Improving Detectability of Advanced Persistent Threats (APT) by Use of APT Group Digital Fingerprints
Abstract
1. Introduction
- Evidence-backed limits of conventional IDS for ICS APTs: We formalize the mechanism-level reasons that signature-, anomaly-, and protocol-conformance detectors miss ICS-focused APTs. We consolidate these in a detection–evasion matrix (Table 1) with case evidence (Section 2 and Section 4.1.2).
- New technical findings from an Industroyer2 analysis: Through static and dynamic analysis, we document (i) hard-coded target specifics (e.g., IPs and IOAs), (ii) strictly valid IEC-104 message sequences (TESTFR/STARTDT, single/double commands), (iii) time-boxed execution via scheduled tasks, (iv) coordinated wiper cleanup, and (v) minimal error handling (no retries, ignores unexpected IOAs). We then derive explicit detection implications from these observations (Section 4.1.2).
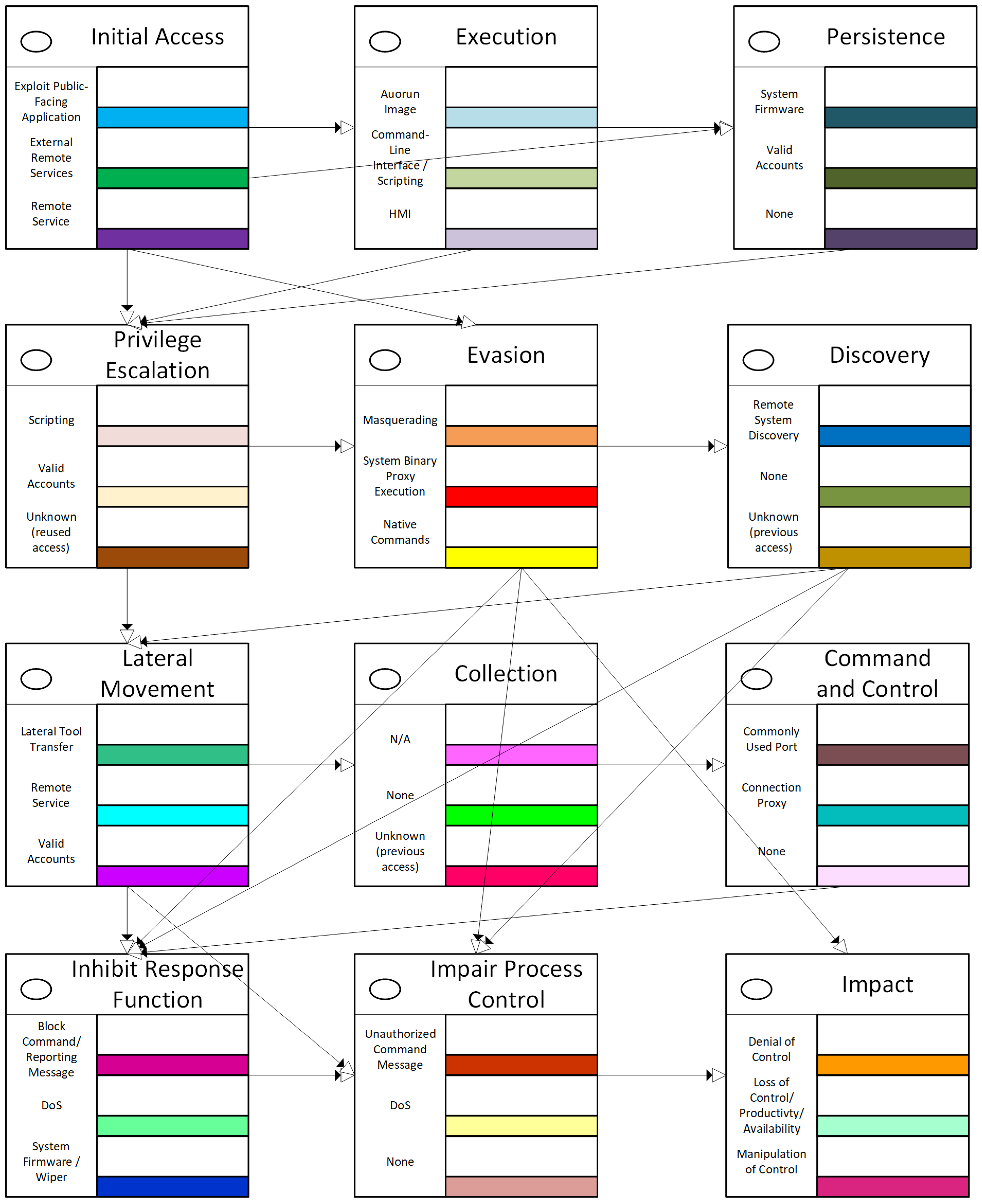
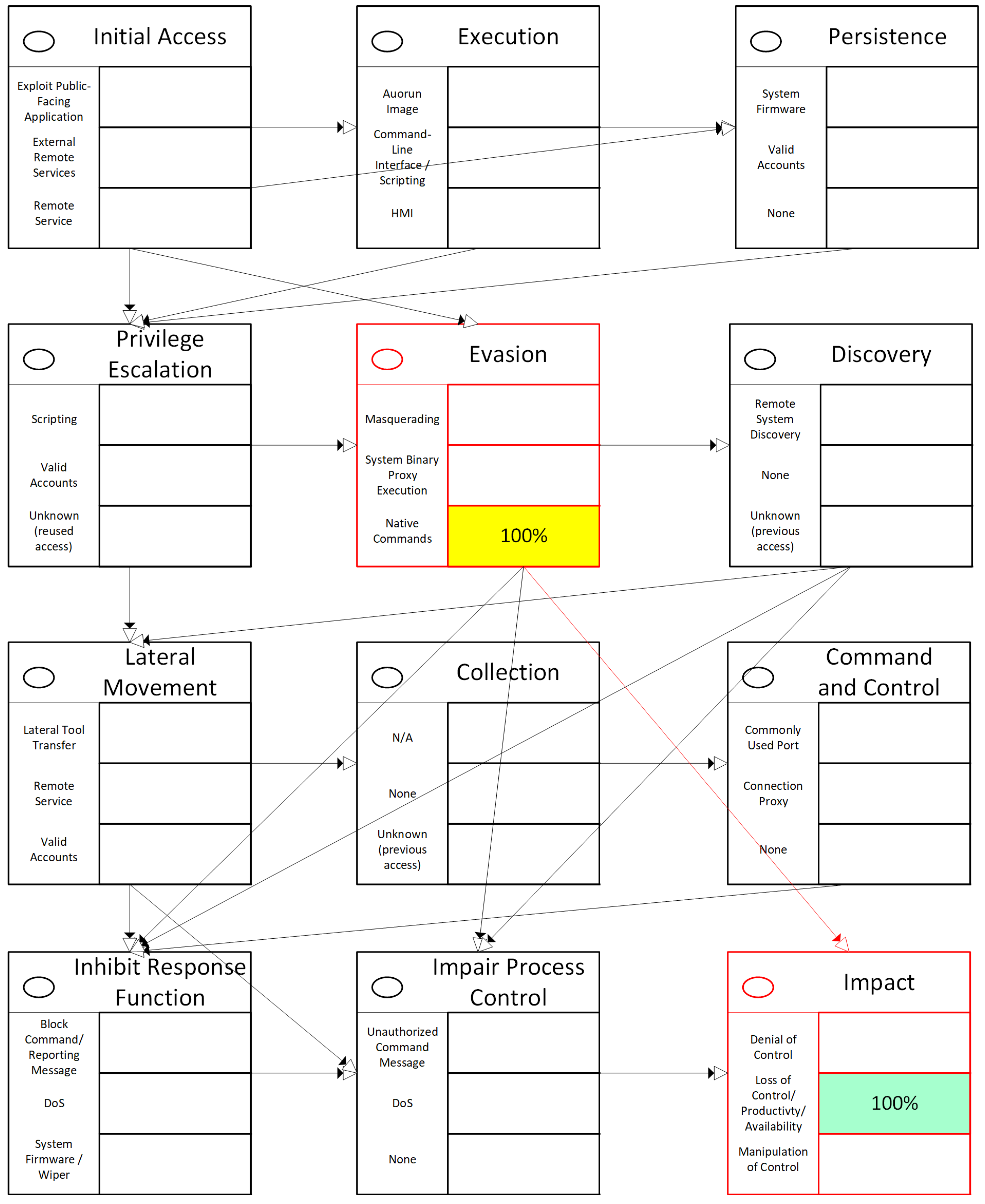
- APT group digital fingerprint for Sandworm: We instantiate a machine-interpretable graph-structured fingerprint as a directed graph over MITRE ATT&CK for ICS steps and encode sequence and state relations; from this, we derive rule sets for state- and sequence-aware detection (Section 5).
