Routing Algorithm Based on User Adaptive Data Transmission Scheme in Opportunistic Social Networks
Abstract
:1. Introduction
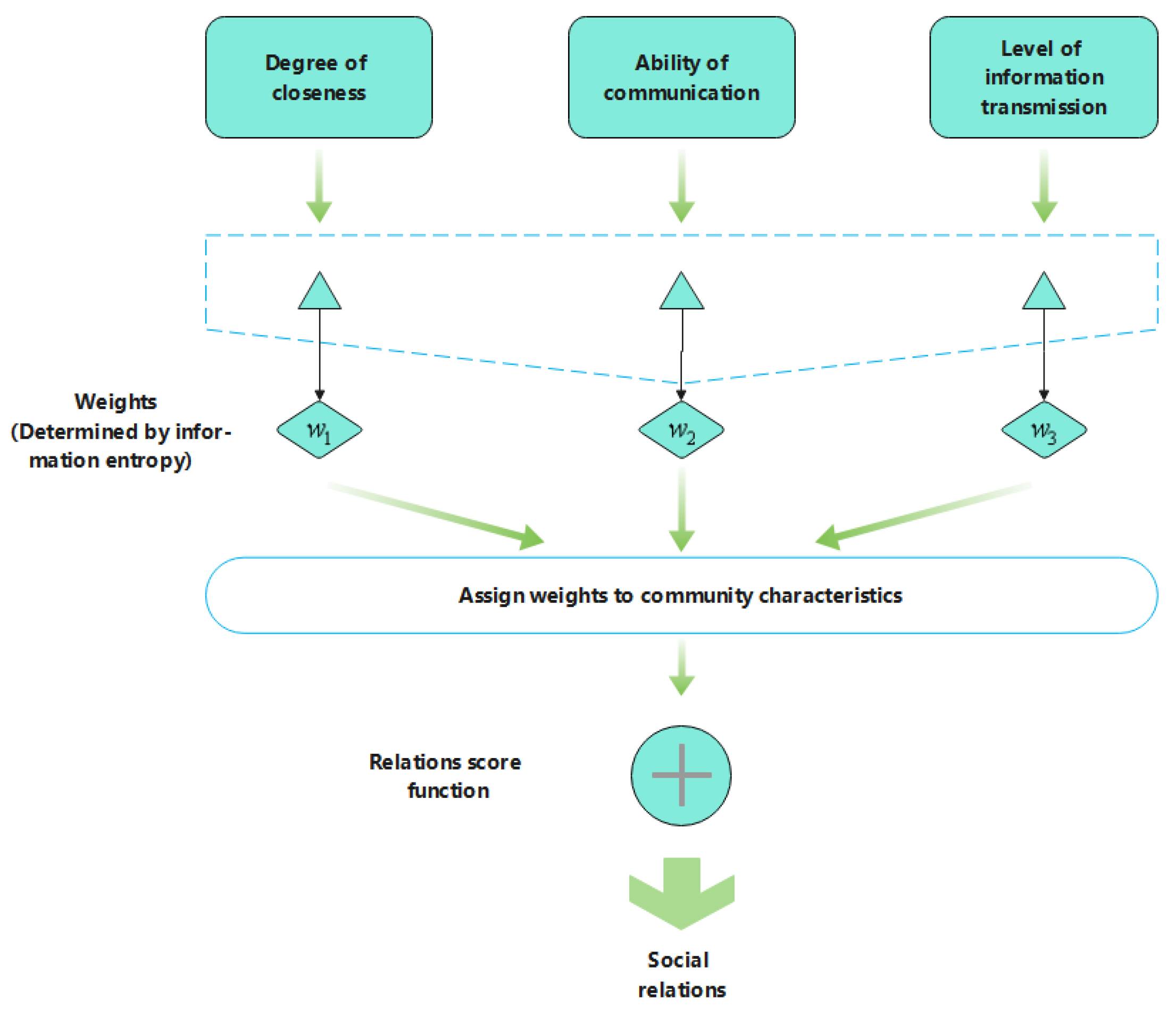
- Propose the concept of edge node based on the characteristics of information transfer, comprehensively consider the three decision feature attributes that affect the node relationship and the method of quantifying the social relationship between nodes so that the social relationship between nodes can be fully and intuitively measured.
