PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles
Abstract
1. Introduction
- Multi-factor authentication integration: by combining PUF’s hardware characteristics with user’s biometrics, the scheme employs a fuzzy extractor to handle the noise of biometric data, thus eliminating the risk of storing the raw biometric templates in plaintext. This approach enhances the reliability of identity authentication and resistance to spoofing.
- Dynamic privacy protection mechanism: a dynamic pseudonym system is introduced to ensure vehicle identity anonymity and session key untraceability while achieving perfect forward secrecy in the protocol.
- Lightweight design: hash functions and “exclusive or” (XOR) operations replace traditional public key cryptography, significantly reducing computational complexity. Simultaneously, dynamic random number updating and timestamp validation mechanisms can defend against replay attacks and ensure forward security.
2. Related Works
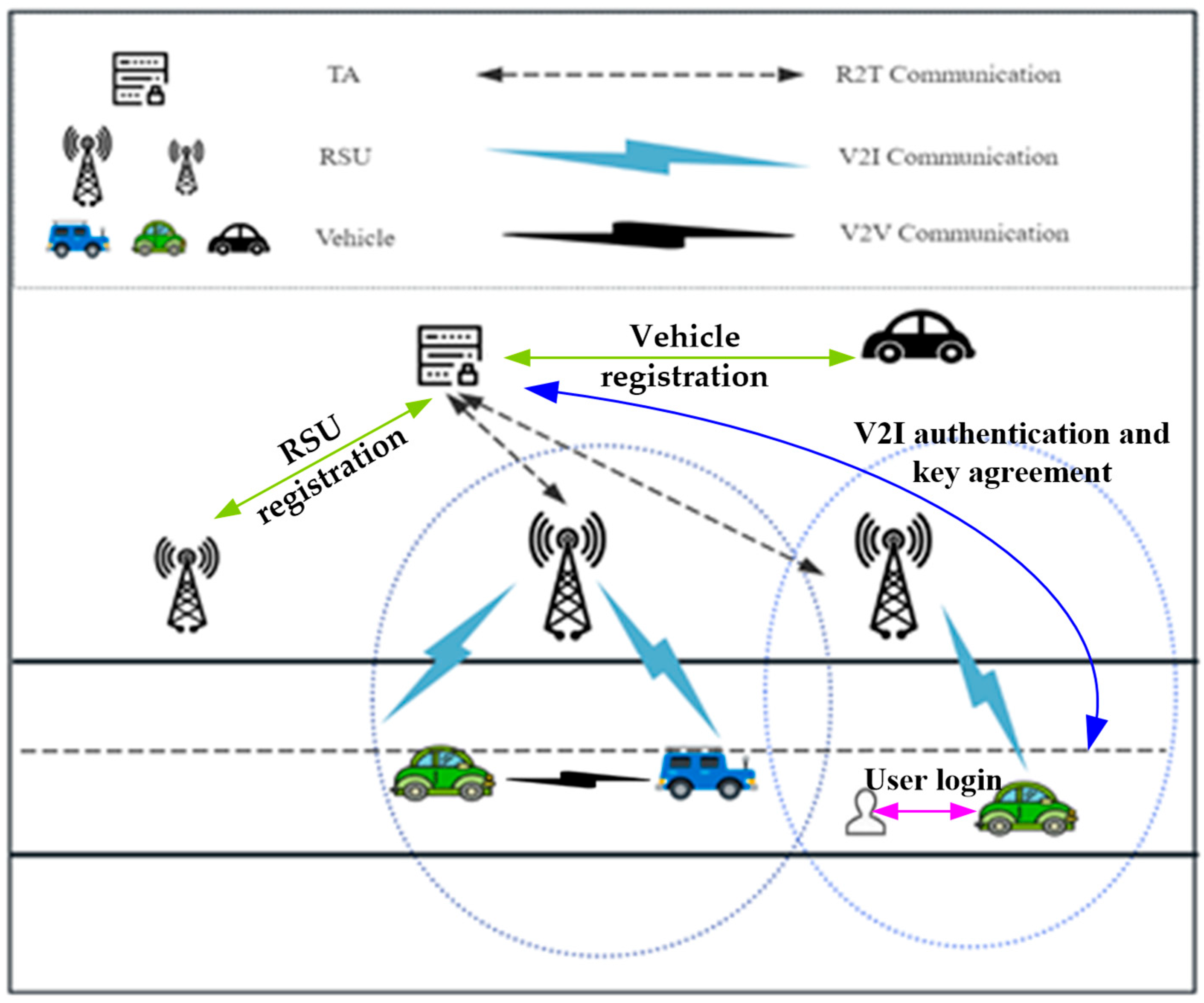
3. System Model
3.1. Network Model
3.2. Threat Model
- Intercepting communications between nodes;
- Tampering with transmitted messages;
- Forging or deleting messages.
- Obtaining secret information and session states through session hijacking attacks;
- Conducting ephemeral secret leakage (ESL) attacks;
- Performing physical capture attacks on vehicle nodes.
4. Proposed PMAKA-IoV Protocol
4.1. Initialization Phase
4.2. Registration Phase
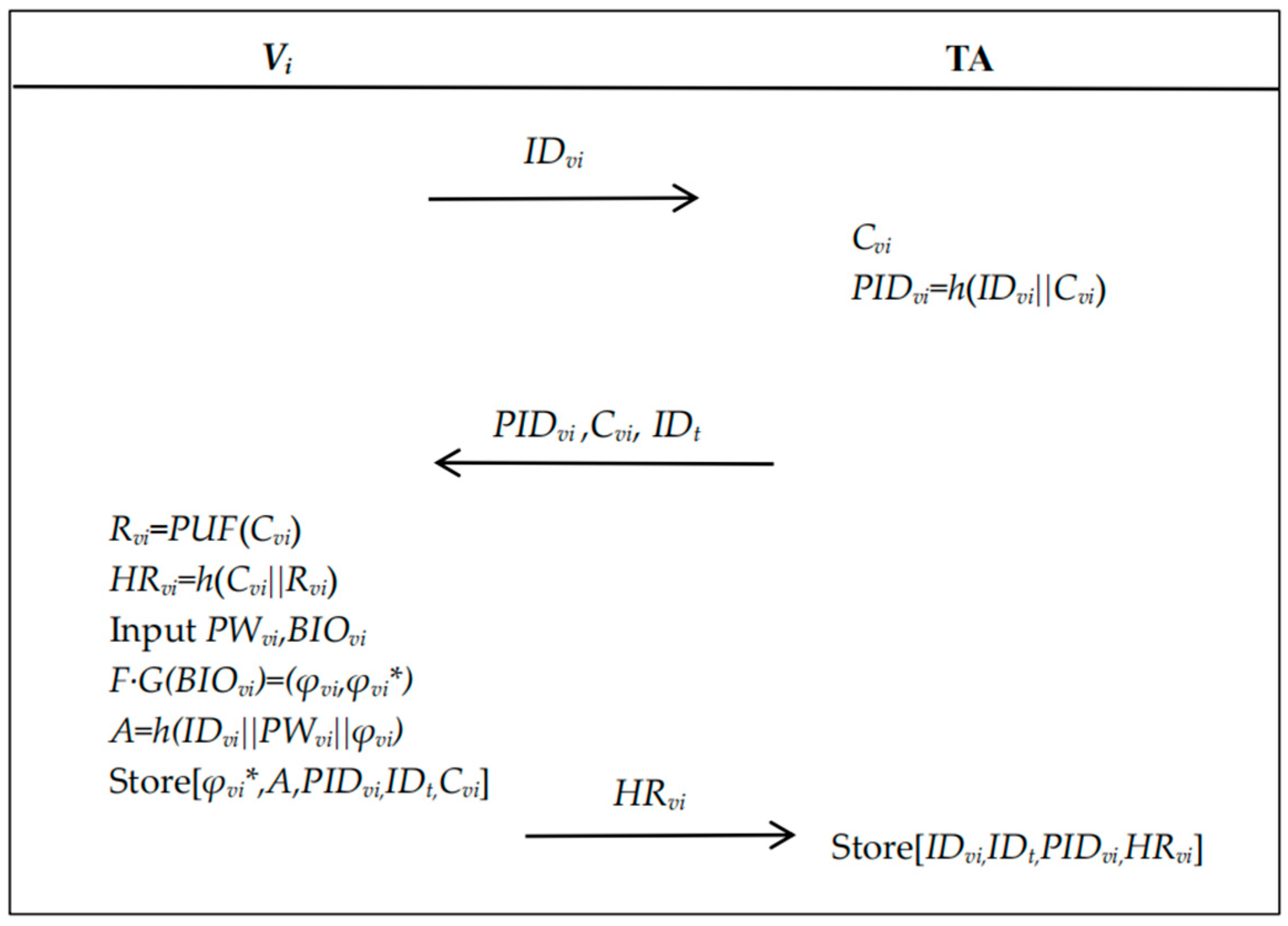
4.2.1. Vehicle Registration
- 1.
