Abstract
City zones have become increasingly overcrowded due to the extensive population widening ratio and the swift relocation of people from villages. The traffic monitoring process is a significant issue in these areas due to the massive traffic flow on the roads. This research proposed a cluster-based improved authentication and communication protocol for an Intelligent Transportation System in Vehicular AdHoc Networks (VANETs). Our primary objective is to optimize resource sharing in vehicular communication. We enhanced the reliability, scalability, and stability of fast-moving VANETs by introducing cluster-based routing protocols for Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) communications. We used a third-party certification authority for vehicle authentication to address security and privacy concerns. Our proposed protocol support minimizes the end-to-end (E2E) delay and route request and reduces link failure. Our protocol’s leading yield includes throughput enhancement, TCP Socket Initialization time minimization, TCP handshake response speedup, and DNS lookup improvement. The protocols are centered on short-range peer-to-peer (P2P) wireless communication in a 400 m radius cluster. They include innovative P2P wireless communications on VANET using minimized resources. The proposed protocols deliver a secure authentication mechanism with a securely generated vehicle authentication key provided by a certification authority. Furthermore, we have developed RESTful APIs in vehicular communication for implementation purposes and also offered and implemented algorithms for resource sharing regarding V2V and V2I communication. Ultimately, we evaluated the performance of our experiments.
1. Introduction
The rapid migration of people from villages to cities has produced major threats regarding controlling the increased traffic. Traffic congestion in a city environment has now become the focal point of many researchers. Vehicular AdHoc networks provide an Intelligent Transportation System with the help of Road Side Units (RSU). These networks are the primary source of improving driving safety by decreasing road side accidents [1]. However, RSU message passing is categorized under Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) Communication. VANETs help minimize road side accidents and recognize the positions of vehicles moving along the same track. On VANETs, spotting emergency vehicles, such as patrol cars and ambulances, is easy. This process is subject to acquiring the moving vehicle’s actual location. According to the survey authors of [2], location-based communication in moving vehicles is the critical application of VANETs, as Internet of Vehicles (IoV) communication faces many distortion-related issues. There is a belief that Intelligent Transportation Systems employ the Internet of Everything (IoE). The authors’ paper also discusses monitoring the traffic flow using edge computing in VANETs [3]. Resource sharing is one of the significant issues involved with vehicular communication. Resource sharing in high-vehicle mobility requires significant power consumption, a severe obstacle in vehicular communication [4]. Distributed resource management is beneficial to optimize resource utilization and reduce network signal overhead [5]. P2P (peer-to-peer) systems using a wireless network are growing in popularity due to the evolution of the Internet. These systems provide optimal performance while sharing messages and other resources. Road safety applications using P2P wireless networks are also becoming a vital part of the VANET for traffic monitoring [6,7]. For Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I), the area is selected by determining a particular cluster or through a distance radius. An Intelligent Traffic System brings numerous benefits to traffic management [8]. These benefits include on-the-mark traffic monitoring, proper traffic congestion analysis, sending accurate traffic violation warnings to drivers, traffic infrastructure analysis, and sending messages using V2V and V2I communication [9].
In an ITS, the average message response time typically takes up to 10 times in milliseconds. The cluster or a distance radius usually has a radius range of approximately 400-m. On a Vehicular AdHoc Network, the message passing can be done through textual, graphic, and audible information. The VANET must be secured against cyber-attacks, unauthorized access, identity theft, and phishing [10]. It may be stated that VANET security is breached when someone gains unauthorized access to a particular Vehicle Onboard Unit (OBU) and can alter or hinder the vehicle’s main functionality. Due to traffic congestion or insufficient road infrastructure, vehicle collision is possible [11]. The “Crash Possibility” message can be conveyed to the vehicle to overcome this issue. Distance measurement is necessary to generate a collision warning message, which can be performed using a camera and a sensor [12]. There is a problem of false messages passing for vehicle collision warnings. To eliminate this issue, we employed the services of a third-party certification authority (CA). The CA will carry out multiple functions like vehicle registration and vehicle authentication. It also acts as a bridge for V2V and V2I communications. Due to authentication with CA, the identity of the false message sender can be highlighted, as shown in Table 1.

Table 1.
Indexed Terms Meanings.
We proposed secure cluster-based authentication and communication protocols for Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) communications. Our work covers the following phases for V2I and V2V communications and resource sharing in a VANET.
- Authentication and registration using third-party certification authority.
- V2I and V2I Communication Channel.
- Graph-Based Resource Sharing in Vehicular Communication.
We took up assistance from the third-party certification authority for registration and authentication, and demonstrated the V2V and V2I communication mechanism in a 400 m diameter. There is much distortion in the moving vehicle, so we set the 400 m cluster for a specific VANET. We addressed primary security goals such as integrity, authenticity, and availability of messages in vehicular communication on a specific cluster. Figure 1 simplifies the Vehicle-to-Vehicle communication in a 400 m cluster. CH means the Head of the Cluster, and CM denotes the other Cluster Member. We proposed two algorithms based on baseline and greedy approaches for resource allocation in vehicular communications.
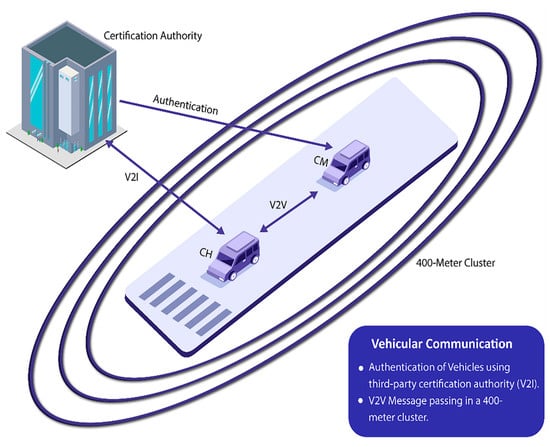
Figure 1.
Vehicular communication in a 400 m diameter.
Section 1 addresses the introduction and research contribution. In Section 2, we discuss previous studies relevant to the research. The various past research contributions on VANET are exhibited by a table. Section 3 includes the research methodology, implementation, performance evaluation, results, and discussions. The methodology section demonstrates the proposed protocol, implementation, and graph-based resource sharing in vehicular communications. This section further addresses notations and assumptions, research results, and performance evaluation. In the implementation subsection, we have discussed the utilized tools and technologies. Ultimately, the paper ends with a conclusion section.
2. Literature Review
In VANETs, the significant contribution of the researchers includes (a) a central service directory architecture [13], (b) directory-less service architecture [14,15,16], and (c) distributed directory service architecture [15,17,18,19,20]. In the first portion, based on central service discovery architecture, the researchers proposed a central discovery server to store the service information and re-join a discovery request with the matched discovery outcomes. Ali et al. [21] discussed a three-way link between 5G technology, Software-Defined Networks, and Vehicular AdHoc Networks. The authors concentrated on creating a network balance by highlighting the mobility, security, and performance of software-defined networks (SDN). Some authors of discussed mystery location-oriented and self-reliance protocols for Mobile AdHoc Network routing [22]. They anticipated their views on a secure packet delivery mechanism in MANETs for vehicular communications. Edge et al. [23] discussed the techniques and methods for providing location-based services for users’ tools by requiring assistance from Service-Based Interfaces.
Other authors [15] proposed the idea of edge computing in Vehicular AdHoc Networks using bit-blocking protocol infrastructure, and elucidated the use and function of wireless Vehicular AdHoc Networks [16]. They differentiated the structure of MANETs and Cellular Networks. Yang et al. [15] clarified the Vehicle-to-Vehicle (V2V) communications using peer-to-peer networks by employing graph theory and consensus algorithm. In addition, some scholars omitted the Road Side Units and defined the serial communication between vehicles moving along the road, and conducted three focus groups and eight individual interviews to address trust and privacy matters in peer-to-peer networks [17]. Shah et al. [18] provided a visual paradigm of VANET in a 5G technology-based network. Singh et al. [19] described the concept of vehicular cloud by using P2P routing protocols to prevent road accidents, monitor traffic, and ensure fast content delivery, and wrote a survey paper on state-of-the-art vehicular communications and future directions for further studies [19,20]. Salem et al. [24] proposed a self-organized framework for VANETs. They applied mathematical analysis to their proposed framework to enhance security goals. They also evaluated their framework’s performance in terms of computation complexity, storage, and communication overhead. By comparing several schemes, they also tested their framework against several types of external attacks. The authors of [25,26] evaluated the performance of vehicular communication on P2P wireless networks, while the authors of [27,28,29,30] discussed several security issues and challenges in VANETs with multiple dimensions, including P2P wireless networks. Table 2 lists VANET (Vehicular AdHoc Network) routing protocols based on transmission strategy and route formation, while Table 3 consists of the comparison of previous research over vehicular communication and VANETs.:

Table 2.
