A Backward Unlinkable Secret Handshake Scheme with Revocation Support in the Standard Model
Abstract
:1. Introduction
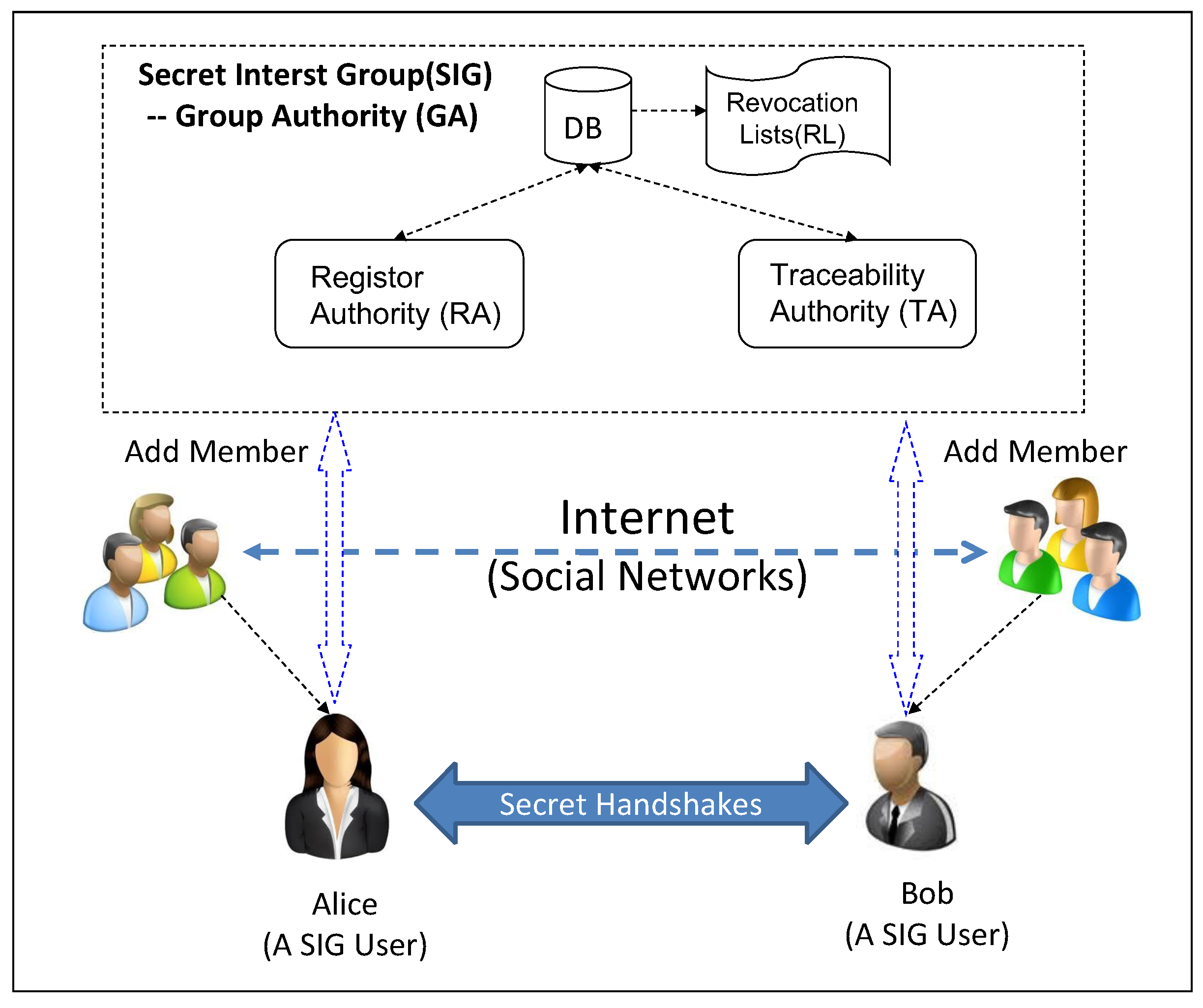
2. Preliminaries
2.1. Bilinear Pairings of Composite Order
- Bilinear: For all , s.t., g is a generator of and , .
