Impact of Security Management Activities on Corporate Performance
Abstract
1. Introduction
- Do security management activities positively affect corporate performance?
- Do the differences in CISO management strategies, as organizational innovation, influence corporate performance?
- Do the differences in total IT investment versus focused information security investment levels affect corporate performance, and if so, how?
- Does the implementation of information security management tools, such as an ISMS, positively moderate the relationship between security management activities and corporate performance?
2. Literature Review and Hypothesis Setting
2.1. Theoretical Consideration
2.1.1. Security Management Activities and the Resource-Based View (RBV)
2.1.2. Security Management Activities and Contingency Theory
2.1.3. Theoretical Justification for Variable Selection and Hypothesis Development
2.2. Non-Financial Security Management Activities
2.2.1. Internal Security Management Activities and Corporate Performance
2.2.2. External Security Management Activities and Corporate Performance
2.3. The Strategic Role of the CISO in Organizational Innovation
CISO’s Work Independence and Corporate Performance
2.4. Strategic Differences in Information Systems Investment Decisions
2.4.1. IT Investment Activities and Corporate Performance
2.4.2. Information Security Sector Investment Activities and Corporate Performance
2.5. ISMS (Information Security Management System) Certification System
2.6. Justification for ISMS as a Moderating Variable and Hypothesis Development
2.6.1. The Significance of the ISMS Certification System in Relation to Internal and External Security Management Activities and Corporate Performance
- Obtaining or maintaining an ISMS-P and ISO/IEC certification will strengthen the positive effect of internal security management activities on corporate performance.
- Obtaining or maintaining an ISMS-P and ISO/IEC certification systems will strengthen the positive effect of external security management activities on corporate performance.
2.6.2. The Significance of the ISMS Certification Systems in Relation to CISO Work Independence and Corporate Performance
- The acquisition or maintenance of ISMS-P and ISO/IEC certification systems will strengthen the positive effects on corporate performance when the CISO performs duties independently without concurrent roles in other executive organizations.
- Obtaining or maintaining ISMS-P and ISO/IEC certification will strengthen the positive effect on corporate performance when the CISO concurrently serves as the CIO, overseeing the IT organization.
2.6.3. The Significance of ISMS Certification in Relation to the Proportion of Investment in IT and Information Security and Corporate Performance
- Obtaining or maintaining ISMS-P and ISO/IEC certification will strengthen the positive effect on corporate performance as the investment ratio in the IT information technology sector increases.
- Obtaining or maintaining ISMS-P and ISO/IEC certification will strengthen the positive effect on corporate performance as the investment ratio in the information security sector increases.
3. Materials and Methods
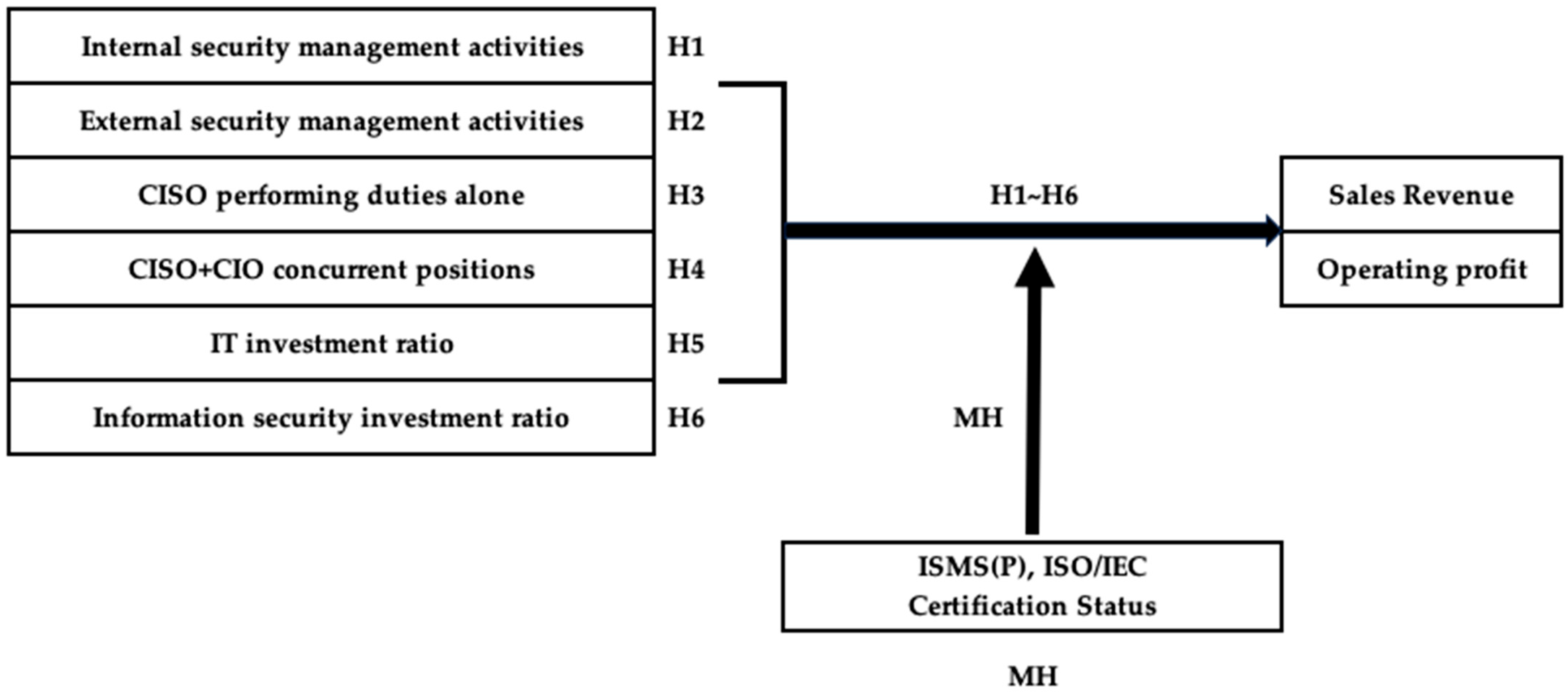
3.1. Research Model
3.2. Variables
3.3. Analysis Method
3.4. Model Specification
3.4.1. Multiple Regression Model
- Notation
- Y: Dependent Variable (Sales Revenue, Operating Profit)
- βi: Estimated Regression Coefficient (i = 0,1,…,11)
- X1: Internal Security Management Activities
- X2: External Security Management Activities
- X3: CISO performing duties independently
- X4: CISO + CIO concurrent positions
- X5: IT Information Technology Sector Investment Ratio
- X6: Information Security Sector Investment Ratio
- C1: Voluntary/Mandatory
- C2: Industry
- C3: IT Industry group status
- C4: Asset size ($1.5 billion or more but less than $4 billion = 1)
- C5: Asset size ($4 billion or more = 1)
3.4.2. Moderated Regression Model
- Notation
- Y: Dependent Variable (Sales Revenue, Operating Profit)
- βi: Estimated Regression Coefficient (i = 0,1,…,8)
