Protection Schemes for DDoS, ARP Spoofing, and IP Fragmentation Attacks in Smart Factory
Abstract
1. Introduction
2. Related Works
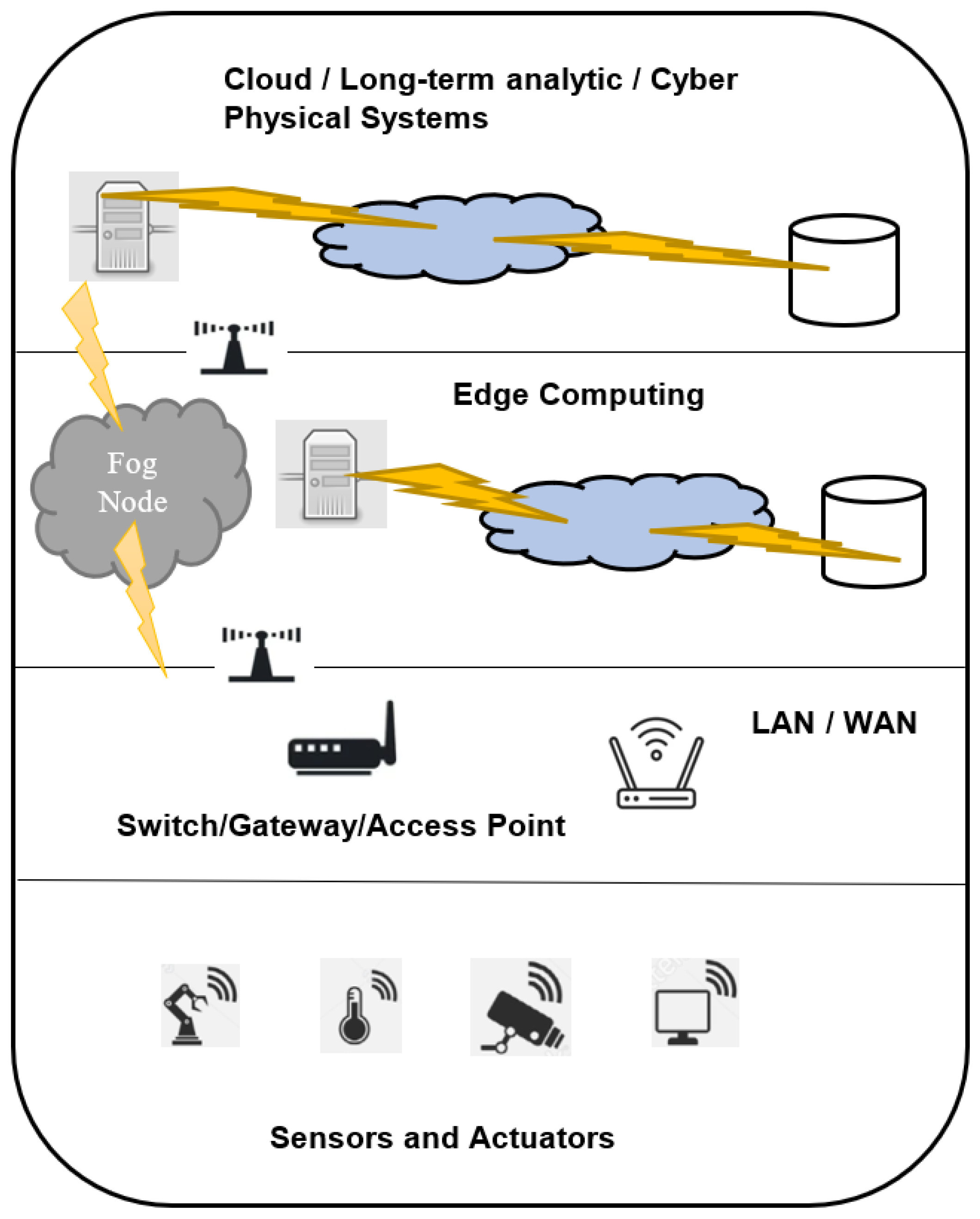
3. Proposed Protection Mechanism
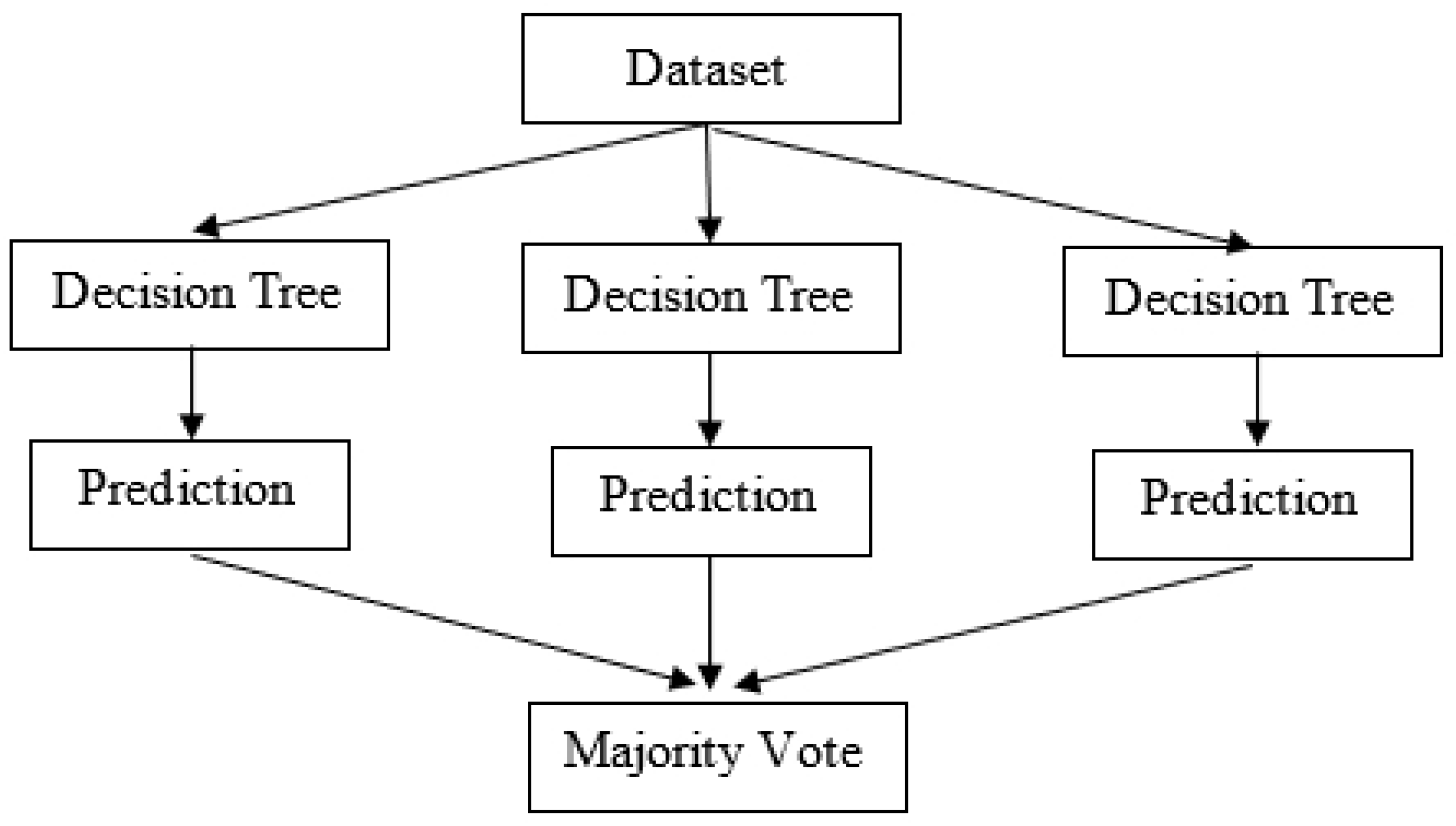
3.1. Random Forest
3.2. Principal Component Analysis
3.3. Entropy-Based Detection
ARP Spoofing Analysis
| Algorithm 1 Proposed ARP Spoofing Detect and Protect Based on Entropy |
| log_monitor_ip_mac: dictionary to keep IP-MAC mapping Input: Time Window slot (W1. . . Wn) = S, Attr1 as sender MAC Output: Set Entropy threshold ← 1.35 for all Wi ∈ S do //get entropy of the ARP traffic in current window slot curEntropyAttr1 ← COMPUTE entropy of sender MAC if (APi(MAC) in capture MAC address) then filterAttackerTraffic() end if //raise alarm if (curEntropyAttr1 < Entropy threshold) then ARP List ← UNIQUE IP, MAC from a high volume of ARP packet’s in Wi //get the Sender IP, MAC in ARP MAC ← MAC in ARP List IP ← IP in ARP List length ← COUNT ARP List if (length > 1)//duplicate address found then detect spoofing ← True else match ← matchMacToIp (IP, MAC, log_monitor_ip_mac) if(!match) then detect spoofing ← True end if end if if (detect spoofing = True) then //keep the mac address in a list UPDATE MAC in capture mac address else //keep the IP-MAC in dictionary for further validation UPDATE IP, MAC in log_monitor_ip_mac end if end if |
3.4. One-Time Code and Timestamp
3.5. Dataset
4. Simulations and Results
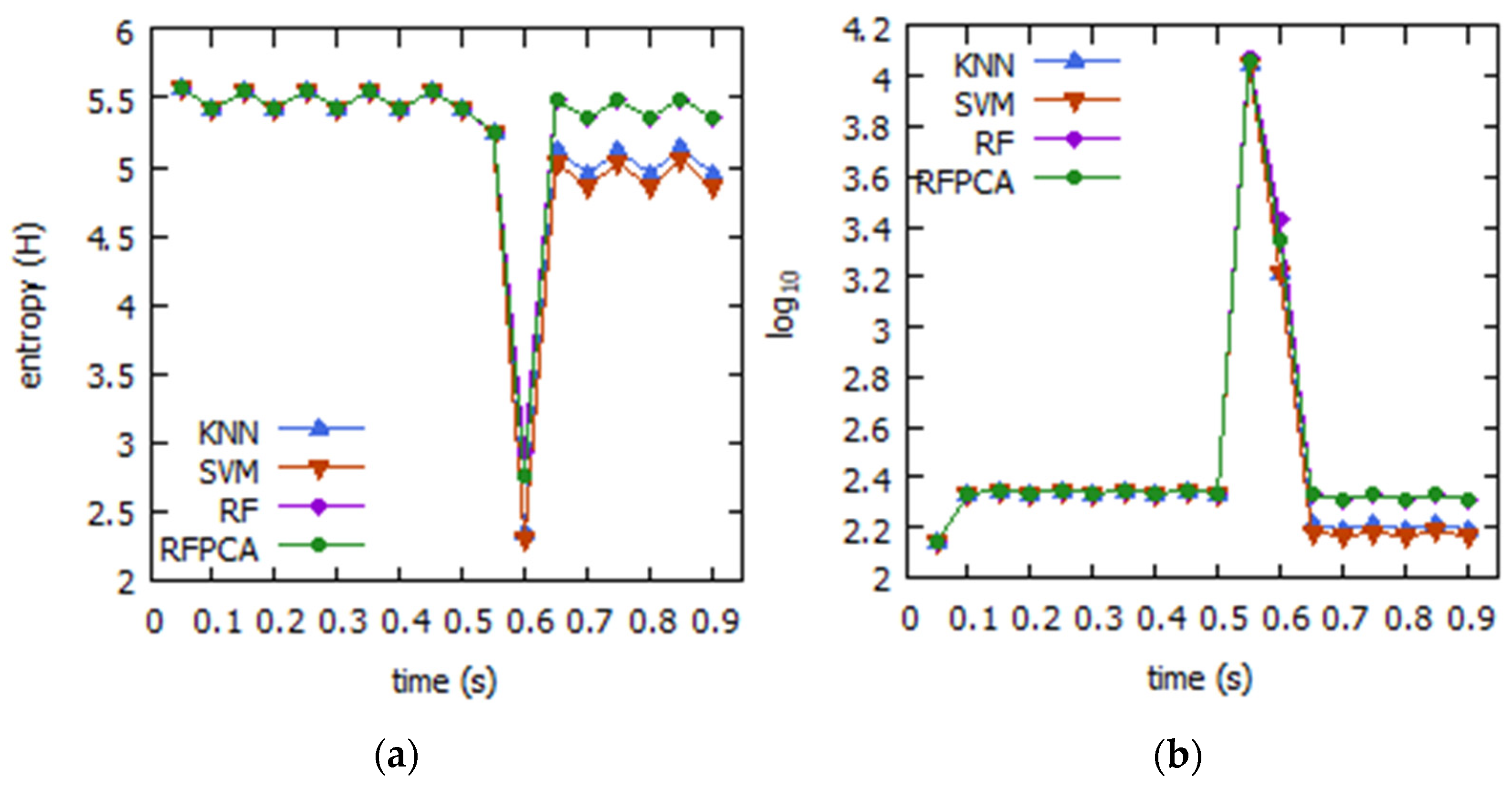
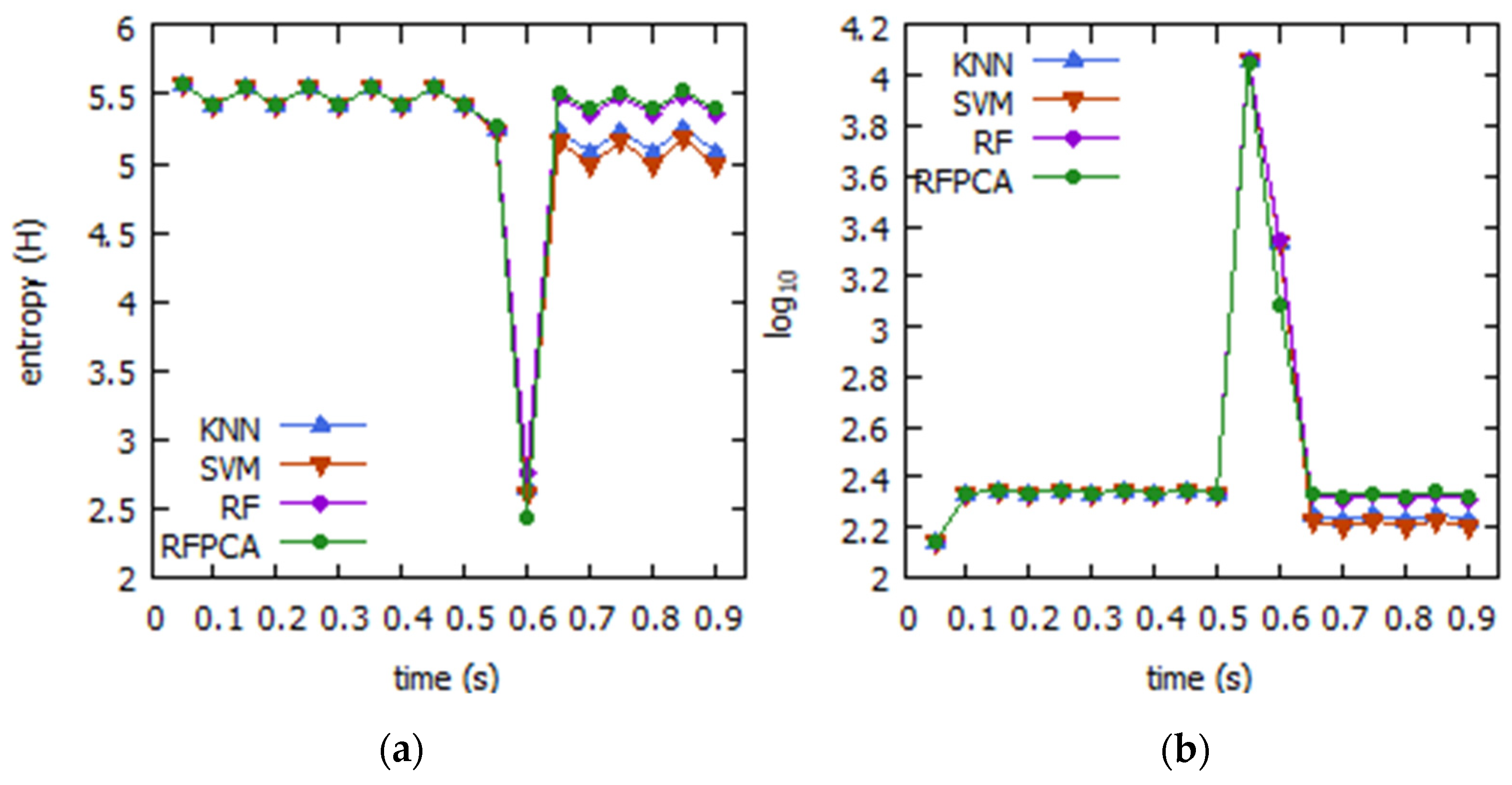
4.1. DDoS
4.1.1. Simulation Analysis
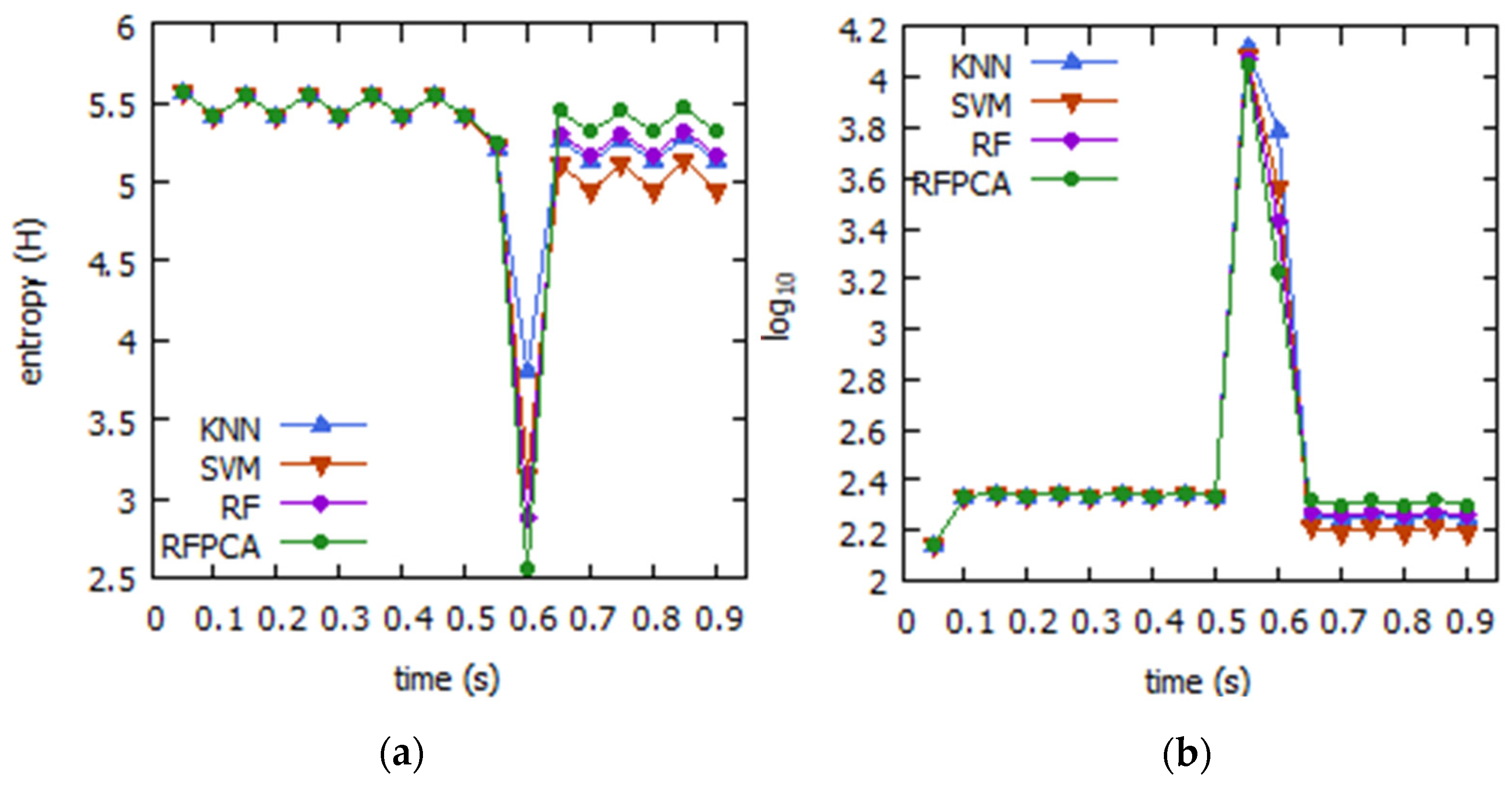
4.1.2. Evaluation and Discussion
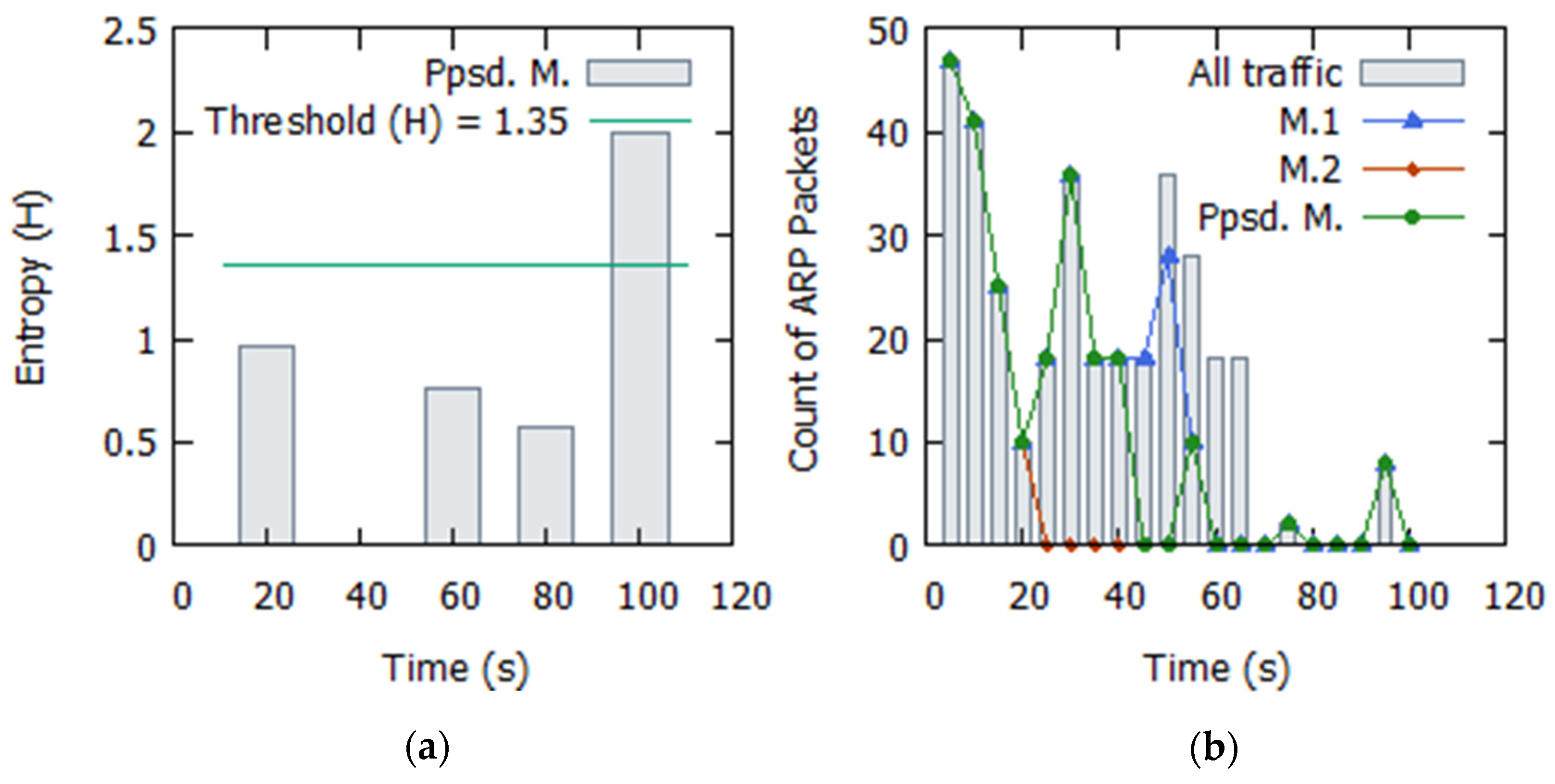
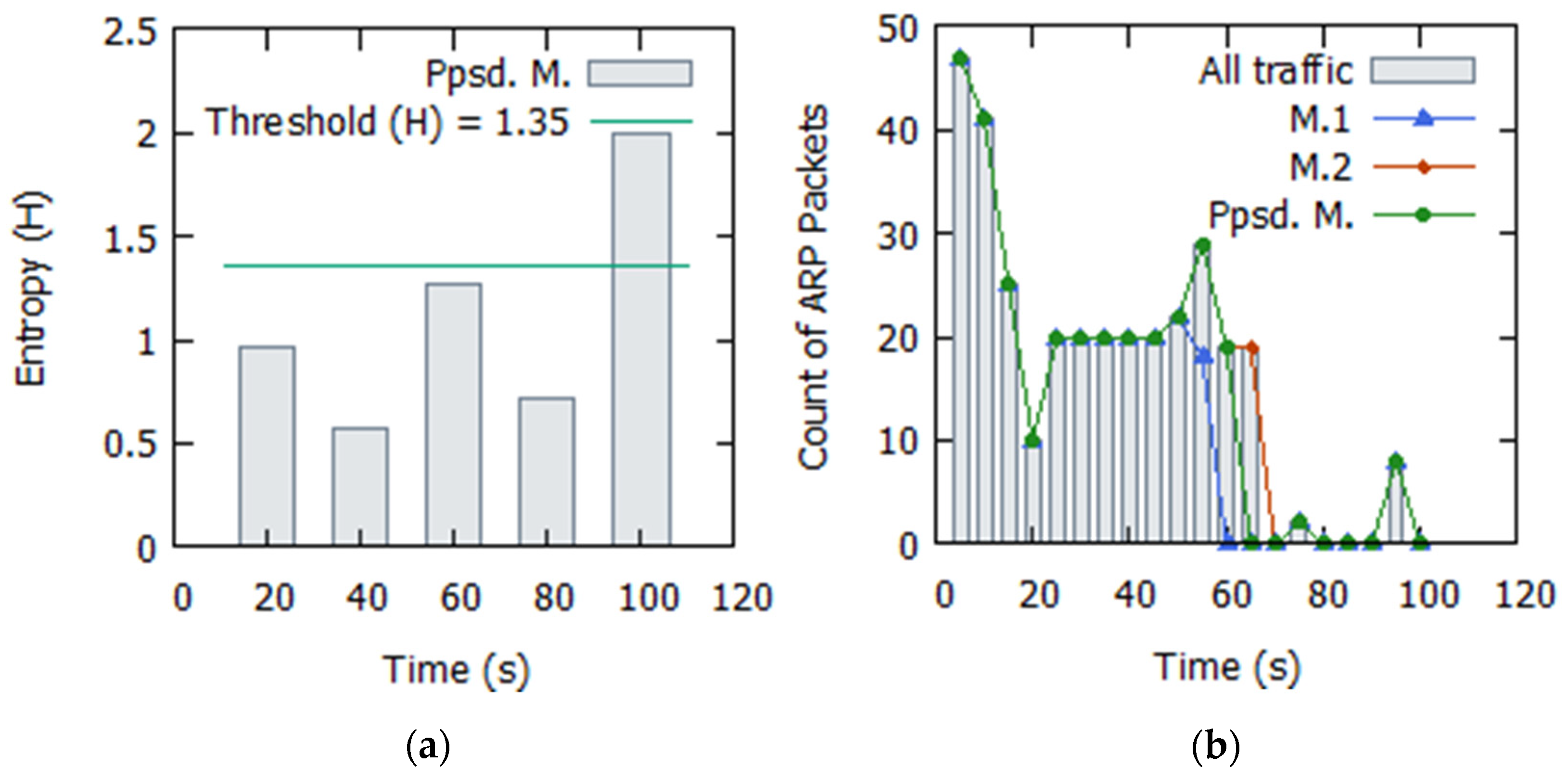
4.2. ARP Spoofing
4.2.1. Simulation Analysis
4.2.2. Evaluation and Discussion
4.3. IP Fragmentation Attack (Mis-Association)
4.3.1. Simulation Analysis
4.3.2. Evaluation and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Russmann, M.; Lorenz, M.; Gerbert, P.; Waldner, M.; Justus, J.; Engel, P.; Harnisch, M. Industry 4.0: The future of productivity and growth in manufacturing industries. Boston Consult. Group 2015, 9, 54–89. [Google Scholar]
