Address Obfuscation to Protect against Hardware Trojans in Network-on-Chips
Abstract
:1. Introduction
2. Related Work
3. Threat Model
4. Attack Model
4.1. Hardware Trojan (HT) Design
4.2. Hardware Trojan Trigger Design
4.3. Off-Chip Hardware Trojan Payload Analysis
5. Defense Model
5.1. LUT Obfuscation
5.2. Pseudo-Randomization of the LUT Indices
6. Evaluation
6.1. Experimental Setup
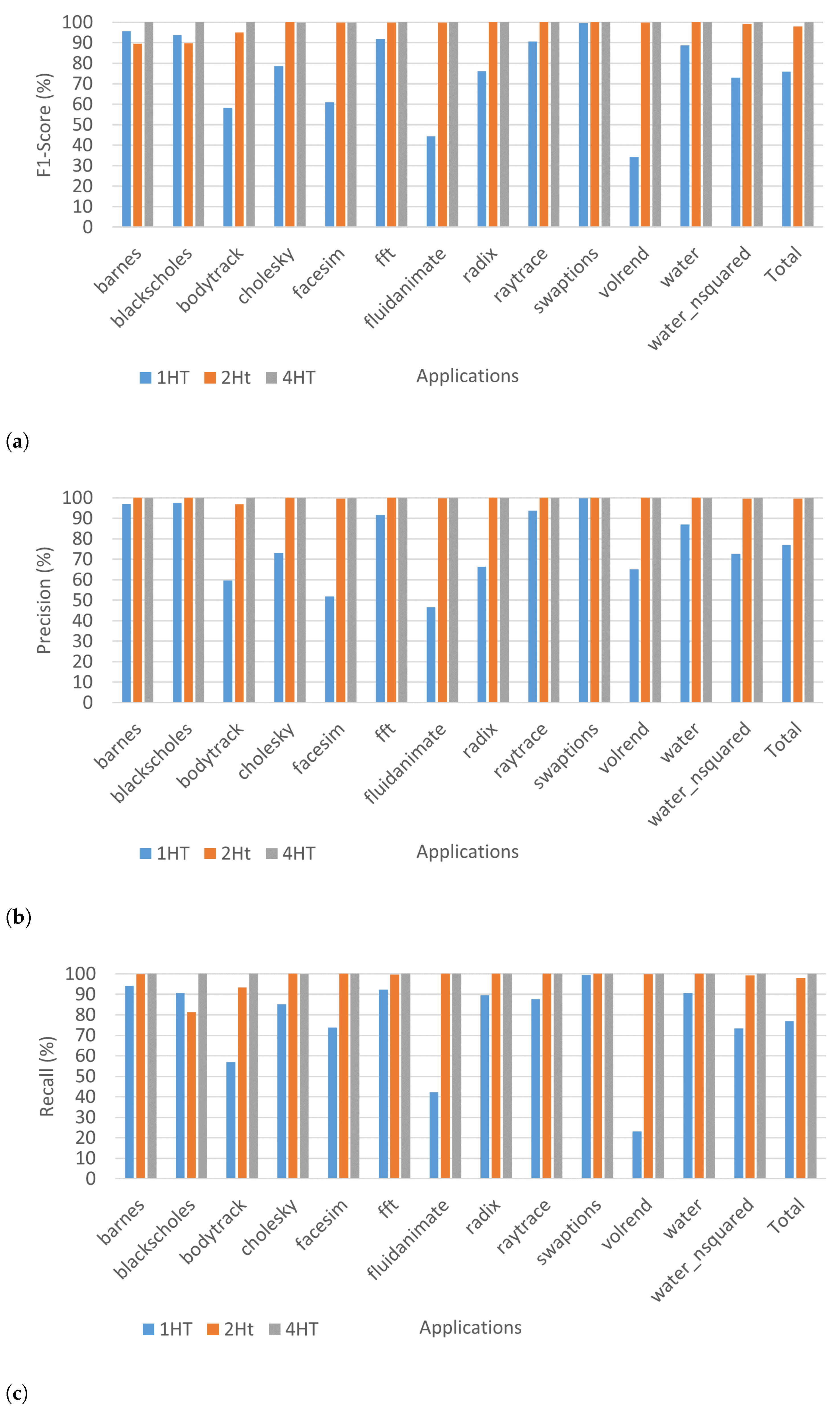
6.2. ML Performance with Proposed LUT Obfuscation
6.3. Routing and HT Overheads
7. Conclusions
Future Work
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Dally, W.J.; Towles, B. Route packets, not wires: On-chip interconnection networks. In Proceedings of the 38th Annual Design Automation Conference, Las Vegas, NV, USA, 22 June 2001. [Google Scholar]
- Xiao, K.; Forte, D.; Jin, Y.; Karri, R.; Bhunia, S.; Tehranipoor, M. Hardware trojans: Lessons learned after one decade of research. ACM Trans. Des. Autom. Electron. Syst. (TODAES) 2016, 22, 1–23. [Google Scholar] [CrossRef]
- Jin, Y.; Kupp, N.; Makris, Y. Experiences in hardware trojan design and implementation. In Proceedings of the IEEE International Workshop on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 27 July 2009. [Google Scholar]
- Chakraborty, R.S.; Narasimhan, S.; Bhunia, S. Hardware trojan: Threats and emerging solutions. In Proceedings of the IEEE International High Level Design Validation and Test Workshop, San Francisco, CA, USA, 4–6 November 2009. [Google Scholar]
- Cruz, J.; Farahmandi, F.; Ahmed, A.; Mishra, P. Hardware trojan detection using atpg and model checking. In Proceedings of the 31st International Conference on VLSI Design and 2018 17th International Conference on Embedded Systems (VLSID), Pune, India, 6–10 January 2018. [Google Scholar]
- Skorobogatov, S. Physical Attacks and Tamper Resistance. In Introduction to Hardware Security and Trust; Springer: New York, NY, USA, 2012. [Google Scholar]
- Dubrova, E.; Näslund, M.; Selander, G. Secure and efficient lbist for feedback shift register-based cryptographic systems. In Proceedings of the 19th IEEE European Test Symposium (ETS), Paderborn, Germany, 26–30 May 2014; pp. 1–6. [Google Scholar]
- Kocher, P.; Jaffe, J.; Jun, B. Differential power analysis. In Advances in Cryptology—CRYPTO’ 99; Wiener, M., Ed.; Springer: Berlin/Heidelberg, Germany, 1999; pp. 388–397. [Google Scholar]
- Manoj Kumar, J.Y.V.; Swain, A.K.; Kumar, S.; Sahoo, S.R.; Mahapatra, K. Run time mitigation of performance degradation hardware trojan attacks in network on chip. In Proceedings of the IEEE Computer Society Annual Symposium on VLSI, Hong Kong, China, 8–11 July 2018; pp. 738–743. [Google Scholar]
- Boraten, T.; Kodi, A.K. Packet security with path sensitization for NoCs. In Proceedings of the Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 14–18 March 2016; pp. 1136–1139. [Google Scholar]
- Raparti, V.Y.; Pasricha, S. Lightweight mitigation of hardware trojan attacks in NoC-based manycore computing. In Proceedings of the 2019 56th ACM/IEEE Design Automation Conference (DAC), Las Vegas, NV, USA, 2–6 June 2019; pp. 1–6. [Google Scholar]
