CSI Frequency Domain Fingerprint-Based Passive Indoor Human Detection
Abstract
:1. Introduction
- Considering that existing passive personnel detection methods rely on a target’s mobility and suffer from environmental changes, low robustness and detection accuracy, we use the highly sensitive CSI information to design a method based on the frequency domain fingerprint, combining the results of multi antenna voting to improve the detection accuracy.
- Through experiments, we find that the detection rate is above 90%, no matter whether the scene is human-free, stationary or a moving human presence, which verifies the effectiveness of this scheme.
2. Related Work
3. Preliminary
3.1. Received Signal Strength Indicator and Channel State Information
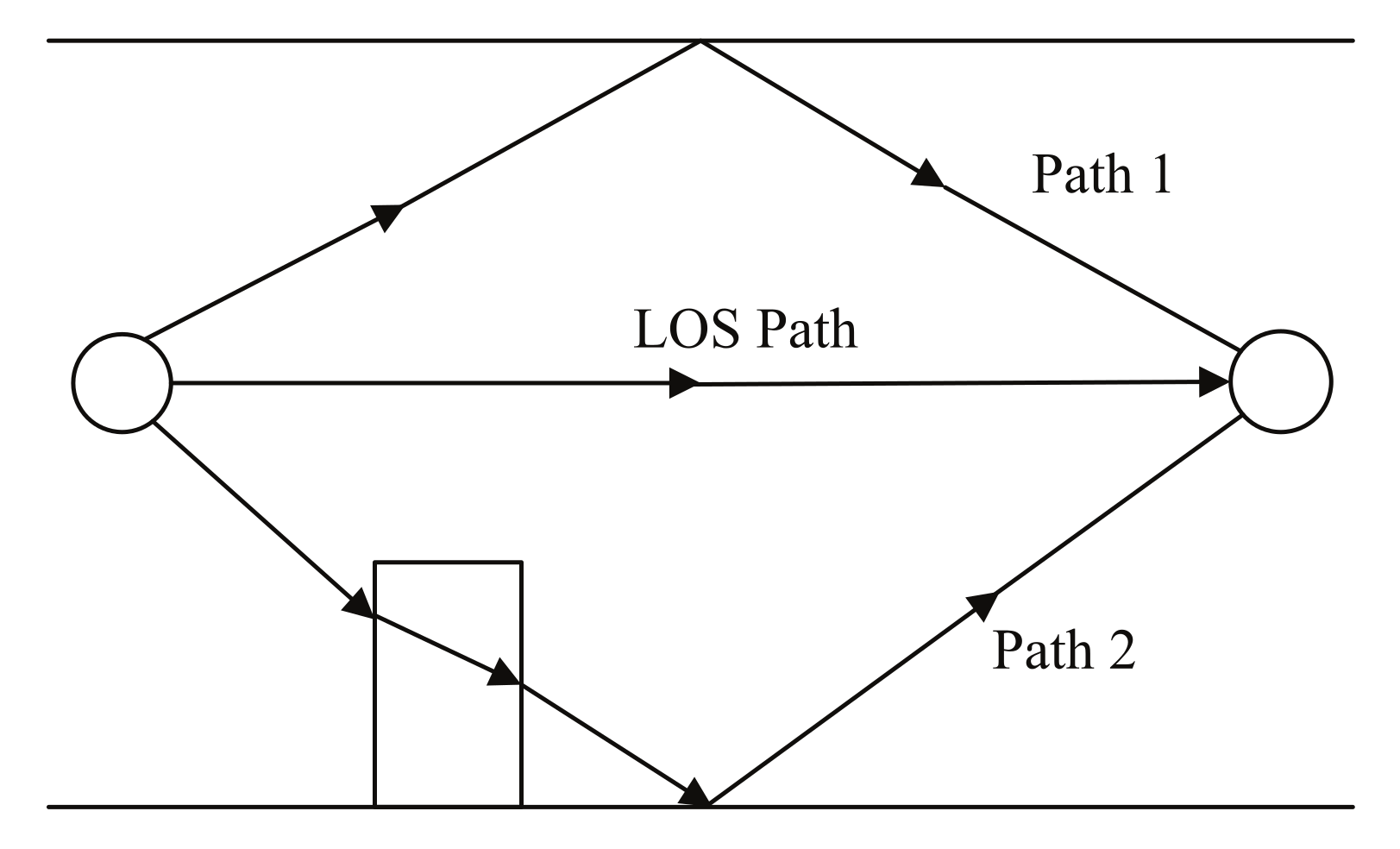
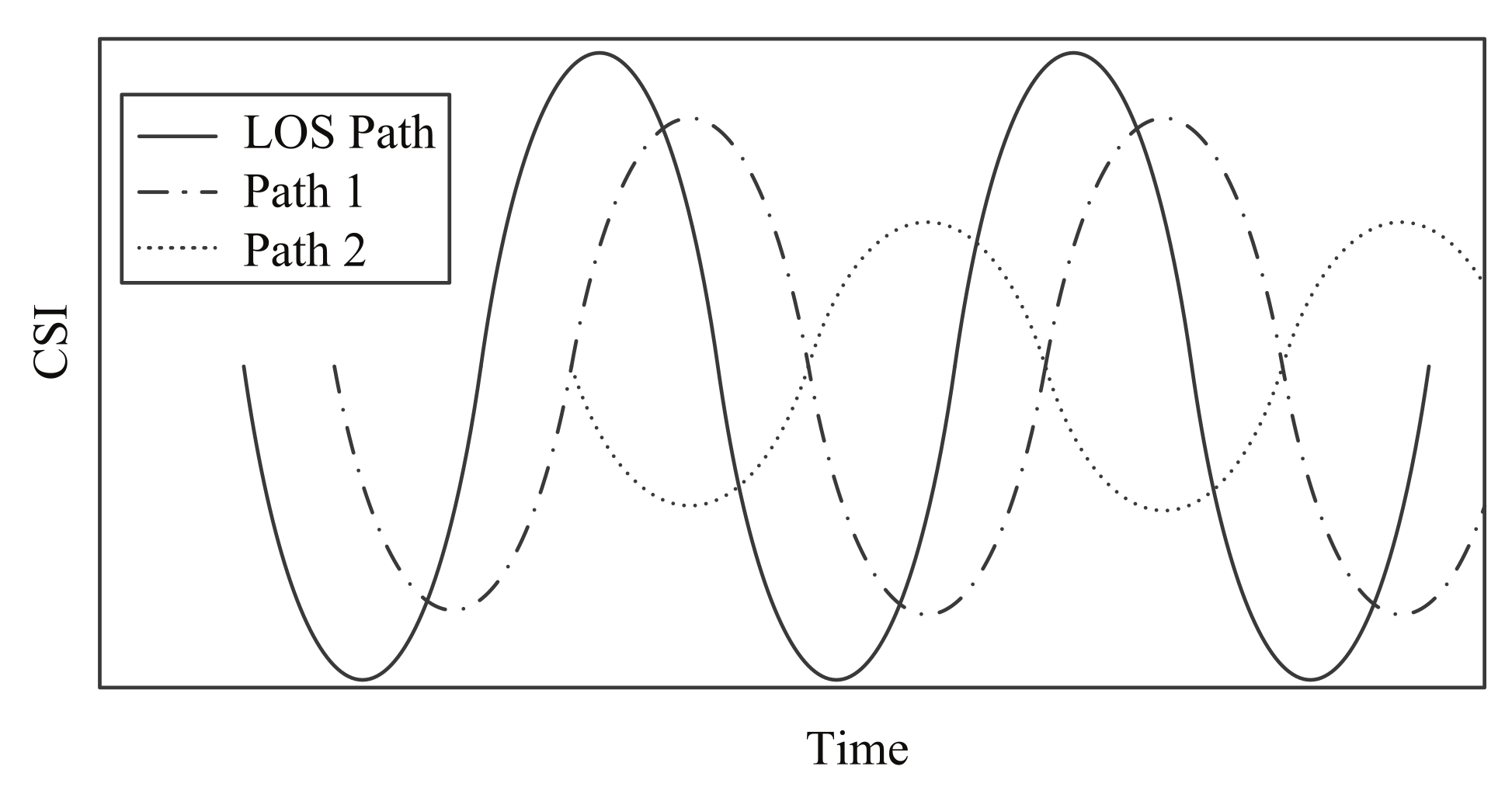
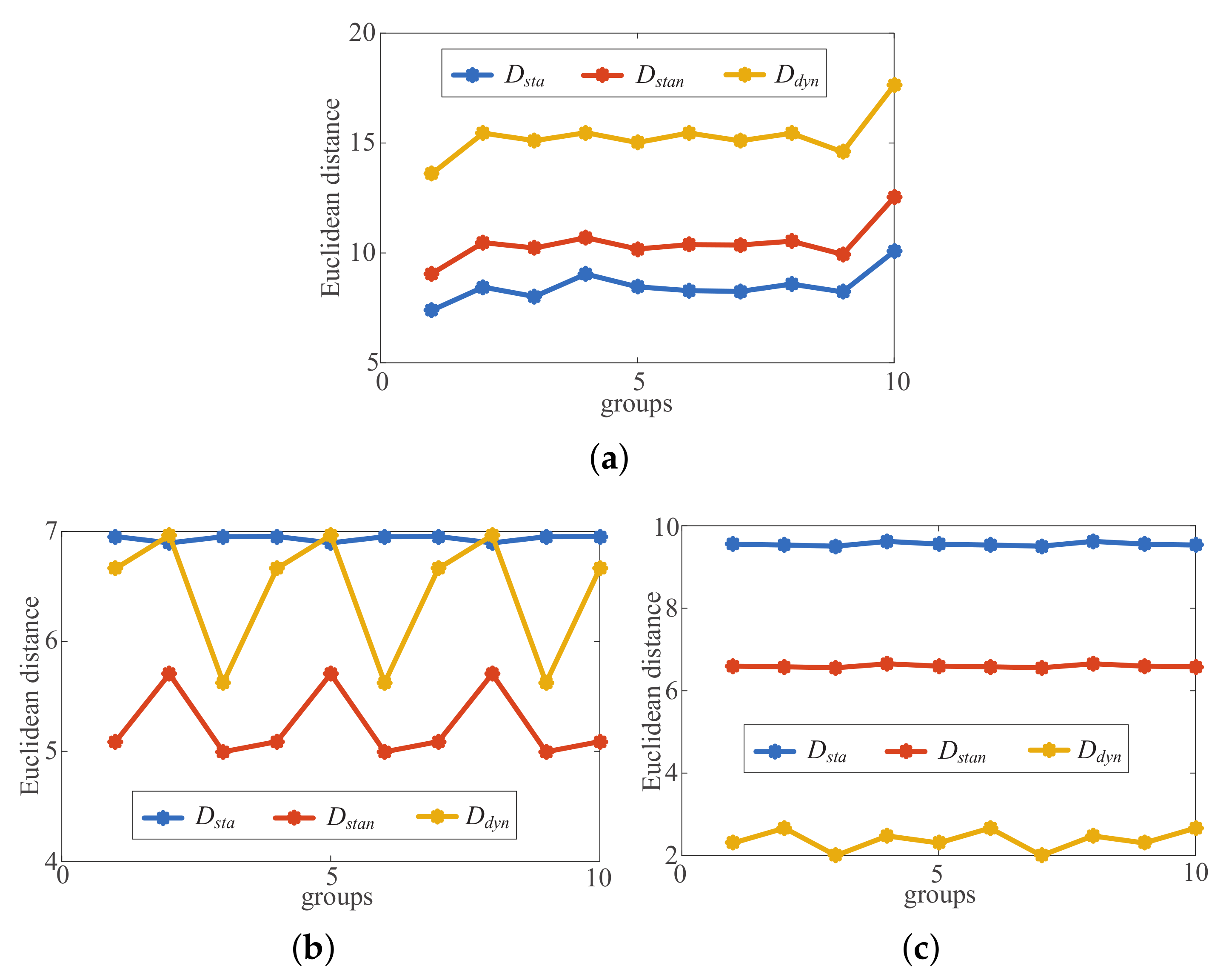
3.2. Feasibility of Distinguishing Indoor Conditions through Frequency Domain Fingerprinting
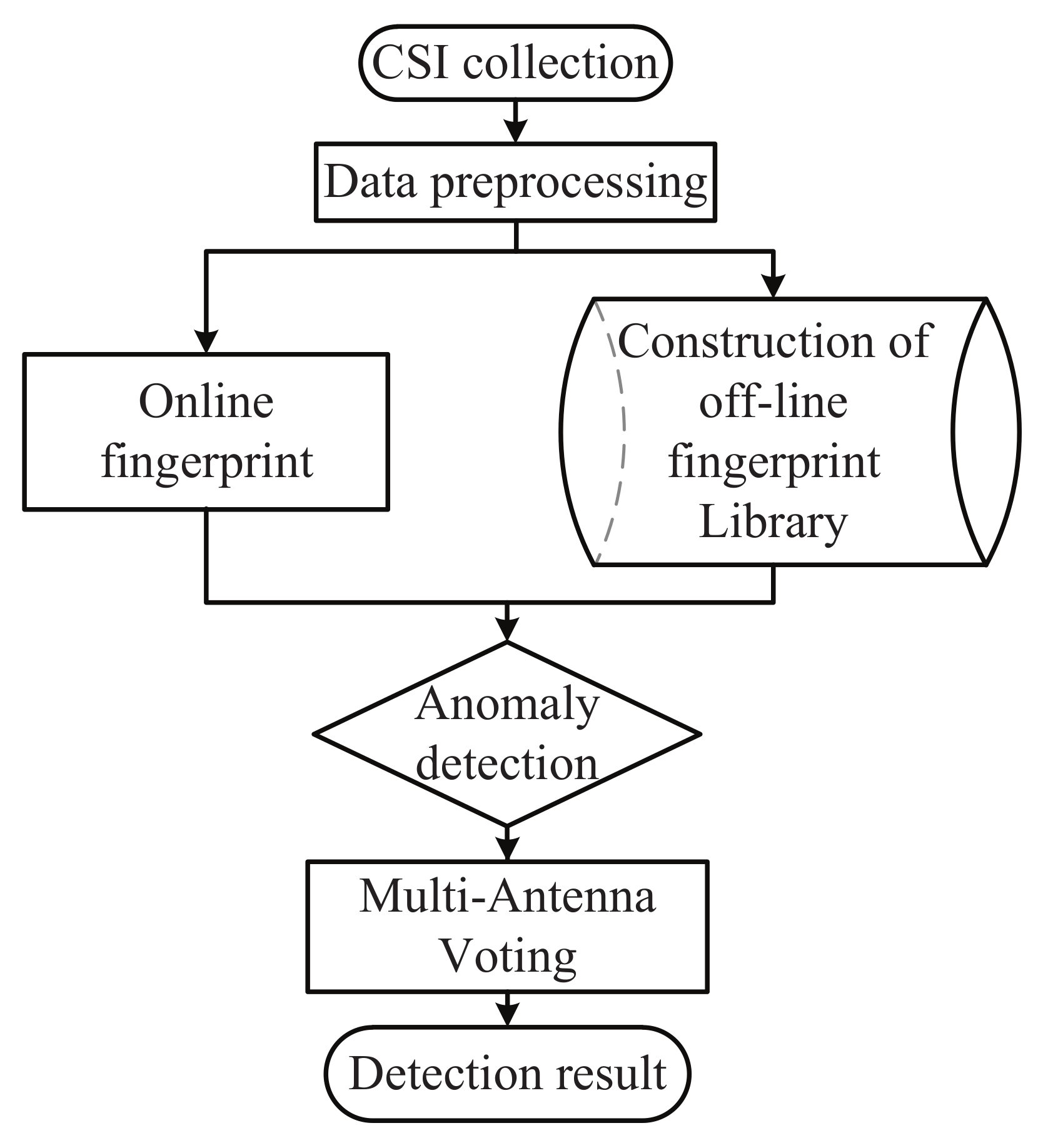
4. System and Methodology
4.1. Offline Phase
4.2. Online Detection and Status Judgment
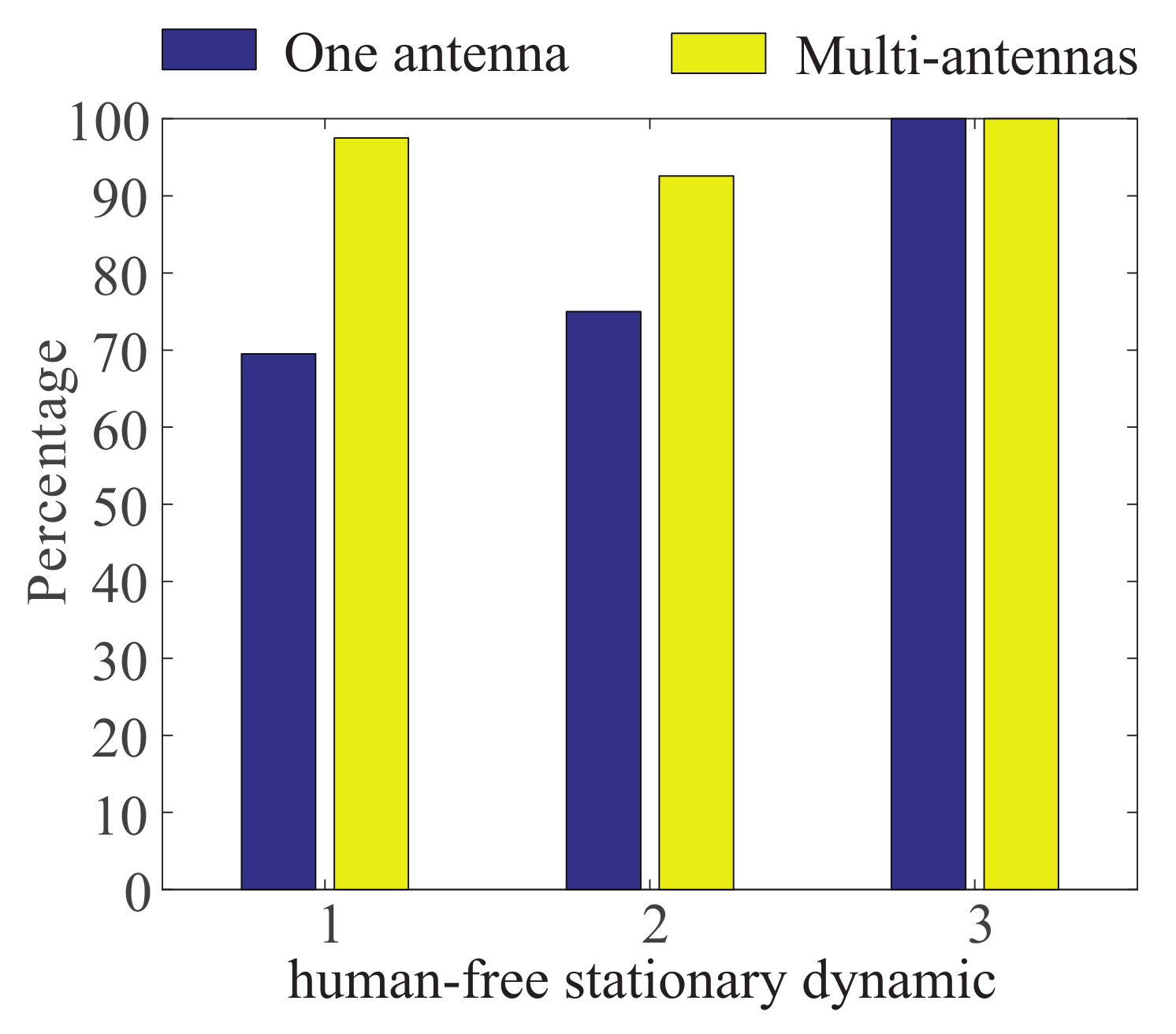
