A Novel Hybrid GWO-RFO Metaheuristic Algorithm for Optimizing 1D-CNN Hyperparameters in IoT Intrusion Detection Systems
Abstract
1. Introduction
2. Literature Review
2.1. Hybrid Metaheuristic-CNN Models for Intrusion Detection
| Study | Model | Dataset | Key Result | Limitation/Future Direction |
|---|---|---|---|---|
| Bahaa Ahmed et al. [54] | APSO-WOA-CNN | N-BaIoT | 94.54% Accuracy | High computational overhead; need for more efficient hybrids. |
| Shan et al. [62] | WOA-GWO Hybrid IDS | NSL-KDD | Achieved high accuracy for binary classification, improving the exploration-exploitation trade-off. | Evaluated on a non-IoT dataset (NSL-KDD) and limited to binary classification. Future work includes testing on IoT-specific datasets (e.g., N-BaIoT, BoT-IoT). |
| Wafi and Nickray [63] | CNN-GRU with GWO | Edge-IIoTset | Achieved 99.3% accuracy, 97% F1-score, 97.8% precision, and 96.7% recall, significantly improving over baselines. | Using only GWO leads to risks of premature convergence and lack of exploration. Future work involves hybrid optimization and federated learning. |
| Khan et al. [64] | Adaptive Hybrid ANN (with GA) | IIoT-specific Dataset | Achieved 99.7% accuracy and an AUC of 0.9969, balancing high detection with low computational cost. | Weaker performance against low-profile attacks (e.g., Probe, R2L); limited generalization to dynamic IIoT environments. Future work includes multi-class testing and federated learning. |
2.2. Standalone Optimizer-CNN Models
| Study | Model | Dataset | Key Result | Limitation/Future Direction |
|---|---|---|---|---|
| Sagu et al. [65] | GRU-CNN (SUCMO-optimized) | UNSW-NB15 | Outperformed baseline CNN models in recognizing spatiotemporal traffic patterns. | High computational requirements, unsuitable for low-resource IoT devices. Future work aims at more efficient versions for constrained environments. |
| Alashjaee [66] | Attention-CNN-LSTM | NSL-KDD, Bot-IoT | Achieved 97.5% and 94.8% accuracy on respective datasets, with fast inference times and strong spatiotemporal feature extraction. | Tested on older/limited datasets, reducing effectiveness for diverse IoT. Future validation on newer datasets (CIC-IDS2017, TON_IoT) and adversarial training. |
| Ankalaki et al. [67] | 1D-CNN with Hierarchical PSO | IoT-specific | Achieved a notable activity detection rate of 99.82%. | High computational cost and risk of local optima constrain adoption. Future work could explore hybrid optimization. |
| Ferrag et al. [68] | DL-based CNN for DDoS (Agriculture) | Agriculture-specific dataset | Achieved 99.95% accuracy for DDoS attack detection in agriculture. | Data imbalance affects detection of infrequent attacks. Future integration of Federated Learning (FL) and blockchain is needed. |
| Wu et al. [69] | Bayesian Optimization (BO) for tuning | General (CNNs, RFs) | Illustrated that BO surpasses manual tuning for CNN and Random Forest hyperparameters. | Failed when applied to Neural Architecture Search (NAS), indicating a need for next-generation hybrid optimizers. |
| Elmasry et al. [70] | Feature/Hyperparameter co-optimization via PSO | NSL-KDD, CICIDS2017 | Produced 99.9% attack detection accuracy. | Fell short of real-time requirements due to computational cost and reliance on offline processing. |
| Hu et al. [71] | Analysis of PSO/GWO/GA for IDS | IoT-specific | Found that hybrid optimizers perform better than single ones. | All approaches (single and hybrid) fell short of real-time requirements, necessitating development of lightweight solutions. |
2.3. Non-CNN Hybrid Frameworks for Intrusion Detection
| Study | Model | Dataset | Key Result | Limitation/Future Direction |
|---|---|---|---|---|
| Zada et al. [72] | PSO-GA Feature Selection + ELM-BA Ensemble | IoT/CICIDS-2017 | 99.96% accuracy with perfect detection of critical attacks (PortScan, SQL Injection, Brute Force). | Reliance on a single dataset and traditional classifiers limits generalizability to real-world IoT traffic. Future: Adopt DRL, test on diverse datasets, embed XAI. |
| Pokhrel et al. [73] | SMOTE-enhanced KNN | IoT Botnet | Highly accurate in botnet detection. | Falls behind in tracing dynamic, evolving attack patterns. |
| Gonçalves et al. [74] | GA-PSO-boosted CNNs | Biomedical (Cancer Detection) | Achieved 0.92 F1-score with minimal tuning. | Too resource-intensive for practical hospital deployment. |
| Alharbi et al. [75] | Hybrid Inertia-weighted BA-NN | N-BaIoT | Detects 90% of N-BaIoT botnets. | Limited by data imbalance and high computational requirements, prompting the need for hybrid algorithms. |
| Nematzadeh et al. [76] | GWO/GA Metaheuristic Framework | Biomedical ML/DNN Tuning | 99.5% diagnostic accuracy. | Lacks scalability and real-time flexibility; requires streaming optimizations. |
| Brodzicki et al. [77] | Whale-inspired 3D-WOA for DNN Tuning | Fashion MNIST | 89% accuracy. | Poor speed and discretization issues hinder practical application. |
| Ali et al. [78] | ESCNN for IoT RAM Attacks | IoT RAM Attacks | 99.29% accuracy. | Not validated in dynamic IoT contexts; requires threat-scenario testing. |
| Alzaqeba et al. [55] | GWO-ELM Hybrid | UNSW-NB15 | 81% accuracy; surpasses PSO/GWO in convergence. | Enterprise security demands greater threat coverage. |
| Abbasi et al. [79] | LR vs. ANN/CNN for NIDS | N-BaIoT | LR achieved 99% accuracy, being more efficient than ANN/CNN for this dataset. | Highlights that ANN/CNN scalability is needed for complex installations, suggesting hybrid techniques. |
| Daghighi et al. [80] | Hybrid DRL-Metaheuristic | IoT-specific (Smart Grid) | 95.3% accuracy with reduced energy use. | Requires validation in a real smart grid environment. |