- Cross-campaign invariants and OT capability mapping: We provide a timeline of Sandworm’s OT activities and a capability comparison across BlackEnergy, Industroyer, and Industroyer2, highlighting invariants that persist when tools/IOCs change (Section 5).
- Illustration of detection concept: We show how the fingerprint would elevate risk for otherwise “normal” IEC-104 traffic when it occurs in improbable sequences or plant states (e.g., bursts of single/double commands outside maintenance). In addition, we demonstrate the specific Industroyer2 path on the fingerprint (Section 5).
2. Background and Related Work
Why Existing IDS Approaches Struggle with ICS APTs (Evidence and Failure Modes)
3. Power Grid Substations and Communication Protocols
4. The Sandworm Group
4.1. OT Related Sandworm Examples
4.1.1. Industroyer-2016
- Scanning the local network to identify IEC-104 endpoints (target devices).
- Establishing TCP connections using the standard IEC-104 port (default: TCP 2404).
- Transmitting various Type Identification (Type ID) messages, including single commands, double commands, general interrogations, and measurement values.
4.1.2. Industroyer2-2022
- Compromised credentials used to access the network via VPN.
- Use of another remote access mechanism or backdoor.
- An insider physically transferring the malware to the target system.
- Deployment via an unknown dropper that placed both Industroyer2 and CaddyWiper on the target device.