- Introduce information entropy and joint entropy theory. The weight assigned to each attribute is adjusted in time according to the dynamic changes of the node relationship, which is convenient to find the best forwarding node. It can improve the efficiency of information transmission and reduce malicious forwarding.
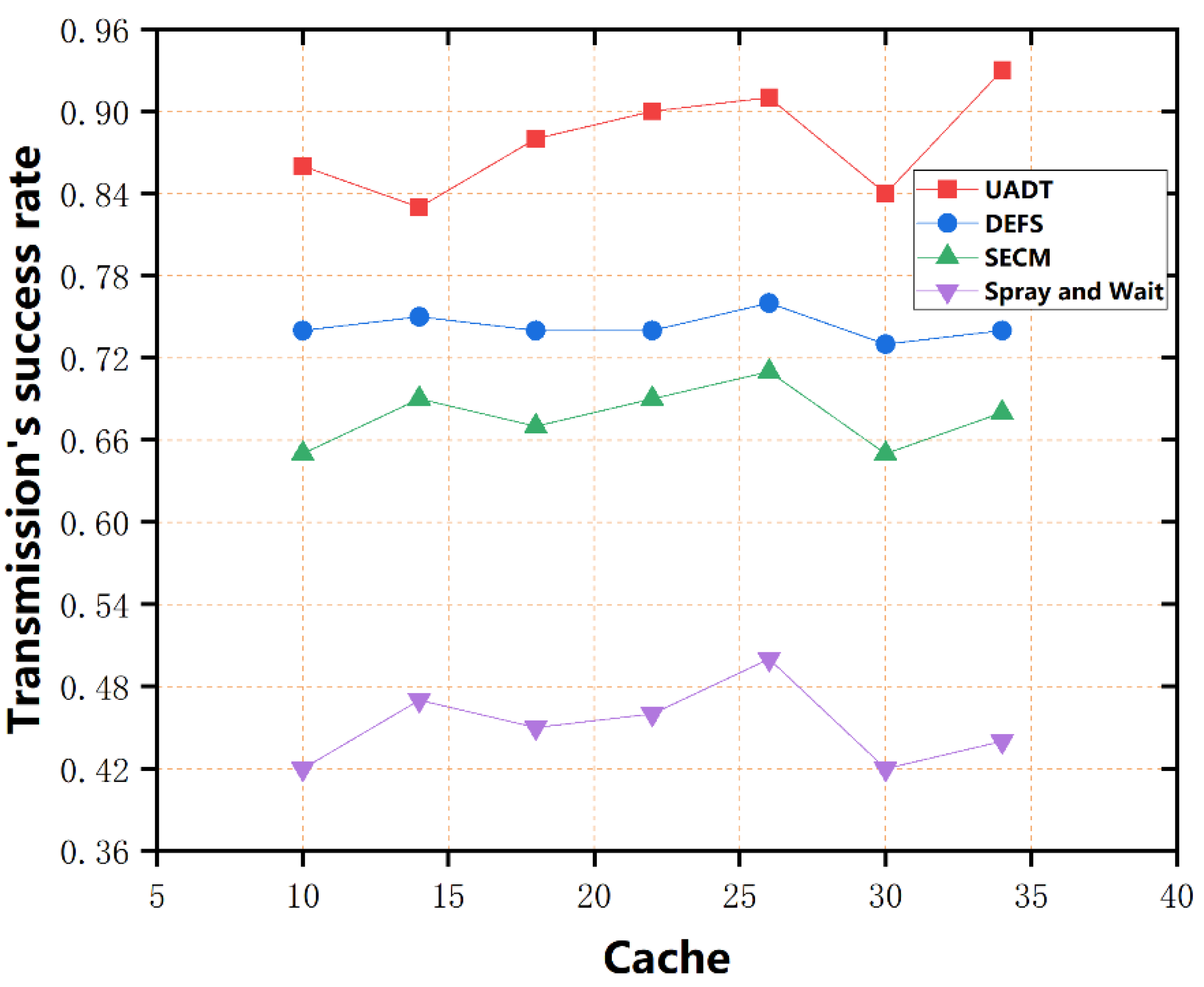
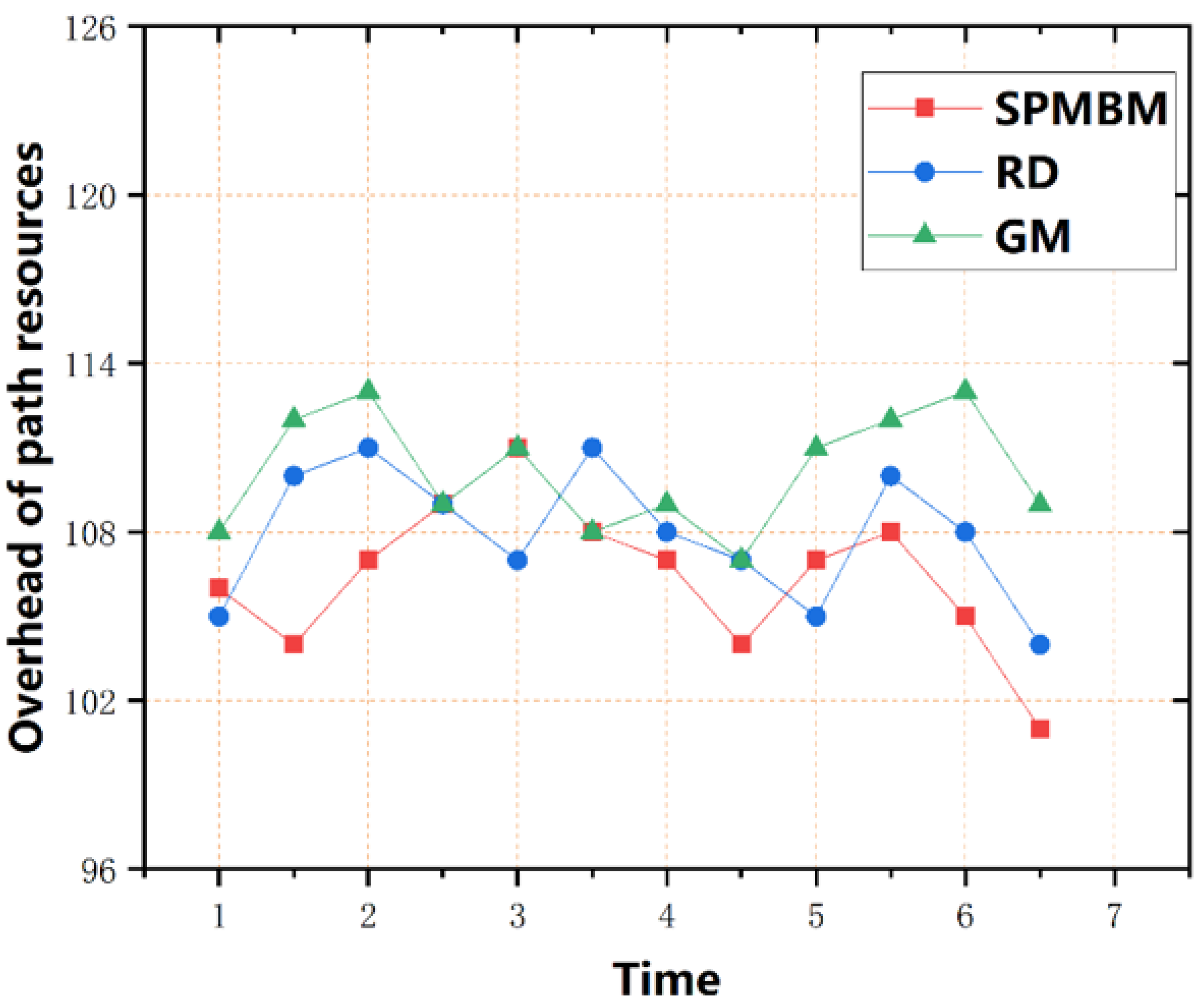
- This paper compares the UADT algorithm with the spray and wait algorithm, the DEFS (direction entropy-based forwarding scheme) [36] algorithm, and the SECM (status estimation and cache management) [37] algorithm to analyze each algorithm’s performance through simulation experiments. The results show that the algorithm proposed in this study has good performance in improving data transmission rate, reducing delay and overhead.
