Challenges and Opportunities of Named Data Networking in Vehicle-To-Everything Communication: A Review
Abstract
:1. Introduction
- dynamic forwarding,
- caching of content,
- security, authenticity and integrity, and
- simulation of wireless NDN communication.
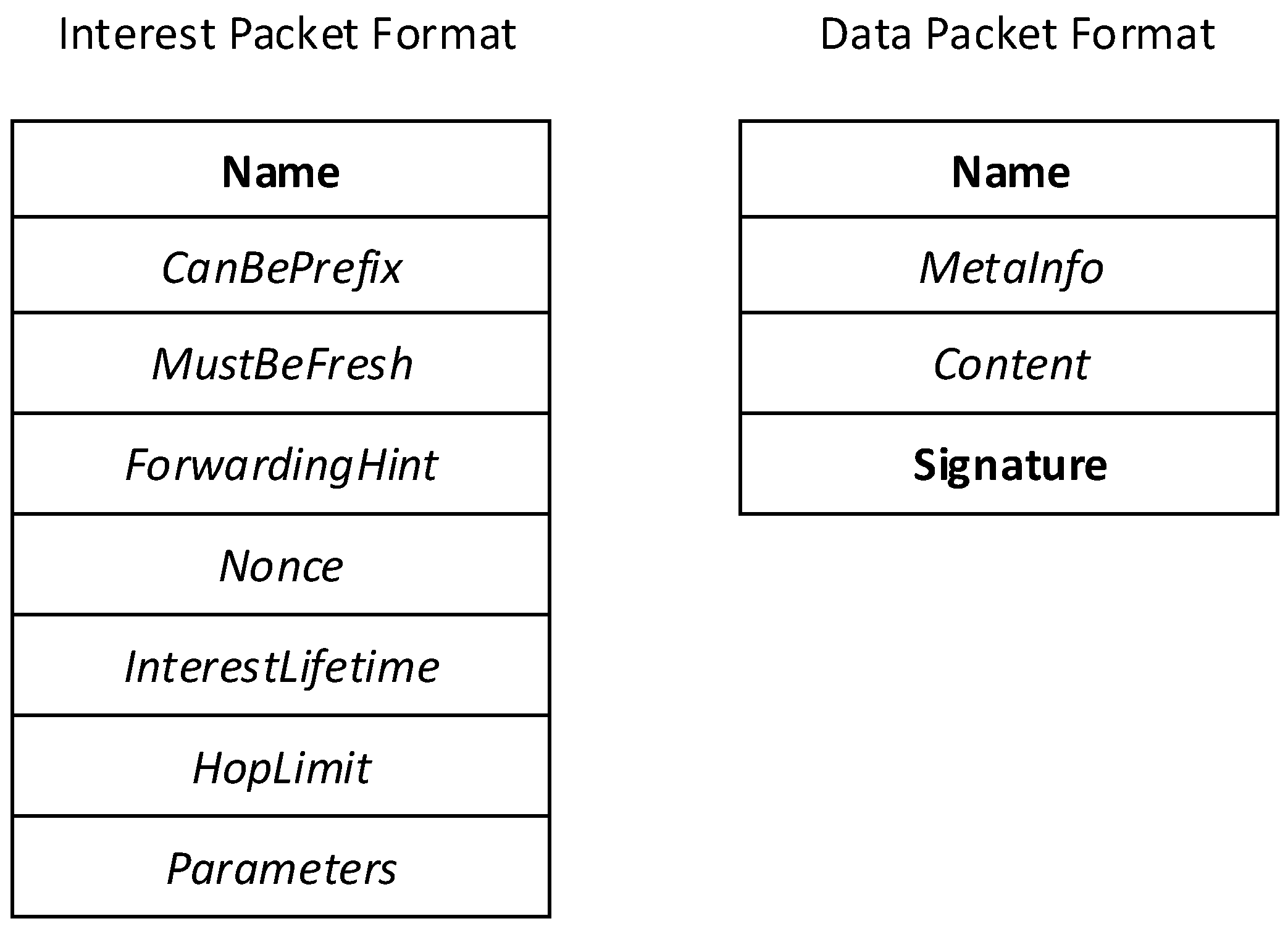
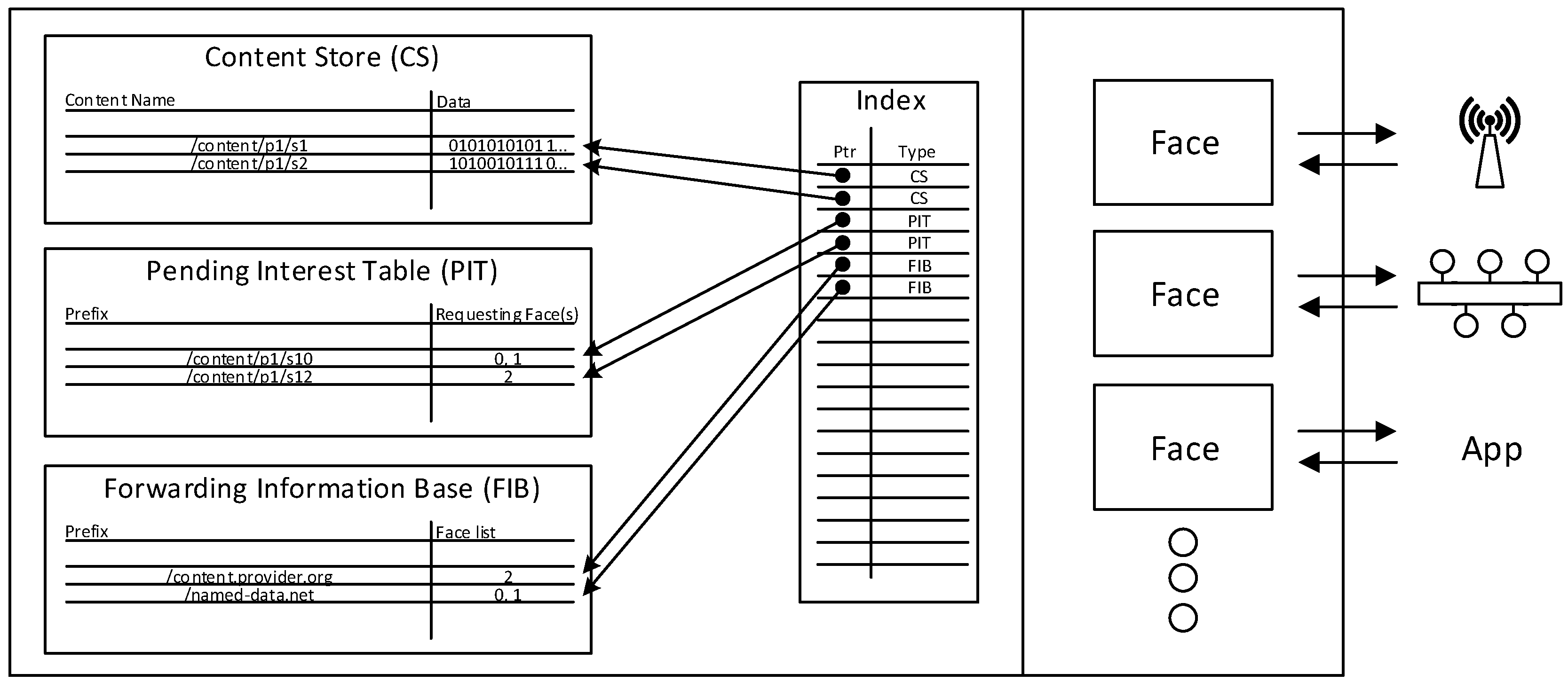
2. NDN Principles
3. NDN Enabled Communication and Transport Research in V2X
3.1. Dynamic Forwarding
3.2. Caching of Content
- Data is twofold
- This means that data can be divided into a category of data which hardly becomes stale (e.g., multimedia data) and data with a short lifetime (e.g., situational data from other vehicles) or a short time span until they are useless.