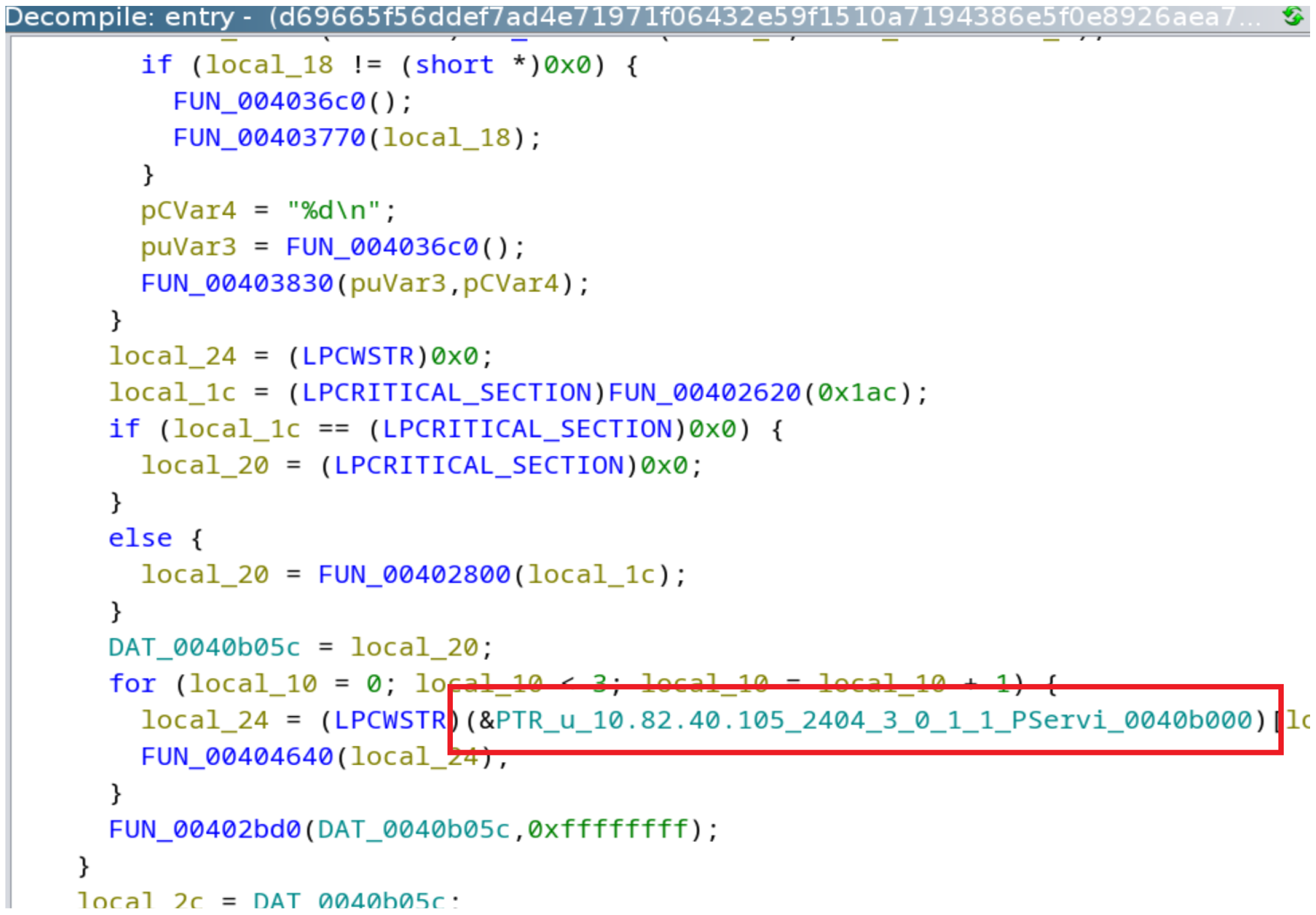
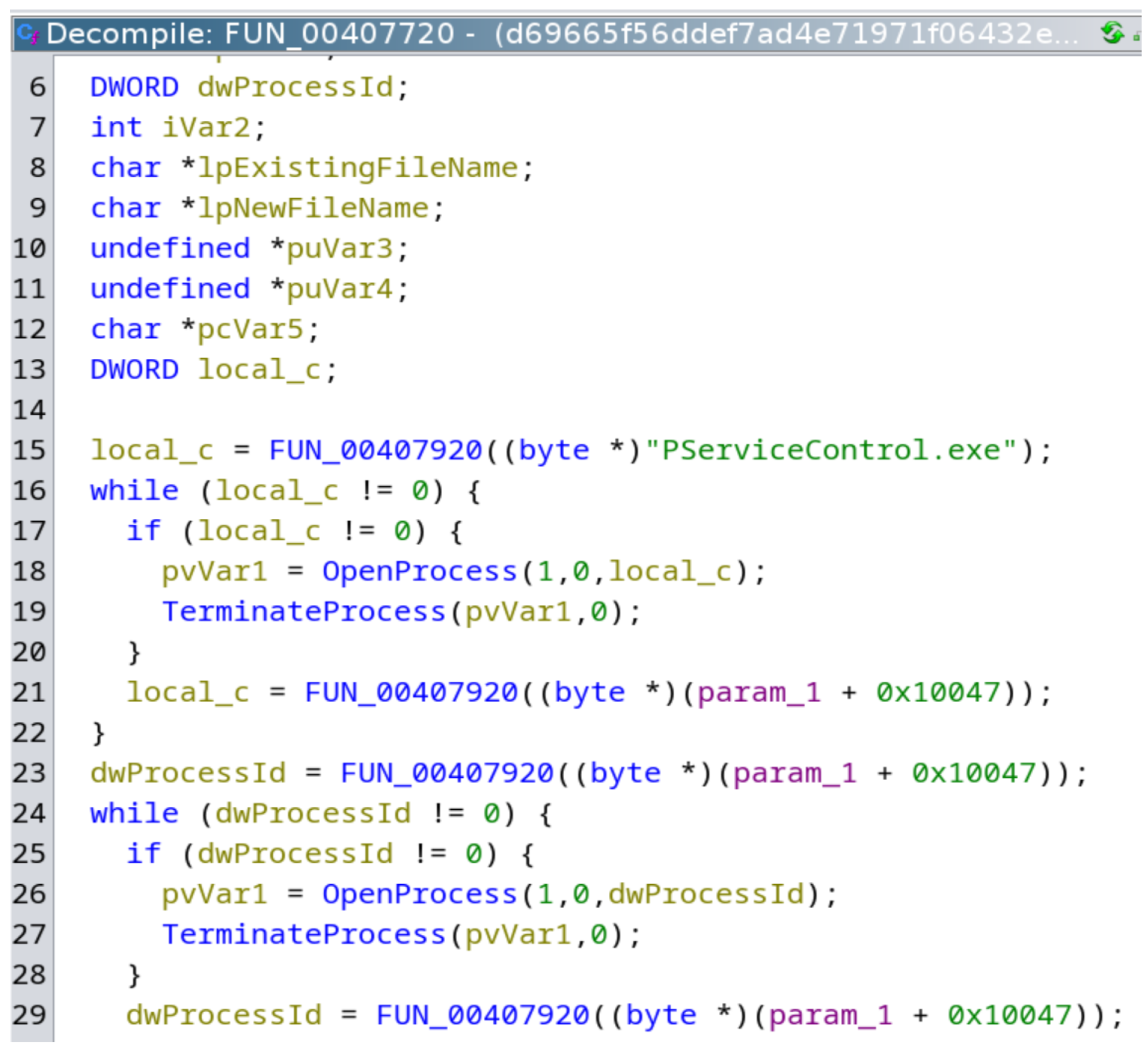
- Termination of existing processes: The malware begins by identifying and terminating processes responsible for communication between the substation and its control center. This is achieved using process enumeration and the TerminateProcess Windows API call (Figure 3).
