1. Introduction
Urban population growth and rising usage of private vehicles have intensified environmental concerns and placed significant strain on transportation infrastructure [
1]. In response, cities are increasingly adopting green mobility strategies such as electric-vehicle sharing and integrated transit platforms to reduce carbon emissions and promote sustainability.
The choice of green mobility systems as the target domain is motivated by both societal and technical imperatives. From a societal perspective, urban transportation is one of the largest contributors to carbon emissions, and the European Union has placed sustainable mobility at the center of the European Green Deal and the Recovery and Resilience Facility (RRF). This study was developed under the A-MoVeR project (“Mobilizing Agenda for the Development of Products & Systems towards an Intelligent and Green Mobility”), which is funded by the Portuguese Recovery and Resilience Plan (RRP) as part of Next Generation EU. From a technical perspective, mobility ecosystems represent one of the most challenging application areas for IAM: they combine heterogeneous IoT devices (vehicles, sensors, smartphones), require low-latency and high-availability authentication, and must safeguard highly sensitive user data such as location and travel patterns. These characteristics make green mobility an ideal stress-test environment to validate the scalability, resilience, and security of IAM solutions.
Concurrently, advances in Internet of Things (IoT) technologies have transformed multiple sectors, with transportation among the most significantly impacted [
2]. Enhanced wireless communication, protocol standardization, and improved device capabilities have enabled the creation of interconnected systems at scale [
3]. In this context, many European cities are adopting Mobility as a Service (MaaS) as a framework for rethinking urban mobility [
4].
IoT underpins Intelligent Transportation Systems (ITS) by enabling real-time communication among vehicles, infrastructure, and users [
5]. It supports dynamic traffic management, vehicle-to-everything (V2X) communication, Software-Defined Vehicles (SDV), and multimodal routing, enhancing both efficiency and user experience [
5,
6,
7].
For example, IoT-enabled electric-vehicle-sharing systems monitor vehicle health, optimize routing, and reduce idle time, contributing to smarter and more sustainable mobility [
5]. Furthermore, real-time data from connected devices power adaptive traffic systems, congestion prediction, and predictive maintenance [
8], reducing emissions and improving overall transportation performance [
9].
Beyond technical innovation, the policy and regulatory context also drives the adoption of secure green mobility. The European Green Deal and United Nations Sustainable Development Goals emphasize digital infrastructures that are both environmentally efficient and secure. In this landscape, mobility platforms must simultaneously achieve sustainability objectives, comply with stringent privacy regulations such as GDPR, and provide trustworthy digital identity management for millions of heterogeneous devices and users.
Traditional transport systems have often relied on siloed authentication or proprietary access control. However, modern MaaS and ITS require scalable, interoperable Identity and Access Management (IAM) solutions that integrate seamlessly across vehicles, charging infrastructures, and user-facing applications. Cloud-native paradigms—and particularly container-orchestrated environments like Kubernetes—have emerged as a foundation for these services, providing elasticity, automated recovery, and strong security primitives. Keycloak, as an open-source IAM platform, has been widely adopted due to its extensibility, standards support (OAuth2, OpenID Connect), and ability to integrate with microservice ecosystems. This combination of Kubernetes and Keycloak provides a unique opportunity to study container-native IAM architectures in practice.
3. Case Study
This case study was conducted within the A-MoVeR (Mobilizing Agenda for the Development of Intelligent Green Mobility Products and Systems) initiative, a Portuguese program focused on accelerating innovation in green, intelligent mobility. As urban transportation becomes increasingly dependent on IoT-enabled systems, the risk of unauthorized access, data breaches, and service disruption also rises.
To address these challenges, we designed and implemented a specialized AAA (Authentication, Authorization, and Accounting) framework using Keycloak, an open-source IAM platform deployed within a Kubernetes-orchestrated container infrastructure. The architecture prioritizes scalability, resilience, and secure integration across distributed applications and IoT workloads. While the framework applies Zero Trust and defense-in-depth principles, it should be noted that no formal symbolic verification of the authentication and authorization protocols was performed. Formal verification tools such as ProVerif or Tamarin could be applied in future work to rigorously analyze the attack surface and validate security attributes under relevant threat models.
4. Results & Discussion
To evaluate the overall effectiveness of the solution presented here, we conducted a comprehensive conceptual and quantitative validation grounded in the existing literature and empirical performance testing. This dual approach ensures both theoretical soundness and practical reliability, comparing the architecture presented here to validated patterns and real-world benchmarks.
Authentication: Support for multiple authentication methods—including SSO, MFA, and federated login—aligns with the requirements identified by Chatterjee and Prinz [
12]. The stateless, JWT-based approach adheres to best practices for distributed environments, as outlined by Gonçalves [
1].
