A Multi-Angle Semantic Feature Fusion Method for Web User Behavior Anomaly Detection
Abstract
1. Introduction
- A significant innovation of this Web anomaly behavior recognition method is its integration of behavior features and semantic features from multiple perspectives, enriching the semantic expression of user behaviors.
- The behavioral modality characterizes user behavior effectively by analyzing user session sequences in Web traffic logs. An improved SimHash algorithm is utilized to address the issue of inconsistent session lengths across users, enabling the model to capture behavioral patterns and regularities.
- The semantic modality employs a multi-head attention-enhanced Transformer model to deeply mine semantic information from textual data, thereby improving the understanding of user intentions and the underlying meanings behind behaviors.
- An end-to-end Web abnormal user behavior detection model is constructed, which not only integrates behavior and semantic features but also designs a set of loss functions, including inter label loss, common space loss, and label loss, to minimize the mapping errors between the two modalities. This design allows the model to focus more on the fusion and complementarity of the two features during training, thereby enhancing the accuracy and robustness of anomaly detection.
2. Related Works
3. The Proposed Model
3.1. Behavior Feature Extraction Algorithm
| Algorithm 1: Behavior Feature Extraction Algorithm |
1. BehaviorHash (Input Vector V): 2. Initialize a vector of length ; # length is f 3. Initialize an f-bit binary value ; # length is f 4. For each element v in V: 5. # Use traditional hash to compute f-bit binary signature b of v; 6. ; 7. For i from 0 to : 8. If : 9. ; 10. Else: 11. ; 12. For i from 0 to : 13. If : 14. ; 15. Else: 16. ; 17. Return the vectorized SimHash value; |
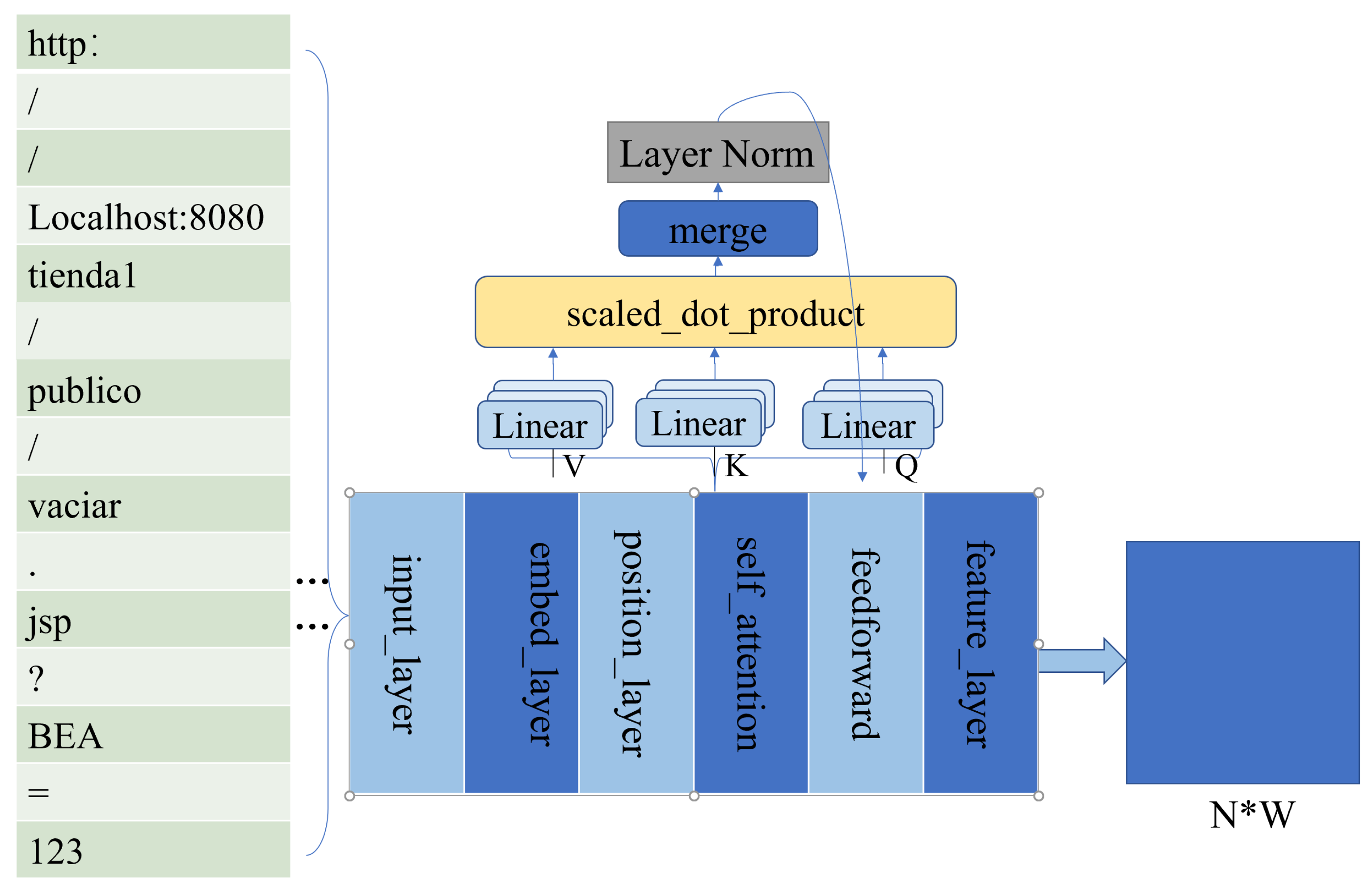
3.2. Semantic Feature Extraction Model
- Input Layer: Receives the input sequence.
- Embedded Layer: Converts discrete or unstructured data into continuous vector representations that the model can understand.
- Positional Layer: Adds positional information to each position in the sequence. The specific calculation methods are as follows:Each word in the sentence has a corresponding position index . This word is mapped to a d-dimensional word vector. In this d-dimensional vector, the even dimensions (0, 2, 4, …) are represented and indexed by , while the odd dimensions (1, 3, 5, …) are represented and indexed by .In code implementation, instead of directly calculating the power of , the equivalent exponential and logarithmic form is used: .Advantages:
- Directly using exponentiation may lead to numeric overflow or underflow.
- In many computing devices and libraries, implementations of exponential and logarithmic operations are typically faster than power operations.
- Self-Attention Layer: The self-attention mechanism is designed to compute relevance weights between each word and other words in the input sequence, generating a representation vector for each word that incorporates contextual information.
- Multi-Head Attention Function: To further enhance the ability of the self-attention mechanism to aggregate contextual information, multi-head attention is implement-ed, allowing the model to focus on different aspects of the context. The calculation formulas are as follows:where Q, K, V, respectively, represent the matrices formed by concatenating the q, k, v vectors from different words in the input sequence.Multi-head attention calculates multiple attention representations in parallel within different subspaces and concatenates them, enhancing the model’s capacity to capture diverse positional relationships across different subspaces.
- Feature Layer: The final output layer projects the model’s output into a two-dimensional subspaces.
- Loss function: we use Mean Squared Error (MSE), and all parameters in the model are optimized using Adam.
3.3. MSFFusion Model
- 1.
- Inner Label LossThe goal of feature fusion is to discover the underlying unified semantic representation across modalities, i.e., to learn a common semantic space. The core objective of this shared space is to eliminate surface-level differences between data from different modalities and to reveal the intrinsic semantic relationships within the data. This ensures that samples close in semantic space have similar representations, while those with semantic differences are represented dissimilarly. This approach facilitates higher-level semantic understanding and analysis tasks. To learn features of web user behavior data, this research proposes a modal discrepancy minimization using Multi-Kernel Maximum Mean Discrepancy (MK-MMD). The goal is to find a function such that the behavior modality and semantic modality can be mapped into the same feature space, i.e., a Hilbert space.where H is the reproducing kernel hilbert space, K is the kernel function, and is the Hilbert space associated with the kernel K.