2. Related Work
3. Routing Algorithm Design
3.1. Node Community Decision Feature Design
3.2. Node Relationship Analysis
4. Simulation
- Spray and wait [39]: In the spray phase, the algorithm forwards the information to neighboring nodes by flooding. If no available node is found, the information is directly copied to the target node in the Wait phase.
- DEFS [36]: The algorithm calculates the node’s primary direction and direction entropy to capture the certainty of the node’s direction. The source node selects a node with a slight direction entropy as a relay node for message forwarding, which balances network traffic and transmission delay well.
- SECM [37]: The algorithm can analyze the relationship between the source node and its neighbor nodes and compare the forwarding probabilities of different neighbor nodes, thereby adjusting the cache information between nodes. The source node selects a neighbor node with a higher probability and uses node coordination to transfer information, which effectively utilizes cache space.
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Stojkoska, B.; Trivodaliev, K.V. A review of Internet of Things for smart home: Challenges and solutions. J. Clean. Prod. 2017, 140 Pt 3, 1454–1464. [Google Scholar] [CrossRef]
- Rashid, Z.; Melià-Seguí, J.; Pous, R.; Peig, E. Using Augmented Reality and Internet of Things to improve accessibility of people with motor disabilities in the context of Smart Cities. Futur. Gener. Comput. Syst. 2017, 76, 248–261. [Google Scholar] [CrossRef] [Green Version]
- China Economic Information Service. Available online: http://ceis.xinhua08.com/a/20200807/1950209.shtml (accessed on 5 May 2021).
- Cauteruccio, F.; Cinelli, L.; Fortino, G.; Savaglio, C.; Terracina, G.; Ursino, D.; Virgili, L. An approach to compute the scope of a social object in a Multi-IoT scenario. Pervasive Mob. Comput. 2020, 67, 101223. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Liu, A.; Guo, M. Joint Optimization of Lifetime and Transport Delay under Reliability Constraint Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2015, 27, 225–236. [Google Scholar] [CrossRef] [Green Version]
- Rasneet Kaur, M.L. Wireless Sensor Networks: A Survey 1. IEEE Commun. Mag. 2002, 38, 393–422. [Google Scholar]
- Akyildiz, I.F.; Wang, X.; Wang, W. Wireless mesh networks: A survey. Comput. Netw. 2005, 47, 445–487. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z.; Zhao, M. Information cache management and data transmission algorithm in opportunistic social networks. Wirel. Netw. 2019, 25, 2977–2988. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Yang, L.T.; Liu, A.; Guo, M. LSCD: A Low-Storage Clone Detection Protocol for Cyber-Physical Systems. IEEE Trans. Comput. Des. Integr. Circuits Syst. 2016, 35, 712–723. [Google Scholar] [CrossRef] [Green Version]
- Dong, M.; Ota, K.; Li, H.; Du, S.; Zhu, H.; Guo, S. RENDEZVOUS: Towards fast event detecting in wireless sensor and actor networks. Computing 2014, 96, 995–1010. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z.; Zhao, M. Community recombination and duplication node traverse algorithm in opportunistic social networks. Peer Peer Netw. Appl. 2020, 13, 940–947. [Google Scholar] [CrossRef]
- Wu, J.; Yu, G.; Guan, P. Interest Characteristic Probability Predicted Method in Social Opportunistic Networks. IEEE Access 2019, 7, 59002–59012. [Google Scholar] [CrossRef]