| Maazalahi et al. [81] | Swarm Intelligence-based IDS | BOT-IoT | 99.8% botnet detection accuracy. | Edge devices require DL acceleration due to computational overhead. |
| Maazalahi et al. [82] | Metaheuristic-Ensemble IDS | IoT DDoS | 99.9% DDoS accuracy. | DL integration is necessary for real-time IoT security. |
| Rabie et al. [83] | Feature-optimized IDS (DRF-DBRF) | IoTID20, NSL KDD, UNSW NB15 | 99.8% threat detection rate. | Requires Federated Learning (FL) updates for distributed deployment. |
| Alqahtany et al. [84] | EGWO-tuned Random Forest | NF-TOI | 99.93% accuracy. | Needs public sector validation before adoption in smart cities/hospitals. |
| Doshi et al. [85] | ML Framework for DDoS | IoT DDoS | >99% detection accuracy. | Dependence on simulated data raises concerns about effectiveness in complex, real-world IoT environments. |
| Anthi et al. [86] | Pulse (Hybrid ML-IDS) | IoT Probe/Flood Attacks | Performs well on probe detection but poorly on flood (UDP/SYN) attacks. | Low attack coverage in testing limits effectiveness. |
| Prachi Shukla [87] | ML-IDS for Wormhole Attacks | IoT Wormhole Attacks | K-means: 93% accuracy (high FPs); Hybrid: balanced performance. | Implementation is limited to simulation; lacks real-world deployment. |
2.4. Lightweight and Resource-Efficient IDS Designs
| Study | Model | Dataset | Key Result | Limitation/Future Direction |
|---|---|---|---|---|
| Deshmukh and Ravulakollu [88] | IIDNet (Lightweight CNN-based IDS) | UNSW-NB15 | 95.47% accuracy, 95.87% F1-Score; designed for low computational overhead. | Evaluated on a single dataset; lacks real-time validation. Future: Integrate hybrid/ensemble models and test with real IoT traffic. |
| Marques Da Silva Cardoso et al. [89] | CEPIDS (Complex Event Processing-based IDS) | DDoS | 93–99% DDoS detection with minimal resource use (~5.6 MB RAM). | Relies on static rules, making it less adaptive to novel threats. |
| Idrissi et al. [90] | CNN-based BotIDS | IoT Botnet | 99.94% attack detection in <1 ms inference time. | Struggles with sequential threats and imbalanced data. |
| Saba Tanzila et al. [91] | CNN-based Anomaly Detection System | Real-world IoT | 99.5% attack detection; tested in real-world settings with limited energy. | Needs Energy Efficiency Improvements |
| De La Torre Parra et al. [92] | Distributed CNN (Edge)-LSTM (Cloud) Framework | IoT Threats | 94.8% threat detection accuracy; bridges device-cloud barrier. | Requires further energy optimization for widespread adoption. |
| Choudhary et al. [93] | Bio-inspired CNN-AO | Self-generated IoT dataset | 95.36% detection of new IoT threats (e.g., blackhole/sinkhole). | Requires Federated Learning (FL) integration for effective edge deployment. |
| Alserhani [94] | Blockchain-IoT with Spiking Neural Networks (SNN) | Simulated IoT | 98.94% accuracy; integrates blockchain for data assurance. | Needs cross-device validation for enterprise-level deployment. |
2.5. The Proposed Novel Hybrid Algorithm
3. Datasets and Methodology
3.1. Datasets
3.2. Data Preprocessing
3.3. Methodology
3.3.1. D CNN Algorithm
3.3.2. Grey Wolf Optimization (GWO)
- Social Hierarchy of Grey Wolves
- •
- Alpha (α): High-ranking wolves who make the decisions (e.g., where to hunt, when and where to relocate).
- •
- Beta (β): Lower-ranking wolves who assist the alpha to impose decisions.
- •
- Delta (δ): Specialist wolves (e.g., scouts, hunters, caregivers).
- •
- Omega (ω): The subordinate wolves who follow members of higher rank.
- GWO Mathematical Model
- Encircling the Prey:
- •
- : Prey position vector.
- •
- : Grey wolf position vector.
- •
- and : determined the coefficient vectors as follows:
- 2.
- Hunting Prey:
- 3.
- Attacking the Prey:
- Exploration and Exploitation
- •
- Exploration: When , wolves leave their prey to look for better options around the world.
- •
- Exploitation: When , wolves converge to the prey to locally update the solution.
3.3.3. Red Fox Optimization (RFO) Algorithm
- Mathematical Model of RFO
- Global Search Phase (Exploration)
- •
- Distance Calculation:
- •
- Movement Update:
- 2.
- Local Search Phase (Exploitation)
- •
- Action Decision:
- •
- Position Update:
- 3.
- Population Management (Reproduction and Replacement)
- •
- Alpha Couple Selection
- •
- Replacement MechanismA random parameter κ ∈ (0, 1) decides whether to:
- •
- Reproduce: Create offspring near the alpha couple (κ < 0.45):
- •
- Introduce Nomadic Foxes: Place new foxes randomly outside the habitat (κ≥0.45).
3.3.4. Hybrid GWO-RFO Algorithm
- •
- GWO-based Update (Exploitation-Leaning): For solutions assigned to the GWO strategy, the standard GWO social hierarchy is enforced. The (α), beta (β), and delta (δ) wolves are the three best solutions. The locations of the alternative solutions (omega wolves, ω) are updated using the standard GWO equations:
- •
- RFO-based Update (Adaptive Exploration & Exploitation): This is where the Escaping and Hunting mechanism explicitly stated in the flow chart is executed for each agent assigned to the RFO strategy to avoid local optima. a stochastic parameter μ ∈ (0, 1) dictates its tactical behavior:
- •
- Hunting (Local Exploitation): If μ > 0.75, then the agent enters hunting mode, a stealthy, exploitative local search. It takes the present global best solution as prey and moves around it using a complicated movement model based on the Cochleoid equation. It generates a new position spirally, allowing an intensive and refined search in the very close vicinity of the best-known solution.
