AI Integration in Tactical Communication Systems and Networks: A Survey and Future Research Directions
Abstract
1. Introduction
1.1. Related Works and Limitations
- Limited scope and fragmentation: Most studies focus on isolated use cases such as EW [17], simulation [15], or mission planning [20], without providing a unified perspective across the full range of tactical communication systems. No prior survey has integrated AI applications across radar systems, surveillance, electronic warfare, UAVs, and information networks within a single defense-oriented framework.
- Conceptual or outdated approaches: Many works emphasize theoretical or strategic constructs without recent empirical validation [16,18,19]. Several surveys do not reflect current AI capabilities, such as Generative AI (LLM) or Federated Learning (FL), which limits their applicability to modern defense scenarios.
- Lack of real-world connection: While some papers explore technical innovations or ethical implications [23,25], they often lack operational insights, practical deployments, or industry-linked case studies. This disconnection between academic models and deployed defense systems leaves military professionals without actionable guidance.
1.2. Scope and Contributions
- First integrated tactical AI survey across domains (civil–military): Unlike previous fragmented studies, this is the first to unify AI integration across all tactical communication subsystems (e.g., radar, EW, UAVs).
- A framework without diluting focus with civil or generic AI applications, accessible to both defense experts and non-specialists.
- Identifying how advanced AI methods from civilian industries can enhance tactical communications.
- AI research status in tactical communications, serving as a foundational reference.
- Assessment of defense industry projects: Reviewing major industry initiatives to demonstrate AI-driven tactical networking and military operations improvements.
- Exploration of standardization and ethical challenges to contribute to the regulatory framework.
- Future research directions: Identifying research gaps and outlining emerging AI trends to guide further advancements in resilient and intelligent military communications.
2. Overview of Artificial Learning and Knowledge
2.1. Levels of Intelligence
2.2. Method for Achieving the AI
2.3. Summary of Types of Learning
- Supervised Learning (SL): The algorithm is trained with labeled data from known categories, enabling tasks like spam filtering, numerical value prediction (e.g., vehicle valuation), and data analysis from Internet of Things (IoT), social networks, or facial recognition, useful for tactical missions.
- Unsupervised Learning (UL): The system learns without labeled data, identifying patterns through grouping, visualization, dimensionality reduction, and association rules, widely used in data mining. Applications include person identification in image datasets, graphical representation of unlabeled data for traceability, user blog clustering, feature simplification, anomaly detection in production chains, and discovering relationships through association rules.
- Semi-supervised Learning (SSL): Used when most data are unlabeled, some partially labeled, and a few labeled. For example, the system groups photos where Person 1 appears (unsupervised) and, after tagging one, automatically labels the rest, simplifying the search.
- Reinforcement Learning (RL): This is based on observation, choosing a policy of action, and maximizing rewards or penalties. The vast majority of AI systems specialized in gaming use this approach.
- Batch learning: The system learns from all available data but always starts from scratch. If trained with 2000 samples, adding 500 more requires retraining with 2500 samples. This method, typically offline, demands significant computing power and time.
- Online or incremental learning: New data are continuously added, enabling immediate learning. Key benefits include memory efficiency (no need to store past data) and rapid change adaptation. However, errors in new data (e.g., faulty sensors) can degrade performance, requiring a rollback to a previous state. Commonly used in the stock market.
- Instance-based learning: The system learns from memorized examples and then discerns new incoming cases based on a measure of similarity.
- Model-based learning: It involves studying the data, selecting a model, training it to minimize a cost function, and applying the algorithm to predict new events.
- Deep learning (DL): It features multiple layers where parameters learn from preceding layers rather than directly from raw data. Each layer may use different ML techniques, typically Multi-Layer Neural Networks (MNN), mimicking the human brain in processing images, sounds, and texts.
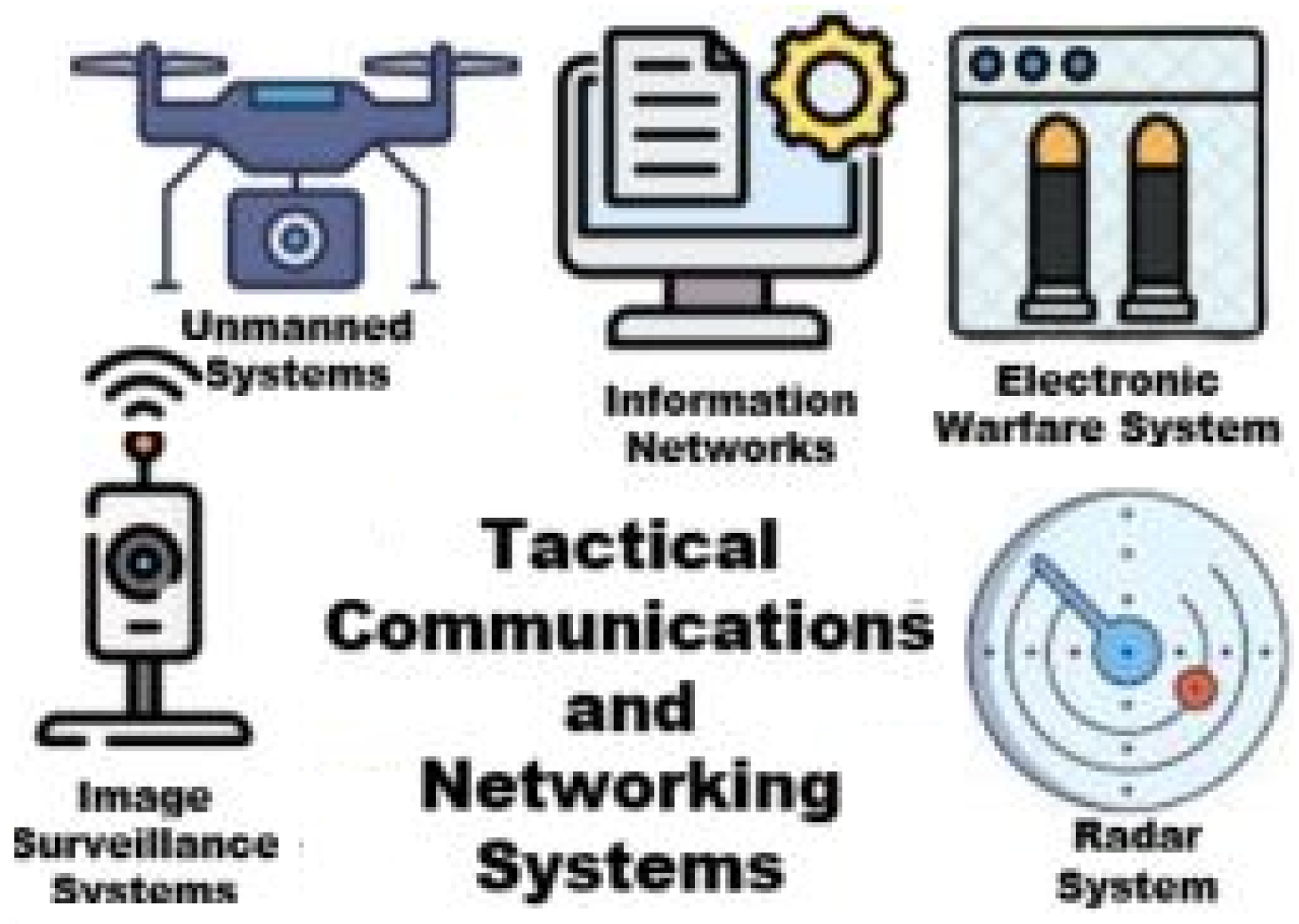
3. Tactical Communications Systems and Networks
3.1. Information Network Systems
3.2. Image Surveillance Systems
3.3. Electronic Warfare Systems
- Electronic Support Measures (ESM): actions to search for, intercept, identify, or locate sources of emitted electromagnetic energy to gain immediate recognition of potential threats.
- Electronic Countermeasures (ECM): actions aimed at denying or reducing the enemy’s use of the electromagnetic spectrum. This includes jamming, deception, and various decoys used for missile defense.
- Electronic Protective Measures (EPM): measures to ensure the reliable use of the electromagnetic spectrum for friendly forces, for instance, fire-control radars are equipped with frequency-hopping agility.
3.4. Radar Systems
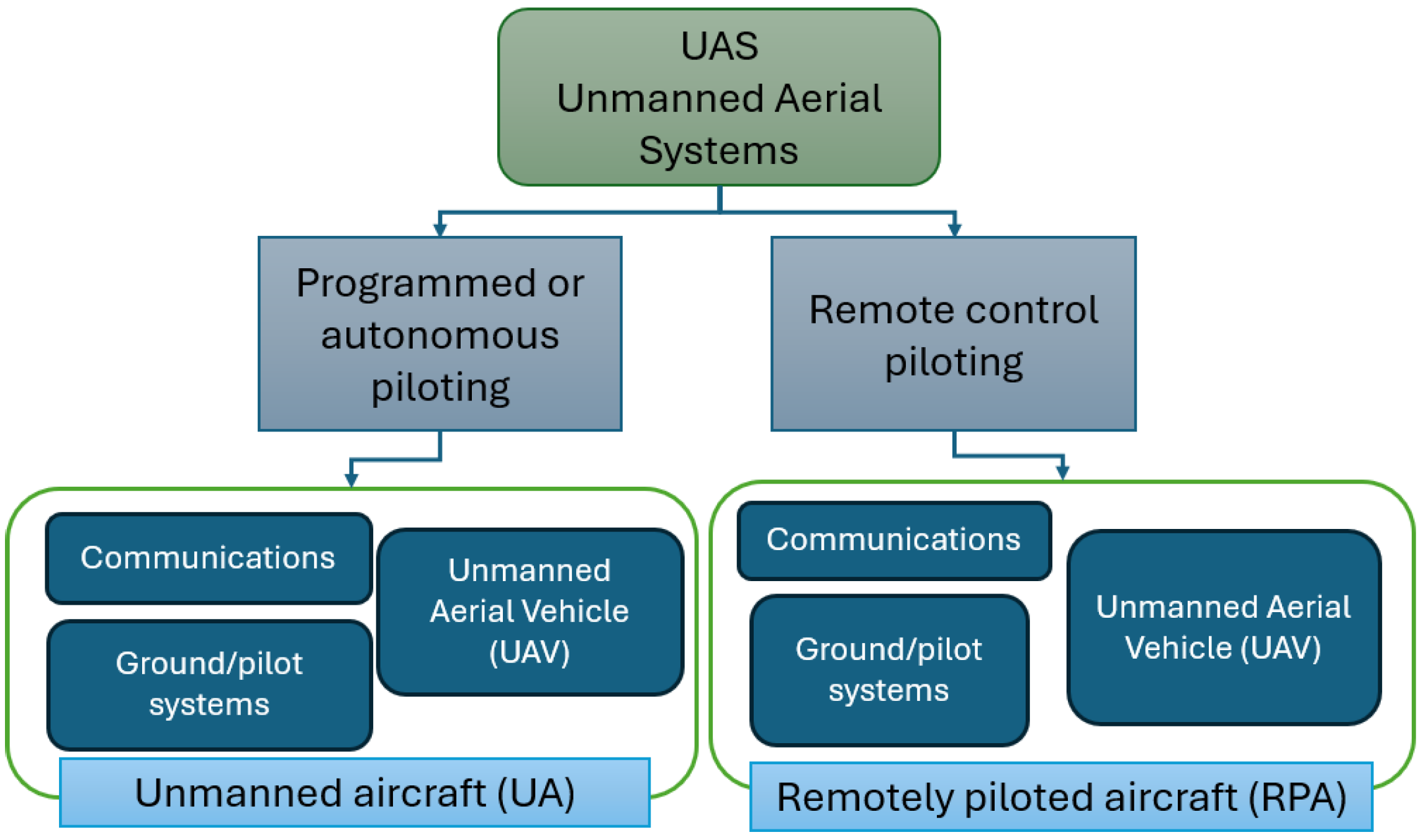
3.5. Unmanned Systems
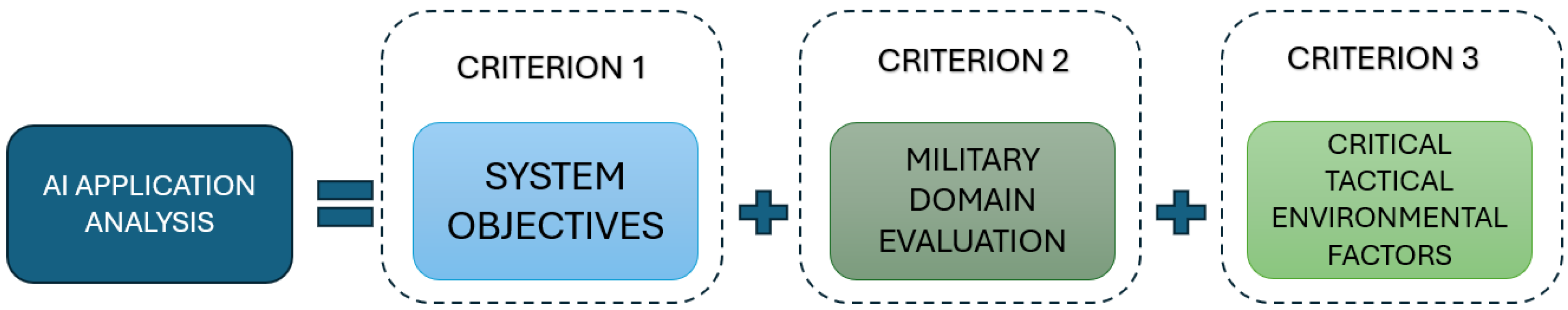
4. Analysis Methodology
- Criterion 1: Covers general data from the selected references.
- Criterion 2: Evaluate the notable and decisive factors relevant to the application in a military domain.
- Criterion 3: Assesses the critical tactical environmental factors affected by the application.
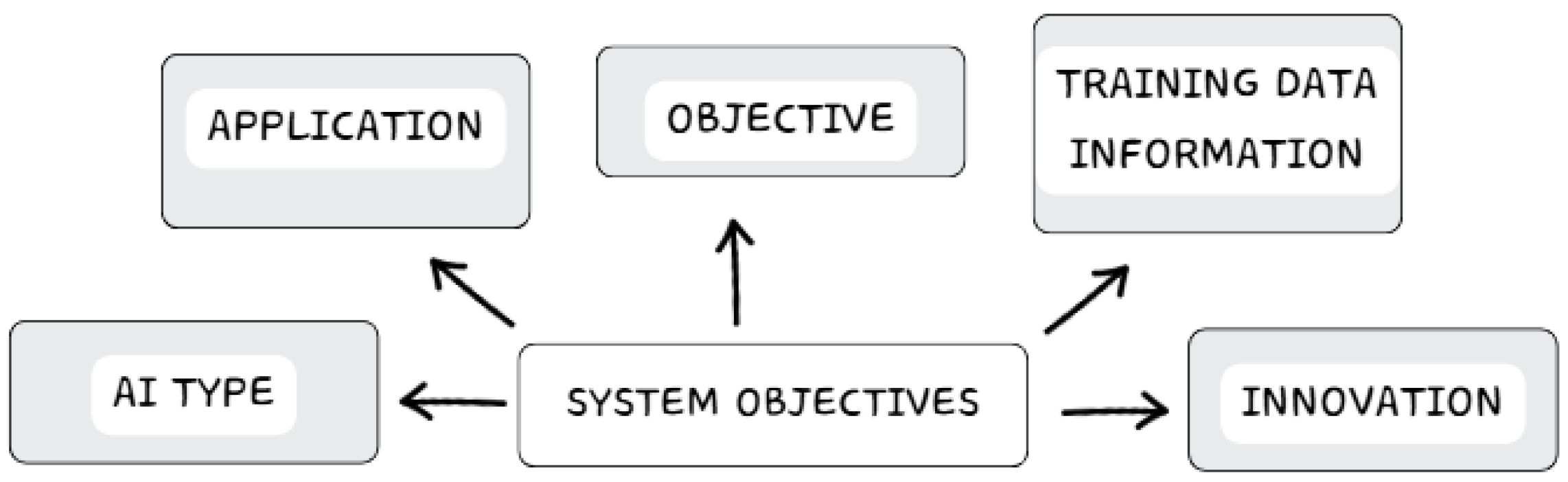
4.1. Criterion 1: System Objectives
- Application: It aligns with the reference title and relates to this publication’s purpose, answering what is intended to be achieved.