- Vehicles move
- Therefore, data may become stale in terms of that it is no longer relevant to vehicles in communication range.
3.3. Security, Authenticity and Integrity
- How can the requesting vehicle retrieve consistent information?
3.4. Naming of Content
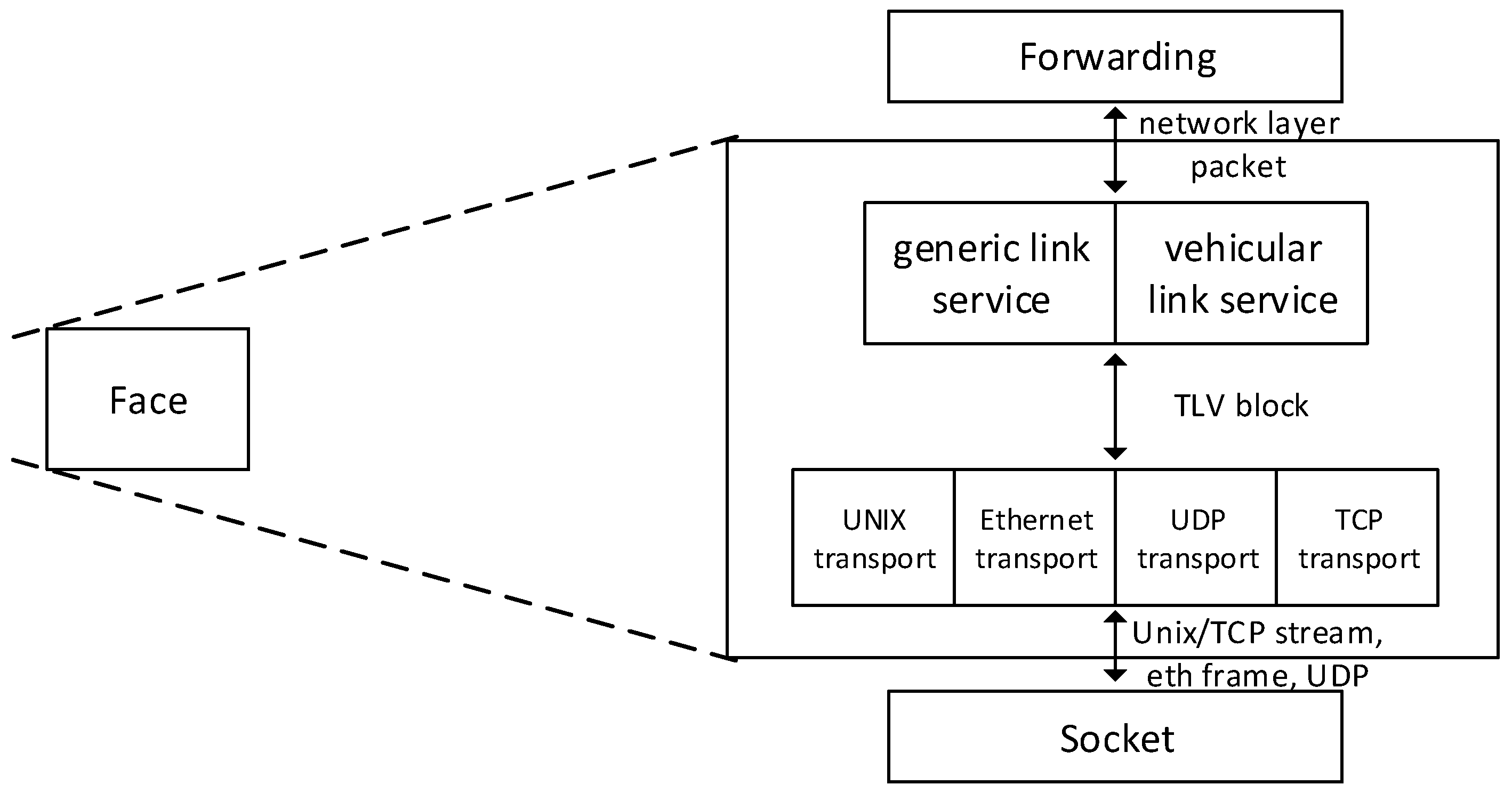
3.5. Wireless Communication in NDN
4. Simulation of NDN Transport in V2X Scenarios
4.1. A Toolchain for NDN Transport Simulation
4.2. Considerations for a V2X Simulation
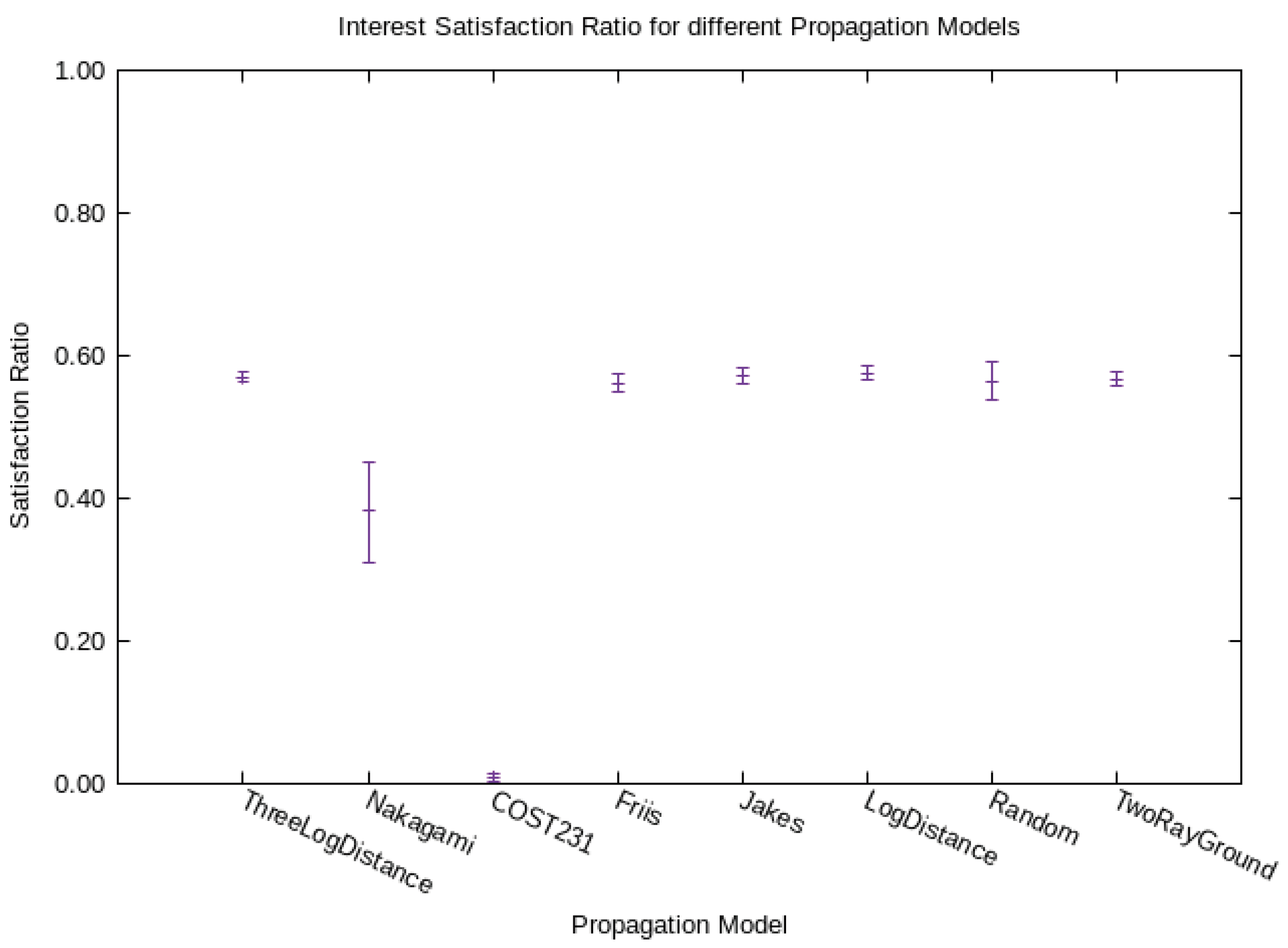
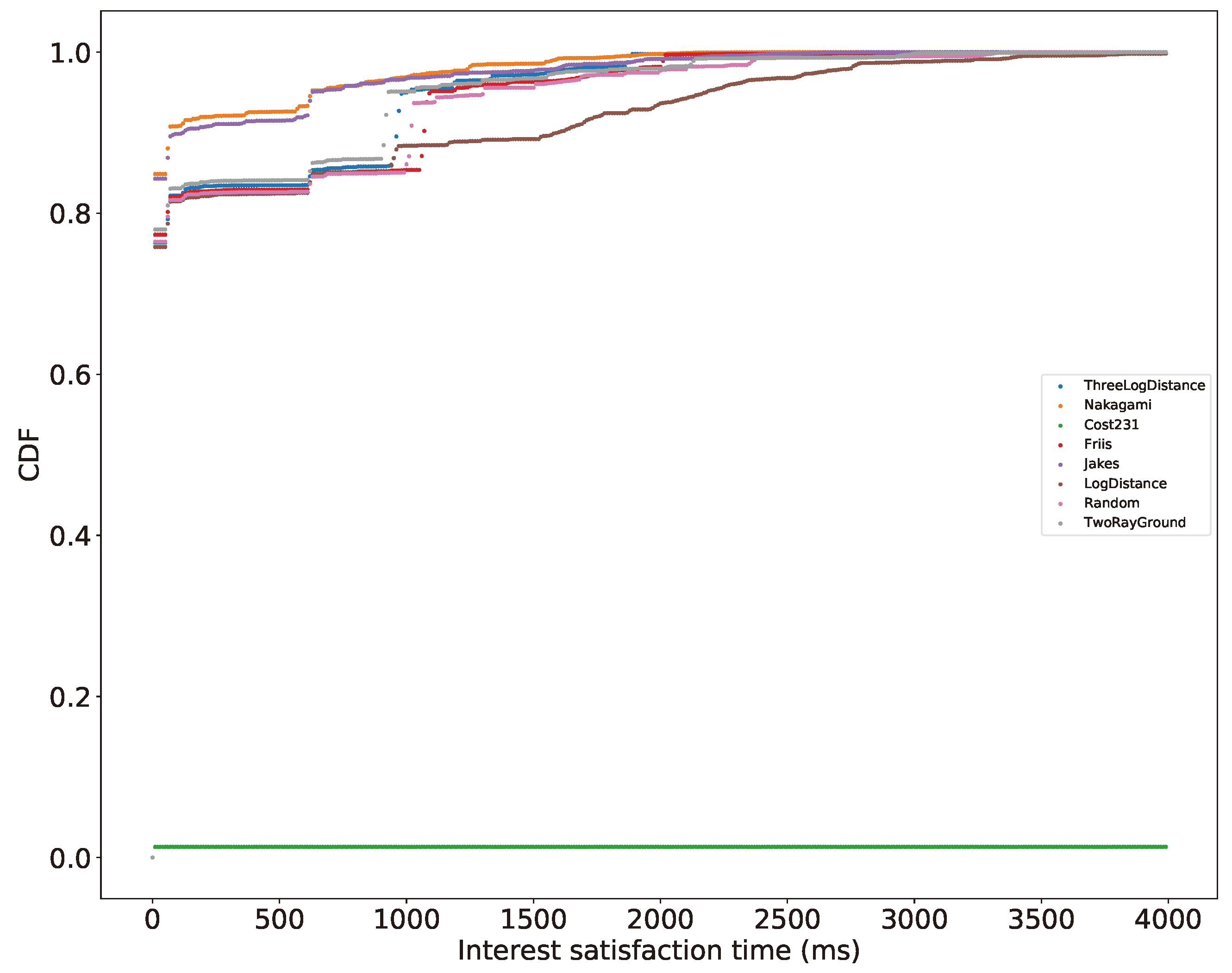
- Friis’ path loss model (free-space, no multi-path propagation, only far field) [61],
- 2-Ray ground reflection path loss model [62],
- Log distance path loss model (inside building, densely populated areas) [63],
- Three log distance path loss model (an enhanced log distance model, for different distances),
- Fixed receiver signal strength models (matrix propagation model, range propagation model, random propagation model),
- COST231 propagation model (applicable to urban areas, extends the Hata model which is based on the Okumura model) [66],
- ITU-R 1411 Line of Sight and Non Line of Sight over roof top propagation models [67],
- Jakes’ propagation model (multi-path fading) [62],
- Kun’s propagation model [68], and
- Okumura’s propagation model [69].
