Magniber v2 Ransomware Decryption: Exploiting the Vulnerability of a Self-Developed Pseudo Random Number Generator
Abstract
1. Introduction
1.1. Background
1.2. Our Contributions
- The existing decryption technique for Magniber-infected files decrypts only version 1, in which the main parameters are hard-coded key. Files infected by Magniber v2, which uses hybrid encryption, cannot be decrypted. We present the first successful decryption of Magniber v2-infected files. Our proposed method is experimentally verified in a demonstration.
- The existing ransomware generates the encryption keys for file encryption by a random number generator (RNG). A typical RNG determines the security strength from seeds generated by collecting various noise sources. Well-known RNGs such as Hash DRBG and CTR DRBG, are deterministic algorithms that derive pseudo random numbers by inputting seeds. However, Magniber v2’s RNG is developed by an attacker and its security is not guaranteed. We reveal the inherent vulnerabilities in Magniber v2’s RNG and exploit them to recover the key parameters such as encryption key and initialization vector (IV). The vulnerability is derived from the seed input and structure of the RNG.
- Once the encryption key has been recovered, its correctness must be verified. Valid encryption key verification can apply a fixed known value, commonly called an authenticator. However, an authentication based verification is difficult when the ransomware encrypts various files. To solve this problem, we apply padding verification and statistical randomness tests. Padding verification is computationally cheaper than randomness tests, but gives a high false-positive rate. To compensate this deficiency, we perform additional randomness tests on the objects passed by the padding verification. By reducing the number of randomness tests, we improve the efficiency of the encryption key verification.
2. Related Work
3. Analysis of Magniber v2
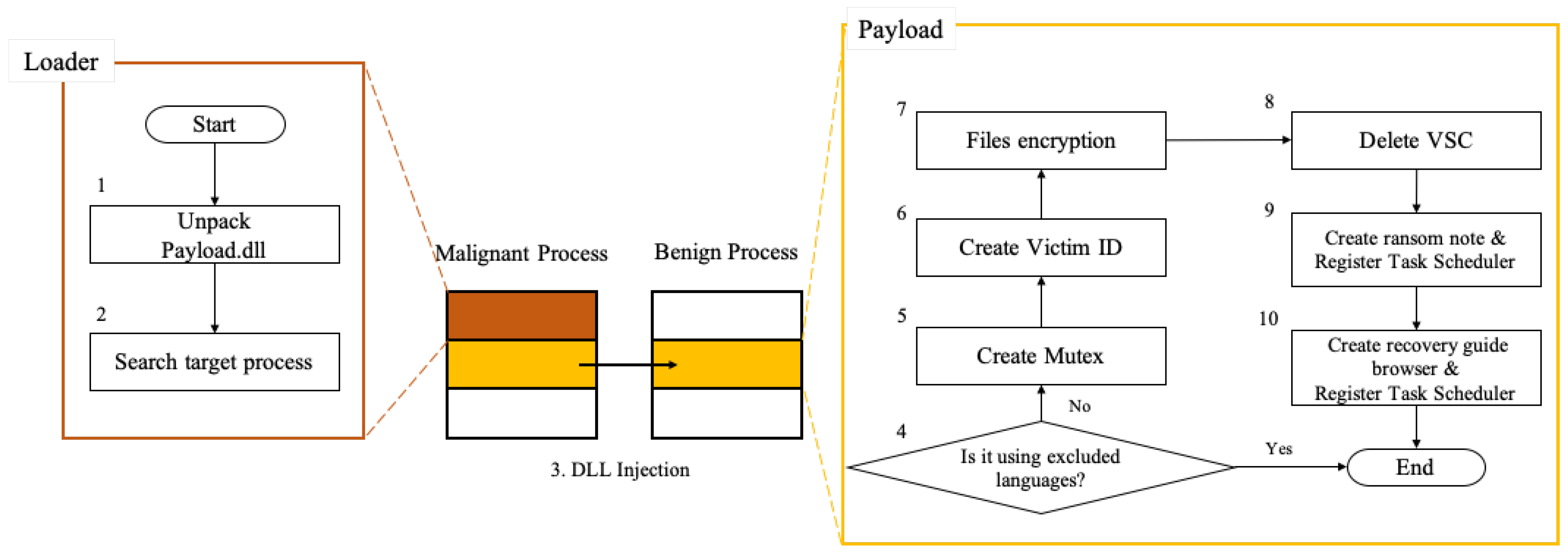
3.1. Malicious Behavior Process
- Loader.dll
- MD5: 72FCE87A976667A8C09ED844564ADC75
- SHA1: D3E17F5ECA5FB23B272549692D84CC449CF71527
- SHA256: 6E57159209611F2531104449F4BB86A7621FB9FBC2E90ADD2ECDFBE293AA9DFC
- Payload.dll
- MD5: 19599CAD1BBCA18AC6473E64710443B7
- SHA1: F9E2111E2903838BB9F4EFB557F75745D028BC3E
- SHA256: FB6C80AE783C1881487F2376F5CACE7532C5EADFC170B39E06E17492652581C2
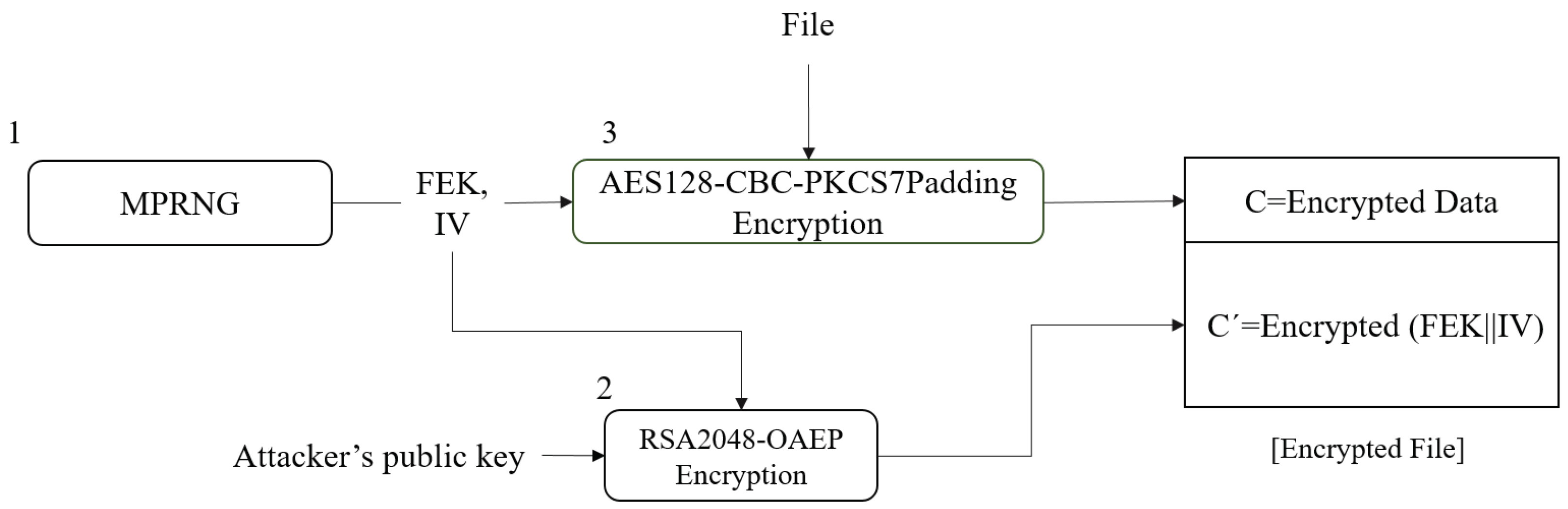
3.2. Encryption Process
3.2.1. and Generation
3.2.2. and Encryption
3.2.3. File Encryption
4. Method for Finding the Encryption Keys of Magniber v2
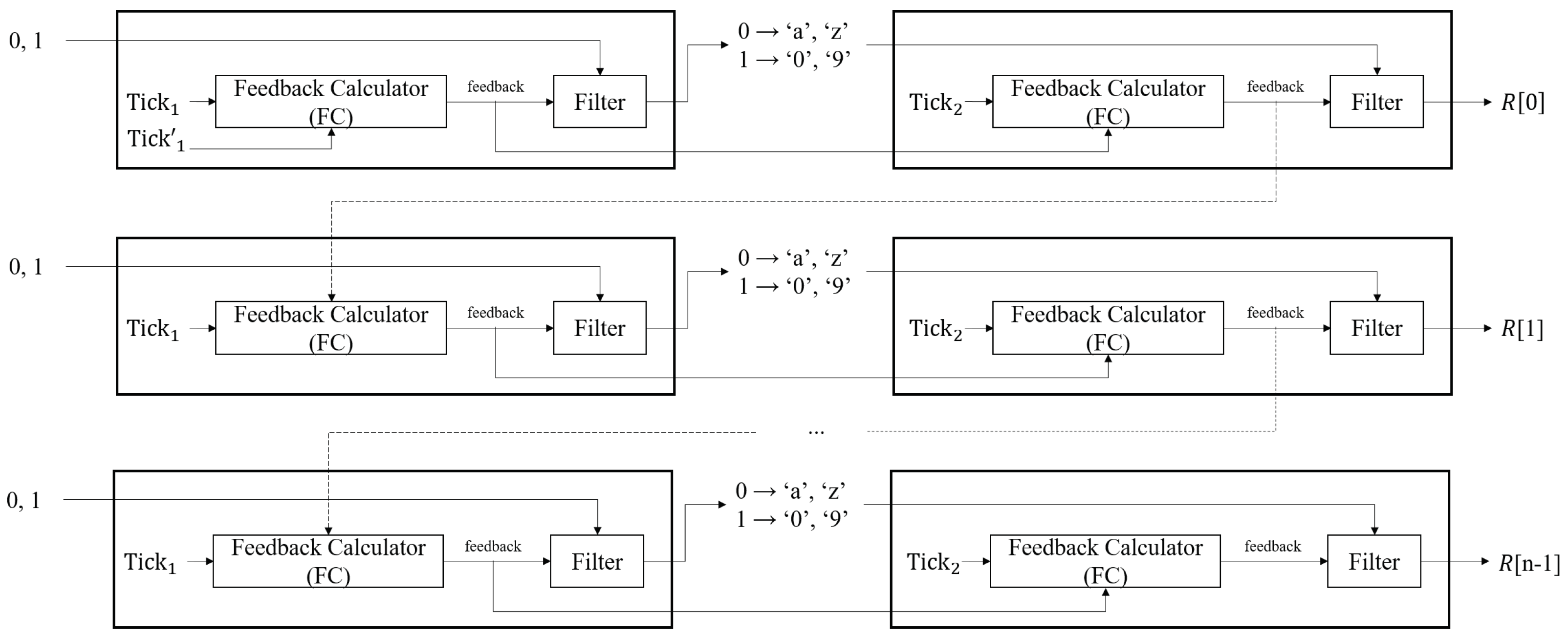
4.1. Magniber PRNG
| Algorithm 1 RNG of Magniber v2 |
|
| Algorithm 2 PRNG of Magniber v2 |
|
4.2. Generating File Encryption Key Candidates