Authorization: The system implements ABAC and PBAC models to enable dynamic, context-aware access control, consistent with the demands of IoT security described by Shrestha [
40].
Scalability: Through Kubernetes-native horizontal scaling and optimized resource management, the architecture achieves elastic scalability. This reflects the scalability principles discussed by Kampa and Vayghan [
13,
41], with database performance emerging as the primary bottleneck under peak loads.
Resilience: Features such as multi-replica deployment, health probes, and automated recovery demonstrate the resilience patterns recommended by Kampa and Wong [
38,
41].
Security: Defense-in-depth, token validation, and secure API gateways address key vulnerabilities noted by Yasrab, Mullinix, and Subramanian [
14,
42,
43].
Operations: CI/CD automation, observability tools, and configuration-as-code reduce maintenance overhead and align with the operational best practices proposed by Badii [
15].
User Experience: Federated and biometric login support, along with seamless token renewal, provide a secure yet user-friendly experience [
1,
12].
Author Contributions
Software, A.S.; Writing—original draft, A.S.; Writing—review and editing, M.J.C.S.R.; Supervision, F.B., A.R. and M.J.C.S.R. All authors have read and agreed to the published version of the manuscript.
Funding
This study was developed under the project A-MoVeR—“Mobilizing Agenda for the Development of Products & Systems towards an Intelligent and Green Mobility”, operation n.° 02/C05-i01.01/2022.PC646908627-00000069, approved under the terms of the call n.° 02/C05-i01/2022—Mobilizing Agendas for Business Innovation, financed by European funds provided to Portugal by the Recovery and Resilience Plan (RRP), in the scope of the European Recovery and Resilience Facility (RRF), framed in the Next Generation UE, for the period from 2021–2026.
Data Availability Statement
The raw data supporting the conclusions of this article will be made available by the authors upon reasonable request to the corresponding author.
Conflicts of Interest
The authors declare no conflicts of interest.
References
- Gonçalves, C.; Sousa, B.; Vuković, M.; Kusek, M. A federated authentication and authorization approach for IoT farming. Internet Things 2023, 22, 100785. [Google Scholar] [CrossRef]
- Sousa, A.; Martins, H.; Khan, D.; Azevedo, J.; Reis, M.J.C.S. Proposal of a Collaborative System to Foster the Concept of Mobility as a Service in the Green Mobility Context. In Proceedings of the Distributed Computing and Artificial Intelligence, Special Sessions I, 21st International Conference; Mehmood, R., Hernández, G., Praça, I., Wikarek, J., Loukanova, R., Monteiro dos Reis, A., Skarmeta, A., Lombardi, E., Eds.; Springer: Cham, Switzerland, 2025; pp. 217–225. [Google Scholar]
- Cui, Y.; Liu, F.; Jing, X.; Mu, J. Integrating Sensing and Communications for Ubiquitous IoT: Applications, Trends and Challenges. arXiv 2021, arXiv:2104.11457. [Google Scholar] [CrossRef]
- Antonialli, F.; Gandia, R.M.; Sugano, J.Y.; Nicolaï, I.; de Miranda Neto, A. Business Platforms for Autonomous Vehicles Within Urban Mobility. WIT Trans. Built Environ. 2019, 186, 175–186. [Google Scholar] [CrossRef]
- Wang, S.; Lehmann, C.; Radeke, R.; Fitzek, F.H.P. Enabling Sustainable Urban Mobility: The Role of 5G Communication in the Mobilities for EU Project. arXiv 2024, arXiv:2412.04006. [Google Scholar] [CrossRef]
- Shamsuddoha, M.; Kashem, M.A.; Nasir, T. A Review of Transportation 5.0: Advancing Sustainable Mobility Through Intelligent Technology and Renewable Energy. Future Transp. 2025, 5, 8. [Google Scholar] [CrossRef]
- Mitropoulos, L.; Kortsari, A.; Mizaras, V.; Ayfantopoulou, G. Mobility as a Service (MaaS) Planning and Implementation: Challenges and Lessons Learned. Future Transp. 2023, 3, 498–518. [Google Scholar] [CrossRef]