- Establishing a TCP connection: It then initiates a TCP connection to the target substation using the hardcoded IP address and port 2404, the standard port for IEC 60870-5-104 communication.
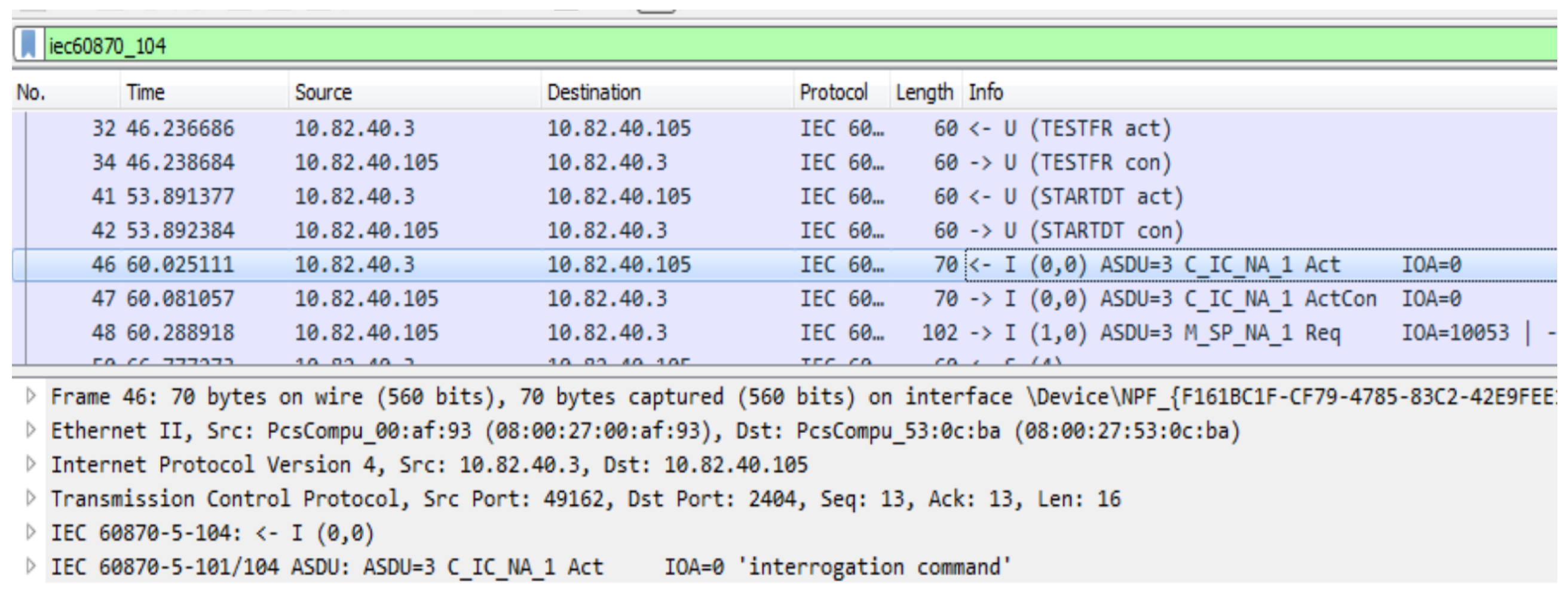
- Sending test frames: The malware sends test frame messages (Figure 4) to verify the availability of the target. If no response is received, execution is aborted.