4.3. Simulation Scenarios for V2X Communication
- S1
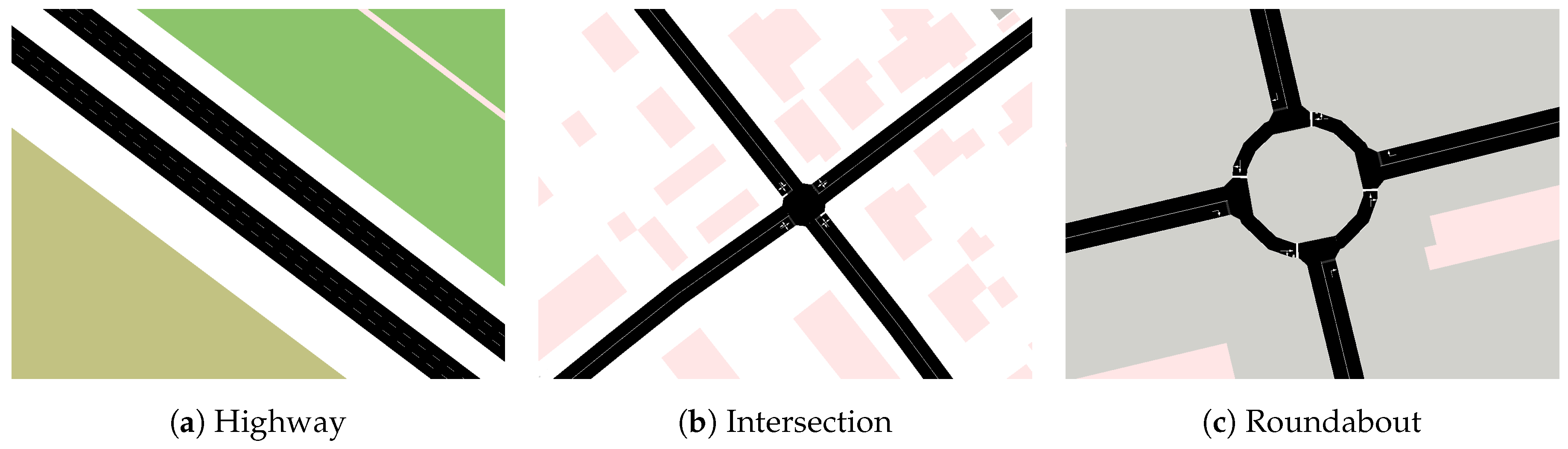
- Several cars driving alongside each other on a highway with approaching priority vehicles.This is a one-way traffic high-speed use case. The challenging networking aspect of this scenario is that on car has to switch lanes such that the priority vehicle is able to overtake. Information from the priority vehicle has to travel and be processed in driving direction faster than the vehicle is driving, and actions have to be taken until the priority vehicle reaches the two cars’ geo-location. Additionally, measures have to be taken that assure the authenticity of the priority vehicle’s messages.
- S2
- Turning left at a traffic light controlled intersection in an urban environment (buildings near the road) at a rainy day.This scenario is especially challenging to simulate realistically. Here, the applied channel model is essential for a realistic simulation, as buildings near the road cause reflections of the electromagnetic waves and wet weather conditions alter the electro-magnetic properties of the various surfaces.
- S3
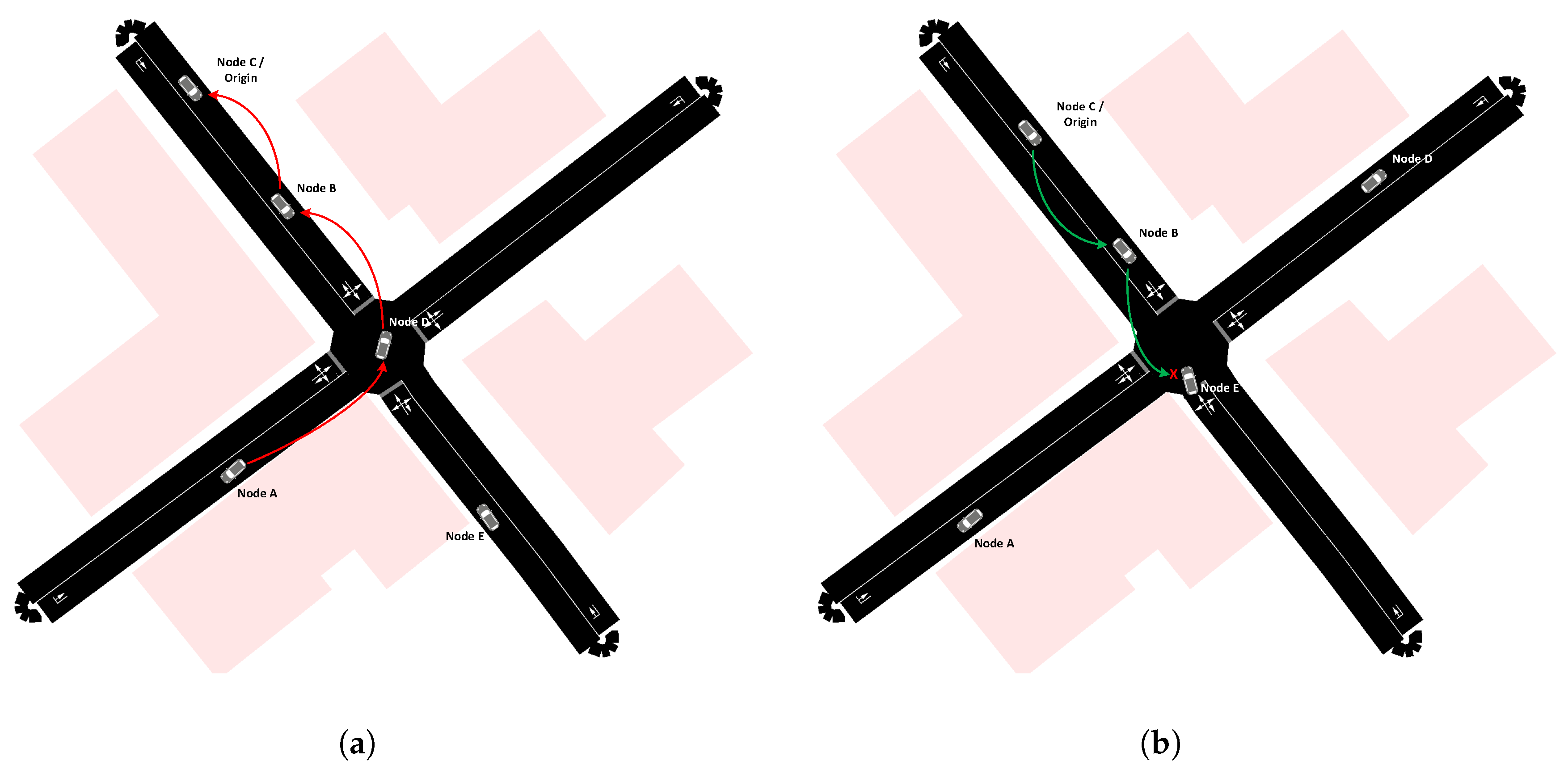
- Turning left at an unmanaged intersection. A rear-end-collision is blocking the turn-left lane five car lengths before the intersection.This scenario covers an intersection where the lane which should be used in normal circumstances is blocked by a traffic incident. However, there is enough space for avoiding the accident and turning left. As in S1, the networking challenge is message authenticity as well as timeliness.