- Santos, G.; Nikolaev, N. Mobility as a Service and Public Transport: A Rapid Literature Review and the Case of Moovit. Sustainability 2021, 13, 3666. [Google Scholar] [CrossRef]
- Derawi, M.; Dalveren, Y.; Cheikh, F.A. Internet-of-Things-Based Smart Transportation Systems for Safer Roads. In Proceedings of the 2020 IEEE 6th World Forum on Internet of Things (WF-IoT), New Orleans, LA, USA, 2–16 June 2020; pp. 1–4. [Google Scholar] [CrossRef]
- Ekpo, O.; Casola, V.; De Benedictis, A. Security and Privacy Issues in Mobility-as-a-Service (MaaS): A Systematic Review. In Proceedings of the 2024 19th Annual System of Systems Engineering Conference (SoSE), Tacoma, WA, USA, 23–26 June 2024; pp. 300–307. [Google Scholar] [CrossRef]
- Garroussi, Z.; Legrain, A.; Gambs, S.; Gautrais, V.; Sansò, B. Data privacy for Mobility as a Service. arXiv 2023, arXiv:2310.10663. [Google Scholar] [CrossRef]
- Chatterjee, A.; Prinz, A. Applying Spring Security Framework with KeyCloak-Based OAuth2 to Protect Microservice Architecture APIs: A Case Study. Sensors 2022, 22, 1703. [Google Scholar] [CrossRef] [PubMed]
- Vayghan, L.; Saied, M.; Toeroe, M.; Khendek, F. A Kubernetes controller for managing the availability of elastic microservice based stateful applications. J. Syst. Softw. 2021, 175, 110924. [Google Scholar] [CrossRef]
- Yasrab, R. Mitigating Docker Security Issues. arXiv 2023, arXiv:1804.05039. [Google Scholar] [CrossRef]
- Badii, C.; Bellini, P.; Difino, A.; Nesi, P. Sii-Mobility: An IoT/IoE Architecture to Enhance Smart City Mobility and Transportation Services. Sensors 2019, 19, 1. [Google Scholar] [CrossRef]
- Esposito, C.; Ficco, M.; Gupta, B.B. Blockchain-based authentication and authorization for smart city applications. Inf. Process. Manag. 2021, 58, 102468. [Google Scholar] [CrossRef]
- The Skycloak Team. How IoT Devices are Revolutionizing Identity Management. Available online: https://skycloak.io/blog/how-iot-devices-are-revolutionizing-identity-management/ (accessed on 27 June 2025).
- Jain, P. Identity and Access Management in the Cloud. Int. J. Sci. Res. Comput. Sci. Eng. Inf. Technol. 2025, 11, 1528–1535. [Google Scholar] [CrossRef]
- Rajba, P.; Orzechowski, N.; Rzepka, K.; Szary, P.; Nastaj, D.; Cabaj, K. Identity and Access Management Architecture in the SILVANUS Project. In Proceedings of the 19th International Conference on Availability, Reliability and Security, New York, NY, USA, 30 July–2 August 2024. [Google Scholar] [CrossRef]
- Thakur, M.A.; Gaikwad, R. User identity and Access Management trends in IT infrastructure- an overview. In Proceedings of the 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–4. [Google Scholar] [CrossRef]
- Sharma, D.H.; Dhote, C.; Potey, M.M. Identity and Access Management as Security-as-a-Service from Clouds. Procedia Comput. Sci. 2016, 79, 170–174. [Google Scholar] [CrossRef]
- Indu, I.; Anand, P.R.; Bhaskar, V. Identity and access management in cloud environment: Mechanisms and challenges. Eng. Sci. Technol. Int. J. 2018, 21, 574–588. [Google Scholar] [CrossRef]
- Singh, C.; Thakkar, R.; Warraich, J. IAM Identity Access Management—Importance in Maintaining Security Systems within Organizations. Eur. J. Eng. Technol. Res. 2023, 8, 30–38. [Google Scholar] [CrossRef]
- TekSlate. Okta vs. Auth0: Detailed Comparison. Available online: https://tekslate.com/okta-vs-auth0 (accessed on 19 December 2024).
- Okta. Okta: Identity for the Internet. Available online: https://www.okta.com/ (accessed on 20 December 2024).
- Gluu. Gluu—Identity and Access Management. 2024. Available online: https://gluu.org/?utm_source=saasworthy.com&utm_medium=cpc&utm_banner=2998550&sub1=2998550&visitorid=2998550 (accessed on 20 December 2024).
- Software, D. IdentityServer—Secure Your Apps and APIs. Available online: https://duendesoftware.com/products/identityserver (accessed on 21 December 2024).