Listing VANET (Vehicular AdHoc Network) routing protocols.

Table 3.
Related Work Comparison.
Table 3 compares related works on Vehicular Communication with paper reference, publishing year, and significant contribution attributes. (✔) indicates that the topic is covered completely, whereas (✗) means no discussion is present, and (✽) conveys that the topic is covered partially.
Routing protocols are crucial in vehicular AdHoc networks, facilitating message transmission between nodes and enabling various services. Two main categories of VANET routing protocols exist: Topological Routing Protocols (TRPs) and Geographic Routing Protocols (GRPs). TRPs focus on maintaining data links and disseminating topological data. However, they face scalability issues, time-consuming discovery, complex control requirements, and cumbersome maintenance. In contrast, GRPs rely on up-to-date location information to establish connections with moving vehicles, with optional data dissemination. GRPs excel in highly dynamic, large-scale networks due to their simplicity, low overhead, superior performance, and scalability. These protocols adjust routes based on precise vehicle coordinates [53,54,55,56,57]. Figure 2 depicts the hierarchical structure of routing protocols and their key components.
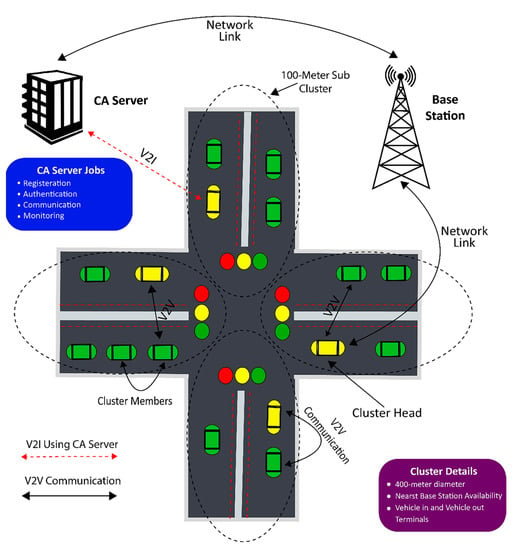
Figure 2.
V2V and V2I Communication on our proposed VANET.
Liang et al. proposed vehicular communication resource allocation and power sharing [32]. High capacity for V2I connections and UR for V2V links were discussed. They suggested efficient resource allocation methods for power-sharing and resource allocation. Zhang et al. [33] suggested a feasible vehicular network model with anticipatory off-loading. Mobile edge computing was used to describe cloud-based vehicle networks in several dimensions. They discussed the mobility and calculation time of V2V and V2I communication modalities. Burg et al. [34] discussed wireless network structure and standards. They investigated a cumulative smart grid model for vehicle mobility and wireless technology. They also covered wireless technology, ranges, and IoT security.
Al-Kinani et al. [35] suggested wireless infrared network architectures and communication channel measurements. They examined over 20 optical wireless communication models for various communication circumstances. Rahman et al. [36] discussed superhighway-linked car longitudinal safety evaluation. A linked car network and high-level control algorithm revealed their intelligent driver model. They suggested time-to-collision, rear-end crash risk index, and sideswipe crash risk for three joining categories: front, rear, and cut. Al-Shareeda et al. and Sugumar, Rengarajan, and Jayakumar [42,58] suggested VANET privacy-preserving communication. They combined identity-based encryption with elliptic curve cryptography. Server impersonation, replay, modification, and man-in-the-middle attacks were covered.
Kolandaisamy et al. [59] recommended models for cluster-based routing in Vehicular AdHoc Networks (VANETs) and a performance measurement approach for security, specifically focused on stream position analysis. Additionally, their approach for detecting Distributed Denial of Service (DDoS) attacks incorporates elements that pose a potential risk to cluster-based routing. Deshmukh, Dhawale, and Dorle [60] analyzed VANET’s cluster-based routing technology in an actual geographic scenario. They simulated SUMO for different vehicle counts.
Yogarayan et al. [61] explored VANET routing protocols using cluster-based routing protocols. Srivastava, Prakash, and Tripathi [62] addressed VANET location-based routing protocol problems. They also addressed cluster-based routing protocol concerns and challenges.
Khatri et al. discussed how machine learning may address VANET safety, communication, and traffic difficulties. It contains a VANET-based case study [44] and explored future approaches and challenges. Alaya et al. proposed an Efficient Key Management Scheme (KMSUNET) to optimize global criteria while increasing class lifespan and information transmission and decreasing inter-class overload [45]. Mirsadeghi et al. presented a trust-based authentication mechanism for clustered vehicular AdHoc networks to build reliable and stable clusters. Cluster Heads are chosen according to the predicted trust degree of each vehicle, and messages are encrypted using a public/private key pair provided by a Trusted Authority [46].
Alkhalidy et al. suggested that Intelligent Transportation Systems, such as vehicular AdHoc networks, are essential for road safety and management, a novel method for identifying malicious nodes using a fuzzy logic model [47]. Bijalwan et al. presented a SAACS, a self-adaptable Angular-based k-medoid Clustering Scheme (SAACS) that reduces network latency by making educated assumptions about route lengths and signal ranges. It is 50% more effective than RTVC plus ECHS and reduces the ratio of lost packets to total packets by 45% [48]. Ouallane et al. analyzed current traffic congestion solutions. It analyzes the three primary subsystems of a Traffic Management System and suggests future research and themes that need more study for a realistic and successful system [49].
Rajeswari et al. analyzed the SUMO that simulates road traffic to assess the effectiveness of a one-way hash chain model to strengthen privacy and data integrity safeguards in VANET-based healthcare networks [50]. The author proposed a methodology to determine which bicycle and pedestrian paths would impact health outcomes most. Walking is the most accessible and social means of transportation, but transportation innovations have reduced the quality of life for pedestrians. This study combines a survey questionnaire and walkability assessment to assess how people feel about walking [63].
This study showed that a pleasant walking environment can positively impact the walking experience. It was found that urban areas with lively public squares and pedestrian walkways provide much visual stimulation, while underpasses lead to 64% fewer head motions and a 164% increase in time glanced down. Two multiple linear regression statistics show the elements of the surroundings that draw the gaze of pedestrians. Humans have a finite range of detection for their sensory organs, so human-scaled walking settings are more engaging [64]. Hireche et al. proposed a new framework for an intelligent data-driven transportation system in metropolitan settings that can display CV data in real-time utilizing a big data analytic engine [51]. Narayanan et al.’s proposed algorithm achieves a maximum cluster efficiency of 96.84, superior to both the Weighted Cluster Protocol and the AWCP Whale algorithmic program protocol regarding encapsulation potency and portability [52].
Our research contributes to vehicular communication by proposing secure cluster-based authentication and communication protocols for Vehicle-to-Vehicle (V2V) and Vehicle-to-Infrastructure (V2I) communications. The protocols we developed address the critical phases of V2I and V2V communications and resource sharing within a VANET. Our contribution includes the following aspects:
- We introduce a secure authentication mechanism that relies on a trusted third-party certification authority. It ensures the integrity and authenticity of vehicles and infrastructure units participating in the communication network. By leveraging this mechanism, we enhance the overall security of V2I and V2V communications.
- Our protocols establish reliable and secure communication channels for V2I and V2V interactions. They enable efficient and seamless communication between vehicles and infrastructure units, facilitating the exchange of critical data and messages.
- We propose a novel resource-sharing approach based on graph theory principles. By modeling the VANET as a graph, we optimize the allocation of resources, such as bandwidth and power, among vehicles and infrastructure units. This ensures fair and efficient resource utilization, enhancing the overall performance of the communication network.
- By addressing these essential aspects, our research advances the security, reliability, and efficiency of V2I and V2V communications in vehicular networks. The proposed protocols and resource-sharing mechanism pave the way for more robust and secure communication systems, fostering the development and deployment of intelligent transportation solutions.
3. Methodology
This research presents an enhanced lightweight authentication protocol for vehicles utilizing a third-party certification authority (CA) in vehicular AdHoc networks (VANETs). The CA assumes the responsibility of monitoring traffic within the network. The study introduces separate protocols for registration, authentication, V2V, and V2X communication while addressing resource allocation and sharing in vehicular communication. The research proposes greedy resource allocation and graph-based baseline resource allocation algorithms, which have been implemented in MATLAB. REST APIs using PHP 8 and MySQL have been developed to establish the V2V and V2I communication channels, with performance analysis conducted using the collaborative API development tool, Postman.
