Selective Noise Based Power-Efficient and Effective Countermeasure against Thermal Covert Channel Attacks in Multi-Core Systems
Abstract
1. Introduction
2. Related Works
2.1. Detection
2.2. Defence
3. System and Threat Model
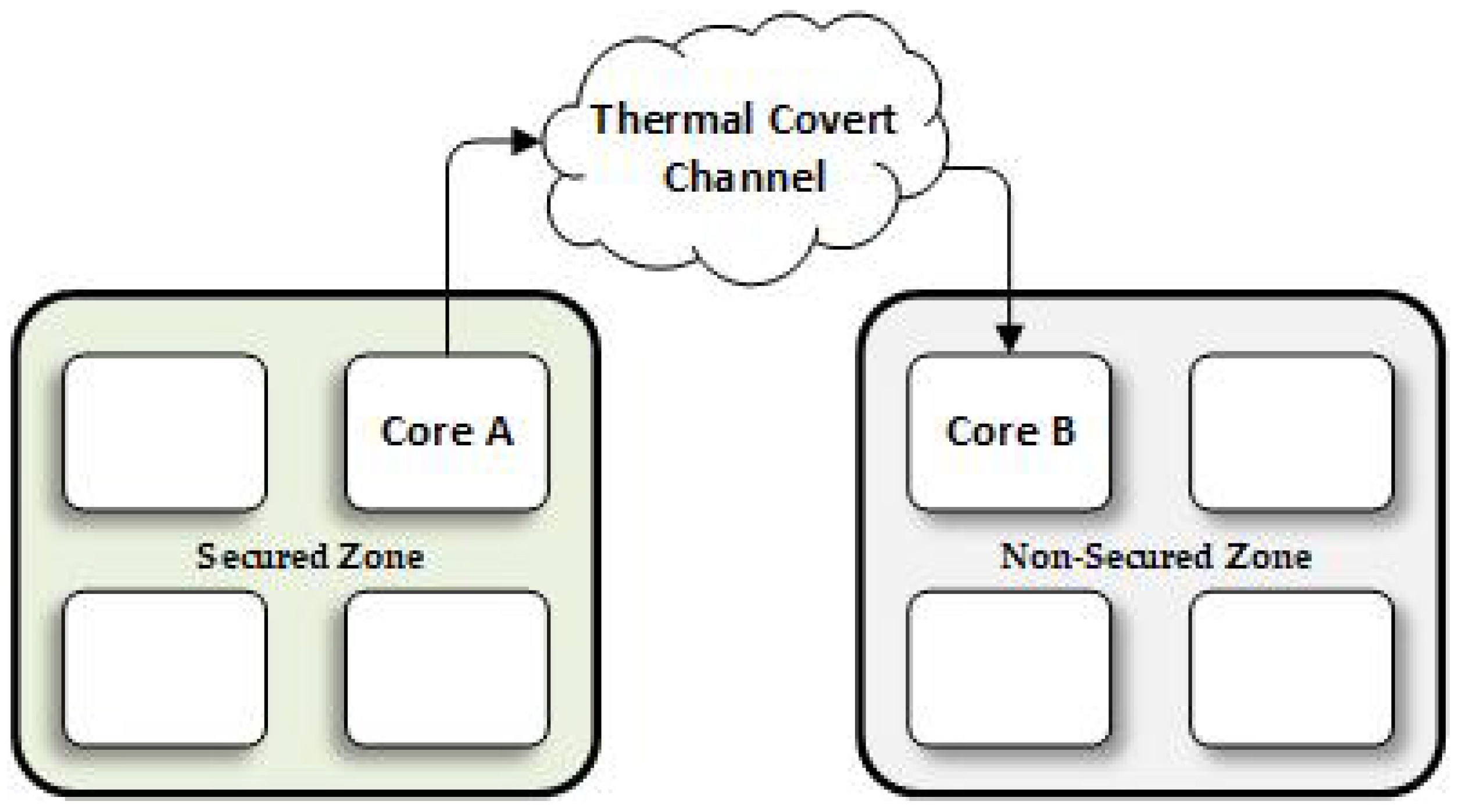
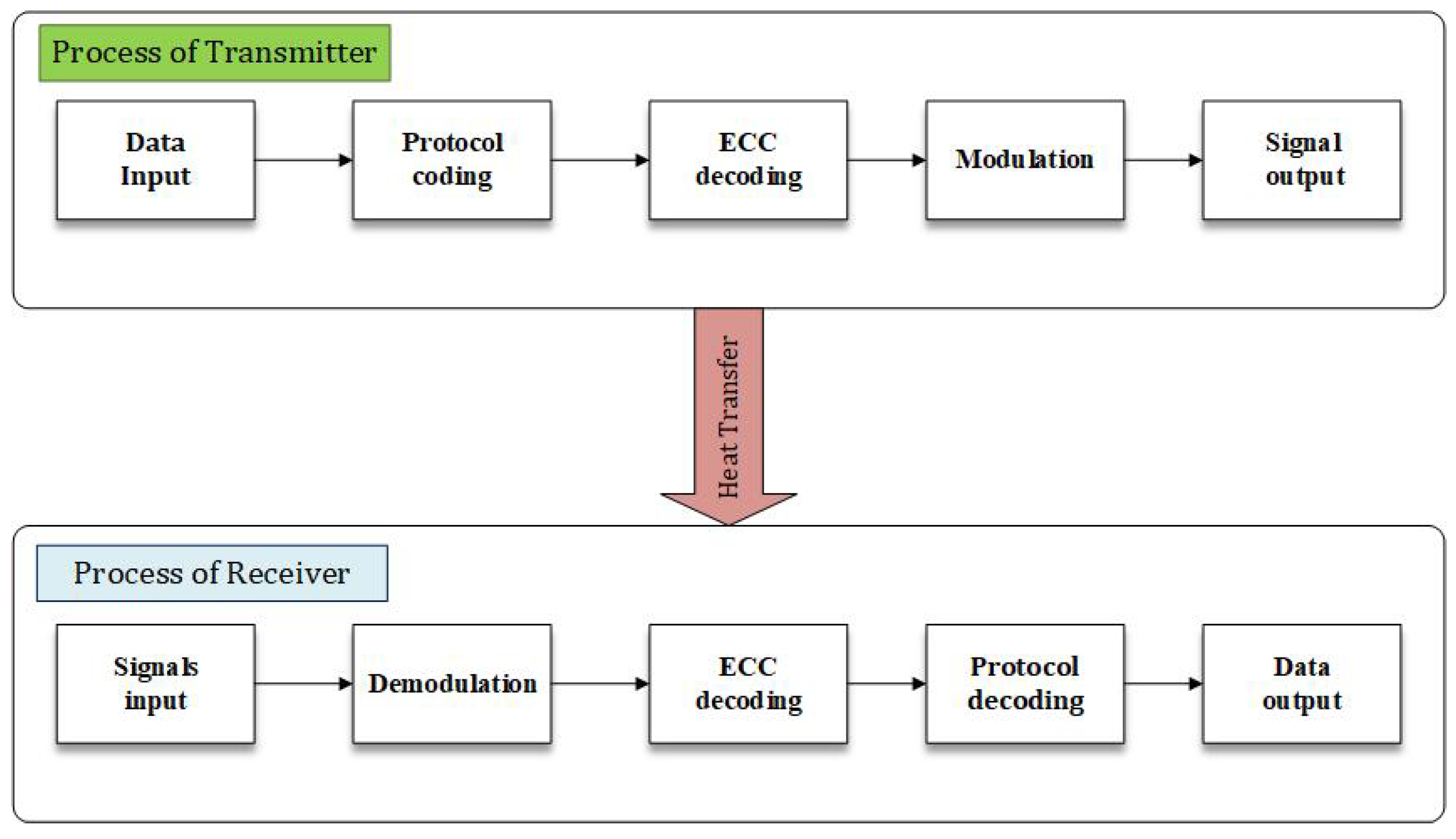
3.1. TCC Communication Architecture
3.2. Challenges of Thermal Covert Channel Attack
3.3. Threat Model
- The attackers have direct access to the target device or systems in order to record and archive thermal traces of the executed decryption. Many key recoveries attacks use a common set of methods or techniques for analysing thermal traces. Simple thermal analysis (STA) includes directly inspecting traces to deduce sensitive data or information when measurements can be recorded to certain data properties [32];
- The attackers can acquire the ciphertext. In the transmission process, the ciphertext data will be employed as default storage parameters for the specific transaction. So, during this process, it is most likely the attackers can access the ciphertext [44];
- The attackers have access to a similar system or device. For example, using off-the-shelf parts such as AVR, ARM, etc;