- Sersemis, A.; Papadopoulos, A.; Spanos, G.; Lalas, A.; Votis, K.; Tzovaras, D. A Novel Cybersecurity Architecture for IoV Communication. In Proceedings of the 25th Pan-Hellenic Conference on Informatics, Volos, Greece, 26–28 November 2021; pp. 357–361. [Google Scholar] [CrossRef]
- Guija, D.; Siddiqui, M.S. Identity and Access Control for micro-services based 5G NFV platforms. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018. [Google Scholar] [CrossRef]
- Al Rahat, T.; Feng, Y.; Tian, Y. AuthSaber: Automated Safety Verification of OpenID Connect Programs. In Proceedings of the 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, UT, USA, 14–18 October 2024; pp. 2949–2962. [Google Scholar] [CrossRef]
- James, M.; Newe, T.; O’Shea, D.; O’Mahony, G.D. Authentication and Authorization in Zero Trust IoT: A Survey. In Proceedings of the 2024 35th Irish Signals and Systems Conference (ISSC), Belfast, UK, 13–14 June 2024; pp. 1–7. [Google Scholar] [CrossRef]
- Amiri, M.J.; Agrawal, D.; El Abbadi, A. Permissioned Blockchains: Properties, Techniques and Applications. In Proceedings of the 2021 International Conference on Management of Data, Virtual, 20–25 June 2021; pp. 2813–2820. [Google Scholar] [CrossRef]
- Sciullo, L.; De Marchi, A.; Gigli, L.; Palmirani, M.; Vitali, F. AAA: A blockchain-based architecture for ethical, robust authenticated anonymity. In Proceedings of the 2024 International Conference on Information Technology for Social Good, Bremen, Germany, 4–6 September 2024; p. 1. [Google Scholar] [CrossRef]
- Jin, X.; Omote, K. An efficient blockchain-based authentication scheme with transferability. PLoS ONE 2024, 19, e0310094. [Google Scholar] [CrossRef] [PubMed]
- Alilwit, N. Authentication Based on Blockchain. Ph.D. Thesis, Embry-Riddle Aeronautical University, Daytona Beach, FL, USA, 2020. [Google Scholar]
- Thakur, M. Authentication, Authorization and Accounting with Ethereum Blockchain, 2017. URN:NBN:fi:hulib-201711145693. Available online: https://helda.helsinki.fi/items/8d0dad04-07f5-4a0d-9ed7-64db26b1e960 (accessed on 3 February 2024).
- Kubernetes Documentation. Kubernetes Concepts Overview. 2024. Available online: https://kubernetes.io/docs/concepts/overview/ (accessed on 3 February 2024).