- Objective: implemented advantages, improvements, and procedures, detailing the steps to enable their application in tactical communication and networks.
- Innovation: It is helpful to determine whether the reference introduces any concept that has not been seen before or is seldom used, which might be worth noting.
- AI Type: Identify the type of learning model and the algorithm utilized. Adapting a commercial design for a defense system differs significantly when the developed algorithm operates offline and is non-incremental.
- Training Data Information: Understanding the training data is crucial, as it can be inadequate, gathered under controlled conditions, or specific to a scenario. This is vital for supervised algorithms, as the characteristics of the training data can limit the system’s scope and applicability.
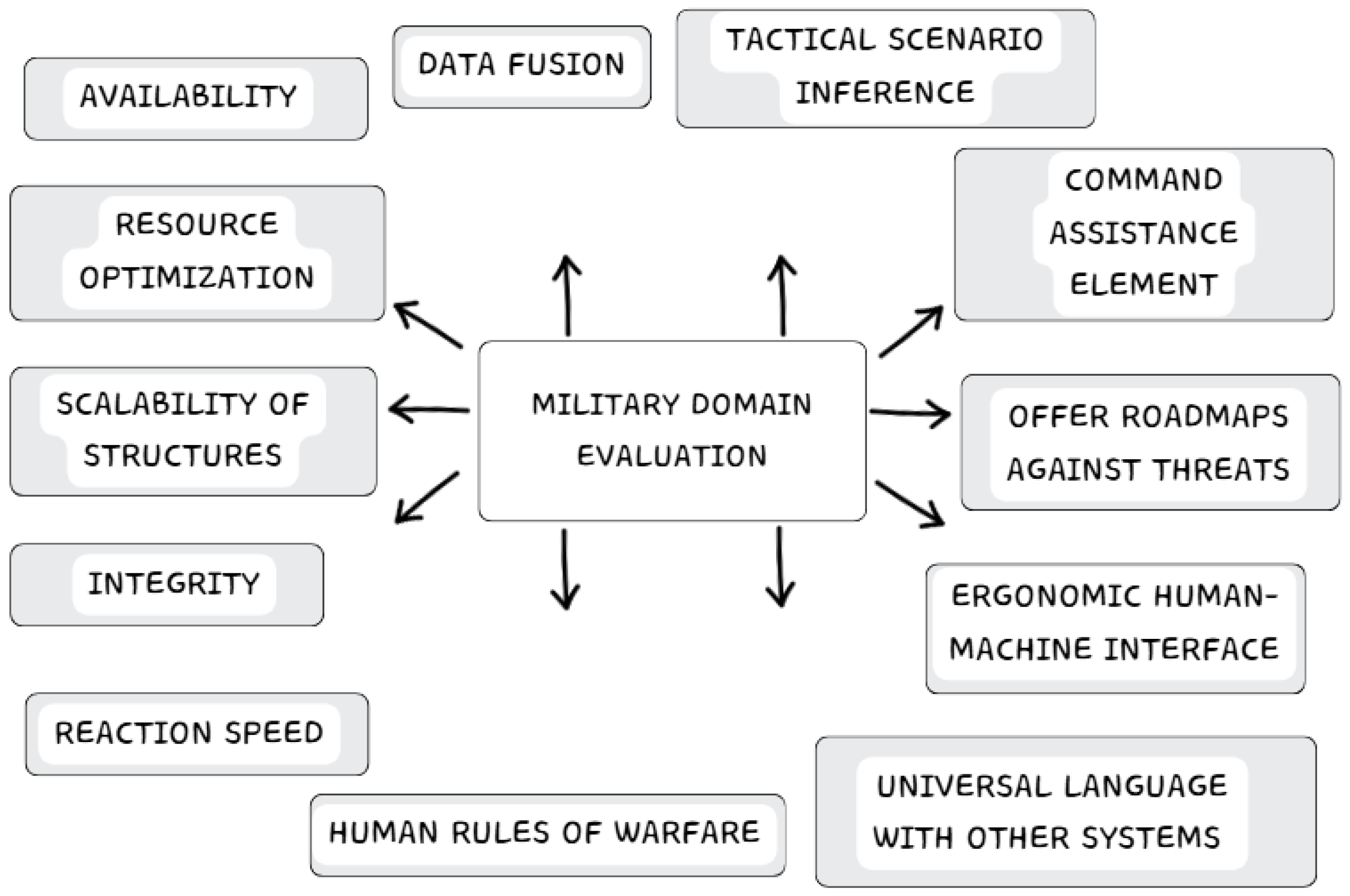
4.2. Criterion 2: Military Domain Evaluation
- Data Fusion: These systems merge information and data from different sources and can process them comprehensively to obtain an accurate and reliable description of the environment. They can describe aspects of a target (speed, heading, size, armor …) or an event (involved personnel, security perimeter, topography, hostile areas …).
- Tactical Scenario Inference: The system must perceive and understand scenario elements, their spatial-temporal placement, and environmental intent. Modern warfare relies on integrated joint combat, coordinating soldiers, drones, tanks, aircraft, ships, and satellites. Combat is multidimensional, requiring commanders to access real-time battlefield data. Effective information processing and distribution across systems is crucial for operational success.
- Command Assistance Element: The decision support system consists of structured and unstructured components. The structured part involves human–machine interaction and data processing, while the unstructured part addresses uncertain and complex scenarios where traditional models cannot effectively represent knowledge. Intelligent systems assist by analyzing warfare models qualitatively. As decision complexity grows, commanders will face an increasing gap between available information and their choices.
- Offer Roadmaps against Threats: AI assists in threat and obstacle avoidance, ensuring fast, efficient path selection. Current methods, such as genetic algorithms and dynamic planning, face challenges when extended to 3D scenarios, as large datasets slow convergence.
- Ergonomic Human–Machine Interface: Command interfaces should deliver timely, intuitive visual information over complex data tables, enhancing operator comprehension and decision-making.
- Universal Language with Other Systems: Unlike human languages in NATO operations, AI-driven machine language ensures seamless interoperability, reducing misinterpretations in multi-system environments.
- Human Rules of Warfare: While AI can enhance autonomy in tactical systems, critical war-related decisions must remain human-controlled, preventing reliance on purely rule-based learning.
- Availability: AI must ensure continuous system uptime and real-time data access; otherwise, its integration adds no operational advantage.
- Resource Optimization: Multi-dimensional combat generates vast data inputs, so AI must balance detail and efficiency to avoid unnecessary computational overload. For example, it would not be necessary to go into maximum detail of a war scenario, training the system with millions of variables, unless absolutely necessary, as this would slow down the system and increase resource consumption.
- Scalability of Structures: As warfare evolves, AI systems must adapt, integrating new actors, data, and strategies without performance degradation.
- Integrity: AI must detect data-manipulation attempts, ensuring consistency, validity, and security during training and operation.
- Reaction speed: AI’s effectiveness in military operations depends on real-time decision-making; delayed responses negate its tactical advantage. The application of AI in military environments is justified if it improves the reaction speed of the command in response to a threat.
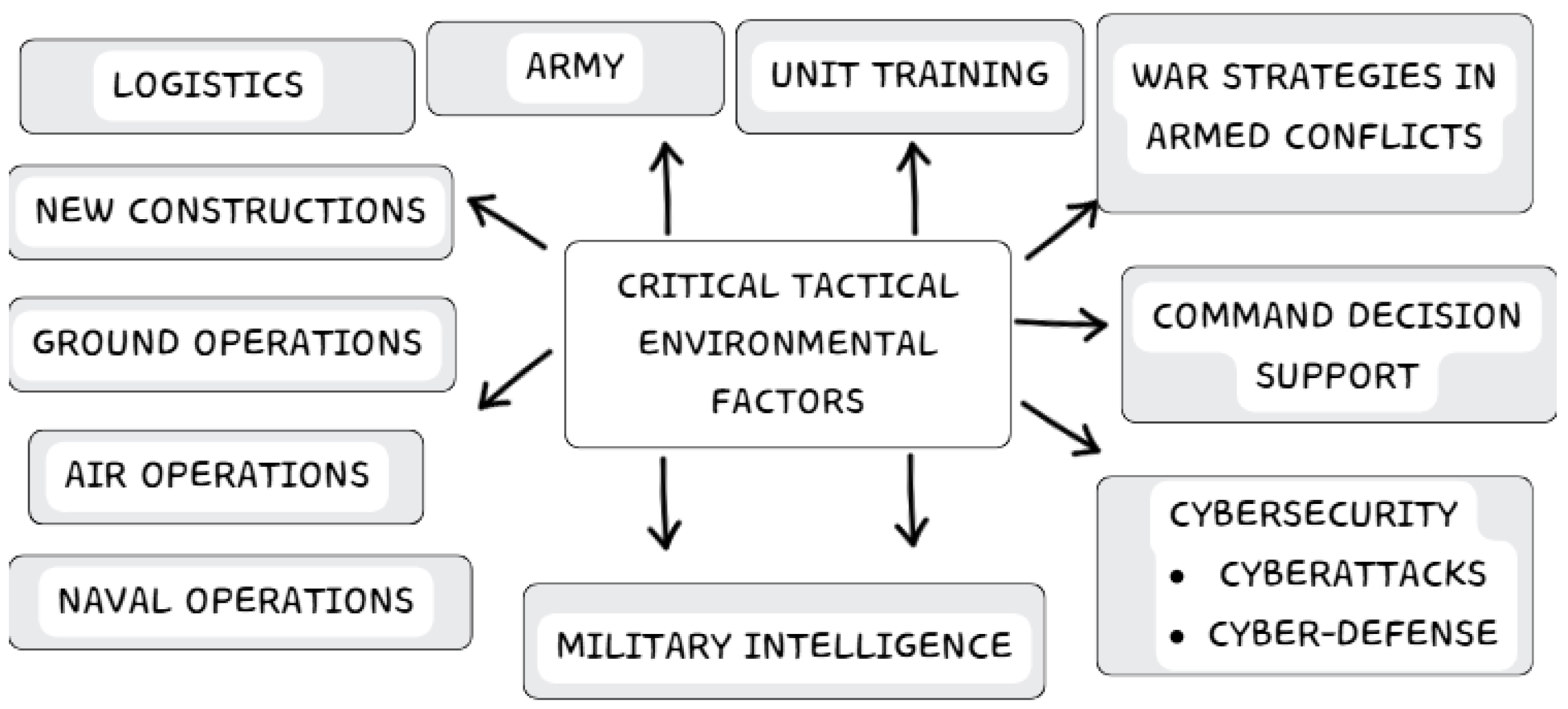
4.3. Criterion 3: Critical Tactical Environmental Factors
- Army: The General Directorate of Armament and Material, under the Secretary of State for Defense, oversees defense projects, aligning military needs with broader defense policies. The army defines technical and operational standards for new systems across air, naval, and ground domains.
- War Strategies in Armed Conflicts: War strategy involves planning military campaigns and troop movements to defeat adversaries. According to International Humanitarian Law (IHL), armed conflict refers to large-scale confrontations causing destruction. This study examines how ML enhances military strategies when integrated into tactical systems.
- Command Decision Support: In potential conflicts, decision-making relies on a secure, collaborative power structure for effective horizontal and vertical communication. AI-driven systems enhance real-time data processing, ensuring timely and accurate decisions.
- Cybersecurity—cyber attacks and cyber defense: Recognized as the fifth military domain at the 2016 NATO summit, cyberspace spans battlefield sensors to C2 networks [54,55]. Traditional security measures (e.g., antivirus, firewalls) now integrate ML for intrusion detection, network access control, and data protection [56]. However, ML is dual-use, serving both cyber defense and offensive cyber attacks, while also being vulnerable to adversarial manipulation.
- Military Intelligence: AI processes vast military datasets (structured, semi-structured, and unstructured) to extract actionable insights. ML clusters intelligence from messages, identity records, and communications to detect military patterns. In aerial and space surveillance, computer vision enables target identification and tracking from satellite and UAV imagery.
- New Constructions: AI applications in warfare predictions may drive adversaries to develop unforeseen strategies and structures, exploiting weaknesses in trained models. AI also enhances manufacturing processes, such as DT simulations, to improve production efficiency.
- Air Operations: Conducted in the aerial domain, these operations involve highly mobile and flexible units for threat deterrence, rapid deployments, and strategic positioning.
- Ground Operations: The primary domain of human activity, hosting key political, economic, and strategic centers [57]. AI-driven analysis supports combat, defense, and stabilization efforts, securing military advantages while fostering conflict resolution strategies.
- Naval Operations: Naval forces provide mobility, availability, and interoperability [58]. Their planning and execution emphasize flexibility, goal alignment, security, and efficiency across various operational levels.
- Logistics: Military logistics involve supply transport, personnel movement, and equipment maintenance. AI optimizes fleet management, predicts anomalies, and improves resource allocation, generating economic savings and operational efficiency.
- Unit Training: Physical military training is costly and inherently risky. AI enables virtual and augmented reality simulations, allowing customized training based on individual combatant performance, improving readiness, and reducing risks.
4.4. Organizing Criteria Answers: A Tabular Approach
- Short Text: Responses of brief description, typically model names, acronyms, or general categories. This is used when a concise label sufficiently conveys the information without additional explanation.
- Descriptive Text: a more detailed explanation is needed without being too lengthy, for example, in descriptions of methodologies or advantages of particular approaches: application and objectives descriptions, or complex descriptive key factors.
- Yes/No: Used for binary responses to indicate the presence or absence of a feature. This is useful for quick verifications, such as whether a model supports a specific functionality.
- Numerical Values: Quantitative indicators such as accuracy, success rates, or performance metrics.
- N/A (Not Available): Used when information is unavailable and/or does not apply to the category. This is common in comparative tables when specific methods are not implemented across all technologies.
5. AI-Driven Tactical Communication and Networks
5.1. Information Network Systems
- Enhanced Situational Awareness: ML algorithms can process sensor data to identify patterns, detect anomalies, and predict adversarial actions, improving battlefield awareness.
- Autonomous Systems: ML enables autonomous drones, surveillance systems, and robotic units to operate with minimal human intervention from information systems.
- Decision Support: ML provides commanders with data-driven recommendations by integrating predictive analytics.
- Cybersecurity: ML fortifies systems against cyber threats by detecting and mitigating unusual network behaviors.
5.2. Image Surveillance Systems
- Enhanced Threat Detection: ML models, such as CNNs, can identify and classify objects like weapons, vehicles, or intruders in real time. For instance, ref. [72] utilized You Only Look Once (YOLO) version 2, YOLOv3, and Faster Region-based CNN (RCNN) Faster-RCNN for automatic weapon detection, demonstrating the potential for rapid and accurate threat identification using CCTV feeds.