- Since the signal on the transmitter side is already distorted by adding noise, it would not be possible to detect it correctly at the receiver side by increasing the frequency of thermal sensors, because the information received would be different from the original information. Further, for proper synchronization of data, it is better for both transmitter and receiver thermal sensors to operate at the same frequency. The transmitter and the receiver also need to reach an agreement on the frequency of transmission for the thermal covert channel [3].
4. Countermeasures against Thermal Covert Channel Attacks
- Step 1 (Detection): The detection algorithm uses the module of bandpass filtering to filter out the thermal signals that are out of every band of interest. The detection algorithm is also designed in a way that it can manage TCC, whose receiver and transmitter runs through two different channels. While designing the countermeasure method, we consider that the receiver and the transmitter have access to the same thermal data files, and also that the transmitter and the receiver threads are both sited in the same physical core and share the same thermal sensors, known as Intra-core channel [3,5]. The frequency scanning process is used to detect any existing TCC channels.In addition, each core specifies the signal’s maximum amplitude from the frequency scanning process and leads it into a module known as the decision-making module. The decision-making module compares the signal’s amplitude against a threshold ( is the pre-set threshold for the signal amplitude in a detection cycle.) and decides whether a signal (e.g., 1 0 1 0) is from a covert channel or not. If the amplitude of the signal is higher than , an attack is present; otherwise, there is no attack happening. Statistically, the threshold is selected experimentally to be 0.02 dB [5].Based on frequency scanning, if the defender, denoted as, global manager, identified the TCC channel exists, the proposed countermeasure is applied;
- Step 2 (Classify bits): For applying the proposed countermeasure, we need to classify bits into “1” and “0” according to the thermal signal changes. In our work, the bit “1” represents changes in the thermal signal, while the bit “0” illustrates no changes;
- Step 3 (Check bits): For this step, the system checks if the bit is “1” or not by considering the changes in the thermal signal. Then, if the bit is “1” the operation will start;
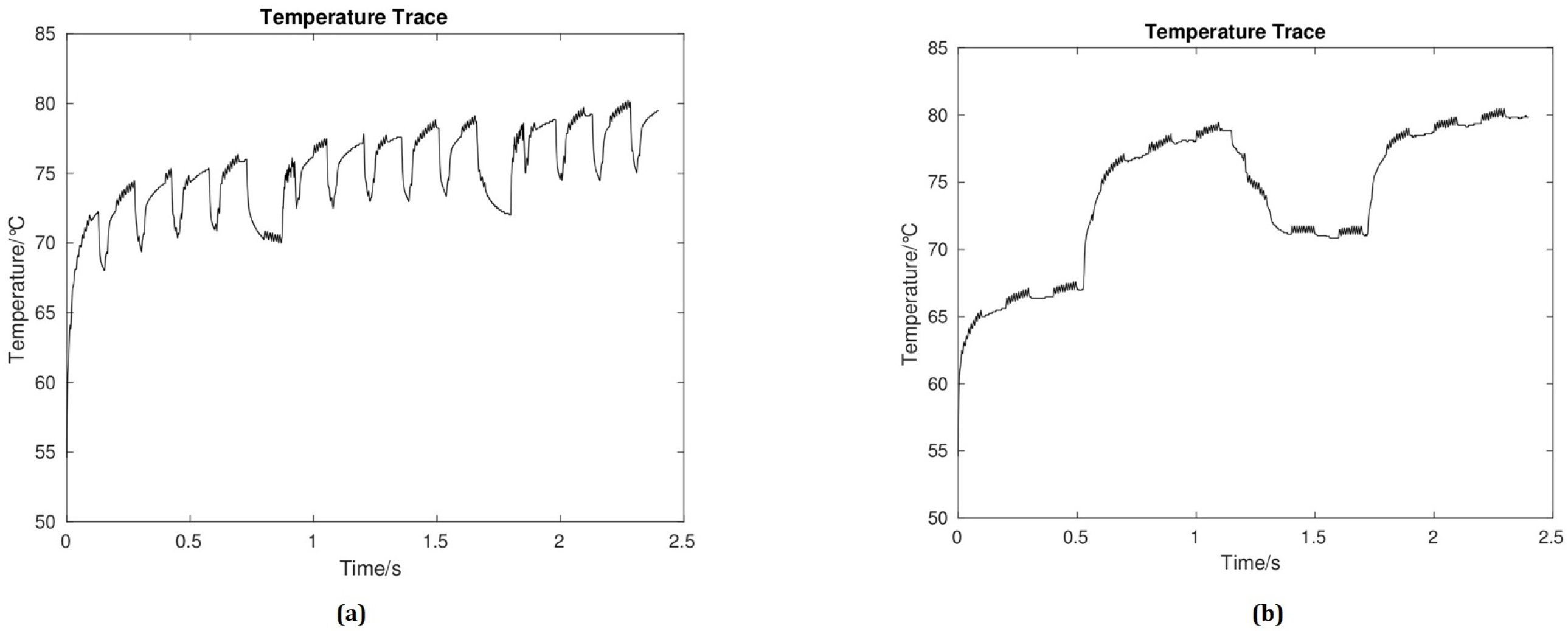
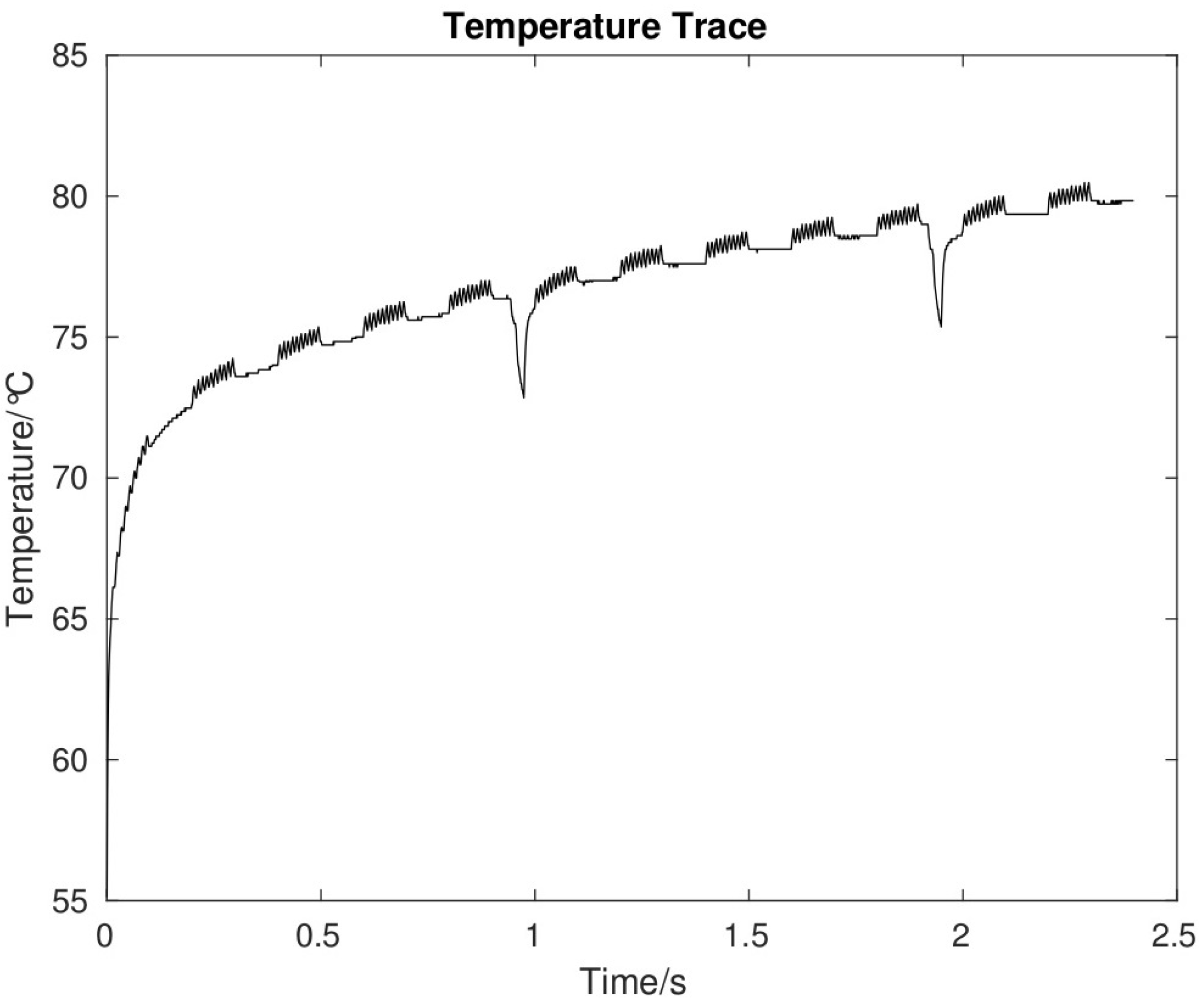
- Step 4 (Adding an extra noise): The last step is adding an extra noise to the temperature signal, which results in generating more heat to the system where the bit is “1”, therefore, there is no bit change for a long duration, as Figure 4 shows.