- Wong, A.Y.; Chekole, E.G.; Ochoa, M.; Zhou, J. Threat Modeling and Security Analysis of Containers: A Survey. arXiv 2021, arXiv:2111.11475. [Google Scholar] [CrossRef]
- MaaS Alliance. MaaS Market Playbook; MaaS Alliance: Brussels, Belgium, 2021; Available online: https://maas-alliance.eu/wp-content/uploads/sites/7/2021/03/05-MaaS-Alliance-Playbook-FINAL.pdf (accessed on 3 February 2024).
- Shrestha, R.; Bertin, E. Access Control for IoT: A Survey of Existing Research, Dynamic Policies and Future Directions. Sensors 2023, 23, 1805. [Google Scholar] [CrossRef]
- Kampa, S. Navigating the Landscape of Kubernetes Security Threats and Challenges. J. Knowl. Learn. Sci. Technol. 2024, 3, 274–281. [Google Scholar] [CrossRef]
- Mullinix, S.P.; Konomi, E.; Townsend, R.D.; Parizi, R.M. On Security Measures for Containerized Applications Imaged with Docker. arXiv 2020, arXiv:2008.04814. [Google Scholar] [CrossRef]
- Subramanian, N.; Jeyaraj, A. Recent security challenges in cloud computing. Comput. Electr. Eng. 2018, 71, 28–42. [Google Scholar] [CrossRef]
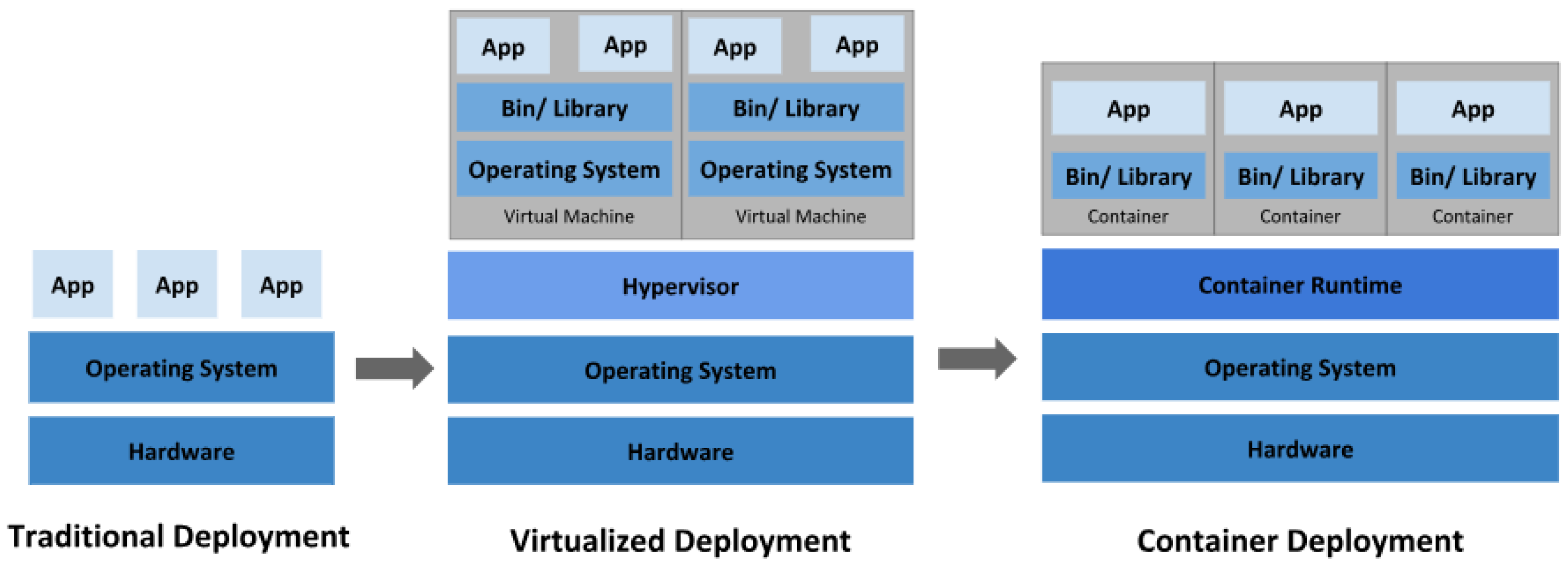
Figure 1.
Comparison of layered architectures: traditional, virtualized, and containerized environments (adapted from [
37]).
Figure 2.
JWT-based access request flow. The client authenticates with the authorization server (SAuth) to obtain a JWT token (Stage 1). After successful authentication, the token is returned to the client (Stage 2), which uses it to request access to a protected service (Stage 3). The service validates the token and grants access to the secure feature (Stage 4).
Figure 3.
Authentication flow for token acquisition and identity verification. The user submits credentials via the login page, which are validated before access is granted and tokens are issued for session management.
Figure 4.
Authorization flow access to a protected resource. The process includes login and token issuance, token validation, role-based access control, and token renewal. Invalid roles or expired tokens result in access denial or reauthentication.
Figure 5.
Proxmox dashboard showing the virtualized infrastructure used in the case study. Three VMs labeled k8s-1, k8s-2, and k8s-3 form the Kubernetes cluster. Additional VMs include linux-app (IAM client), and OS templates (ubuntu-template, debian-template). Resource usage for each node is displayed in real time.