- The vehicle Vi generates its identity IDvi and sends it to the TA.
- 2.
- Upon receiving IDvi, the TA queries its database to verify whether IDvi already exists. If not, the TA generates a challenge Cvi, computes the pseudonym PIDvi = h(IDviCvi), and sends {PIDvi, Cvi, IDt} to Vi, where IDt is the identity of the TA.
- 3.
- After receiving the message, Vi computes the response Rvi = PUF(Cvi) and HRvi = h(CviRvi). The user of Vi then inputs its password PWvi and biometric data BIOvi. Subsequently, Vi calculates F·G(BIOvi) = (φvi, φvi*) and A = h(IDviPWviφvi). Finally, Vi stores [φvi*, A, PIDvi, IDt, Cvi] in the OBU and sends {HRvi} to the TA.
- 4.
- The TA securely stores [IDvi, PIDvi, IDt, HRvi] in its database.
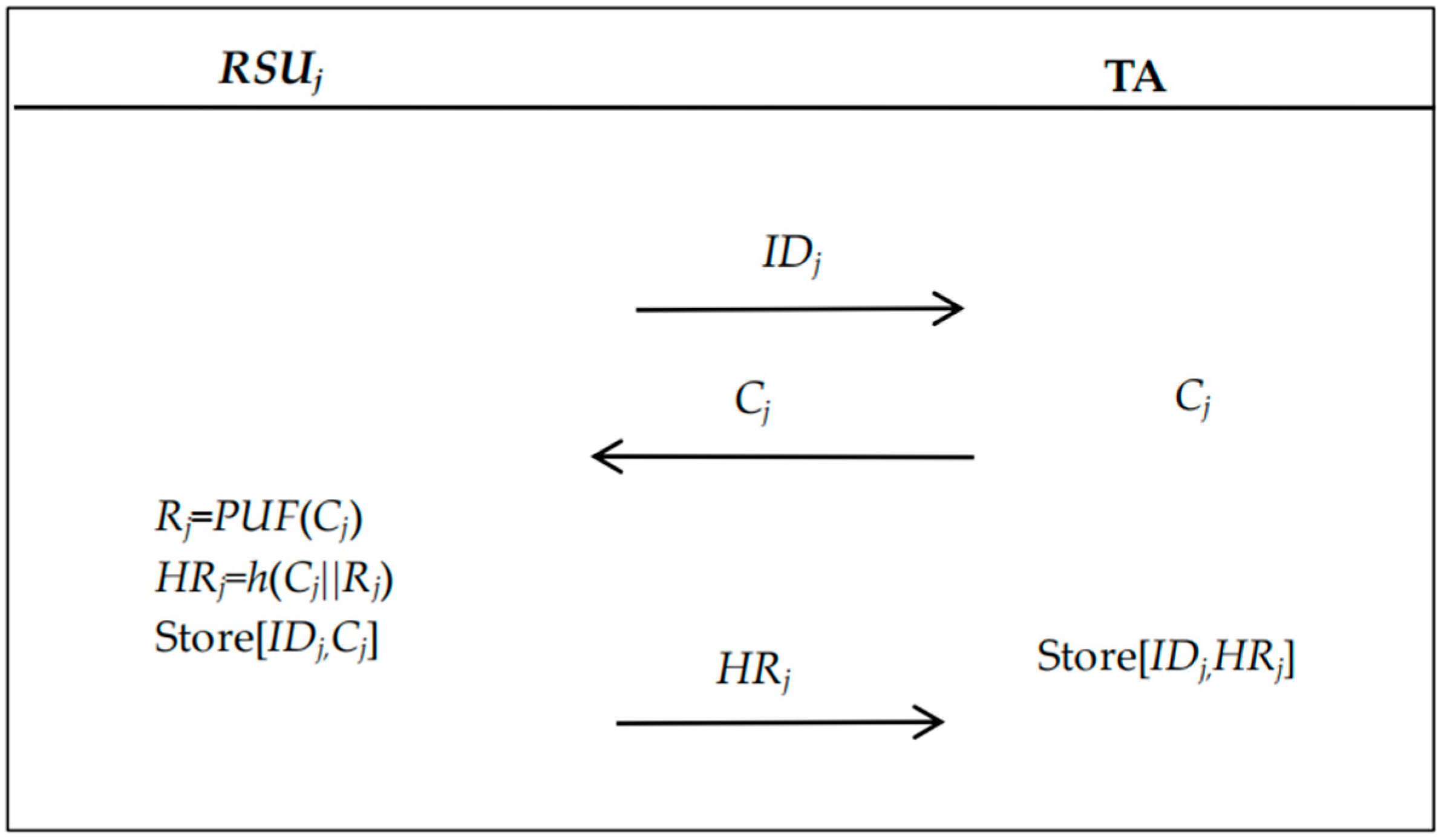
4.2.2. RSU Registration
- 1.
- RSUj sends its identity IDj to the TA, where RSUj is the RSU.
- 2.
- The TA generates a challenge Cj and sends it to RSUj.
- 3.
- Upon receiving the message, RSUj computes the response Rj = PUF(Cj) and HRj = h(CjRj). It then stores [IDj, Cj] locally and sends HRj to the TA.
- 4.
- The TA securely stores [IDj, HRj] in its database.
4.3. Login Phase
- 1.
- The user of Vi inputs IDvi, PWvi, and BIOvi.
- 2.
- By using the fuzzy extractor, Vi calculates φvi = F·R(BIOvi,φvi*) and computes A′ = h(IDviPWviφvi). Vi then verifies whether the computed A′ matches the stored security parameter A. If they are equal, the login succeeds.
4.4. V2I Authentication and Key Agreement Phase
- 1.
- Vi computes Rvi = PUF(Cvi) and HRvi = h(CviRvi), generates a random number ri and a timestamp T1, and then calculates A1 = IDviHRviIDtri and M1 = h(IDjPIDviHRviriA1T1). Finally, Vi sends {PIDvi,M1,A1,T1} to RSUj.
- 2.
