical Engineering: Seattle, WA, USA, 2005. [Google Scholar]
- Sampigethaya, K.; Li, M.; Huang, L.; Poovendran, R. AMOEBA: Robust Location Privacy Scheme for VANET. IEEE J. Sel. Areas Commun. 2007, 25, 1569–1589. [Google Scholar] [CrossRef]
- Huang, L.; Matsuura, K.; Yamane, H.; Sezaki, K. Enhancing wireless location privacy using silent period. IEEE Wirel. Commun. Netw. Conf. 2005, 2, 1187–1192. [Google Scholar]
- Buttyán, L.; Holczer, T.; Weimerskirch, A.; Whyte, W. SLOW: A Practical Pseudonym Changing Scheme for Location Privacy in VANETs. In Proceedings of the 2009 IEEE Vehicular Networking Conference (VNC), Tokyo, Japan, 28–30 October 2009; pp. 1–8. [Google Scholar]
- Boualouache, A.; Moussaoui, S. S2SI: A Practical Pseudonym Changing Strategy for Location Privacy in VANETs. In Proceedings of the 2014 IEEE International Conference on Advanced Networking Distributed Systems and Applications, Bejaia, Algeria, 17–19 June 2014; pp. 70–75. [Google Scholar]
- Khodaei, M.; Noroozi, H.; Papadimitratos, P. Privacy Preservation through Uniformity. In Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks, Stockholm, Sweden, 18–20 June 2018; pp. 279–280. [Google Scholar]
- Lu, R.; Lin, X.; Luan, T.H.; Liang, X.; Shen, X. Pseudonym Changing at Social Spots: An Effective Strategy for Location Privacy in VANETs. IEEE Trans. Veh. Technol. 2011, 61, 86–96. [Google Scholar] [CrossRef]
- Santos-Jaimes, L.M.; Moreira, E.d.S. Pseudonym change strategy based on the reputation of the neighbouring vehicles in vanets. DYNA 2019, 86, 157–166. [Google Scholar] [CrossRef]
- Liu, Z.; Zhang, L.; Ni, W.; Collings, I.B. Uncoordinated pseudonym changes for privacy preserving in distributed networks. IEEE Trans. Mob. Comput. 2019, 19, 1465–1477. [Google Scholar] [CrossRef]
- Zhao, Z.; Ye, A.; Meng, L.; Zhang, Q. Pseudonym changing for vehicles in vanets: A game-theoretic analysis based approach. In Proceedings of the 2019 IEEE International Conference on Networking and Network Applications (NaNA), Daegu, Korea, 10–13 October 2019; pp. 70–74. [Google Scholar]
- Zeng, M.; Xu, H. Mix-context-based pseudonym changing privacy preserving authentication in vanets. Mob. Inf. Syst. 2019, 2019. [Google Scholar] [CrossRef]
- Yang, M.; Feng, Y.; Fu, X.; Qian, Q. Location privacy preserving scheme based on dynamic pseudonym swap zone for internet of vehicles. Int. J. Distrib. Sens. Netw. 2019, 15, 1550147719865508. [Google Scholar] [CrossRef]
- Benarous, L.; Kadri, B.; Boudjit, S. Alloyed pseudonym change strategy for location privacy in vanets. In Proceedings of the 2020 IEEE 17th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 10–13 January 2020; pp. 1–6. [Google Scholar]
- Mitzenmacher, M.; Pontarelli, S.; Reviriego, P. Adaptive cuckoo filters. ACM J. Exp. 2020, 25, 20. [Google Scholar] [CrossRef]
- Cramer, R.; Shoup, V. Universal hash proofs and a paradigm for adaptive chosen ciphertext secure public-key encryption. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 45–64. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).