- •
- Escaping (Global Exploration): If μ ≤ 0.75, the agent is deemed to have been discovered and must escape to avoid stagnation. It calculates a movement vector towards with a random step size: . The key to ‘escaping’ is the rejection criterion: if this new position does not improve fitness, the agent discards it and reverts to its previous position. This forces the agent to effectively abandon an unsuccessful hunt and encourages exploration in a different, potentially more fruitful, region of the search area, preventing premature convergence.
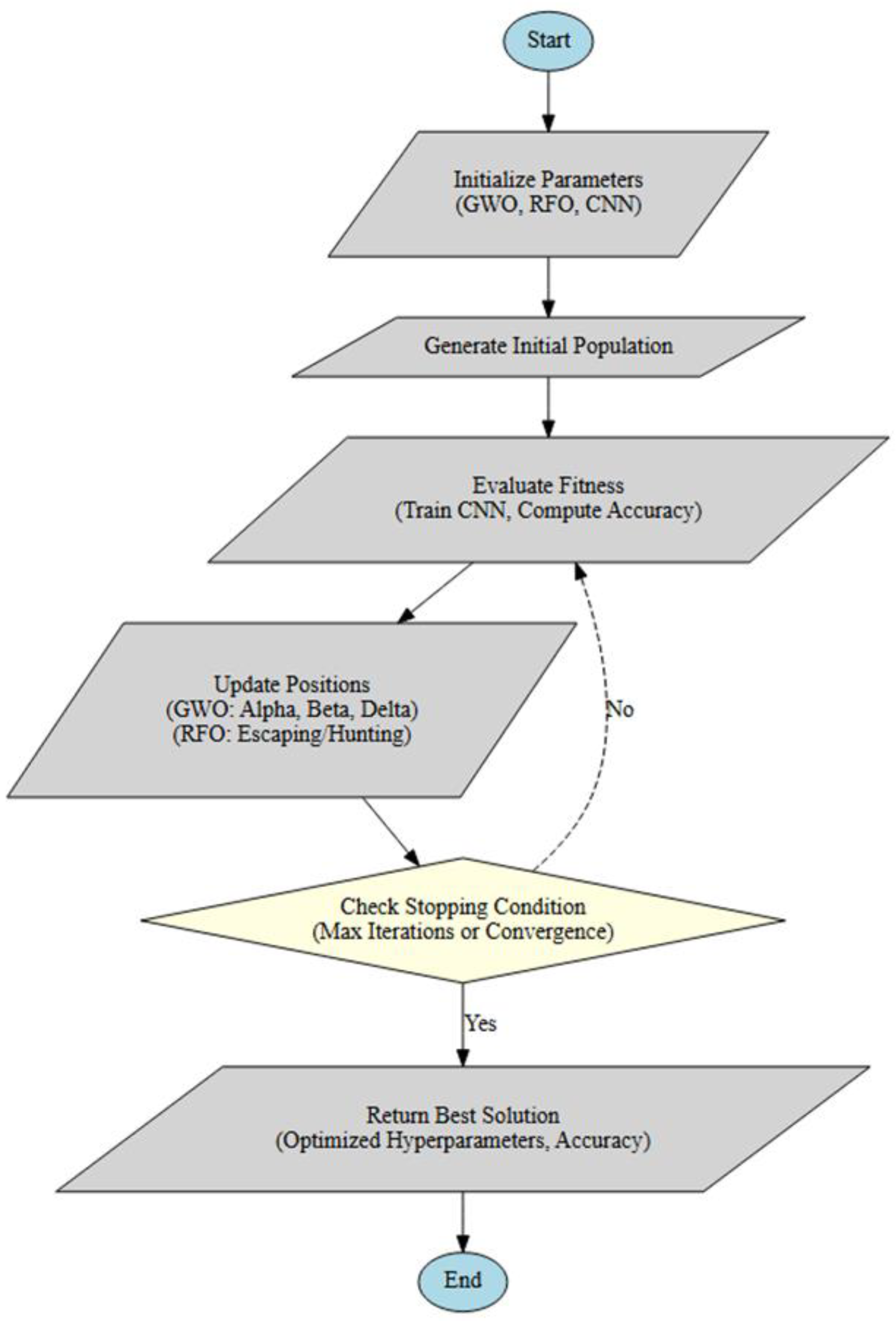
| Algorithm 1. The FW-CNN Algorithm to Optimize Hyperparameters Pseudocode |
| Input: N = Total populations, d, t_max 1. Initialize parameters for GWO, RFO, and CNN. 2. Generate the initial population. 3. While (t < tmax) 4. Evaluate the fitness for each individual by training CNN and computing accuracy. 