- Non-degeneracy: , i.e., if g generates , then generates with order N.
- Computability: There exists an efficient algorithm for computing .
2.2. Complexity Assumptions
2.3. Secret Handshakes: Definition and Security Properties
- Setup: The Setup algorithm selects a security parameter κ to generate the public parameters params common to all subsequently generated groups.
- CreateGroup: CreateGroup is a key generation algorithm executed by the GA to establish a group G. It takes params as input and outputs group public key and private key .
- AddUser: AddUser is a two-party protocol run by the user and the GA. The GA plays the role of the CA for the group, which issues the credentials for a legitimate user of the group. After verifying the users’ real identity, the GA will issue credential for to each user after the protocol.
- Handshake: Handshake is a two-party authenticate protocol executed by a pair of anonymous users (A, B), where (A, B) are possible users who may belong to different groups. This protocol takes as input the anonymous user’ secrets () and other public information, where is a group public key of the target group for the participator’s authentication policy. The output of the protocol for either party is either “1” or “0”. If the output is “1”, this means that the secret handshake protocol is successful, and a session key K will be produced that can be used for subsequent secure communication between the two users. Otherwise, the handshake protocol is a failure, and the two users cannot distinguish the other’s group information.
- TraceUser: TraceUser is a polynomial time algorithm that is executed by the GA. The protocol outputs the identity of user U, whilst a transcript of the secret handshake involved with user U is submitted.
- RemoveUser: RemoveUser is a polynomial time algorithm that is authorized by the GA. It takes its current revocation list (RL) and U’s revocation tokens as the inputs, whilst outputting an up-to-date RL that includes new revocation records.
- (1)
- Completeness: It requires that the SH protocol always outputs “1” when any interactive participators and honestly execute the Handshake protocol and satisfy the authentication policy of the counter-party, respectively.
- (2)
- Impersonator resistance: An adversary who attempts to impersonate a legitimate user of one group cannot succeed with a non-negligible probability. In other words, any adversary not satisfying the authentication policies cannot accomplish a successful secret handshake.Formally, the property is defined in the following game between an adversary and a challenger :
- Init: The adversary first sets . Then, simulates Setup, CreateGroup and AddMember and sends the group public keys and up-to-date RL to .
- Queries: can make the following queries, such that the responses will be simulated by .
- –
- Corruption queries: The corruption list is initialized as ∅. The adversary can query CreateGroup and AddMember for the secret information of some groups and members, except for . will respond to the simulated information and update the corruption list .
- –
- Handshake queries: The adversary can make queries on the Handshake protocol with the group members. The transcripts of the queried members can be generated by . During a handshake, can query the hash functions used in the Handshake protocol. In particular, can request a non-interactive proof of knowledge of a random message for any member at the current interval.
- Challenge: The challenger acts as the group member of and executes the handshake protocol with the adversary . attempts to convince that is a legitimate member of the group .
- Output: If the adversary on half of a member i in the group succeeds in executing Handshake with , the output of the game is “1”. Otherwise, the output is “0”. Note that it is required that never queried any secret information with respect to the member i of the group , i.e., .
Let ; we say that SHS satisfies the impersonator resistance if the function is negligible for any polynomially-bounded adversary. - (3)
- Detector resistance: An adversary will not succeed with non-negligible probability when he activates Handshake with one honest member in order to determine whether he satisfies the authentication policies or not.Formally, the property is defined in the following game between an adversary and a challenger :
- Init: The adversary first sets . Then, simulates Setup, CreateGroup and AddMember and sends group public keys together with revocation lists of all groups to .
- Queries: can make the following queries, such that the responses will be simulated by .
- –
- Corruption queries: The corruption list is initialized as ∅. The adversary can query CreateGroup and AddMember for the secret information of some groups and members, except for . Thus, will respond to the simulated information and update the corruption list .