| Algorithm 3 Candidates Generation Algorithm |
|
5. Recovery of Encryption Keys and Decryption of Files Encrypted by Magniber v2
5.1. Verifying the Generated File Encryption Key Candidates
5.2. File Encryption Key Recovery
| Algorithm 4 Recovery Algorithm |
|
5.3. Experimental Result
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Norsk Hydro Ransomware Incident Losses Reach $40 Million after One Week. Available online: https://www.zdnet.com/article/norsk-hydro-ransomware-incident-losses-reach-40-million-after-one-week/ (accessed on 17 December 2020).
- Georgia County Pays a Whopping $400,000 to Get Rid of a Ransomware Infection. Available online: https://www.zdnet.com/article/georgia-county-pays-a-whopping-400000-to-get-rid-of-a-ransomware-infection/ (accessed on 17 December 2020).
- BBC News, ISS World Hack Leaves Thousands of Employees Offline. Available online: https://www.bbc.com/news/technology-51572575 (accessed on 17 December 2020).
- Maginber, The worst Ransomware in First Quarter. Available online: https://www.ahnlab.com/kr/site/securityinfo/secunews/secuNewsView.do?menu_dist=2&seq=27370 (accessed on 17 December 2020).
- Magniber Ransomware: Exclusively for South Koreans. Available online: https://blog.malwarebytes.com/threat-analysis/2017/10/magniber-ransomware-exclusively-for-south-koreans/ (accessed on 17 December 2020).