5. Update best solutions (alpha, beta, delta for GWO; escaping/hunting strategies for RFO). 6. Update positions of individuals using: - GWO: Alpha, Beta, Delta influence. - RFO: Random escaping and hunting strategies. 7. Check stopping condition (max iterations or convergence). 8. If stopping condition met: Return best solution (optimized hyperparameters, accuracy). 9. Else: Continue to next iteration. 10. t = t + 1. 11. End while. 12. Return best optimized solution. |
4. Experiments
4.1. Software and Hardware
4.2. Simulation and Discussion
4.2.1. Training Accuracy
4.2.2. Validation Accuracy
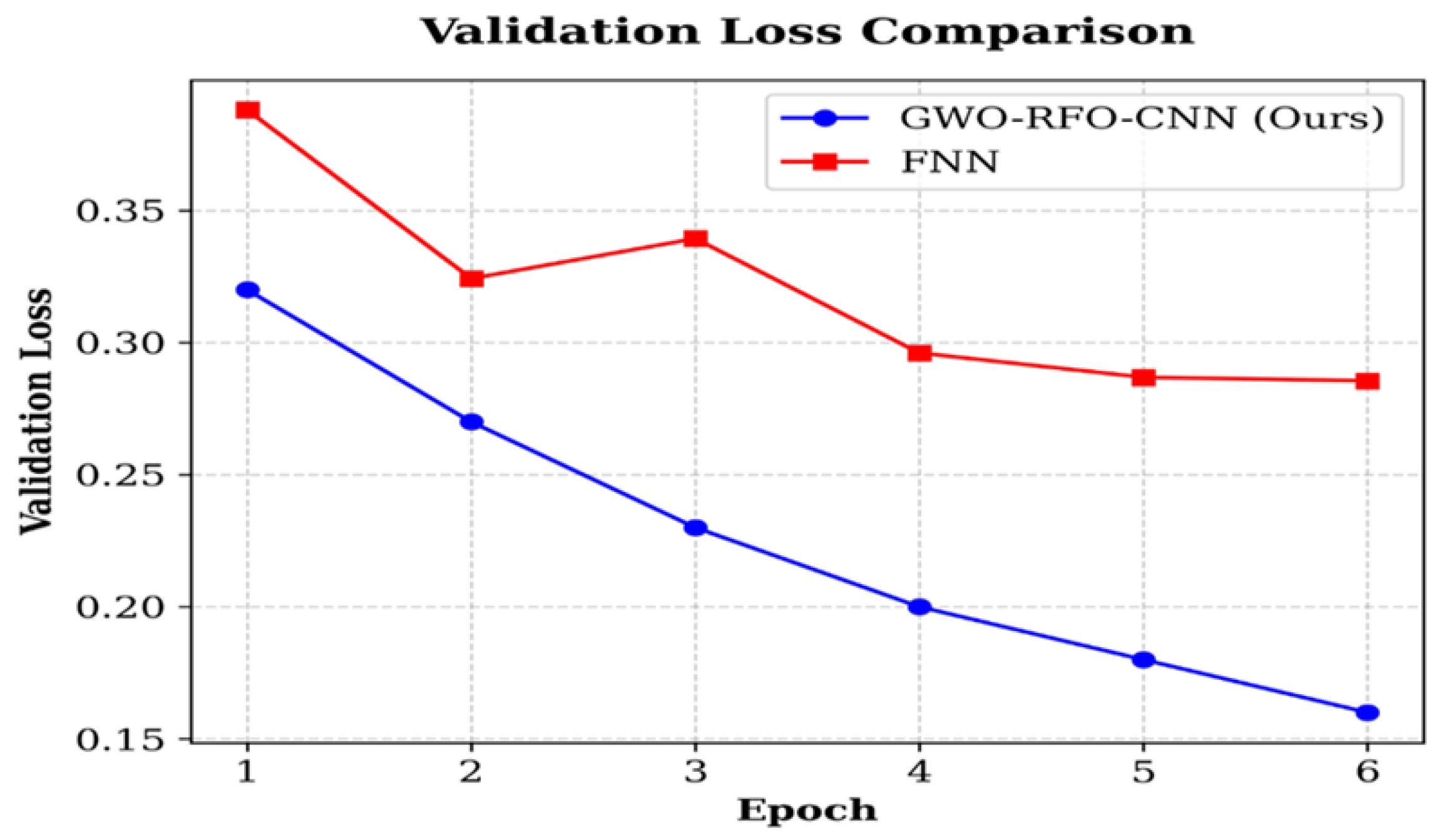
4.2.3. Validation Loss
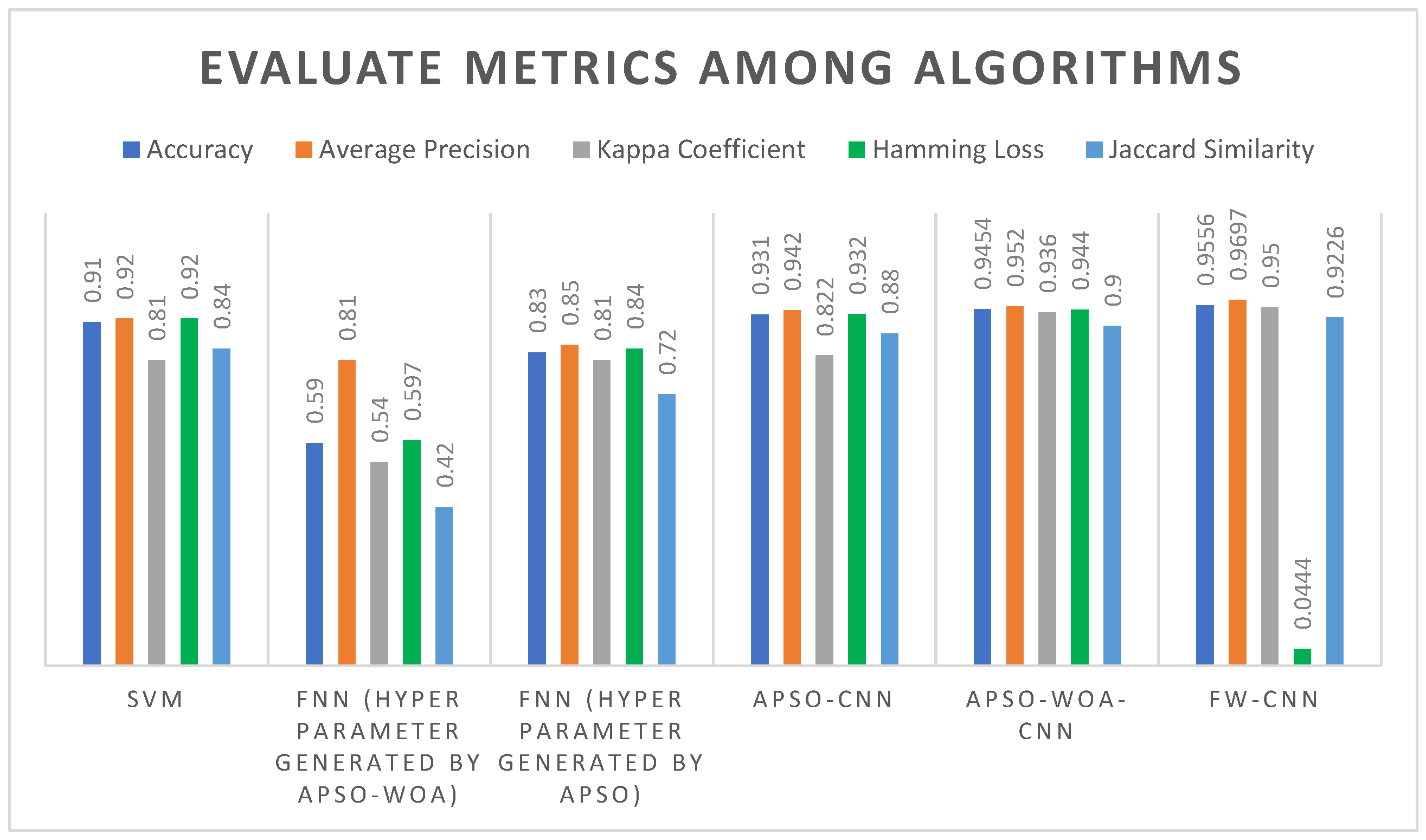
4.3. Results and Performance Analysis
4.4. Study Limitations
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Fourth Industrial Revolution. World Economic Forum. Available online: https://www.weforum.org/focus/fourth-industrial-revolution/ (accessed on 4 September 2025).