4.3. Multiple Antenna Voting
5. Experiment Results
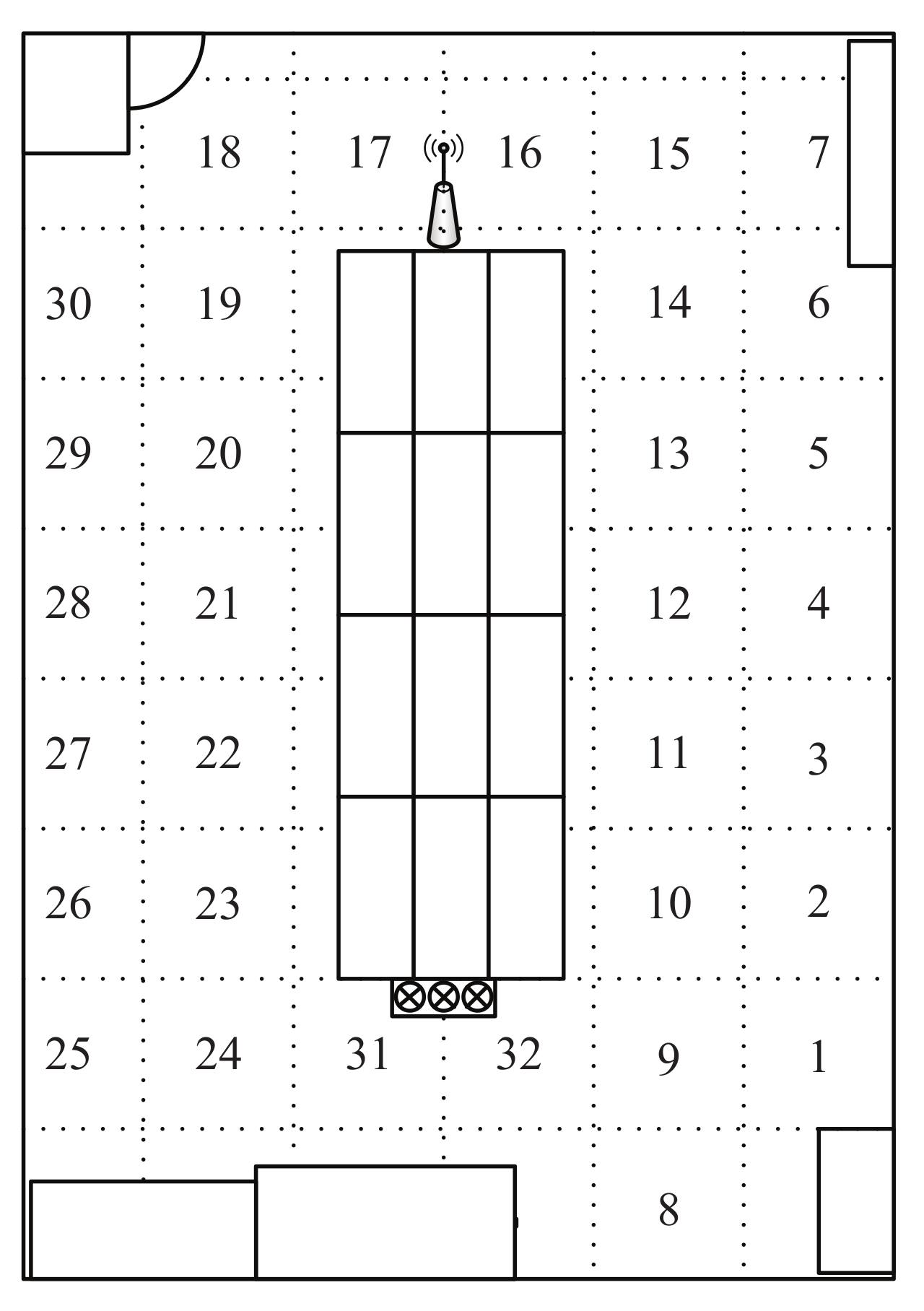
5.1. The Layout of the Experimental Scene
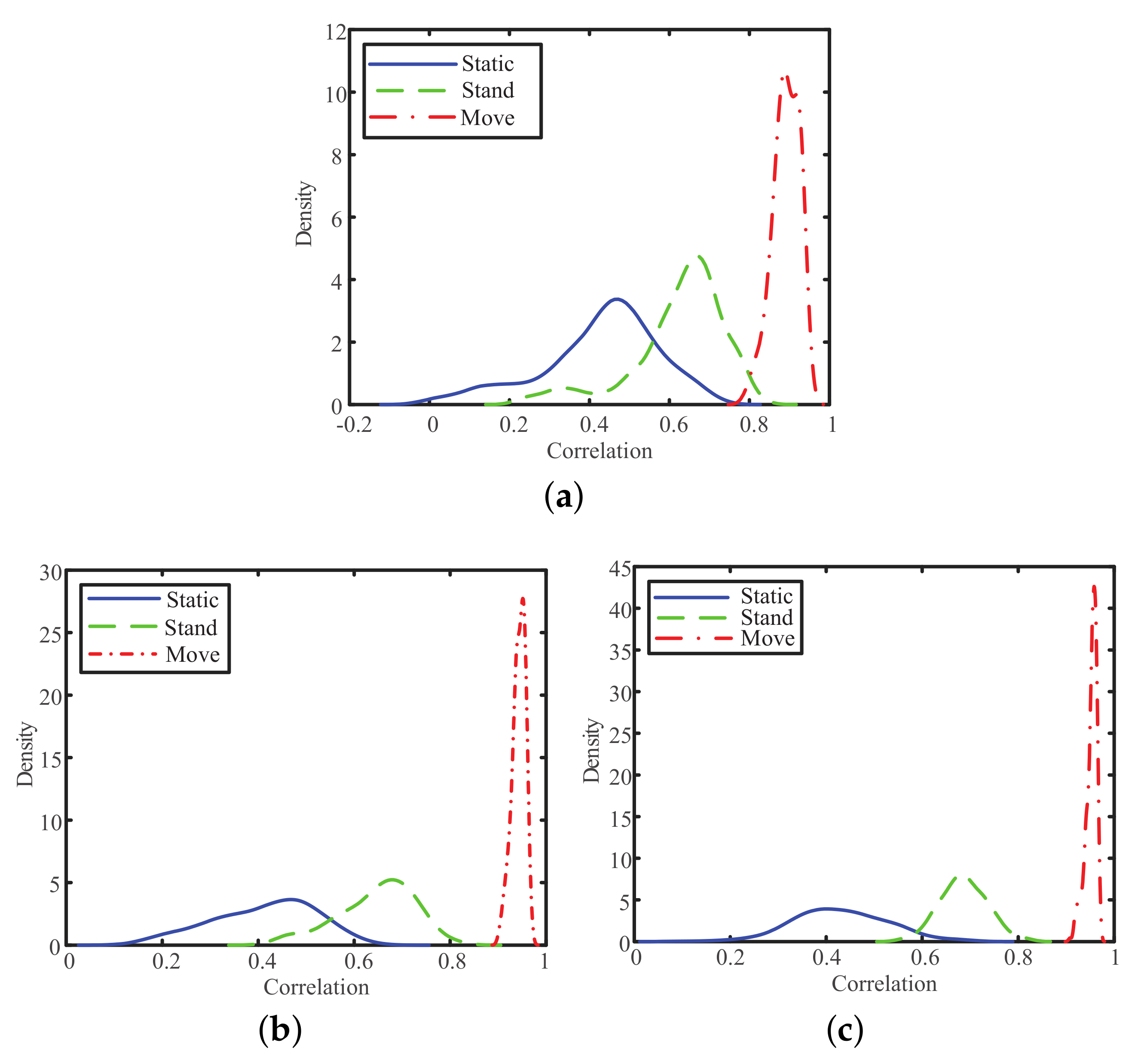
5.2. Impact of Multiple Antennas’ Voting on Test Results
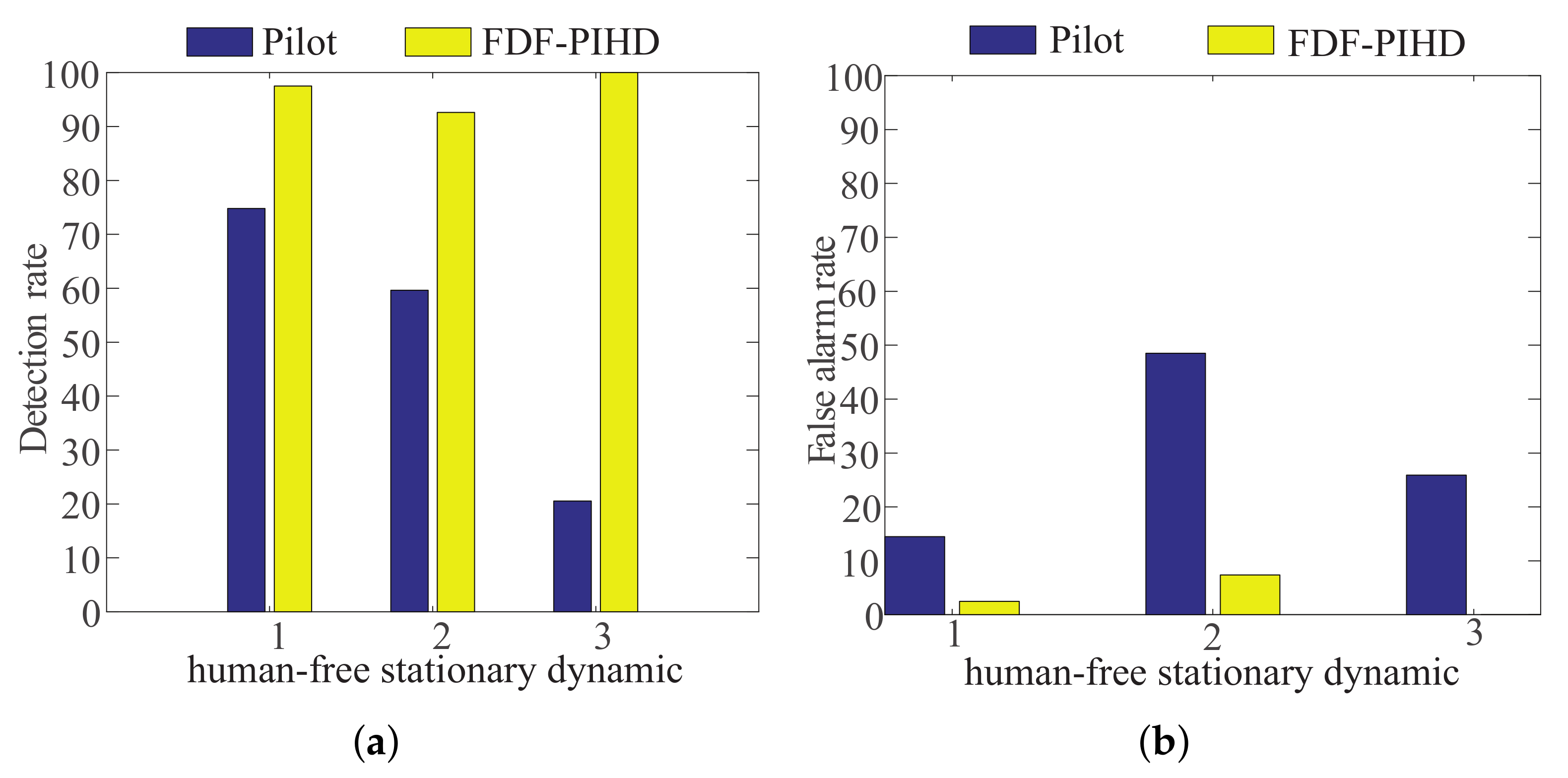
5.3. Detection Rate Comparison between FDF-PIHD and the Pilot
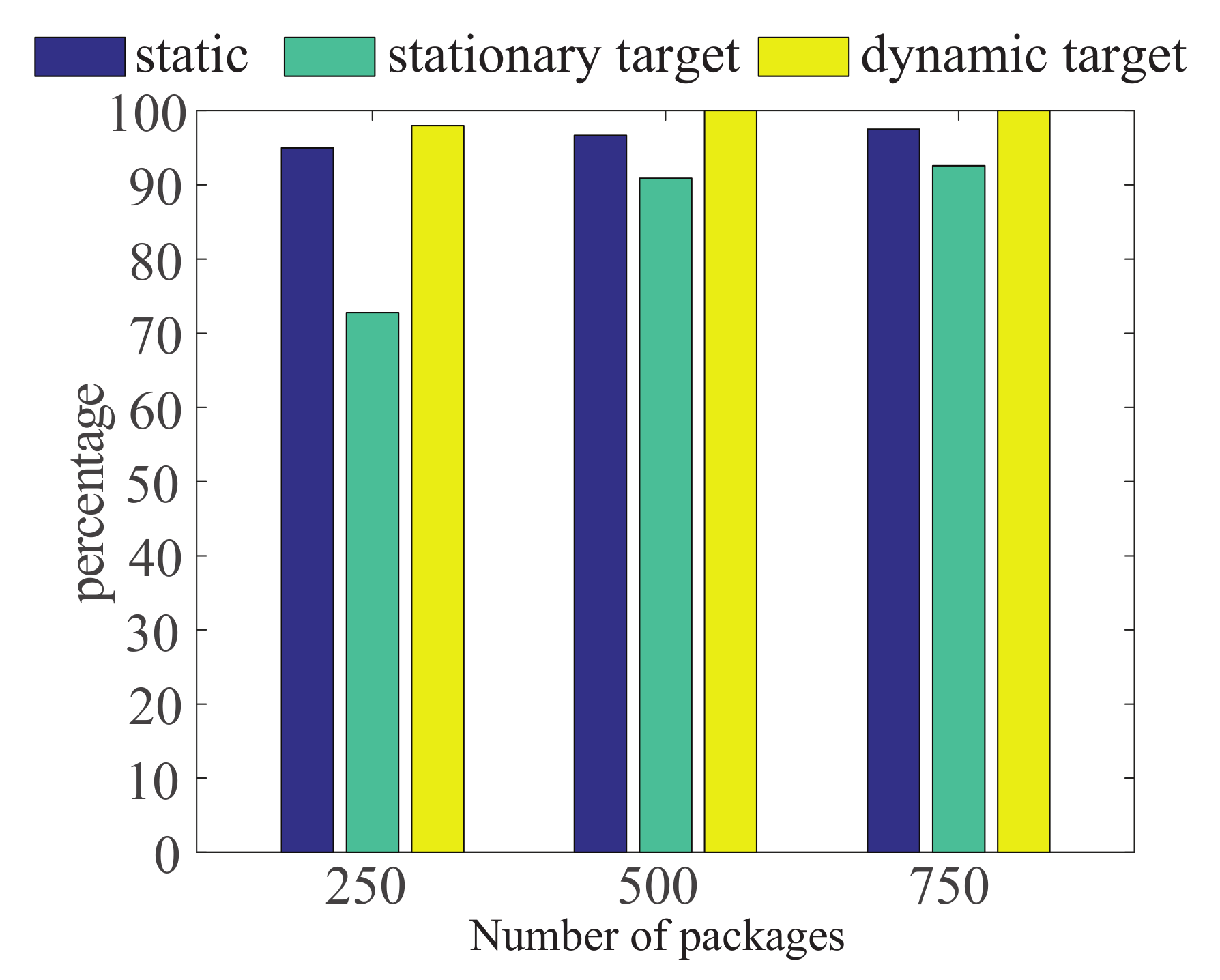
5.4. The Impact of the Number of Packets Used for Fingerprinting on Test Results
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Alemdar, H.; Ersoy, C. Wireless sensor networks for healthcare: A survey. Comput. Netw. 2010, 54, 2688–2710. [Google Scholar] [CrossRef]
- Patwari, N.; Brewer, L.; Tate, Q.; Kaltiokallio, O.; Bocca, M. Breathfinding: A wireless network that monitors and locates breathing in a home. IEEE J. Sel. Top. Signal Process. 2014, 8, 30–42. [Google Scholar] [CrossRef]
- Wang, X.; Yi, P. Security Framework for Wireless Communications in Smart Distribution Grid. IEEE Trans. Smart Grid 2011, 2, 809–818. [Google Scholar] [CrossRef]
