Generic Architecture for Self-Organized Adaptive Platform System of Systems
Abstract
1. Introduction
2. Background
3. Methods
4. Generic Architecture Principles for Platform SOS
4.1. Modularity
4.2. Adaptability
4.3. Interoperability
4.4. Redundancy
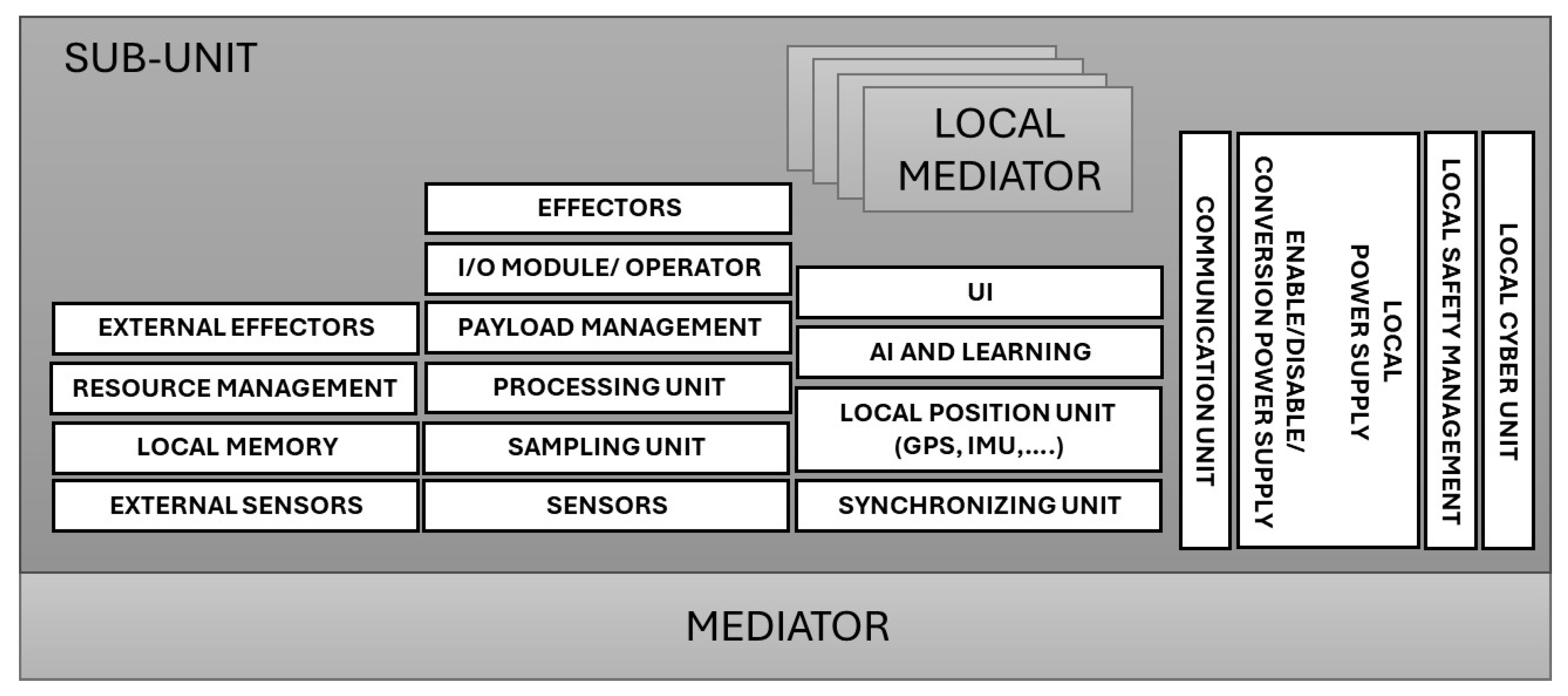
5. The Generic Architecture Model of a Self-Organized Adaptive Platform SOS
5.1. The Model
5.2. The Main Layers
5.3. Transverse Layers
5.4. Main Components
6. Case Study
6.1. Overview
6.2. Upgrades from the Previous Generation of Fighters to F-35 JSF First Version
- Information sharing between the sensor and the vehicle system is enabled only through the ICP.
- Information sharing between effectors, such as fire control, is enabled only within the ICP.
- Lack of governance unit.
- Lack of cybersecurity and safety layers.
- There are no physical or virtual mediators in the general architecture to allow new information sharing with legacy components.