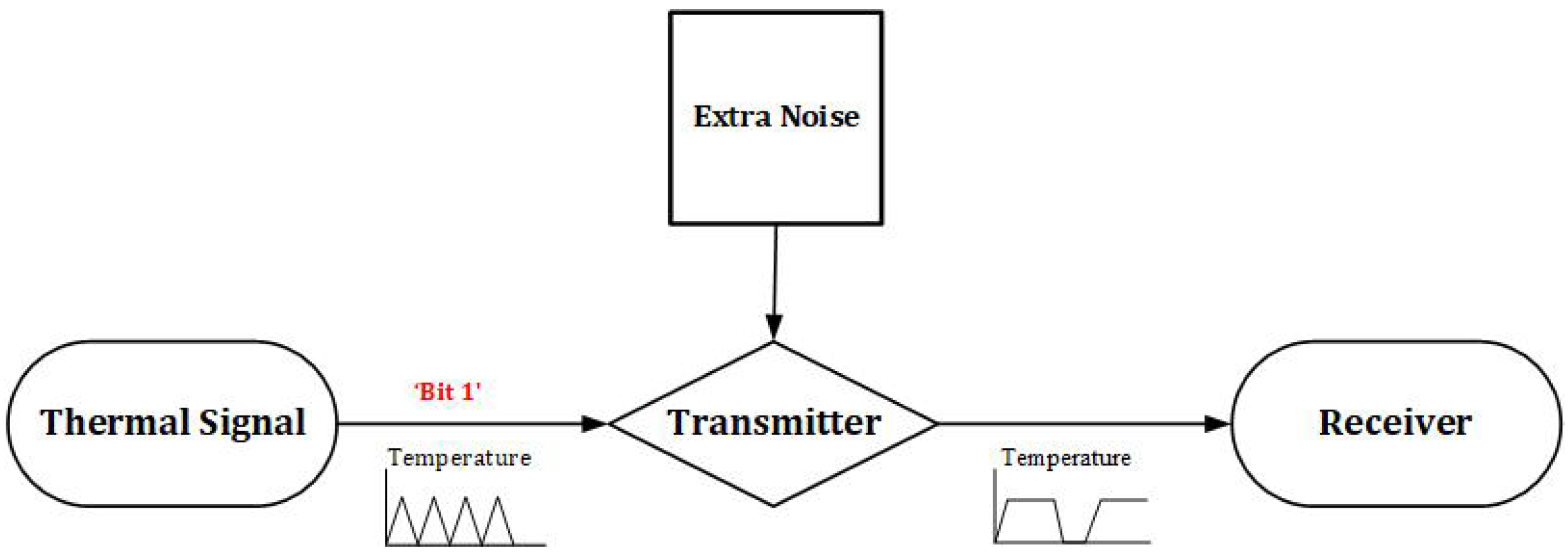
4.1. Extra Noise Generation by Random Numbers
| Algorithm 1 Psuedorandom Number Generator |
| Input: Two random numbers X1 and X2 |
| Output: Psuedorandom sequence period of X1 + X2 |
| 1: for n = 100, do |
| 2: if then |
| 3: X1 = rollDie(); |
| 4: X2 = rollDie(); |
| 5: Count n = X1 + X2 |
| 6: return |
| 7: end if |
| 8: end for |
4.2. Selective Noise
4.3. Selective Noise Countermeasure
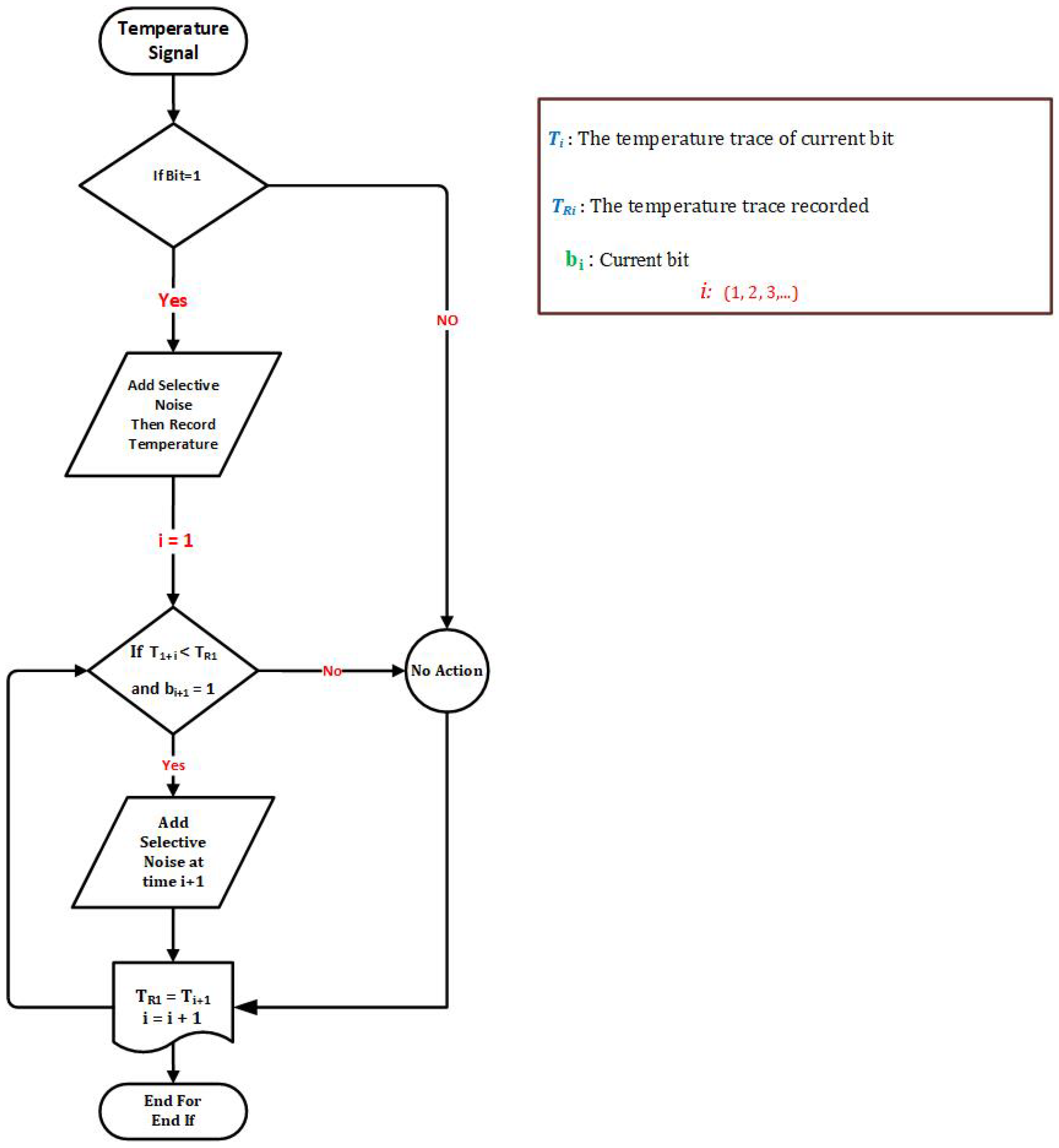
- Step 1 (Record temperature): This step consists of monitoring and recording the temperature. The extra noise is added when the bit is “1”. The current temperature is then recorded by the temperature sensor and used for the next step;
- Step 2 (Temperature monitoring of processors and adding selective noise): In the last step, the next bit’s temperature is compared with the recorded temperature (TR) from the previous step. If the temperature of the current bit is less than TR or starting to decrease, the selective noise is added to keep the temperature at the same level, otherwise it is moved to the next bit. This progress continues until the end of the transmission process.
5. Experimental Evaluation
- : is the position (core id) of the detected thermal covert channel transmitter/receiver cores.