We need both approaches, greedy resource allocation and graph-based baseline resource allocation algorithms, because they serve different purposes and are suited for different resource allocation problems. Greedy algorithms offer simplicity and efficiency, making them useful for quick and straightforward allocation tasks where immediate gains are prioritized. On the other hand, graph-based baseline algorithms provide a more comprehensive and optimized solution by considering dependencies, constraints, and the overall system state. They are suitable for complex resource allocation problems requiring a global perspective and the ability to handle intricate resource relationships. By having both approaches, we can apply the most appropriate algorithm based on the specific requirements and constraints of the resource allocation problem.
The results demonstrate the exceptional performance of the protocols in V2V and V2X communication, particularly in terms of average End-to-End (E2E) delay, link failure, and secure communication. The protocols yield notable benefits, including enhanced throughput, maximized Packet Delivery Ratio (PDR), and reduced TCP connection timeouts. The notions and assumptions are presented in Table 4.

Table 4.
Notation Guide.
3.1. Explanation of Notations
- The range of in varies from 1 to , i.e., , but in other notations, it varies from to i.e.,
- MD5-based secure hash function 128-bit hash value ranges from
- such that presents a set of random numbers generated using the LCG algorithm
- Linear congruential generators can be defined through recurrence relation as:
- will generate a six-digit code.
- is generated using the Fisher–Yates shuffle algorithm. Here is the pseudo representation of this algorithm:
- ○
- function fisherYatesShuffle(array)
- ○
- = length(array)
- ○
- for i from down to 1 do
- ○
- = random integer between 0 and (inclusive)
- ○
- swap and
- ○
- return array
- Explanation of Fisher–Yates Shuffle Algorithm:
- The fisherYatesShuffle function takes an array as input and returns the shuffled array.
- It initializes the variable n with the length of the array.
- The algorithm starts a loop from down to 1. This loop iterates over the elements of the array in reverse order.
- A random integer is generated inside the loop between 0 and (inclusive), where is the current iteration index.
- The elements at indices and are swapped using a temporary variable.
- After the loop completes, the shuffled array is returned.
The Fisher–Yates shuffle algorithm guarantees a uniformly random shuffle and has a time complexity of , where n is the number of elements in the array.
- and are two extractor functions that extract latitude and longitude from the input location.
- contains message templates. These messages might contain the following commands:
- ○
- Please give me the way. I am on your back!
- ○
- Speed up!
- ○
- Danger ahead!
- ○
- Traffic is jammed on the road. Please adopt an alternative way.
- ○
- I run short of fuel. Please help!
- ○
- I need a mechanic.
- ○
- The tire is punctured.
- ○
- There is an accident on the road near my location.
- ○
- There is a crowd protesting on the way.
- ○
- Please give way to the ambulance!
- ○
- Stop on the way. There is a check post.
- ○
- The weather condition is bad.
- contains three values, including 0, 1, and 2. (0) means the priority of this message is nothing. It might be an informative message. 1 means normal priority, while 2 means a very high priority.
3.2. Motivations and Deployment Considerations
The deployment of a third-party certification authority (CA) for monitoring urban traffic and implementing a separate authentication communication scheme in vehicular AdHoc networks (VANETs) is motivated by several key factors. This section provides an overview of the motivations and considerations behind using the third-party CA, the impact of capacity and speed on network signaling overhead, and the importance of cluster management.
3.2.1. Third-Party CA for Traffic Monitoring
Deploying a third-party CA in VANETs is crucial to monitoring urban traffic. The CA enhances vehicular communication’s overall security and reliability by employing a dedicated authority to oversee and regulate the network. This monitoring capability identifies and mitigates potential threats or malicious activities, ensuring a safer and more efficient transportation system.
3.2.2. Separate Authentication Communication Scheme
Adopting a separate authentication communication scheme in VANETs offers significant advantages over traditional approaches. The system becomes more resilient to attacks and unauthorized access by decoupling the authentication process from other communication protocols. This separation of authentication ensures the integrity and authenticity of participating vehicles and infrastructure units, fostering a secure and trusted communication environment.
3.2.3. Influence of Capacity and Speed on Network Signaling Overhead
The capacity and speed of vehicles in VANETs directly impact network signaling overhead. High-speed vehicles generate increased signaling traffic due to frequent handoffs between network nodes. This overhead can degrade the overall network performance and hinder real-time communication. Understanding the relationship between capacity, speed, and signaling overhead is essential for optimizing network resources and minimizing delays in high-speed environments.
3.2.4. Cluster Management
Effective cluster management is crucial for efficient resource allocation and communication in VANETs. Clustering enables forming groups or clusters of nearby vehicles, facilitating localized communication and reducing the overall network load. Proper management of clusters ensures optimized resource allocation, improves scalability, and enhances the overall performance of the vehicular communication system.
In summary, the motivations for deploying a third-party CA for traffic monitoring, implementing a separate authentication communication scheme, considering the influence of capacity and speed on network signaling overhead, and ensuring effective cluster management are essential considerations in the design and deployment of VANETs. These factors contribute to vehicular communications’ security, efficiency, and reliability in urban environments.
4. Proposed Protocol
In this section, we have shown the step-by-step process of our protocol, which we have employed in the authentication and communication protocols for urban traffic monitoring in VANETs based on cluster management.
4.1. Registration Phase
The API needs three parameters in the registration phase of our proposed protocol:
- E-mail;
- Password;
- Vehicle Registration Number.
The API will get the current time on the vehicle onboard unit side. The other operations include encrypting passwords using MD5, extracting numeric values from vehicle registration numbers, generating updated codes, and creating reference values for vehicles OBU. The function takes the registration number as input and returns all numeric characters from the input string in our scenario. After extracting the , this is concatenated with API from the database, which fetches that. For example, if there is no registered vehicle on the CA Server, the database will return 0, and API will increment the value by 1 in . We have applied the SQL aggregate MAX function that will return the maximum stored in the table. The combined value of and is assigned to . A lightweight block is created to prevent database record tempering in the form of a field that takes , , and as inputs, merges these values using the concatenation operator, and produces the vehicle registration reference . The API sends on a public channel. The Certification Authority Server generates Updated Vehicle Code by taking and a random number . The is shuffled using the function to form . This is then passed to function in order to produce . This can be used for authentication henceforth. After all this processing, the Certification Authority Server stores in the DB table. The CA Server also generates Session Keys for the onboard vehicle unit. The is generated by combining and . The CA Server sends to the OBU after handling all the processes mentioned above. Finally, the OBU stores in its shared preferences for session management (see Table 5).

Table 5.
Registration phase.
4.2. Authentication Phase
In the authentication phase, there are two possibilities for authentication with the Certification Authority Server. Authentication can be done using e-mail or password or the authentication code obtained in the registration phase. After selecting any login method, is computed by the OBU for updating the logs table. is passed to the server along with its corresponding parameters. The CA Server checks the authentication type. We set two threshold values, i.e., 0 for and 1 for . If == 0; then, the CA server compares database records. If the vehicle code already exists in the database, the server sends a response with a success message and starts the OBU session. The CA Server also updates the logs table for log maintenance. Otherwise, the server sends a failure message in response and does not start the OBU session on failure. It is clear from threshold values that 0 is for , and 1 is for ; that is why when the CA Server receives == 0, the server compares database records. If records match, the server sends a response with a success message, starts the OBU session, and updates the log table. Otherwise, the CA Server sends a failure message in the response and does not start the OBU session. The server sends { } as a response to the OBU. The OBU checks the response; if and then OBU sets ; otherwise (see Table 6).

Table 6.
Login and authentication phase.
4.3. V2I Communication
V2I communication is only possible when the vehicle is registered on the CA Server and has an active session. On the vehicle side, The OBU computes , , , , and . is composed of the latitude and longitude of the vehicle. The CA Server gets as parameters. and are concatenated to form . If the CA Server receives a value regarding the current location of the OBU, it extracts latitude and longitudes from . Otherwise, it returns null values in response. The parameters are then passed to the vehicle for parsing purposes (see Table 7).

Table 7.
V2I Communication phase.
4.4. V2V Communication
In V2V communication, Vehicle A selects , and . The is composed of and . Vehicle A, through APIs, sends as parameters to Vehicle B. After the acknowledgment, Vehicle B can reply to Vehicle A, but doing so is optional (see Table 8).

Table 8.
V2V Communication phase.