- Bisio, I.; Lavagetto, F.; Marchese, M.; Sciarrone, A. Performance Comparison of a Probabilistic Fingerprint-based Indoor Positioning System over Different Smartphones. In Proceedings of the 2013 International Symposium on Performance Evaluation of Computer and Telecommunication Systems, Toronto, ON, Canada, 7–10 July 2013. [Google Scholar]
- Bisio, I.; Cerruti, M.; Lavagetto, F.; Marchese, M.; Pastorino, M.; Randazzo, A.; Sciarrone, A. A Trainingless WiFi Fingerprint Positioning Approach over Mobile Devices. IEEE Antennas Wirel. Propag. Lett. 2014, 13, 832–835. [Google Scholar] [CrossRef]
- Erceg, V.; Greenstein, L.J.; Tjandra, S.Y.; Parkoff, S.R.; Gupta, A.; Kulic, B.; Julius, A.; Jastrzab, R. An empirically based path loss model for wireless channels in suburban environments. IEEE J. Sel. Areas Commun. 2002, 17, 1205–1211. [Google Scholar] [CrossRef]
- Xia, P.; Zhou, S.; Giannakis, G.B. Adaptive MIMO-OFDM based on partial channel state information. IEEE Trans. Signal Process. 2004, 52, 202–213. [Google Scholar] [CrossRef]
- Nee, R.V.; Prasad, R. OFDM for Wireless Multimedia Communications; Artech House: Norwood, MA, USA, 2000. [Google Scholar]