- Chen, B.; Wan, J.; Shu, L.; Li, P.; Mukherjee, M.; Yin, B. Smart factory of industry 4.0: Key technologies, application case, and challenges. IEEE Access 2017, 6, 6505–6519. [Google Scholar] [CrossRef]
- Yao, X.; Zhou, J.; Lin, Y.; Li, Y.; Yu, H.; Liu, Y. Smart manufacturing based on cyber-physical systems and beyond. J. Intell. Manuf. 2019, 30, 2805–2817. [Google Scholar] [CrossRef]
- Nagy, J.; Olah, J.; Erdei, E.; Mate, D.; Popp, J. The role and impact of industry 4.0 and the internet of things on the business strategy of the value chain-the case of hungary. Sustainability 2018, 10, 3491. [Google Scholar] [CrossRef]
- Liu, Q.; Li, P.; Zhao, W.; Cai, W.; Yu, S.; Leung, V.C.M. A survey on security threats and defensive techniques of machine learning: A data driven view. IEEE Access 2018, 6, 12103–12117. [Google Scholar] [CrossRef]
- Syafrudin, M.; Alfian, G.; Fitriyani, N.L.; Rhee, J. Performance analysis of IoT-based sensor, big data processing, and machine learning model for real-time monitoring system in automotive manufacturing. Sensors 2018, 18, 2946. [Google Scholar] [CrossRef] [PubMed]