- X: Independent Variable
- W: Moderator Variable
- XW: Interaction Term between X and W
- C1: Voluntary/Mandatory
- C2: Industry
- C3: IT Industry group status
- C4: Asset size ($1.5 billion or more but less than $4 billion = 1)
- C5: Asset size ($4 billion or more = 1)
3.5. Data Collection
4. Results
4.1. General Characteristics of the Research Variables
4.2. Correlation Analysis Among Research Variables
4.3. Verification Results of Research Hypotheses H1–H6
4.4. Results of the Moderating Effect Analysis for Research Hypothesis (MH)
4.4.1. Analysis of the Moderating Effects of ISMS-P and ISO/IEC Certification Status on the Relationship Between Security Management Activities and Sales Revenue
4.4.2. Analysis of the Moderating Effect of ISMS-P and ISO/IEC Certification Status on the Relationship Between Security Management Activities and Operating Profit
5. Discussion
6. Conclusions
6.1. Practical Implications
6.2. Academic Implications
6.3. Limitations of the Study
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A
| Research Hypothesis | Verification Results | |
|---|---|---|
| Sales Revenue | Operating Profit | |
| Hypothesis 1: Internal security management activities have a positive impact on corporate performance. | Adopted | Rejected |
| Hypothesis 2: External security management activities have a positive impact on corporate performance. | Adopted | Rejected |
| Hypothesis 3: Having the CISO perform duties independently will have a positive impact on corporate performance. | Rejected | Rejected |
| Hypothesis 4: Having the CISO also serve as CIO will have a positive impact on corporate performance. | Rejected | Rejected |
| Hypothesis 5: A higher investment ratio in the IT information technology sector will have a positive effect on corporate performance. | Rejected | Rejected |
| Hypothesis 6: A higher proportion of investment in the information security sector will have a positive effect on corporate performance. | Rejected | Rejected |
| Moderating Hypotheses 1: Obtaining or maintaining an ISMS-P and ISO/IEC certification will strengthen the positive effect of internal security management activities on corporate performance. | Rejected | Rejected |
| Moderating Hypotheses 2: Obtaining or maintaining an ISMS-P and ISO/IEC certification systems will strengthen the positive effect of external security management activities on corporate performance. | Rejected | Rejected |
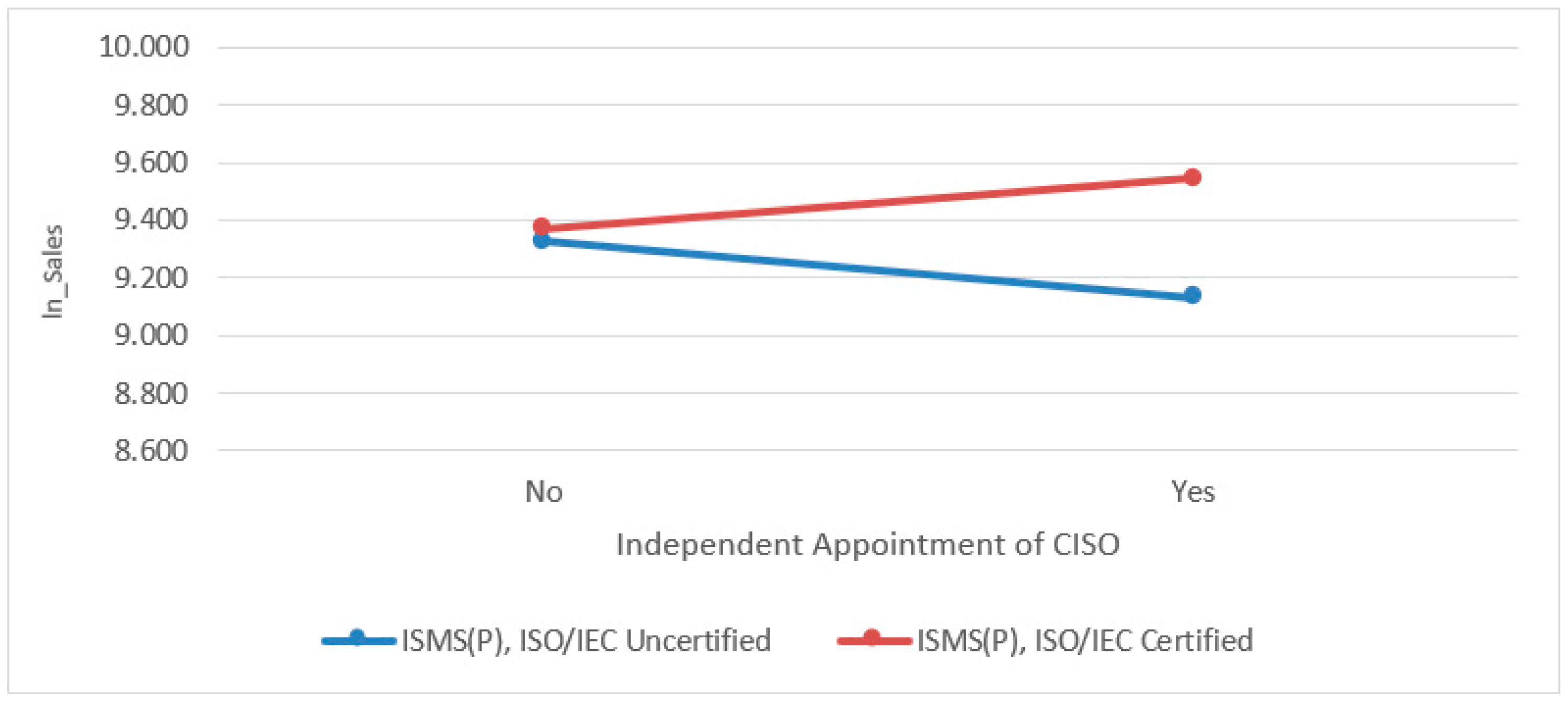
| Moderating Hypotheses 3: The acquisition or maintenance of ISMS-P and ISO/IEC certification systems will strengthen the positive effect on corporate performance when the CISO performs duties independently without concurrent roles in other executive organizations. | Adopted | Rejected |
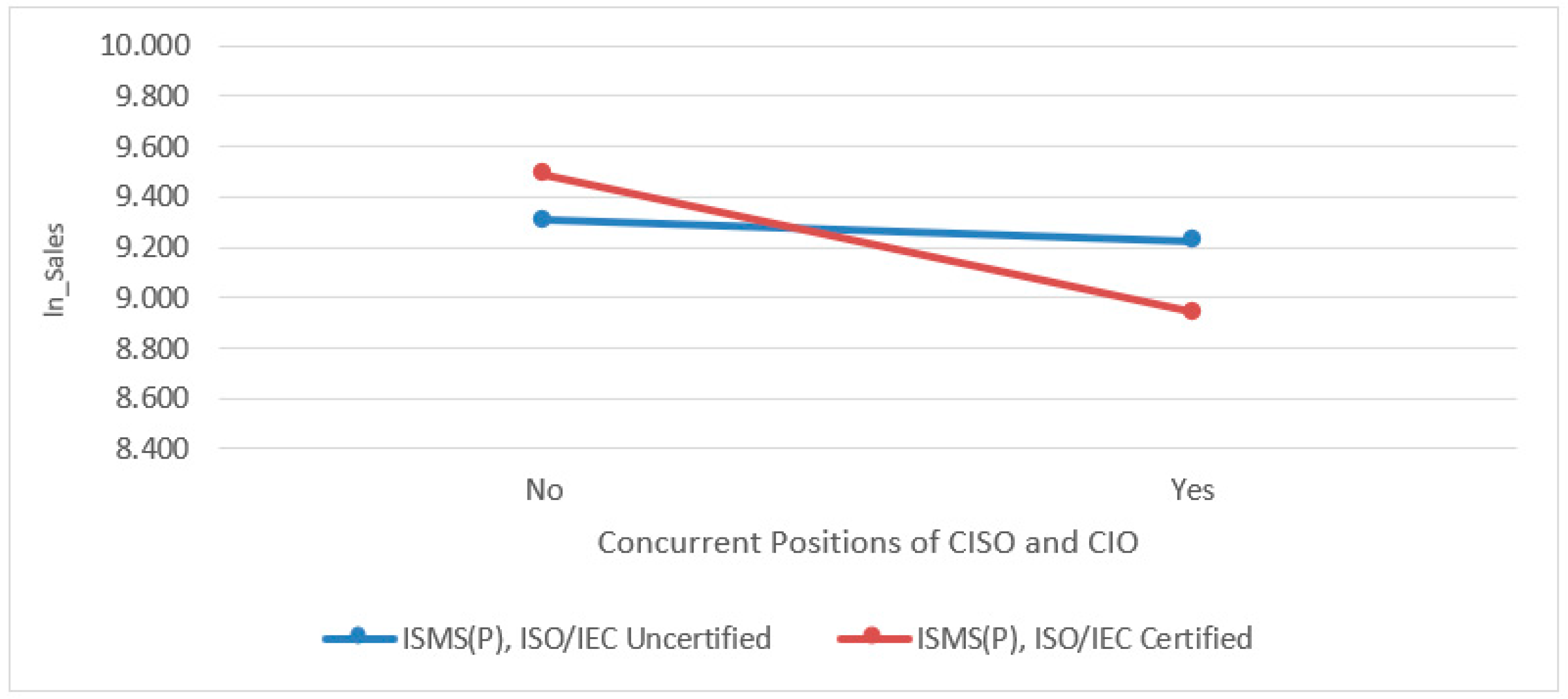
| Moderating Hypotheses 4: Obtaining or maintaining an ISMS-P and ISO/IEC certification will strengthen the positive effect on corporate performance when the CISO concurrently serves as the CIO overseeing the IT organization. | Rejected | Rejected |
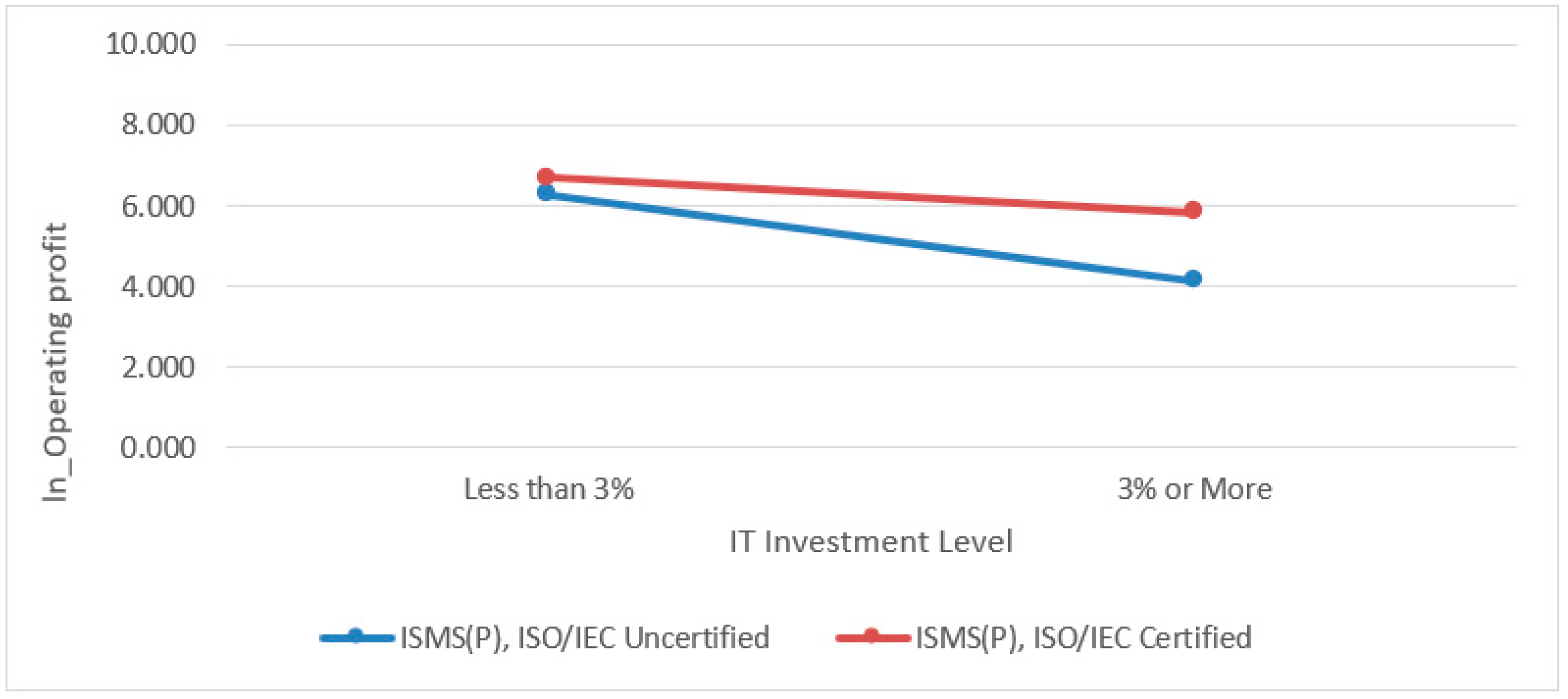
| Moderating Hypotheses 5: Obtaining or maintaining an ISMS-P and ISO/IEC certification will strengthen the positive effect on corporate performance as the investment ratio in the IT information technology sector increases. | Adopted | Adopted |
| Moderating Hypotheses 6: Obtaining or maintaining an ISMS-P and ISO/IEC certification will strengthen the positive effect on corporate performance as the investment ratio in the information security sector increases. | Rejected | Rejected |
References
- Wikipedia Contributors. 2024 United States Telecommunications Hack. Wikipedia. 22 April 2024. Available online: https://en.wikipedia.org/wiki/The_Washington_Post (accessed on 27 August 2024).
- Newman, L.H. The Worst Hacks of 2024 So Far. WIRED, 20 March 2024. [Google Scholar]
- Global Cybersecurity Outlook 2024; World Economic Forum: Cologny, Switzerland, 2024.
- Mmango, N.; Gundu, T. Cybersecurity as a competitive advantage for entrepreneurs. In Annual Conference of South African Institute of Computer Scientists and Information Technologists; Springer Nature: Cham, Switzerland, 2024; pp. 374–387. [Google Scholar]