6.3. Upgrades from the F-35 JSF First Version to the Fusion Architecture
- Information sharing between the sensor and vehicle system/mission system flows via the fusion algorithms and creates a single point of failure.
- Lack of information sharing between effectors and all other components.
- Lack of governance unit.
- Lack of cybersecurity and safety layers.
7. Discussion
8. Conclusions
- Adaptability: by incorporating principles of modularity and standardization, the model enables platforms to adapt to new scenarios and requirements that may not have been foreseen during the initial design phase.
- Simplified system engineering: the generic architecture serves as a valuable tool for system architects, providing a baseline structure that ensures all necessary logical and physical components are considered; this approach can significantly streamline the design process and reduce the likelihood of overlooking critical elements.
- Cost and time efficiency: by embedding the infrastructure for change within the system architecture, the model minimizes the need for extensive redesign and redevelopment when modifications are required; this can lead to substantial savings in both cost and time over the system’s lifecycle.
- Enhanced interoperability: the emphasis on standardized interfaces and modular design facilitates easier integration of new components and payloads, promoting a “plug-and-play” functionality that can extend the platform’s capabilities over time.
- Futureproofing: the architecture’s focus on self-organization and adaptability prepares platforms to handle unforeseen operational scenarios and evolving stakeholder needs, ensuring their continued relevance and effectiveness.
- Explore the application of this generic architecture model to other domains beyond aerial platforms (land or sea platforms). Demonstrate additional test cases and their improvement using additional elements in the generic architecture.
- Deepen the design of the components of the connectivity layer.
- Explore how to identify the need for a change in the system state and the essence of the change in the system. Future research is required to complete the logic that identifies the change and determines the necessary adjustments. This work suggests that the AI and governance components incorporated into the architecture can implement this logic.
- Architecture model quantitative validation.
- Quantitative risk analysis to address the model redundancy and handle single points of failure. Furthermore, quantitative examination of the number of connections in a system when designed according to the model, where the connectivity layer connects all system components.
- Expand the architectural model to collaborative and virtual SOSs.
- Amplify the utility of the generic architecture model by coupling it with existing architecture frameworks, such as DoDAF.
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Bar-Yam, Y. Unifying principles in complex systems. In Converging Technologies for Improving Human Performance: Nanotechnology, Biotechnology, Information Technology and Cognitive Science; Springer: Dordrecht, The Netherlands, 2003; pp. 380–409. [Google Scholar]
- Hybertson, D.W. Model-Oriented Systems Engineering Science: A Unifying Framework for Traditional and Complex Systems; Auerbach Publications: New York, NY, USA, 2016. [Google Scholar]
- Goerger, S.; Madni, A.; Eslinger, O. Engineered resilient systems: A DoD perspective. Procedia Comput. Sci. 2014, 28, 865–872. [Google Scholar] [CrossRef]
- Bar-Yam, Y.; McKay, S.; Christian, W. Dynamics of complex systems (studies in nonlinearity). Comput. Phys. 1998, 12, 335–336. [Google Scholar] [CrossRef]
- Ladyman, J.; Lambert, J.; Wiesner, K. What is a complex system? Eur. J. Philos. Sci. 2013, 3, 33–67. [Google Scholar] [CrossRef]
- Birdsey, L.; Szabo, C.; Falkner, K. Identifying self-organization and adaptability in complex adaptive systems. In Proceedings of the 2017 IEEE 11th International Conference on Self-Adaptive and Self-Organizing Systems (SASO), Tucson, AZ, USA, 18–22 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 131–140. [Google Scholar]