- Sengupta, J.; Ruj, S.; das Bit, S. A secure fog-based architecture for industrial internet of things and industry 4.0. IEEE Trans. Ind. Inform. 2020, 17, 2316–2324. [Google Scholar] [CrossRef]
- Qi, Q.; Tao, F. A smart manufacturing service system based on edge computing, fog computing, and cloud computing. IEEE Access 2019, 7, 86769–88677. [Google Scholar] [CrossRef]
- Vaidya, S.; Ambad, P.; Bhosle, S. Industry 4.0—A glimpse. Procedia Manuf. 2018, 20, 233–238. [Google Scholar] [CrossRef]
- Tawalbeh, L.; Muheidat, F.; Tawalbeh, M.; Quwaider, M. IoT privacy and security: Challenges and solutions. Appl. Sci. 2020, 10, 4102. [Google Scholar] [CrossRef]
- Tuptuk, N.; Hailes, S. Security of smart manufacturing systems. J. Manuf. Syst. 2018, 47, 93–106. [Google Scholar] [CrossRef]
- Yu, M.; Zhuge, J.; Cao, M.; Shi, Z.; Jiang, L. A survey of security vulnerability analysis, discovery, detection, and mitigation on IoT devices. Future Internet 2020, 12, 27. [Google Scholar] [CrossRef]