- : is the actual position of the transmitter/receiver cores.
- :
- The number of cores.
- :
- The number of functional units within a core.
- :
- The average power consumption for functional unit u from core c.
| Countermeasures | Bit Error Rate | Avg. Power Consumption (w) |
|---|---|---|
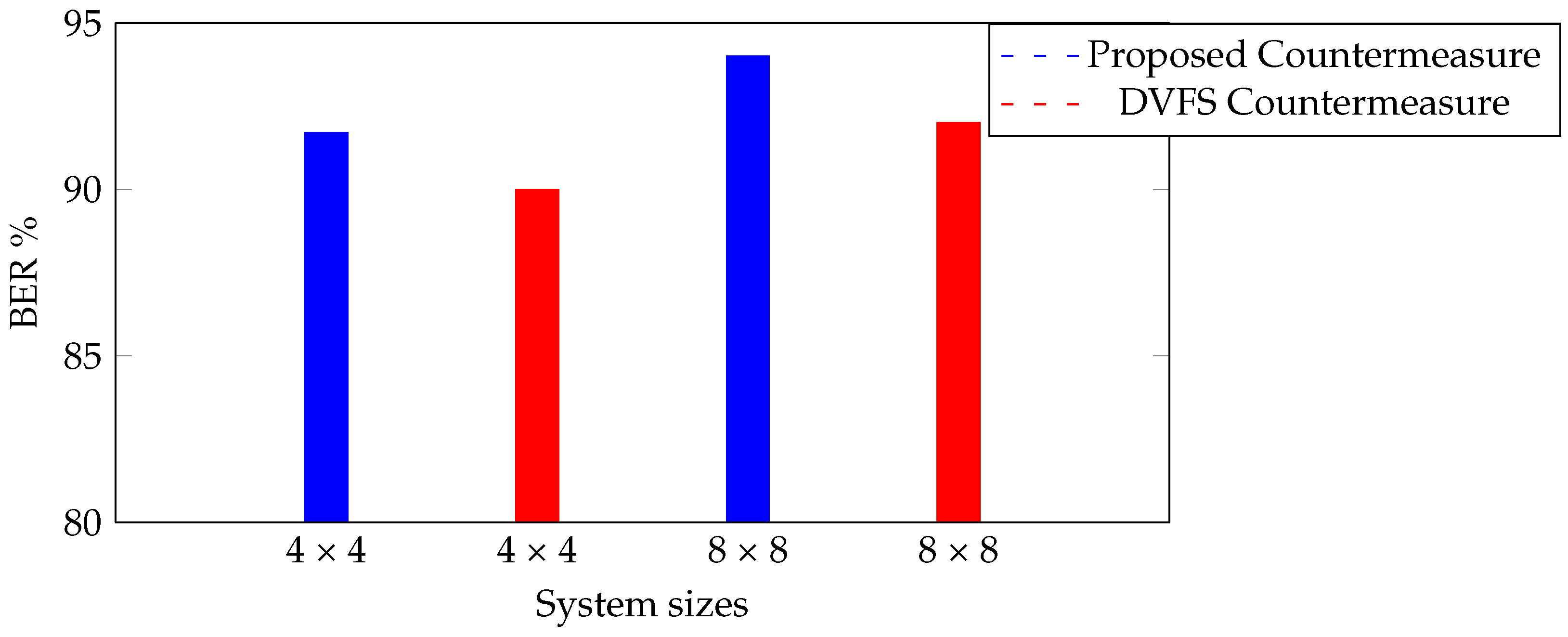
| TCC with periodically scanning the frequency and add a strong noise source [12]. | 85% | 22.27 |
| TCC with DVFS (Figure 2b) [3,5]. | 92% | 22.31799 |
| TCC with One Extra Noise (Figure 4b) | 94% | 23.74631 |
| TCC with Selective Noise (Figure 6) | 94% | 22.81277 |
- The first and most important advantage of this work is the high bit error rate, which means that the vulnerability of the system will decrease significantly. Therefore, any possible TCC attacks can hardly happen in this methodology;
- Low power consumption: one of the most important metrics of any embedded system is power consumption [51]. This is mainly because the increase in power consumption is a significant factor for elevated temperatures. Therefore, low power consumption can affect the systems’ temperatures;
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Miedl, P.; Bartolini, D.B.; Thiele, L. On the Capacity of Thermal Covert Channels in Multicores. In Proceedings of the 11th European Conference on Computer Systems (EuroSys), London, UK, 18–21 April 2016; pp. 1–16. [Google Scholar]
- Wang, Z.; Lee, R.B. Covert and Side Channels Due to Processor Architecture. In Proceedings of the 22nd Annual Computer Security Applications Conference (ACSAC’06), Miami Beach, FL, USA, 1–15 December 2006; Volume 8354, pp. 473–482. [Google Scholar]
- Huang, H.; Wang, X.; Jiang, Y.; Singh, A.K.; Yang, M.; Huang, L. Detection of and Countermeasure against Thermal Covert Channel in Many-core Systems. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2021, 41, 252–265. [Google Scholar] [CrossRef]
- Masti, R.J.; Rai, D.; Ranganathan, A.; Müller, C.; Thiele, L.; Capkun, S. Thermal covert channels on multi-core platforms. In Proceedings of the 24th USENIX Security Symposium (USENIX Security 15), Washington, DC, USA, 12–14 August 2015; pp. 865–880. [Google Scholar]
- Huang, H.; Wang, X.; Jiang, Y.; Singh, A.K.; Yang, M.; Huang, L. On countermeasures against the thermal covert channel attacks targeting many-core systems. In Proceedings of the 57th ACM/IEEE Design Automation Conference (DAC), San Francisco, CA, USA, 20–24 July 2020; pp. 1–6. [Google Scholar]
- Gu, P.; Stow, D.; Barnes, R.; Kursun, E.; Xie, Y. Thermal-aware 3D design for side-channel information leakage. In Proceedings of the IEEE 34th International Conference on Computer Design (ICCD), Scottsdale, AZ, USA, 2–5 October 2016; pp. 520–527. [Google Scholar]
- Huang, X.; Wang, X.; Jiang, Y.; Singh, A.K.; Yang, M. Dynamic allocation/reallocation of dark cores in many-core systems for improved system performance. IEEE Access 2020, 8, 165693–165707. [Google Scholar] [CrossRef]
- Okhravi, H.; Bak, S.; King, S.T. Design, implementation and evaluation of covert channel attacks. In Proceedings of the IEEE International Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 8–10 November 2010; pp. 481–487. [Google Scholar]
- Alagappan, M.; Rajendran, J.; Doroslovački, M.; Venkataramani, G. DFS covert channels on multi-core platforms. In Proceedings of the IFIP/IEEE International Conference on Very Large Scale Integration (VLSI-SoC), Abu Dhabi, United Arab Emirates, 23–25 October 2017; pp. 1–6. [Google Scholar]
- Florea, A.; Buduleci, C.; Chiş, R.; Gellert, A.; Vinţan, L. Enhancing the sniper simulator with thermal measurement. In Proceedings of the 18th International Conference on System Theory, Control and Computing (ICSTCC), Sinaia, Romania, 17–19 October 2014; pp. 31–36. [Google Scholar]
- Carlson, T.E.; Heirman, W.; Eyerman, S.; Hur, I.; Eeckhout, L. An evaluation of high-level mechanistic core models. ACM Trans. Archit. Code Optim. (TACO) 2014, 11, 1–25. [Google Scholar] [CrossRef]