- Yang, Z.; Wu, C.; Liu, Y. Locating in fingerprint space: wireless indoor localization with little human intervention. In Proceedings of the 18th Annual International Conference on Mobile Computing and Networking, Istanbul, Turkey, 22–26 August 2012; pp. 269–280. [Google Scholar]
- Wang, Z.M.; Zhang, L.; Bao, H. Bi-channel Video Fusion Human Invasion Detection Based on Neural Network. Comput. Eng. 2012, 38, 183–187. [Google Scholar]
- Chan, Y.T.; Hang, H.Y.C.; Ching, P.C. Exact and approximate maximum likelihood localization algorithms. IEEE Trans. Veh. Technol. 2006, 55, 10–16. [Google Scholar] [CrossRef]
- Choi, Y.K.; Kim, K.M.; Jung, J.W. Acoustic intruder detection system for home security. IEEE Trans. Consum. Electron. 2005, 51, 130–138. [Google Scholar] [CrossRef]
- Cheng, W.D.; Dong, Y.G. Detection of human body motion features using pyroelectric sensor. Chin. J. Sci. Instrum. 2008, 29, 1020–1023. [Google Scholar]
- Youssef, M.; Mah, M.; Agrawala, A. Challenges: Device-free passive localization for wireless environments. In Proceedings of the 13th Annual ACM International Conference on Mobile Computing and Networking, Montréal, QC, Canada, 9–14 September 2007; pp. 222–229. [Google Scholar]