- Improved Accuracy: ML aids in reducing false positives and negatives by learning from diverse datasets, including thermal and infrared images. Thermal imaging applications, such as those in [73], leverage models like YOLOv8, achieving a mean Average Precision (mAP) of 96%, even in challenging environmental conditions.
- Anomaly Detection: Algorithms like AutoEncoder (AE) can identify unusual activities or objects, enhancing perimeter security. This capability has been effectively demonstrated in radar-based applications [74], where noise-removal AE improved underwater image quality for better anomaly detection.
- Operational Efficiency: Autonomous systems, powered by ML, can monitor areas continuously with minimal human intervention, optimizing resource utilization. For example, the drone detection systems in [75] employed Faster-RCNN and YOLOv3 models to enable high-accuracy UAV tracking in diverse aerial scenarios.
- Data Fusion and Tactical Insights: ML enables the fusion of multimodal data, such as infrared and visible images, to provide more precise and informative surveillance outputs. As shown in [76], Deep Supervised Generative (DSG)-Fusion techniques allow for integrating multiple image sources, aiding tactical scenario analysis.
- Resource Optimization and Scalability: These systems can scale efficiently to handle increasing data loads while maintaining high performance. For instance, ref. [77] demonstrated real-time military aircraft detection using TensorFlow-based CNNs on large annotated datasets, ensuring scalable and reliable surveillance operations.
5.3. Electronic Warfare Systems
- Enhanced Threat Detection: ML algorithms improve threat detection and classification by analyzing vast datasets to identify patterns and anomalies that may indicate hostile activities. This capability allows for real-time adaptive responses, improving the system’s effectiveness in dynamic environments.
- Automation: ML facilitates the automation of signal-processing tasks, reducing the cognitive load on human operators and increasing operational efficiency. By learning from historical data, ML models can predict and counteract enemy tactics, providing a strategic advantage.
- Adaptation: ML-driven EW systems can continuously evolve, adapting to new threats and technologies without requiring extensive reprogramming. This adaptability ensures that military forces maintain a technological edge over adversaries.
- Integration: The integration of ML into EW systems supports the development of more sophisticated jamming and deception techniques, enhancing the ability to disrupt enemy communications and radar systems. ML significantly increases EW operations’ capability, adaptability, and resilience.
5.4. Radar Systems
- Clutter Suppression: Conventional algorithms struggle to differentiate meaningful targets from environmental noise or clutter in dynamic scenarios like urban areas or rough seas. ML models, trained on diverse datasets, excel at recognizing patterns and suppressing noise, thus improving target detection accuracy.
- Real-Time Adaptability: Radar systems must adapt to rapidly changing environments, such as varying weather conditions or evolving combat scenarios. ML enables systems to learn and adjust quickly, enhancing situational awareness and decision-making capabilities.
- Automation of Complex Tasks: Modern radar systems handle large volumes of data, requiring efficient automation of tasks like anomaly detection, predictive maintenance, and data fusion. ML algorithms provide the computational power and intelligence to automate these processes without compromising accuracy.
- Robust Performance in Complex Environments: ML models can adapt to complex scenarios, including multi-path effects, electromagnetic interference, or high-clutter environments, maintaining high performance where traditional methods falter.
- Enhanced Detection and Classification: ML algorithms significantly improve the detection and classification of targets by learning from extensive datasets. This is particularly useful in distinguishing between similar objects, such as UAVs and birds, or identifying subtle changes in terrain.
- Predictive and Proactive Capabilities: Incorporating ML allows radar systems to predict potential issues, such as equipment failures or evolving threats, enabling proactive measures.
- Increased Efficiency: By automating repetitive or computationally intensive tasks, ML reduces the workload on human operators and accelerates processing speeds, making real-time analysis feasible.
5.5. Unmanned Systems
- Enhancement of Autonomous Decision Making: ML algorithms enable US to process large amounts of data in real time, allowing rapid and accurate responses to dynamic battlefield conditions. This capability reduces the reliance on human operators and improves the speed and precision of military operations.
- Predictive Maintenance: ML models can analyze data from various sensors to predict equipment failures before they occur, thus reducing downtime and maintenance costs. This predictive capability ensures that US remains operational for extended periods, increasing their availability and reliability in critical missions.
- Operation: By integrating data from multiple sources, such as satellite imagery, radar, and on-ground sensors, ML algorithms can provide a comprehensive and coherent picture of the operational environment. This improved situational awareness is crucial for mission planning and execution, enabling more informed and effective decision-making.
- Adaptation: ML contributes to developing adaptive and resilient systems. The US, equipped with ML, can learn from past experiences and adapt its behavior to new and unforeseen challenges. This adaptability is essential in complex and unpredictable military environments, where static programming may fall short.
6. Projects and Defense Industry Integrating AI
6.1. AIDA
6.2. ASTRAEA
- Integrating AI capabilities for decision-making in combat, surveillance, and logistics missions, optimizing the systems’ autonomy and ability to adapt to rapid environmental changes.
- Developing technologies for autonomous air and ground vehicles that operate without direct human intervention. These systems are essential for reconnaissance, exploration, and logistical support missions in conflict zones.
- Ensuring the resilience of systems against cyber attacks and providing the ability to self-diagnose or recover from failures is a key component of the project, ensuring that systems remain uncompromised during critical missions.
6.3. ATLAS
- Data collection on potential types of military targets and performing a prior training of the ML algorithm.
- Imaging processing applying ML techniques for objectives classification, recognition, identification, and tracking.
- Shot control. In this area, advanced guiding algorithms, the automation of the shooting process, and weapon recommendations are fundamental to be used according to the identified objective.
- The technical support integrated into the combat vehicle is necessary due to a high voltage power system (600 Vdc) and the integration of sensors and electronics.
- Sensors. To carry out all needed automatization and provide available actual data for the ML algorithm, tanks are equipped with sensors in the visible spectrum, infrared spectrum (NIR, SWIR, MWIR, and LWIR), 360º rotation of the sensors and rangefinder lasers (LADAR and LIDAR).
6.4. COBRA
- To simulate topology networks and real traffic.
- To develop random and parameterizable scenarios.
- To develop adaptive cyber maneuvers using gamification.
- To validate the entire proposal in the Cyber Range of the Joint Cyberspace of the Ministry of Defence of Spain.
6.5. DARPA
- OFFensive Swarm-Enabled Tactics (OFFSET) [107]: Aims to develop swarms of small autonomous drones capable of operating together to perform reconnaissance, attacks, and rescue missions.
- Lifelong Learning Machines (L2M) [108]: Seeks to use ML to train cybersecurity systems capable of detecting threats and continuously adapting to new attack tactics. Creating autonomous systems that can defend computer networks and protect critical infrastructures against cyber threats.
- AI for Military Operations (AIMO) [109]: A program aimed at developing AI technologies that help improve the precision of military operations and optimize resources. The project also addresses how to integrate AI into joint military operations efficiently.
6.6. General Dynamics
6.7. GIDE
6.8. Iron Dome
- Detection radar: The system uses advanced radars to detect real-time threats such as incoming rockets and missiles. These radars provide high-precision data about the trajectory of the projectiles.
- Battle control center: Once the threat is detected, the system performs an automatic analysis to determine if the projectile is a real threat to the protected areas. If the projectile is deemed capable of causing damage, the system autonomously intercepts it.
- Interceptors: The Iron Dome interceptors are launched to destroy the incoming projectile in the air before it can reach its target. The system has a high success rate, intercepting more than 90% of threats aimed at civilian areas.
6.9. Lockheed Martin
- Autonomy in aircraft and UAV: The use of AI for real-time decision-making during combat or reconnaissance missions
- AI for failure prediction: They use predictive models to anticipate failures in system components, optimizing maintenance.
6.10. Maven
6.11. NORINCO
6.12. Northrop Grumman
6.13. Russia
6.14. SEDA
6.15. SOPRENE
7. Results and Quantitative Insights
- CNNs are more used for strong spatial/spectral patterns (e.g., perception from Electro-Optical/IR/SAR; spectrogram-based RF classification) with moderate, controllable inference latency;
- RNNs/LSTMs/Gated Recurrent Unit are more used for sequence modeling for time-correlated behaviors (traffic/load dynamics, policy rollout), increasingly supplanted by attention on long contexts;
- GNNs are proposed in the literature for topology-aware reasoning (routing, coalition formation, jamming propagation) with message-passing overhead proportional to graph density;
- Transformers are proposed as long-range dependency modeling and cross-modal alignment, with higher memory/compute demands mitigated by pruning/quantization/distillation at the edge.
8. Future Research Directions
8.1. Key Challenges in AI-Driven Military Communications
- Interoperability Across Multidomain Operations: AI-driven military networks must integrate seamlessly across land, air, sea, space, and cyber domains. Current AI models often lack the adaptability required to function efficiently in diverse operational environments, necessitating the development of standardized communication protocols.
- Adversarial Threats, Cybersecurity Risks, and Ethical Considerations: AI-enabled defense networks are vulnerable to EW, cyber attacks, and adversarial AI tactics. Future research must focus on robust AI security mechanisms, encryption-enhanced network resilience, and real-time threat detection algorithms. Ethical concerns surrounding AI in warfare require standardized frameworks and regulations to ensure accountability and compliance (see [6]).
- Data Scarcity and Real-World Adaptability: Military AI models require extensive, high-quality data to enhance learning capabilities. However, access to real-world datasets is restricted due to security concerns. The development of synthetic data generation and simulation-based AI training is crucial to overcoming these limitations. Within the broader data-acquisition discussion, PHY-layer artifacts—such as IQ sample capture and CSI estimation—pose their challenges. Tactical radios already employ mature techniques that mitigate many of these issues; nevertheless, an important research avenue is to extend AI to these processes (e.g., robust estimation, denoising, compression, uncertainty-aware inference) to further improve tactical communications performance under mobility, interference, and spectrum congestion.
- Scalability and Latency in Tactical Communications: AI-driven communication systems must operate in low-latency, high-mobility battlefield environments. Future research should focus on optimizing real-time AI inference, edge computing for tactical units, and decentralized AI architectures to reduce reliance on centralized cloud processing.
- Fusion in information signals: Despite notable progress within single-modality pipelines, we find a persistent gap in end-to-end, AI-enabled multimodal fusion that jointly exploits radar returns, Electro-Optical/IR imagery, and communications-derived metadata to strengthen situational awareness in contested electromagnetic environments. Promising directions include cross-modal Transformers for feature-level alignment/attention and Bayesian fusion networks for uncertainty-aware, decision-level integration. Expected gains are improved interference/clutter suppression, track continuity, and robust target recognition under low SNR and partial observability. However, key barriers remain—precise time/geo-synchronization and calibration across heterogeneous sensors, modality imbalance and missing data, bandwidth/latency limits at the tactical edge, and resilience to deception (decoys/spoofing) in EW/ESM settings. We therefore propose this as a priority future research line for tactical systems, supported by simulation-driven verification with standardized metrics (e.g., probability of detection and/or false alarm under jamming, multi-object tracking, localization Circular Error Probable, end-to-end latency/energy budgets, and uncertainty calibration via Expected Calibration Error/Brier), plus ablations with modality dropouts and spectrum-congestion stress tests, ideally enabled by shareable synthetic multimodal datasets with controllable threat models.
8.2. Emerging Trends in AI for Military Communication Networks
- FL for secure AI model training: Distributed AI training allows allied nations and defense units to develop AI models collaboratively without sharing raw data, improving confidentiality while enhancing AI performance.
- AI-enhanced network resilience and self-healing communications: AI-based autonomous recovery mechanisms can enhance the survivability of battlefield networks by dynamically reconfiguring communication pathways in response to disruptions.
- Cognitive radio and AI-driven spectrum management: AI can optimize spectrum allocation, interference mitigation, and adaptive frequency hopping to ensure uninterrupted military communications in congested or adversarial environments.
- Neuromorphic computing for low-power AI in tactical networks: Neuromorphic computing enables low-power, high-efficiency AI models for real-time signal processing and decision-making in battlefield networks. These architectures offer advantages for on-device intelligence in edge computing environments, allowing UAVs, UGVs, and remote sensors to operate with minimal latency and reduced energy consumption. Future research should explore neuromorphic chips for adaptive AI models in contested electromagnetic environments, ensuring robustness in military operations.
8.3. Strategic Recommendations for Future AI Research in Defense Communications
- Developing Standardized AI Interoperability Frameworks: Establishing unified protocols for AI-driven communication systems will enable seamless integration between different military branches and allied forces. Study of CNN/RNN/GNN/Transformer architectures specifically for tactical radio tasks under standardized, threat-realistic benchmarks. For more about tactical radio, the reader can link to [10] for context.
- Enhancing AI Resilience Against EW and Cyber Threats: Research should prioritize adversarial training, AI-driven jamming detection, and AI-based cyber deception strategies to counteract evolving threats.
- Investment in AI-Powered Tactical Edge Computing: The deployment of AI-enabled edge devices will enhance battlefield decision-making capabilities while reducing dependence on centralized computing infrastructures.
- Advancing AI-Driven UAV and UGV Communications for Tactical Networks: While AI-powered UAVs and UGVs have been successfully deployed for tactical communications, challenges remain in optimizing their network coordination, adaptability, and resilience in contested environments. Future research should focus on enhancing real-time adaptive routing, developing self-learning communication protocols, and integrating AI-based dynamic spectrum allocation to improve interoperability across multidomain operations. Additionally, advancements in federated learning and neuromorphic computing could enable greater autonomy and efficiency in UAV-UGV communication networks, ensuring seamless integration with existing defense infrastructure.
- Strengthening Civilian-Military AI Collaboration: Encouraging partnerships between defense agencies, academic institutions, and private AI developers can accelerate innovation in military communication technologies.
9. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 5G | 5th Generation | AR | Augmented Reality |
| A2A | Aerial to Aerial | ATLAS | Advanced Targeting and Lethality Automated System |
| A2G | Aerial to Ground | C2 | Command and Control |
| AE | AutoEncoder | C2IS | C2 Information Systems |
| AESA | Active Electronically Scanned Array | C4ISR | C2 Communications Computers ISR |
| AI | Artificial Intelligence | CCD | Charge-Coupled Device |
| AIDA | Artificial Intelligence Deployable Agent | CCTV | Closed-Circuit Television |
| AIMO | AI for Military Operations | CCW | Convention on Certain Conventional Weapons |
| AMDR | Air and Missile Defense Radar | CEW | Cognitive Electronic Warfare |
| ANN | Artificial Neural Networks | CFAR | Constant False Alarm Rate |
| cGAN | Conditional Generative Adversarial Network | MARL | Multi-agent reinforcement learning |
| CIT | Configured Item Tree | MDM | Mobile Device Management |
| CL | Cooperative Learning | MIMO | Multiple-Input Multiple-Output |
| CNN | Convolutional Neural Network | ML | Machine Learning |
| COF | Cost Objective Function | MLP | Multi-Layer Perceptron |
| CSI | Channel State Information | MLOp | ML Operations |
| DARPA | Defense Advanced Research Projects Agency | MNN | Multi-Layer Neural Networks |
| DDPG | Deep Deterministic Policy Gradient Algorithm | MWIR | Mid-Wave Infrared |
| DIL | Disconnected Intermittent and Limited | N/A | Not Available |
| DL | Deep Learning | NAC | Network Access Control |
| DLP | Data Loss Prevention | NATO | North Atlantic Treaty Organization |
| DNN | Deep Neural Networks | NGO | Non-Governmental Organization |
| DQN | Deep Q-Network | NIR | Near Infrared |
| DRL | Deep Reinforcement Learning | NLP | Natural Language Processing |
| DSG | Deep Supervised Generative | PSO | Particle Swarm Optimization |
| DT | Digital Twin | QoE | Quality of Experience |
| ECM | Electronic Countermeasures | QoS | Quality of Service |
| EPM | Electronic Protective Measures | RCNN | Region-based CNN |
| ESM | Electronic Support Measures | RCS | Radar Cross Section |
| EW | Electronic Warfare | RCV | Robotic Combat Vehicle |
| FL | Federated Learning | RF | Random Forest |
| FSO | Free Space Optics | RIS | Reconfigurable Intelligent Surfaces |
| G2A | Ground to Aerial | RL | Reinforcement Learning |
| GA | Genetic algorithms | RMA | Radar Modular Assemble |
| GaN | Gallium Nitride | RNN | Recurrent Neural Network |
| GAN | Generative Adversarial Network | ROI | Region of Interest |
| GenAI | Generative AI | SA | Situational Awareness |
| GEOINT | Geospatial Intelligence | SAR | Synthetic Aperture Radar |
| GGE | Group of Governmental Experts | SDR | Software Defined Radio |
| GIDE | Global Information Dominance Experiment | SEDA | SatEllite Data Ai |
| GNN | Graph Neural Network | SL | Supervised Learning |
| GNSS | Global Navigation Satellite System | SNN | Spiking Neural Network |
| GPS | Global Positioning System | SNR | Signal-to-Noise Ratio |
| HMFFNet | Hybrid Model featuring a Feature Fusion Network | SSL | Semi-supervised Learning |
| ICMP | Integrated Class Maintenance Plan | SVM | Support Vector Machines |
| IDS | Intrusion Detection System | SWIR | Short-Wave Infrared |
| IED | Improvised Explosive Device | TAK-ML | Tactical Assault Kit-ML |
| IHL | International Humanitarian Law | U.S. | United States |
| IoBT | Internet of Battlefield Things | UAS | Unmanned Aerial System |
| IoT | Internet of Things | UAV | Unmanned Aerial Vehicle |
| IPS | Intrusion Prevention System | UGV | Unmanned Ground Vehicle |
| IR | Infra Red | UL | Unsupervised Learning |
| ISR | Intelligence Surveillance and Reconnaissance | US | Unmanned Systems |
| JREAP | Joint Range Extension Application Protocol | MUS | Maritime Unmanned Systems |
| KNN | K-Nearest Neighbors | VGG | Visual Geometry Group |
| L2M | Lifelong Learning Machines | VMF | Variable Message Format |
| LAWS | Lethal Autonomous Weapon Systems | XAI | Explainable AI |
| LFPSO | Levy Flight Particle Swarm Optimization | YOLO | You Only Look Once |
| LLM | Large Language Model | LSTM | Long Short-Term Memory |
| LVC | Live-Virtual-Constructive | LWIR | Long-Wave Infrared |
| mAP | Mean Average Precision |
References
- Anastasiou, T.; Pastellas, I.; Karagiorgou, S. Adversarial Explanations for Informed Civilian and Environmental Protection. In Proceedings of the 2024 IEEE International Conference on Big Data (BigData), Washington, DC, USA, 15–18 December 2024; pp. 2672–2681. [Google Scholar] [CrossRef]
- He, Y.; Huang, F.; Jiang, X.; Nie, Y.; Wang, M.; Wang, J. Foundation Model for Advancing Healthcare: Challenges, Opportunities and Future Directions. IEEE Rev. Biomed. Eng. 2025, 18, 172–191. [Google Scholar] [CrossRef]
- Hamissi, A.; Dhraief, A.; Sliman, L. A Comprehensive Survey on Conflict Detection and Resolution in Unmanned Aircraft System Traffic Management. IEEE Trans. Intell. Transp. Syst. 2025, 26, 1395–1418. [Google Scholar] [CrossRef]
- Fontanesi, G.; Ortiz, F.; Lagunas, E.; Garcés-Socarrás, L.M.; Monzon Baeza, V.; Vázquez, M.A. Artificial Intelligence for Satellite Communication: A Survey. IEEE Commun. Surv. Tutor. 2025; Early Access. 1. [Google Scholar] [CrossRef]
- Datumaya Wahyudi Sumari, A. Smart Military Society: Defining the characteristics to score the “Smart” of the military services. In Proceedings of the International Conference on ICT for Smart Society, Jakarta, Indonesia, 13–14 June 2013; pp. 1–8. [Google Scholar] [CrossRef]
- Alcántara Suárez, E.J.; Monzon Baeza, V. Evaluating the Role of Machine Learning in Defense Applications and Industry. Mach. Learn. Knowl. Extr. 2023, 5, 1557–1569. [Google Scholar] [CrossRef]
- Hu, C.; Zhao, Y.; Wang, Z.; Du, H.; Liu, J. Games for Artificial Intelligence Research: A Review and Perspectives. IEEE Trans. Artif. Intell. 2024, 5, 5949–5968. [Google Scholar] [CrossRef]
- Chen, Z.; Zhu, J. Intelligent inference in combat simulation systems based on key feature extraction and uncertainty interval estimation. IEEE Trans. Instrum. Meas. 2025, 74, 3507912. [Google Scholar] [CrossRef]
- Baeza, V.M.; Salor, L.C. New horizons in tactical communications: An overview of emerging technologies possibilities. IEEE Potentials 2024, 43, 12–19. [Google Scholar] [CrossRef]
- Concha Salor, L.; Monzon Baeza, V. Harnessing the Potential of Emerging Technologies to Break down Barriers in Tactical Communications. Telecom 2023, 4, 709–731. [Google Scholar] [CrossRef]
- Creus, J.G.; Baeza, V.M. Exploiting the Digital Twin Technology Advantages over Telemetry Data in GNSS. IEEE Netw. 2025, Early Access. 1. [Google Scholar] [CrossRef]
- Mikhailov, D.I. Optimizing National Security Strategies through LLM-Driven Artificial Intelligence Integration. arXiv 2023, arXiv:2305.13927. [Google Scholar] [CrossRef]
- Army, U. Smart Logistics: Navigating the AI Frontier in Sustainment Operations. Available online: https://www.army.mil/article/280377/smart_logistics_navigating_the_ai_frontier_in_sustainment_operations (accessed on 15 July 2025).
- Lingel, S.; Hagen, J.; Hastings, E.; Lee, M.; Sargent, M.; Walsh, M.; Zhang, L.A.; Blancett, D. Joint All Domain Command and Control for Modern Warfare: An Analytic Framework for Identifying and Developing Artificial Intelligence Applications; Technical Report; Defense Technical Information Center, 1 July 2020; Available online: https://www.rand.org/pubs/research_reports/RR4408z1.html (accessed on 27 August 2025).
- Campbell, L.; Lotmin, A.; DeRico, M.M.G.; Ray, C. The use of Artificial Intelligence in military simulations. In Proceedings of the IEEE International Conference on Systems, Man, and Cybernetics. Computational Cybernetics and Simulation, Orlando, FL, USA, 12–15 October 1997; Volume 3, pp. 2607–2612. [Google Scholar] [CrossRef]
- Bistron, M.; Piotrowski, Z. Artificial Intelligence Applications in Military Systems and Their Influence on Sense of Security of Citizens. Electronics 2021, 10, 871. [Google Scholar] [CrossRef]
- Ammar, M.A.; Abdel-Latif, M.S.; Badran, K.M.; Hassan, H.A. Deep learning Achievements and Opportunities in Domain of Electronic Warfare Applications. In Proceedings of the Tenth ICICIS, Greater Noida, India, 15–16 March 2021; pp. 41–50. [Google Scholar] [CrossRef]
- Rawat, D.B. Artificial Intelligence Meets Tactical Autonomy: Challenges and Perspectives. In Proceedings of the IEEE 4th International Conference on CogMI, Atlanta, GA, USA, 14–17 December 2022; pp. 49–51. [Google Scholar] [CrossRef]
- Jyothi, A.P.; Shankar, A.; Narayan, A.J.R.; Bhavya, K.; Reddy, M.S.; Yashwanth, A. AI Methodologies in Upcoming Modern Warfare Systems. In Proceedings of the 2022 IEEE CCET, Bhopal, India, 23–24 December 2022; pp. 1–7. [Google Scholar] [CrossRef]
- Ali, A.; Farid, A.; Al-kassem, A.H.; Khan, Z.A.; Qamer, M.; Ghouri, K.F.K. Development and use of Artificial Intelligence in the Defense Sector. In Proceedings of the 2023 ICBATS, Dubai, United Arab Emirates, 7–8 March 2023; pp. 1–10. [Google Scholar] [CrossRef]
- Jyothi, A.P.; Shankar, A.; Narayan, A.J.R.; Bhavya, K.; Yadav, S.M.M. AI & ML Methodologies in Navy & their Systems. In Proceedings of the 2023 EASCT, Bengaluru, India, 20–21 October 2023; pp. 1–6. [Google Scholar] [CrossRef]
- Oliveira, E.; Rodrigues, M.; Pereira, J.P.; Lopes, A.M.; Mestric, I.I.; Bjelogrlic, S. Unlabeled learning algorithms and operations: Overview and future trends in defense sector. Artif. Intell. Rev. 2024, 57, 66. [Google Scholar] [CrossRef]
- Pakholchuk, V.; Horiacheva, K. Methodological Concepts of Applying AI into Military and Economic Capabilities Data Analysis. 2024. CNDCGS’2024; Num. 1. Volume 1. Available online: https://journals.unob.cz/index.php/CNDCGS/article/view/2088 (accessed on 27 August 2025).
- Sebastian, L.; Axel, S. Enhancing Tactical Military Mission Execution through Human-AI Collaboration: A View on Air Battle Management Systems. In Proceedings of the IEEE 4th ICHMS, Toronto, ON, Canada, 15–17 May 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Arrabito, R.; Hou, M.; Fischmeister, S.; Falk, T.H.; Willoughby, H.; Cameron, M. Tracking user trust and mental states during cyber-attacks: A survey of existing methods and future research directions on AI-enabled decision-making for the Royal Canadian Navy. In Proceedings of the IEEE 4th ICHMS, Toronto, ON, Canada, 15–17 May 2024; pp. 1–4. [Google Scholar] [CrossRef]
- Patil, A.T.; Vidhale, B.; Titarmare, A. Strategic Innovations in Defense Systems: A Comprehensive Analysis of Emerging Technologies and Future Trends. In Proceedings of the ISCS, Gurugram, India, 3–4 May 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Hagos, D.H.; Rawat, D.B. Neuro-Symbolic AI for Military Applications. IEEE Trans. Artif. Intell. 2024, 5, 6012–6026. [Google Scholar] [CrossRef]
- Hadlington, L.; Binder, J.; Gardner, S.; Knight, S. The use of Artificial Intelligence in a military context: Development of the attitudes toward AI in defense (AAID) scale. Front. Psychol. 2023, 14, 1164810. [Google Scholar] [CrossRef] [PubMed]
- Wang, W.; Liu, H.; Lin, W.; Chen, Y.; Yang, J.-A. Investigation on Works and Military Applications of Artificial Intelligence. IEEE Access 2020, 8, 131614–131625. [Google Scholar] [CrossRef]
- AlphaStar. AlphaStar: Mastering the Real-Time Strategy Game StarCraft. Available online: https://www.deepmind.com/blog/alphastar-mastering-the-real-time-strategy-game-starcraft-ii (accessed on 15 July 2025).
- Martín, J.A.R. IMF, Blog de Tecnología. Artículo Google Imágenes y el Machine Learning Que Todo Lo Ve. Available online: https://blogs.imf-formacion.com/blog/tecnologia/google-imagenes-cerebro-electronico-lo-ve/ (accessed on 15 July 2025).
- Gamarra, G. Profesional Review—Artículo las 5 Mejores Aplicaciones de Reconocimiento de Voz. Available online: https://www.profesionalreview.com/2016/08/17/5-mejores-aplicaciones-reconocimiento-voz/ (accessed on 15 July 2025).
- Kumar, A. Neural Network Types & Real-Life Examples. Available online: https://vitalflux.com/deep-neural-network-examples-from-real-life/ (accessed on 15 July 2025).
- Center, B.S. MareNostrum5: A new EuroHPC World-Class Supercomputer in Spain. Available online: https://www.bsc.es/news/bsc-news/marenostrum5-new-eurohpc-world-class-supercomputer-spain (accessed on 15 July 2025).
- Estapé, J.A.P. Computer hoy. Artículo IBM Summit: Así es el Superordenador Más Potente del Mundo. Available online: https://computerhoy.com/reportajes/tecnologia/ibm-summit-superordenador-mas-potente-del-mundo-627963 (accessed on 15 July 2025).
- Hemsoth, N. NextPlatform. Artículo CHINA YA HA ALCANZADO LA EXAESCALA, EN DOS SISTEMAS SEPARADOS. Available online: https://www.nextplatform.com/2021/10/26/china-has-already-reached-exascale-on-two-separate-systems/ (accessed on 15 July 2025).
- Geron, A. Hands-on Machine Learning with Scikit-Learn, Keras, and TensorFlow: Concepts, Tools, and Techniques to Build Intelligent Systems, 2nd ed.; O’Reilly Media: Sebastopol, CA, USA, 2019. [Google Scholar]
- Bobadilla, J. Machine Learning y Deep Learning Usando Python, Scikit y Keras; Ediciones de la U: Bogotá, Colombia, 2020. [Google Scholar]
- Martínez, A. OSINT—La información es Poder. Available online: https://www.incibe.es/incibe-cert/blog/osint-la-informacion-es-poder (accessed on 15 July 2025).
- Tecnobit. Procesador Data Link Multi-Protocolo (LINPRO). Available online: https://grupooesia.com/casos-de-exito/instalacion-linpro-armada-holandesa/ (accessed on 15 July 2025).
- SYSCOM. ¿Quién Inventó el Primer Sistema de CCTV? Available online: https://www.syscomblog.com/2021/11/quien-invento-el-primer-sistema-de-cctv.html (accessed on 15 July 2025).
- Elias, R. Sistemas de CCTV, Más Allá de la Seguridad. Available online: https://www.interempresas.net/Seguridad/Articulos/247951-Sistemas-de-CCTV-mas-alla-de-la-seguridad.html (accessed on 15 July 2025).
- Caught on Camera. What Are the Different Types of CCTV Camera? Available online: https://www.caughtoncamera.net/news/different-types-of-cctv/ (accessed on 15 July 2025).
- Spanish Ministry of Defense Regimiento de Guerra Electronica 31. Available online: https://ejercito.defensa.gob.es/ca/unidades/Madrid/rew31/Organizacion/index.html (accessed on 15 July 2025).
- García, J.M.N. El sistema de Guerra electróNica de la Fragata F-110. Available online: https://www.defensa.com/espana/sistema-guerra-electronica-fragata-f-110 (accessed on 15 July 2025).
- de Canales Martínez, M.G. Desarrollo de un Sistema de Guerra Electrónica para la Detección y Perturbación de Radares Marinos en Banda X. Master’s Thesis, University of Vigo, Vigo, Spain, 2020. [Google Scholar]
- Parker Sanfuentes, J. Radar History. Available online: https://revistamarina.cl/revistas/2000/1/jparkers.pdf (accessed on 15 July 2025).