- Magniber Decryptor Release. Available online: https://www.ahnlab.com/kr/site/securityinfo/secunews/secuNewsView.do?seq=27312 (accessed on 17 December 2020).
- Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Barker, E.; Leigh, S.; Levenson, M.; Vangel, M.; Banks, D.; Heckert, A.; et al. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; SP 800-22; NIST: Gaithersburg, MD, USA, 2010.
- Kanwal, M.; Thakur, S. An app based on static analysis for android ransomware. In Proceedings of the 2017 International Conference on Computing, Communication and Automation (ICCCA), Greater Noida, India, 5–6 May 2017; pp. 813–818. [Google Scholar]
- Andronio, N.; Zanero, S.; Maggi, F. Heldroid: Dissecting and detecting mobile ransomware. In International Symposium on Recent Advances in Intrusion Detection; Springer: Berlin, Germany, 2015; pp. 382–404. [Google Scholar]
- Moser, A.; Kruegel, C.; Kirda, E. Limits of static analysis for malware detection. In Proceedings of the Twenty-Third Annual Computer Security Applications Conference (ACSAC 2007), Miami Beach, FL, USA, 10–14 December 2007; pp. 421–430. [Google Scholar]
- Continella, A.; Guagnelli, A.; Zingaro, G.; De Pasquale, G.; Barenghi, A.; Zanero, S.; Maggi, F. ShieldFS: A self-healing, ransomwareaware filesystem. In Proceedings of the 32nd Annual Conference on Computer Security Applications, Los Angeles, CA, USA, 5–9 December 2016; pp. 336–347. [Google Scholar]
- Mehnaz, S.; Mudgerikar, A.; Bertino, E. Rwguard: A real-time detection system against cryptographic ransomware. In International Symposium on Research in Attacks, Intrusions, and Defenses; Springer: Berlin, Germany, 2018; pp. 114–136. [Google Scholar]
- Jung, S.; Won, Y. Ransomware detection method based on context-aware entropy analysis. Soft Comput. 2018, 22, 6731–6740. [Google Scholar] [CrossRef]
- Hampton, N.; Baig, Z.; Zeadally, S. Ransomware behavioural analysis on windows platforms. J. Inf. Secur. Appl. 2018, 40, 44–51. [Google Scholar] [CrossRef]
- Kharaz, A.; Arshad, S.; Mulliner, C.; Robertson, W.; Kirda, E. {UNVEIL}: A large-scale, automated approach to detecting ransomware. In Proceedings of the 25th {USENIX} Security Symposium ({USENIX} Security 16), Austin, TX, USA, 10–12 August 2016; pp. 757–772. [Google Scholar]
- Hasan, M.M.; Rahman, M.M. RansHunt: A support vector machines based ransomware analysis framework with integrated feature set. In Proceedings of the 2017 20th International Conference of Computer and Information Technology (ICCIT), Dhaka, Bangladesh, 22–24 December 2017; pp. 1–7. [Google Scholar]
- Lee, K.; Lee, S.Y.; Yim, K. Machine learning based file entropy analysis for ransomware detection in backup systems. IEEE Access 2019, 7, 110205–110215. [Google Scholar] [CrossRef]
- Almashhadani, A.O.; Kaiiali, M.; Sezer, S.; O’Kane, P. A multi-classifier network-based crypto ransomware detection system: A case study of Locky ransomware. IEEE Access 2019, 7, 47053–47067. [Google Scholar] [CrossRef]
- Kolodenker, E.; Koch, W.; Stringhini, G.; Egele, M. Paybreak: Defense against cryptographic ransomware. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, UAE, 2–6 April 2017; pp. 599–611. [Google Scholar]
- Kim, H.; Yoo, D.; Kang, J.S.; Yeom, Y. Dynamic ransomware protection using deterministic random bit generator. In Proceedings of the 2017 IEEE Conference on Application, Information and Network Security (AINS), Miri, Malaysia, 13–14 November 2017; pp. 64–68. [Google Scholar]
- García, H.M.; Us, L.C. Hidden Tear: Análisis del primer Ransomware Open Source. Av. Perspect. Innov. Investig. Vincul. Mérida Yucatán M. 2015, 1, 31–54. [Google Scholar]
- Destroying The Encryption of Hidden Tear Ransomware. Available online: https://utkusen.com/blog/destroying-the-encryption-of-hidden-tear-ransomware.html (accessed on 17 December 2020).