- Fallahpour, A.; Wong, K.Y.; Rajoo, S.; Fathollahi-Fard, A.M.; Antucheviciene, J.; Nayeri, S. An integrated approach for a sustainable supplier selection based on Industry 4.0 concept. Environ. Sci. Pollut. Res. 2021. ahead of print. [Google Scholar] [CrossRef] [PubMed]
- Patel, N.A.; Parekh, D.A.; Shah, Y.A.; Mangrulkar, R. In Cyber Security and Digital Forensics, Ghonge, M.M., Pramanik, S., Mangrulkar, R., Le, D., Eds.; 4S Framework: A Practical CPS Design Security Assessment & Benchmarking Framework, 1st ed.; Wiley: New York, NY, USA, 2022; pp. 163–204. [Google Scholar] [CrossRef]
- Attaran, M. The Internet Of Things: Limitless Opportunities For Business And Society. Bus. Horiz. 2017, 60, 831–841. [Google Scholar]
- Ortega, F.; González-Prieto, Á.; Bobadilla, J.; Gutiérrez, A. Collaborative Filtering to Predict Sensor Array Values in Large IoT Networks. Sensors 2020, 20, 4628. [Google Scholar] [CrossRef] [PubMed]
- Bout, E.; Loscri, V.; Gallais, A. Evolution of IoT Security: The Era of Smart Attacks. IEEE Internet Things M. 2022, 5, 108–113. [Google Scholar] [CrossRef]
- Memos, V.A.; Psannis, K.E. NFV-Based Scheme for Effective Protection against Bot Attacks in AI-Enabled IoT. IEEE Internet Things M. 2022, 5, 91–95. [Google Scholar] [CrossRef]
- Symantec Internet Security Threat Report. Volume 24: Executive Summary. 2019. Available online: https://docs.broadcom.com/doc/istr-24-2019-en (accessed on 4 September 2025).
- Alsheikh, M.; Konieczny, L.; Prater, M.; Smith, G.; Uludag, S. The State of IoT Security: Unequivocal Appeal to Cybercriminals, Onerous to Defenders. IEEE Consum. Electron. Mag. 2022, 11, 59–68. [Google Scholar] [CrossRef]
- Gmcdouga. A Perfect Storm: The Security Challenges of Coronavirus Threats and Mass Remote Working. Check Point Blog 2020. Available online: https://blog.checkpoint.com/security/a-perfect-storm-the-security-challenges-of-coronavirus-threats-and-mass-remote-working/ (accessed on 10 September 2025).
- Raponi, S.; Sciancalepore, S.; Oligeri, G.; Di Pietro, R. Road Traffic Poisoning of Navigation Apps: Threats and Countermeasures. IEEE Secur. Priv. 2022, 20, 71–79. [Google Scholar] [CrossRef]
- Abbas, G.; Mehmood, A.; Carsten, M.; Epiphaniou, G.; Lloret, J. Safety, Security and Privacy in Machine Learning Based Internet of Things. J. Sens. Actuator Netw. 2022, 11, 38. [Google Scholar] [CrossRef]
- Hireche, R.; Mansouri, H.; Pathan, A.-S.K. Security and Privacy Management in Internet of Medical Things (IoMT): A Synthesis. J. Cybersecur. Priv. 2022, 2, 640–661. [Google Scholar] [CrossRef]
- Goudarzi, A.; Ghayoor, F.; Waseem, M.; Fahad, S.; Traore, I. A Survey on IoT-Enabled Smart Grids: Emerging, Applications, Challenges, and Outlook. Energies 2022, 15, 6984. [Google Scholar] [CrossRef]
- Zhang, C.; Zuo, W.; Yang, P.; Li, Y.; Wang, X. Outsourced privacy-preserving anomaly detection in time series of multi-party. China Commun. 2022, 19, 201–213. [Google Scholar] [CrossRef]
- Yin, X.; Wang, S.; Shahzad, M.; Hu, J. An IoT-Oriented Privacy-Preserving Fingerprint Authentication System. IEEE Internet Things J. 2022, 9, 11760–11771. [Google Scholar] [CrossRef]
- Zhang, C.; Zhu, L.; Xu, C. BPAF: Blockchain-Enabled Reliable and Privacy-Preserving Authentication for Fog-Based IoT Devices. IEEE Consum. Electron. Mag. 2022, 11, 88–96. [Google Scholar] [CrossRef]
- Hunter, J.; Huber, B.; Kandah, F. Towards feasibility of Deep-Learning based Intrusion Detection System for IoT Embedded Devices. In Proceedings of the 2022 IEEE 19th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 947–948. [Google Scholar] [CrossRef]
- Awad, M.; Fraihat, S.; Salameh, K.; Al Redhaei, A. Examining the Suitability of NetFlow Features in Detecting IoT Network Intrusions. Sensors 2022, 22, 6164. [Google Scholar] [CrossRef] [PubMed]
- Alani, M.M.; Miri, A. Towards an Explainable Universal Feature Set for IoT Intrusion Detection. Sensors 2022, 22, 5690. [Google Scholar] [CrossRef]
- Al-rawashdeh, M.; Keikhosrokiani, P.; Belaton, B.; Alawida, M.; Zwiri, A. IoT Adoption and Application for Smart Healthcare: A Systematic Review. Sensors 2022, 22, 5377. [Google Scholar] [CrossRef]
- Breitenbacher, D.; Homoliak, I.; Aung, Y.L.; Elovici, Y.; Tippenhauer, N.O. HADES-IoT: A Practical and Effective Host-Based Anomaly Detection System for IoT Devices (Extended Version). IEEE Internet Things J. 2022, 9, 9640–9658. [Google Scholar] [CrossRef]