- Wolff, C. Radar Tutorial. Available online: https://www.radartutorial.eu/02.basics/rp10.es.html (accessed on 15 July 2025).
- Martin, L. SPY-7 Is the Backbone of Multiple Defense Systems on Land, Air & Sea. Available online: https://www.lockheedmartin.com/en-us/products/spy-7.html (accessed on 15 July 2025).
- Wikipedia. AN/SPY-6. Available online: https://en.wikipedia.org/wiki/AN/SPY-6 (accessed on 15 July 2025).
- Boschetti, N.; Nikas, I.; Sharma, S.; Falco, G. A Global Ionosphere Situational Awareness Architecture for Over the Horizon Radar Operations. In Proceedings of the 2024 IEEE Aerospace Conference, Big Sky, MT, USA, 2–9 March 2024; pp. 1–9. [Google Scholar] [CrossRef]
- Cuerno-Rejado, C.; García-Hernández, L.; Sánchez-Carmona, A.; Carrio, A.; Sanchez-López, J.L.; Campoy, P. Historical Evolution of the Unmanned Aerial Vehicles to the Present. Dyna 2016, 91, 282–288. [Google Scholar] [CrossRef]
- Flir, T. FLIR. Available online: https://www.flir.es/products/black-hornet-3/?vertical=uas-norway&segment=uis (accessed on 15 July 2025).
- Sande, C.A.S. Operaciones en el Ciberespacio. Available online: https://www.ccn-cert.cni.es/pdf/documentos-publicos/xiii-jornadas-stic-ccn-cert/ponencias/4390-s16-11-02-planeamiento-operaciones-en-el-ciberespacio/file.html (accessed on 15 July 2025).
- Zhang, Y.; Dai, Z.; Zhang, L.; Wang, Z.; Chen, L.; Zhou, Y. Application of Artificial Intelligence in Military: From Projects View. In Proceedings of the 2020 6th International Conference on BigDIA, Shenzhen, China, 4–6 December 2020; pp. 113–116. [Google Scholar] [CrossRef]
- Ágreda, A.G. Usos Militares de la Inteligencia Artificial, la Automatización y la Robótica (IAA&R). Available online: https://emad.defensa.gob.es/Galerias/CCDC/files/USOS_MILITARES_DE_LA_INTELIGENCIA_ARTIFICIALx_LA_AUTOMATIZACION_Y_LA_ROBOTICA_xIAAxRx.-_VV.AA.pdf (accessed on 15 July 2025).
- Benson, C.B. Operaciones Terrestres Unificadas: La Evolución de la Doctrina del Ejército Para Lograr el éXito en el Siglo XXI. Available online: https://www.armyupress.army.mil/Portals/7/military-review/Archives/Spanish/MilitaryReview_20120630_art005SPA.pdf (accessed on 15 July 2025).
- del Río, J.M.D.D. Concepto de Operaciones Navales. Available online: https://www.ieee.es/Galerias/fichero/OtrasPublicaciones/Nacional/2015/ArmadaEspanola_COPNAV.pdf (accessed on 15 July 2025).
- Möhlenhof, T.; Jansen, N.; Rachid, W. Reinforcement Learning Environment for Tactical Networks. In Proceedings of the 2021 International Conference ICMCIS, The Hague, The Netherlands, 4–5 May 2021; pp. 1–8. [Google Scholar] [CrossRef]
- Karim, H.; Rawat, D.B. Evaluating Machine Learning Classifiers for Data Sharing in Internet of Battlefield Things. In Proceedings of the 2021 IEEE SSCI, Orlando, FL, USA, 5–7 December 2021; pp. 1–7. [Google Scholar] [CrossRef]
- Aghabeiki, S.; Hallet, C.; Noutehou, E.-R.; Rassem, N.; Adjali, I.; Mabrouk, M.B. Machine-learning-based spectrum sensing enhancement for software-defined radio applications. In Proceedings of the 2021 IEEE Cognitive Communications for Aerospace Applications Workshop (CCAAW), Cleveland, OH, USA, 21–23 June 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Freiberg, M.; McLaughlin, K.; Ningtyas, A.; Taylor, O.; Adams, S.; Beling, P.A. Enemy Location Prediction in Naval Combat Using Deep Learning. In Proceedings of the 2021 Systems and Information Engineering Design Symposium (SIEDS), Charlottesville, VA, USA, 29–30 April 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Intizhami, N.S.; Husodo, A.Y.; Jatmiko, W. Warfare Simulation: Predicting Battleship Winner Using Random Forest. In Proceedings of the 2019 IEEE International Conference on Communication, Networks and Satellite (Comnetsat), Makassar, Indonesia, 1–3 August 2019; pp. 30–34. [Google Scholar] [CrossRef]
- Chin, P.; Do, E.; Doucette, C.; Kalashian, B.; Last, S.; Lenz, N. TAK-ML: Applying Machine Learning at the Tactical Edge. In Proceedings of the MILCOM 2021—2021 IEEE Military Communications Conference (MILCOM), San Diego, CA, USA, 29 November–2 December 2021; pp. 108–114. [Google Scholar] [CrossRef]
- Hu, D.; Yang, R.; Zuo, J.; Zhang, A.; Wu, J.; Wang, Y. Application of Deep Reinforcement Learning in Maneuver Planning of Beyond-Visual-Range Air Combat. IEEE Access 2021, 9, 32282–32297. [Google Scholar] [CrossRef]
- Qu, T.; Xiong, G.; Dong, X.; Li, W.; Tao, H.; Yan, J. Missile Defense Decision-Making under Incomplete Information Using The Artificial Neural Network. In Proceedings of the 2021 IEEE 17th International Conference on Automation Science and Engineering (CASE), Lyon, France, 23–27 August 2021; pp. 1825–1830. [Google Scholar] [CrossRef]
- Faisal, K.M.; Choi, W. Machine Learning Approaches for Reconfigurable Intelligent Surfaces: A Survey. IEEE Access 2022, 10, 27343–27367. [Google Scholar] [CrossRef]
- Loevenich, J.F.; Lopes, R.R.F. DRL meets GNN to improve QoS in Tactical MANETs. In Proceedings of the NOMS 2024-2024 IEEE Network Operations and Management Symposium, Seoul, Republic of Korea, 6–10 May 2024; pp. 1–4. [Google Scholar] [CrossRef]
- Dimitriu, A.; Michaletzky, T.V.; Remeli, V.; Tihanyi, V.R. A Reinforcement Learning Approach to Military Simulations in Command: Modern Operations. IEEE Access 2024, 12, 77501–77513. [Google Scholar] [CrossRef]
- Álvaro González, J.; García, A.M.S.; Baeza, V.M. Blockchain-Enabled Management Framework for Federated Coalition Networks. arXiv 2025, arXiv:cs.CR/2503.09666. [Google Scholar]
- Kadam, P.; Vora, D.; Mishra, S.; Patil, S.; Kotecha, K.; Abraham, A. Recent Challenges and Opportunities in Video Summarization With Machine Learning Algorithms. IEEE Access 2022, 10, 122762–122785. [Google Scholar] [CrossRef]
- Bhatti, M.T.; Khan, M.G.; Aslam, M.; Fiaz, M.J. Weapon Detection in Real-Time CCTV Videos Using Deep Learning. IEEE Access 2021, 9, 34366–34382. [Google Scholar] [CrossRef]
- Elgohary, R.; Mahmoud, A.K.; Khaled, O.; Salah, S.; Badawi, M.B. Enhanced Thermal Human Detection in Military Applications Using Deep Learning. In Proceedings of the 2024 ITC-Egypt, Cairo, Egypt, 22–25 July 2024; pp. 91–98. [Google Scholar] [CrossRef]
- Illig, D.W.; Kocan, K.X.; Mullen, L.J. Machine Learning Applied to the Underwater Radar-Encoded Laser System. In Proceedings of the Global Oceans 2020: Singapore—U.S. Gulf Coast, Biloxi, MS, USA, 5–30 October 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmad, H.; Farhan, M.; Farooq, U. Computer Vision Techniques for Military Surveillance Drones. Wasit J. Comput. Math. Sci. 2023, 2, 53–59. [Google Scholar] [CrossRef]
- Yang, X.; Huo, H.; Li, J.; Li, C.; Liu, Z.; Chen, X. DSG-Fusion: Infrared and visible image fusion via generative adversarial networks and guided filter. Expert Syst. Appl. 2022, 200, 116905. [Google Scholar] [CrossRef]
- Sampath, P.; Haseeb, S.; Jaideep, A.; Kiran, J.P.; Devi, S.A.; Srinivas, P.V.V.S. Revolutionizing Military Surveillance: Advanced Deep Learning Techniques for Aircraft Detection. In Proceedings of the 2023 ICSCSS, Coimbatore, India, 14–16 June 2023; pp. 12–19. [Google Scholar] [CrossRef]
- Gacche, P.; Kokare, M.; Rathod, S.M.; Arulprasath, K.; Rathod, S.; Sharma, A. Foreign Object Detection and Classification using AI and ML for Radio Images. In Proceedings of the 2022 International Conference IConSIP, Pune, India, 26–27 August 2022; pp. 1–5. [Google Scholar] [CrossRef]
- Legendre, D.; Vankka, J. Military Vehicle Recognition with Different Image Machine Learning Techniques. In Information and Software Technologies, Proceedings of the 26th International Conference, ICIST 2020, Kaunas, Lithuania, 15–17 October 2020; Springer: Cham, Switzerland, 2020; pp. 220–242. [Google Scholar]
- McWhorter, T.; Morys, M.; Severyn, S.; Stevens, S.; Chan, L.; Cheng, C.-H. Machine Learning Aided Electronic Warfare System. IEEE Access 2021, 9, 94691–94699. [Google Scholar] [CrossRef]
- You, S.; Diao, M.; Gao, L. Deep Reinforcement Learning for Target Searching in Cognitive Electronic Warfare. IEEE Access 2019, 7, 37432–37447. [Google Scholar] [CrossRef]
- Jarvis, D.E. Machine Learning of an Approximate Morphism of an Electronic Warfare Simulation Component. In Proceedings of the 2020 Spring Simulation Conference (SpringSim), Fairfax, VA, USA, 19–21 May 2020; pp. 1–12. [Google Scholar] [CrossRef]
- Shao, G.; Chen, Y.; Wei, Y. Convolutional Neural Network-Based Radar Jamming Signal Classification With Sufficient and Limited Samples. IEEE Access 2020, 8, 80588–80598. [Google Scholar] [CrossRef]
- Siemuri, A.; Selvan, K.; Kuusniemi, H.; Valisuo, P.; Elmusrati, M.S. A Systematic Review of Machine Learning Techniques for GNSS Use Cases. IEEE Trans. Aerosp. Electron. Syst. 2022, 58, 5043–5077. [Google Scholar] [CrossRef]
- Lee, G.-H.; Jo, J.; Park, C.H. Jamming Prediction for Radar Signals Using Machine Learning Methods. Secur. Commun. Netw. 2020, 2020, 2151570. [Google Scholar] [CrossRef]
- Satapathy, J.R.; Bodade, R.M.; Ayeelyan, J. CNN based Modulation classifier and Radio Fingerprinting for Electronic Warfare Systems. In Proceedings of the 2024 4th International Conference on Advance Computing and Innovative Technologies in Engineering (ICACITE), Greater Noida, India, 14–15 May 2024; pp. 1880–1885. [Google Scholar] [CrossRef]
- Wrabel, A.; Graef, R.; Brosch, T. A Survey of Artificial Intelligence Approaches for Target Surveillance With Radar Sensors. IEEE Aerosp. Electron. Syst. Mag. 2021, 36, 26–43. [Google Scholar] [CrossRef]
- Lee, H.; Kim, C.F.; Kim, M.-S.; Kim, Y.-H.; Park, H.-K.; Lee, J.-S. Fault Detection of Air Defense Radar Systems Using Machine Learning. In Proceedings of the 2024 18th International Conference on Ubiquitous Information Management and Communication (IMCOM), Kuala Lumpur, Malaysia, 3–5 January 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Oveis, A.H.; Giusti, E.; Ghio, S.; Martorella, M. A Survey on the Applications of Convolutional Neural Networks for Synthetic Aperture Radar: Recent Advances. IEEE Aerosp. Electron. Syst. Mag. 2022, 37, 18–42. [Google Scholar] [CrossRef]
- Kellett, J.; Dawber, W.; Wallace, W.; Branson, J. Multifunction Maritime Radar and RF Systems—Technology Challenges and Areas of Development. IEEE Aerosp. Electron. Syst. Mag. 2022, 37, 6–20. [Google Scholar] [CrossRef]
- Rizvi, S.M.D.; Ahmad, S.; Khan, K.; Hasan, A.; Masood, A. Deep Learning Approach for Fixed and Rotary-Wing Target Detection and Classification in Radars. IEEE Aerosp. Electron. Syst. Mag. 2022, 37, 32–42. [Google Scholar] [CrossRef]
- Ma, L.; Zhang, Y.; Leiva, V.; Liu, S.; Ma, T. A new clustering algorithm based on a radar scanning strategy with applications to machine learning data. Expert Syst. Appl. 2022, 191, 116143. [Google Scholar] [CrossRef]
- Hu, J.; Wei, Z.; Li, Y.; Li, H.; Wu, J. Designing Unimodular Waveform(s) for MIMO Radar by Deep Learning Method. IEEE Trans. Aerosp. Electron. Syst. 2021, 57, 1184–1196. [Google Scholar] [CrossRef]
- Yavuz, F. Radar Target Detection with CNN. In Proceedings of the 2021 29th EUSIPCO, Dublin, Ireland, 23–27 August 2021; pp. 1581–1585. [Google Scholar] [CrossRef]
- Ozdemir, M.R.; Kucuk, A.F.; Inalhan, G.; Baspinar, B.; Ertekin, S. Machine Learning Based Radar Cross-Section Clustering Towards Enhanced Situational Awareness for Next-Generation Fighter Aircraft. In Proceedings of the 2024 AIAA DATC/IEEE 43rd DASC, San Diego, CA, USA, 29 September–3 October 2024; pp. 1–8. [Google Scholar] [CrossRef]
- Aissa, S.B.; Letaifa, A.B. UAV Communications with Machine Learning: Challenges, Applications and Open Issues. Arab. J. Sci. Eng. 2022, 47, 1559–1577. [Google Scholar] [CrossRef]
- Kumbasar, N.; Kılıç, R.; Oral, E.A.; Ozbek, I.Y. Comparison of spectrogram, persistence spectrum and percentile spectrum based image representation performances in drone detection and classification using novel HMFFNet: Hybrid Model with Feature Fusion Network. Expert Syst. Appl. 2022, 206, 117654. [Google Scholar] [CrossRef]
- Orzechowski, P.F.; Burger, C.; Lauer, M. Decision-Making for Automated Vehicles Using a Hierarchical Behavior-Based Arbitration Scheme. In Proceedings of the 2020 IEEE IV Symposium, Las Vegas, NV, USA, 19 October–13 November 2020; pp. 767–774. [Google Scholar] [CrossRef]
- Group, T. Thales to Lead European AI-Driven Cyberdefence Project for Aircraft Systems. Available online: https://defence-industry.eu/thales-to-lead-european-ai-driven-cyberdefence-project-for-aircraft-systems (accessed on 15 July 2025).