- Upon receiving the message, RSUj generates a timestamp T2. If |T2-T1|<∆T, the message is discarded, i.e., verifying the freshness of T1. Otherwise, RSUj generates a random number rj; computes Rj = PUF(Cj), HRj = h(CjRj), A2 = IDjHRjrj, and M2 = h(M1IDtHRjrjA2T2); and then sends {PIDvi,IDj,,M2,A1,A2,T1,T2} to the TA.
- 3.
- The TA verifies the freshness of T2. By using PIDvi, it retrieves HRvi and IDvi, computes ri = IDviHRviIDtA1, validates M1 = h(IDjPIDviHRviriA1T1), and retrieves HRj based on IDj. Next, it computes rj = IDjHRjA2 and M2′ = h(M1IDtHRjrjA2T2) and then verifies whether M2′ = M2. If this is valid, the TA generates a new random number rtnew, a timestamp T3, and a master key mk. It computes PIDvinew = h(IDviCvirt), X = mkHRvirt, Y = mkHRjrt, A3 = rj(rirt), M3 = h(IDjmkrjrtHRjT3), and M4 = h(IDvimkrirtHRviT3)). The TA stores PIDvinew and sends {A3, M3, M4, X, Y, T3} to RSUj.
- 4.
- RSUj generates timestamp T4; verifies the freshness of T3; computes (rirt) = rjA3, mk = YHRjrt, and M3′ = h(IDjmkrjrtHRjT3); and then checks whether M3′ = M3. If this is valid, RSUj calculates the session key SKij = h(IDjPIDvirirj rtmk), computes A4 = ri(rjrt) and M5 = h(IDjM4PIDviSKijT4), and then sends {A4,X,M4,M5,T3,T4} to Vi.
- 5.
- Vi verifies the freshness of T4; computes (rjrt) = riA4, mk = XHRvirt, and M4′ = h(IDvimkrirtHRviT3); and then checks whether M4′ = M4. If this is valid, Vi computes M5′ = h(IDjM4PIDviSKijT4) and verifies whether M5′ = M5. If this is valid, Vi updates PIDvinew in the OBU.

5. Security Analysis
5.1. Informal Analysis
- 1.
- Physical Capture Attack
- 2.
- Replay Attack
- 3.
- Man-in-the-Middle Attack
- 4.
- Session Key Disclosure Attack
- 5.
- Desynchronization Attack
- 6.
- Mutual Authentication
- 7.
- Anonymity and Untraceability
- 8.
- Perfect Forward Secrecy
- 9.
- Denial-of-Service (DoS) Attack
- 10.
- Impersonation Attack
- 11.
- ESL Attacks
5.2. Formal Analysis
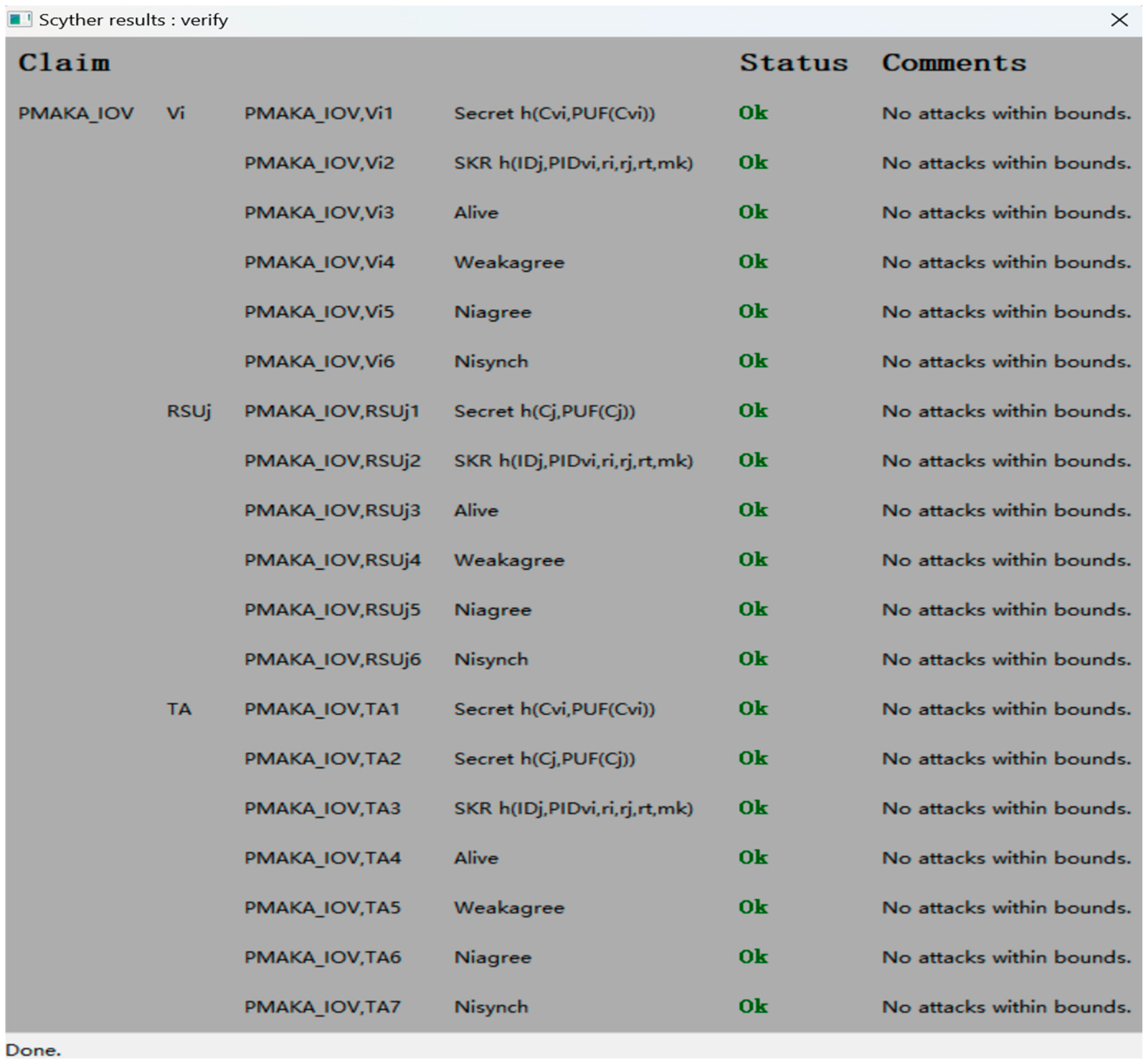
5.3. Security Verification Based on Scyther
- 1.
- No Successful Attack Traces: Scyther exhaustively explored all possible interleavings of protocol runs and failed to find any violations of the specified security properties. For example, the attempts to forge M3 = h(IDjmkrjrtHRjT3) without knowledge of HRj or mk were detected as invalid.
- 2.
- Mutual Authentication Guarantees: The tool verified that Vvi and Rj mutually authenticate each other through TA-mediated validation of M1, M2, M4, and M5. Any tampering with these messages will destroy the integrity of the hash-chain, thus triggering the termination of the protocol.
- 3.
- Session Key Confidentiality: Scyther confirmed that SKij remains secret even if the long-term key mk is compromised, as SKij relies on ephemeral values erased after each session.
- 4.
- Desynchronization Resilience: The dual pseudonym storage of this protocol ensures continuity, even though messages are lost or tampered. Scyther validated that the TA retains both versions until successful key confirmation, preventing denial-of-service via forced state mismatches.