- Moussa, M.; Youssef, M. Smart devices for smart environments: Device-free passive detection in real environments. In Proceedings of the 2009 IEEE International Conference on Pervasive Computing and Communications, Galveston, TX, USA, 9–13 March 2009; pp. 1–6. [Google Scholar]
- Kaltiokallio, O.; Bocca, M. Real-Time Intrusion Detection and Tracking in Indoor Environment through Distributed RSSI Processing. In Proceedings of the IEEE 17th International Conference on Embedded and Real-Time Computing Systems and Applications, Toyama, Japan, 28–31 August 2011; pp. 61–70. [Google Scholar]
- Mrazovac, B.; Bjelica, M.Z.; Kukolj, D.; Vukosavljev, S.; Todorovic, B.M. System Design for Passive Human Detection Using Principal Components of the Signal Strength Space. In Proceedings of the 2012 IEEE 19th International Conference and Workshops on Engineering of Computer Based Systems, Novi Sad, Serbia, 11–13 April 2012; pp. 164–172. [Google Scholar]
- Zhang, D.; Ma, J.; Chen, Q.; Ni, L.M. An RF-Based System for Tracking Transceiver-Free Objects. In Proceedings of the IEEE 5th Annual International Conference on Pervasive Computing and Communications, White Plains, NY, USA, 19–23 March 2007; pp. 135–144. [Google Scholar]