- Group, T. Thales Group AI-Enhanced Radar Systems for Air Defense. Available online: https://www.thalesgroup.com/en/airborne-surveillance-radar (accessed on 15 July 2025).
- Systems, B. ASTREA Project: Autonomous Systems Technology Related Airborne Evaluation & Assessment. BAE Systems News, 1 July 2006. Available online: https://web.archive.org/web/20161029203024/http://astraea.aero/ (accessed on 15 July 2025).
- Govtribe. Industry Day for the Advanced Targeting and Lethality Automated System (ATLAS) Program. Available online: https://govtribe.com/opportunity/federal-contract-opportunity/industry-day-for-the-advanced-targeting-and-lethality-automated-system-atlas-program-w909my19rc004 (accessed on 15 July 2025).
- Stutzer, A.; Zehnder, M. Camera Surveillance as a Measure of Counterterrorism? Economics of Security Working Paper Series 34; DIW Berlin, German Institute for Economic Research: Berlin, Germany, 2010. [Google Scholar]
- Gómez Mármol, F.; Ruipérez-Valiente, J.A.; Nespoli, P.; Martínez Pérez, G.; Rivera Pinto, D.; Larriva Novo, X.A.; Álvarez-Campana, M.; Villagrá González, V.; Maestre Vidal, J.; Rodriguez López, F.A.; et al. COBRA: Cibermaniobras adaptativas y personalizables de simulación hiperrealista de APTs y entrenamiento en ciberdefensa usando gamificación. In Proceedings of the VI JNIC 2021. Available online: https://hdl.handle.net/10578/28661 (accessed on 15 July 2025).
- Spanish Minsitry of Defense COINCIDENTE (Cooperación en Investigación Científica y Desarrollo en Tecnologías Estratégicas). Available online: https://www.tecnologiaeinnovacion.defensa.gob.es/es-es/Presentacion/ImasD/Paginas/Coincidente.aspx (accessed on 15 July 2025).
- DARPA. DARPA and Artificial Intelligence for Military Operations. Available online: https://www.darpa.mil (accessed on 15 July 2025).
- DARPA. DARPA’s OFFSET Program: Autonomous Swarming for Combat Operations. Available online: https://www.darpa.mil/research/programs/offensive-swarm-enabled-tactics (accessed on 15 July 2025).
- DARPA. Lifelong Learning Machines (L2M): Enhancing Cybersecurity Through AI. Available online: https://www.darpa.mil/program/lifelong-learning-machines (accessed on 15 July 2025).
- DARPA. Artificial Intelligence for Military Operations (AIMO): Optimizing Military Precision with AI. Available online: https://www.darpa.mil/research/programs (accessed on 15 July 2025).
- Dynamics, G. General Dynamics AI Integration in Defense Technologies. Available online: https://www.klover.ai/general-dynamics-ai-strategy-analysis-of-dominance-in-aerospace-defense-ai/ (accessed on 27 August 2025).
- Vázquez, D. El Pentágono Desarrolla una IA para Anticipar Problemas Antes de Surjan en Zonas de Conflicto. Available online: https://www.businessinsider.es/pentagono-desarrolla-ia-anticipar-problemas-909385 (accessed on 15 July 2025).
- Tingley, B. TheDrive. Available online: https://www.thedrive.com/the-war-zone/41771/the-pentagon-is-experimenting-with-using-artificial-intelligence-to-see-days-in-advance (accessed on 15 July 2025).
- Ross, P.E. What Does Iron Dome Prove About Antimissile Systems? IEEE Spectr. 28 December 2012. Available online: https://spectrum.ieee.org/what-does-iron-dome-prove-about-antimissile-systems (accessed on 27 August 2025).
- Martin, L. Lockheed Martin Leverages AI and Machine Learning to Revolutionize Defense and Space Technology. Available online: https://www.lockheedmartin.com/en-us/news/features/2024/lockheed-martin-leverages-ai-and-machine-learning-to-revolutionize-defense-and-space-technology.html (accessed on 15 July 2025).
- Department of Defense, U.S. Pentagon’s Project Maven: AI for Analyzing Drone Footage. DefenseOne 2024. Available online: https://www.giest.or.jp/en/contents/briefs/2872/ (accessed on 27 August 2025).
- China North Industries Group Corporation Limited NORINCO Develops AI-Driven Autonomous Military Drones. Available online: http://en.norincogroup.com.cn/col/col441/index.html (accessed on 15 July 2025).
- NORINCO. Chinese NORINCO Unveils Compact Anti-Drone, Electronic Warfare Systems for Tanks. DefenseMirror. 2024. Available online: https://www.defensemirror.com/news/38127 (accessed on 15 July 2025).
- Grumman, N. Northrop Grumman’s AI Integration in Defense Technologies. Northrop Grumman News, 1 July 2024. [Google Scholar]
- Grumman, N. Artificial Intelligence Applications in Defense by Northrop Grumman. Defense News, 1 July 2024. [Google Scholar]
- Group, K. Russia’s AI Integration in Autonomous Combat Robots and Missile Systems. Defense Industry News, 8 November 2021. [Google Scholar]
- Almaz-Antey. Russia’s Smart Missile Systems and AI Development in Defense. Russia Defense News, 1 July 2024.
- Hi-iberia. SEDA: SatEllite Data AI. Available online: https://seda.hi-iberia.es/en/ (accessed on 15 July 2025).
- del Rio Durán, J.D. Mantenimiento Inteligente en la Armada: En Vanguardia y Trazando el Futuro. Rev. Gen. Mar. 2021, 281, 4. [Google Scholar]





| Ref. | Army/Defense | Tactical Technologies | Military Technological Description | Future Research Lines (Update ✓ or Outdated ✗ | Survey Mode (Including AI Techniques) | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Air | Naval | Land | Space | UAV | Radar | Info Syst | EW |
Surv.
Image | ||||
| [15] | ✓ | ✓ | ✓ | |||||||||
| [16] | ✓ | ✓ | ✓(✗) | |||||||||
| [17] | ✓ | |||||||||||
| [18] | ✓ | ✓ | ||||||||||
| [19] | ✓ | ✓ | ✓(✗) | |||||||||
| [20] | ✓ | ✓ | ✓ | |||||||||
| [21] | ✓ | ✓ | ✓ | |||||||||
| [22] | ✓ | ✓(✗) | ||||||||||
| [23] | ||||||||||||
| [24] | ✓ | |||||||||||
| [25] | ✓ | ✓(✗) | ✓(✗) | |||||||||
| [26] | ✓ | ✓ | ✓ | ✓ | ✓(✗) | |||||||
| [27] | ✓ | |||||||||||
| [28] | ✓ | ✓(✗) | ||||||||||
| This Survey | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓(✓) | ✓(✓) |
| Ref. | Application | Objective | Innovation | AI Type | Training Data Information |
|---|---|---|---|---|---|
| [59] | Decentralized multi-agent architecture to optimize communication for military applications in DIL tactical networks using CL techniques enhanced with ML. | Decentralized reinforcement-based ML approach to enhance the network, where each node is optimized by a CL agent employing RL to act based on its local observations. | DIL Networks; C2IS service layers; GNN architectures. | RL based on CL observations. | The actions performed by tactical agents, as well as the SNR ratios calculated between each pair of units and positions, are stored in the Tactical Replay database. |
| [60] | Introduction of a ML classifier to determine what type of IoBT device data to transmit on the battlefield and under what conditions. | Transforming real-time data from C4ISR IoBT devices into secure, reliable, and actionable information, as IoBT devices must exchange data and receive feedback from other devices, such as tanks and C2 infrastructure in real time. | C4ISR devices, IoBT devices, JointField blockchain network. | SVM, Bayes Point Match, Boosted Decision Trees, Decision Forests, and Decision Jungles. | No specific military database was found. The study recommends conducting tests in a real-world environment. |
| [61] | Enhancing free spectrum detection using ML for SDR applications. | Providing flexibility and configurability to address spectrum scarcity in wireless communication systems. | SDR and CR networks. | Comparison of 4 supervised ML models: Native Bayes classifier, SVM, Gradient Boosting Machine, and Distributed Random Forest. | No specific military database was found. |
| [62] | Predicting enemy location in naval combat using DL. | Forecasting enemy naval positions and movements based on known locations. | Inferring adversarial intentions. | ANN and Random Forest implementations. | Models trained and tested with “World of Warships” gameplay data from former naval officers. |
| [63] | Warfare simulation to predict the winning warship using Random Forest. | Predicting the winner based on seven characteristics: size, speed, capacity, crew number, attack, additional attack, and defense. | OODA loop. | Supervised ML using Random Forest. | Using 9660 battleship datasets (7728 training—1932 testing). |
| [64] | Describing the TAK-ML framework for data collection, model building, and deployment in soldier-proximal tactical environments. | Exploiting battlefield sensor data to provide services for other applications. | Every Soldier is a Sensor (ES2), TAK ecosystems, SA. | TAK-ML harmonizes ML libraries, sensors, hardware, and applications on TAK servers. | TAK servers collect, fuse, and analyze data to enable ES2 battlefield operations. |
| [65] | LSTM-DQN algorithm and deep network to solve BVR maneuver planning issues. | Avoid enemy threats and gather advantages to threaten targets, enabling intelligent aerial combat. | BVR aerial combat; reactive and deductive decision-making. | DQN and Based on LSTM cells, where the perception layer converts basic states into high-dimensional SA. | Not specified. |
| [66] | Missile defense decision-making system in incomplete information scenarios. | Facing massive missile attacks in a short time frame. | N/A. | Hybrid method combining a prior probability hypothesis of attack and RL framework. | Recommends adding factors like missile angle and increasing missile/asset types and scales. |
| [67] | ML for RIS to enhance network capacity and coverage. | Maximizing wireless communication advantages with increased interactions. | Introducing RIS technology | SL, UL, RL, and FL. | Not specified. |
| [68] | Enhanced QoS of information operating in hostile environments that may host active adversaries | Improving QoS in tactical MANETs. | A hybrid AI model combining GNN and DRL | RNN, GNN, DRL | Not specified. |
| [69] | enhancing information in C2 systems under modern operations | automating and enhancing military decision-making in C2 systems. | decision-making with capabilities of RL. | RL | Not specified. |
| Ref. | Data Fusion | Tactical Scenario Inference | Command Assistance Element | Offer Roadmaps Against Threats | Ergonomic Human–Machine Interface | Universal Language with Other Systems | Human Rules of Warfare | Availability | Resource Optimization | Scalability of Structures | Integrity | Reaction Speed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [59] | N/A | Environment-dependent communication. | Yes | Yes, decentralized architecture. | N/A | Yes, requires CL communication. | N/A | Varies by topology and link quality. | Yes, optimizes network use. | Yes, extends to nodes. | Nodes vulnerable to attacks. | Depends on nodes and CL. |
| [60] | Yes, large IoBT data. | Yes, prioritizes battlefield data. | Yes | No, lacks threat roadmap. | N/A | Yes, devices intercommunicate. | N/A | Decision Jungles are optimal. | Yes, filters massive data. | Yes, applies to scenarios. | Dynamic threat routes. | Decision Jungles optimal. |
| [61] | N/A | Yes, studies spectrum use. | Yes, finds free spectrum. | Yes, proposes zones. | N/A | Yes, 4 valid SDR algorithms. | N/A | Naïve Bayes preferred. | Yes. | Yes. | Yes. | Low for wideband. |
| [62] | Predictive map of enemy in AR. | Locates enemy. | 40% prediction with 3 games. | Only predicts position. | Overlay AR map. | N/A. | Ex-officers’ decisions. | ANN superior. | ANN superior. | 6 ships, no unit expansion. | Study false signals. | ANN superior. |
| [63] | Needs 7 battleship features. | No scenario. | Missing factors. | No roadmap. | Win/loss only. | N/A | 7 features based. | Simple algorithm. | Simple algorithm. | Future work. | Too few features. | Simple algorithm. |
| [64] | Shares map, chat, video in battle. | Depends on TAK-ML app. | Image recognition. | Terrain learning. | Visual apps. | TAK-ML info-sharing. | Depends on app. | Depends on coverage. | Harmonizes data. | Harmonizes ML and apps. | TLS/SSL in TAK-ML. | Depends on app and coverage. |
| [65] | Used in flight and motion models. | Basic combat model: flight, motion, missile. | Assists pilot. | Evades threats, guarantees position. | Graphical. | Automatic alternative. | Motion models, missile envelopes. | Short-range combat focus. | N/A | N/A | Calculates best tactics. | Slow if using deductive decisions. |
| [66] | Merge attack, defense, and missile layers. | Unknown missile distribution. | Attack alternatives. | Optimizes defense missile allocation. | Graphical. | Integrates defense system. | Needs asset list. | Hybrid method surpasses heuristic methods, DQN. | Uses only necessary defense. | Adapts to available missiles. | Low, missile distribution unknown. | Hybrid method enables real-time deployment. |
| [67] | RIS retransmits data. | Poor CSI must be addressed. | Extends battlefield wireless network. | N/A | N/A | Interacts with other systems. | N/A | Needs accurate channel info. | Improves energy efficiency. | Scalable RIS structure. | Enhances link quality. | Needs real-time data. |
| [68] | Adversary flow data. | Active adversary data. | No specification. | Improves defense. | Graphical implied. | Must communicate with C2. | N/A | Not specified. | QoS optimization. | No | Predicted by network. | Slow info update. |
| [69] | From various operations. | Central C2 system. | Through C2. | Should consider it as C2. | C2 system. | Not specified. | N/A | Not specified. | No | Yes | Very robust. | Fast, real time. |
| Ref. | Army | War Strategies | Command Support | Cybersecurity | Military Intelligence | New Constructions | Air Operations | Ground Operations | Naval Operations | Logistics | Unit Training |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [59] | Land | Yes | Yes | Study node/CL manipulation | Yes | N/A | Possible, few nodes | Yes | Possible, few nodes | Yes | Yes |
| [60] | Land | Yes | Yes | Use game theory for data deception | Yes | N/A | N/A | Yes | N/A | Yes | Yes |
| [61] | Land | N/A | Yes, free spectrum system | Study spectrum manipulation | Yes, free spectrum system | N/A | Possible | Yes | Possible | Possible with fewer devices | Possible |
| [62] | Navy | Yes | Yes | False signals for deception | Prediction with satellite/UAVs | New naval platforms incentive | Algorithm modifiable | Algorithm modifiable | Yes | Yes | Yes |
| [63] | Navy | Yes, Random Forest 80% accuracy | Yes | N/A | Yes | New naval platforms incentive | Algorithm modifiable | Algorithm modifiable | Yes | Yes | Yes |
| [64] | Land | Yes, depends on application | Yes, depends on application | Study false signals or TLS/SSL enabled | Yes, depends on application | Yes, new applications possible | No, primarily | Yes | Yes, for asymmetric warfare | Yes, depends on application | Yes, depends on application |
| [65] | Air and Space | Yes, aerial strategy for missile launch | Yes, action plan for aircraft | Study interference in decision-making | N/A | N/A | Yes | Algorithm modifiable | Algorithm modifiable | N/A | Yes, adapts to simulations |
| [66] | Land | Yes, prioritize assets | Yes, missile allocation | N/A | Converge with military intelligence | N/A | Yes | Algorithm modifiable | Algorithm modifiable | N/A | Yes, adapts to simulations |
| [67] | Land | Yes, wireless network for battlefield info | Yes, real-time battle info | Study wireless interference | Yes, RIS with UAVs | N/A | Yes | Yes | Yes | N/A | Yes, train network usage for battle |
| [68] | Land | No | Yes | No | Yes | N/A | Yes | Yes | Yes | N/A | N/A |
| [69] | All | Yes | Yes | No | No | N/A | Yes | Yes | Yes | No | No |
| Ref. | Application | Objective | Innovation | AI Type | Training Data Information |
|---|---|---|---|---|---|
| [72] | Automatic weapon detection in real time using CCTV videos. | Balances real-time performance with accuracy. | ROI-based object detection. | VGG16, YOLOv3, YOLOv4, etc. | Custom dataset from web and videos. |
| [73] | Thermal human detection for security operations. | Achieves 96% mAP. | YOLOv8 for thermal imaging. | YOLOv7, YOLOv8. | Augmented thermal datasets. |
| [74] | Improving laser-coded images for underwater systems. | Resolves turbid environment challenges. | Noise removal autoencoder. | Shallow and deep networks. | Lab-collected images. |
| [75] | Autonomous drone detection and tracking. | High accuracy with optimized memory. | Unified Object Scale Optimization. | YOLOv3, Mask R-CNN. | Kaggle/custom drone images. |