- Initiating communication: Upon receiving a valid test frame response, the malware sends a STARTDT (Start Data Transfer) message to begin communication. If the corresponding confirmation is not received, the malware terminates.
- Interrogation: A general interrogation command is issued to retrieve a list of active Information Object Addresses (IOAs).
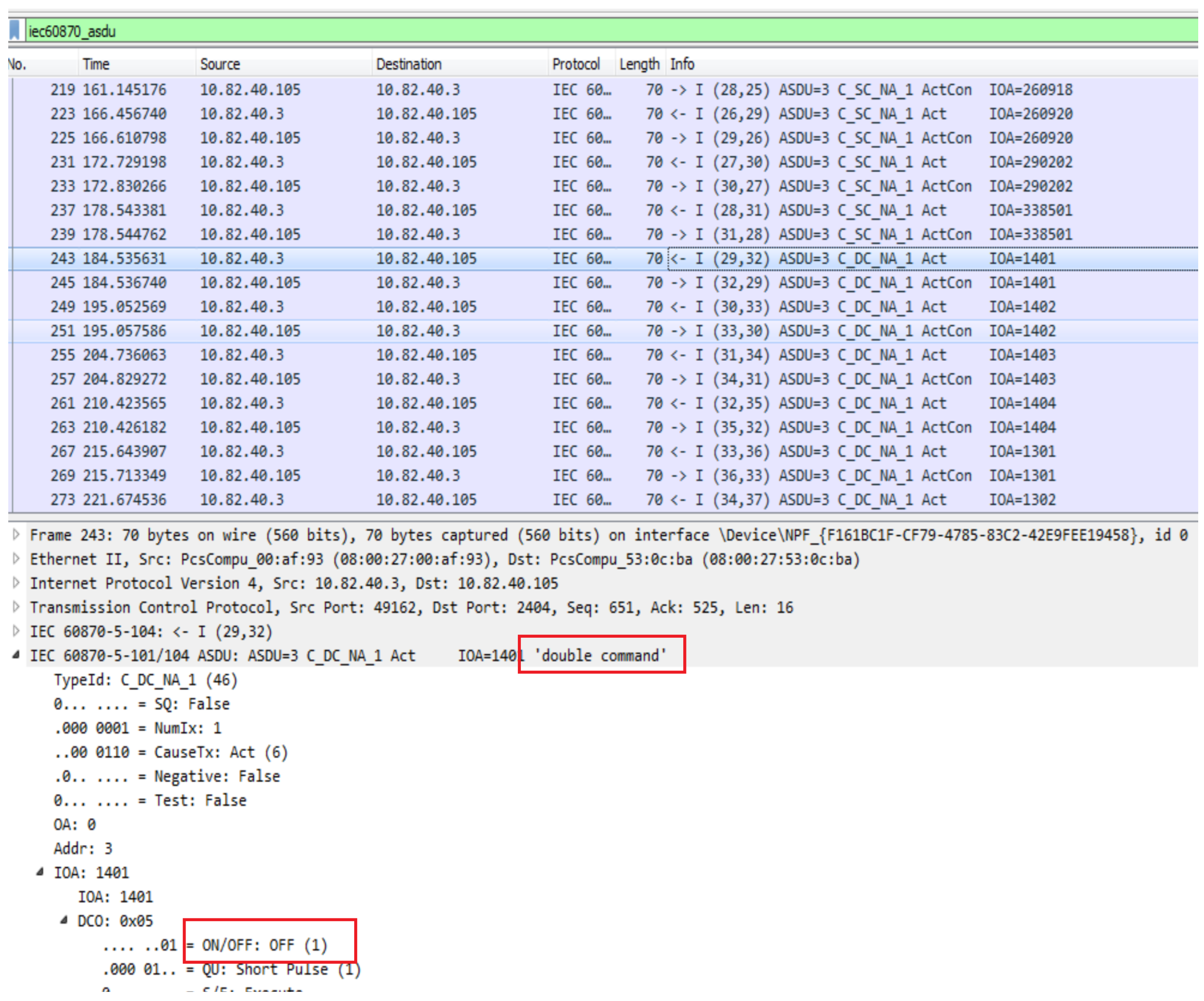
- Issuing single commands: The malware sends single commands to set 28 IOAs to the ON state. These IOAs fall within the address range 130202–338501 (Figure 1).
- Issuing double commands: It then sends double commands to set 16 IOAs to the OFF state, targeting addresses between 1101–1404 (Figure 1).
- Terminating communication: A STOPDT (Stop Data Transfer) message is sent to end the session.