- Lee, S.; Kim, S.; Kim, G.; Kim, D.; Park, Y.; Kim, J. A Study on the Decryption of Donut Ransomware through Memory Analysis. J. Digit. Forensics 2019, 13, 13–22. [Google Scholar]
- Lee, S.; Youn, B.; Kim, S.; Kim, G.; Lee, Y.; Kim, D.; Park, H.; Kim, J. A Study on Encryption Process and Decryption of Ransomware in 2019. J. Korea Inst. Inf. Secur. Cryptol. 2019, 29, 1339–1350. [Google Scholar]
- Cyber Attack Hits 200,000 in at Least 150 Countries: Europol. Available online: https://www.reuters.com/article/us-cyber-attack-europol/cyber-attack-hits-200000-in-at-least-150-countries-europol-idUSKCN18A0FX (accessed on 17 December 2020).
- Akbanov, M.; Vassilakis, V.G.; Logothetis, M.D. WannaCry ransomware: Analysis of infection, persistence, recovery prevention and propagation mechanisms. J. Telecommun. Inf. Technol. 2019. [Google Scholar] [CrossRef]
- Github, Wanakiwi. Available online: https://github.com/gentilkiwi/wanakiwi (accessed on 17 December 2020).
- Boczan, T. The Evolution of GandCrab Ransomware. Available online: https://www.youtube.com/watch?v=b57VV9BC6tE&t=1863s (accessed on 17 December 2020).