- Manju, R.; Das, A.; Jose, J.; Mishra, P. Sectar: Secure noc using trojan aware routing. In Proceedings of the 2020 14th IEEE/ACM International Symposium on Networks-on-Chip (NOCS), Hamburg, Germany, 24–25 September 2020; pp. 1–8. [Google Scholar]
- Ancajas, D.M.; Chakraborty, K.; Roy, S. Fort-NoCs: Mitigating the threat of a compromised NoC. In Proceedings of the 2014 51st ACM/EDAC/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 1–5 June 2014; pp. 1–6. [Google Scholar]
- Fernandes, R.; Marcon, C.; Cataldo, R.; Silveira, J.; Sigl, G.; Sepúlveda, J. A security aware routing approach for NoC-based MPSoCs. In Proceedings of the Symposium on Integrated Circuits and Systems Design, Belo Horizonte, Brazil, 29 August–3 September 2016. [Google Scholar]
- Indrusiak, L.S.; Harbin, J.; Sepulveda, M.J. Side-channel attack resilience through route randomisation in secure real-time networks-on-chip. In Proceedings of the International Symposium on Reconfigurable Communication-Centric SoC (ReCoSoC), Madrid, Spain, 12–14 July 2017. [Google Scholar]
- Boraten, T.H.; Kodi, A.K. Securing NoCs against timing attacks with non-interference based adaptive routing. In Proceedings of the IEEE/ACM International Symposium on Networks-on-Chip (NOCS), Torino, Italy, 4–5 October 2018. [Google Scholar]
- Shalaby, A.; Tavva, Y.; Carlson, T.E.; Peh, L.-S. Sentry-NoC: A statically-scheduled NoC for secure SoCs. In Proceedings of the 15th IEEE/ACM International Symposium on Networks-on-Chip, Madison, WI, USA, 14–15 October 2021. [Google Scholar]
- Meng, X.; Raj, K.; Ray, S.; Basu, K. SEVNOC: Security Validation of System-on-Chip Designs with NoC Fabrics. IEEE Trans.-Comput.-Aided Des. Integr. Circuits Syst. 2022, 42, 672–682. [Google Scholar] [CrossRef]
- Weber, I.; Marchezan, G.; Caimi, L.; Marcon, C.; Moraes, F.G. Open-source NoC-based many-core for evaluating hardware trojan detection methods. In Proceedings of the 2020 IEEE International Symposium on Circuits and Systems (ISCAS), Seville, Spain, 12–14 October 2020. [Google Scholar]
- Li, Z.; Wang, J.; Huang, Z.; Wang, Q. EA-based Mitigation of Hardware Trojan Attacks in NoC of Coarse-Grained Reconfigurable Arrays. In Proceedings of the 2022 International Conference on Networking and Network Applications (NaNA), Urumqi, China, 3–5 December 2022. [Google Scholar]
- Yao, J.; Zhang, Y.; Hua, Y.; Li, Y.; Yang, J.; Chen, X. Spotlight: An Impairing Packet Transmission Attack Targeting Specific Node in NoC-based TCMP. In Proceedings of the 2023 IEEE European Test Symposium (ETS), Venezia, Italy, 22–26 May 2023. [Google Scholar]
- Pande, P.P.; Grecu, C.; Jones, M.; Ivanov, A.; Saleh, R. Performance evaluation and design trade-offs for network-on-chip interconnect architectures. IEEE Trans. Comput. 2005, 54, 1025–1040. [Google Scholar] [CrossRef]
- Ahmed, M.M.; Dhavlle, A.; Mansoor, N.; Sutradhar, P.; Dinakarrao, S.M.P.; Basu, K.; Ganguly, A. Defense against on-chip trojans enabling traffic analysis attacks. In Proceedings of the in 2020 Asian Hardware Oriented Security and Trust Symposium (AsianHOST), Kolkata, India, 15–17 December 2020; pp. 1–6. [Google Scholar]