- Qi, L.; Zhang, X.; Dou, W.; Hu, C.; Yang, C.; Chen, J. A two-stage locality-sensitive hashing based approach for privacy-preserving mobile service recommendation in cross-platform edge environment. Futur. Gener. Comput. Syst. 2018, 88, 636–643. [Google Scholar] [CrossRef]
- Zhang, X.; Jang-Jaccard, J.; Qi, L.; Bhuiyan, Z.A.; Liu, C. Privacy Issues in Big Data Mining Infrastructure, Platforms, and Applications. Secur. Commun. Netw. 2018, 2018, 1–3. [Google Scholar] [CrossRef] [Green Version]
- Yang, W.; Wu, J.; Luo, J. Effective Data Transmission and Control Based on Social Communication in Social Opportunistic Complex Networks. Complexity 2020, 2020, 1–20. [Google Scholar] [CrossRef]
- Wang, S.; Zhang, Y.; Wang, H.; Huang, Z.; Wang, X.; Jiang, T. Large Scale Measurement and Analytics on Social Groups of Device-to-Device Sharing in Mobile Social Networks. Mob. Netw. Appl. 2017, 23, 203–215. [Google Scholar] [CrossRef]
- Wang, Y.; Wu, J.; Xiao, M. Hierarchical Cooperative Caching in Mobile Opportunistic Social Networks. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014. [Google Scholar]
- Guo, H.; Wang, X.W.; Huang, M.; Jiang, D.D. Adaptive Epidemic Routing Algorithm Based on Multi Queue in DTN. J. Chin. Comput. Syst. 2012, 33, 829–832. [Google Scholar]
- Xiao, Y.; Wu, J. Data Transmission and Management Based on Node Communication in Opportunistic Social Networks. Symmetry 2020, 12, 1288. [Google Scholar] [CrossRef]
- Xu, Y.; Chen, Z.G.; Wu, J.; Yu, G. MNSRQ: Mobile node social relationship quantification algorithm for data transmission in Internet of things. IET Commun. 2021, 15, 748–761. [Google Scholar] [CrossRef]
- Dou, W.; Tang, W.; Li, S.; Yu, S.; Choo, K.-K.R. A heuristic line piloting method to disclose malicious taxicab driver’s privacy over GPS big data. Inf. Sci. 2019, 483, 247–261. [Google Scholar] [CrossRef]
- Yan, Y.; Chen, Z.; Wu, J.; Wang, L.; Liu, K.; Wu, Y. Effective Data Transmission Strategy Based on Node Socialization in Opportunistic Social Networks. IEEE Access 2019, 7, 22144–22160. [Google Scholar] [CrossRef]
- Li, X.J. Node-Oriented Secure Data Transmission Algorithm Based on IoT System in Social Networks. IEEE Commun. Lett. 2020, 24, 2898–2902. [Google Scholar] [CrossRef]
- Yu, G.; Wu, J. Content caching based on mobility prediction and joint user Prefetch in Mobile edge networks. Peer Peer Netw. Appl. 2020, 13, 1839–1852. [Google Scholar] [CrossRef]
- Bulut, E.; Szymanski, B.K. Exploiting Friendship Relations for Efficient Routing in Mobile Social Networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 2254–2265. [Google Scholar] [CrossRef]
- Wong, K.; Chang, Y.; Jia, X.; Wong, K.H.; Hui, W.Y. Performance Evaluation of Social Relation Opportunistic Routing in Dynamic Social Networks. In Proceedings of the 2015 International Conference on Computing, Networking and Communications (ICNC), Garden Grove, CA, USA, 16–19 February 2015; pp. 874–878. [Google Scholar]
- Souza, C.; Mota, E.; Manzoni, P.; Cano, J.C.; Calafate, C.T.; Hernández-Orallo, E.; Tapia, J.H. Friendly-drop: A social-based buffer management algorithm for opportunistic networks. In Proceedings of the 2018 Wireless Days (WD), Dubai, United Arab Emirates, 3–5 April 2018; pp. 172–177. [Google Scholar]
- Ying, Z.; Zhang, C.; Li, F.; Wang, Y. Geo-social: Routing with location and social metrics in mobile opportunistic networks. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 3405–3410. [Google Scholar]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially Connected ad Hoc Networks. 2000. Available online: http://issg.cs.duke.edu/epidemic/epidemic.pdf (accessed on 5 May 2021).