- –
- Handshake queries: The adversary can make queries on the protocol with the group members. The transcripts of the queried members can be generated by . During a handshake, can query the hash functions used in the protocol. In particular, can request the non-interactive proof of knowledge of a random message for any member at the current interval.
- Challenge: The challenger selects a random bit . Then, acts as the member in the group and executes the handshake protocol with the adversary . attempts to distinguish to which group belongs.
- Output: The adversary outputs as its guess of ϕ.
Let ; we say that SHS satisfies the detector resistance if the function is negligible for any polynomially-bounded adversary. - (4)
- Unlinkability: This requirement implies that any adversary cannot find any relation between two instances of the Handshake algorithm, which is involved with the same honest members. Anyone except the GA could not distinguish whether two instances of the SH protocol are executed by the same honest member. In addition, the GA will never link two executions run by the same member, unless it carries out the TraceMember algorithm. Thus, the TraceMember algorithm can be authorized by a separate trace authority of the GA in order to improve the unlinkability. In the security definition of SHS [13], the privacy property explicitly implies both the unlinkability and the detector resistance. The formal definition of unlinkability is easily derived from of the detector resistance when the “Challenge” phase is executed twice. Let and be the random bits of the two challenges, respectively. If , let , else let . Therefore, the adversary outputs as its guess of ϕ to distinguish the two different challenges. We say that SHS satisfies the unlinkability if the probability of outputting the correct is negligible for any polynomially-bounded adversary.Remark on backward unlinkability: If a group member is removed from his group, i.e., his revocation token is added to the RL, the anonymity of the revoked member before the revocation is desirable to be sustained (i.e., backward unlinkability). This means that even after a member is revoked, all past handshake behaviors produced from the revoked member remain private and unlinkable. The formal definition of the property is easily obtained by revising the and “Challenge” phase of , which is similar to backward unlinkability in [14].
3. A Backward Unlinkable Secret Handshake Scheme with Revocation Support in the Standard Model
- Setup: Given a security parameter κ, the algorithm runs . The public parameters , which are shared by all participators in the scheme. Here, g is a generator of a subgroup of composite order , where p and q are random primes. Let and be the cyclic subgroups of with respective order p and q. The algorithm picks a generator h of . are selected randomly from . In addition, and are two cryptographic hash functions. T is the number of time intervals in the secret handshake system, and represents the j-th time interval for each . Finally, F is a function that represents the attribute. Suppose one attribute P is denoted by n-bits string , .
- CreateGroup: The GA chooses and generates . The GA outputs its group secret key and group public key .
- AddUser(n, T): Assuming that GA can add n users to the group in T time intervals, the GA issues attribute credential for each user. After verifying the identity of a user , the GA randomly selects secret key , and computes attribute credential . The user verifies that the credential is valid by testing and . In addition, the GA will calculate this user’s revocation token where for each time interval , such that . Then, becomes the valid member of the group, and the GA stores the user’s credential and revocation tokens in the member database.
- Handshake: Suppose A and B are two parties who want to execute a secret handshake protocol to authenticate each other without leaking their privacy at time interval . Participator A runs the protocol with and , which are created by group , and participator B runs it with and , which are created by group . Let and denote the target group public keys and target property (i.e., authentication policy) of the participators A and B, respectively. The protocol proceeds as follows:
- (1)
- (a)
- A chooses .
- (b)
- A computes , , , , , .
- (c)
- A calculates , , , , , .
Finally, A sends to B.- (2)
- (a)
- By verifying for all of the target group of B, B executes the revocation check to ensure that the A is not revoked at the time interval .
- (b)
- B will verify the correctness of and by testing , .
- (c)
- Similarly, B also generates proof knowledge of : .
- (d)
- If A does not pass the revocation check, B will generate a random value as the verification response. Otherwise, B will recover and from by using his target group public key and computes a verification value as follows.
- –
- B retrieves from and uses his target group public key to compute: .