| [76] | Fusion of infrared and visible spectrum images. | Texture retention in fused images. | Double-flow guided filter. | VGG, GAN. | Not specified. |
| [77] | Military aircraft detection for real-time surveillance. | Reliable under varying conditions. | TensorFlow-based pre-processing. | CNN. | Large dataset with annotations. |
| [78] | Foreign object detection in radio imaging. | Accurate in noisy environments. | YOLOv3 applied to radar images. | CNN, YOLOv3. | Synthetic RF radar images. |
| [79] | Military vehicle recognition using small datasets. | High resource demand for neural networks. | Transfer learning with ResNet50. | ResNet50, Xception. | Social media images with augmentation. |
| Ref. | Data Fusion | Tactical Scenario Inference | Command Assistance Element | Offer Roadmaps Against Threats | Ergonomic Human–Machine Interface | Universal Language with Other Systems | Human Rules of Warfare | Availability | Resource Optimization | Scalability of Structures | Integrity | Reaction Speed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [72] | Multi-angle images | Weapon occlusion issues | Defense system applications | Alerts in case of threat | Not indicated, but should be ergonomic | Associated with lighting/weapons | N/A | Real time | N/A | More classes needed | 99% confidence score | Improve precision |
| [73] | Thermal imaging datasets | Robust in fog/smoke | Improves human detection | Enhances threat awareness | Interpretable thermal imagery | Security infrastructure integration | N/A | Real time with YOLOv8 | Processing efficiency | Supports larger datasets | 96% mAP | Real-time alerts |
| [74] | Laser images | Better scattering suppression | Enhances underwater imaging | N/A | Ergonomic and visual interface | Sonar compatibility | N/A | Improves image quality by 25% | Extends detection range in turbid zones | N/A | No behavior under disturbance | Not indicated |
| [75] | Multi-frame fusion for drones | Effective in aerial scenarios | Enhances real-time drone detection | Warns UAV threats | User-friendly platform | Compatible with multi-sensor tracking | Designed for military compliance | High frame rate | Memory optimization | Tracks multiple drones | High UAV detection reliability | Low-latency detection |
| [76] | Infrared and visible fusion | Influenced by atmospheric conditions | Aids in target identification | N/A | Good visual interface | Fire control/CCTV application | N/A | Real time | N/A | Scales to CCTV systems | No countermeasures for heat deception | Low latency |
| [77] | Diverse perspectives | Aircraft detection in varied conditions | Precise localization | Aerial threat alerts | Simplifies detection | Coordinates with monitoring systems | Standards compliance | Rapid detection | Resource-efficient | Large-scale monitoring | Reliable in challenges | Fast processing |
| [78] | Radar imaging | Reliable in noisy environments | Detects concealed objects | Identifies explosives | Intuitive radar interface | Adaptable for radar warnings | N/A | Real-time imaging | Minimal dataset reliability | Various radar applications | Reliable detection | Quick response |
| [79] | Augmented datasets | Identifies vehicles in dynamic settings | Aids tactical decisions | Vehicle threat insights | Enhances situational awareness | Integrates with vehicle systems | Standards compliance | Real-time processing | Efficient dataset use | Scales to fleets | High accuracy in conditions | Minimal latency |
| Ref. | Army | War Strategies | Command Support | Cybersecurity | Military Intelligence | New Constructions | Air Operations | Ground Operations | Naval Operations | Logistics | Unit Training |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [72] | Land | CCTV detects armed personnel. | Confirms threats using data. | CCTV dependent systems. | Aids monitoring in zones. | N/A | N/A | N/A | N/A | N/A | Systems trained for monitoring. |
| [73] | Land | Thermal systems detect threats. | Alerts for low visibility risks. | N/A | Identifies targets in fog. | N/A | Rescue aid in missions. | N/A | N/A | N/A | Thermal training improves. |
| [74] | Land | Supports command weapon data. | Improves tactical decisions. | N/A | Captures in turbid conditions. | N/A | N/A | N/A | N/A | N/A | Training for imaging systems. |
| [75] | Land | Tracks UAVs in combat. | Drone data aids command. | N/A | Predicts aerial threats. | N/A | Improves UAV usage in combat. | N/A | N/A | N/A | Drone training readiness. |
| [76] | Land | Captures clearer images. | Better tactical insights. | N/A | Alternate viewpoints support missions. | N/A | N/A | N/A | N/A | N/A | Operational training needed. |
| [77] | Land | Aircraft tracking aids ops. | Precise aerial surveillance. | Relies on secure channels. | Supports tactical analysis. | N/A | Insights for aerial ops. | N/A | N/A | N/A | Aerial imagery training. |
| [78] | Land | Radar images find IEDs. | Supports precise commands. | Enhances detection. | Tracks threats with accuracy. | N/A | Urban detection tools aid ops. | N/A | N/A | N/A | Improves system training. |
| [79] | Land | Vehicle ID in combat. | Better fleet decisions. | Secure data usage. | Military vehicle insights. | N/A | Scalable tracking systems. | N/A | N/A | Logistics aid fleet tracking. | Fleet-based training. |
| Ref. | Application | Objective | Innovation | AI Type | Training Data Information |
|---|---|---|---|---|---|
| [80] | Integrated ML-assisted system. | Detect and combat hostile radars, ML to classify signals, CEW system. | Cognitive and multimode radar systems. | Automatic decision tree generator, diffuse logic model and LSTM. | Decision tree is automatically generated from simulated EW encounters and data. |
| [81] | 3D Explorer Space Program to Simulate CEW Environments. | Stand-alone threat detection decision process, classification and countermeasure selection. | CEW tasks with DRL Algorithm. | Variational Bayesian method. | Deep Deterministic Policy Gradient Algorithm (DDPG). |
| [82] | Reduced electromagnetic wave shape model construction, for radar and EW simulations. | Improve computational efficiency of radar and EW simulations. | Coupling between representation and algorithms operating on representation. | Supervised and Unsupervised Machine Learning. | It is not contemplated. Underlying sources of error were identified. |
| [83] | CNN-based method for classifying radar interference signal. | 1D-CNN designed to classify radar interference signals. | Siamese-CNN (S-CNN) | SVM, Decision Tree Classifiers, Logistic Regression and RF. | Limited training samples. A CNN-based simesan network. |
| [84] | ML-based GNSS models to improve robustness and position signal performance. | Deliver low-cost, high-performance solution. | Positioning, Navigation and Timing, Time to First Correction (TTFF) | 213 application studies from 2000 to 2021. Mostly used RF, SVM, ANN and CNN. | |
| [85] | Two deep learning-based methods for predicting the proper interference technique. | DNN on manually extracted feature values from the PDW list and using LSTM that takes the PDW list as input. | Press Description Word (PDW), Long Short-Term Memory (LSTM). | DNN of different structures and LSTM. | Training data built from the library. Trained ML model to predict interference technique. |
| [86] | CNN-based radio fingerprinting. | Timely interception of tactical and strategic transmissions. | Transform the identification and classification of RF signals. | CNN. | IQ Data and Image Processing. |
| Ref. | Data Fusion | Tactical Scenario Inference | Command Assistance Element | Offer Roadmaps Against Threats | Ergonomic Human–Machine Interface | Universal Language with Other Systems | Human Rules of Warfare | Availability | Resource Optimization | Scalability of Structures | Integrity | Reaction Speed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [80] | Yes, environments difficult to analyze. | Yes, systems must accurately model their environment. | Yes, system detects, acquires and follows goals, and guides the platform. | Yes, the Electronic Attack (EA) assessment model recommendations. | The interface is not specified by supposedly visual. | Yes, with other radar systems and countermeasures. | Observed radar threat level determined by distance and mode. | Satisfactory results in a simulated environment against multiple multifunction radars. | Better result with short-term memory neural network. | Yes, focus allows automatic updates in progress. | Each case was simulated 100 times and successful missions were recorded. | Depends on the distance at which the location of the threat is assumed. |
| [81] | UAV speed and direction of motion need to be controlled while verifying the integrity of the CEW system function. | You can search for the station in the mission map + Bayesian inference or applying evolutionary computing method. | Yes, to locate ground stations that are transmitting. | No, it is not contemplated. | No, it is not considered. | Both the UAV and ground station use radar-like observation sensors. | In this case, it is a game-like simulation. | Partial observability of the environment, and physical UAV maneuverability restrictions. | No, it is not considered. | Detection sensor modules and countermeasure weapons can be expanded. | The interaction between each part and the environment has a clear mathematical model. | UAV movement prioritizes physical restrictions of movement over CEW system operation. |
| [82] | Yes, there is a representative coupling of the sampled signal and morphism. | N/A | N/A | N/A | N/A | Seeks to formulate learning problem in a unified way to increase efficiency. | N/A | Loss of information due to morphism and error in the approximations of the supervised learning algorithm. | Yes, morphism avoids computational bottleneck. | Learning problem should be formulated in a unified way to increase the effectiveness of the outcome. | Worsens by being more truthful about sampled representations than morphism. | Improvement with approximate morphism based on features of a reduced model. |
| [83] | S-CNN to classify different interference signals with limited samples. | N/A | Yes, this electromagnetic signal classification method can give enemy information. | N/A | N/A | N/A | N/A | Yes, 1D-CNN experimental result. S-CNN result under limited training samples. | N/A | N/A | 12 typical types of radar interference signals. | N/A |
| [84] | N/A | Yes, GNSS in both indoor and outdoor environments. | Yes, early detection of faults and errors can lead to timely correct it. | N/A | N/A | N/A | N/A | Reduce maintenance effort and downtime. | Yes, it is the goal with ML. | N/A | Sources of errors exist for satellite-based positioning. | Dependent, SVM speed does not meet the real-time requirements for interference monitoring. |
| [85] | Yes, ML model generates interference techniques for incoming threat signals. | N/A | Yes, predicts proper interference technique in the face of a threat. | Yes, suggest an interference technique before a threat. | N/A | N/A | N/A | Interference method can be predicted for unknown radar signal with an average accuracy of about 92%. | Yes, the predicted interference method will be used first. | N/A | Prediction accuracy of the LSTM model was higher. | DNN-based method is faster than LSTM method. |
| [86] | IQ Data and Image. | Hybrid multi-level approach for fingerprinting and confirming transmitter identification. | Yes, confirming transmitter identification in a dynamic and wider spectrum. | Yes, identifying high-value targets and assisting in Identification Friend or Foe, anti-spoofing. | N/A | N/A | N/A | Presented concepts and solutions can be a game changer for both military and civilian use. | Yes, the hybrid approach reduces computational load. | N/A | Consistency in accuracy in SNR levels and BW. IQ and Image processing-based models showed an exponential decline in accuracy. | N/A |
| Ref. | Army | War Strategies in Armed Conflicts | Command Decision Support | Cybersecurity | Military Intelligence | New Constructions | Air Operations | Ground Operations | Naval Operations | Logistics | Unit Training |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [80] | Air and Space. | Yes, electromagnetic signal capture and classification is vital. | Yes, an imminent danger detected anticipates decisions. | N/A | Yes, although the algorithm collects real-time data there is a signal database. | Yes, new UAV capability and drives projects like NGJ-MB. | Yes | Could be applied. | Could be applied. | N/A | Yes, operator training would be convenient. |
| [81] | Air and Space. | Yes, ground station transmission detection-interference is vital. | Yes, an imminent danger detected anticipates decisions. | N/A | Yes, location of transmitting earth stations. | Yes, new UAV capacity. | Yes | Could be applied. | Could be applied. | N/A | Yes, operator training would be convenient. |
| [82] | Air and Space. | N/A | N/A | N/A | N/A | Yes, it could be considered in new radar and EW processing. | May be applied on radar and EW. | May be applied on radar and EW. | May be applied on radar and EW. | N/A | N/A |
| [83] | Ground. | Yes, signal classification gives enemy information. | Yes | N/A | Yes, signal classification gives enemy information. | N/A | Yes | Yes | Yes | N/A | N/A |
| [84] | Ground. | Yes, may cause interference with GPS signal from units. | Yes, an accurate signal is needed. | N/A | Yes, identifies unit positions. | N/A | Yes | Yes | Yes | N/A | N/A |
| [85] | Ground. | Yes, can cause radar interference or enemy EW. | Yes, it prepares interference system such as a pitcher. | N/A | Yes, it could be associated with the military and with the interference system. | N/A | Yes | Yes | Yes | Yes, you can predict which interference systems to have armed. | Yes, its use should be trained. |
| [86] | Air, Ground and Space. | Yes, interception of crucial tactical and strategic transmissions. | Yes, RF fingerprinting serves as a cornerstone in ensuring seamless operations. | Security and operational integrity by RF fingerprinting. | Yes, a comprehensive solution for fingerprinting and confirming transmitter identification. | Yes, considering the merits and drawbacks of previous approaches, a hybrid approach is proposed. | Yes | Yes | Yes | Yes, RF fingerprinting in fortifying security and operational integrity within the EW spectrum. | N/A |
| Ref. | Application | Objective | Innovation | AI Type | Training Data |
|---|---|---|---|---|---|
| [88] | Maintenance of air defense radar systems | Detect faults | Fault detection using multiple ML models | Random Forest, MLP, etc. | Data collected in faulty and normal states |
| [89] | SAR data analysis for HD imaging | Automatic target recognition | CNN for noise removal and segmentation | CNN, RNN, AE, etc. | Data augmentation for SAR-ATR |
| [90] | Radar resource management | Improve reaction time and integrity | Multifunction radar with adaptive features | CNN | Limited data from exceptional cases |
| [91] | Airborne target detection | Classify targets as fixed- or rotary-wing aircraft | Two-stage CNN for noise filtering | CNN | 83,740 Doppler images |
| [92] | Radar scan clustering | Reduce dataset size | Density-based clustering algorithm | Unsupervised learning | Real dataset |
| [93] | MIMO radar waveform design | Improve localization and clutter mitigation | Deep residual network optimization | DL (CON model) | Adam algorithm with unsupervised COF |
| [94] | Pulsed Doppler radar detection | Improve CFAR performance | RadCNN for low SNR scenarios | CNN | 182,000 files for training/testing |
| [95] | Situational awareness | Reduce radar cross-section processing time | Optimized ML-based clustering | K-Means | 9 homogeneous and heterogeneous clusters |
| Ref. | Data Fusion | Tactical Scenario Inference | Command Assistance Element | Offer Roadmaps Against Threats | Ergonomic Human–Machine Interface | Universal Language with Other Systems | Human Rules of Warfare | Availability | Resource Optimization | Scalability of Structures | Integrity | Reaction Speed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [88] | Yes, streams from different states | No | No | No | No | Yes, with EW | N/A | Medium | No | Future works | True positive rate: 0.84 | N/A |