- Son, T.H. The Impact of Corporate Information Protection Activities on Information Security and Information Management Performance. Ph.D. Dissertation, Graduate School, Myongji University, Seoul, Republic of Korea, 2015. [Google Scholar]
- Byun, J. A Study on the Impact of Personal Information Protection Regulatory Compliance on the Competitiveness of IT Companies Based on Regulatory Perception; Graduate School of Soongsil University: Seoul, Republic of Korea, 2019. [Google Scholar]
- Jung, S. The Impact of Government Regulation on Corporate Technological Innovation Behavior; Policy Research 2007-13; Science and Technology Policy Institute: Sejong-si, Republic of Korea, 2007. [Google Scholar]
- Hameed, M.A.; Arachchilage, N.A.G. On the impact of perceived vulnerability in the adoption of information systems security innovations. arXiv 2019, arXiv:1904.08229. [Google Scholar] [CrossRef]
- Barney, J.B. Firm resources and sustained competitive advantage. J. Manag. 1991, 17, 99–120. [Google Scholar] [CrossRef]
- Lawrence, P.R.; Lorsch, J.W. Organization and Environment: Managing Differentiation and Integration; Harvard Business School Press: Boston, MA, USA, 1967. [Google Scholar]
- Jeon, S. Information Security Incidents That CISOs and DPOs Must Know: Hacking Judgments Analyzed by a Hacker-Turned-Lawyer; Samil Info Mine: Seoul, Republic of Korea, 2020. [Google Scholar]
- Jang, S. Introduction to Information Security and Personal Information Protection Management Systems; Saengneung Publishing Co., Ltd.: Paju, Republic of Korea, 2020. [Google Scholar]
- Posey, C.; Roberts, T.L.; Lowry, P.B.; Bennett, R.J.; Courtney, J.F. Insiders’ protection of organizational information assets: Development of a systematics-based taxonomy and theory of diversity for protection-motivated behaviors. Mis Q. 2013, 37, 1189–1210. [Google Scholar] [CrossRef]
- Kim, A.; Kim, Y.J. Digital Entrepreneurship and Corporate Performance. Bus. Adm. Res. 2021, 50, 1–22. [Google Scholar]
- Garavan, T.; O’Brien, F. Contingency theory. In A Guide to Key Theories for Human Resource Management Research; Edward Elgar Publishing: Cheltenham, UK, 2024; pp. 67–72. [Google Scholar]
- Donaldson, L. The Theory of Organizational Fit; Gyeongmunsa: Seoul, Republic of Korea, 2003. [Google Scholar]
- Ciekanowski, M.; Żurawski, S.; Ciekanowski, Z.; Pauliuchuk, Y.; Czech, A. Chief information security officer: A vital component of organizational information security management. Eur. Res. Stud. J. 2024, 27, 35–46. [Google Scholar] [CrossRef]
- Choi, D.; Kim, T. The Concurrent Role of the Chief Information Security Officer and Information Security Performance: Focusing on Information Security Disclosure Data. Korean Manag. Assoc. 2024, 28, 49–63. [Google Scholar]
- Kim, K. A Study on the Comparison of Effective Organizational Leadership According to Organizational Type: Focusing on Situational Theory. Soc. Welf. Manag. Res. 2024, 11, 1–22. [Google Scholar]
- Oh, S.; Son, T.; Lee, C. Major Theories of Organization, 6th ed.; Beomunsa: Paju, Republic of Korea, 2024. [Google Scholar]
- Vehent, J. DevOps Security in Cloud Environments; Hong, S.; Joo, S., Translators; Wikibooks: Paju, Republic of Korea, 2018. [Google Scholar]
- Sun, J.; Jiao, H. Emerging IT investments and firm performance: A perspective of the digital options. Chin. Manag. Stud. 2024, 18, 506–525. [Google Scholar] [CrossRef]
- Agustina, N.; Pramana, S. The impact of development and government expenditure for information and communication technology on Indonesian economic growth. Asian J. Bus. Environ. 2019, 9, 5–13. [Google Scholar] [CrossRef]
- Gartner. 2024 Report. In Korea IT Spending Forecast; Gartner: Stamford, CT, USA, 2024. [Google Scholar]
- Information and Communications Policy Research Institute. ICT Technology Policy Cooperation; Policy Report No. 24-21-01; Korea Information Society Development Institute (KISDI): Jincheon, Republic of Korea, 2024; pp. 1–440. Available online: www.kisdi.re.kr (accessed on 27 August 2024).