- –
- B calculates by using as follows,
- –
- B will compute the following verification value , such that:
Finally, B sends both and to A.
- (3)
- (a)
- By checking for all after getting from B, A executes the similar revocation check to ensure that B is also not revoked at the time interval .
- (b)
- If B is revoked at time interval , A responds with a random value , as well. Otherwise, A retrieves and from by using its own target group public key .
- (c)
- A verifies the with the equation . If the above equation holds, A will output “1” and send to B. Else A outputs “0” and also responds with a random value to B.
- (d)
- B verifies with the following equation . B outputs “1” only if the above equation holds, else B outputs “0”.
- TraceUser: When a dispute happens, the GA first retrieves the proof information and from a transcript of a secret handshake instance at time interval . Then, GA checks for all in the user lists to identify who has executed the malicious secret handshakes.
- RemoveUser: The GA is responsible for the update of the RL for each time interval after tracing some malicious group users or receiving some users’ revocation requests. In order to remove a user from one group at time interval , the GA firstly looks up the user ’s information from its user lists. Then, the GA removes the user’s revocation tokens for all from the RL of its group. Consequently, other unrevoked group users can execute the revocation check under the updated RL to identify whether the counter-party is revoked. Particularly, the revocation tokens before the time interval are not added in the updated RL and will not satisfy the revocation check equation. Moreover, it is infeasible to deduce the previous revocation tokens for all from the revocation tokens for all that have been added in the updated RL at the time interval . Therefore, the past transcripts of revoked users still remain unrecognized and private, which achieves backward unlinkability.
4. Security and Performance Analysis
4.1. Security
- Init: To achieve the simulation, B first initiates the interaction settings where can simulate Setup, CreateGroup and AddUser(n, T) for every group in BU-RSH. In the Setup phase, B selects , as well as and , where means the number of queries of AddUser, and then prepares the public parameters for the adversary , . In the CreateGroup phase, first sets . For the group , sets the group public key to be for group , where . Additionally, prepares n pairs for each user , where . from the ℓ-HSDH challenge are distributed randomly in the user sets. For each , we mark either if is known or if is not from the ℓ-HSDH challenge and selected randomly from . Finally, B calculates for all and for all and . For other groups and their users, randomly generates and for every group and user and then executes CreateGroup and AddUser(n, T) just as the underlying algorithms in BU-RSH.
- Queries: can make the following queries, each of which is serviced by sequentially.
- –
- Corruption queries: The corruption list is initialized as ∅. The adversary can query CreateGroup and AddUser for the secret information of some groups and users. If , will respond and update the corruption list . If , simulates the GA correctly, and obtains the credential . Otherwise, reports failure and aborts. Since the verification equations and are satisfied, this is not distinguishable from receiving the real credential. However, if , aborts, as well.
- –
- Hash queries: The adversary can query the hash functions used in the Handshake protocol.
- –
- PROOF Queries: The adversary can query a proof of knowledge of message as user i at time interval . If , responds to the proof using the secret key . If , B selects and implicitly defines . The function is written as where , . Based on the above implicit definition , B can respond with the corresponding proof to the adversary.
- –
- Handshake queries: The adversary can make queries on the Handshake protocol with the group users. The transcripts of the queried users can be generated by using the corresponding attribute certificates, which are in accordance with the Handshake algorithm.
- Output: The output of the security game is “1”, only if the adversary on half of one user in the group succeeds in executing Handshake with . After at most total queries, will be dedicated to forge the PROOF on one random message on behalf of one group user from and execute the handshake protocol with .