- S4
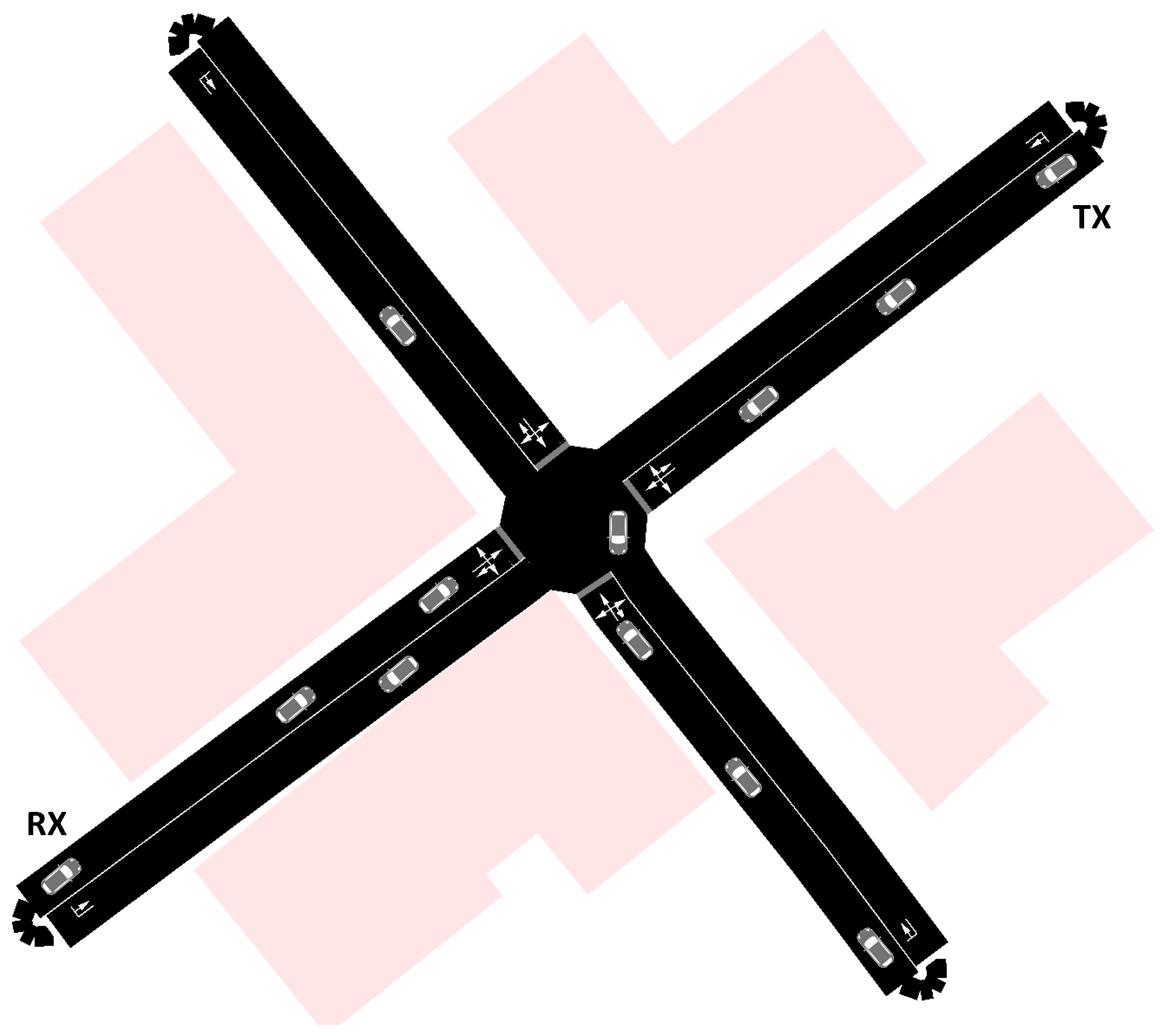
- Taking a roundabout exit with crossing pedestrians at this exit.While recent literature covers intersections, we also propose to simulate other bottlenecks such as roundabouts. From a communication point of view, this scenario is interesting, as following cars can be warned of potentially crossing pedestrians that are in general not part of the communication network.
5. Conclusions
- How to deal with unsolicited data in V2X context?
- How to incorporate vehicular mobility (vehicles entering/leaving communication range) in the forwarding process?
- How to make use of the NDN ForwardingHint?
- How to prevent broadcast storms originating in Interest flooding?
- What should a caching strategy for multiple types of data look like?
- How to combine geo-location and popularity information in content caching?
- How to deal with caching, encrypted content, and the lack of computational resources?
- How to deal with content poisoning attacks without verification at intermediate routers?
- How to detect and deal with byzantine vehicles?
- How well do models of the physical channel map the uses cases we want to simulate?
Author Contributions
Funding
Conflicts of Interest
References
- Ress, C.; Wiecker, M. Evaluating the Potential of V2X Communication for Road Safety and Efficiency. ATZ Worldw. 2016, 118, 16–21. [Google Scholar] [CrossRef]
- Le, L.; Festag, A.; Baldessari, R.; Zhang, W. V2X Communication and Intersection Safety. In Advanced Microsystems for Automotive Applications 2009: Smart Systems for Safety, Sustainability, and Comfort; Meyer, G., Valldorf, J., Gessner, W., Eds.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 97–107. [Google Scholar]
- Grylls, B. Qualcomm and Partners Showcase C-V2X Direct Communications Interoperability to Improve Road Safety. Available online: http://www.newelectronics.co.uk/electronics-news/c/173305/ (accessed on 15 May 2018).