- Lee, S.; Shin, G.; Lee, J. A Study on the Relationship between the Adoption of 4th Industrial Revolution Technologies and Productivity in Enterprises: Absolute Level and Relative Position. J. Korean Innov. Soc. 2022, 17, 251–279. [Google Scholar]
- Financial Services Commission. Electronic Financial Supervision Regulations, Article 8, Paragraph 2. 2011. Available online: https://www.fsc.go.kr (accessed on 27 August 2024).
- Shariffuddin, N.; Mohamed, A. IT security and IT governance alignment: A review. In Proceedings of the 3rd International Conference on Networking, Information Systems & Security, New York, NY, USA, 31 March–2 April 2020; pp. 1–8. [Google Scholar]
- Ko, B.; Kim, S.-T. Study on the determinants of growth in SMEs: Focusing on the characteristics based on various growth measurement methods. Financ. Plan. Rev. 2023, 16, 1–28. [Google Scholar]
- Science and Technology Policy Institute. A Study on the Innovation Characteristics of High-Growth Service Companies: Focusing on Innovation Activities and Innovation Outcomes; Science and Technology: Seoul, Republic of Korea, 2023. [Google Scholar]
- Kim, J. A Study on the Current Status and Support Policies for Deep Tech Startups; Korean Chamber of Commerce and Industry in America: New York, NY, USA, 2023. [Google Scholar]
- Lee, K. Operating Profit Sustainability and Managerial Accuracy in Predicting Operating Profit. Tax Account. Res. 2011, 30, 1–17. [Google Scholar]
- Moon, S. A Comparative Study of Global R&D Firm Performance and R&D Investment Support Systems. Asia-Pac. Res. 2024, 31, 114–143. [Google Scholar]
- Kim, H. A Review of Research Trends on the Financial Performance of Medical Institutions. J. Korean Soc. Nurs. Adm. 2023, 29, 76–85. [Google Scholar]
- Korea Credit Guarantee Fund. A Study on Predicting the Risk of Default in Equipment Construction Companies Using Corporate Financial Data; Korea Credit Guarantee Fund: Daegu, Republic of Korea, 2023. [Google Scholar]
- Humphreys, E. Implementing the ISO/IEC 27001: 2013 ISMS Standard; Artech House: Minto, NSW, Australia, 2016. [Google Scholar]
- Broderick, J.S. ISMS, security standards and security regulations. Inf. Secur. Tech. Rep. 2006, 11, 26–31. [Google Scholar] [CrossRef]
- Song, H.; Lee, Y.; Kang, J. Analysis of major defects repeatedly identified in information security and personal information protection management system (ISMS-P) certification audits. J. Korean Soc. Ind. Technol. 2024, 25, 427–432. [Google Scholar]
- Hong, S.; Park, J. Effective Operation of the Information Security and Personal Information Protection Management System (ISMS-P) Certification System. J. Korean Soc. Ind. Technol. 2020, 21, 634–640. [Google Scholar]
- Dyer, J.H.; Singh, H. The relational view: Cooperative strategy and sources of interorganizational competitive advantage. Acad. Manag. Rev. 1998, 23, 660–679. [Google Scholar] [CrossRef]
- Shin, E. The Impact of Security Performance on Business Performance in the Manufacturing Industry: Focusing on the Production Department; Chung Ang University, Graduate School: Seoul, Republic of Korea, 2021. [Google Scholar]
- Zhang, M.J. Information systems, strategic flexibility and firm performance: An empirical investigation. J. Eng. Technol. Manag. 2005, 22, 163–184. [Google Scholar] [CrossRef]
- Galbraith, J.R. Designing Complex Organizations; Addison-Wesley: Boston, MA, USA, 1973. [Google Scholar]
- Lee, H.B.; Kim, Y. The effects of Information System Operating Environment on the Productivity and Performance of Small and Medium Sized Manufacturing Enterprises. J. Korea Soc. Comput. Inf. 2021, 26, 91–102. [Google Scholar]
- Alharbi, A.; Gregg, D. The Impact of IT Investment and IT Security Intensity on Firm Performance. In Proceedings of the 2022 IFIP 8.11/11.13 Dewald Roode Information Security Research Workshop, Denver, CO, USA, 7–8 October 2022; pp. 1–21. Available online: https://ifip.org/ (accessed on 16 June 2025).
- Chawla, R.N.; Goyal, P.; Saxena, D.K. The role of CIO in digital transformation: An exploratory study. Inf. Syst. E-Bus. Manag. 2023, 21, 797–835. [Google Scholar] [CrossRef]
- Solow, R. We’d Better Watch Out. Newyork Times Book Review, 12 July 1987. [Google Scholar]
- Korea Institute of Science and Technology Planning and Evaluation. 2022 Research and Development Activity Survey; Korea Institute of Science and Technology Planning and Evaluation: Eumseong, Republic of Korea, 2024. [Google Scholar]
- Park, S.; Koo, B.; Ham, Y.; Lee, G. Information Technology Investment Costs and Effects: Analysis and Empirical Study of Domestic Companies. Inf. Syst. Rev. 2006, 8, 201–223. [Google Scholar]
- Lee, S. A study on the management of corporate information technology expenditures: An empirical study focused on large enterprises. J. Manag. Inf. Syst. Res. 1999, 9, 1–23. [Google Scholar]
- Korea Internet & Security Agency. In Introduction to the Information Security and Personal Information Protection Management System Certification Information Security Rating System; Korea Internet & Security Agency: Naju, Republic of Korea, 2024.