4.2. Performance Analysis
| Ateniese et al. [8] | Kawai et al. [12] | Wen and Zhang [15] | BU-RSH | |
|---|---|---|---|---|
| Setup | 0 | 0 | 0 | |
| CreateGroup | ||||
| AddUser | ||||
| Handshake | 11 | |||
| Traceability | No | Yes | Yes | Yes |
| Revocation | No | No | Yes | Yes |
| Backward Unlinkability | No | No | Yes | Yes |
| Random Oracles | without | with | with | without |
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Camenisch, J.; Michels, A. An efficient system for non-transferable anonymous credentials with optional anonymity revoction. In Advances in Cryptology—EUROCRYPT 2001, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques, Innsbruck, Austria, 6–10 May 2001; Springer: Berlin/Heidelberg, Germany, 2001. Lecture Notes in Computer Science. Volume 2045, pp. 93–118. [Google Scholar]
- Balfanz, D.; Durfee, G.; Shankar, N.; Smetters, D.; Staddon, J.; Wong, H. Secret handshakes from pairing-based key agreements. In Proceedings of the IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 11–14 May 2003; pp. 180–196.
- Castelluccia, C.; Jarecki, S.; Tsudik, G. Secret handshakes from ca-oblivious encryption. In Advances in Cryptology—ASIACRYPT 2004, Proceedings of the 10th International Conference on the Theory and Application of Cryptology and Information Security, Jeju Island, Korea, 5–9 December 2004; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3329, pp. 293–307. [Google Scholar]
- Zhou, L.; Susilo, W.; Mu, Y. Three-round secret handshakes based on elgamal and dsa. In Information Security Practice and Experience, Proceedings of the Second International Conference, ISPEC 2006, Hangzhou, China, 11–14 April 2006; Springer: Berlin/Heidelberg, Germany, 2006. Lecture Notes in Computer Science. Volume 3903, pp. 332–342. [Google Scholar]
- Vergnaud, D. RSA-based secret handshakes. In Coding and Cryptography, Proceedings of the WCC 2005, Bergen, Norway, 14–18 March 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3969, pp. 252–274. [Google Scholar]
- Xu, S.; Yung, M. K-anonymous secret handshakes with reusable credentials. In Proceedings of the ACM Conference on Computer and Communications Security, Washington, DC, USA, 25–29 October 2004; pp. 158–167.
- Waters, B. Efficient identity-based encryption without random oracles. In Advances in Cryptology—EUROCRYPT 2005, Proceedings of the 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3494, pp. 114–127. [Google Scholar]
- Ateniese, G.; Blanton, M.; Kirsch, J. Secret handshakes with dynamic and fuzzy matching. In Proceedings of the Network and Distributed System Security Symposium (NDSS 2007), San Diego, CA, USA, 28 February–2 March 2007; pp. 159–177.
- Jarecki, S.; Liu, X. Unlinkable secret handshakes and key-private group key management schemes. In Applied Cryptography and Network Security, Proceedings of the 5th International Conference, ACNS 2007, Zhuhai, China, 5–8 June 2007; Springer: Berlin/Heidelberg, Germany, 2007. Lecture Notes in Computer Science. Volume 4521, pp. 270–287. [Google Scholar]
- Sorniotti, A.; Molva, R. Secret handshakes with revocation support. In Information, Security and Cryptology—ICISC 2009, Proceedings of the 12th International Conference, ICISC 2009, Seoul, Korea, 2–4 December 2009; Springer: Berlin/Heidelberg, Germany, 2009. Lecture Notes in Computer Science. Volume 5984, pp. 274–299. [Google Scholar]
- Sorniotti, A.; Molva, R. Federated secret handshakes with support for revocation. In Information and Communications Security, Proceedings of the 12th International Conference, ICICS 2010, Barcelona, Spain, 15–17 December 2010; Springer: Berlin/Heidelberg, Germany, 2010. Lecture Notes in Computer Science. Volume 6476, pp. 218–234. [Google Scholar]