5.4. Security Comparison
6. Performance Analysis
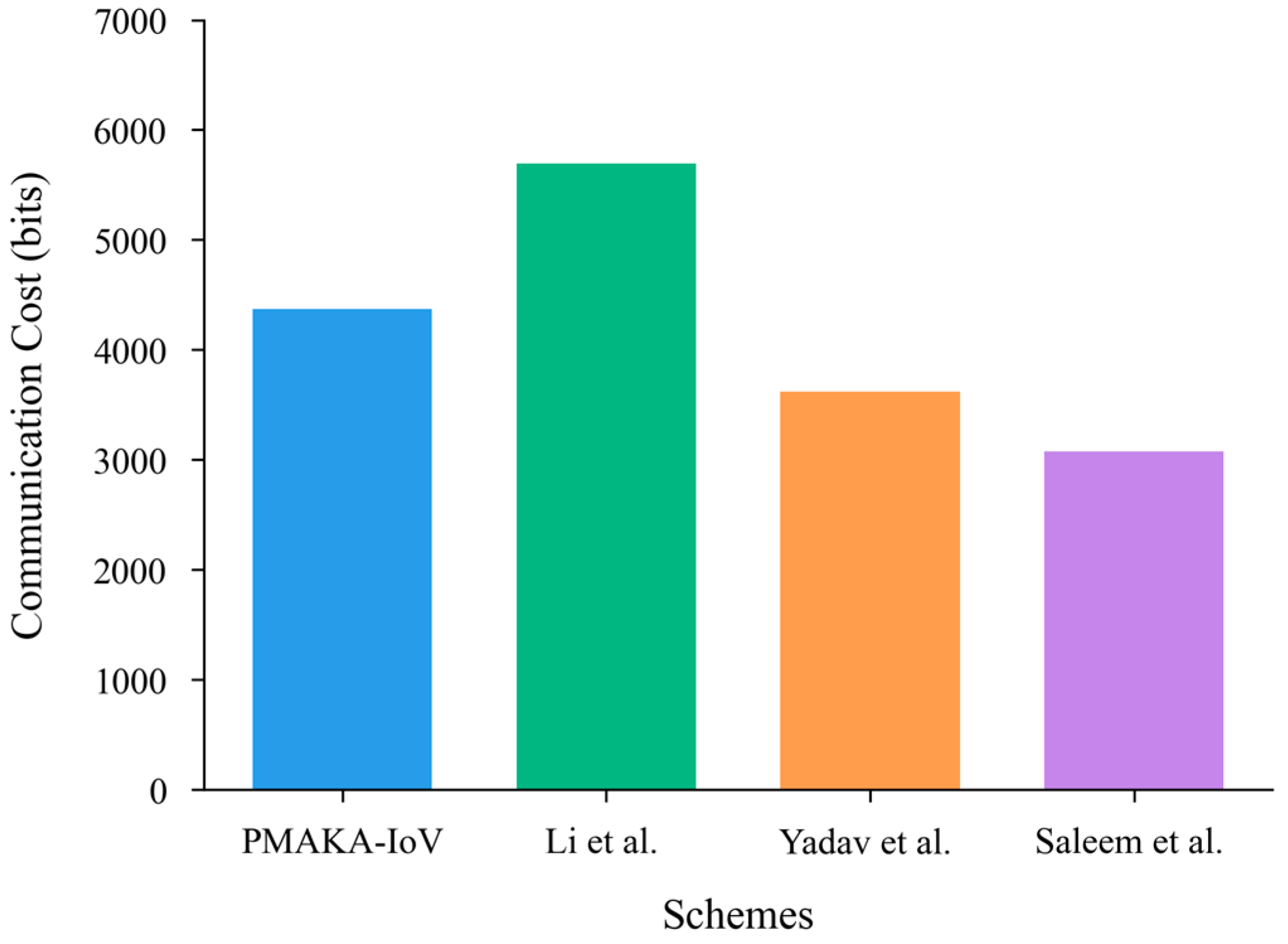
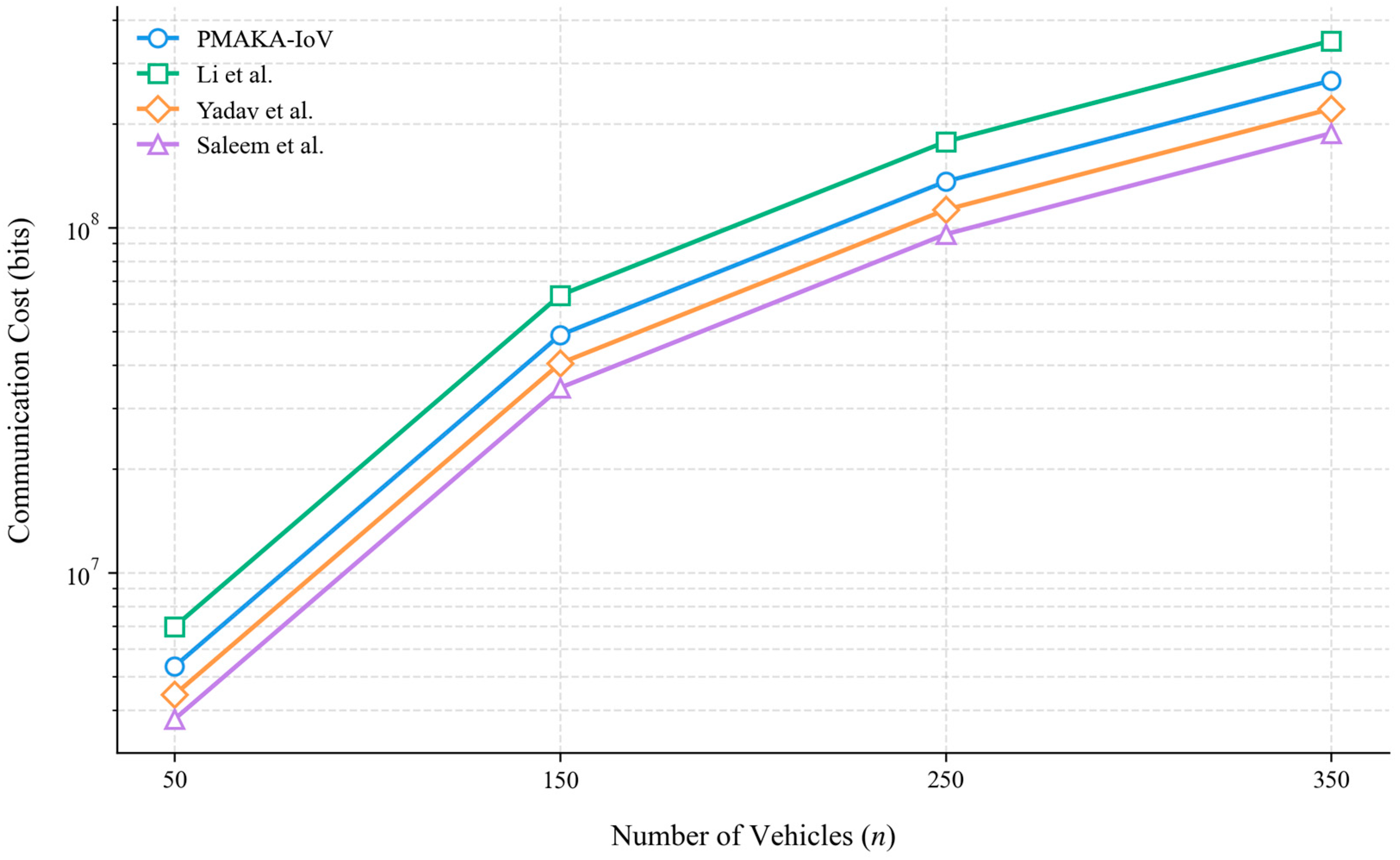
6.1. Communication Cost
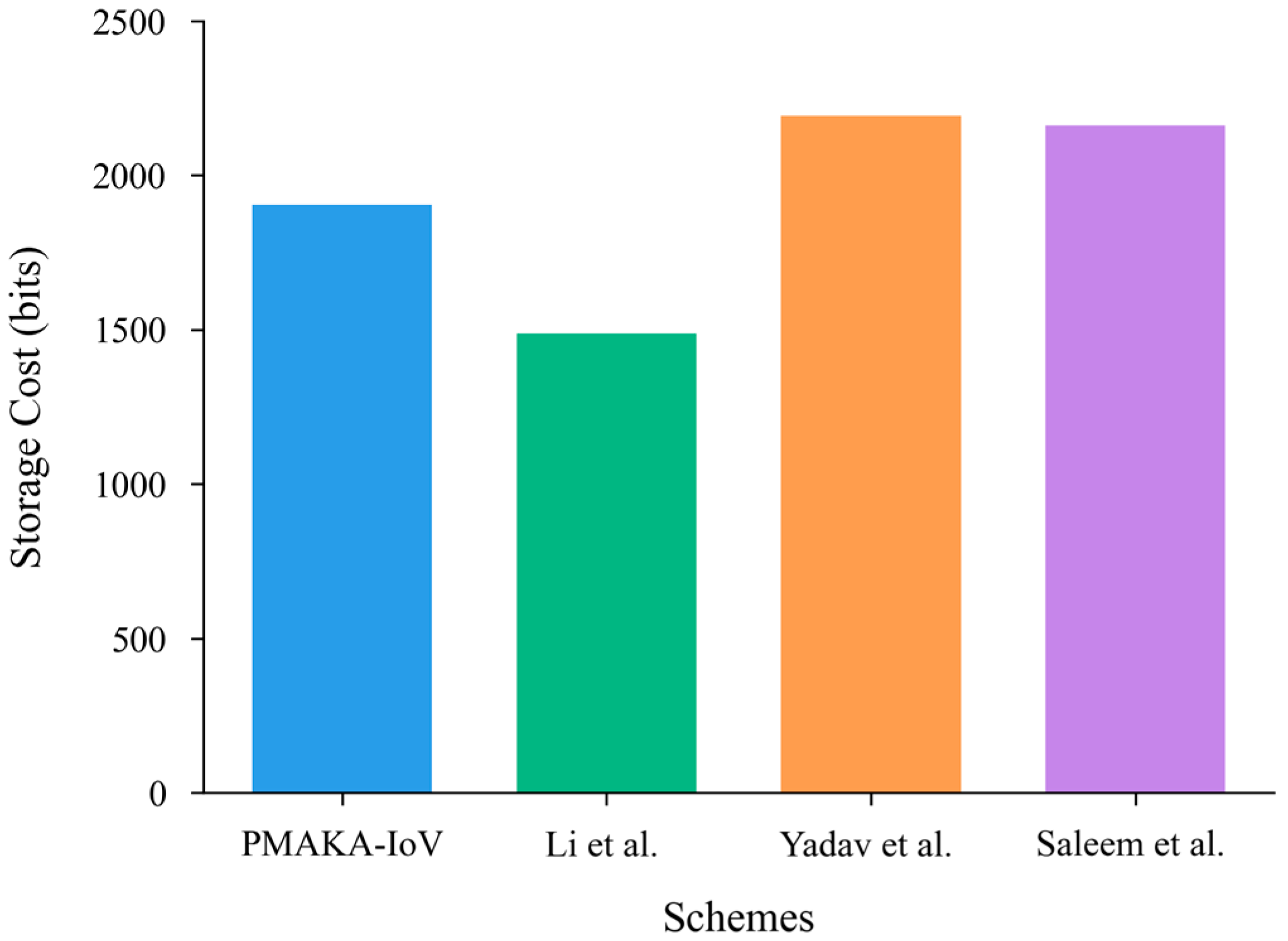
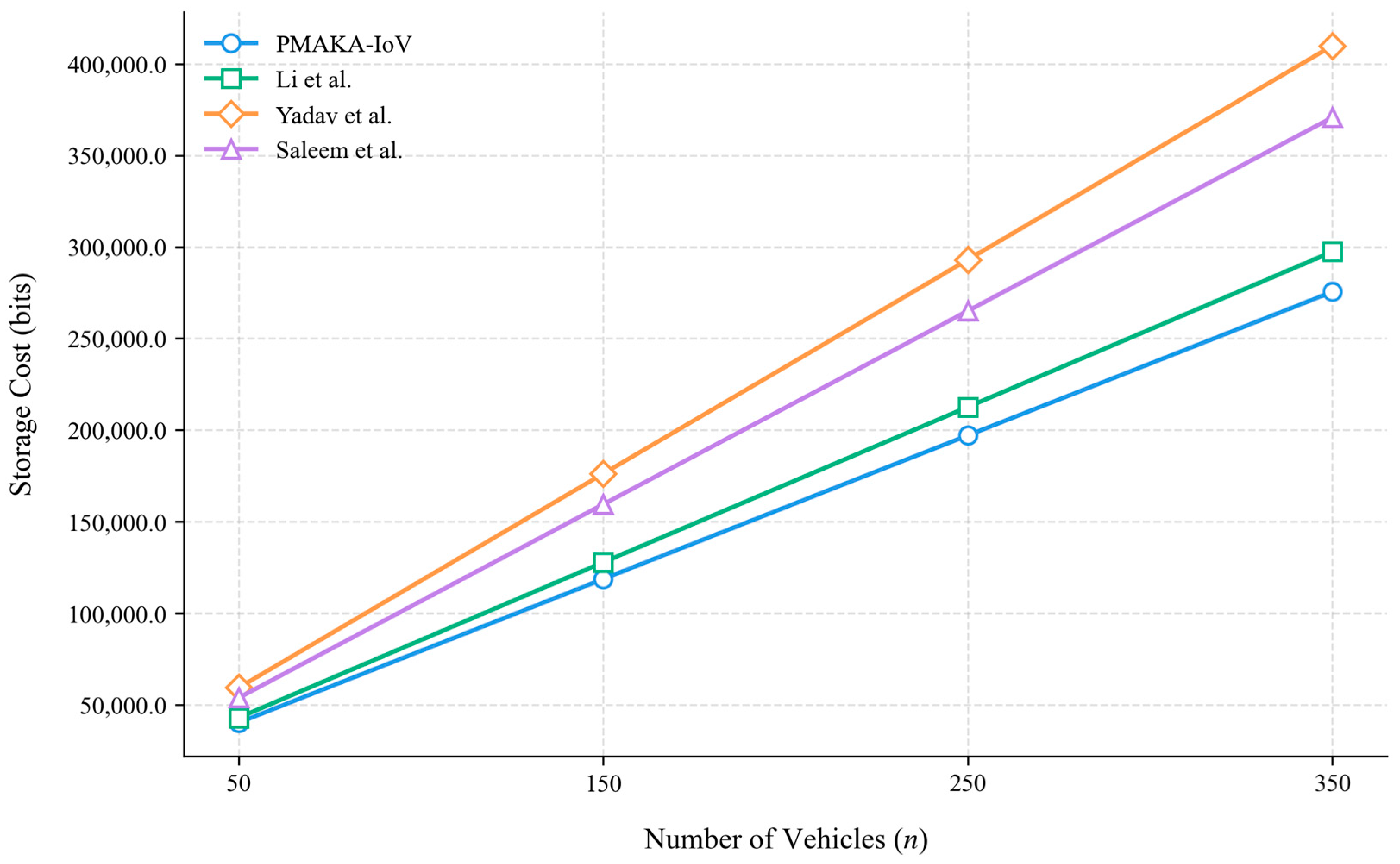
6.2. Storage Cost
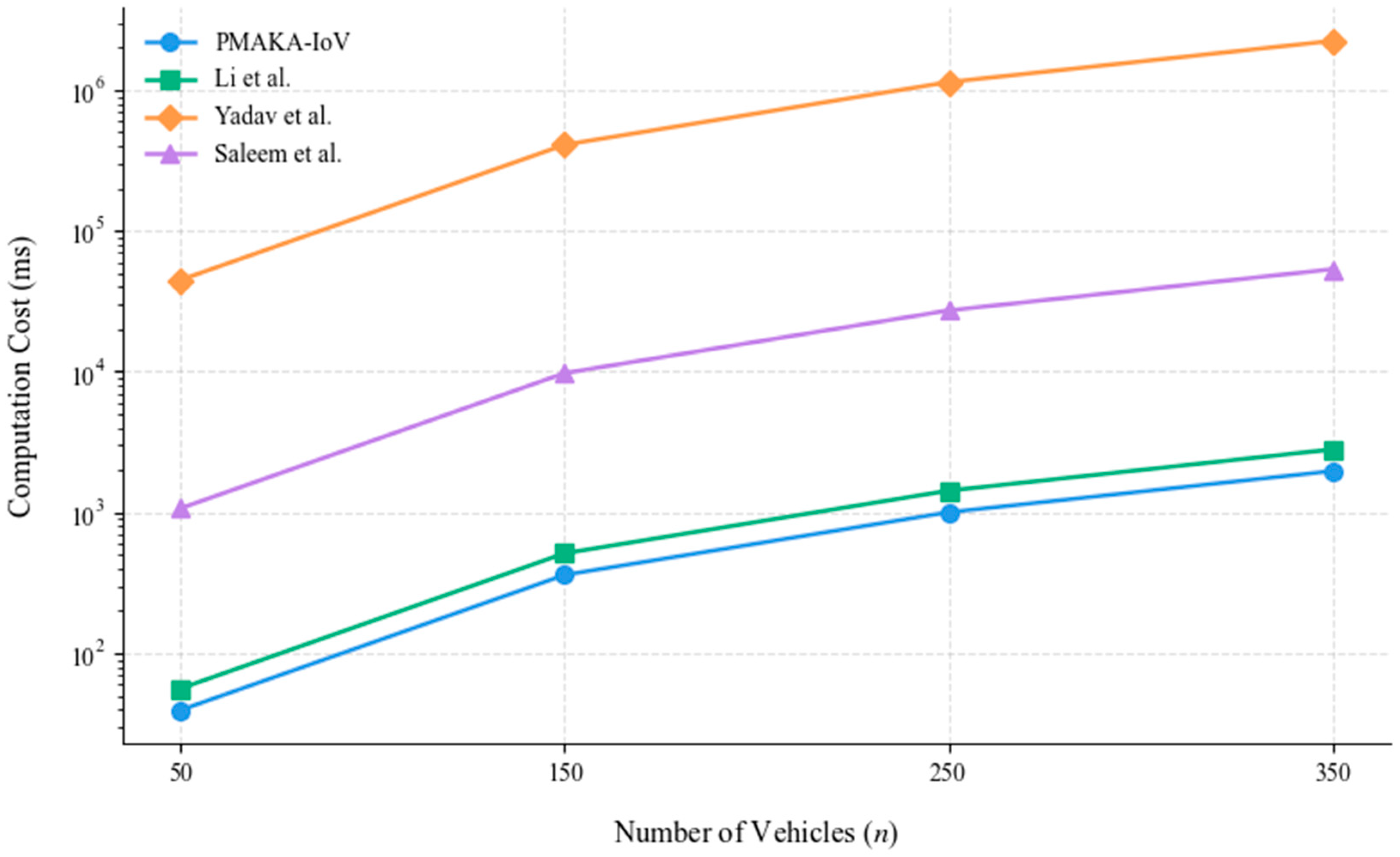
6.3. Computation Cost
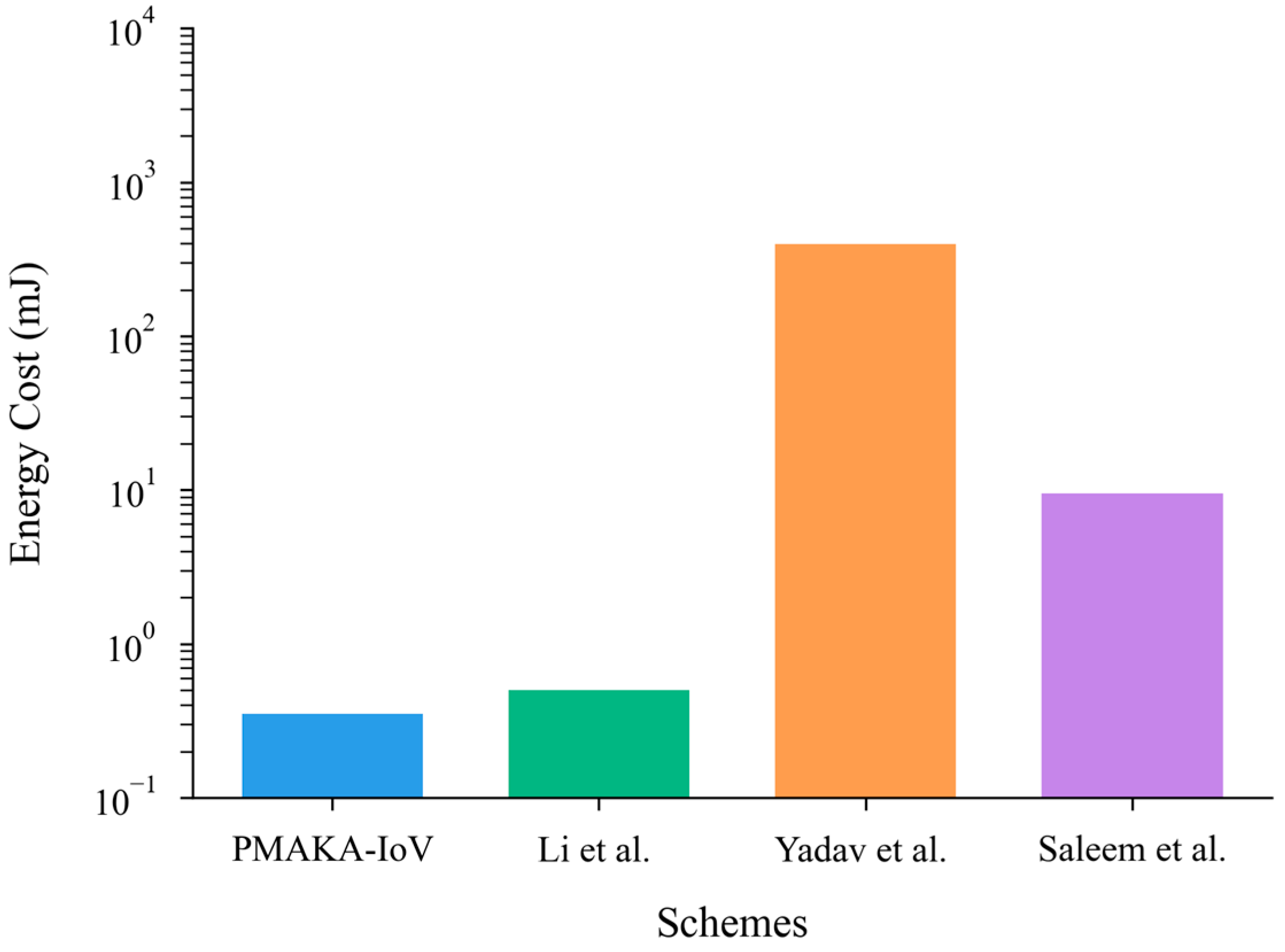
6.4. Energy Cost
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Muhammad, M.; Safdar, G.A. Survey on existing authentication issues for cellular-assisted V2X communication. Veh. Commun. 2018, 12, 50–65. [Google Scholar] [CrossRef]
- Wei, L.; Cui, J.; Zhong, H.; Xu, Y.; Liu, L. Proven secure tree-based authenticated key agreement for securing V2V and V2I communications in VANETs. IEEE Trans. Mob. Comput. 2021, 21, 3280–3297. [Google Scholar] [CrossRef]
- Li, Z.; Wu, H.; Dai, Y.; Lu, Y. PAFL: Parameter-Authentication Federated Learning for Internet of Vehicles. In Proceedings of the GLOBECOM 2023 IEEE Global Communications Conference, Kuala Lumpur, Malaysia, 4–8 December 2023; pp. 1241–1246. [Google Scholar]
- Zhao, P.; Huang, Y.; Gao, J.; Ling, X.; Wu, H.; Ma, H. Federated learning-based collaborative authentication protocol for shared data in social IoV. IEEE Sens. J. 2022, 22, 7385–7398. [Google Scholar] [CrossRef]
- Alkhalidy, M.; Taha, M.B.; Chowdhury, R.; Ould-Slimane, H.; Mourad, A.; Talhi, C. Vehicular edge-based approach for optimizing urban data privacy. IEEE Sens. J. 2023, 24, 5609–5621. [Google Scholar] [CrossRef]