- 2.
- Common Space LossCommon Space Loss has been effectively utilized in the field of multimodal research and has been demonstrated in the literature to improve the detection performance of models. Therefore, we adopt the aforementioned approach and, following the work of Refs. [23,24], we incorporate this concept into our framework. Additionally, Ref. [25] demonstrated that features fused into a common space are the most effective for classification tasks. Building on the assumption that these two semantic features are projected into the same shared space, this paper introduces a common space loss function to optimize the shared feature representation. This loss encourages vectors of user behaviors belonging to the same class to be more compact, and those of different classes to have larger distance differences, thereby enhancing the discriminability between different request categories.where , , . The cosine similarity measures the angular similarity between two vectors. , , . The indicator function assigns a value of 1 if the two elements belong to the same class; otherwise, 0. The aim is to maximize the distances between representations of different modalities while minimizing the distances within the same modality.
- 3.
- Label LossTo reduce the distance between the true and predicted values, the Mean Absolute Error (MAE) function is used, where is the prediction function and represents the label.where and denote the semantic modal loss and behavior modal classification loss, respectively. indicate the labels for corresponding classes.
- 4.
- The final combined loss function (from Equation (5) to (8)) is shown as follows:
4. Experiments and Results
4.1. Datasets
4.2. Evaluation Methods and Model Parameters
4.3. Experimental Results and Analysis
4.3.1. Comparison of Models Under Different Scenarios
4.3.2. Performance Comparison of Semantic Features
4.3.3. Performance Comparison of Behavioral Features
4.3.4. Ablation Study
4.3.5. Efficiency Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| XSS | Cross-Site Scripting |
| Web | World Wide Web |
| XGBoost | eXtreme Gradient Boosting |
| EDoS | Economic Denial of Sustainability |
| OWASP | Open Web Application Security |
| API | Application Programming Interface |
| GMM | Gaussian Mixture Models |
| BGMM | Bayesian Gaussian Mixture Models |
| LSTM | Long Short-Term Memory |
| WebLearner | Web-based Learner |
| LR | Logistic Regression |
| CNN | Convolutional Neural Network |
| URLs | Uniform Resource Locators |
| MSE | Mean Squared Error |
| MK-MMD | Multi-Kernel Maximum Mean Discrepancy |
| MAE | Mean Absolute Error |
| MACCDC | Mid-Atlantic Collegiate Cyber Defense Competition |
| CSNS | China Spallation Neutron Source |
References
- Kruegel, C.; Vigna, G. Anomaly detection of web-based attacks. In CCS ’03, Proceedings of the 10th ACM Conference on Computer and Communications Security, Washington, DC, USA, 27–31 October 2003; Association for Computing Machinery: New York, NY, USA, 2003; pp. 251–261. [Google Scholar] [CrossRef]
- Kruegel, C.; Vigna, G.; Robertson, W. A multi-model approach to the detection of web-based attacks. Comput. Netw. 2005, 48, 717–738. [Google Scholar] [CrossRef]
- Robertson, W.; Vigna, G.; Kruegel, C.; Kemmerer, R.A. Using Generalization and Characterization Techniques in the Anomaly-Based Detection of Web Attacks. NDSS. 2006. Available online: https://api.semanticscholar.org/CorpusID:8266221 (accessed on 14 September 2025).