- Maier, M.W. Architecting principles for systems-of-systems. Syst. Eng. J. Int. Counc. Syst. Eng. 1998, 1, 267–284. [Google Scholar] [CrossRef]
- Dahmann, J.S.; Baldwin, K.J. Understanding the current state of US defense systems of systems and the implications for systems engineering. In Proceedings of the 2008 2nd Annual IEEE Systems Conference, Montreal, QC, Canada, 7–10 April 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 1–7. [Google Scholar]
- Madni, A. Adaptable platform-based engineering: Key enablers and outlook for the future. Syst. Eng. 2012, 15, 95–107. [Google Scholar] [CrossRef]
- Schöpping, T.; Korthals, T.; Hesse, M.; Rückert, U. Generic Architecture for Modular Real-time Systems in Robotics. In Proceedings of the ICINCO 2018, Portu, Portugal, 29–31 July 2018; Volume 2, pp. 413–420. [Google Scholar]
- Engel, A.; Reich, Y. Advancing architecture options theory: Six industrial case studies. Syst. Eng. 2015, 18, 396–414. [Google Scholar] [CrossRef]
- Gaide, B.; Gaitonde, D.; Ravishankar, C.; Bauer, T. Xilinx adaptive compute acceleration platform: Versaltm architecture. In Proceedings of the 2019 ACM/SIGDA International Symposium on Field-Programmable Gate Arrays, Seaside, CA, USA, 24–26 February 2019; pp. 84–93. [Google Scholar]
- Reich, Y.; Sitton, M.; Engel, A.; Orion, U.; Danielli, A.; Hauptman, A.; Blekhman, A.; Shabi, J. Context-Dependent Research Agenda for Systems Engineering in 2050. In Proceedings of the Conference on Systems Engineering Research, Hoboken, NJ, USA, 16–17 March 2023; Springer Nature: Cham, Switzerland, 2023; pp. 655–661. [Google Scholar]
- Miller, W.D. The future of systems engineering: Realizing the systems engineering vision 2035. In Transdisciplinarity and the Future of Engineering; IOS Press: Amsterdam, The Netherlands, 2022; pp. 739–747. [Google Scholar]
- Petitdemange, F.; Borne, I.; Buisson, J. Assisting the evolutionary development of SoS with reconfiguration patterns. In Proceedings of the 10th European Conference on Software Architecture Workshops, Copenhagen, Denmark, 28 November–2December 2016; pp. 1–7. [Google Scholar]
- Cronel, M.; Dumas, B.; Palanque, P.; Canny, A. MIODMIT: A generic architecture for dynamic multimodal interactive systems. In Human-Centered Software Engineering, Proceedings of the 7th IFIP WG 13.2 International Working Conference, HCSE 2018, Sophia Antipolis, France, 3–5 September 2018; Revised Selected Papers 7; Springer International Publishing: Cham, Switzerland, 2019; pp. 109–129. [Google Scholar]
- Wang, W.; Lee, K.; Murray, D. A global generic architecture for the future Internet of Things. Serv. Oriented Comput. Appl. 2017, 11, 329–344. [Google Scholar] [CrossRef]
- Iqbal, J.; Khan, M.; Talha, M.; Farman, H.; Jan, B.; Muhammad, A.; Khattak, H.A. A generic internet of things architecture for controlling electrical energy consumption in smart homes. Sustain. Cities Soc. 2018, 43, 443–450. [Google Scholar] [CrossRef]
- Woods, D.D. Four concepts for resilience and the implications for the future of resilience engineering. Reliab. Eng. Syst. Saf. 2015, 141, 5–9. [Google Scholar] [CrossRef]
- Broniatowski, D.A.; Moses, J. Measuring flexibility, descriptive complexity, and rework potential in generic system architectures. Syst. Eng. 2016, 19, 207–221. [Google Scholar] [CrossRef]
- Jamshidi, M. Introduction to system of systems. In Systems of Systems Engineering; CRC Press: Boca Raton, FL, USA, 2017; pp. 1–36. [Google Scholar]
- Vargas, I.G.; Gottardi, T.; Braga, R.T.V. An approach to integrate systems towards a directed system-of-systems. In Proceedings of the 12th European Conference on Software Architecture: Companion Proceedings, Madrid, Spain, 24–28 September 2018; pp. 1–7. [Google Scholar]
- Sitton, M.; Reich, Y. EPIC framework for enterprise processes integrative collaboration. Syst. Eng. 2018, 21, 30–46. [Google Scholar] [CrossRef]
- Oreizy, P.; Gorlick, M.M.; Taylor, R.N.; Heimhigner, D.; Johnson, G.; Medvidovic, N.; Quilici, A.; Rosenblum, D.S.; Wolf, A.L. An architecture-based approach to self-adaptive software. IEEE Intell. Syst. Their Appl. 1999, 14, 54–62. [Google Scholar] [CrossRef]
- Fang, Z.; DeLaurentis, D.; Davendralingam, N. An approach to facilitate decision making on architecture evolution strategies. Procedia Comput. Sci. 2013, 16, 275–282. [Google Scholar] [CrossRef]