- Dutta, V.; Choraś, M.; Pawlicki, M.; Kozik, R. A Deep Learning Ensemble for Network Anomaly and Cyber-Attack Detection. Sensors 2020, 20, 4583. [Google Scholar] [CrossRef]
- Muthanna, M.S.A.; Alkanhel, R.; Muthanna, A.; Rafiq, A.; Abdullah, W.A.M. Towards SDN-Enabled, Intelligent Intrusion Detection System for Internet of Things (IoT). IEEE Access 2022, 10, 22756–22768. [Google Scholar] [CrossRef]
- Gao, B.; Bu, B.; Zhang, W.; Li, X. An Intrusion Detection Method Based on Machine Learning and State Observer for Train-Ground Communication Systems. IEEE Trans. Intell. Transport. Syst. 2022, 23, 6608–6620. [Google Scholar] [CrossRef]
- Abdel-Basset, M.; Moustafa, N.; Hawash, H.; Razzak, I.; Sallam, K.M.; Elkomy, O.M. Federated Intrusion Detection in Blockchain-Based Smart Transportation Systems. IEEE Trans. Intell. Transport. Syst. 2022, 23, 2523–2537. [Google Scholar] [CrossRef]
- Aribisala, A.; Khan, M.S.; Husari, G. Feed-Forward Intrusion Detection and Classification on a Smart Grid Network. In Proceedings of the 2022 IEEE 12th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 26–29 January 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 99–105. [Google Scholar] [CrossRef]
- Efe, A.; Abaci, İ.N. Comparison of the Host Based Intrusion Detection Systems and Network Based Intrusion Detection Systems. Celal Bayar Üniversitesi Fen Bilim. Derg. 2022, 18, 23–32. [Google Scholar] [CrossRef]
- Bahaa, A.; Abdelaziz, A.; Sayed, A.; Elfangary, L.; Fahmy, H. Monitoring Real Time Security Attacks for IoT Systems Using DevSecOps: A Systematic Literature Review. Information 2021, 12, 154. [Google Scholar] [CrossRef]
- Bahsi, H.; Nomm, S.; La Torre, F.B. Dimensionality Reduction for Machine Learning Based IoT Botnet Detection. In Proceedings of the 2018 15th International Conference on Control, Automation, Robotics and Vision (ICARCV), Singapore, 18–21 November 2018; IEEE: New York, NY, USA, 2018; pp. 1857–1862. [Google Scholar] [CrossRef]
- Meidan, Y.; Bohadana, M.; Mathov, Y.; Mirsky, Y.; Breitenbacher, D.; Shabtai, A.; Elovici, Y. N-BaIoT: Network-based Detection of IoT Botnet Attacks Using Deep Autoencoders. IEEE Pervasive Comput. 2018, 17, 12–22. [Google Scholar] [CrossRef]
- Sattari, F.; Farooqi, A.H.; Qadir, Z.; Raza, B.; Nazari, H.; Almutiry, M. A Hybrid Deep Learning Approach for Bottleneck Detection in IoT. IEEE Access 2022, 10, 77039–77053. [Google Scholar] [CrossRef]
- Nguyen, T.N.; Ngo, Q.-D.; Nguyen, H.-T.; Nguyen, G.L. An Advanced Computing Approach for IoT-Botnet Detection in Industrial Internet of Things. IEEE Trans. Ind. Inf. 2022, 18, 8298–8306. [Google Scholar] [CrossRef]
- Jiang, S.; Firouzi, F.; Chakrabarty, K.; Elbogen, E.B. A Resilient and Hierarchical IoT-Based Solution for Stress Monitoring in Everyday Settings. IEEE Internet Things J. 2022, 9, 10224–10243. [Google Scholar] [CrossRef]
- Jamalipour, A.; Murali, S. A Taxonomy of Machine-Learning-Based Intrusion Detection Systems for the Internet of Things: A Survey. IEEE Internet Things J. 2022, 9, 9444–9466. [Google Scholar] [CrossRef]
- Zhou, X.; Liang, W.; Li, W.; Yan, K.; Shimizu, S.; Wang, K.I.-K. Hierarchical Adversarial Attacks Against Graph-Neural-Network-Based IoT Network Intrusion Detection System. IEEE Internet Things J. 2022, 9, 9310–9319. [Google Scholar] [CrossRef]
- Elsaeidy, A.A.; Jamalipour, A.; Munasinghe, K.S. A Hybrid Deep Learning Approach for Replay and DDoS Attack Detection in a Smart City. IEEE Access 2021, 9, 154864–154875. [Google Scholar] [CrossRef]
- Huang, Y.; Qiao, X.; Dustdar, S.; Zhang, J.; Li, J. Toward Decentralized and Collaborative Deep Learning Inference for Intelligent IoT Devices. IEEE Netw. 2022, 36, 59–68. [Google Scholar] [CrossRef]
- Zhang, S.; Wang, Z.; Zhou, Z.; Wang, Y.; Zhang, H.; Zhang, G.; Ding, H.; Mumtaz, S.; Guizani, M. Blockchain and Federated Deep Reinforcement Learning Based Secure Cloud-Edge-End Collaboration in Power IoT. IEEE Wirel. Commun. 2022, 29, 84–91. [Google Scholar] [CrossRef]
- Kumar, P.; Gupta, G.P.; Tripathi, R. PEFL: Deep Privacy-Encoding-Based Federated Learning Framework for Smart Agriculture. IEEE Micro 2022, 42, 33–40. [Google Scholar] [CrossRef]