4.5. Vehicle Clustering and Monitoring
One certification authority (CA) in a VANET authenticates all the vehicles within a 400 m cluster. The cluster may include 100 m range sub-clusters as per the topology of the VANET. The CA is a trusted third party that manages registration, authentication, and vehicle communication record registers. The vehicles moving on the highway are divided into several clusters. Each cluster has one Cluster Head (CH) and one or more cluster members. The cluster has two bands, each with one or more lanes. All the vehicles inside the cluster are inter-connected directly and can communicate with each other. Outside the cluster, communication vehicles can communicate using corresponding Cluster Heads. The cluster structure in our system primarily consists of a designated head, who assumes a leadership role, and the remaining vehicles within the cluster, which function as members. Figure 2 shows the lattice of our proposed VANET for V2V and V2I communications. The range of clusters in this scenario is 400 m. The central cluster is subdivided into a 100 m range for each. The CA performs the registration, authentication, monitoring, and allowing of vehicles’ communications. The base station provides the network link to CH and CA. The CA server is responsible for issuing and managing digital certificates, ensuring the authenticity and integrity of communication in the system. Conversely, the base station provides Internet signals, enabling connectivity and network access for the devices within its coverage area.
Due to the dynamic nature of moving vehicles in a vehicular ad hoc network (VANET), various sources of distortion can arise, potentially impacting communication effectiveness between vehicles. To mitigate these challenges, a specific VANET may employ the concept of a 400 m cluster. This cluster refers to a grouping of vehicles within a 400 m radius to enhance communication reliability and minimize distortion effects.
By organizing vehicles into clusters, proximity-based communication is prioritized, allowing for more efficient transmission of messages and data. Within a cluster, vehicles are closer to each other, reducing the impact of signal attenuation, interference, and other distortions that can occur in VANET environments. The 400 m range is chosen based on the characteristics of the wireless communication technology, the expected vehicle density, and the desired trade-off between cluster size and communication performance.
Setting a specific cluster size helps improve the quality and reliability of communication within the VANET. By limiting the cluster size to 400 m, vehicles in the same cluster are more likely to have stronger signal strengths, lower path loss, and reduced interference, thereby improving the overall communication performance and ensuring the timely and accurate exchange of information [65].
Selecting the Cluster Head is described in algorithm while the topology of traffic flow in different types of clusters in VANET is described in Figure 3. In the monitoring phase, the CA collects the behavioral information of all vehicles in a cluster. This all-encompassing review comprehensively examines the diverse array of methods explored in current literature as potential remedies for mitigating the widespread issue of traffic congestion. The authentication phase of our proposed protocol addresses this issue.
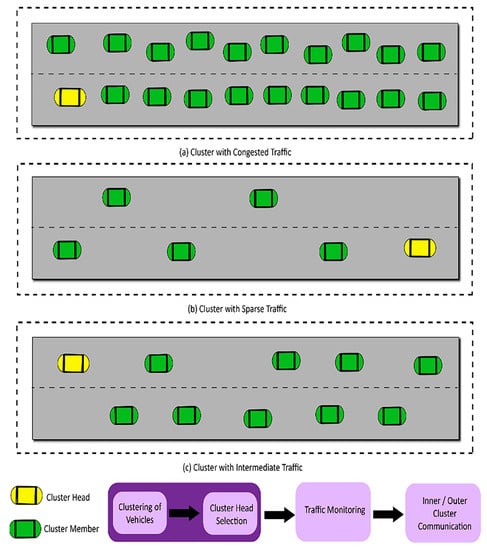
Figure 3.
V2V and V2I Communication in a cluster.
4.6. Cluster Head Selection Algorithm
- Each vehicle inside a cluster announces itself as a “Cluster Head“ and displays the broadcast signal:
- Every vehicle displays the list of closest vehicles () after getting from
- is estimated by
- The weighted sum is calculated by
- The vehicle calculates the above equation’s arguments, and the range of weighted constants varies from 0 to 1. Since the weighted sum is derived from these arguments, the Cluster Head based on this sum will be the most efficient and trustworthy.
- In the end, the with the lowest is selected as the Cluster Head.
- Pseudo code for the Cluster Head Selection Algorithm:
- function select cluster head (clusterVehicles)
- lowest weight = infinity
- selected cluster head = null
- for each vehicle in clusterVehicles do
- = get Closest Vehicles List ()
- weighted sum = calculate Weighted Sum (, )
- if weighted sum < lowest weight then
- lowest weight = weighted sum
- selected cluster head =
- return selected cluster head
- Explanation:
- The select cluster head function takes the list of vehicles within the cluster as input and returns the selected cluster head.
- It initializes the lowest Weight variable with a high value (infinity) and sets the selected Cluster Head to null.
- For each vehicle in the clusterVehicles list, the algorithm retrieves the list of closest vehicles using the get Closest Vehicles List function.
- The weighted sum is calculated using the arguments (the current vehicle) and (the closest vehicles list).
- If the calculated weighted sum is lower than the current lowest Weight, the lowest Weight is updated, and the corresponding vehicle is selected as the potential cluster head.
- After processing all vehicles, the algorithm returns the selected cluster head with the lowest weighted sum.
The specific implementations of the get Closest Vehicles List and calculate Weighted Sum functions should be defined separately based on your system’s requirements and available information.
The Cluster Head Selection Algorithm utilizes several notations to describe its functionality, further elaborated in Table 9.

Table 9.
Explanation of the notations.
5. Simulation Setup and Experiments
For experimental purposes, we formed three clusters featuring (a) congested traffic, (b) sparse traffic, and (c) intermediate traffic, as shown in Figure 3. Each cluster band has two lanes, and each lane has at least one or more vehicles obeying the instructions of the CH vehicle, which is a unique vehicle in a cluster. We developed restful APIs in PHP to implement our proposed protocol. We employed the most recent PHP (PHP 8) version and MySQL to maintain CA, vehicle communication, and monitoring registers. We send five different HTTP requests using the HTTP GET method. We used the Postman tool for API performance evaluation and noted the results obtained in all scenarios.
Moreover, we worked on the resource allocation of V2V and V2I communication by proposing two algorithms and their implementation in MATLAB. To measure the security and message delivery, we compared our implementation results with the research work of Sugumar et al. [58], which simulated their proposed protocol using an open-source Network Simulator Version 2, NS2. This tool is frequently used by researchers in computer communications and networking-related research, especially wireless networks. In this paper, we compared their research work with ours. First, we compared our protocol’s resultant authentication delay, detection accuracy, keying overhead, and packet delivery ratio with the authors’ results [58]. Later, we compared the transmission range in the context of packet delivery, authentication delay, keying overhead, and detection accuracy. The details of the results obtained from our experiments are described in the following sub-sections.
5.1. Varying the Attackers
To inspect our proposed protocol’s authentication delay, we set the transmission range to 400 m. This choice (400 m) is because moving vehicles face many distortion-related issues due to network instability. We counted the average authentication delay of clusters having congested, average, and sparse traffic, respectively. Each cluster’s number of attackers or malicious vehicles varied from one to five. Figure 4a depicts the average authentication delay in milliseconds for all DDoS attacks and mitigation methods, including HTTP Flood and Ping of Death. The results indicated a better performance than the experiment by Sugumar et al. [58]. The authors discussed a trust-based Authentication Technique (TBAT) and advanced Secure mechanism based on Clustering and Key Distribution (SCKD) in their research, but they did not test their protocol on different types of clusters. We compared authentication and Communication Protocol (ACP) results with the SCKD and TBAT experimental results. For comparison, we did not show the different authentication delays for each congested, average, or sparse cluster. We calculated each cluster’s average authentication delay and compared it with the number of attackers. Our protocol also provided efficient results regarding Detection Accuracy and Keying Overhead. Figure 4b demonstrates Detection Accuracy, and it can be observed that when the number of attackers increased, the detection accuracy decreased in all three protocols. Figure 4c shows the Keying Overhead of our protocol concerning the scheme of [58]. Since the experiment of Sugumar et al. [58] includes a complex keying generation process, their results do not provide better results than ours. In Figure 4d, we compared the packet delivery ratio in the context of varying attackers with the results of Sugumar et al. [58]. Our results indicate a better performance compared to that obtained by the authors [58].
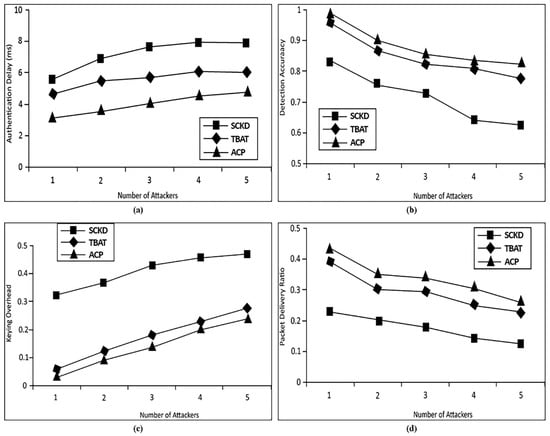
Figure 4.