- Shayan, M.; Basu, K.; Karri, R. Hardware trojans inspired ip watermarks. IEEE Des. Test 2019, 36, 72–79. [Google Scholar] [CrossRef]
- Hogg, R.V.; McKean, J.; Craig, A.T. Introduction to Mathematical Statistics; Pearson Education: New York, NY, USA, 2005. [Google Scholar]
- Pandita, N. The Ganita Kaumudi; Indian Press: Benares, India, 1936. [Google Scholar]
- Roy, R. Sources in the Development of Mathematics: Series and Products from the Fifteenth to the Twenty-First Century; Cambridge University Press: Cambridge, UK, 2011. [Google Scholar]
- Hull, T.E.; Dobell, A.R. Random number generators. SIAM Rev. 1962, 4, 230–254. [Google Scholar] [CrossRef]
- Badr, M.; Jerger, N.E. Synfull: Synthetic traffic models capturing cache coherent behaviour. ACM SIGARCH Comput. Archit. News 2014, 42, 109–120. [Google Scholar] [CrossRef]
- Catania, V.; Mineo, A.; Monteleone, S.; Palesi, M.; Patti, D. Noxim: An open, extensible and cycle-accurate network on chip simulator. In Proceedings of the IEEE 26th International Conference on Application-Specific Systems, Architectures and Processors (ASAP), Toronto, ON, Canada, 27–29 July 2015. [Google Scholar]



| Input Image Dimensions | (#HT * 80) × 13 |
| Hidden Layer | Convolution: two layers |
| Activation Function | LeakyReLu |
| Dropout | 0.4 |
| Output Layer | Dense with sigmoid activation |
| Optimizer | Adam with learning rate = 0.0002 and beta_1 = 0.5 |
| Loss Function | Binary cross entropy |
| Component | Configuration |
|---|---|
| System size | 64 cores, Out-of-Order, 16 cores/chip |
| Cache | 32 KB (private L1), 512 KB (shared L2), MOESI |
| NoC router | 3 stage pipe-lined 5 ports, 0.07 8pJ/bit |
| Total VC | 4, each 8 flits deep, 64 bits/flit |
| Wired NoC links | 64-bit flits, single cycle latency, 0.2 pJ/bit/mm |
| Technology | 65 nm, 1 V supply, 1 GHz clock |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mountford, T.; Dhavlle, A.; Tevebaugh, A.; Mansoor, N.; Dinakarrao, S.M.P.; Ganguly, A. Address Obfuscation to Protect against Hardware Trojans in Network-on-Chips. J. Low Power Electron. Appl. 2023, 13, 50. https://doi.org/10.3390/jlpea13030050
Mountford T, Dhavlle A, Tevebaugh A, Mansoor N, Dinakarrao SMP, Ganguly A. Address Obfuscation to Protect against Hardware Trojans in Network-on-Chips. Journal of Low Power Electronics and Applications. 2023; 13(3):50. https://doi.org/10.3390/jlpea13030050
Chicago/Turabian StyleMountford, Thomas, Abhijitt Dhavlle, Andrew Tevebaugh, Naseef Mansoor, Sai Manoj Pudukotai Dinakarrao, and Amlan Ganguly. 2023. "Address Obfuscation to Protect against Hardware Trojans in Network-on-Chips" Journal of Low Power Electronics and Applications 13, no. 3: 50. https://doi.org/10.3390/jlpea13030050
APA StyleMountford, T., Dhavlle, A., Tevebaugh, A., Mansoor, N., Dinakarrao, S. M. P., & Ganguly, A. (2023). Address Obfuscation to Protect against Hardware Trojans in Network-on-Chips. Journal of Low Power Electronics and Applications, 13(3), 50. https://doi.org/10.3390/jlpea13030050