- Ma, Z.; Zhang, J.; Guo, Y.; Liu, Y.; Liu, X.; He, W. An efficient decentralized key management mechanism for VANET with blockchain. IEEE Trans. Veh. Technol. 2020, 69, 5836–5849. [Google Scholar] [CrossRef]
- Wang, C.; Shen, J.; Lai, J.F.; Liu, J. B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Trans. Emerg. Top. Comput. 2020, 9, 1386–1396. [Google Scholar] [CrossRef]
- Son, S.; Lee, J.; Park, Y.; Park, Y.; Das, A.K. Design of blockchain-based lightweight V2I handover authentication protocol for VANET. IEEE Trans. Netw. Sci. Eng. 2022, 9, 1346–1358. [Google Scholar] [CrossRef]
- Roy, S.; Nandi, S.; Maheshwari, R.; Shetty, S.; Das, A.K.; Lorenz, P. Blockchain-based efficient access control with handover policy in IoV-enabled intelligent transportation system. IEEE Trans. Veh. Technol. 2023, 73, 3009–3024. [Google Scholar] [CrossRef]
- Zheng, Y.; Liu, W.; Gu, C.; Chang, C.H. PUF-based mutual authentication and key exchange protocol for peer-to-peer IoT applications. IEEE Trans. Dependable Secur. Comput. 2022, 20, 3299–3316. [Google Scholar] [CrossRef]
- Chatterjee, U.; Govindan, V.; Sadhukhan, R.; Mukhopadhyay, D.; Chakraborty, R.S.; Mahata, D.; Prabhu, M.M. Building PUF based authentication and key exchange protocol for IoT without explicit CRPs in verifier database. IEEE Trans. Dependable Secur. Comput. 2018, 16, 424–437. [Google Scholar] [CrossRef]
- Aman, M.N.; Javaid, U.; Sikdar, B. A privacy-preserving and scalable authentication protocol for the internet of vehicles. IEEE Internet Things J. 2020, 8, 1123–1139. [Google Scholar] [CrossRef]