- Yu, J.Y.; Lee, J.I. Information Security for the Diffusion of New IT Services. Korea Inf. Process. Soc. Rev. 2010, 17, 10–17. [Google Scholar]
- Alghorbany, A.; Che-Ahmad, A.; Abdulmalik, S.O. IT investment and corporate performance: Evidence from Malaysia. Cogent Bus. Manag. 2022, 9, 2055906. [Google Scholar] [CrossRef]
- Rudner, M. Cyber-threats to critical national infrastructure: An intelligence challenge. Int. J. Intell. CounterIntelligence 2013, 26, 453–481. [Google Scholar] [CrossRef]
- Kosutic, D.; Pigni, F. Cybersecurity: Investing for competitive outcomes. J. Bus. Strategy 2022, 43, 28–36. [Google Scholar] [CrossRef]
- Park, J.H.; Lee, J.S.; Bae, J.T. Technology introduction through licensing and innovation performance: Focusing on domestic manufacturing SMEs. SME Res. 2015, 37, 99–125. [Google Scholar]
- Onibere, M.; Ahmad, A.; Maynard, S.B. Dynamic information security management capability: Strategising for organisational performance. arXiv 2021, arXiv:2104.07141. [Google Scholar] [CrossRef]
- Marhad, S.S.; Abd Goni, S.Z.; Sani, M.K.J.A. Implementation of Information Security Management Systems for Data Protection in Organizations: A systematic literature review. Environ.-Behav. Proc. J. 2024, 9, 197–203. [Google Scholar] [CrossRef]
- Bokhari, S.A.A.; Manzoor, S. Impact of information security management system on firm financial performance: Perspective of corporate reputation and branding. Am. J. Ind. Bus. Manag. 2022, 12, 934–954. [Google Scholar] [CrossRef]
- Weishäupl, E.; Yasasin, E.; Schryen, G. Information security investments: An exploratory multiple case study on decision-making, evaluation and learning. Comput. Secur. 2018, 77, 807–823. [Google Scholar] [CrossRef]
- Ministry of Science and ICT. Notice on the Granting of Information Security Management Grades (No. 2017-7); Ministry of Science and ICT: Seoul, Republic of Korea, 2017. [Google Scholar]
- Lee, S.W. The Impact of ISO 22301 and ISMS Certification on Business Continuity Performance: Focusing on Corporate Culture and Processes. Domestic Doctoral Dissertation, Soongsil University Graduate School, Seoul, Republic of Korea, 2021. [Google Scholar]
- Jo, J.-K. A Study on Changes in Corporate Value after Obtaining Information Security Management System (ISMS) Certification. Master’s Thesis, Chungbuk National University Graduate School, Cheongju-si, Republic of Korea, 2016. [Google Scholar]
- Bae, Y. A Study on the Impact of Information Security Management System (ISMS) Certification on Organizational Performance. J. Korean Soc. Ind. Technol. 2012, 13, 4224–4233. [Google Scholar]
- Li, X.; Zhao, L.; Ren, J.; Sun, Y.; Tan, C.F.; Yeo, Z.; Xiao, G. A Unified Framework to Classify Business Activities into International Standard Industrial Classification through Large Language Models for Circular Economy. In Proceedings of the 2024 IEEE International Conference on Industrial Engineering and Engineering Management (IEEM), Bangkok, Thailand, 15–18 December 2024; IEEE: New York, NY, USA, 2024; pp. 1422–1426. [Google Scholar]
- Statistics Korea. Korea Standard Industrial Classification (KSIC). 2024. Available online: https://kostat.go.kr (accessed on 27 August 2024).
- Kakushadze, Z.; Yu, W. Open Source Fundamental Industry Classification. Data 2017, 2, 20. [Google Scholar] [CrossRef]
- Kim, S.J.; Kim, T.S. Analysis of Information Security Management System Certification and Organizational Characteristics Using Information Security Disclosure Data. Korean Soc. Manag. Inf. 2023, 25, 205–231. [Google Scholar]
- National Intelligence Service. National Information Security White Paper. 2024. Available online: https://www.nis.go.kr (accessed on 27 August 2024).
- Kim, S.C.; Park, Y.S. Corporate Asset Composition and Performance: The Impact of Intangible Assets on Corporate Growth and Value. Account. Policy Res. 2022, 27, 59–84. [Google Scholar]
- Lim, J.; Han, J. The Impact of ESG Activities on Management Performance: Focusing on Corporate Size and Disclosure Roles. Commer. Educ. Res. 2022, 36, 29–51. [Google Scholar]
- Rizka, N.R.; Ulfida, D. Asset growth and firm performance: The moderating role of asset utilization. BAJ: Behav. Account. J. 2024, 7, 118–135. [Google Scholar] [CrossRef]
- Rahima, A.Y.; Muid, D. The effect of financial performance and firm size on firm value: Case study of banking companies listed on the Indonesia Stock Exchange in 2018–2020. Tax Account. Appl. J. 2023, 2, 1–8. [Google Scholar] [CrossRef]
- Utami, S.W. The effect of financial performance and capital structure on company value with company size as a moderation variable. Asian J. Econ. Bus. Account. 2023, 23, 112–123. [Google Scholar] [CrossRef]
- Fiana, F.; Endri, E. Corporate social responsibility and financial performance: The moderating role of firm size. Int. J. Econ. Financ. Issues 2025, 15, 244–251. [Google Scholar] [CrossRef]
- Bhandari, P. Control Variables|What Are They & Why Do They Matter? 2023. Scribbr. Available online: https://www.scribbr.com/methodology/control-variable/ (accessed on 16 June 2025).
- Field, A. Discovering Statistics Using IBM SPSS Statistics, 5th ed.; SAGE Publications: Thousand Oaks, CA, USA, 2018. [Google Scholar]
- Cohen, J.; Cohen, P.; West, S.G.; Aiken, L.S. Applied Multiple Regression/Correlation Analysis for the Behavioral Sciences, 3rd ed.; Routledge: Oxfordshire, UK, 2013. [Google Scholar]
- Hayes, A.F. Introduction to Mediation, Moderation, and Conditional Process Analysis: A Regression-Based Approach; Guilford Press: New York, NY, USA, 2013. [Google Scholar]
- Hayes, A.F. Introduction to Mediation, Moderation, and Conditional Process Analysis: A Regression-Based Approach, 2nd ed.; Guilford Publications: New York, NY, USA, 2017. [Google Scholar]
- West, S.G.; Finch, J.F.; Curran, P.J. Structural equation models with nonnormal variables: Problems and remedies. In Structural Equation Modeling: Concepts, Issues, and Applications; Hoyle, R.H., Ed.; SAGE: Atlanta, GA, USA, 1995; pp. 56–75. [Google Scholar]
- Hair, J.F., Jr.; Black, W.C.; Babin, B.J.; Anderson, R.E. Multivariate data analysis. In Multivariate Data Analysis; Prentice Hall: Saddle River, NJ, USA, 2010; p. 785. [Google Scholar]
- Han, J.; Lee, J. The influence of behavioral inhibition temperament on internalizing behavioral problems in infants: The moderating effect of maternal overprotection. J. Emot. Behav. Disord. 2024, 40, 65–84. [Google Scholar]
- Moon, Y.K. The influence of temperamental fear on emotional and anxiety problems in infants: Focusing on the moderating effect of attention regulation and the moderated moderating effect of attention regulation and parental co-parenting. Play Ther. Res. 2022, 26, 1–20. [Google Scholar] [CrossRef]