- Fernandes, R.; Matos, J.N.; Varum, T.; Pinho, P. Wi-Fi intruder detection. In Proceedings of the 2014 IEEE Conference on Wireless Sensors, Subang, Malaysia, 26–28 October 2014; pp. 96–99. [Google Scholar]
- Alfandi, O.; Bochem, A.; Bulert, K.; Hogrefe, D.; Maier, A. Received signal strength indication for movement detection. In Proceedings of the 2015 Eighth International Conference on Mobile Computing and Ubiquitous Networking, Hakodate, Japan, 20–22 January 2015; pp. 82–83. [Google Scholar]
- Han, G.; Klinker, G.J. Dynamic threshold adjustment in a proximity-based location tracking system using reference modules. In Proceedings of the 2015 International Wireless Communications and Mobile Computing Conference, Dubrovnik, Croatia, 24–28 August 2015; pp. 1248–1253. [Google Scholar]
- Younus, M.U.; Li, Y.; Shahbaz, M.; Shafi, R.; He, H. Robust security system for intruder detection and its weight estimation in controlled environment using Wi-Fi. In Proceedings of the 2016 IEEE 2nd International Conference on Computer and Communications, Chengdu, China, 14–17 October 2016; pp. 985–990. [Google Scholar]
- Brauers, C.; Endemann, W.; Kays, R. Augmenting OFDM wireless local networks with motion detection capability. In Proceedings of the 2016 IEEE 6th International Conference on Consumer Electronics-Berlin, Berlin, Germany, 5–7 September 2016; pp. 253–257. [Google Scholar]
- Lv, J.; Yang, W.; Gong, L.; Man, D.; Du, X. Robust WLAN-Based Indoor Fine-Grained Intrusion Detection. In Proceedings of the 2016 IEEE Global Communications Conference, Washington, DC, USA, 4–8 December 2016; pp. 1–6. [Google Scholar]
- Qian, K.; Wu, C.; Yang, Z.; Liu, Y.; Zhou, Z. PADS: Passive detection of moving targets with dynamic speed using PHY layer information. In Proceedings of the IEEE International Conference on Parallel and Distributed Systems, Hsinchu, Taiwan, 16–19 December 2014; pp. 1–8. [Google Scholar]
- Xiao, J.; Wu, K.; Yi, Y.; Wang, L.; Ni, L.M. FIMD: Fine-grained Device-free Motion Detection. In Proceedings of the IEEE International Conference on Parallel and Distributed Systems, Singapore, 17–19 December 2012; pp. 229–235. [Google Scholar]