- Umar, M.; Islam, S.H.; Mahmood, K.; Ahmed, S.; Ghaffar, Z.; Saleem, M.A. Provable secure identity-based anonymous and privacy-preserving inter-vehicular authentication protocol for VANETS using PUF. IEEE Trans. Veh. Technol. 2021, 70, 12158–12167. [Google Scholar] [CrossRef]
- Xie, Q.; Ding, Z.; Zheng, P. Provably secure and anonymous V2I and V2V authentication protocol for VANETs. IEEE Trans. Intell. Transp. Syst. 2023, 24, 7318–7327. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, X.; Zhang, N.; Tian, Y.; Ma, X.; Ma, J. Three-factor authentication protocol using physical unclonable function for IoV. Comput. Commun. 2021, 173, 45–55. [Google Scholar] [CrossRef]
- Saleem, M.A.; Li, X.; Ayub, M.F.; Shamshad, S.; Wu, F.; Abbas, H. An efficient and physically secure privacy-preserving key-agreement protocol for vehicular ad-hoc network. IEEE Trans. Intell. Transp. Syst. 2023, 24, 9940–9951. [Google Scholar] [CrossRef]
- Jiang, Q.; Zhang, N.; Ni, J.; Ma, J.; Ma, X.; Choo, K.K.R. Unified biometric privacy preserving three-factor authentication and key agreement for cloud-assisted autonomous vehicles. IEEE Trans. Veh. Technol. 2020, 69, 9390–9401. [Google Scholar] [CrossRef]
- Tahir, H.; Mahmood, K.; Ayub, M.F.; Saleem, M.A.; Ferzund, J.; Kumar, N. Lightweight and secure multi-factor authentication scheme in VANETs. IEEE Trans. Veh. Technol. 2023, 72, 14978–14986. [Google Scholar] [CrossRef]
- Awais, S.M.; Yucheng, W.; Mahmood, K.; Akram, M.W.; Hussain, S.; Das, A.K.; Park, Y. PUF-based privacy-preserving simultaneous authentication among multiple vehicles in VANET. IEEE Trans. Veh. Technol. 2023, 73, 6727–6739. [Google Scholar] [CrossRef]