Figure 6.
High-level design of the virtual infrastructure used for the prototype deployment. The architecture includes a Kubernetes cluster composed of three nodes (Node 1–3) running within virtual machines, alongside a separate Linux-based application VM. This setup replicates a realistic IoT-enabled mobility environment for AAA system validation.
Figure 7.
Keycloak administrative interface showing the configuration of realm-level roles within the web_app realm. Roles such as end_user, fabricante, and vendedordefine fine-grained access control across different user types. These roles are essential for implementing context-aware and role-based authorization in the green mobility ecosystem.
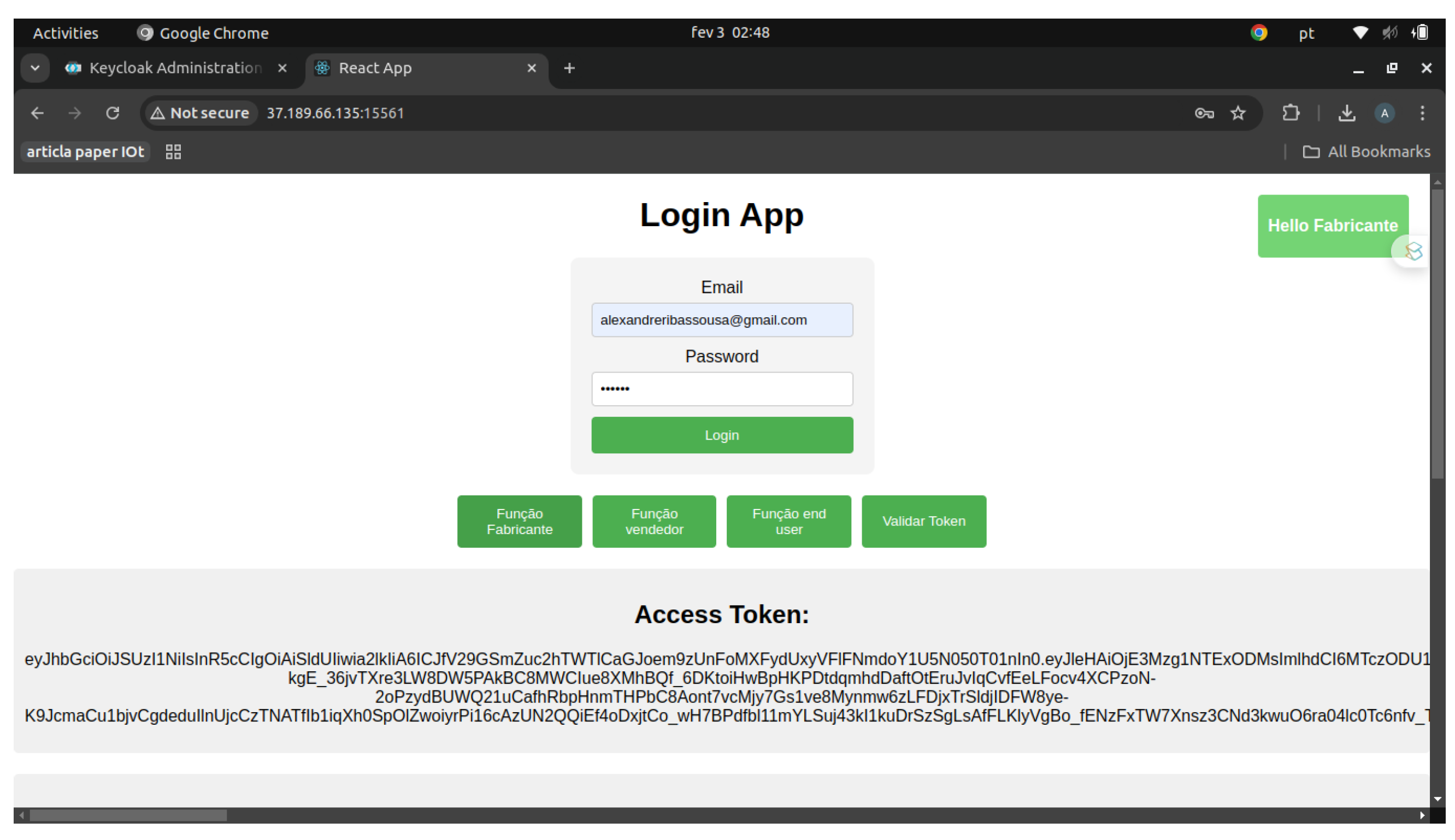
Figure 8.
Web application demonstrating successful IAM integration using Keycloak. Upon authentication, the user—assigned the fabricante role—is granted access to role-specific UI elements and receives a signed access token (JWT). The application dynamically renders role-based content and enables token validation workflows, showcasing the effectiveness of RBAC in the front end.
Figure 9.
Mobile application demonstrating successful IAM integration with Keycloak. The user authenticates using credentials, receives a signed JWT access token, and is granted UI-level permissions based on the assigned Vendedor role. The app adapts role-specific functionality and confirms access rights via a contextual success message.
Figure 10.
Linux-based command-line application demonstrating successful IAM token acquisition and role-based access. After being authenticated via Keycloak, the user receives a JWT token and gains access to the fabricante feature based on their assigned role.
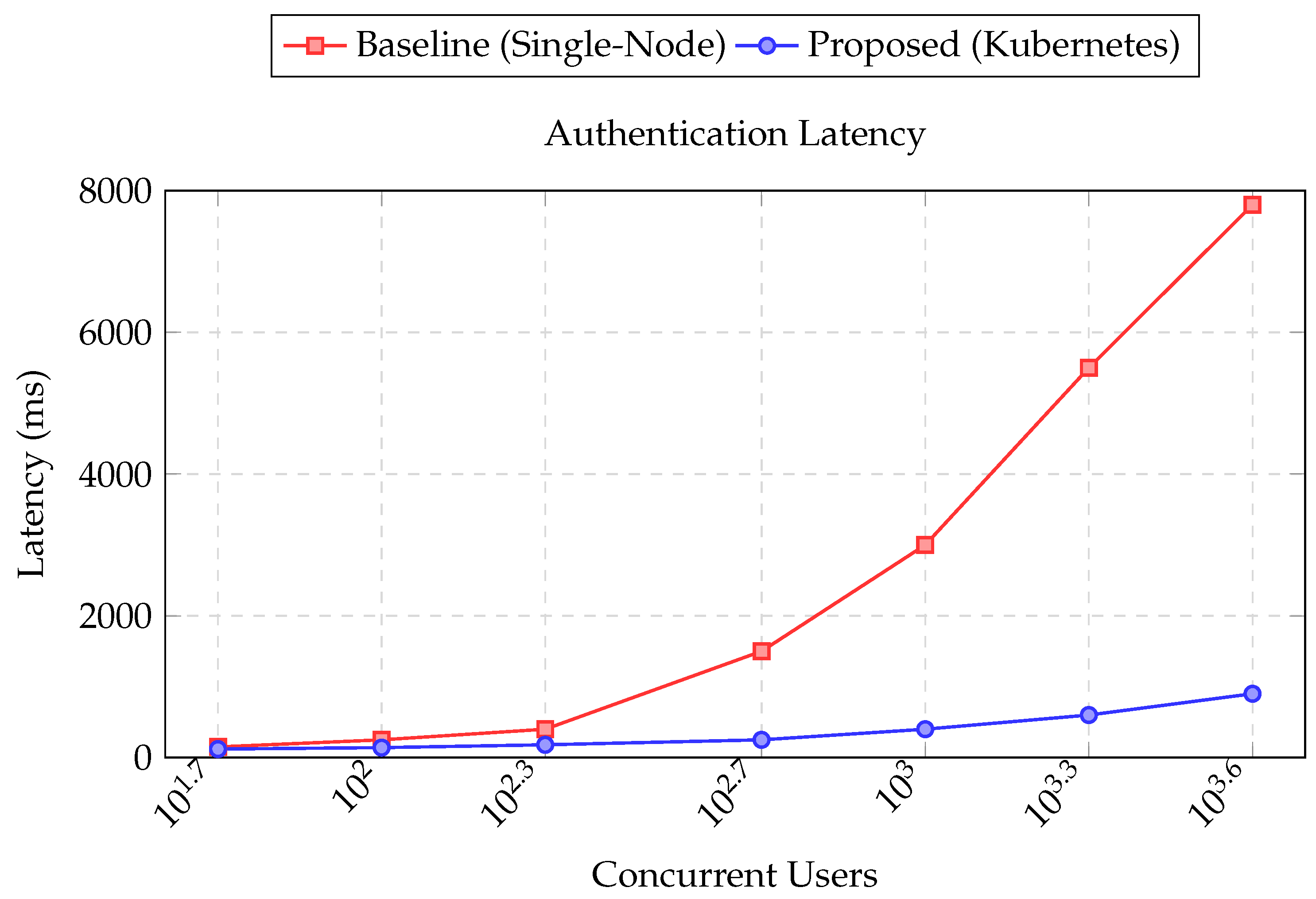
Figure 11.
Average authentication latency across varying concurrency levels. The baseline monolithic deployment shows a steep rise in latency beyond 200 users, while the proposed Kubernetes-based architecture maintains subsecond response times up to 4000 concurrent users.
Figure 12.