- Closing the connection: Finally, the TCP connection is closed, completing the attack sequence.
- Absence of responses to test frame (TESTFR) or STARTDT messages.
- Responses containing previously unknown IOAs during interrogation.
- Failure of the substation to confirm state changes for specific IOAs.
- The ON and OFF states may be logical representations, with their physical effects determined by wiring configurations. If ON and OFF were reversed due to system setup, the attacker may still have achieved the intended outcome, indicating deep knowledge of the target environment.
- Alternatively, the single-command IOAs may not have controlled circuit breakers (which typically require double commands for safety). In this case, the attacker may have attempted to activate all available systems in order to increase load or create confusion, followed by selectively opening breakers using double commands.
- Clear separation of OT and IT roles: The executable responsible for Operational Technology (OT) actions was a standalone Portable Executable (PE) file that was focused solely on issuing IEC 104 commands. It did not include any IT-related functionalities such as persistence mechanisms or forensic evasion. This separation aligns with known tactics of the Sandworm group, which is believed to operate an OT-focused subgroup known as Electrum.
- Minimalist and protocol-compliant OT execution: The OT module executed its tasks using only standard well-formed IEC 104 protocol messages. There was no evidence of protocol misuse or exploitation. The malware simply leveraged its privileged network position along with pre-acquired knowledge such as IP addresses and IOA mappings to issue legitimate control commands.
- Modular IT components: The IT side of the operation was handled by separate independent modules. One or more of these modules likely deployed the Industroyer2 executable to the target environment. Scheduled tasks were created by another component, and the wiper module (CaddyWiper) functioned as a standalone tool responsible for post-execution cleanup.
- No OT-level zero-day exploits: The malware did not rely on any previously unknown vulnerabilities in OT systems. Its success was entirely dependent on having accurate reconnaissance data and access to the appropriate network segment.
- On-wire: All IEC-104 PDUs (TESTFR/STARTDT/single/double) were valid, meaning that protocol-conformance sensors would not trigger.
- On-host: No long-lived persistence or C2; execution was scheduled and time-boxed, and a wiper removed artifacts minutes later, starving host anomaly detectors of dwell.
5. APT Group Digital Fingerprint: Sandworm
6. Discussion and Summary
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- IEEE Spectrum. The Real Story of STUXNET. Available online: https://spectrum.ieee.org/the-real-story-of-stuxnet (accessed on 4 February 2013).
- NATO Standardization Office (NSO). AJP-3.20 Allied Joint Doctrine for Cyberspace Operations. NATO Standard, Edition A Version 1. Available online: https://assets.publishing.service.gov.uk/media/5f086ec4d3bf7f2bef137675/doctrine_nato_cyberspace_operations_ajp_3_20_1_.pdf (accessed on 6 January 2020).
- Ahlberg, C. Moving Toward a Security Intelligence Program. In The Threat Intelligence Handbook, 2nd ed.; CyberEdge Group LLC: Annapolis, MD, USA, 2019. [Google Scholar]
- IBM Security. Cost of a Data Breach Report. 2020. Available online: https://tinyurl.com/ypbk4m2m (accessed on 12 July 2025).
- International Electrotechnical Commission. IEC 60870-5-104:2006+AMD1:2016 CSV, Telecontrol Equipment and Systems–Part 5-104: Transmission Protocols–Network Access for IEC 60870-5-101 Using Standard Transport Profiles, 2.1 ed; IEC: Geneva, Switzerland, 2016; ISBN 978-2-8322-3459-4. [Google Scholar]
- Defense Use Case. Analysis of the Cyber Attack on the Ukrainian Power Grid; Electricity Information Sharing and Analysis Center (E-ISAC): Washington, DC, USA, 2016; Volume 388, p. 3. [Google Scholar]
- Lipovský, R.; Cherepanov, A. Industroyer2: The Return of the Most Powerful Industrial Malware; ESET Research: Bratislava, Slovakia, 2022; Available online: https://www.welivesecurity.com/2022/04/12/industroyer2-industroyer-reloaded/ (accessed on 12 July 2025).
- Dragos Inc. CRASHOVERRIDE: Analyzing the Malware that Attacks Power Grids; Dragos Inc.: Hanover, MD, USA, 2017; Available online: https://www.dragos.com/resources/whitepaper/crashoverride-analyzing-the-malware-that-attacks-power-grids/ (accessed on 12 July 2025).
- International Electrotechnical Commission (IEC). IEC 61850:2024 SER Communication Networks and Systems for Power Utility Automation—All Parts; IEC: Geneva, Switzerland, 2024; Available online: https://webstore.iec.ch/publication/6028 (accessed on 20 October 2024).