- Guan, P.; Wu, J. Effective Data Communication Based on Social Community in Social Opportunistic Networks. IEEE Access 2019, 7, 12405–12414. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. Internet Things J. IEEE 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Xia, X.; Chen, F.; He, Q.; Grundy, J.C.; Abdelrazek, M.; Jin, H. Cost-Effective App Data Distribution in Edge Computing. IEEE Trans. Parallel Distrib. Syst. 2020, 32, 31–44. [Google Scholar] [CrossRef]
- Zhang, M.; Zhang, C.; Pai, V.S.; Peterson, L.L.; Wang, R.Y. Planetseer: Internet path failure monitoring and characterization in wide-area services. OSDI 2004, 4, 12. [Google Scholar]
- Wu, J.; Qu, J.; Yu, G. Behavior prediction based on interest characteristic and user communication in opportunistic social networks. Peer Peer Netw. Appl. 2021, 2021, 1006–1018. [Google Scholar] [CrossRef]
- Wu, X.; Chang, L.; Luo, J.; Wu, J. Efficient Edge Cache Collaboration Transmission Strategy of Opportunistic Social Network in Trusted Community. IEEE Access 2021, 9, 51772–51783. [Google Scholar] [CrossRef]
- Jeon, M.S.; Kim, S.K.; Yoon, J.H.; Lee, J.; Yang, S.B. A Direction Entropy-Based Forwarding Schemeinan Opportunistic Network. J. Comput. Sci. Eng. 2014, 8, 173–179. [Google Scholar] [CrossRef]
- Wu, J.; Chen, Z.; Zhao, M. SECM status estimation. J. Supercomput. 2019, 75, 2629–2647. [Google Scholar] [CrossRef]
- Lenando, H.; Alrfaay, M. EpSoc: Social-Based Epidemic-Based Routing Protocol in Opportunistic Mobile Social Network. Mob. Inf. Syst. 2018, 2018, 6462826. [Google Scholar] [CrossRef] [Green Version]
- Wu, L.; Cao, S.; Chen, Y.; Cui, J.; Chang, Y. An adaptive multiple spray-and-wait routing algorithm based on social circles in delay tolerant networks. Comput. Netw. 2021, 189, 107901. [Google Scholar] [CrossRef]
- Wang, G.; Zhang, H.; Pan, D.; Tao, J. A routing scheme based on Spray-and-Wait and Connecting-Capability of Node. In Proceedings of the 2016 International Conference on Progress in Informatics and Computing (PIC), Shanghai, China, 23–25 December 2016; pp. 577–580. [Google Scholar]
- Srinidhi, N.N.; Sagar, C.S.; Shreyas, J.; SM, D.K. An improved PRoPHET—Random forest based optimized multi-copy routing for opportunistic IoT networks. Internet Things 2020, 11, 100203. [Google Scholar] [CrossRef]
- Duan, Z.-T.; Yang, Y.; Fan, N.; Zhu, Y.-S. Opportunistic forwarding algorithm based on connection time in probabilistic routing. Microelectron. Comput. 2018, 35, 50–54. [Google Scholar]
- Sharma, D.K.; Agrawal, S.; Bansal, V. Ameliorations in MaxProp Routing Protocol in Delay-tolerant Networks. In Proceedings of the 2018 Fourteenth International Conference on Information Processing (ICINPRO), Bengaluru, India, 21–23 December 2018. [Google Scholar]