Throughput comparison under increasing concurrency. The container-orchestrated Keycloak deployment exhibits near-linear scalability, achieving over 40,000 requests per second at peak load, while the monolithic baseline saturates early and degrades after 500 users.
Table 1.
Key challenges in green mobility ecosystems.
| Category | Challenge |
|---|
| Data & Security | Privacy of sensitive user and operational data. |
| Development | Misconfigurations resulting in vulnerabilities in applications. |
| Access | Weak AAA (Authentication, Authorization, Auditing) implementations. |
| Architecture | Single points of failure that reduce system availability. |
| Availability | Denial-of-Service (DoS) attacks that can disrupt services. |
Table 2.
Comparative Analysis of IAM Solutions.
| Feature | Auth0 | Okta | Gluu | IdentityServer | Keycloak | Blockchain-Based IAM |
|---|
| Hosting | Cloud-only (SaaS) | Cloud-managed | Self-hosted or cloud-ready | Self-hosted (.NET) | Self-hosted/containerized | Decentralized (distributed nodes) |
| Customization | APIs, rules, hooks | UI + policy rules | Scripting, workflows | Deep .NET extensibility | Themes, login flows, plugins | Smart contracts, on-chain policies |
| Protocol Support | OAuth2, OIDC, SAML, WebAuthn | OAuth2, OIDC, SAML, WS-Fed | OAuth2, UMA, SAML, FIDO2 | OAuth2, OIDC, WS-Fed | OAuth2, OIDC, LDAP, FIDO2 | DIDs, VCs, cryptographic proofs |
| MFA Support | OTP/SMS | TOTP, Okta Verify | OTP, WebAuthn, FIDO2 | Plug-in MFA | FIDO2, TOTP | Wallets, key-pairs |
| User Federation | Social + LDAP/DB | Out-of-box providers | Configurable connectors | Manual setup | LDAP + social federation | Self-sovereign identity |
| API Integration | Extensive APIs | SSO + auth APIs | REST + LDAP APIs | .NET-focused APIs | REST APIs + adapters | Ledger APIs, DID resolution |
| Scalability | Cloud-native | Enterprise-grade SLA | Manual HA setup | .NET-native scaling | Kubernetes-native scaling | Chain-dependent |
| Cost Model | Freemium | Subscription | Free core + support | Free (.NET license) | Open-source (Red Hat support optional) | Transaction-based (e.g., gas fees) |
| Ease of Use | Dev-focused docs | Admin UI–oriented | Steep learning curve | Dev-intensive | Moderate, active community | Crypto-heavy learning curve |
Table 3.