- Staddon, E.; Loscri, V.; Mitton, N. Attack categorisation for IoT applications in critical infrastructures, a survey. Appl. Sci. 2021, 11, 7228. [Google Scholar] [CrossRef]
- Lee, Y.; Chae, H.; Lee, K. Countermeasures against large-scale reflection DDoS attacks using exploit IoT devices. Automatika 2021, 62, 127–136. [Google Scholar] [CrossRef]
- Li, D.; Yu, C.; Zhou, Q.; Yu, J. Using SVM to Detect DDoS Attack in SDN Network. J. Phys. Conf. Ser. 2019, 1237, 1–5. [Google Scholar] [CrossRef]
- Lohachab, A.; Karambir, B. Critical analysis of DDoS—An emerging security threat over IoT networks. J. Commun. Inf. Netw. 2018, 3, 57–78. [Google Scholar] [CrossRef]
- Butun, I.; Osterberg, P.; Song, H. Security of the internet of things: Vulnerabilities, attacks and countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 16–18 August 2017; pp. 1093–1110. [Google Scholar]
- Sinanovic, H.; Mrdovic, S. Analysis of Mirai malicious software. In Proceedings of the 25th International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 21–23 September 2017. [Google Scholar]
- Router and IoT Vulnerabilities: Insecure by Design; IOT Security Foundation: West Lothian, UK, 2021.