- Ahlgren, B.; Dannewitz, C.; Imbrenda, C.; Kutscher, D.; Ohlman, B. A Survey of Information-Centric Networking. IEEE Commun. Mag. 2012, 50, 26–36. [Google Scholar] [CrossRef]
- Xylomenos, G.; Ververidis, C.N.; Siris, V.A.; Fotiou, N.; Tsilopoulos, C.; Vasilakos, X.; Katsaros, K.V.; Polyzos, G.C. A Survey of Information-Centric Networking Research. IEEE Commun. Surv. Tutor. 2014, 16, 1024–1049. [Google Scholar] [CrossRef] [Green Version]
- Zhang, L.; Afanasyev, A.; Burke, J.; Jacobson, V.; Claffy, K.; Crowley, P.; Papadopoulos, C.; Wang, L.; Zhang, B. Named Data Networking. ACM SIGCOMM Comput. Commun. Rev. 2014, 44, 66–73. [Google Scholar] [CrossRef]
- Chen, M.; Mau, D.O.; Zhang, Y.; Taleb, T.; Leung, V.C. VENDNET: VEhicular Named Data NETwork. Veh. Commun. 2014, 1, 208–213. [Google Scholar] [CrossRef]
- NDN Packet Format Version 0.3. Available online: http://named-data.net/doc/NDN-packet-spec/current/intro.html (accessed on 27 September 2018).
- Rossini, G.; Rossi, D. Coupling Caching and Forwarding: Benefits, Analysis, and Implementation. In Proceedings of the 1st International Conference on Information-Centric Networking, Paris, France, 24–26 September 2014; ACM: New York, NY, USA, 2014; pp. 127–136. [Google Scholar] [CrossRef]
- Chiocchetti, R.; Perino, D.; Carofiglio, G.; Rossi, D.; Rossini, G. INFORM: A Dynamic Interest Forwarding Mechanism for ICN. In Proceedings of the 3rd ACM SIGCOMM Workshop on ICN, Hong Kong, China, 12 August 2013; pp. 9–14. [Google Scholar] [CrossRef]
- Carofiglio, G.; Gallo, M.; Muscariello, L.; Papalini, M.; Wang, S. Optimal Multipath Congestion Control and Request Forwarding in Information-Centric Networks. In Proceedings of the 21st IEEE International Conference on Network Protocols (ICNP), Göttingen, Germany, 7–10 October 2013. [Google Scholar]
- Posch, D.; Rainer, B.; Hellwagner, H. SAF: Stochastic Adaptive Forwarding in Named Data Networking. IEEE/ACM Trans. Netw. 2017, 25, 1089–1102. [Google Scholar] [CrossRef] [Green Version]
- Yaqub, M.A.; Ahmed, S.H.; Bouk, S.H.; Kim, D. Interest Forwarding in Vehicular Information Centric Networks: A Survey. In Proceedings of the 31st Annual ACM Symposium on Applied Computing (SAC ’16), Pisa, Italy, 4–8 April 2016; ACM: New York, NY, USA, 2016; pp. 724–729. [Google Scholar] [CrossRef]
- Grassi, G.; Pesavento, D.; Pau, G.; Vuyyuru, R.; Wakikawa, R.; Zhang, L. VANET via Named Data Networking. In Proceedings of the 2014 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Toronto, ON, Canada, 27 April–2 May 2014; pp. 410–415. [Google Scholar] [CrossRef]
- Grassi, G.; Pesavento, D.; Pau, G.; Zhang, L.; Fdida, S. Navigo: Interest forwarding by geolocations in vehicular Named Data Networking. In Proceedings of the 2015 IEEE 16th International Symposium on a World of Wireless, Mobile and Multimedia Networks (WoWMoM), Boston, MA, USA, 14–17 June 2015; pp. 1–10. [Google Scholar] [CrossRef]
- Liu, X.; João Nicolau, M.; Costa, A.; Macedo, J.; Santos, A. A Geographic Opportunistic Forwarding Strategy for Vehicular Named Data Networking. In Intelligent Distributed Computing IX; Novais, P., Camacho, D., Analide, C., El Fallah Seghrouchni, A., Badica, C., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 509–521. [Google Scholar]
- Ahmed, S.H.; Bouk, S.H.; Yaqub, M.A.; Kim, D.; Song, H.; Lloret, J. CODIE: Controlled Data and Interest Evaluation in Vehicular Named Data Networks. IEEE Trans. Veh. Technol. 2016, 65, 3954–3963. [Google Scholar] [CrossRef]
- Boukerche, A.; Coutinho, R.W.L.; Yu, X. LISIC: A Link Stability-Based Protocol for Vehicular Information-Centric Networks. In Proceedings of the 2017 IEEE 14th International Conference on Mobile Ad Hoc and Sensor Systems (MASS), Orlando, FL, USA, 22–25 October 2017; pp. 233–240. [Google Scholar] [CrossRef]
- Kuai, M.; Hong, X.; Yu, Q. Density-Aware Delay-Tolerant Interest Forwarding in Vehicular Named Data Networking. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Kalogeiton, E.; Kolonko, T.; Braun, T. A multihop and multipath routing protocol using NDN for VANETs. In Proceedings of the 2017 16th Annual Mediterranean Ad Hoc Networking Workshop (Med-Hoc-Net), Budva, Montenegro, 28–30 June 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Perkins, C.E.; Royer, E.M. Ad-hoc on-demand distance vector routing. In Proceedings of the 2nd IEEE Workshop on Mobile Computing Systems and Applications (WMCSA ’99), 1999. New Orleans, LA, USA, 25–26 February 1999; pp. 90–100. [Google Scholar] [CrossRef]
- Johnson, D.; Hu, Y.; Maltz, D. The Dynamic Source Routing Protocol (DSR) for Mobile Ad Hoc Networks for IPv4. RFC 4728. 2007. Available online: https://www.rfc-editor.org/info/rfc4728 (accessed on 15 July 2018).[Green Version]
- Zhang, M.; Luo, H.; Zhang, H. A Survey of Caching Mechanisms in Information-Centric Networking. IEEE Commun. Surv. Tutor. 2015, 17, 1473–1499. [Google Scholar] [CrossRef]
- Abani, N.; Braun, T.; Gerla, M. Proactive Caching with Mobility Prediction Under Uncertainty in Information-centric Networks. In Proceedings of the 4th ACM Conference on Information-Centric Networking (ICN ’17), Berlin, Germany, 26–28 September 2017; ACM: New York, NY, USA, 2017; pp. 88–97. [Google Scholar] [CrossRef]
- Mauri, G.; Gerla, M.; Bruno, F.; Cesana, M.; Verticale, G. Optimal Content Prefetching in NDN Vehicle-to-Infrastructure Scenario. IEEE Trans. Veh. Technol. 2017, 66, 2513–2525. [Google Scholar] [CrossRef]
- Zhao, W.; Qin, Y.; Gao, D.; Foh, C.H.; Chao, H. An Efficient Cache Strategy in Information Centric Networking Vehicle-to-Vehicle Scenario. IEEE Access 2017, 5, 12657–12667. [Google Scholar] [CrossRef]
- Modesto, F.M.; Boukerche, A. An analysis of caching in information-centric vehicular networks. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, S.; Mizero, F. A Survey on Security in Named Data Networking. arXiv, 2015; arXiv:1512.04127. [Google Scholar]