- Luo, C.; Tan, Z.; Min, G.; Gan, J.; Shi, W.; Tian, Z. A Novel Web Attack Detection System for Internet of Things via Ensemble Classification. IEEE Trans. Ind. Inform. 2021, 17, 5810–5818. [Google Scholar] [CrossRef]
- Laiq, F.; Al-Obeidat, F.; Amin, A.; Moreira, F. DDoS Attack Detection in Edge-IIoT using Ensemble Learning. In Proceedings of the 2023 7th Cyber Security in Networking Conference (CSNet), Montreal, QC, Canada, 16–18 October 2023; pp. 204–207. [Google Scholar] [CrossRef]
- Xie, Y.; Tang, S. Online anomaly detection based on web usage mining. In Proceedings of the 2012 IEEE 26th International Parallel and Distributed Processing Symposium Workshops PhD Forum, Shanghai, China, 21–25 May 2012; pp. 1177–1182. [Google Scholar] [CrossRef]
- Zhang, Z.; Sun, R.; Wang, X.; Zhao, C. A situational analytic method for user behavior pattern in multimedia social networks. IEEE Trans. Big Data 2019, 5, 520–528. [Google Scholar] [CrossRef]
- Hong, L. Based on the user behavior characteristics of mining database anomaly detection model design. In Proceedings of the 2013 6th International Conference on Information Management, Innovation Management and Industrial Engineering, Xi’an, China, 23–24 November 2013; Volume 2, pp. 619–622. [Google Scholar] [CrossRef]
- Zhou, Y.; Wang, Y.; Ma, X. A user behavior anomaly detection approach based on sequence mining over data streams. In Proceedings of the 2016 17th International Conference on Parallel and Distributed Computing, Applications and Technologies (PDCAT), Guangzhou, China, 16–18 December 2016; pp. 376–381. [Google Scholar] [CrossRef]
- Prinakaa, S.; Bavanika, V.; Sanjana, S.; Srinivasan, S.; Sarasvathi, V. A Real-Time Approach to Detecting API Abuses Based on Behavioral Patterns. In Proceedings of the 2024 8th International Conference on Cryptography, Security and Privacy (CSP), Osaka, Japan, 20–24 April 2024; pp. 24–28. [Google Scholar] [CrossRef]
- Hu, S.; Xiao, Z.; Rao, Q.; Liao, R. An anomaly detection model of user behavior based on similarity clustering. In Proceedings of the 2018 IEEE 4th Information Technology and Mechatronics Engineering Conference (ITOEC), Chongqing, China, 14–16 December 2018; pp. 835–838. [Google Scholar] [CrossRef]
- Gao, Y.; Ma, Y.; Li, D. Anomaly detection of malicious users’ behaviors for web applications based on web logs. In Proceedings of the 2017 IEEE 17th International Conference on Communication Technology (ICCT), Chengdu, China, 27–30 October 2017; pp. 1352–1355. [Google Scholar] [CrossRef]
- Paul, M.; Medhe, K. Using Machine Learning to Detect Anomalies in Internet Browsing Pattern of Users. In Proceedings of the 5th International Conference on Cyber Security & Privacy in Communication Networks (ICCS) 2019, Kurukshetra, India, 29–30 November2019; Available online: https://ssrn.com/abstract=3511054 (accessed on 14 September 2025).
- Xiao, R.; Su, J.; Du, X.; Jiang, J.; Lin, X.; Lin, L. Sfad: Toward effective anomaly detection based on session feature similarity. Knowl. Based Syst. 2019, 165, 149–156. Available online: https://api.semanticscholar.org/CorpusID:58005338 (accessed on 1 February 2019). [CrossRef]
- Modell, A.; Larson, J.; Turcotte, M.; Bertiger, A. A graph embedding approach to user behavior anomaly detection. In Proceedings of the 2021 IEEE International Conference on Big Data (Big Data), Orlando, FL, USA, 15–18 December 2021; pp. 2650–2655. [Google Scholar] [CrossRef]
- Ma, H.; Wang, C.; Qi, H. Anomaly Behavior Detection for the Web Application Based on LSTM. In Proceedings of the 2021 IEEE Conference on Telecommunications, Optics and Computer Science (TOCS), Shenyang, China, 10–11 December 2021; pp. 553–559. [Google Scholar] [CrossRef]
- Gui, J.; Chen, Z.; Yu, X.; Lumezanu, C.; Chen, H. Anomaly detection on web-user behaviors through deep learning. In Security and Privacy in Communication Networks; Springer International Publishing: Cham, Switzerland, 2020; Available online: https://api.semanticscholar.org/CorpusID:229182996 (accessed on 12 December 2020).