- Zhou, B.; Dvoryanchikova, A.; Lobov, A.; Lastra, J.L.M. Modeling system of systems: A generic method based on system characteristics and interface. In Proceedings of the 2011 9th IEEE International Conference on Industrial Informatics, Lisbon, Portugal, 26–29 July 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 361–368. [Google Scholar]
- Chen, T.; Bahsoon, R.; Yao, X. Synergizing domain expertise with self-awareness in software systems: A patternized architecture guideline. Proc. IEEE 2020, 108, 1094–1126. [Google Scholar] [CrossRef]
- Boyd, J.R. A Discourse on Winning and Losing; Air University Press: Maxwell Air Force Base, AL, USA, 2018; Volume 400. [Google Scholar]
- Hoffmann, H.; Maggio, M.; Santambrogio, M.D.; Leva, A.; Agarwal, A. SEEC: A General and Extensible Framework for Self-Aware Computing; MIT-CSAIL: Cambridge, MA, USA, 2011. [Google Scholar]
- Brehmer, B. The dynamic OODA loop: Amalgamating Boyd’s OODA loop and the cybernetic approach to command and control. In Proceedings of the 10th International Command and Control Research Technology Symposium, McLean, Virginia, 13–16 June 2005; pp. 365–368. [Google Scholar]
- Giese, H.; Vogel, T.; Diaconescu, A.; Götz, S.; Kounev, S. Architectural concepts for self-aware computing systems. In Self-Aware Computing Systems; Springer: Cham, Switzerland, 2017; pp. 109–147. [Google Scholar]
- Ingram, C.; Payne, R.; Perry, S.; Holt, J.; Hansen, F.O.; Couto, L.D. Modelling patterns for systems of systems architectures. In Proceedings of the 2014 IEEE International Systems Conference Proceedings, Ottawa, ON, Canada, 31 March–3 April 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 146–153. [Google Scholar]
- Crawley, E.; Cameron, B.; Selva, D. System Architecture: Strategy and Product Development for Complex Systems; Prentice Hall Press: Hoboken, NJ, USA, 2015. [Google Scholar]
- Annighoefer, B.; Riedlinger, M.; Marquardt, O.; Ahmadi, R.; Schulz, B.; Brunner, M.; Reichel, R. The adaptive avionics platform. IEEE Aerosp. Electron. Syst. Mag. 2019, 34, 6–17. [Google Scholar] [CrossRef]
- DoD. Department of Defense Architecture Framework (DoDAF) Version 2.02; U.S. Department of Defense: Arlington County, VA, USA, 2010.
- TheOpenGroup 1. The Open Group Architecture (TOGAF); The Open Group: Boston, MA, USA, 2009. [Google Scholar]
- Ministry of Defence. Defence Standard 23-09, Issue 1 Publication Date 20 August 2010, Generic Vehicle Architecture (GVA), D/DStan/36/9, UK Defence Standardization Kentigern House 65 Brown Street GLASGOW G2 8EX; UK Defence Standardization: Glasgow, UK, 2010.
- Yin, R.K. Applications of Case Study Research; Sage: New York, NY, USA, 2012; Volume 34. [Google Scholar]
- Sinha, K.; Suh, E.S. Pareto-optimization of complex system architecture for structural complexity and modularity. Res. Eng. Des. 2018, 29, 123–141. [Google Scholar] [CrossRef]
- Hölttä-Otto, K.; De Weck, O. Metrics for assessing coupling density and modularity in complex products and systems. In Proceedings of the International Design Engineering Technical Conferences and Computers and Information in Engineering Conference, Las Vegas, NV, USA, 4–7 September 2007; Volume 48043, pp. 343–352. [Google Scholar]
- Engel, A.; Browning, T.R. Designing systems for adaptability by means of architecture options. Syst. Eng. 2008, 11, 125–146. [Google Scholar] [CrossRef]
- Nešić, D.; Krüger, J.; Stănciulescu, Ș.; Berger, T. Principles of feature modeling. In Proceedings of the 2019 27th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Tallinn, Estonia, 26–30 August 2019; pp. 62–73. [Google Scholar]
- Sered, Y.; Reich, Y. Standardization and modularization driven by minimizing overall process effort. Comput.-Aided Des. 2006, 38, 405–416. [Google Scholar] [CrossRef]
- Trunzer, E.; Calà, A.; Leitão, P.; Gepp, M.; Kinghorst, J.; Lüder, A.; Vogel-Heuser, B. System architectures for Industrie 4.0 applications: Derivation of a generic architecture proposal. Prod. Eng. 2019, 13, 247–257. [Google Scholar] [CrossRef]
- Uday, P.; Marais, K. Designing resilient systems-of-systems: A survey of metrics, methods, and challenges. Syst. Eng. 2015, 18, 491–510. [Google Scholar] [CrossRef]