- Posch, D.; Hellwagner, H.; Schartner, P. On-demand video streaming based on dynamic adaptive encrypted content chunks. In Proceedings of the 4th 2013 21st IEEE International Conference on Network Protocols (ICNP), Goettingen, Germany, 7–10 October 2013; pp. 1–6. [Google Scholar] [CrossRef]
- Nguyen, T.; Marchal, X.; Doyen, G.; Cholez, T.; Cogranne, R. Content Poisoning in Named Data Networking: Comprehensive characterization of real deployment. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; pp. 72–80. [Google Scholar] [CrossRef]
- Kim, D.; Bi, J.; Vasilakos, A.V.; Yeom, I. Security of Cached Content in NDN. IEEE Trans. Inf. Forensics Secur. 2017, 12, 2933–2944. [Google Scholar] [CrossRef]
- Ballani, H.; Francis, P.; Zhang, X. A Study of Prefix Hijacking and Interception in the Internet. In Proceedings of the 2007 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications (SIGCOMM ’07), Kyoto, Japan, 27–31 August 2007; ACM: New York, NY, USA, 2007; pp. 265–276. [Google Scholar] [CrossRef]
- Compagno, A.; Zeng, X.; Muscariello, L.; Carofiglio, G.; Augé, J. Secure Producer Mobility in Information-centric Network. In Proceedings of the 4th ACM Conference on Information-Centric Networking (ICN ’17), Berlin, Germany, 26–28 September 2017; ACM: New York, NY, USA, 2017; pp. 163–169. [Google Scholar] [CrossRef]
- Zhang, Y.; Zhang, H.; Zhang, L. Kite: A Mobility Support Scheme for NDN. In Proceedings of the 1st ACM Conference on Information-Centric Networking (ACM-ICN ’14), Paris, France, 24–26 September 2014; ACM: New York, NY, USA, 2014; pp. 179–180. [Google Scholar] [CrossRef]
- Karnouskos, S.; Kerschbaum, F. Privacy and Integrity Considerations in Hyperconnected Autonomous Vehicles. Proc. IEEE 2018, 106, 160–170. [Google Scholar] [CrossRef]
- Castro, M.; Liskov, B. Practical Byzantine Fault Tolerance. In Proceedings of the Third Symposium on Operating Systems Design and Implementation (OSDI ’99), New Orleans, LA, USA, 22–25 February 1999; USENIX Association: Berkeley, CA, USA, 1999; pp. 173–186. [Google Scholar]
- Abd-El-Malek, M.; Ganger, G.R.; Goodson, G.R.; Reiter, M.K.; Wylie, J.J. Fault-scalable Byzantine Fault-tolerant Services. SIGOPS Oper. Syst. Rev. 2005, 39, 59–74. [Google Scholar] [CrossRef]
- Cowling, J.; Myers, D.; Liskov, B.; Rodrigues, R.; Shrira, L. HQ Replication: A Hybrid Quorum Protocol for Byzantine Fault Tolerance. In Proceedings of the 7th Symposium on Operating Systems Design and Implementation (OSDI ’06), Seattle, WA, USA, 6–8 November 2006; USENIX Association: Berkeley, CA, USA, 2006; pp. 177–190. [Google Scholar]
- Kotla, R.; Alvisi, L.; Dahlin, M.; Clement, A.; Wong, E. Zyzzyva: Speculative Byzantine Fault Tolerance. SIGOPS Oper. Syst. Rev. 2007, 41, 45–58. [Google Scholar] [CrossRef]
- Clement, A.; Wong, E.; Alvisi, L.; Dahlin, M.; Marchetti, M. Making Byzantine Fault Tolerant Systems Tolerate Byzantine Faults. In Proceedings of the 6th USENIX Symposium on Networked Systems Design and Implementation (NSDI’09), San Jose, CA, USA, 8–10 May 2009; USENIX Association: Berkeley, CA, USA, 2009; pp. 153–168. [Google Scholar]
- Drira, W.; Filali, F. NDN-Q: An NDN query mechanism for efficient V2X data collection. In Proceedings of the 2014 Eleventh Annual IEEE International Conference on Sensing, Communication, and Networking Workshops (SECON Workshops), Singapore, 30 June–3 July 2014; pp. 13–18. [Google Scholar] [CrossRef]
- Wang, L.; Wakikawa, R.; Kuntz, R.; Vuyyuru, R.; Zhang, L. Data naming in Vehicle-to-Vehicle communications. In Proceedings of the 2012 Proceedings IEEE INFOCOM Workshops, Orlando, FL, USA, 25–30 March 2012; pp. 328–333. [Google Scholar] [CrossRef]
- Zhu, Z.; Loo, J.; Chen, Y.; Chai, K.K.; Zhang, T. Recent advances in connected vehicles via information-centric networking. In Proceedings of the IET International Conference on Intelligent and Connected Vehicles (ICV 2016), Chongqing, China, 22–23 September 2016; pp. 1–8. [Google Scholar] [CrossRef]
- Tarroumi, M.; Jabri, I. EVNDN: Enhanced vehicular named data networking. In Proceedings of the 2017 International Symposium on Networks, Computers and Communications (ISNCC), Marrakech, Morocco, 16–18 May 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Molinaro, A. CRoWN: Content-Centric Networking in Vehicular Ad Hoc Networks. IEEE Commun. Lett. 2012, 16, 1380–1383. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Molinaro, A. Content-centric Networking: Is That a Solution for Upcoming Vehicular Networks? In Proceedings of the Ninth ACM International Workshop on Vehicular Inter-networking, Systems, and Applications (VANET ’12), Lake District, UK, 25 June 2012; ACM: New York, NY, USA, 2012; pp. 99–102. [Google Scholar] [CrossRef]
- IEEE Standard for Information technology—Local and metropolitan area networks—Specific requirements—Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments. In IEEE Std 802.11p-2010 (Amendment to IEEE Std 802.11-2007 as Amended by IEEE Std 802.11k-2008, IEEE Std 802.11r-2008, IEEE Std 802.11y-2008, IEEE Std 802.11n-2009, and IEEE Std 802.11w-2009); IEEE: Washington, DC, USA, 2010; pp. 1–51. [CrossRef]
- Bazzi, A.; Masini, B.M.; Zanella, A.; Castro, C.D.; Raffaelli, C.; Andrisano, O. Cellular aided vehicular named data networking. In Proceedings of the 2014 International Conference on Connected Vehicles and Expo (ICCVE), Vienna, Austria, 3–7 November 2014; pp. 747–752. [Google Scholar] [CrossRef]