- Ahmed, A.; Tjortjis, C. Machine Learning based IoT-BotNet Attack Detection Using Real-time Heterogeneous Data. In Proceedings of the 2022 International Conference on Electrical, Computer and Energy Technologies (ICECET), Prague, Czech Republic, 20–22 July 2022; IEEE: Piscataway, NJ, USA, 2022; pp. 1–6. [Google Scholar] [CrossRef]
- Aslam, M.; Ye, D.; Tariq, A.; Asad, M.; Hanif, M.; Ndzi, D.; Chelloug, S.A.; Elaziz, M.A.; Al-Qaness, M.A.A.; Jilani, S.F. Adaptive Machine Learning Based Distributed Denial-of-Services Attacks Detection and Mitigation System for SDN-Enabled IoT. Sensors 2022, 22, 2697. [Google Scholar] [CrossRef]
- Zeeshan, M.; Riaz, Q.; Bilal, M.A.; Shahzad, M.K.; Jabeen, H.; Haider, S.A.; Rahim, A. Protocol-Based Deep Intrusion Detection for DoS and DDoS Attacks Using UNSW-NB15 and Bot-IoT Data-Sets. IEEE Access 2022, 10, 2269–2283. [Google Scholar] [CrossRef]
- Alothman, Z.; Alkasassbeh, M.; Al-Haj Baddar, S. An efficient approach to detect IoT botnet attacks using machine learning. J. High Speed Netw. 2020, 26, 241–254. [Google Scholar] [CrossRef]
- Popoola, S.I.; Ande, R.; Adebisi, B.; Gui, G.; Hammoudeh, M.; Jogunola, O. Federated Deep Learning for Zero-Day Botnet Attack Detection in IoT-Edge Devices. IEEE Internet Things J. 2022, 9, 3930–3944. [Google Scholar] [CrossRef]
- Booij, T.M.; Chiscop, I.; Meeuwissen, E.; Moustafa, N.; Hartog, F.T.H.D. ToN_IoT: The Role of Heterogeneity and the Need for Standardization of Features and Attack Types in IoT Network Intrusion Data Sets. IEEE Internet Things J. 2022, 9, 485–496. [Google Scholar] [CrossRef]
- Huancayo Ramos, K.S.; Sotelo Monge, M.A.; Maestre Vidal, J. Benchmark-Based Reference Model for Evaluating Botnet Detection Tools Driven by Traffic-Flow Analytics. Sensors 2020, 20, 4501. [Google Scholar] [CrossRef] [PubMed]
- Sen, S.Y.; Ozkurt, N. Convolutional Neural Network Hyperparameter Tuning with Adam Optimizer for ECG Classification. In Proceedings of the 2020 Innovations in Intelligent Systems and Applications Conference (ASYU), Istanbul, Turkey, 15–17 October 2020; IEEE: New York, NY, USA, 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Qu, Z.; Yuan, S.; Chi, R.; Chang, L.; Zhao, L. Genetic Optimization Method of Pantograph and Catenary Comprehensive Monitor Status Prediction Model Based on Adadelta Deep Neural Network. IEEE Access 2019, 7, 23210–23221. [Google Scholar] [CrossRef]
- He, X.; Zheng, Z.; Chen, C.; Zhou, Y.; Luo, C.; Lin, Q. Distributed Evolution Strategies for Black-box Stochastic Optimization. arXiv 2022, arXiv:2204.04450. [Google Scholar] [CrossRef]
- Mirjalili, S.; Mirjalili, S.M.; Lewis, A. Grey Wolf Optimizer. Adv. Eng. Softw. 2014, 69, 46–61. [Google Scholar] [CrossRef]
- Mirjalili, S.; Lewis, A. The Whale Optimization Algorithm. Adv. Eng. Softw. 2016, 95, 51–67. [Google Scholar] [CrossRef]
- Kan, X.; Fan, Y.; Fang, Z.; Cao, L.; Xiong, N.N.; Yang, D.; Li, X. A novel IoT network intrusion detection approach based on Adaptive Particle Swarm Optimization Convolutional Neural Network. Inf. Sci. 2021, 568, 147–162. [Google Scholar] [CrossRef]
- Bahaa, A.; Sayed, A.; Elfangary, L.; Fahmy, H. A novel hybrid optimization enabled robust CNN algorithm for an IoT network intrusion detection approach. PLoS ONE 2022, 17, e0278493. [Google Scholar] [CrossRef] [PubMed]
- Alzaqebah, A.; Aljarah, I.; Al-Kadi, O.; Damaševičius, R. A Modified Grey Wolf Optimization Algorithm for an Intrusion Detection System. Mathematics 2022, 10, 999. [Google Scholar] [CrossRef]
- Lokku, G.; Reddy, G.H.; Prasad, M.N.G. OPFaceNet: OPtimized Face Recognition Network for noise and occlusion affected face images using Hyperparameters tuned Convolutional Neural Network. Appl. Soft Comput. 2022, 117, 108365. [Google Scholar] [CrossRef]
- Połap, D.; Woźniak, M. Red fox optimization algorithm. Expert Syst. Appl. 2021, 166, 114107. [Google Scholar] [CrossRef]
- Thapa, N.; Liu, Z.; Shaver, A.; Esterline, A.; Gokaraju, B.; Roy, K. Secure Cyber Defense: An Analysis of Network Intrusion-Based Dataset CCD-IDSv1 with Machine Learning and Deep Learning Models. Electronics 2021, 10, 1747. [Google Scholar] [CrossRef]
- Ahmed, N.; Ngadi, A.B.; Sharif, J.M.; Hussain, S.; Uddin, M.; Rathore, M.S.; Iqbal, J.; Abdelhaq, M.; Alsaqour, R.; Ullah, S.S.; et al. Network Threat Detection Using Machine/Deep Learning in SDN-Based Platforms: A Comprehensive Analysis of State-of-the-Art Solutions, Discussion, Challenges, and Future Research Direction. Sensors 2022, 22, 7896. [Google Scholar] [CrossRef]