- Aytac, T.; Aydın, M.A.; Zaim, A.H. Detection DDoS attacks using machine learning methods. Electrica 2020, 20, 159–167. [Google Scholar] [CrossRef]
- Wang, S.; Gomez, K.; Sithamparanathan, K.; Asghar, M.R.; Russello, G.; Zanna, P. Mitigating DDoS attacks in SDN-based IoT networks leveraging secure control and data plane algorithm. Appl. Sci. 2021, 11, 929. [Google Scholar] [CrossRef]
- Sudar, K.M.; Beulah, M.; Deepalakshmi, P.; Nagaraj, P.; Chinnasamy, P. Detection of distributed denial of service attacks in SDN using machine learning techniques. In Proceedings of the 2021 International Conference on Computer Communication and Informatics, ICCCI 2021, Coimbatore, India, 27–29 January 2021; pp. 25–29. [Google Scholar]
- Dong, S.; Sarem, M. DDoS attack detection method based on Improved KNN with the degree of DDoS attack in software-defined networks. IEEE Access 2020, 8, 5039–5048. [Google Scholar] [CrossRef]
- Pei, J.; Chen, Y.; Ji, W. A DDoS attack detection method based on machine learning. J. Phys. Conf. Ser. 2019, 1237, 032040. [Google Scholar] [CrossRef]
- Gao, W.; Sun, Y.; Fu, Q.; Wu, Z.; Ma, X.; Zheng, K.; Huang, X. ARP poisoning prevention in internet of things. In Proceedings of the 9th International Conference on Information Technology in Medicine and Education (ITME), Hangzhou, China, 19–21 October 2018; pp. 733–736. [Google Scholar]
- Abid, M.; Singh, A. ARP spoofing detection via wireshark and veracode. Int. J. New Technol. Res. 2018, 4, 263063. [Google Scholar]
- Aly, M.; Khomh, F.; Gueheneuc, Y.G.; Washizaki, H.; Yacout, S. Is fragmentation a threat to the success of the internet of things. IEEE Internet Things J. 2019, 6, 472–487. [Google Scholar] [CrossRef]
- Feng, X.; Li, Q.; Sun, K.; Xu, K.; Liu, B.; Zheng, X.; Yang, Q.; Duan, H.; Qian, Z. PMTUD is not panacea: Revisiting IP fragmentation attacks against TCP. In Proceedings of the Network & Distributed System Security Symposium (NDSS), San Diego, CA, USA, 24–28 April 2022. [Google Scholar]
- Suciu, I.; Vilajosana, X.; Adelantado, F. An analysis of packet fragmentation impact in LPWAN. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018. [Google Scholar]
- Dai, T.; Shulman, H.; Waidner, M. DNS-over-TCP considered vulnerable. In Proceedings of the Applied Networking Research Workshop (ANRW), New York, NY, USA, 24–30 July 2021; pp. 76–81. [Google Scholar]
- Mohandoss, P.; Shi, Y.; Suo, K. Outlier prediction using random forest classifier. In Proceedings of the 2021 IEEE 11th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 27–30 January 2021. [Google Scholar]