- Ma, C.-S.; Du, X.-R.; Lou, J.; Wang, M.-Q. A User Behavior Prediction Method for Web Applications Based on Deep For-est. J. Web Eng. 2025, 24, 39–56. [Google Scholar] [CrossRef]
- Perumal, S.; Sujatha, P.K. Stacking ensemble-based xss attack detection strategy using classiffcation algorithms. In Proceedings of the 2021 6th International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 8–10 July 2021; pp. 897–901. [Google Scholar] [CrossRef]
- Le, H.; Pham, Q.; Sahoo, D.; Hoi, S.C. Urlnet: Learning a url representation with deep learning for malicious url detection. arXiv 2018, arXiv:abs/1802.03162. Available online: https://api.semanticscholar.org/CorpusID:3670018 (accessed on 9 February 2018). [CrossRef]
- Li, H.; Ni, Y. Intrusion detection technology research based on apriori algorithm. Phys. Procedia 2012, 24, 1615–1620. [Google Scholar] [CrossRef]
- Zolotukhin, M.; Hämäläinen, T.; Kokkonen, T.; Siltanen, J. Analysis of http requests for anomaly detection of web attacks. In Proceedings of the 2014 IEEE 12th International Conference on Dependable, Autonomic and Secure Computing, Dalian, China, 24–27 August 2014; pp. 406–411. [Google Scholar] [CrossRef]
- Rathi, P.; Singh, N. An improved medoid clustering algorithm for intrusion detection using web usage mining technique. J. Posit. Sch. Psychol. 2022, 6, 10095–10108. [Google Scholar]
- Zhen, L.; Hu, P.; Wang, X.; Peng, D. Deep supervised cross-modal retrieval. In Proceedings of the 2019 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Long Beach, CA, USA, 15–20 June 2019; pp. 10386–10395. [Google Scholar] [CrossRef]
- Zeng, D.; Oyama, K. Learning joint embedding for cross-modal retrieval. In Proceedings of the 2019 International Conference on Data Mining Workshops (ICDMW), Beijing, China, 8–11 November 2019; pp. 1070–1071. [Google Scholar] [CrossRef]
- Yang, T.; Li, M.; Deng, H.; Wang, J. A sentence-bert-based model for expressing key features of hospital web logs. In Proceedings of the 2023 4th International Seminar on Artiffcial Intelligence, Networking and Information Technology (AINIT), Nanjing, China, 16–18 June 2023; pp. 467–470. [Google Scholar] [CrossRef]
- Ahir, D.; Shaikh, N. Analyzing Machine Learning Frameworks for Anomaly Detection on Web Server Log Data. In Proceedings of the 2025 International Conference on Emerging Smart Computing and Informatics (ESCI), Pune, India, 5–7 March 2025; pp. 1–7. [Google Scholar] [CrossRef]
- Wang, J.; Zhou, Z.; Chen, J. Evaluating cnn and lstm for web attack detection. In Proceedings of the 2018 10th International Conference on Machine Learning and Computing, Macau, China, 26–28 February 2018; ACM: New York, NY, USA, 2018; pp. 283–287. [Google Scholar]
- Mac, H.; Truong, D.; Nguyen, L.; Nguyen, H.; Tran, H.A.; Tran, D. Detecting attacks on web applications using autoencoder. In Proceedings of the Ninth International Symposium on Information and Communication Technology, Da Nang, Vietnam, 6–7 December 2018; pp. 416–421. [Google Scholar]


| Parameters | Type | Description |
|---|---|---|
| ts | Time | Request timestamp |
| uid | String | Connect the unique ID to identify the session. |
| id | Record | A class that includes source host/source port and destination host/destination port numbers |
| trans_depth | Count | Length of the transmitted content |