- He, Z.; Tan, W.; Long, Y.; Chen, Y.; Niu, K.; Li, C.; Tan, W. VC-MAKA: Mutual Authentication and Key Agreement Protocol Based on Verifiable Commitment for Internet of Vehicles. IEEE Internet Things J. 2024, 11, 41166–41181. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the Security of Public Key Protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally Composable Notions of Key Exchange and Secure Channels. In Proceedings of the Advances in Cryptology (EUROCRYPT 2002), Berlin/Heidelberg, Germany, 28 April–2 May 2002; pp. 337–351. [Google Scholar]
- Fábrega, F.J.T.; Herzog, J.C.; Guttman, J.D. Strand spaces: Proving security protocols correct. J. Comput. Secur. 1999, 7, 191–230. [Google Scholar] [CrossRef]
- Fábrega, F.J.T.; Herzog, J.C.; Guttman, J.D. Mixed strand spaces. In Proceedings of the 12th IEEE Computer Security Foundations Workshop, Mordano, Italy, 30 June 1999; pp. 72–82. [Google Scholar]
- Herzog, J.C. The Diffie-Hellman Key-agreement Scheme in the Strand Space Model. In Proceedings of the 16th IEEE Computer Security Foundations Workshop, 2003 Proceedings, Pacific Grove, CA, USA, 30 June–2 July 2003; pp. 234–247. [Google Scholar]
- Cremers, C.J.F. Scyther—Semantics and Verification of Security Protocols. Ph.D. Dissertation, Institute for Programming Research Algorithmics, Eindhoven University of Technology, Eindhoven, The Netherlands, 2006. [Google Scholar]
- The Scyther Tool. Available online: http://www.cs.ox.ac.uk/people/cas.cremers/scyther (accessed on 7 May 2022).