- Rashid, M.T.A.; Yussof, S.; Yusoff, Y.; Ismail, R. A Review of Security Attacks on IEC61850 Substation Automation System Network. In Proceedings of the 6th International Conference on Information Technology and Multimedia (ICIMU), Putrajaya, Malaysia, 18–20 November 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Ashraf, S.; Shawon, M.H.; Khalid, H.M.; Muyeen, S.M. Denial-of-Service Attack on IEC 61850-Based Substation Automation System: A Crucial Cyber Threat towards Smart Substation Pathways. Sensors 2021, 21, 6415. [Google Scholar] [CrossRef] [PubMed]
- Erdődi, L.; Kaliyar, P.; Houmb, S.H.; Akbarzadeh, A.; Waltoft-Olsen, A.J. Attacking Power Grid Substations: An Experiment Demonstrating How to Attack the SCADA Protocol IEC 60870-5-104. In Proceedings of the ARES ’22: Proceedings of the 17th International Conference on Availability, Reliability and Security, Vienna, Austria, 23–26 August 2022; pp. 1–10. [Google Scholar] [CrossRef]
- Akbarzadeh, A.; Erdodi, L.; Houmb, S.H.; Soltvedt, T.G.; Muggerud, H.K. Attacking IEC 61850 Substations by Targeting the PTP Protocol. Electronics 2023, 12, 2596. [Google Scholar] [CrossRef]
- Krishnapriya, S.; Singh, S. A Comprehensive Survey on Advanced Persistent Threat (APT) Detection Techniques. Comput. Mater. Contin. 2024, 80, 2675–2719. [Google Scholar] [CrossRef]
- Slick, S.B. Intelligence in Defense of Democracy, PRP 221; LBJ School of Public Affairs: Austin, TX, USA, 2022. [Google Scholar]
- Slowik, J. Crashoverride: Reassessing the 2016 Ukraine Electric Power Event as a Protection-Focused Attack; Dragos, Inc.: Hanover, MD, USA, 2019. [Google Scholar]
- Gaspar, J.; Cruz, T.; Lam, C.-T.; Simões, P. Smart Substation Communications and Cybersecurity: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2023, 25, 2456–2493. [Google Scholar] [CrossRef]
- Pinto, A.D.; Dragoni, Y.; Carcano, A. TRITON: The First ICS Cyber Attack on Safety Instrument Systems. In Proceedings of the Black Hat USA, Las Vegas, NV, USA, 8–9 August 2018; pp. 1–26. [Google Scholar]
- Assante, M.J.; Lee, R.M. The Industrial Control System Cyber Kill Chain; SANS Institute InfoSec Reading Room: Bethesda, MD, USA, 2015; Volume 1, p. 2. [Google Scholar]
- Gady, F.-S.; Stronell, A. Cyber Capabilities and Multi-Domain Operations in Future High-Intensity Warfare in 2030. In Cyber Threats and NATO 2030: Horizon Scanning and Analysis; NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE): Tallinn, Estonia, 2020; p. 151. [Google Scholar]
- Lockheed Martin Corporation. Cyber Kill Chain®; Lockheed Martin: Bethesda, MD, USA. Available online: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html (accessed on 12 July 2025).
- Akbarzadeh, A.; Erdodi, L.; Houmb, S.H.; Soltvedt, T.G. Two-stage advanced persistent threat (APT) attack on an IEC 61850 power grid substation. Int. J. Inf. Secur. 2024, 23, 2739–2758. [Google Scholar] [CrossRef]
- Abuse, C. MalwareBazaar: A Repository for Sharing Malware Samples. Available online: https://bazaar.abuse.ch (accessed on 12 July 2025).
- IFE. CybWin—Cybersecurity Platform for Assessment and Training for Critical Infrastructures; Institute for Energy Technology (IFE): Halden, Norway, 2022; Available online: https://ife.no/en/cybwin-project-results/ (accessed on 12 July 2025).
- NORCE. Drilling and Well Center–Stavanger; Norwegian Research Centre AS (NORCE): Stavanger, Norway, 2022; Available online: https://ullrigg.norceresearch.no/ (accessed on 12 July 2025).
| Approach | What It Flags | Why ICS APTs Evade | Evidence |
|---|---|---|---|
| Signature-based | Known byte/host IOCs | Recompiled, target-specific binaries; valid IEC-104/61850 frames yield no novel signature; wipers remove artifacts | [7,8] |
| Anomaly/behavior | Baseline deviation | Short, scheduled execution; maintenance confounders; low dwell | [3,4,7] |
| Protocol-conformance | Malformed/forbidden PDUs | Industroyer(2) used correct TESTFR/STARTDT/single/double commands; impersonated master | [7,8] |
| Year(s) | Attack Name | Target(s) | Impact |
|---|---|---|---|
| 2014–2016 | BlackEnergy | Ukrainian power grid, media, government | First known cyberattack to disrupt power (Ukraine, 2015 [6]). |
| 2016 | Industroyer/CrashOverride | Ukrainian power infrastructure | Purpose-built ICS-disruption malware; caused power outage in Kyiv. |
| 2016–2018 | VPNFilter | Routers and NAS devices worldwide | Large-scale botnet campaign enabling espionage and sabotage. |
| 2017 | NotPetya | Ukrainian supply chain (MeDoc); global spread | Fake ransomware/wiper; caused $10B+ in global damages. |
| 2018 | Olympic Destroyer | PyeongChang Winter Olympics | Disruption of IT systems; sophisticated false-flag operation. |
| 2022 | Industroyer2 | Ukrainian electric grid | Updated Industroyer malware; attempt to cause blackout during invasion. |
| 2022 | AcidRain | Viasat KA-SAT satellite modems | Wiper malware disabled satellite comms across Ukraine and parts of Europe. |
| 2016–present | Operation Ghostwriter | Eastern Europe (esp. Poland, Baltics) | Info ops with cyberattacks (phishing, defacements, disinfo campaigns). |