- Baccelli, E.; Mehlis, C.; Hahm, O.; Schmidt, T.C.; Wählisch, M. Information Centric Networking in the IoT: Experiments with NDN in the Wild. In Proceedings of the 1st ACM Conference on Information-Centric Networking (ACM-ICN ’14), Paris, France, 24–26 September 2014; ACM: New York, NY, USA, 2014; pp. 77–86. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Quevedo, J.; Corujo, D.; Molinaro, A.; Iera, A.; Aguiar, R.L.; Vasilakos, A.V. Information-centric networking for the internet of things: challenges and opportunities. IEEE Netw. 2016, 30, 92–100. [Google Scholar] [CrossRef]
- Dinh, N.; Kim, Y. Potential of information-centric wireless sensor and actor networking. In Proceedings of the 2013 International Conference on Computing, Management and Telecommunications (ComManTel), Ho Chi Minh City, Vietnam, 21–24 January 2013; pp. 163–168. [Google Scholar] [CrossRef]
- Rainer, B.; Posch, D.; Hellwagner, H. Investigating the Performance of Pull-Based Dynamic Adaptive Streaming in NDN. IEEE J. Sel. Areas Commun. 2016, 34, 2130–2140. [Google Scholar] [CrossRef]
- Xu, C.; Quan, W.; Vasilakos, A.V.; Zhang, H.; Muntean, G.M. Information-centric Cost-efficient Optimization for Multimedia Content Delivery in Mobile Vehicular Networks. Comput. Commun. 2017, 99, 93–106. [Google Scholar] [CrossRef]
- Dinh, N.T.; Kim, Y. Information-centric Dissemination Protocol for Safety Information in Vehicular Ad-hoc Networks. Wirel. Netw. 2017, 23, 1359–1371. [Google Scholar] [CrossRef]
- Yan, Z.; Zeadally, S.; Park, Y. A Novel Vehicular Information Network Architecture Based on Named Data Networking (NDN). IEEE Internet Things J. 2014, 1, 525–532. [Google Scholar] [CrossRef]
- Mastorakis, S.; Afanasyev, A.; Zhang, L. On the Evolution of ndnSIM: an Open-Source Simulator for NDN Experimentation. ACM Comput. Commun. Rev. 2017, 44, 19–33. [Google Scholar] [CrossRef]
- ns-3. Available online: http://www.nsnam.org (accessed on 27 September 2018).
- Krajzewicz, D.; Erdmann, J.; Behrisch, M.; Bieker, L. Recent Development and Applications of SUMO—Simulation of Urban MObility. Int. J. Adv. Syst. Meas. 2012, 5, 128–138. [Google Scholar]
- Angeles, W.; Borin, V.P.; Munaretto, A.; Fonseca, M. The Impact of Propagation Models in the Performance of Ad Hoc Routing Protocols for Urban VANET. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Eltahir, I.K. The Impact of Different Radio Propagation Models for Mobile Ad hoc NETworks (MANET) in Urban Area Environment. In Proceedings of the 2nd International Conference on Wireless Broadband and Ultra Wideband Communications (AusWireless 2007), Sydney, Australia, 27–30 August 2007; p. 30. [Google Scholar] [CrossRef]
- Friis, H.T. A Note on a Simple Transmission Formula. Proc. IRE 1946, 34, 254–256. [Google Scholar] [CrossRef]
- Jakes, W.C.; Cox, D.C. (Eds.) Microwave Mobile Communications; Wiley-IEEE Press: Hoboken, NJ, USA, 1994. [Google Scholar]
- Goldhirsh, J.; Vogel, W.J. Handbook of Propagation Effects for Vehicular and Personal Mobile Satellite Systems Overview of Experimental and Modeling Results; NASA Reference Publication: Washington, DC, USA, 1998. [Google Scholar]
- Nakagami, M. The m-Distribution—A General Formula of Intensity Distribution of Rapid Fading. In Statistical Methods in Radio Wave Propagation; Hoffman, W., Ed.; RAND Corporation: Pergamon, Turkey, 1960; pp. 3–36. [Google Scholar]
- Molisch, A.; Tufvesson, F.; Karedal, J.; Mecklenbrauker, C. A Survey on Vehicle-to-vehicle Propagation Channels. Wirel. Commun. 2009, 16, 12–22. [Google Scholar] [CrossRef]
- European Commission. COST Action 231: Digital Mobile Radio towards Future Generation Systems, Final Report; European Commission: Brussels, Belgium, 1980. [Google Scholar]
- ITU-R. Propagation Data and Prediction Methods for the Planning of Short-Range Outdoor Radiocommunication Systems and Radio local Area Networks in the Frequency Range 300 MHz to 100 GHz; ITU-R: Geneva, Switzerland, 2012. [Google Scholar]
- Kun, S.; Ping, W.; Yingze, L. Path loss models for suburban scenario at 2.3 GHz, 2.6 GHz and 3.5 GHz. In Proceedings of the 2008 8th International Symposium on Antennas, Propagation and EM Theory, Kunming, China, 2–5 November 2008; pp. 438–441. [Google Scholar] [CrossRef]
- Medeisis, A.; Kajackas, A. On the use of the universal Okumura-Hata propagation prediction model in rural areas. In Proceedings of the VTC2000-Spring, 2000 IEEE 51st Vehicular Technology Conference Proceedings (Cat. No. 00CH37026), Tokyo, Japan, 15–18 May 2000; Volume 3, pp. 1815–1818. [Google Scholar] [CrossRef]
- Valenzuela, R. A ray tracing approach to predicting indoor wireless transmission. In Proceedings of the IEEE 43rd Vehicular Technology Conference, Secaucus, NJ, USA, 18–20 May 1993; pp. 214–218. [Google Scholar] [CrossRef]
- Yun, Z.; Iskander, M.F. Ray Tracing for Radio Propagation Modeling: Principles and Applications. IEEE Access 2015, 3, 1089–1100. [Google Scholar] [CrossRef] [Green Version]
- IEEE Guide for Wireless Access in Vehicular Environments (WAVE)—Architecture; IEEE: Piscataway, NJ, USA, 2014; pp. 1–78. [CrossRef]
- Li, Y.J. An Overview of the DSRC/WAVE Technology. In Quality, Reliability, Security and Robustness in Heterogeneous Networks; Zhang, X., Qiao, D., Eds.; Springer: Berlin/Heidelberg, Germnay, 2012; pp. 544–558. [Google Scholar]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Rainer, B.; Petscharnig, S. Challenges and Opportunities of Named Data Networking in Vehicle-To-Everything Communication: A Review. Information 2018, 9, 264. https://doi.org/10.3390/info9110264
Rainer B, Petscharnig S. Challenges and Opportunities of Named Data Networking in Vehicle-To-Everything Communication: A Review. Information. 2018; 9(11):264. https://doi.org/10.3390/info9110264
Chicago/Turabian StyleRainer, Benjamin, and Stefan Petscharnig. 2018. "Challenges and Opportunities of Named Data Networking in Vehicle-To-Everything Communication: A Review" Information 9, no. 11: 264. https://doi.org/10.3390/info9110264