- Wang, J.; Wang, X.; Jiang, Y.; Singh, A.K.; Huang, L.; Yang, M. Combating Enhanced Thermal Covert Channel in Multi-/Many-Core Systems With Channel-Aware Jamming. IEEE Trans. Comput.-Aided Des. Integr. Circuits Syst. 2020, 39, 3276–3287. [Google Scholar] [CrossRef]
- Wu, Z.; Xu, Z.; Wang, H. Whispers in the hyper-space: High-bandwidth and reliable covert channel attacks inside the cloud. IEEE/ACM Trans. Netw. 2014, 23, 603–615. [Google Scholar] [CrossRef]
- Tuptuk, N.; Hailes, S. Covert channel attacks in pervasive computing. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications (PerCom), St. Louis, MO, USA, 23–27 March 2015; pp. 236–242. [Google Scholar]
- Costa, G.; Pinelli, F.; Soderi, S.; Tolomei, G. Covert Channel Attack to Federated Learning Systems. arXiv 2021, arXiv:2104.10561. [Google Scholar]
- Deshotels, L. Inaudible sound as a covert channel in mobile devices. In Proceedings of the 8th USENIX Workshop on Offensive Technologies (WOOT’14), San Diego, CA, USA, 19 August 2014. [Google Scholar]
- Yao, F.; Venkataramani, G.; Doroslovački, M. Covert timing channels exploiting non-uniform memory access based architectures. In Proceedings of the Great Lakes Symposium on VLSI 2017, Banff, AB, Canada, 10–12 May 2017; pp. 155–160. [Google Scholar]
- Zhang, X.; Tan, Y.A.; Liang, C.; Li, Y.; Li, J. A covert channel over volte via adjusting silence periods. IEEE Access 2018, 6, 9292–9302. [Google Scholar] [CrossRef]
- Matyunin, N.; Szefer, J.; Biedermann, S.; Katzenbeisser, S. Covert channels using mobile device’s magnetic field sensors. In Proceedings of the 2016 21st Asia and South Pacific Design Automation Conference (ASP-DAC), Macau, China, 25–28 January 2016; pp. 525–532. [Google Scholar]
- Guri, M.; Monitz, M.; Elovici, Y. SBee: Air-gap covert-channel via electromagnetic emission from USB. In Proceedings of the 2016 14th Annual Conference on Privacy, Security and Trust (PST), Auckland, New Zealand, 12–14 December 2016; pp. 264–268. [Google Scholar]
- Guri, M.; Hasson, O.; Kedma, G.; Elovici, Y. VisiSploit: An optical covert-channel to leak data through an air-gap. arXiv 2016, arXiv:1607.03946. [Google Scholar]
- Liu, W.; Zhou, X.; Huo, J.; Yan, K. Modeling of visible light channel based on matrix reconstruction. Int. Soc. Opt. Photonics 2016, 9902, 990205. [Google Scholar]
- Gnad, D.R.; Nguyen, C.D.K.; Gillani, S.H.; Tahoori, M.B. Voltage-based Covert Channels in Multi-Tenant FPGAs. IIACR Cryptol. ePrint Arch. 2019, 2019, 1394. [Google Scholar]
- Bossuet, L. Dvfs as a security failure of trustzone-enabled heterogeneous soc. In Proceedings of the 2018 25th IEEE International Conference on Electronics, Circuits and Systems (ICECS), Bordeaux, France, 9–12 December 2018; pp. 489–492. [Google Scholar]
- Ge, Q.; Yarom, Y.; Cock, D.; Heiser, G. A survey of microarchitectural timing attacks and countermeasures on contemporary hardware. J. Cryptogr. Eng. 2018, 8, 1–27. [Google Scholar] [CrossRef]
- Darwish, O.; Al-Fuqaha, A.; Brahim, G.B.; Jenhani, I.; Anan, M. Towards a streaming approach to the mitigation of covert timing channels. In Proceedings of the 2018 14th International Wireless Communications & Mobile Computing Conference (IWCMC), Limassol, Cyprus, 25–29 June 2018; pp. 255–260. [Google Scholar]
- Lampson, B.W. A note on the confinement problem. Commun. ACM 1973, 16, 613–615. [Google Scholar] [CrossRef]
- Iakymchuk, T.; Nikodem, M.; Kępa, K. Temperature-based covert channel in FPGA systems. In Proceedings of the 6th International Workshop on Reconfigurable Communication-Centric Systems-on-Chip (ReCoSoC), Montpellier, France, 20–22 June 2011; pp. 1–7. [Google Scholar]
- Murdoch, S.J. Hot or not: Revealing hidden services by their clock skew. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; pp. 27–36. [Google Scholar]
- Hutter, M.; Schmidt, J.M. The temperature side channel and heating fault attacks. In Proceedings of the International Conference on Smart Card Research and Advanced Applications, Berlin, Germany, 27–29 November 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 219–235. [Google Scholar]