- Xiao, J.; Wu, K.; Yi, Y.; Wang, L.; Ni, L.M. Pilot: Passive Device-Free Indoor Localization Using Channel State Information. In Proceedings of the 2013 IEEE 33rd International Conference on Distributed Computing Systems, Philadelphia, PA, USA, 8–11 July 2013; pp. 236–245. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Han, C.; Tan, Q.; Sun, L.; Zhu, H.; Guo, J. CSI Frequency Domain Fingerprint-Based Passive Indoor Human Detection. Information 2018, 9, 95. https://doi.org/10.3390/info9040095
Han C, Tan Q, Sun L, Zhu H, Guo J. CSI Frequency Domain Fingerprint-Based Passive Indoor Human Detection. Information. 2018; 9(4):95. https://doi.org/10.3390/info9040095
Chicago/Turabian StyleHan, Chong, Qingqing Tan, Lijuan Sun, Hai Zhu, and Jian Guo. 2018. "CSI Frequency Domain Fingerprint-Based Passive Indoor Human Detection" Information 9, no. 4: 95. https://doi.org/10.3390/info9040095
APA StyleHan, C., Tan, Q., Sun, L., Zhu, H., & Guo, J. (2018). CSI Frequency Domain Fingerprint-Based Passive Indoor Human Detection. Information, 9(4), 95. https://doi.org/10.3390/info9040095