- Bitdefender, Europol, Romanian Police, DIICOT team up for GandCrab Decryption Tool. Available online: https://labs.bitdefender.com/2018/02/bitdefender-europol-romanian-police-diicot-team-up-for-gandcrab-removal-tool/ (accessed on 17 December 2020).
- Bleeping Computer, FBI Releases Master Decryption Keys for GandCrab Ransomware. Available online: https://www.bleepingcomputer.com/news/security/fbi-releases-master-decryption-keys-for-gandcrab-ransomware/ (accessed on 17 December 2020).
- No More Ransom Project. Available online: https://www.nomoreransom.org (accessed on 17 December 2020).
- Hybrid Analysis. Available online: https://www.hybrid-analysis.com (accessed on 17 December 2020).


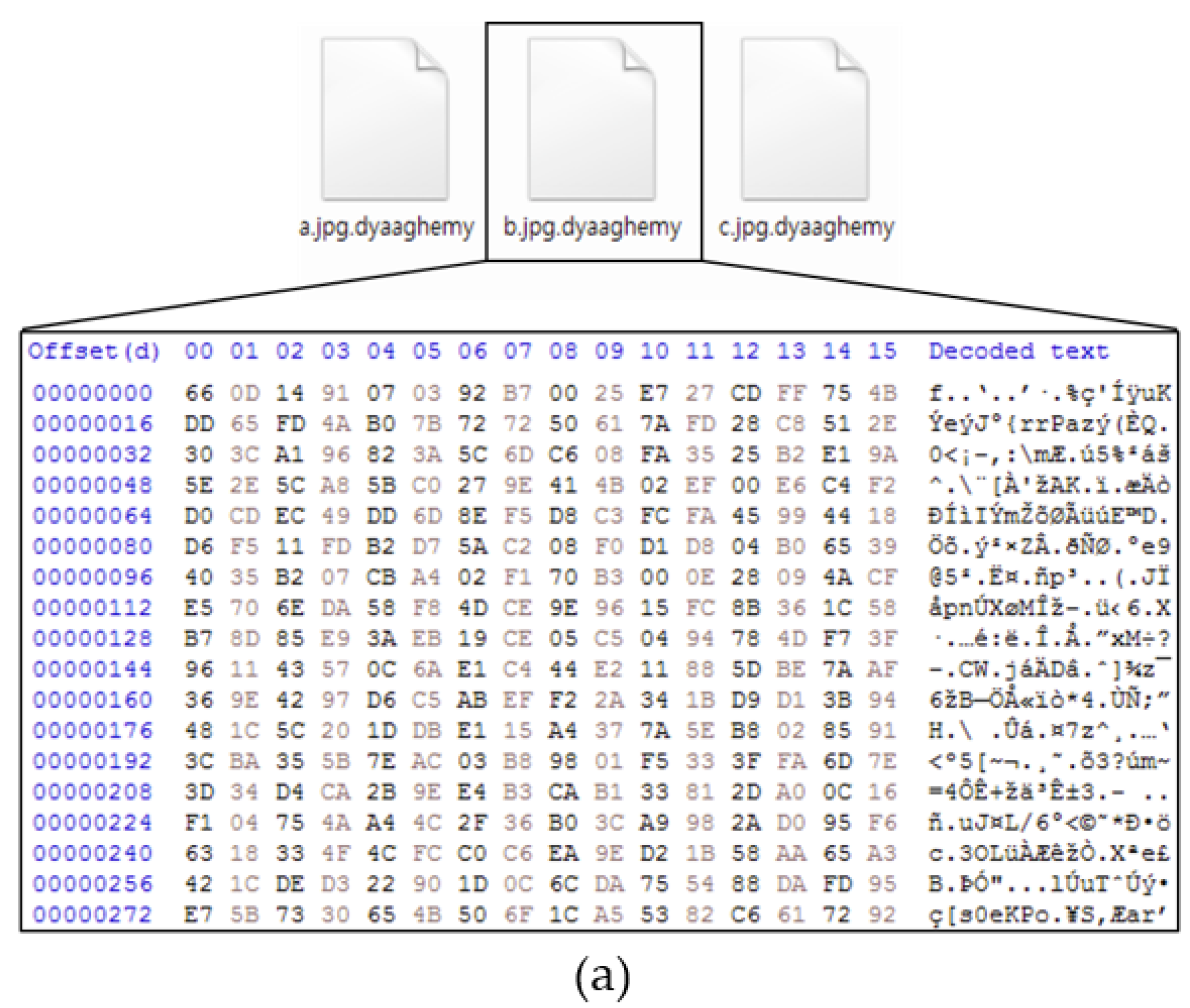
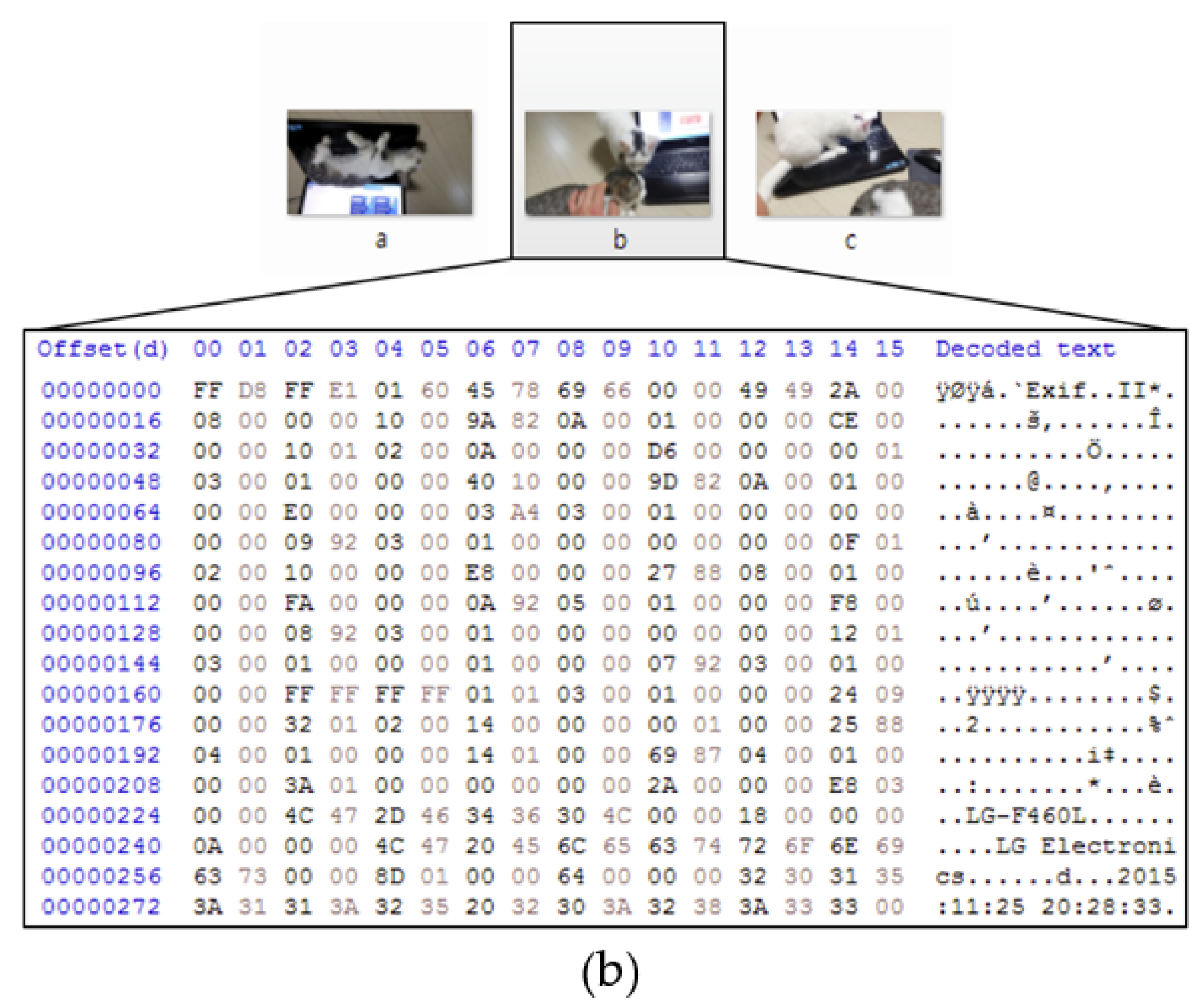
| Ransomware | Magniber v1 | Magniber v2 |
|---|---|---|
| Crypto system | AES128-CBC-PKCS7Padding | AES128-CBC-PKCS7Padding RSA2048-OAEP |
| Key generation | 1. Receive from C&C server 2. Fixed in code | Attacker’s PRNG |
| Key management | None | Encrypted AES key with RSA stored in end of file |
| Key destruction | Yes | Yes |
| Decryption tool | Yes | No |
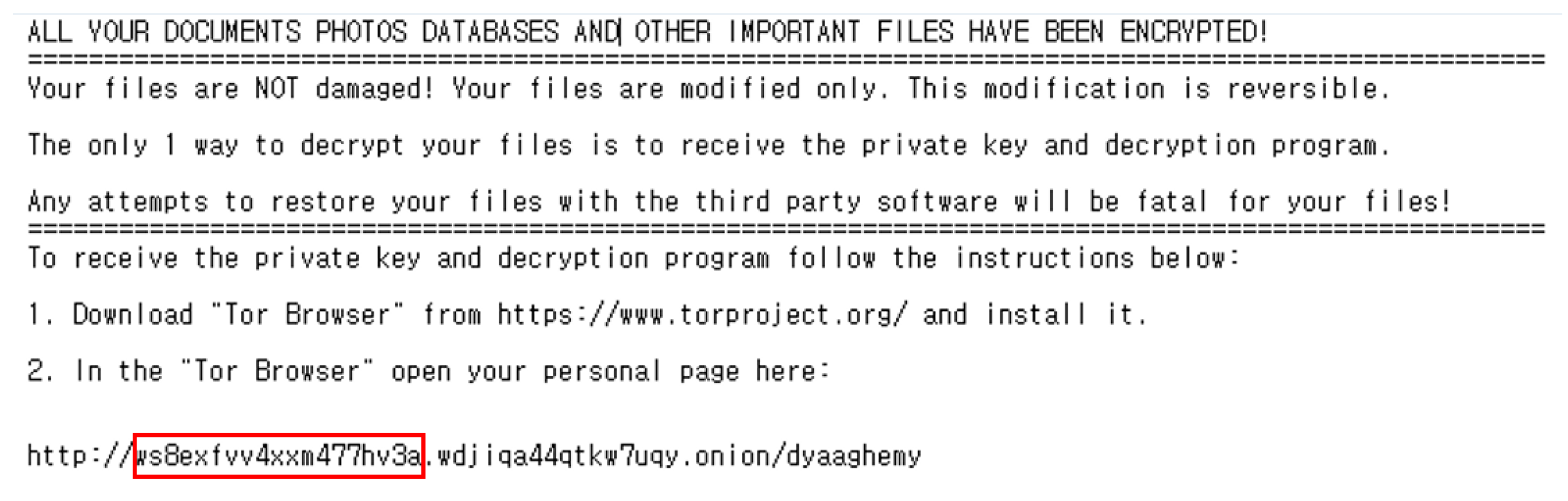