Presents the Varying the Attackers (a) Authentication Delay vs. Number of Attackers, (b) Detection Accuracy vs. Number of Attackers, (c) Keying Overhead vs. Number of Attackers, (d) Packet Delivery Ratio vs. Number of Attackers.
5.2. Transmission Range
We noted the sub-cluster effect on the transmission range in our next experiment. We formed a 400 m cluster with varying speeds. Through this method, we noted the average packet delivery ratio of three clusters (Congested, Sparse, and Intermediate) concerning the corresponding cluster range. For the Postman simulation, we supposed that the location of the base station is fixed at a certain point. The routing delay will occur as the vehicle moves in a corresponding cluster. We also supposed that the delay factor in routing would increase when the range is increased. Figure 5a compares Cluster Range and Packet Delivery. Our proposed Authentication and Communication Protocol (ACP) results perform much better than those obtained by Sugumar et al. [58], as shown in Figure 5a. In Figure 5b, we compare Authentication Delay, while Figure 5c shows Keying Overhead in the context of varying cluster ranges. In Figure 5d, we compare the Detection Accuracy with the results obtained by [58]. It is observable that our protocol has also provided much better performance in varying cluster ranges.
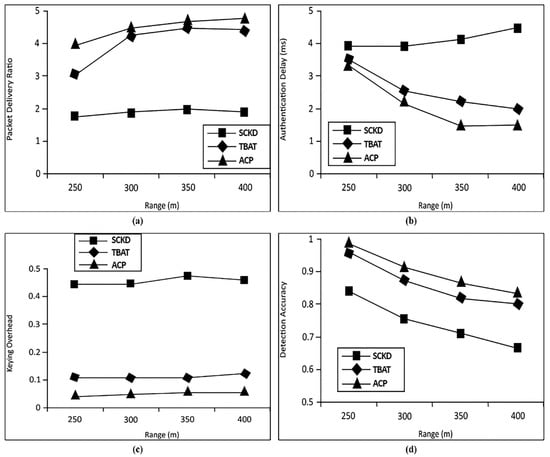
Figure 5.
(a) Delivery Ratio and Cluster Range Comparison, (b) Authentication Delay and Cluster Range Comparison, (c) Keying Overhead and Cluster Range Comparison, (d) Detection Accuracy and Cluster Range Comparison.
5.3. Baseline Graph-Based Resource Allocation
The optimization of resources in high-mobile vehicles is a significant issue. We introduced a baseline low-complexity algorithm. To achieve this milestone, we first assigned an arbitrary V2V link to all clusters specified in Figure 2 and then simulated our baseline graph-based resource allocation approach using MATLAB. Algorithm 1 presents our proposed resource optimization and allocation method.
| Algorithm 1: Baseline Graph-Based Resource Allocation Algorithm |
| 1. Arbitrarily allocate one V2V link to every cluster from C clusters (C1, …… Cn). 2. for m = 1 to M do 3. for n = 1 to N do 4. for f = 1 to F do 5. Compute the V2I optimal transmit power using the algorithms provided by [66]. 6. Compute the V2V optimal transmit power using the algorithms provided by [66]. 7. Compute the V2I and V2V power gain capacity from the base station resource blocks with the optimized power control parameters. 8. end for 9. end for 10. end for 11. Construct a tripartite graph where M represents V2I links and N represents V2V links. 12. Return the power allocation using resource blocks. |
The baseline graph-based resource allocation algorithm aims to optimize resource allocation in high-mobile vehicle environments, specifically for vehicular-to-vehicular (V2V) communication. The algorithm utilizes a graph-based approach to effectively distribute resources among clusters, ensuring efficient utilization and improved network performance. The algorithm follows the following steps:
- Initialization: Assign an arbitrary V2V link to each cluster based on predefined criteria or randomly.
- Graph Construction: Create a graph representation where each cluster is represented as a node, and the V2V links between clusters are represented as edges. This graph captures the connectivity and relationships between clusters.
- Resource Evaluation: Evaluate the resources available within each cluster and the requirements of the V2V communication links. This assessment may include available bandwidth, signal strength, channel conditions, and quality-of-service (QoS) metrics.
- Resource Allocation: Utilize graph-based algorithms to allocate resources based on connectivity and performance requirements. Various graph algorithms, such as minimum spanning tree, shortest path, or maximum flow algorithms, can be employed to optimize resource allocation.
- Optimization: Continuously evaluate and optimize the resource allocation based on dynamic changes in the network, such as variations in vehicle density, traffic conditions, or communication demands. This ensures adaptability and efficient resource utilization in real-time scenarios.
The baseline graph-based resource allocation algorithm serves as a starting point and provides a low-complexity solution for resource optimization in high-mobile vehicle environments. It aims to balance resource utilization, network performance, and scalability. By leveraging connectivity information and graph-based techniques, the algorithm optimizes the allocation of resources, enhancing the overall performance and efficiency of V2V communication in vehicular networks.
Figure 6 shows the Cumulative distribution function (CDF) of the quick Signal-to-Interference-Plus-Noise Ratio (SINR) of V2V and V2I communications using our proposed graph-based resource allocation algorithm.
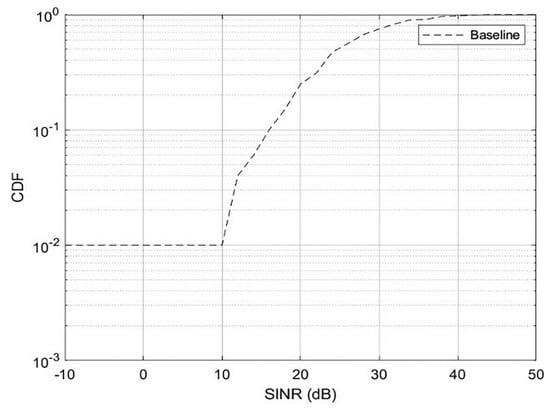
Figure 6.
Cumulative Distribution Function (CDF) of Instantaneous Signal−to−Interference-Plus-Noise Ratio (SINR) of V2V and V2I Communications.
In Figure 7, we have merely discussed the Sum of V2I capacity with varying vehicle speeds by adopting the algorithm provided by [66] in our algorithm. V2V transmit power in dBm is taken as 33. Large-scale fading parameters are V2V = 3 and V2I = 8, which are shadowing standard deviations. Cell parameter setup is done so that the carrier frequency is 3.5 GHz, 200 cell radius in meters, base station height 25 m, 35 m BS-highway distance in meters, and base station noise is 5dB. The vehicle antenna height is 1.5 m, with the vehicle antenna gain of 3 dBi and the vehicle noise being 9 dB. The number of lanes is reduced from six to four, and the lane width is reduced from 4 to 3 m. The velocity range is from 20 to 160. According to TR 36.885, the average inter-vehicle distance is 2.5. *v/3.6. The maximum number of links for V2I is reduced from 10 to 5 [32].
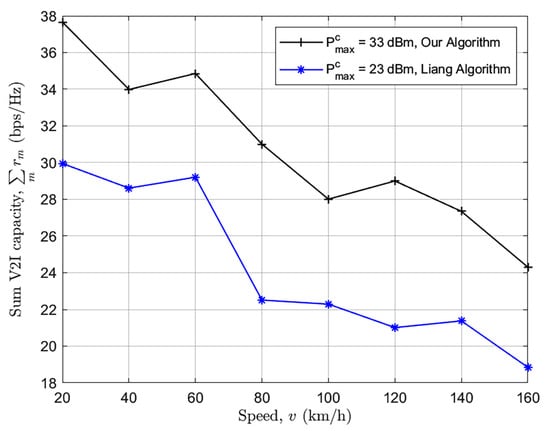
Figure 7.
Sum of V2I Capacity with Varying Vehicle Speeds.
5.4. Greedy Resource Allocation
We proposed an additional algorithm based on the Greedy Approach grounded on the baseline graph-based resource allocation algorithm. Algorithm 2 shows our proposed greedy approach.
| Algorithm 2: Greedy Resource Allocation Algorithm |
| 1. Obtain V2V and V2I clustering results from the baseline graph-based resource allocation algorithm. 2. Repeat the process. for k = 1 to K do Initialize all zero vectors of length N. for n = 1 to N do If the kth V2V is not only in its current cluster C, then set Ck = n end if end for end for Return the power allocation using resource blocks. |
The greedy resource allocation algorithm is a method used to allocate resources in vehicular networks, explicitly focusing on vehicular-to-vehicular (V2V) communication. The algorithm uses a greedy approach to allocate resources based on immediate local optimization criteria. The algorithm operates as follows:
- Initialization: Begin with an initial set of available resources and an open allocation plan.
- Vehicle Selection: Select a vehicle from the pool of vehicles requiring resource allocation.