- Kawai, Y.; Yoneyama, K.; Ohta, K. Secret handshake: Strong anonymity definition and construction. In Information Security Practice and Experience, Proceedings of the 5th International Conference, ISPEC 2009, Xi’an, China, 13–15 April 2009; Springer: Berlin/Heidelberg, Germany, 2009. Lecture Notes in Computer Science. Volume 5451, pp. 219–229. [Google Scholar]
- Jarecki, S.; Liu, X. Private mutual authentication and conditional oblivious transfer. In Advances in Cryptology—CRYPTO 2009, Proceedings of the 29th Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2009; Springer: Berlin/Heidelberg, Germany, 2009. Lecture Notes in Computer Science. Volume 5677, pp. 90–107. [Google Scholar]
- Nakanishi, T.; Funabiki, N. Verifier-local revocation group signature schemes with backward unlinkability from bilinear maps. In Advances in Cryptology—ASIACRYPT 2005, Proceedings of the 11th International Conference on the Theory and Application of Cryptology and Information Security, Chennai, India, 4–8 December 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3788, pp. 533–548. [Google Scholar]
- Wen, Y.; Zhang, F. A new revocable secret handshake scheme with backward unlinkability. In Public Key Infrastructures, Services and Applications, Proceedings of the 7th European Workshop, EuroPKI 2010, Athens, Greece, 23–24 September 2010; Springer: Berlin/Heidelberg, Germany, 2011. Lecture Notes in Computer Science. Volume 6711, pp. 17–30. [Google Scholar]
- Yang, Y.; Lu, H.; Weng, J.; Ding, X.; Zhou, J. A generic approach for providing revocation support in secret handshake. In Information and Communications Security, Proceedings of the 14th International Conference, ICICS 2012, Hong Kong, China, 29–31 October 2012; Springer: Berlin/Heidelberg, Germany, 2012. Lecture Notes in Computer Science. Volume 7618, pp. 276–284. [Google Scholar]
- Boneh, D.; Goh, E.; Nissim, K. Evaluationg 2-DNF formulas on ciphertexts. In Theory of Cryptography, Proceedings of the Second Theory of Cryptography Conference, TCC 2005, Cambridge, MA, USA, 10–12 February 2005; Springer: Berlin/Heidelberg, Germany, 2005. Lecture Notes in Computer Science. Volume 3378, pp. 325–341. [Google Scholar]
- Boyen, X.; Waters, B. Full-domain subgroup hiding and constant-size group signatures. In Public Key Cryptography–PKC 2007, Proceedings of the 10th International Conference on Practice and Theory in Public-Key Cryptography, Beijing, China, 16–20 April 2007; Springer: Berlin/Heidelberg, Germany, 2007. Lecture Notes in Computer Science. Volume 4450, pp. 1–15. [Google Scholar]
- Libert, B.; Vergnaud, D. Group signatures with verifier-local revocation and backward unlinkability in the standard model. In Cryptology and Network Security, Proceedings of the Conference on CANS 2009, Kanazawa, Japan, 12–14 December 2009; Springer: Berlin/Heidelberg, Germany, 2009. Lecture Notes in Computer Science. Volume 5888, pp. 498–517. [Google Scholar]
- Barreto, P. The ηT approach to the Tate pairing, and supporting (supersingular) elliptic curve arithmetic in characteristic 3. Available online: http://www.larc.usp.br/pbarreto/Pairings.GPL.zip (accessed on 25 July 2010).
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wen, Y.; Gong, Z.; Xu, L. A Backward Unlinkable Secret Handshake Scheme with Revocation Support in the Standard Model. Information 2015, 6, 576-591. https://doi.org/10.3390/info6040576
Wen Y, Gong Z, Xu L. A Backward Unlinkable Secret Handshake Scheme with Revocation Support in the Standard Model. Information. 2015; 6(4):576-591. https://doi.org/10.3390/info6040576
Chicago/Turabian StyleWen, Yamin, Zheng Gong, and Lingling Xu. 2015. "A Backward Unlinkable Secret Handshake Scheme with Revocation Support in the Standard Model" Information 6, no. 4: 576-591. https://doi.org/10.3390/info6040576
APA StyleWen, Y., Gong, Z., & Xu, L. (2015). A Backward Unlinkable Secret Handshake Scheme with Revocation Support in the Standard Model. Information, 6(4), 576-591. https://doi.org/10.3390/info6040576