- Lee, C.S.; Shin, E.M.; Kim, Y.S. Analysis of Mediating Effects, Moderating Effects, and Moderated Mediating Effects Using the Case-Centered PROCESS Macro; Saeron: Cheonan-si, Republic of Korea, 2024. [Google Scholar]
- Seo, S. Security Economics: An Information Security Investment Guide for CEOs; Seoul National University Press: Seoul, Republic of Korea, 2015. [Google Scholar]
- Mithas, S.; Rust, R.T. How information technology strategy and investments influence firm performance. Mis Q. 2016, 40, 223–246. [Google Scholar] [CrossRef]
- Winarno, W.A.; Tjahjadi, B.; Irwanto, A. Time lag effects of IT investment on firm performance: Evidence form Indonesia. J. Ekon. Malays. 2021, 55, 89–101. [Google Scholar]
- Ilmudeen, A.; Bao, Y. Mediating role of managing information technology and its impact on firm performance: Insight from China. Ind. Manag. Data Syst. 2018, 118, 912–929. [Google Scholar] [CrossRef]
- Symons, C.; Cecere, M.; Young, G.O.; Lambert, N. IT Governance Framework: Structures, Processes and Communication; Forrester Research Inc.: Cambridge, MA, USA, 2005. [Google Scholar]

| Research Hypotheses | Theoretical Foundations | References | |
|---|---|---|---|
| Resource-Based View (RBV) | Contingency Theory | ||
| H1/H2 | Security management activities are strategic managerial assets unique to the organization that can demonstrate a competitive advantage. | The appropriateness of security management activities may vary depending on external stakeholders and environmental changes, making context-specific external responses essential. | Donaldson, L. (2003) [16]. Barney, J. B. (1991) [9]. |
| H3/H4 | An independent CISO, as a human capital resource with security expertise, can enhance organizational capabilities, while the integration of the CISO and CIO roles may function as synergistic capabilities that combine technology and security. | The decentralization and integration of authority within an organization should be adjusted according to its structural characteristics and environmental complexity. In environments where both technology and security are critical, role integration can enhance operational efficiency. | Dyer, J. H., & Singh, H. (1998) [40]. Lawrence, P. R., & Lorsch, J. W. (1967) [10]. |
| H5/H6 | IT investment strengthens a company’s technological infrastructure and enables sustained competitive advantage, while security investment is considered a core capability that contributes to long-term performance. | The contribution of IT investment to performance varies depending on industry characteristics and the technological environment, while the level of security investment should be strategically adjusted based on factors such as regulatory requirements, threat landscape, and customer expectations within the industry. | Zhang, M. J. (2005) [42]. Galbraith, J. R. (1973) [43]. |
| MH1~MH7 | ISMS and ISO certifications serve as systematic management resources possessed by the firm, enhancing the effectiveness of the existing activities. | Standardized certification systems function as adaptive strategies to organizational environments and moderate the effects of existing variables on performance. | Donaldson, L. (2003) [16]. Barney, J. B. (1991) [9]. |
| Research Variables | Operational Definition | Measurement Method | References | |
|---|---|---|---|---|
| Independent Variables | Internal Security Management Activities | 2024 Information Security Activities Disclosure Contents ① Implemented information security training for all employees, ② Established an information security committee, or ③ whether an internal information security audit was conducted. | If one or more of ①, ②, or ③ were implemented, dummy 1; if no implementation was conducted, dummy 0. | Jeon, S. J. (2020) [11]; Jang, S. S. (2020) [12]; Posey, C., et al. (2013) [13]. |
| External Security Management Activities | 2024 Disclosure Contents National-level security events ① Participated in the Integrated Security Support Project ② Participated in the Cyber Threat Information (C-TAS), or ③ Participated in security threat simulation exercises (KISA). | If one or more of ①, ②, or ③ were implemented, enter dummy 1; if none were implemented, enter dummy 0. | Kim, A., & Kim, Y. J. (2021) [14]. Garavan, T., & O’Brien, F. (2024) [15]. Donaldson, L. (2003) [16]. | |
| CISO performing duties independently | As of the end of June 2024, based on information disclosed, CISO performing duties independently. | If sole responsibility, dummy 1; if concurrent roles, dummy 0. | Ciekanowski, M., et al. (2024) [17]. Choi, D., & Kim, T. (2024) [18]. | |
| CISO + CIO concurrent positions | As of the end of June 2024, based on information disclosed, CISO concurrent positions with CIO. | If concurrently performing CIO duties, dummy 1; otherwise, dummy 0. | Kim, K. (2024) [19]. Oh S., et al. (2024) [20]. Vehent, J. (2018) [21]. | |
| IT Information Technology Sector Investment Ratio | Average sales from 2022 to 2024, the effective disclosure period, compared to the average IT information technology sector investment performance over three years. | 1 if 3% or more. If less than 3%, dummy 0. | Sun, J., & Jiao, H. (2024) [22]. Agustina, N., & Pramana, S. (2019) [23]. Gartner. (2024) [24]. Information and Communications Policy Research Institute. (2024) [25]. | |
| Information Security Sector Investment Ratio | Effective Disclosure Period 2022–2024 IT Information Technology Sector Average Investment Amount. Ratio 3-Year Average Information Security Sector Investment Execution Performance. | 8% or higher: dummy 1. If less than 8%, dummy 0. | Lee, S., et al. (2022) [26]. Electronic Financial Supervision Regulations. (2011) [27]. Shariffuddin, N., & Mohamed, A. (2020, March) [28]. Rudner, M. (2013) [54]. | |
| Research Variables | Operational Definition | Measurement Method | References | |
|---|---|---|---|---|
| Moderating variables | ISMS (P), ISO/IEC possession | Valid disclosure period 2022–2024 ① ISMS-P or ② ISO 27001 certification acquisition/renewal maintenance status. | ①, ② Among If one or more are met, dummy 1; otherwise, dummy 0 | Humphreys, E. (2016) [36]. Broderick, J. S. (2006) [37]. Song. H., et al. (2024) [38]. Hong, S., & Park, J. (2020) [39]. |
| Dependent Variable | Sales Revenue, Operating Profit | Average performance from 2022 to 2024. | Public Institutions or Financial Institutions Survey Data (Continuous). | Go, B., & Kim, S. (2023) [29]. Science and Technology Policy Institute. (2023) [30]. Kim, J. (2023) [31]. Lee, K. (2011) [32]. Moon, S. (2024) [33]. Kim, H. (2023) [34]. Korea Credit Guarantee Fund. (2023) [35]. |
| Control Variables | IT Industry group status | Based on disclosure content registered as of the end of June 2024 Corporate Industry Classification. | IT industry group: dummy 1. Non-IT industry group: dummy 0 | Information and Communications Policy Research Institute. (2024) [25]. Korea Institute of Science and Technology Evaluation and Planning. (2024) [48]. Li, X., et al. (2024, December) [65]. |