- Resource Evaluation: Evaluate the available resources and the requirements of the selected vehicle. This evaluation may include available bandwidth, signal quality, channel conditions, proximity to other vehicles, and communication demands.
- Resource Allocation: Allocate the resources to the selected vehicle based on the evaluation. The allocation decision is made greedily, considering the local optimization criteria. For example, the algorithm may prioritize allocating resources to vehicles with higher communication demands or vehicles experiencing poor signal quality.
- Update Resource Pool: Update the pool of available resources by subtracting the allocated resources from the total available resources.
- Repeat Steps 2–5: Repeat the vehicle selection process, resource evaluation, allocation, and resource pool update for the remaining vehicles until all vehicles have been allocated resources.
The greedy resource allocation algorithm aims to maximize the immediate benefit by making locally optimal decisions at each step. However, it may not always result in the globally optimal allocation of resources. Nevertheless, the algorithm provides a simple and efficient solution for resource allocation in dynamic vehicular environments where real-time decision-making is crucial. It is important to note that the greedy resource allocation algorithm can be customized and adapted based on the specific requirements and constraints of the vehicular network, such as quality-of-service (QoS) guarantees, fairness considerations, or traffic prioritization. This algorithm can optimize resource utilization, enhancing V2V communication performance and network efficiency. Figure 8a,b shows the simulation results of the baseline greedy resource allocation algorithm:
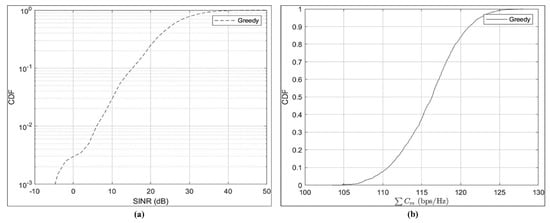
Figure 8.
(a) Cumulative Distribution Function (CDF) of Instantaneous Signal-to-Interference-Plus-Noise Ratio (SINR), (b) Cumulative Distribution Function (CDF) Concerning the Sum of V2I Capacity.
5.5. V2I and V2V Communications
In our study, we utilized Postman to generate the results, focusing on critical factors influencing API performance. These factors include API status, API response size, socket initialization, DNS lookup, TCP handshake, transfer rate, and download rate. Less impactful factors were omitted, such as preparation time and response headers. We tested our developed API using five HTTP requests to ensure a comprehensive evaluation. Table 6 presents the API response time for each request, where a status code of 200 indicates a successful response. Although the response size remained consistent at 289 bytes, the response times for other parameters varied across instances. Our APIs consistently provided successful responses, with the server delivering JSON responses to the vehicle (client side) for each request. This novel concept of vehicular communication in 5G VANET utilizing RESTful APIs holds the potential to enhance VANET’s overall performance significantly. Our algorithms also incorporate security and privacy features, and the introduction of RESTful APIs adds a layer of security to the client–server model deployed for vehicular communication. Harnessing the substantial bandwidth and rapid communication rates offered by 5G technology, our proposed algorithm demonstrates resilient packet delivery and expedited API responses. The streamlined code and compact size of the APIs contribute to their exceptional performance, as the client-side data remain in a stateless form. Furthermore, RESTful APIs facilitate cache storage, resulting in improved response time. We ensured accurate measurement of all attribute values by clearing the Postman cache, which demonstrated the notably faster response rate achieved after implementing cache storage, as shown in Table 10.

Table 10.
API Response for 5 Random HTTP Requests.
6. Conclusions
This research covered a broad spectrum of vehicular communications on VANET. We proposed authentication and communication resource-sharing algorithms for vehicular communications. We discussed previously conducted works relevant to our study in detail with the help of a literature comparison table. The proposed cluster-based improved authentication and communication protocol for an Intelligent Transportation System in VANETs addresses the significant issues of traffic monitoring in overcrowded city zones. Using cluster-based routing protocols for V2V and V2I communication enhances the reliability, scalability, and stability of fast-moving VANETs. The third-party certification authority for vehicle authentication provides a secure and private mechanism for authentication. The protocols minimize the E2E delay and route request, reduce link failure, and improve the throughput, TCP Socket Initialization time, TCP handshake response, and DNS lookup. The innovative P2P wireless communication in a 400 m radius cluster minimizes the resources used, and the RESTful APIs and resource-sharing algorithms enable vehicular communication implementation. The experimental evaluation demonstrates the effectiveness of the proposed protocols in optimizing resource sharing in vehicular communication. The proposed protocol can contribute to developing more efficient and reliable Intelligent Transportation Systems in VANETs, improving traffic management, and reducing congestion in overcrowded city zones. We demonstrated our protocol and algorithms by using their corresponding behaviors and functionalities. We briefly discussed the security goals of our proposed protocol. For simulation and performance evaluation, we used MATLAB and REST APIs. We compared our results with those obtained through relevant past studies and evaluated our improved cluster-based authentication and communication protocol performance. The simulation results indicate the superior performance of our protocols and algorithms compared to other approaches.
Since the 5G network diminishes the Internet speed barrier and other issues related to VANETs communication, our proposed improved cluster-based authentication and communication protocol will provide accelerated performance in V2I and V2V communications. We are also interested in developing real-world apps in the future by adopting this secure and reliable protocol. Integrating blockchain technology is one future trend in VANETs (Vehicular AdHoc Networks) urban traffic monitoring based on cluster management. Blockchain can provide a secure and decentralized way of managing the clusters and nodes in VANETs, enhancing the security and privacy of the communication and authentication protocols. Another trend is using artificial intelligence and machine learning algorithms to improve traffic monitoring and management accuracy and efficiency. These techniques can help identify patterns, predict traffic congestion, and optimize traffic flow. IoT (Internet of Things) sensors and devices, such as cameras and traffic sensors, can be integrated into VANETs for collecting real-time data and improving the accuracy of traffic monitoring and management accuracy. Finally, developing new communication protocols and standards for VANETs can also be expected. The focus will be on enhancing the communication protocols’ reliability, security, and privacy and ensuring interoperability and compatibility with other networks and systems.
7. Future Recommendations
Integration of artificial intelligence (AI) and machine learning (ML): Incorporating AI and ML techniques can further enhance the performance and efficiency of the proposed authentication and communication protocol. By leveraging AI and ML algorithms, the protocol can adapt dynamically to changing traffic conditions, optimize resource allocation, and improve decision-making processes for routing and communication.
- As security and privacy concerns remain critical in VANETs, future work should focus on developing advanced encryption and cryptographic techniques to safeguard sensitive information and prevent unauthorized access. Additionally, privacy-preserving mechanisms, such as secure data aggregation and anonymization, should be explored to protect the privacy of vehicle and driver identities.
- Conducting real-world deployments and field testing of the proposed protocol will provide valuable insights into its practical feasibility and effectiveness. Evaluating the protocol’s performance under various traffic scenarios, road conditions, and network densities will help identify potential limitations and areas for further improvement.
- In order to achieve uninterrupted communication and practical cooperation between diverse vehicles and infrastructure systems, it is imperative to establish interoperability standards. These standards will promote compatibility and collaboration among various Vehicular AdHoc Networks (VANETs), facilitating enhanced traffic management and safer interactions between vehicles and infrastructure components.
- Energy Efficiency Considerations: Energy efficiency is crucial to VANETs, as vehicles operate on limited power resources. Future research should explore energy-aware strategies and mechanisms to optimize power consumption, prolong the network’s lifetime, and reduce the carbon footprint associated with vehicular communication.
- As urban areas continue to expand, the scalability and robustness of the proposed protocol need to be thoroughly investigated. Future work should address the challenges of large-scale VANET deployments, including managing a vast number of vehicles, efficient cluster formation, and effective communication in highly dynamic environments.
Author Contributions
Conceptualization, R.M.A.L., M.J., J.H. and M.F.; methodology, R.M.A.L.; software, R.M.A.L.; validation R.M.A.L. and M.J.; formal analysis, R.M.A.L.; investigation, M.J.; resources, J.H.; data curation, M.J.; writing—original draft preparation, R.M.A.L. and M.J.; writing—review and editing, J.H.; visualization, J.H.; supervision, J.H. and M.F.; project administration, J.H.; funding acquisition, J.H. All authors have read and agreed to the published version of the manuscript.
Funding
This study was founded by National Natural Science Foundation of China, grant number 42171214.
Data Availability Statement
The data supporting the findings of this study are available upon reasonable request. https://github.com/Rana64/Urban-Traffic-Monitoring-in-VANETs-Based-on-Cluster-Management accessed on 2 June 2023.
Conflicts of Interest
The authors declare that they have no conflict of interest.