| method | String | Request method: GET, POST, etc. |
| host | String | Service address in the request. |
| uri | String | Uniform Resource Identifier in the request |
| referrer | Count | The content of Referrer in the header |
| user_agent | String | User-agent in the web request header, representing the client content requesting the web service |
| request_body_len | Count | The actual size of uncompressed data transmitted from the client |
| response_body_len | Count | The actual size of uncompressed data transmitted from the server |
| status_code | Count | Status code returned from the server, usually including codes like 404, 302, etc. |
| status_msg | String | Message returned from the server; for example, 404 indicates the requested page was not found, does not exist |
| info_code | Count | The server’s last response code, generally an 1xx informational response code |
| info_msg | String | The message from the server corresponding to the last 1xx response code |
| tags | Set | Indicators for various discovered attributes |
| username | Vector | If basic authentication is performed on the request, this is the username |
| password | Vector | If basic authentication is performed on the request, this is the password |
| Scenarios | Anomaly/Sessions | Normal/Sessions |
|---|---|---|
| Scenario 1 | 5000 | 100,000 |
| Scenario 2 | 10,000 | 100,000 |
| Scenario 3 | 20,000 | 100,000 |
| Scenario 4 | 30,000 | 100,000 |
| Scenario 5 | 40,000 | 100,000 |
| Parameters | Value |
|---|---|
| Learning rate | 0.01 |
| Batch size | 256 |
| EPOCH | 100 |
| Method | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| Scenario 1 | 90.48 | 95.12 | 92.75 |
| Scenario 2 | 95.65 | 93.22 | 93.92 |
| Scenario 3 | 95.15 | 93.27 | 93.68 |
| Scenario 4 | 98.77 | 98.75 | 98.73 |
| Scenario 5 | 99.72 | 99.73 | 99.72 |
| Method | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| CNN | 94.34 | 97.31 | 95.80 |
| CNN-GRU | 93.31 | 97.01 | 95.13 |
| RNN | 92.07 | 97.46 | 94.69 |
| Our Method | 99.72 | 99.73 | 99.72 |
| Method | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| CNN | 89.26 | 94.03 | 90.52 |
| CNN-GRU | 90.74 | 94.96 | 91.25 |
| RNN | 91.71 | 96.23 | 92.39 |
| Our Method | 99.72 | 99.73 | 99.72 |
| Method | Precision (%) | Recall (%) | F1-Score (%) |
|---|---|---|---|
| L1 | 95.81 | 96.09 | 95.74 |
| L2 | 96.94 | 96.53 | 96.22 |
| L3 | 99.72 | 99.73 | 99.72 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, L.; Xia, M.; Li, Y.; Xu, J.; Hou, F.; Qi, F. A Multi-Angle Semantic Feature Fusion Method for Web User Behavior Anomaly Detection. Information 2025, 16, 807. https://doi.org/10.3390/info16090807
Wang L, Xia M, Li Y, Xu J, Hou F, Qi F. A Multi-Angle Semantic Feature Fusion Method for Web User Behavior Anomaly Detection. Information. 2025; 16(9):807. https://doi.org/10.3390/info16090807
Chicago/Turabian StyleWang, Li, Mingshan Xia, Yakang Li, Jiahong Xu, Fengyao Hou, and Fazhi Qi. 2025. "A Multi-Angle Semantic Feature Fusion Method for Web User Behavior Anomaly Detection" Information 16, no. 9: 807. https://doi.org/10.3390/info16090807
APA StyleWang, L., Xia, M., Li, Y., Xu, J., Hou, F., & Qi, F. (2025). A Multi-Angle Semantic Feature Fusion Method for Web User Behavior Anomaly Detection. Information, 16(9), 807. https://doi.org/10.3390/info16090807