| Known extensions | kympzmzw, owxpzylj, prueitfik, rwighmoz, bnxzoucsx, tzdbkjry, iuoqetgb, pgvuuryti, zpnjelt, gnhnzhu, hssjfbd, ldolfoxwu, zskgavp, gwinpyizt, hxzrvhh, cmjedin, dzvtwtqz, pxynindl, sqzprtt, etc. | fprgbk, ihsdj, kgpvwnr, vbdrj, skvtb, vpgvlkb, dlenggrl, dxjay, fbuvkngy, xhspythxn, demffue, mftzmxqo, qmdjtc, wmfxdqz, ndpyhss, dyaaghemy, etc. |
| Test List (ms/Test *) | Video | Image | Audio | Document | Compressed | Encrypted | False Positive Rate |
|---|---|---|---|---|---|---|---|
| Frequency (4) | 2 | 8 | 11 | 5 | 5 | 100 | 5.17% |
| Block frequency (2) | 0 | 0 | 0 | 0 | 3 | 98 | 0.83% |
| Runs (4) | 0 | 1 | 1 | 1 | 5 | 97 | 1.83% |
| Longest run (5) | 33 | 0 | 4 | 10 | 31 | 100 | 13% |
| Rank (47) | 8 | 7 | 50 | 33 | 55 | 99 | 25.67% |
| FFT (188) | 4 | 2 | 32 | 12 | 41 | 98 | 15.5% |
| Non overlapping template (1167) | 0 | 0 | 0 | 1 | 4 | 100 | 0.83% |
| Overlapping template (35) | 28 | 8 | 4 | 1 | 24 | 100 | 10.83% |
| Universal (30) | 0 | 0 | 0 | 0 | 8 | 96 | 2% |
| Approximate entropy (124) | 0 | 0 | 0 | 0 | 4 | 100 | 0.67% |
| Serial (343) | 0 | 0 | 0 | 0 | 8 | 97 | 1.83% |
| Linear complexity (1890) | 17 | 10 | 47 | 23 | 56 | 100 | 25.5% |
| Cumulative sums (5) | 1 | 0 | 0 | 1 | 4 | 100 | 1% |
| Random excursions (4) | 0 | 0 | 0 | 0 | 2 | 65 | 6.17% |
| Random excursions variants (4) | 0 | 0 | 1 | 0 | 2 | 62 | 6.83% |