| [89] | Feasibility of transferring CNN learning to SAR | No, potential improvement | Yes, visual info for command | Continuation of development | N/A | Neural networks compatible with systems | N/A | Uses large-scale datasets | Feasibility of CNN learning in SAR | Video application possible | Testing of DL algorithms needed | N/A |
| [90] | Yes, MIMO radars | Yes, ML for overloaded radars | Yes, exploration system for ESM, EA, communication | N/A | N/A | Yes, integrates ESM/EA | Yes, EA-specific | Low, no physical testing | Radar has multiple functions | N/A | Yes, ML improves integrity | N/A |
| [91] | Two-dimensional radar, single/series pulses | N/A | Yes, identifies aircraft type | N/A | Two-stage noise removal | N/A | N/A | Higher, reduces filtering stages | Eliminates CFAR/peak detection | N/A | 96% target hits, 85% noise | Higher, discards 30% noise |
| [92] | PDF projects dataset into 1D space | Adaptive cluster extraction | Yes, dense target info extraction | N/A | N/A | N/A | N/A | Higher, reduces time | Determines parameters for clustering | N/A | Efficient density-based scanning | Fast adaptive mean-shift algorithm |
| [93] | MIMO radar waveform facilitates implementation | N/A | Yes, improved waveform adds capabilities | N/A | N/A | Yes, integrates communication systems | N/A | Superior performance, acceptable optimization time | Solves waveform design problem | Possible use in warfare | Waveform enhances integrity | Feasible within computational complexity |
| [94] | N/A | Yes, affects detection results | Yes, real-time response | N/A | Real-time noise filtering | N/A | N/A | Outperforms CFAR techniques | RadCNN reduces complexity | N/A | RadCNN superior to state-of-art | Real-time feasibility |
| [95] | Single data stream | Full SA | No | Yes | No | No | Full | No | No | No | Residual error: 118807.63 | N/A |
| Ref. | Army | War Strategies in Armed Conflicts | Command Decision Support | Cybersecurity | Military Intelligence | New Constructions | Air Operations | Ground Operations | Naval Operations | Logistics | Unit Training |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [88] | Air | No specified | Yes, evaluation of an air defense system | Not included | No | No | Yes | No | No | N/A | N/A |
| [89] | Air and Space | Yes, they depend on the images. | Yes, decisions based on images. | It will depend on the location of the data processor. | Yes, image segmentation, change analysis, terrain analysis. | N/A | Yes | Yes | Yes | N/A | Yes, its use should be trained. |
| [90] | Air and Space | Yes, ESM and EA. | Yes, exploration and communication. | N/A | Yes, database. | N/A | Yes | Yes | Yes | N/A | Yes, its use should be trained. |
| [91] | Air and Space | Yes, the presence of many rotary-wing enemies (including UAVs) changes the command strategy. | Yes, different ways of attacking fixed-wing to rotary-wing targets. | N/A. | Yes, identifies the type of aircraft. | Yes, implies new developments to avoid such classification. | Yes | Yes | Yes | N/A | Yes, its use should be trained. |
| [92] | Air and Space | N/A | Yes, identifies targets in dense areas. | N/A | N/A | N/A | Yes | Yes | Yes | N/A | Yes, the way to deceive the algorithm could be trained. |
| [93] | Air and Space | Yes, it can provide communication in battle and greater precision. | Yes, greater security in decision-making. | N/A | Yes, more accurate information. | N/A | Yes | Yes | Yes | N/A | Yes, the way to deceive the algorithm could be trained. |
| [94] | Air and Space | N/A | Yes, real-time information. | N/A | Yes, more information available with less SNR ratio. | N/A | Yes | Yes | Yes | N/A | Yes, the way to deceive the algorithm could be trained. |
| [95] | Air | Pilots to assess, anticipate, and respond adeptly to dynamic combat scenarios. | Help to Pilots | No | No | N/A | Yes | No | No | N/A | N/A |
| Ref. | Application | Objective | Innovation | AI Type | Training Data Information |
|---|---|---|---|---|---|
| [96] | Overcoming the mobility, communication, resource management and security challenges. | ML focused on meeting network requirements, taking into account the roles, collaboration, cooperation, and changing contexts. | Study A2A, A2G, and G2A communications to ensure QoS and QoE. | Algorithms like ANN, CNN, DNN, SVM, DQN, RandF, KNN are analyzed depending on the type of A2A, A2G, and G2A communication. | Not determined as it is an analysis and collection of different research. |
| [97] | Classification of drones using radio frequency (RF) signals. | Use of RF signals for drone detection with specific frequency ranges. | Hybrid Model with Feature Fusion Network (HMFFNet). | CNN-based feature extraction followed by feature fusion and SVM-based classification. | Features captured with a Deep Learning VGG19 network and sorting done with SVM. |
| [98] | Architectural design for automatic AV behavior generation. | Widespread and scalable decision-making framework. | Tactical and Strategic Behaviors in Automated Driving. | Behavior-Based Hierarchical Arbitration Scheme. | Database containing a merged and abstract representation of available sensor data. |
| Ref. | Data Fusion | Tactical Scenario Inference | Command Assistance Element | Offer Roadmaps Against Threats | Ergonomic Human–Machine Interface | Universal Language with Other Systems | Human Rules of Warfare | Availability | Resource Optimization | Scalability of Structures | Integrity | Reaction Speed |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| [96] | Alternatives to ad hoc flying networks, caching or UAV processing. | Needed awareness of context changes and adaptability to current service requirements. | Yes, overcoming the 4 challenges already described. | A2A communications (participation threshold based on energy, capacity, mobility) and A2G communications (interference management and spectrum mapping). | N/A | Yes, the UAV network and base stations should be understood. | N/A | ML is a suitable solution for a dense and dynamic environment. | Yes, ML is the right tool for predicting context changes and optimization. | Yes, it should be adapted to the number of UAVs, mobility, communication, resource management, and security. | Dependent on performance, communications delays, and resource management efficiency. | It will depend on the functions and missions entrusted. |
| [97] | Yes, the characteristics of the 3 stages are merged for better discriminatory property. | N/A | Yes, it is another sound, image, or radar classification. | N/A | Not specified but should exist. | If you want to automate the defense process. | N/A | High. | Yes, audio, image or radar sensors are not required. | N/A | Could be altered with electronic warfare and assume a fake drone. | Fast |
| [98] | Merges information from all available sensors. | Contains a fused, tracked, and filtered representation of the world. | Yes, because AV would be autonomous. | A cost-based arbitration scheme is useful when multiple behavioral options are applied. | N/A | The same language between all sensors and the autonomous system. | It contains parking and emergency behaviors and prevents indefinite states. | Robust and efficient modular system. | Human resources would not be necessary. | Structure designed for cars in cities and roads, but could be extended to military vehicles in areas of operation. | Supports different planning approaches. | Immediate to avoid an accident. |
| Ref. | Army | War Strategies in Armed Conflicts | Command Decision Support | Cybersecurity | Military Intelligence | New Constructions | Air Operations | Ground Operations | Naval Operations | Logistics | Unit Training |
|---|---|---|---|---|---|---|---|---|---|---|---|
| [96] | Earth or Air and Space. | Yes, it could be a network of connected UAVs locating real-time targets. | Yes, it will depend on the use of UAVs. | It is necessary to have an autonomous defense system that guarantees the integrity, confidentiality, and availability of the data. | Yes, if it applies to recognition work. | Yes, the UAVs network study may be an inducement for new construction. | Yes | Yes | Yes | The transport of information data affects this area. | Yes, it is necessary to train the use of these networks and their defense. |
| [97] | Earth. | Yes, the radio spectrum could be analyzed to find out how many drones are in the battle. | Yes, it is a way for classifying. | Study Potential Interference. | Yes, if you can analyze the spectrum and determine no drones. | Yes, encourage to work with other forms of communication. | Yes | Yes | Yes | N/A | Yes, it could be trained in different ways to deceive the RF classification. |
| [98] | Earth. | Yes, having autonomous vehicles provides new strategies. | N/A | N/A | Yes, they could be used in recognition work. | Yes, the first 100% autonomous vehicle developments are emerging. | Yes | Yes | Yes | Yes | Yes, training is required along with autonomous vehicles. |
| Initiative | Type of Initiative | Year Starting | Main Supporter | Main Technological System |
|---|---|---|---|---|
| AIDA | Project | 2023 | Funded by European Defense Fund. | Information System in Tactical Environments. |
| ASTRAEA | Project | 2006 | Consortium of companies and government agencies of the United Kingdom. | Unmanned Systems. |
| ATLAS | Project | 2020 | Project developed by the U.S. Army. | Fire and Weapon Direction Systems. |
| COBRA | Project | N/A | Project developed by Directorate of Armament and Material (DGAM) of Spain. | Information Systems in Tactical Environments. |
| DARPA | R&D Agency | 1958 | Agency of the United States Department of Defense responsible for research and development of new technologies and innovative systems to develop disruptive technologies. | Information Systems in Tactical Environments and Unmanned Systems. |
| General Dynamics | Defense company | N/A | Defense company in the United States. | Information Systems in Tactical Environments. |
| GIDE | Project | 2020 | Led by the U.S. Department of Defense. | Information Systems in Tactical Environments. |
| Iron Dome | Project | 2021 | Developed by Israel. | Fire and Weapon Direction Systems. |
| Lockheed Martin | Defense company | N/A | Based in Bethesda, Maryland, U.S. It manufactures some of the world’s most advanced stealth combat aircraft in the defense sector. | Fire and Weapon Direction Systems and Unit Maintenance Management Systems and Logistics. |
| Maven | Project | 2017 | Project initiated by the U.S. Department of Defense. | Image Surveillance Systems. |
| NORINCO | Defense corporation | N/A | Chinese state-owned defense corporation that manufactures commercial and military products. | Information Systems in Tactical Environments, Radar Systems, and Unmanned Systems. |
| Northrop Grumman | Defense company | N/A | American multinational aerospace and defense company. | Information Systems in Tactical Environments, Radar Systems, Fire and Weapon Direction Systems, Unmanned Systems, and Unit Maintenance Management Systems and Logistics. |
| Russia | Country | N/A | Russian defense companies: Kalashnikov Group and Almaz-Antey. | Information Systems in Tactical Environments, Electronic Warefare System, Fire and Weapon Direction Systems, and Unmanned Systems |
| SEDA | Project | 2018 | Spanish initiative based on the COINCIDENTE program of the General Directorate of Armament and Material (DGAM) of Spain. | Image Surveillance Systems. |
| SOPRENE | Project | N/A | Spanish initiative based on the COINCIDENTE program of the General Directorate of Armament and Material (DGAM) of Spain. | Unit Maintenance Management Systems and Logistics. |
| Parameter | Typical Values (Baseline) | Improvement Target with AI |
|---|---|---|
| Latency (Edge/Inference) | <10 ms in edge systems (TinyML) | ≤5 ms for real-time tactical response |
| Throughput (e.g., ResNet-50) | ∼500 queries/s with optimizations | >1000 qps to support multiple concurrent streams |
| Energy Efficiency | 6× energy savings in optimized architectures | >10× for extended autonomous deployment |
| SWaP (Size, Weight, Power) | SoC-based chips (Jetson, FPGA) | 30–50% reduction in footprint and power |
| Security and Privacy | Edge processing reduces data exposure | Local encryption + threat detection for resilience |
| Robustness (Adversarial Evaluation) | Tested via red teaming and offline validation | Continuous adversarial benchmarking |
| Performance per Watt (TOPS/W) | 30–80 TOPS/W in current AI accelerators | >100 TOPS/W in next-gen tactical AI chips |
| AI Technique | UAV Ops | Radar | EW | Maritime/Naval | Surveillance Systems | Info Networks | Space Environments |
|---|---|---|---|---|---|---|---|
| CNN | ✓ Object recognition | ✓ Target ID | ✓ RF classification | ✓ Ship detection | ✓ Thermal/visual detection | ✓ Feature extraction | ✓ Image recognition from satellites |
| LSTM | ✓ Flight prediction | ✗ Slow for real time | ✗ Limited | ✗ Motion modeling | ✗ Rare | ✗ High memory | ✗ Temporal modeling limited |
| RL | ✓ Autonomous pathing | ✗ Rarely used | ✓ Threat response | ✓ Route planning | ✓ Swarm coordination | ✓ Adaptive routing | ✓ Orbital coordination |
| SVM | ✗ Not used | ✓ Legacy signal ID | ✓ Interference detection | ✗ Limited | ✓ Pattern classification | ✓ Traffic classification | ✓ Signal filtering |
| FL | ✓ Collaborative learning | ✗ Not mature | ✗ Deployment limits | ✓ Shared models | ✓ Model updates | ✓ Decentralized training | ✓ Privacy-focused federated updates |
| GNN | ✓ Swarm behavior | ✗ Complex | ✗ Rare | ✓ Mesh optimization | ✓ Scene graphing | ✓ Topological modeling | ✓ Graph-based orbit modeling |
| Attacker Mode | Targeted System/Layer | Typical Threat Scenario | AI-Enabled Defense Mechanism |
|---|---|---|---|
| Jamming | Wireless channels, EW systems | Adversary disrupts communication by overwhelming the spectrum with interference | Deep Reinforcement Learning (DRL)-based anti-jamming for adaptive spectrum access and channel hopping |
| Spoofing | Radar, UAV control, GPS | Adversary injects false signals (e.g., fake GPS coordinates or radar echoes) | Adversarial detection models with anomaly-based ML; cross-sensor data fusion for signal validation |
| Evasion Attacks | Image surveillance, radar object detection | Adversarial perturbations designed to fool AI classifiers into mislabeling targets | Adversarial training, robust feature extraction, and XAI for resilient detection |
| Data Poisoning | Training datasets, tactical information networks | Corrupted training samples degrade ML performance in deployed systems | Robust data sanitization, secure data provenance, and Federated Learning (FL) with anomaly detection |
| Byzantine Attacks | Distributed learning across coalition networks | Malicious clients send manipulated updates to degrade global models | Byzantine-robust FL algorithms (median-based aggregation, Krum, Trimmed Mean) with trust scoring |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Monzon Baeza, V.; Parada, R.; Concha Salor, L.; Monzo, C. AI Integration in Tactical Communication Systems and Networks: A Survey and Future Research Directions. Systems 2025, 13, 752. https://doi.org/10.3390/systems13090752
Monzon Baeza V, Parada R, Concha Salor L, Monzo C. AI Integration in Tactical Communication Systems and Networks: A Survey and Future Research Directions. Systems. 2025; 13(9):752. https://doi.org/10.3390/systems13090752
Chicago/Turabian StyleMonzon Baeza, Victor, Raúl Parada, Laura Concha Salor, and Carlos Monzo. 2025. "AI Integration in Tactical Communication Systems and Networks: A Survey and Future Research Directions" Systems 13, no. 9: 752. https://doi.org/10.3390/systems13090752
APA StyleMonzon Baeza, V., Parada, R., Concha Salor, L., & Monzo, C. (2025). AI Integration in Tactical Communication Systems and Networks: A Survey and Future Research Directions. Systems, 13(9), 752. https://doi.org/10.3390/systems13090752