References
- Jithendra, H.; Rekha, D. Secured Trusted Authentication with Trust-Based Congestion Scheme for V2V Communication; Chapman and Hall/CRC: Boca Raton, FL, USA, 2022; pp. 157–168. [Google Scholar]
- Panigrahy, S.K.; Emany, H. A survey and tutorial on network optimization for intelligent transport system using the internet of vehicles. Sensors 2023, 23, 555. [Google Scholar] [CrossRef] [PubMed]
- Cui, J.; Wei, L.; Zhong, H.; Zhang, J.; Xu, Y.; Liu, L. Edge computing in VANETs-an efficient and privacy-preserving cooperative downloading scheme. IEEE J. Sel. Areas Commun. 2020, 38, 1191–1204. [Google Scholar] [CrossRef]
- Hamzah, M.; Islam, M.M.; Hassan, S.; Akhtar, M.N.; Ferdous, M.J.; Jasser, M.B.; Mohamed, A.W. Distributed Control of Cyber Physical System on Various Domains: A Critical Review. Systems 2023, 11, 208. [Google Scholar] [CrossRef]
- Goyal, A.K.; Agarwal, G.; Tripathi, A.K.; Sharma, G. Systematic Study of VANET: Applications, Challenges, Threats, Attacks, Schemes and Issues in Research. In Green Computing in Network Security; CRC Press: Boca Raton, FL, USA, 2022; pp. 33–52. [Google Scholar]
- Singh, M.; Kumar, C.; Nath, P. P2P Applications in 4G/5G Networks Using D2D Communication Based on Social Attributes of Users. In Proceedings of the Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27–28 July 2020; pp. 730–738. [Google Scholar]
- Hamdi, M.M.; Audah, L.; Rashid, S.A.; Mohammed, A.H.; Alani, S.; Mustafa, A.S. A review of applications, characteristics and challenges in vehicular ad hoc networks (VANETs). In Proceedings of the International Congress on Human-Computer Interaction, Optimization and Robotic Applications (HORA), Ankara, Turkey, 26–28 June 2020; pp. 1–7. [Google Scholar]
- Hsieh, F.-S. Improving Acceptability of Cost Savings Allocation in Ridesharing Systems Based on Analysis of Proportional Methods. Systems 2023, 11, 187. [Google Scholar] [CrossRef]
- Shen, X.; Lu, Y.; Zhang, Y.; Liu, X.; Zhang, L. An Innovative Data Integrity Verification Scheme in the Internet of Things assisted information exchange in transportation systems. Clust. Comput. 2022, 25, 1791–1803. [Google Scholar] [CrossRef]
- Sharma, S.K.; Rao, R.S.; Singh, P.; Khan, S.A. Evaluation of VANETs routing protocols for data-based smart health monitoring in intelligent transportation systems. Int. J. Math. Eng. Manag. Sci. 2022, 7, 211. [Google Scholar] [CrossRef]
- Gao, Z.; Xu, X.; Hu, Y.; Wang, H.; Zhou, C.; Zhang, H. Based on Improved NSGA-II Algorithm for Solving Time-Dependent Green Vehicle Routing Problem of Urban Waste Removal with the Consideration of Traffic Congestion: A Case Study in China. Systems 2023, 11, 173. [Google Scholar] [CrossRef]
- Lim, K.; Tuladhar, K.M.; Kim, H. Detecting location spoofing using ADAS sensors in VANETs. In Proceedings of the 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–4. [Google Scholar]
- Ku, I.; Lu, Y.; Gerla, M.; Gomes, R.L.; Ongaro, F.; Cerqueira, E. Towards software-defined VANET: Architecture and services. In Proceedings of the 13th Annual Mediterranean ad Hoc Networking Workshop (MED-HOC-NET), Piran, Slovenia, 2–4 June 2014; pp. 103–110. [Google Scholar]
- Open Connectivity Foundation. Unlocking the Massive Opportunity in the Internet of Things. Available online: https://openconnectivity.org/technology/iotivity/ (accessed on 25 January 2023).
- Yang, L.; Li, H. Vehicle-to-vehicle communication based on a peer-to-peer network with graph theory and consensus algorithm. IET Intell. Transp. Syst. 2018, 13, 280–285. [Google Scholar] [CrossRef]
- Appiahene, P.; Serwah, S.; Mensah, C.; Kesse-Yaw, B. Application of Wireless Ad-Hoc Networks Model to provide Education to rural Communities in Ghana. In Proceedings of the International Conference on Applied Science and Technology Conference Proceedings, Bali, Indonesia, 24–25 October 2019; pp. 114–121. [Google Scholar]
- Bossauer, P.; Neifer, T.; Stevens, G.; Pakusch, C. Trust versus Privacy: Using Connected Car Data in Peer-to-Peer Carsharing. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; pp. 1–13. [Google Scholar]
- Shah, S.A.A.; Ahmed, E.; Imran, M.; Zeadally, S. 5G for vehicular communications. IEEE Commun. Mag. 2018, 56, 111–117. [Google Scholar] [CrossRef]
- Meneguette, R.I.; Boukerche, A. Peer-to-peer protocol for allocated resources in vehicular cloud based on V2V communication. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), San Francisco, CA, USA, 19–22 March 2017; pp. 1–6. [Google Scholar]
- Singh, P.K.; Nandi, S.K.; Nandi, S. A tutorial survey on vehicular communication state of the art, and future research directions. Veh. Commun. 2019, 18, 100164. [Google Scholar] [CrossRef]
- Hussein, A.; Elhajj, I.H.; Chehab, A.; Kayssi, A. SDN VANETs in 5G: An architecture for resilient security services. In Proceedings of the Fourth International Conference on Software Defined Systems (SDS), Valencia, Spain, 8–11 May 2017; pp. 67–74. [Google Scholar]
- Balamurugan, M.; Anand, M.S.; Kumar, D.S.; Devi, A.S. Anonymous Location-Support and Self-Reliance Routing Protocol For Manet. Indian J. Public Health Res. Dev. 2018, 9, 323–326. [Google Scholar] [CrossRef]
- Edge, S.W.; Cheng, H.; Zisimopoulos, H. Systems and Methods for 5G Location Support Using Service Based Interfaces. U.S. Patent 11,128,985, 21 September 2022. [Google Scholar]
- Salem, F.M.; Ali, A.S. SOS: Self-organized secure framework for VANET. Int. J. Commun. Syst. 2020, 33, e4317. [Google Scholar] [CrossRef]
- Takashi, T.; Takumi, M.; Taku, Y.; Olivier, F. Performance Evaluation of Multi-Hop Communication on Inter-vehicular P2P Network. IEICE Tech. Rep. 2020, 119, 135–140. [Google Scholar]
- Zhang, R.; Lu, Y.; Liu, B. Pricing Decisions and Game Analysis on Advanced Delivery and Cross-Channel Return in a Dual-Channel Supply Chain System. Systems 2023, 11, 155. [Google Scholar] [CrossRef]
- Mondal, A.; Mitra, S. Security Issues in Vehicular Ad Hoc Networks for Evolution Towards Internet of Vehicles; Springer: Berlin/Heidelberg, Germany, 2020; pp. 253–307. [Google Scholar]
- Zhong, S.; Zhong, H.; Huang, X.; Yang, P.; Shi, J.; Xie, L.; Wang, K. Connecting Things to Things in Physical-World: Security and Privacy Issues in Vehicular Ad-Hoc Networks; Springer: Berlin/Heidelberg, Germany, 2019; pp. 101–134. [Google Scholar]
- Stepień, K.; Poniszewska-Marańda, A. Towards the security measures of the vehicular ad-hoc networks. In Proceedings of the International Conference on Internet of Vehicles, Paris, France, 20–22 November 2018; pp. 233–248. [Google Scholar]
- Ayaz, S.B.; Tian, H.; Gao, S.; Fisher, D.L. Proactive route choice with real-time information: Learning and effects of network complexity and cognitive load. Transp. Res. Part C Emerg. Technol. 2023, 149, 104035. [Google Scholar] [CrossRef]
- Zhang, K.; Leng, S.; Peng, X.; Pan, L.; Maharjan, S.; Zhang, Y. Artificial intelligence inspired transmission scheduling in cognitive vehicular communications and networks. IEEE Internet Things J. 2018, 6, 1987–1997. [Google Scholar] [CrossRef]