| Industry Classification | Based on disclosure content registered as of the end of June 2024 Corporate Industry Classification. | Manufacturing industry: Dummy 1. Service industry: Dummy 0. | Korean Standard Industrial Classification (2024) [66]. Kakushadze, Z., & Yu, W. (2017) [67]. | |
| Information Security Disclosure Type | Information security disclosure content as of the end of June. 2024 Information security disclosure type classification. | Dummy 1 for companies with disclosure obligations. Dummy 0 for companies with voluntary disclosure. | Kim, S. J. & Kim, T. S. (2023) [68]. National Intelligence Service (2024) [69]. | |
| Asset Size | Asset valuation amounts measured through surveys of public institutions or financial institutions from 2022 to 2024. | $1.5 billion to $4 billion is dummy 1. $250 million to $1.5 billion is dummy 0. | Kim, S. C. & Park, Y. S. (2022) [70]. Lim, J., & Han, J. (2022) [71]. Rizka, N. R., & Ulfida, D. (2024) [72]. Rahima, A. Y., & Muid, D. (2023) [73]. Utami, S. W. (2023) [74]. Fiana, F., & Endri, E. (2025) [75]. | |
| Asset valuation amounts measured through surveys of public institutions or financial institutions from 2022 to 2024. | 1 if $4 billion or more. $250 million to $1.5 billion is 0. | |||
| Characteristic | Category | Frequency (Number) | Percentage (%) |
|---|---|---|---|
| 545 | 100 | ||
| Voluntary/Mandatory | Voluntary | 41 | 7.5 |
| Mandatory | 504 | 92.5 | |
| Industry | Service Industry | 182 | 33.4 |
| Manufacturing Industry | 363 | 66.6 | |
| IT Industry group status | Non-IT Industry | 459 | 84.2 |
| IT Industry | 86 | 15.8 | |
| Asset Size | $250 million or more to less than $1.5 billion | 369 | 67.7 |
| $1.5 billion or more to less than $4 billion | 78 | 14.3 | |
| $4 billion or more | 98 | 18 |
| Research Variable | Category | Frequency (Number) | Percentage (%) |
|---|---|---|---|
| 545 | 100 | ||
| Internal Security Management Activities | Not implemented | 423 | 77.6 |
| Implemented | 122 | 22.4 | |
| External Security Management Activities | Not implemented | 463 | 85 |
| Implemented | 82 | 15 | |
| CISO performing duties independently | No | 433 | 79.4 |
| Yes | 112 | 20.6 | |
| CISO + CIO concurrent positions | No | 453 | 83.1 |
| Yes | 92 | 16.9 | |
| IT Information Technology Sector Investment Ratio | Less than 3% | 468 | 85.9 |
| 3% or more | 77 | 14.1 | |
| Information Security Sector Investment Ratio | Less than 8% | 328 | 60.2 |
| 8% or more | 217 | 39.8 | |
| ISMS (P), ISO/IEC possession | Not certified | 337 | 61.8 |
| Certified | 208 | 38.2 |
| N | Minimum Value | Maximum Value | Average | Standard Deviation | Skewness | Kurtosis | |
|---|---|---|---|---|---|---|---|
| Sales revenue ($80 thousand) | 545 | 23.13 | 3,058,374.17 | 47,085.4145 | 180,592.4621 | 11.084 | 159.028 |
| ln_Sales revenue ($80 thousand) | 545 | 3.140 | 14.930 | 9.341 | 1.505 | 0.194 | 1.851 |
| Operating profit ($80 thousand) | 545 | 0.860 | 378,114.710 | 3634.744 | 21,247.921 | 13.569 | 209.631 |
| ln_Operating profit ($80 thousand) | 545 | −0.150 | 12.840 | 6.289 | 1.796 | 0.013 | 0.876 |
| Research Variables | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1. ln_Sales revenue ($80 thousand) | 1.000 | ||||||||||||
| 2. ln_Operating profit ($80 thousand) | 0.784 *** | 1.000 | |||||||||||
| 3. Voluntary/Mandatory | 0.217 *** | 0.086 * | 1.000 | ||||||||||
| 4. Industry | 0.097 * | 0.024 | 0.167 *** | 1.000 | |||||||||
| 5. IT Industry group status | −0.176 *** | −0.046 | −0.239 *** | −0.611 *** | 1.000 | ||||||||
| 6. Asset Size | 0.753 *** | 0.695 *** | −0.003 | −0.107 * | 0.102 * | 1.000 | |||||||
| 7. Internal Security Management Activities | 0.130 ** | 0.111 ** | −0.030 | −0.198 *** | 0.166 *** | 0.167 *** | 1.000 | ||||||
| 8. External Security Management Activities | 0.055 | 0.078 | −0.211 *** | −0.105 * | 0.128 ** | 0.143 *** | −0.226 *** | 1.000 | |||||
| 9. CISO performing duties independently | 0.097 * | 0.085 * | 0.025 | −0.064 | 0.017 | 0.126 ** | 0.032 | 0.053 | 1.000 | ||||
| 10. CISO + CIO concurrent positions | −0.115 ** | −0.117 ** | 0.017 | −0.003 | −0.074 | −0.096 * | −0.042 | 0.030 | −0.229 *** | 1.000 | |||
| 11. IT Information Technology Sector Investment Ratio | −0.345 *** | −0.202 *** | −0.224 *** | −0.539 *** | 0.663 *** | −0.052 | 0.199 *** | 0.168 *** | 0.028 | 0.014 | 1.000 | ||
| 12. Information Security Sector Investment Ratio | −0.105 * | −0.066 | −0.152 *** | 0.067 | −0.033 | −0.116 ** | −0.005 | 0.046 | −0.033 | 0.044 | −0.072 | 1.000 | |
| 13. ISMS-P, ISO/IEC possession | 0.233 *** | 0.291 *** | −0.177 *** | −0.365 *** | 0.344 *** | 0.404 *** | 0.366 *** | 0.155 *** | 0.124 ** | −0.082 | 0.419 *** | −0.068 | 1.000 |
| Research Variable | B | β | SE | t | p | LLCI | ULCI | VIF | |
|---|---|---|---|---|---|---|---|---|---|
| Independent Variables | Internal Security Management Activities | 0.327 | 0.217 | 0.094 | 3.471 ** | 0.001 | 0.172 | 0.482 | 1.207 |
| External Security Management Activities | 0.262 | 0.062 | 0.110 | 2.379 * | 0.018 | 0.081 | 0.444 | 1.216 | |
| CISO performing duties independently | −0.042 | −0.011 | 0.092 | −0.455 | 0.650 | −0.194 | 0.110 | 1.087 | |
| CISO + CIO concurrent positions | −0.191 | −0.048 | 0.100 | −1.919 + | 0.056 | −0.355 | −0.027 | 1.087 | |
| IT Information Technology Sector Investment Ratio | −1.115 | −0.258 | 0.148 | −7.543 *** | 0.000 | −1.359 | −0.872 | 2.075 | |
| Information Security Sector Investment Ratio | −0.063 | −0.020 | 0.075 | −0.830 | 0.407 | −0.187 | 0.062 | 1.063 | |
| Control Variables | (constant) | 7.999 | 0.178 | 44.888 *** | 0.000 | 7.705 | 8.292 | ||
| Voluntary/Mandatory | 0.922 | 0.162 | 0.145 | 6.368 *** | 0.000 | 0.684 | 1.161 | 1.141 | |
| Industry | −0.040 | −0.013 | 0.100 | −0.401 | 0.688 | −0.204 | 0.124 | 1.729 | |
| IT Industry group status | −0.320 | −0.078 | 0.147 | −2.180 * | 0.030 | −0.561 | −0.078 | 2.234 | |
| Asset size ($1.5 billion or more but less than $4 billion = 1) | 1.207 | 0.281 | 0.107 | 11.320 *** | 0.000 | 1.032 | 1.383 | 1.091 | |
| Asset size ($4 billion or more = 1) | 2.805 | 0.717 | 0.102 | 27.464 *** | 0.000 | 2.637 | 2.974 | 1.204 | |
| F = 112.275 *** (p < 0.001); R2 = 0.699 | |||||||||
| Research Variable | B | β | SE | t | p | LLCI | ULCI | VIF | |
|---|---|---|---|---|---|---|---|---|---|
| Independent Variables | Internal Security Management Activities | 0.171 | 0.095 | 0.142 | 1.201 | 0.230 | −0.063 | 0.405 | 1.207 |
| External Security Management Activities | 0.164 | 0.033 | 0.166 | 0.988 | 0.324 | −0.110 | 0.439 | 1.216 | |
| CISO performing duties independently | −0.055 | −0.012 | 0.139 | −0.394 | 0.693 | −0.284 | 0.174 | 1.087 | |