- Das, M.; Sarkar, S.; Iqbal, S.M.A. TTL based MaxProp routing protocol. In Proceedings of the 2016 19th International Conference on Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 18–20 December 2016; pp. 7–12. [Google Scholar]
- Yu, G.; Chen, Z.G.; Wu, J.; Wu, J. Quantitative social relations based on trust routing algorithm in opportunistic socialnetwork. Eurasip J. Wirel. Commun. Netw. 2019, 2019, 83. [Google Scholar] [CrossRef]
- Daly, E.M.; Haahr, M. Social Network Analysis for Information Flow in Disconnected Delay-Tolerant MANETs. IEEE Trans. Mob. Comput. 2009, 8, 606–621. [Google Scholar] [CrossRef]
- Yi, J.; Yin, M.; Zhang, Y.; Zhao, X. A novel recommender algorithm using information entropy and secondary clustering. In Proceedings of the 2017 2nd IEEE International Conference on Computational Intelligence and Applications (ICCIA), Beijing, China, 8–11 September 2017; pp. 128–132. [Google Scholar]
- Luo, J.; Wu, J.; Wu, Y. Advanced Data Delivery Strategy Based on Multiperceived Community with IoT in Social Complex Networks. Complexity 2020, 2020, 1–15. [Google Scholar] [CrossRef]
- Keranen, A. Opportunistic Network Environment Simulator; Special Assignment Report; Helsinki University of Technology, Department of Communications and Networking: Espoo, Finland, 2008; Available online: https://scholar.google.com.tw/scholar?hl=en&as_sdt=0%2C5&q=Opportunistic+Network+Environment+Simulator%3B+Special+Assignment+Report%3B+Helsinki+University+of+Technology%2C+Department+of+Communications+and+Networking%3A+Espoo%2C+Finland%2C+2008.&btnG= (accessed on 5 May 2021).








| Parameter | Value |
|---|---|
| Simulation time | 1–6.5 h |
| Simulation area | 2500 m × 3200 m |
| Cache | 10–34 M |
| TTL | 6 h |
| Data packet transmission time | 27–40 s |
| Maximum transmission radius | 12 m |
| Message size | 255 KBps |
| Interval time between message generation | 28 s |
| Node initial energy | 100 J |
| The packet loss threshold | 13% |
| Pedestrian speed | 0.8–4.8 m/s |
| Frequency range | 25–35 Hz |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, Y.; Chang, L.; Luo, J.; Wu, J. Routing Algorithm Based on User Adaptive Data Transmission Scheme in Opportunistic Social Networks. Electronics 2021, 10, 1138. https://doi.org/10.3390/electronics10101138
Lu Y, Chang L, Luo J, Wu J. Routing Algorithm Based on User Adaptive Data Transmission Scheme in Opportunistic Social Networks. Electronics. 2021; 10(10):1138. https://doi.org/10.3390/electronics10101138
Chicago/Turabian StyleLu, Yu, Liu Chang, Jingwen Luo, and Jia Wu. 2021. "Routing Algorithm Based on User Adaptive Data Transmission Scheme in Opportunistic Social Networks" Electronics 10, no. 10: 1138. https://doi.org/10.3390/electronics10101138
APA StyleLu, Y., Chang, L., Luo, J., & Wu, J. (2021). Routing Algorithm Based on User Adaptive Data Transmission Scheme in Opportunistic Social Networks. Electronics, 10(10), 1138. https://doi.org/10.3390/electronics10101138