- Liang, L.; Li, G.Y.; Xu, W. Resource allocation for D2D-enabled vehicular communications. IEEE Trans. Commun. 2017, 65, 3186–3197. [Google Scholar] [CrossRef]
- Zhang, K.; Mao, Y.; Leng, S.; He, Y.; Zhang, Y. Mobile-edge computing for vehicular networks: A promising network paradigm with predictive off-loading. IEEE Veh. Technol. Mag. 2017, 12, 36–44. [Google Scholar] [CrossRef]
- Burg, A.; Chattopadhyay, A.; Lam, K.-Y. Wireless communication and security issues for cyber–physical systems and the Internet-of-Things. Proc. IEEE 2017, 106, 38–60. [Google Scholar] [CrossRef]
- Al-Kinani, A.; Wang, C.-X.; Zhou, L.; Zhang, W. Optical wireless communication channel measurements and models. IEEE Commun. Surv. Tutor. 2018, 20, 1939–1962. [Google Scholar] [CrossRef]
- Rahman, M.S.; Abdel-Aty, M. Longitudinal safety evaluation of connected vehicles’ platooning on expressways. Accid. Anal. Prev. 2018, 117, 381–391. [Google Scholar] [CrossRef]
- Masini, B.M.; Bazzi, A.; Zanella, A. A survey on the roadmap to mandate on board connectivity and enable V2V-based vehicular sensor networks. Sensors 2018, 18, 2207. [Google Scholar] [CrossRef] [PubMed]
- Liang, L.; Peng, H.; Li, G.Y.; Shen, X. Vehicular communications: A physical layer perspective. IEEE Trans. Veh. Technol. 2017, 66, 10647–10659. [Google Scholar] [CrossRef]
- Yan, G.; Rawat, D.B. Vehicle-to-vehicle connectivity analysis for vehicular ad-hoc networks. Ad Hoc Networks 2017, 58, 25–35. [Google Scholar] [CrossRef]
- Liu, G.; Qi, N.; Chen, J.; Dong, C.; Huang, Z. Enhancing clustering stability in VANET: A spectral clustering based approach. China Commun. 2020, 17, 140–151. [Google Scholar] [CrossRef]
- Abdelatif, S.; Derdour, M.; Ghoualmi-Zine, N.; Marzak, B. VANET: A novel service for predicting and disseminating vehicle traffic information. Int. J. Commun. Syst. 2020, 33, e4288. [Google Scholar] [CrossRef]
- Al-Shareeda, M.A.; Anbar, M.; Manickam, S.; Yassin, A.A. Vppcs: Vanet-based privacy-preserving communication scheme. IEEE Access 2020, 8, 150914–150928. [Google Scholar] [CrossRef]
- Xiao, H.; Zhang, Q.; Ouyang, S.; Chronopoulos, A.T. Connectivity probability analysis for VANET freeway traffic using a cell transmission model. IEEE Syst. J. 2020, 15, 1815–1824. [Google Scholar] [CrossRef]
- Khatri, S.; Vachhani, H.; Shah, S.; Bhatia, J.; Chaturvedi, M.; Tanwar, S.; Kumar, N. Machine learning models and techniques for VANET based traffic management: Implementation issues and challenges. Peer-to-Peer Netw. Appl. 2021, 14, 1778–1805. [Google Scholar] [CrossRef]
- Alaya, B.; Sellami, L. Clustering method and symmetric/asymmetric cryptography scheme adapted to securing urban VANET networks. J. Inf. Secur. Appl. 2021, 58, 102779. [Google Scholar] [CrossRef]
- Mirsadeghi, F.; Rafsanjani, M.K.; Gupta, B.B. A trust infrastructure based authentication method for clustered vehicular ad hoc networks. Peer-to-Peer Netw. Appl. 2021, 14, 2537–2553. [Google Scholar] [CrossRef]
- Alkhalidy, M.; Al-Serhan, A.F.; Alsarhan, A.; Igried, B. A new scheme for detecting malicious nodes in vehicular ad hoc networks based on monitoring node behavior. Future Internet 2022, 14, 223. [Google Scholar] [CrossRef]
- Bijalwan, A.; Purohit, K.C.; Malik, P.; Mittal, M. A Self-Adaptable Angular Based K-Medoid Clustering Scheme (SAACS) for Dynamic VANETs. Electronics 2022, 11, 3071. [Google Scholar] [CrossRef]
- Ouallane, A.A.; Bakali, A.; Bahnasse, A.; Broumi, S.; Talea, M. Fusion of engineering insights and emerging trends: Intelligent urban traffic management system. Inf. Fusion 2022, 88, 218–248. [Google Scholar] [CrossRef]
- Rajeswari, R.; Rajesh, S. Enhance Security and Privacy in VANET Based Sensor Monitoring and Emergency Services. Cybern. Syst. 2023, 1, 1–22. [Google Scholar] [CrossRef]
- Hireche, S.; Dennai, A.; Kadri, B. Toward a Novel RESTFUL Big Data-Based Urban Traffic Incident Data Web Service for Connected Vehicles. Comput. J. 2023, 1. [Google Scholar] [CrossRef]
- Narayanan, K.L.; Naresh, R. An efficient key validation mechanism with VANET in real-time cloud monitoring metrics to enhance cloud storage and security. Sustain. Energy Technol. Assess. 2023, 56, 102970. [Google Scholar]
- Nazib, R.A.; Moh, S. Routing Protocols for Unmanned Aerial Vehicle-Aided Vehicular Ad Hoc Networks: A Survey. IEEE Access 2020, 8, 77535–77560. [Google Scholar] [CrossRef]
- Qureshi, K.N.; Bashir, F.; Abdullah, A.H. Distance and signal quality aware next hop selection routing protocol for vehicular ad hoc networks. Neural Comput. Appl. 2020, 32, 2351–2364. [Google Scholar] [CrossRef]
- Jaiswal, R.K. Position-based routing protocol using Kalman filter as a prediction module for vehicular ad hoc networks. Comput. Electr. Eng. 2020, 83, 106599. [Google Scholar] [CrossRef]
- Eldin, K.Y.E.; Ahwal, A.A. A Comparative Study On Vehicular Ad-Hoc Networks Topology Based Routing Protocols. Eng. Res. J. 2020, 1, 111–117. [Google Scholar]
- Obaidat, M.; Khodjaeva, M.; Holst, J.; Zid, M.B. Security and Privacy Challenges in Vehicular Ad Hoc Networks; Springer: Berlin/Heidelberg, Germany, 2020; pp. 223–251. [Google Scholar]
- Sugumar, R.; Rengarajan, A.; Jayakumar, C. Trust based authentication technique for cluster based vehicular ad hoc networks (VANET). Wirel. Netw. 2018, 24, 373–382. [Google Scholar] [CrossRef]
- Kolandaisamy, R.; Noor, R.M.; Kolandaisamy, I.; Ahmedy, I.; Kiah, M.L.M.; Tamil, M.E.M.; Nandy, T. A stream position performance analysis model based on DDoS attack detection for cluster-based routing in VANET. J. Ambient. Intell. Humaniz. Comput. 2020, 12, 6599–6612. [Google Scholar] [CrossRef]
- Deshmukh, A.R.; Dhawale, S.A.; Dorle, S. Analysis of Cluster Based Routing Protocol (CBRP) for Vehicular Adhoc Network (VANet) in Real Geographic Scenario. In Proceedings of the IEEE International Conference on Electronics, Computing and Communication Technologies (CONECCT), Bangalore, India, 2–4 July 2020; pp. 1–5. [Google Scholar]
- Yogarayan, S.; Razak, S.F.A.; Azman, A.; Abdullah, M.F.; Ibrahim, S.Z.; Raman, K.J. A Review of Routing Protocols for Vehicular Ad-Hoc Networks (VANETs). In Proceedings of the 8th International Conference on Information and Communication Technology (ICoICT), Yogyakarta, Indonesia, 24–26 June 2020; pp. 1–7. [Google Scholar]
- Srivastava, A.; Prakash, A.; Tripathi, R. Location based routing protocols in VANET: Issues and existing solutions. Veh. Commun. 2020, 23, 100231. [Google Scholar] [CrossRef]
- Ariffin, R.N.R.; Zahari, R.K. Perceptions of the urban walking environments. Procedia-Soc. Behav. Sci. 2013, 105, 589–597. [Google Scholar] [CrossRef]
- Hillnhütter, H. Stimulating urban walking environments–Can we measure the effect? Environ. Plan. B Urban Anal. City Sci. 2022, 49, 275–289. [Google Scholar] [CrossRef]
- dos Santos, P.M.S. Wireless Protocols and Channel Estimation for Data Gathering with Mobile Nodes. Ph.D. Thesis, Universidade do Porto, Porto, Portugal, 2017. [Google Scholar]
- Liang, L.; Xie, S.; Li, G.Y.; Ding, Z.; Yu, X. Graph-based resource sharing in vehicular communication. IEEE Trans. Wirel. Commun. 2018, 17, 4579–4592. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).