| CISO + CIO concurrent positions | −0.258 | −0.054 | 0.150 | −1.716 + | 0.087 | −0.505 | −0.010 | 1.087 | |
| IT Information Technology Sector Investment Ratio | −0.810 | −0.157 | 0.223 | −3.629 *** | 0.000 | −1.178 | −0.442 | 2.075 | |
| Information Security Sector Investment Ratio | 0.036 | 0.010 | 0.114 | 0.314 | 0.754 | −0.152 | 0.223 | 1.063 | |
| Control Variables | (constant) | 5.204 | 0.269 | 19.350 *** | 0.000 | 4.761 | 5.647 | ||
| Voluntary/Mandatory | 0.418 | 0.061 | 0.219 | 1.911 + | 0.057 | 0.058 | 0.778 | 1.141 | |
| Industry | 0.031 | 0.008 | 0.150 | 0.205 | 0.837 | −0.217 | 0.279 | 1.729 | |
| IT Industry group status | −0.027 | −0.005 | 0.221 | −0.122 | 0.903 | −0.392 | 0.338 | 2.234 | |
| Asset size ($1.5 billion or more but less than $4 billion = 1) | 1.505 | 0.294 | 0.161 | 9.354 *** | 0.000 | 1.240 | 1.771 | 1.091 | |
| Asset size ($4 billion or more = 1) | 3.114 | 0.666 | 0.154 | 20.198 *** | 0.000 | 2.860 | 3.368 | 1.204 | |
| F = 52.080 *** (p < 0.001); R2 = 0.518 | |||||||||
| Research Variable | Internal Security Management Activities | External Security Management Activities | CISO Performing Duties Independently | CISO + CIO Concurrent Positions | IT Information Technology Sector Investment Ratio | Information Security Sector Investment Ratio | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| B | p | B | p | B | p | B | p | B | p | B | p | ||
| Independent Variable (X) | 0.312 * | 0.048 | 0.059 | 0.707 | −0.196 | 0.129 | −0.080 | 0.510 | −2.340 *** | 0.000 | 0.053 | 0.586 | |
| Moderating variable | ISMS (P), ISO/IEC possession (W) | 0.132 | 0.217 | 0.125 | 0.204 | 0.042 | 0.677 | 0.185 + | 0.061 | 0.248 ** | 0.009 | 0.172 | 0.122 |
| Interaction Term (XW) | −0.254 | 0.206 | −0.052 | 0.811 | 0.373 * | 0.049 | −0.468 | 0.034 | 1.364 *** | 0.000 | −0.141 | 0.382 | |
| Control Variables | (constant) | 7.664 *** | 0.000 | 7.691 *** | 0.000 | 7.730 *** | 0.000 | 7.773 *** | 0.000 | 7.900 *** | 0.000 | 7.682 *** | 0.000 |
| Voluntary/ Mandatory | 0.990 *** | 0.000 | 0.995 *** | 0.000 | 0.987 *** | 0.000 | 0.969 *** | 0.000 | 0.993 *** | 0.000 | 0.983 *** | 0.000 | |
| Industry | 0.141 | 0.175 | 0.132 | 0.202 | 0.142 | 0.170 | 0.094 | 0.365 | −0.045 | 0.647 | 0.137 | 0.187 | |
| IT Industry group status | −0.837 | 0.000 | −0.838 | 0.000 | −0.835 | 0.000 | −0.886 *** | 0.000 | −0.310 | 0.031 | −0.833 | 0.000 | |
| Asset size ($1.5 billion or more but less than $4 billion = 1) | 1.293 *** | 0.000 | 1.3 *** | 0.000 | 1.302 *** | 0.000 | 1.310 *** | 0.000 | 1.199 *** | 0.000 | 1.307 *** | 0.000 | |
| Asset size ($4 billion or more = 1) | 2.972 *** | 0.000 | 2.977 *** | 0.000 | 2.977 *** | 0.000 | 2.934 *** | 0.000 | 2.759 *** | 0.000 | 2.980 *** | 0.000 | |
| Model Fit | F = 132.286 *** (p < 0.001); R2 = 0.664 | F = 130.804 *** (p < 0.001); R2 = 0.661 | F = 132.214 *** (p < 0.001); R2 = 0.664 | F = 134.163 *** (p < 0.001); R2 = 0.667 | F = 162.319 *** (p < 0.001); R2 = 0.708 | F = 131.033 *** (p < 0.001); R2 = 0.662 | |||||||
| Moderating Variable | B | SE | t | p | Bootstrapping CI | |
|---|---|---|---|---|---|---|
| LLCI | ULCI | |||||
| ISMS (P), ISO/IEC Not certified | −0.196 | 0.129 | −1.519 | 0.129 | −0.409 | 0.017 |
| ISMS (P), ISO/IEC Certified | 0.177 | 0.139 | 1.275 | 0.203 | −0.052 | 0.405 |
| Moderating Variable | B | SE | t | p | Bootstrapping CI | |
|---|---|---|---|---|---|---|
| LLCI | ULCI | |||||
| ISMS (P), ISO/IEC Not certified | −0.080 | 0.121 | −0.659 | 0.510 | −0.279 | 0.120 |
| ISMS (P), ISO/IEC Certified | −0.548 | 0.184 | −2.971 ** | 0.003 | −0.852 | −0.244 |
| Moderating Variable | B | SE | t | p | Bootstrapping CI | |
|---|---|---|---|---|---|---|
| LLCI | ULCI | |||||
| ISMS (P), ISO/IEC Not certified | −2.340 | 0.294 | 7.963 *** | 0.000 | −2.824 | −1.856 |
| ISMS (P), ISO/IEC Certified | −0.975 | 0.158 | 6.164 *** | 0.000 | −1.236 | −0.715 |
| Research Variable | Internal Security Management Activities | External Security Management Activities | CISO Performing Duties Independently | CISO + CIO Concurrent Positions | IT Information Technology Sector Investment Ratio | Information Security Sector Investment Ratio | |||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| B | p | B | p | B | p | B | p | B | p | B | p | ||
| Independent Variable (X) | −0.020 | 0.931 | 0.023 | 0.918 | −0.213 | 0.253 | −0.193 | 0.271 | −2.129 *** | 0.000 | 0.154 | 0.276 | |
| Moderating variable | ISMS (P), ISO/IEC possession (W) | 0.306 * | 0.049 | 0.308 * | 0.030 | 0.225 | 0.122 | 0.328 * | 0.022 | 0.407 ** | 0.005 | 0.380 * | 0.018 |
| Interaction Term (XW) | 0.007 | 0.982 | −0.038 | 0.904 | 0.381 | 0.162 | −0.220 | 0.490 | 1.292 ** | 0.005 | −0.198 | 0.394 | |
| Control Variables | (constant) | 4.864 *** | 0.000 | 4.86 *** | 0.000 | 4.891 *** | 0.000 | 4.937 *** | 0.000 | 5.034 *** | 0.000 | 4.777 *** | 0.000 |
| Voluntary/ Mandatory | 0.487 * | 0.024 | 0.486 * | 0.027 | 0.485 * | 0.024 | 0.476 * | 0.027 | 0.494 * | 0.019 | 0.503 * | 0.021 | |
| Industry | 0.229 | 0.127 | 0.229 | 0.125 | 0.238 | 0.111 | 0.199 | 0.184 | 0.072 | 0.629 | 0.230 | 0.124 | |
| IT Industry group status | −0.441 | 0.024 | −0.439 | 0.025 | −0.437 | 0.024 | −0.419 | 0.014 | 0.020 | 0.925 | −0.430 | 0.027 | |
| Asset size ($1.5 billion or more but less than $4 billion = 1) | 1.514 *** | 0.000 | 1.511 *** | 0.000 | 1.510 *** | 0.000 | 1.522 *** | 0.000 | 1.420 *** | 0.000 | 1.524 *** | 0.000 | |
| Asset size ($4 billion or more = 1) | 3.128 *** | 0.000 | 3.127 *** | 0.000 | 3.125 *** | 0.000 | 3.091 *** | 0.000 | 2.936 *** | 0.000 | 3.134 *** | 0.000 | |
| Model Fit | F = 68.801 *** (p < 0.001); R2 = 0.507 | F = 68.801 *** (p < 0.001); R2 = 0.507 | F = 69.312 *** (p < 0.001); R2 = 0.508 | F = 69.708 *** (p < 0.001); R2 = 0.510 | F = 76.377 *** (p < 0.001); R2 = 0.533 | F = 69.115 *** (p < 0.001); R2 = 0.510 | |||||||
| Moderating Variable | B | SE | t | p | Bootstrapping CI | |
|---|---|---|---|---|---|---|
| LLCI | ULCI | |||||
| ISMS (P), ISO/IEC Not certified | −2.129 | 0.443 | 4.800 *** | 0.000 | −2.860 | −1.398 |
| ISMS (P), ISO/IEC Certified | −0.837 | 0.239 | 3.505 *** | 0.000 | −1.231 | −0.444 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cho, H.; Cho, K. Impact of Security Management Activities on Corporate Performance. Systems 2025, 13, 633. https://doi.org/10.3390/systems13080633
Cho H, Cho K. Impact of Security Management Activities on Corporate Performance. Systems. 2025; 13(8):633. https://doi.org/10.3390/systems13080633
Chicago/Turabian StyleCho, Hyunwoo, and Keuntae Cho. 2025. "Impact of Security Management Activities on Corporate Performance" Systems 13, no. 8: 633. https://doi.org/10.3390/systems13080633
APA StyleCho, H., & Cho, K. (2025). Impact of Security Management Activities on Corporate Performance. Systems, 13(8), 633. https://doi.org/10.3390/systems13080633