- Derigent, W.; David, M.; André, P.; Cardin, O. Generic aggregation model for reconfigurable holonic control architecture–the GARCIA framework. In Proceedings of the International Workshop on Service Orientation in Holonic and Multi-Agent Manufacturing, Bucharest, Romania, 22–23 September 2022; Springer International Publishing: Cham, Switzerland, 2022; pp. 407–422. [Google Scholar]
- Sitton, M.; Reich, Y. Enterprise systems engineering for better operational interoperability. Syst. Eng. 2015, 18, 625–638. [Google Scholar] [CrossRef]
- Bone, M.A.; Blackburn, M.R.; Rhodes, D.H.; Cohen, D.N.; Guerrero, J.A. Transforming systems engineering through digital engineering. J. Def. Model. Simul. 2019, 16, 339–355. [Google Scholar] [CrossRef]
- Keating, C.B.; Katina, P.F. Complex system governance: Concept, utility, and challenges. Syst. Res. Behav. Sci. 2019, 36, 687–705. [Google Scholar] [CrossRef]
- Wong, T.; Wagner, M.; Treude, C. Self-adaptive systems: A systematic literature review across categories and domains. Inf. Softw. Technol. 2022, 148, 106934. [Google Scholar] [CrossRef]
- Shaked, A. A model-based methodology to support systems security design and assessment. J. Ind. Inf. Integr. 2023, 33, 100465. [Google Scholar] [CrossRef]
- VanderLeest, S.H. Designing a future airborne capability environment (FACE) hypervisor for safety and security. In Proceedings of the 2017 IEEE/AIAA 36th Digital Avionics Systems Conference (DASC), St. Petersburg, FL, USA, 17–21 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–9. [Google Scholar]
- Gaska, T.; Watkin, C.; Chen, Y. Integrated modular avionics-past, present, and future. IEEE Aerosp. Electron. Syst. Mag. 2015, 30, 12–23. [Google Scholar] [CrossRef]
- Wiegand, C. F-35 air vehicle technology overview. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, Georgia, 25–29 June 2018; p. 3368. [Google Scholar]
- Lemons, G.T.; Carrington, K. F-35 mission systems design, development & verification. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, Georgia, 25–29 June 2018; p. 3519. [Google Scholar]
- Frey, T.L.; Aguilar, C.; Engebretson, K.; Faulk, D.; Lenning, L.G. F-35 information fusion. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, Georgia, 25–29 June 2018; p. 3520. [Google Scholar]
- Filyner, B. Open systems avionics architectures considerations. IEEE Aerosp. Electron. Syst. Mag. 2003, 18, 3–10. [Google Scholar] [CrossRef]
- Robbins, D.; Bobalik, J.; De Stena, D.; Martin, N.; Plag, K.; Rail, K.; Wall, K. F-35 subsystems design, development & verification. In Proceedings of the 2018 Aviation Technology, Integration, and Operations Conference, Atlanta, Georgia, 25–29 June 2018; p. 3518. [Google Scholar]
- Garrison, P.E. The architecture of the F-35 lightning II mission system integration lab then and now. In Proceedings of the Annual Conference of the International Test and Evaluation Association, Huntsville, AL, USA, 1–3 October 2019. [Google Scholar]
- Gershenson, C. Guiding the self-organization of cyber-physical systems. Front. Robot. AI 2020, 7, 41. [Google Scholar] [CrossRef]
- Giordano, A.; Spezzano, G.; Vinci, A. A smart platform for large-scale cyber-physical systems. In Management of Cyber Physical Objects in the Future Internet of Things: Methods, Architectures and Applications; Springer: Cham, Switzerland, 2016; pp. 115–134. [Google Scholar]





Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sitton, M.; Alon, R.; Reich, Y. Generic Architecture for Self-Organized Adaptive Platform System of Systems. Systems 2025, 13, 368. https://doi.org/10.3390/systems13050368
Sitton M, Alon R, Reich Y. Generic Architecture for Self-Organized Adaptive Platform System of Systems. Systems. 2025; 13(5):368. https://doi.org/10.3390/systems13050368
Chicago/Turabian StyleSitton, Miri, Rozi Alon, and Yoram Reich. 2025. "Generic Architecture for Self-Organized Adaptive Platform System of Systems" Systems 13, no. 5: 368. https://doi.org/10.3390/systems13050368
APA StyleSitton, M., Alon, R., & Reich, Y. (2025). Generic Architecture for Self-Organized Adaptive Platform System of Systems. Systems, 13(5), 368. https://doi.org/10.3390/systems13050368