Framework Layers.
| Layer | Primary Components | Purpose |
|---|
| Aplication | IoT Devices, Mobile/Web applications, backend services. | Interface for users. |
| Integration | Istio, cert-manager, MetalLB. | Secure service mesh management, TLS certificates and load balancer. |
| IAM | Keycloak, PostgreSQL, SMTP. | Centralized management access and identities. |
| Access | API Gateway (EMQX para MQTT, middleware JS for HTTP). | Routing and gateway for services. |
| Monitoring | Stack ELK, Prometheus, Grafana. | Observability, event logging and performance metrics. |
Table 4.
Technologies Employed in the Prototype.
| Category | Technologies |
|---|
| Orchestration | Kubernetes (1.30), Docker (26.1) |
| Security | Keycloak (24.0.4), Istio (1.22), cert-manager (1.15) |
| Gateways | EMQX (5.7.1), custom JavaScript middleware (ECMAScript 2023 (ES14) Standard) |
| Monitoring | ELK Stack (8.13), Prometheus (2.53), Grafana (11.0) |
| DevOps | Ansible (10.0), Helm (3.15), GitLab (17.1), VS Code (1.90), Android Studio (Koala 2024.1.1) |
| Protocols | OAuth 2.0, OpenID Connect (1.0 Standard), MQTT (5.0 Standard), HTTPS (1.3) |
| Languages/Frameworks | JavaScript (ECMAScript 2023 (ES14) Standard), Python (3.12.4), React (18.3.1), Flutter (3.22) |
| Storage/Email | PostgreSQL (16.3 Standard ), Mailu (2.0) |
Table 5.
System Configuration for Comparative Analysis.
| Parameter | Baseline (Monolithic) | Proposed (Orchestrated) | Rationale |
|---|
| Deployment Model | Single VM | Three-Node Kubernetes Cluster | Evaluate container orchestration impact. |
| Total vCPU | 4 vCPU | 6 vCPU (two per worker) | Ensure balanced CPU resources. |
| Total RAM | 8 GB | 12 GB | Account for Kubernetes overhead. |
| Keycloak Version | 26.0.7 | 26.0.7 | Maintain test consistency. |
| PostgreSQL Version | 15.6 | 15.6 (StatefulSet) | Maintain test consistency. |
| Networking | Host Networking | Kubernetes + Istio | Assess service mesh impact. |
Table 6.
Comparative analysis of the proposed IAM architecture against the baseline (monolithic Keycloak). Results are reported as mean ± SD, with 95% confidence intervals (CIs) provided in footnotes.
| Metric | Baseline (Monolithic) | Proposed (Kubernetes-Orchestrated) |
|---|
| Initial Startup Time (minutes) | 4.5 ± 0.2 1 | 0.75 ± 0.1 2 |
| Idle Memory Usage (GB) | 3.8 ± 0.2 3 | 0.85 ± 0.1 4 |
| Peak Throughput (req/s) | 480 ± 40 5 | 2100 ± 95 6 |
| p99 Latency at 200 req/s (ms) | 150 ± 12 7 | 95 ± 9 8 |
Table 7.
Comparative PostgreSQL metrics under peak load for the proposed IAM architecture versus the baseline (monolithic Keycloak).
| Metric | Baseline (Monolithic) | Proposed (Kubernetes-Orchestrated) |
|---|
| CPU Usage (%) | 88 | 92 |
| I/O Wait (%) | 22 | 35 |
| Queries per Second | 850 | 1500 |
| Memory Usage (GB) | 2.4 | 2.8 |
Table 8.
Resilience Test Results: System Recovery Time (TTR).
| Fault Scenario | Detection Method | Recovery Action | Mean Time to Recovery (TTR) |
|---|
| Pod Failure (Orchestrated) | Kubelet Liveness Probe | Controller Manager creates new pod | 52 s |
| Node Failure (Orchestrated) | Kubelet Heartbeat Timeout | Scheduler reschedules pods | 3.5 min |
| Process Crash (Baseline) | External Monitoring/Manual | Manual restart | >5 min |
| VM Crash (Baseline) | Hypervisor Alert/Manual | Manual reboot | >10 min |
| Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).