| Number of Tick Changes during FEKi | No Tick Changes during Generation of IVi−1 | Tick Changes during Generation of IVi−1 |
|---|---|---|
| 0 | 0.140 s | 56 min. |
| 1 | 2.465 s | 17 hrs. |
| 2 | 1.5 min. | 29 day. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.; Park, M.; Kim, J. Magniber v2 Ransomware Decryption: Exploiting the Vulnerability of a Self-Developed Pseudo Random Number Generator. Electronics 2021, 10, 16. https://doi.org/10.3390/electronics10010016
Lee S, Park M, Kim J. Magniber v2 Ransomware Decryption: Exploiting the Vulnerability of a Self-Developed Pseudo Random Number Generator. Electronics. 2021; 10(1):16. https://doi.org/10.3390/electronics10010016
Chicago/Turabian StyleLee, Sehoon, Myungseo Park, and Jongsung Kim. 2021. "Magniber v2 Ransomware Decryption: Exploiting the Vulnerability of a Self-Developed Pseudo Random Number Generator" Electronics 10, no. 1: 16. https://doi.org/10.3390/electronics10010016
APA StyleLee, S., Park, M., & Kim, J. (2021). Magniber v2 Ransomware Decryption: Exploiting the Vulnerability of a Self-Developed Pseudo Random Number Generator. Electronics, 10(1), 16. https://doi.org/10.3390/electronics10010016