- Reis, C.; Barth, A.; Pizano, C. Browser Security: Lessons from Google Chrome: Google Chrome developers focused on three key problems to shield the browser from attacks. Queue 2009, 7, 3–8. [Google Scholar] [CrossRef]
- Lee, J.S.; Skadron, K.; Chung, S.W. Predictive temperature-aware DVFS. IEEE Trans. Comput. 2009, 59, 127–133. [Google Scholar] [CrossRef]
- Hackenberg, D.; Schöne, R.; Ilsche, T.; Molka, D.; Schuchart, J.; Geyer, R. An energy efficiency feature survey of the intel haswell processor. In Proceedings of the IEEE International Parallel and Distributed Processing Symposium Workshop, Hyderabad, India, 25–29 May 2015; pp. 896–904. [Google Scholar]
- Singh, A.K.; Dey, S.; McDonald-Maier, K.; Basireddy, K.R.; Merrett, G.V.; Al-Hashimi, B.M. Dynamic energy and thermal management of multi-core mobile platforms: A survey. IEEE Des. Test. 2020, 37, 25–33. [Google Scholar] [CrossRef]
- Vateva-Gurova, T.; Suri, N. On the Detection of Side-Channel Attacks. In Proceedings of the IEEE 23rd Pacific Rim International Symposium on Dependable Computing (PRDC), Taipei, Taiwan, 4–7 December 2018; pp. 185–186. [Google Scholar]
- Happe, M.; Agne, A.; Plessl, C. Measuring and predicting temperature distributions on FPGAs at run-time. In Proceedings of the International Conference on Reconfigurable Computing and FPGAs, Cancun, Mexico, 30 November–2 December 2011; pp. 55–60. [Google Scholar]
- Gao, F.; Zhu, L.; Gai, K.; Zhang, C.; Liu, S. Achieving a covert channel over an open blockchain network. IEEE Netw. 2020, 34, 6–13. [Google Scholar] [CrossRef]
- Wen, S.; Wang, X.; Singh, A.K.; Jiang, Y.; Yang, M. Performance optimization of many-core systems by exploiting task migration and dark core allocation. IEEE Trans. Comput. 2020, 71, 92–106. [Google Scholar] [CrossRef]
- Chen, S.; Xiong, W.; Xu, Y.; Li, B.; Szefer, J. Thermal covert channels leveraging package-on-package DRAM. In Proceedings of the 18th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/13th IEEE International Conference on Big Data Science and Engineering, Rotorua, New Zealand, 5–8 August 2019; pp. 319–326. [Google Scholar]
- Saligane, M.; Khayatzadeh, M.; Zhang, Y.; Jeong, S.; Blaauw, D.; Sylvester, D. All-digital SoC thermal sensor using on-chip high order temperature curvature correction. In Proceedings of the 2015 IEEE Custom Integrated Circuits Conference (CICC), San Jose, CA, USA, 28–30 September 2015; pp. 1–4. [Google Scholar]
- Chundi, P.K.; Zhou, Y.; Kim, M.; Kursun, E.; Seok, M. Hotspot monitoring and temperature estimation with miniature on-chip temperature sensors. In Proceedings of the 2017 IEEE/ACM International Symposium on Low Power Electronics and Design (ISLPED), Taipei, Taiwan, 24–26 July 2017; pp. 1–6. [Google Scholar]
- Murdock, K.; Oswald, D.; Garcia, F.D.; Van Bulck, J.; Gruss, D.; Piessens, F. Plundervolt: Software-based fault injection attacks against Intel SGX. In Proceedings of the 2020 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 18–21 May 2020; pp. 1466–1482. [Google Scholar]
- Pan, S.; Makinwa, K.A. A 0.25 mm 2-Resistor-Based Temperature Sensor With an Inaccuracy of 0.12 °C (3σ) From −55 °C to 125 °C. IEEE J. Solid-State Circuits 2018, 53, 3347–3355. [Google Scholar] [CrossRef]
- Kean, T.; McLaren, D.; Marsh, C. Verifying the authenticity of chip designs with the DesignTag system. In Proceedings of the IEEE International Workshop on Hardware-Oriented Security and Trust, Anaheim, CA, USA, 9 June 2008; pp. 59–64. [Google Scholar]
- Raffaelli, F.; Ferranti, G.; Mahler, D.H.; Sibson, P.; Kennard, J.E.; Santamato, A.; Sinclair, G.; Bonneau, D.; Thompson, M.G.; Matthews, J.C. A homodyne detector integrated onto a photonic chip for measuring quantum states and generating random numbers. Quantum Sci. Technol. 2018, 3, 025003. [Google Scholar] [CrossRef]
- Vivoli, V.C.; Sekatski, P.; Bancal, J.D.; Lim, C.C.W.; Martin, A.; Thew, R.T.; Zbinden, H.; Gisin, N.; Sangouard, N. Comparing different approaches for generating random numbers device-independently using a photon pair source. New J. Phys. 2015, 17, 023023. [Google Scholar] [CrossRef][Green Version]