| Capability | Examples/Tools | Description/Notes |
|---|---|---|
| Wiper Functionality | KillDisk, Olympic Destroyer, CaddyWiper | Destructive malware used to erase or corrupt data, often targeting critical infrastructure or during hybrid operations. |
| Custom Backdoors | BlackEnergy, Exaramel | Used for long-term access and command-and-control; often part of initial infection chains. |
| ICS/SCADA-Specific Modules | Industroyer, Industroyer2 | Modules tailored for industrial protocols (e.g., IEC-104), demonstrating deep operational technology (OT) knowledge. |
| DDoS Capabilities | BlackEnergy (with plugins) | Supports large-scale disruption campaigns; used against media and energy sectors in Ukraine. |
| Persistence Techniques | Registry keys, Scheduled tasks | Common techniques for maintaining foothold across reboots and user sessions. |
| Credential Dumping | Mimikatz, custom scripts | Used for privilege escalation and lateral movement within the network. |
| Driver Exploitation | Vulnerable Windows drivers | Abuse of known driver flaws to escalate privileges or bypass protections like Driver Signature Enforcement. |
| Lateral Movement | Custom tools, PsExec-like methods | Internal network traversal to reach high-value targets, often post-compromise. |
| Defense Evasion | Legitimate binary abuse, false flags (e.g., Olympic Destroyer) | Techniques to avoid detection or mislead attribution, including use of signed binaries and mimicking other threat actors. |
| Time | Activity | Capabilities |
|---|---|---|
| 2014–2015 | Reconnaissance starts | Credential harvesting, information gathering of various types |
| 2015 | BlackEnergy deployed in Ukraine | Less sophisticated OT functions with focus on accessing control stations and manually issuing OT commands |
| 16 December 2016 | Industroyer (CrashOverride) attack on Pivnichna substation near Kyiv, Ukraine | First modular OT malware: separate modules for IEC-101, IEC-104, and OPC protocols; included wiper module and Windows persistence mechanisms |
| 8 April 2022 | Industroyer2 detected targeting Ukraine’s energy infrastructure | Compact, tailored OT modules per target; synchronized attacks across multiple substations; no persistence, designed for rapid execution |
| Capability Area | BlackEnergy (2015) | CrashOverride/ Industroyer (2016) | Industroyer2 (2022) |
|---|---|---|---|
| Initial Access | Spearphishing with malicious Office macros and BlackEnergy3 loader | Likely spearphishing or lateral movement from earlier compromise | No new vector; relied on previous compromise |
| Persistence | DLL side-loading; scheduled tasks | Registry run keys; service installation | No long-term persistence; scheduled execution |
| Privilege Escalation | PowerShell scripts; custom tools | Unknown but likely achieved; reused access | Elevated privileges already present |
| Defense Evasion | Custom packers, signed drivers, misleading filenames | Native ICS communication to avoid IT detection | Small footprint; fast execution; timed shutdown |
| Credential Access | Mimikatz, password dumping | Likely used; not central | Not disclosed; assumed pre-obtained |
| Discovery/Lateral Movement | PsExec, SMB, network scanning | ICS network scanning; knowledge of device layout | Manual reconnaissance evident; binary hardcoded for target |
| ICS-Specific Capabilities | None directly; relied on manual control | Native ICS protocol modules: IEC-101, IEC-104, OPC, IEC-61850 | Custom IEC-104 messages; directly opened breakers |
| Command & Control (C2) | HTTP/S, Tor proxies | Local-only, time-triggered execution | No C2; single-use binary |
| Impact/Disruption | Breaker manipulation via HMI; triggered KillDisk | Automated breaker control; optional KillDisk wiper | Breaker manipulation and system corruption with wipers |
| Wiper/Destruction | KillDisk to damage systems post-attack | KillDisk re-used to delay recovery | CaddyWiper (Windows), ORCSHRED/ SOLOSHRED/ AWFULSHRED (Linux/Solaris) |
| Targeting Approach | IT & OT; operator involvement required | Protocol-agnostic, modular for reuse | Fully hardcoded to a single infrastructure layout |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Erdodi, L.; Abraham, D.; Houmb, S.H. Improving Detectability of Advanced Persistent Threats (APT) by Use of APT Group Digital Fingerprints. Information 2025, 16, 811. https://doi.org/10.3390/info16090811
Erdodi L, Abraham D, Houmb SH. Improving Detectability of Advanced Persistent Threats (APT) by Use of APT Group Digital Fingerprints. Information. 2025; 16(9):811. https://doi.org/10.3390/info16090811
Chicago/Turabian StyleErdodi, Laszlo, Doney Abraham, and Siv Hilde Houmb. 2025. "Improving Detectability of Advanced Persistent Threats (APT) by Use of APT Group Digital Fingerprints" Information 16, no. 9: 811. https://doi.org/10.3390/info16090811
APA StyleErdodi, L., Abraham, D., & Houmb, S. H. (2025). Improving Detectability of Advanced Persistent Threats (APT) by Use of APT Group Digital Fingerprints. Information, 16(9), 811. https://doi.org/10.3390/info16090811