- Hoang, D.H.; Nguyen, H.D. A PCA-based method for IoT network traffic anomaly detection. In Proceedings of the 2018 20th International Conference on Advanced Communication Technology (ICACT), Chuncheon, Republic of Korea, 11–14 February 2018; pp. 381–386. [Google Scholar]
- Alghawli, S. Complex methods detect anomalies in real time based on time series analysis. Alex. Eng. J. 2022, 61, 549–561. [Google Scholar] [CrossRef]
- Komazec, T.; Gajin, S. Analysis of flow-based anomaly detection using shannon’s entropy. In Proceedings of the 27th Telecommunications Forum (TELFOR), Belgrade, Serbia, 26–27 November 2019; pp. 1–4. [Google Scholar]
- OMNeT++. Omnet++ Discrete Event Simulator. Available online: omnetpp.org (accessed on 10 January 2023).
- INET. Inet Framework. Available online: https://inet.omnetpp.org/Introduction.htm (accessed on 10 January 2023).



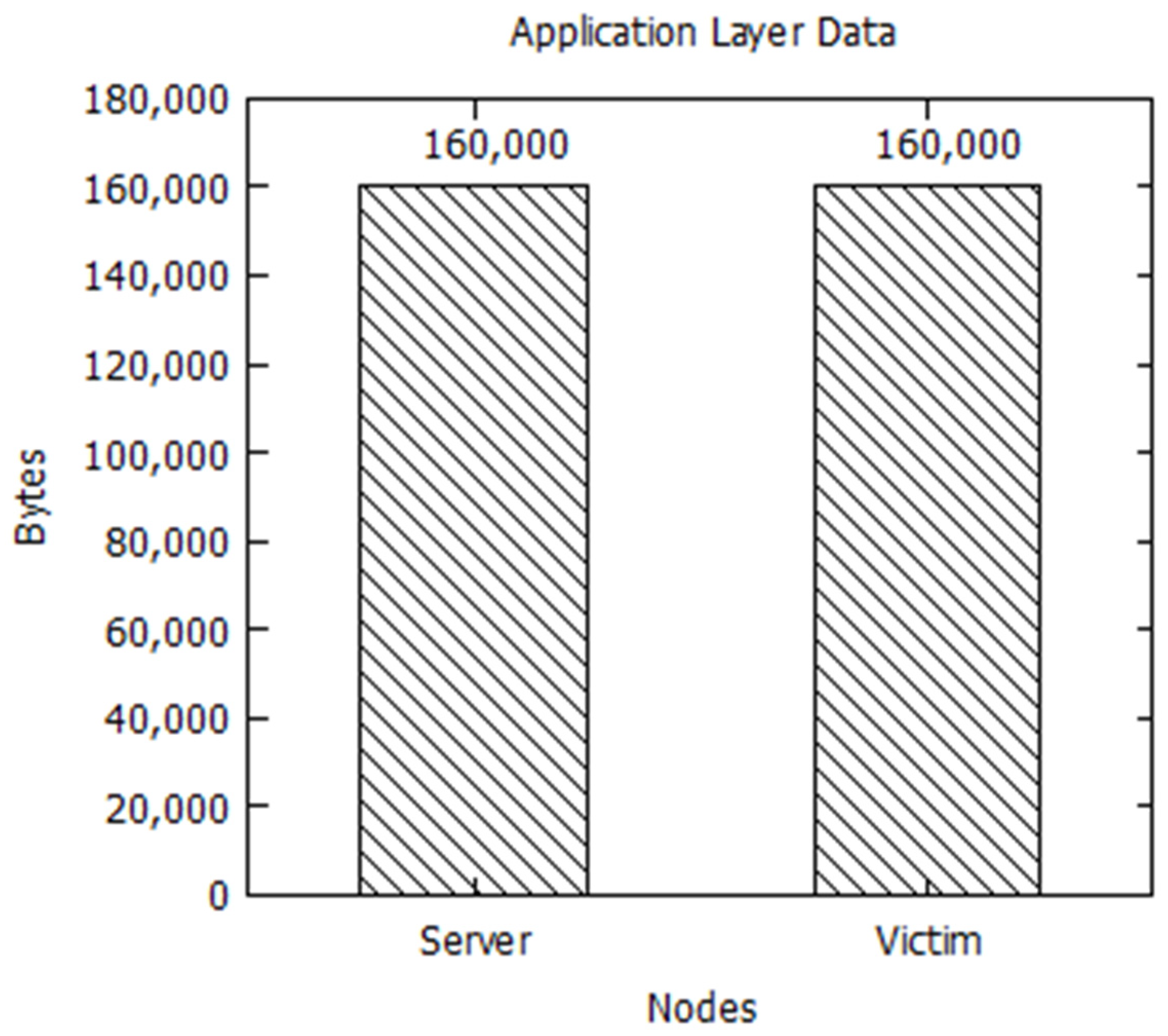
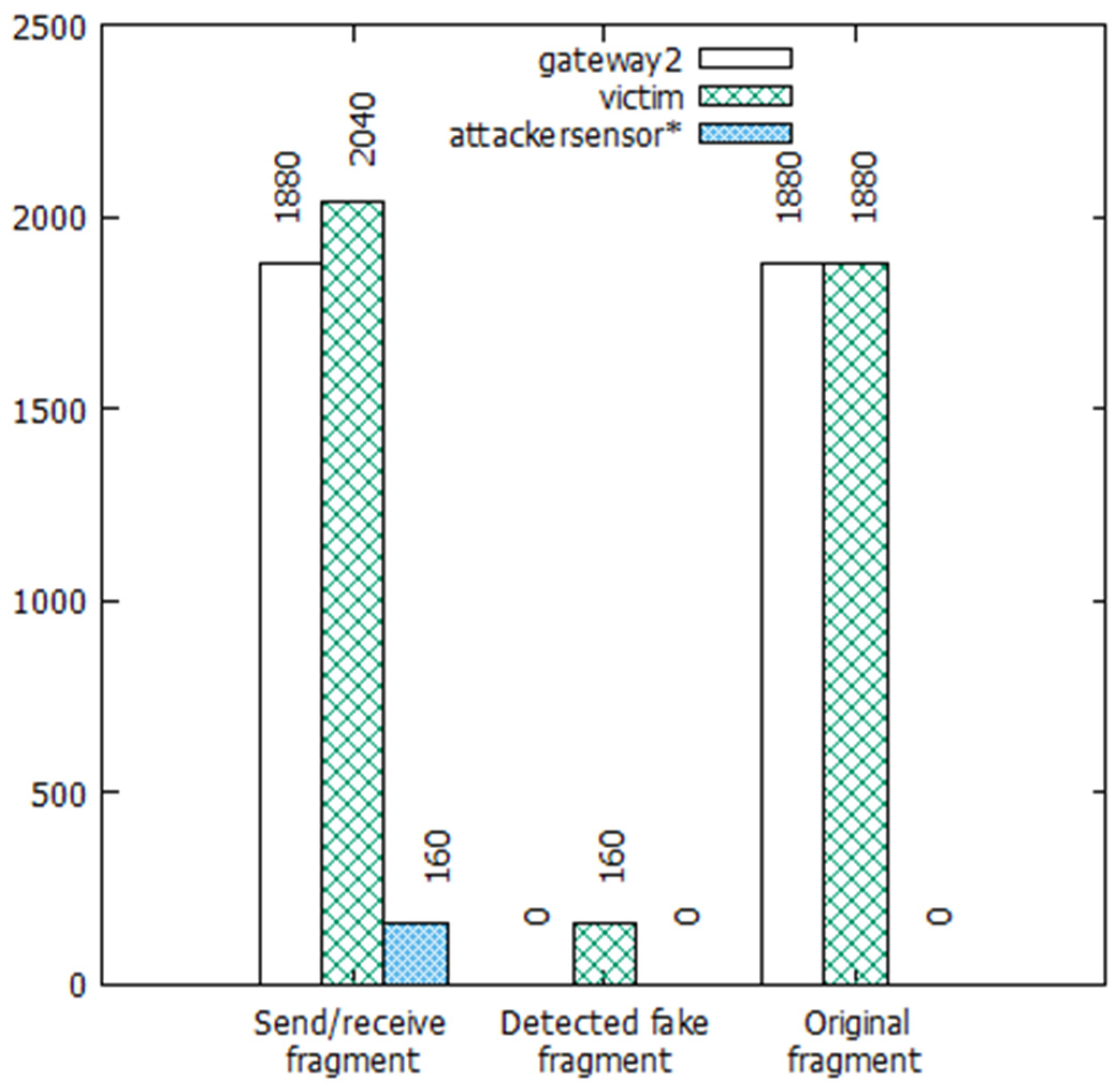
| Node | Source IP | Destination IP (Server) | Source Port | Destination Port | Bytes (Sent) |
|---|---|---|---|---|---|
| Legitimate (65 nodes) | Unique | 1 | Random | Highly random (port no. 80–11,000) | Varies |
| Attacker (35 nodes) | Unique | 1 | Random | Random (with port no 3000–11,000) | Similar |
| No. | Field Name | Field Name (Dataset) | Data Type | Description |
|---|---|---|---|---|
| 1 | Protocol | Protocol | Numerical | Protocol id represent TCP/UDP |
| 2 | Source port | Srcport | Numerical | Source port from sender (incoming) |
| 3 | Destination port | Destport | Numerical | Destination port (incoming) |
| 4 | Bytes | Bytes | Numerical | Data bytes (incoming) |
| Method | Authors | Reference |
|---|---|---|
| SVM | K.M. Sudar, M. Beulah, P. Deepalakshmi, P. Nagaraj and P. Chinnasamy | [23] |
| KNN | S. Dong, and M. Sarem | [24] |
| RF | J. Pei, Y. Chen, and W. Ji | [25] |
| Parameter | Value |
|---|---|
| No. of legitimate nodes (Sender/gateway) | 65 |
| No. of attacker (Gateway) | 35 |
| No. of router (Server-side) | 1 |
| No. of Server | 1 |
| Attacker target | Server |
| Simulation time | 1 s |
| Attack duration | 0.5–0.6 s |
| Sending interval (Attackers) | 0.0001 s |
| Sending interval (Legitimate node) | UDP = 0.01–0.02 s; TCP = 0.3 s |
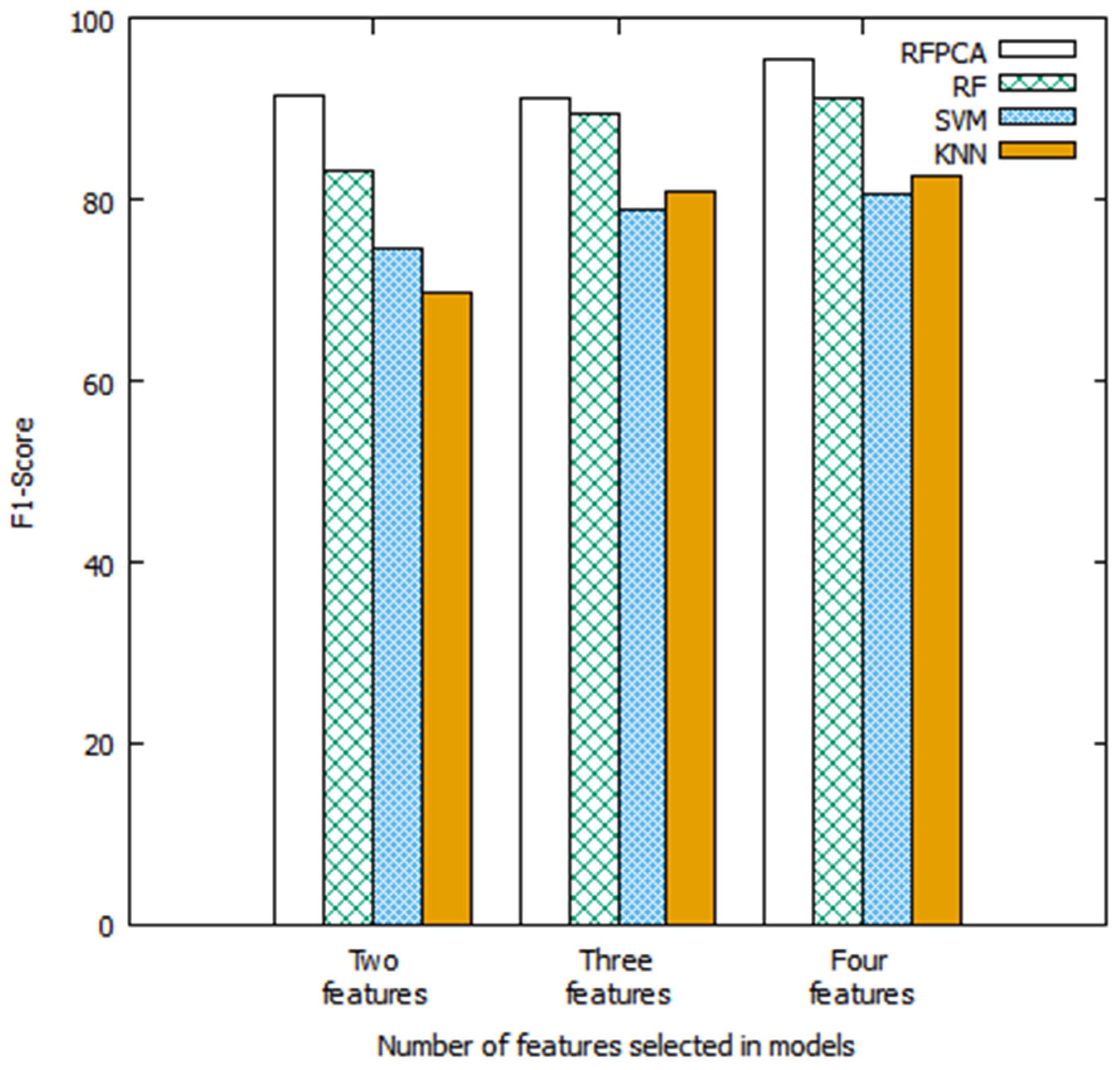
| RFPCA | RF | KNN | SVM | ||
|---|---|---|---|---|---|
| Two features | F1 | 91.43 | 83.33 | 69.7 | 74.67 |
| Accuracy | 94 | 88 | 80 | 81 | |
| Precision | 91.43 | 81.08 | 74.2 | 70 | |
| Recall | 91.43 | 85.71 | 65.71 | 80 | |
| Three features | F1 | 91.18 | 89.55 | 81.01 | 79.02 |
| Accuracy | 94 | 93 | 85 | 83 | |
| Precision | 93.94 | 93.75 | 72.72 | 69.57 | |