- Chiş, R.; Florea, A.; Buduleci, C.; VinţAN, L. Multi-objective optimization for an enhanced multi-core SNIPER simulator. Proc. Rom. Acad.-Ser. A 2018, 19, 85–93. [Google Scholar]
- Aljuffri, A.; Zwalua, M.; Reinbrecht, C.R.W.; Hamdioui, S.; Taouil, M. Applying Thermal Side-Channel Attacks on Asymmetric Cryptography. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 2009, 29, 1930–1942. [Google Scholar] [CrossRef]
- Zander, S.; Branch, P.; Armitage, G. Capacity of temperature-based covert channels. IEEE Commun. Lett. 2010, 15, 82–84. [Google Scholar] [CrossRef]
- Long, Z.; Wang, X.; Jiang, Y.; Cui, G.; Zhang, L.; Mak, T. Improving the efficiency of thermal covert channels in multi-/many-core systems. In Proceedings of the 2018 Design, Automation & Test in Europe Conference & Exhibition (DATE), Dresden, Germany, 19–23 March 2018; pp. 1459–1464. [Google Scholar]
- Rahimi, P.; Singh, A.K.; Wang, X.; Prakash, A. Trends and Challenges in Ensuring Security for Low-Power and High-Performance Embedded SoCs. In Proceedings of the 2021 IEEE 14th International Symposium on Embedded Multicore/Many-Core Systems-On-Chip (MCSoC), Singapore, 20–23 December 2021; pp. 226–233. [Google Scholar]
- Claeys, T.; Rousseau, F.; Simunovic, B.; Tourancheau, B. Thermal covert channel in Bluetooth low energy networks. In Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks, Miami, FL, USA, 15–17 May 2019; pp. 267–276. [Google Scholar]
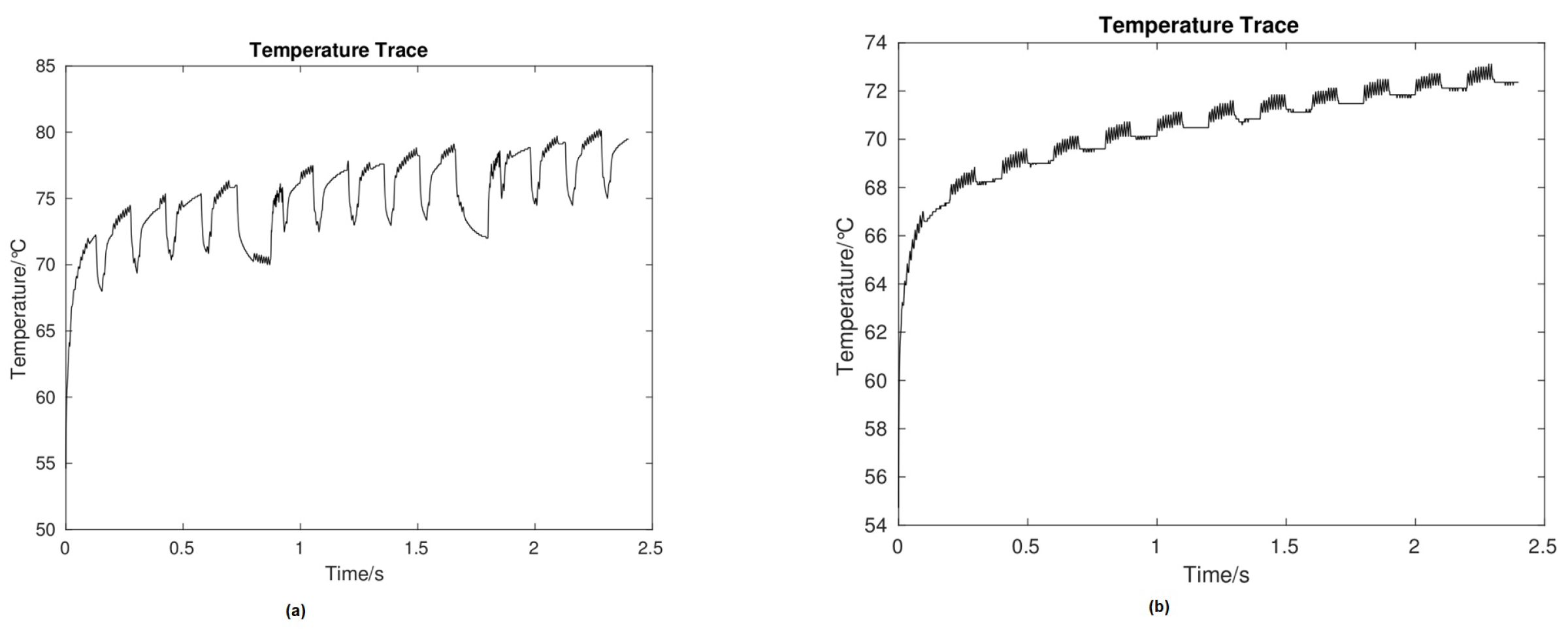
| Countermeasures | Generate Random Numbers | Bit Error Rate | Avg. Power Consumption (w) |
|---|---|---|---|
| One Extra Noise | 20 | 22% | 22.50966 |
| 50 | 22% | 22.80794 | |
| 100 | 94% | 23.74631 | |
| 150 | 94% | 23.96022 |
| Sniper Configuration | |
|---|---|
| Instruction set architecture | x86-64 |
| Operate System | Ubuntu 16.04.5 LTS |
| Number of cores | 4 × 4, 8 × 8 |
| Number of SMT threads per core | 2 |
| Frequency of CPUs (MHz) | 2000 |
| Benckmarks of PARSEC | Blackscholes, Canneal, Fluidanimate, |
| Streamcluster, Swaptions, X-264, Dedup, Freqmine | |
| Benckmarks of SPLASH-2 | Raytrace, Barnes |
| Configuration for an integrated Hotspot | |
| Chip thickness | 0.15 mm |
| Silicon thermal conductivity | 100 W/(m·K) |
| Silicon specific heat capacity | 1.75 × 106 J/(m3·K) |
| Heat sink side | 0.06 m |
| Heat sink thickness | 6.9 mm |
| Heat sink thermal conductivity | 400 W/(m·K) |
| Specific heat capacity of heat sink | 3.55 × 106 J/(m3·K) |
| Configuration for TCC programs | |
| Transmission frequency | 10 Hz, 20 Hz, 50 Hz, 80 Hz, |
| 100 Hz, 150 Hz, etc. | |
| Preamble of a packet | 1010101 |
| Packet size in bits | 64 |
| ECC method | Hamming code |
| System Sizes | |
|---|---|
| 4 × 4 | 0.975 |
| 8 × 8 | 0.97 |
| Countermeasures | Bit Error Rate | Avg. Power Consumption (w) |
|---|---|---|
| Two Extra Noise | 95% | 25.77204 |
| Three Extra Noise | 98% | 28.19446 |
| More than three Extra Noise (Five Extra Noise) | 98% | 34.20743 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rahimi, P.; Singh, A.K.; Wang, X. Selective Noise Based Power-Efficient and Effective Countermeasure against Thermal Covert Channel Attacks in Multi-Core Systems. J. Low Power Electron. Appl. 2022, 12, 25. https://doi.org/10.3390/jlpea12020025
Rahimi P, Singh AK, Wang X. Selective Noise Based Power-Efficient and Effective Countermeasure against Thermal Covert Channel Attacks in Multi-Core Systems. Journal of Low Power Electronics and Applications. 2022; 12(2):25. https://doi.org/10.3390/jlpea12020025
Chicago/Turabian StyleRahimi, Parisa, Amit Kumar Singh, and Xiaohang Wang. 2022. "Selective Noise Based Power-Efficient and Effective Countermeasure against Thermal Covert Channel Attacks in Multi-Core Systems" Journal of Low Power Electronics and Applications 12, no. 2: 25. https://doi.org/10.3390/jlpea12020025
APA StyleRahimi, P., Singh, A. K., & Wang, X. (2022). Selective Noise Based Power-Efficient and Effective Countermeasure against Thermal Covert Channel Attacks in Multi-Core Systems. Journal of Low Power Electronics and Applications, 12(2), 25. https://doi.org/10.3390/jlpea12020025