- Li, X.; Liu, T.; Obaidat, M.S.; Wu, F.; Vijayakumar, P.; Kumar, N. A lightweight privacy-preserving authentication protocol for VANETs. IEEE Syst. J. 2020, 14, 3547–3557. [Google Scholar] [CrossRef]
- Yadav, K.A.; Vijayakumar, P. LPPSA: An efficient lightweight privacy-preserving signature-based authentication protocol for a vehicular ad hoc network. Ann. Telecommun. 2022, 77, 473–489. [Google Scholar] [CrossRef]
- Brighente, A.; Conti, M.; Vasudev, H. MeLSeC: A Method for Lightweight and Secure Communication in Internet of Vehicles. In Proceedings of the 2022 IEEE Intl Conf on Dependable, Autonomic and Secure Computing, Intl Conf on Pervasive Intelligence and Computing, Intl Conf on Cloud and Big Data Computing, Intl Conf on Cyber Science and Technology Congress, Falerna, Italy, 12–15 September 2022; pp. 1–8. [Google Scholar]
- Sikarwar, H.; Das, D. A novel MAC-based authentication scheme (NoMAS) for Internet of Vehicles (IoV). IEEE Trans. Intell. Transp. Syst. 2023, 24, 4904–4916. [Google Scholar] [CrossRef]
- Limbasiya, T.; Das, D. Lightweight secure message broadcasting protocol for vehicle-to-vehicle communication. IEEE Syst. J. 2019, 14, 520–529. [Google Scholar] [CrossRef]
| Scheme | Year | Cryptographic Techniques | Advantages | Limitations |
|---|---|---|---|---|
| Chatterjee et al. [11] | 2018 | Uses PUF and hash functions | Avoids explicit storage of secret CRPs | Lacks user anonymity and relies on random number check for replay resistance |
| Aman et al. [12] | 2020 | Uses PUF and hash functions | Reduces the risk of key storage via PUF and provides hardware-level random number generation to improve encryption efficiency | Does not provide PUF challenge–response pair protection |
| Jiang et al. [17] | 2020 | Uses ECC | Provides three-factor authentication | The computational complexity is relatively high |
| Umar et al. [13] | 2021 | Uses XOR, hash functions, and PUF | Uses lightweight operations, thus suitable for resource-constrained devices | Temporary identifiers lack dynamic updates, risking privacy breaches |
| Jiang et al. [15] | 2021 | Uses PUF and hash functions | Provides three-factor authentication and resists impersonation attacks | Involves some entities that cannot be fully trusted |
| Xie et al. [14] | 2023 | Uses PUF and ECC | Combines PUF with ECC for anonymous authentication and provides high security with low computational complexity | Relies on partially trusted RSUs and vehicles and is vulnerable to spoofing attacks by malicious RSUs |
| Saleem et al. [16] | 2023 | Uses PUF, hash functions, XOR, and fuzzy extractor | Provides lightweight operations and protects OBUs from physical tampering and cloning attacks using PUF and fuzzy extractors | Vulnerable to desynchronization attacks |
| Tahir et al. [18] | 2023 | Uses XOR and hash functions | Provides multi-factor authentication and verifies vehicle location for system robustness | Vulnerable to physical capture attacks |
| Awais et al. [19] | 2023 | Uses PUF, hash functions, and ECC | Provides high security and is free from the influence of known attacks | Does not provide PUF challenge–response pair protection |
| He et al. [20] | 2024 | Uses PUF, hash functions, and symmetric encryption/decryption | Provides mutual authentication, secure session key establishment, rapid session key updates, and conditional anonymity | Not applicable to high-traffic IoV scenarios |
| Notation | Description |
|---|---|
| Vi | vehicle |
| RSUj | RSU |
| IDvi, PWvi | Identity and password of the user of Vi, respectively |
| BIOvi | Biometric data of the user of Vi |
| Cvi, Rvi | PUF challenge–response pair of Vi |
| IDj, IDt | Identities of RSUj and the TA, respectively |
| PIDvi | Pseudonym of Vi |
| Cj, Rj | PUF challenge–response pair of RSUj |
| ri, rj, rt | Random numbers |
| T1, T2, T3, T4 | Timestamps |
| Maximum transmission time delay | |
| F·G() | Biometric fuzzy generator function |
| F·R() | Biometric fuzzy reproducer function |
| mk | Master key generated by the TA |
| SKij | Session key between Vi and RSUj |
| , | Concatenation and bitwise XOR operator, respectively |
| PUF(), h() | PUF function and hash function, respectively |
| (φvi, φvi*) | Parameters generated by fuzzy extractors |
| Feature | Li et al. [28] | Yadav et al. [29] | Saleem et al. [16] | PMAKA-IoV |
|---|---|---|---|---|
| Anonymity | ✔ | ✔ | ✔ | ✔ |
| Mutual Authentication | ✔ | ✔ | ✔ | ✔ |
| Resistance to Man-in-the-Middle Attack | ✗ | ✔ | ✔ | ✔ |
| Resistance to Replay Attack | ✗ | ✗ | ✗ | ✔ |
| Unlinkability | ✗ | ✗ | ✔ | ✔ |
| Resistance to Password Guessing Attack | ✔ | ✔ | ✔ | ✔ |
| Resistance to Desynchronization Attack | ✗ | ✗ | ✗ | ✔ |
| Resistance to Impersonation Attack | ✔ | ✔ | ✔ | ✔ |
| Resistance to DoS Attack | ✗ | ✗ | ✗ | ✔ |
| Resistance to Physical Capture Attack | ✗ | ✗ | ✔ | ✔ |
| Perfect Forward Secrecy | ✗ | ✔ | ✔ | ✔ |
| Scheme | Communication Cost |
|---|---|
| PMAKA-IoV | 4368 bits |
| Li et al. [28] | 5696 bits |
| Yadav et al. [29] | 3616 bits |
| Saleem et al. [16] | 3072 bits |
| Scheme | Vehicle | TA | RSU | Total Cost |
|---|---|---|---|---|
| PMAKA-IoV | 784 bits | 1008 bits | 112 bits | 1904 bits |
| Li et al. [28] | 848 bits | 400 bits | 240 bits | 1488 bits |
| Yadav et al. [29] | 1168 bits | 768 bits | 256 bits | 2192 bits |
| Saleem et al. [16] | 1056 bits | 768 bits | 336 bits | 2160 bits |
| Operation | Notation | Execution Time Per Operation |
|---|---|---|
| One-way hash function | Th() | 0.0020 ms |
| AES encryption | TAE | 0.0100 ms |
| AES decryption | TAD | 0.0100 ms |
| PUF operation | TPUF | 0.00013 ms |
| Elliptic curve multiplication | TECC | 2.6100 ms |
| Multiplication operation | TMUL | 0.2680 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yuan, M.; Xiao, Y. PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles. Information 2025, 16, 404. https://doi.org/10.3390/info16050404
Yuan M, Xiao Y. PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles. Information. 2025; 16(5):404. https://doi.org/10.3390/info16050404
Chicago/Turabian StyleYuan, Ming, and Yuelei Xiao. 2025. "PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles" Information 16, no. 5: 404. https://doi.org/10.3390/info16050404
APA StyleYuan, M., & Xiao, Y. (2025). PMAKA-IoV: A Physical Unclonable Function (PUF)-Based Multi-Factor Authentication and Key Agreement Protocol for Internet of Vehicles. Information, 16(5), 404. https://doi.org/10.3390/info16050404