| Recall | 88.57 | 85.71 | 91.43 | 91.43 | |
| Four features | F1 | 95.65 | 91.18 | 82.67 | 80.52 |
| Accuracy | 97 | 94 | 87 | 85 | |
| Precision | 97.06 | 93.94 | 77.5 | 73.81 | |
| Recall | 94.29 | 88.57 | 88.57 | 88.57 | |
| Attack Mode | Description |
|---|---|
| Mode-1 | The attacker sends spoofed ARP requests to the router and Node03. |
| Mode-2 | The attacker sends spoofed ARP replies, mimicking a gratuitous ARP variant to the router and Node03. |
| Mode-3 | The attacker replies to a legitimate ARP request with spoofed ARP messages to Node03 and then sends spoofed ARP requests to the router. |
| Parameter | Value |
|---|---|
| No. of attackers | 1 |
| No. nodes in local network (with router) | 10 |
| No. of servers | 1 |
| Attacker target | 2 nodes (Router and Node03) |
| Simulation time | 100 s |
| Attack session | 20–70 s |
| ARP cache timeout | 30 s |
| Method | Description |
|---|---|
| Proposed method | ARP packets are grouped by time window. The protection algorithm is triggered to check for any IP-MAC mapping mismatch or duplicate IP showing the attacker’s address. |
| Method-1 [26] | Each window consists of a maximum of 260 packets. In the separate window, if less than 1/3 of the ARP requests belong to the ARP replies triggered in bulk, then the source address in the ARP reply is the attacker’s address. |
| Method-2 [27] | Spoofed ARP, a variant of gratuitous ARP, is detected if the destination address specifies the destination node. |
| Parameter | Value |
|---|---|
| No. target IoT | 1 |
| No. of attackers | 4 |
| Total cycle of simulation/length | 40 cycle/400 s |
| Data/cycle (Firmware size) | 4 kB |
| Protection | One-time code (OTC) and timestamp |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chai, T.U.; Goh, H.G.; Liew, S.-Y.; Ponnusamy, V. Protection Schemes for DDoS, ARP Spoofing, and IP Fragmentation Attacks in Smart Factory. Systems 2023, 11, 211. https://doi.org/10.3390/systems11040211
Chai TU, Goh HG, Liew S-Y, Ponnusamy V. Protection Schemes for DDoS, ARP Spoofing, and IP Fragmentation Attacks in Smart Factory. Systems. 2023; 11(4):211. https://doi.org/10.3390/systems11040211
Chicago/Turabian StyleChai, Tze Uei, Hock Guan Goh, Soung-Yue Liew, and Vasaki Ponnusamy. 2023. "Protection Schemes for DDoS, ARP Spoofing, and IP Fragmentation Attacks in Smart Factory" Systems 11, no. 4: 211. https://doi.org/10.3390/systems11040211
APA StyleChai, T. U., Goh, H. G., Liew, S.-Y., & Ponnusamy, V. (2023). Protection Schemes for DDoS, ARP Spoofing, and IP Fragmentation Attacks in Smart Factory. Systems, 11(4), 211. https://doi.org/10.3390/systems11040211