- Abdelmoumin, G.; Rawat, D.B.; Rahman, A. On the Performance of Machine Learning Models for Anomaly-Based Intelligent Intrusion Detection Systems for the Internet of Things. IEEE Internet Things J. 2022, 9, 4280–4290. [Google Scholar] [CrossRef]
- Lin, W.-H.; Wang, P.; Chao, K.-M.; Lin, H.-C.; Yang, Z.-Y.; Lai, Y.-H. Deep-Learning Model Selection and Parameter Estimation from a Wind Power Farm in Taiwan. Appl. Sci. 2022, 12, 7067. [Google Scholar] [CrossRef]
- Shan, L. (IoT) Network intrusion detection system using optimization algorithms. Sci. Rep. 2025, 15, 21706. [Google Scholar] [CrossRef] [PubMed]
- Wafi, M.N.A.Z. CNN-RGU Hyperparameter Tuning for Improving Cybersecurity Intrusion Detection in Industrial IOT Environment. J. Inf. Syst. Eng. Manag. 2025, 10, 450–458. [Google Scholar] [CrossRef]
- Khan, M.Z.; Reshi, A.A.; Shafi, S.; Aljubayri, I. An adaptive hybrid framework for IIoT intrusion detection using neural networks and feature optimization using genetic algorithms. Discov. Sustain. 2025, 6, 382. [Google Scholar] [CrossRef]
- Sagu, A.; Gill, N.S.; Gulia, P.; Alduaiji, N.; Shukla, P.K.; Shah, M.A. Advances to IoT security using a GRU-CNN deep learning model trained on SUCMO algorithm. Sci. Rep. 2025, 15, 16485. [Google Scholar] [CrossRef] [PubMed]
- Alashjaee, A.M. Deep learning for network security: An Attention-CNN-LSTM model for accurate intrusion detection. Sci. Rep. 2025, 15, 21856. [Google Scholar] [CrossRef] [PubMed]
- Ankalaki, S.; Thippeswamy, M.N. Optimized Convolutional Neural Network Using Hierarchical Particle Swarm Optimization for Sensor Based Human Activity Recognition. SN Comput. Sci. 2024, 5, 447. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Djallel, H.; Choo, K.-K.R. Deep Learning-Based Intrusion Detection for Distributed Denial of Service Attack in Agriculture 4.0. Electronics 2021, 10, 1257. [Google Scholar] [CrossRef]
- Wu, J.; Chen, X.-Y.; Zhang, H.; Xiong, L.-D.; Lei, H.; Deng, S.-H. Hyperparameter Optimization for Machine Learning Models Based on Bayesian Optimization. J. Electron. Sci. Technol. 2019, 17, 26–40. [Google Scholar]
- Elmasry, W.; Akbulut, A.; Zaim, A.H. Evolving deep learning architectures for network intrusion detection using a double PSO metaheuristic. Comput. Netw. 2020, 168, 107042. [Google Scholar] [CrossRef]
- Hu, W.; Cao, Q.; Darbandi, M.; Jafari Navimipour, N. A deep analysis of nature-inspired and meta-heuristic algorithms for designing intrusion detection systems in cloud/edge and IoT: State-of-the-art techniques, challenges, and future directions. Clust. Comput. 2024, 27, 8789–8815. [Google Scholar] [CrossRef]
- Zada, I.; Omran, E.; Jan, S.; Alfraihi, H.; Alsalamah, S.; Alshahrani, A.; Hayat, S.; Phi, N. Enhancing IoT cybersecurity through lean-based hybrid feature selection and ensemble learning: A visual analytics approach to intrusion detection. PLoS ONE 2025, 20, e0328050. [Google Scholar] [CrossRef]
- Pokhrel, S.; Abbas, R.; Aryal, B. IoT Security: Botnet detection in IoT using Machine learning. arXiv 2021, arXiv:2104.02231. [Google Scholar] [CrossRef]
- Gonçalves, C.B.; Souza, J.R.; Fernandes, H. CNN architecture optimization using bio-inspired algorithms for breast cancer detection in infrared images. Comput. Biol. Med. 2022, 142, 105205. [Google Scholar] [CrossRef] [PubMed]
- Alharbi, A.; Alosaimi, W.; Alyami, H.; Rauf, H.T.; Damaševičius, R. Botnet Attack Detection Using Local Global Best Bat Algorithm for Industrial Internet of Things. Electronics 2021, 10, 1341. [Google Scholar] [CrossRef]
- Nematzadeh, S.; Kiani, F.; Torkamanian-Afshar, M.; Aydin, N. Tuning hyperparameters of machine learning algorithms and deep neural networks using metaheuristics: A bioinformatics study on biomedical and biological cases. Comput. Biol. Chem. 2022, 97, 107619. [Google Scholar] [CrossRef] [PubMed]
- Brodzicki, A.; Piekarski, M.; Jaworek-Korjakowska, J. The Whale Optimization Algorithm Approach for Deep Neural Networks. Sensors 2021, 21, 8003. [Google Scholar] [CrossRef]
- Ali, M.H.; Jaber, M.M.; Abd, S.K.; Rehman, A.; Awan, M.J.; Damaševičius, R.; Bahaj, S.A. Threat Analysis and Distributed Denial of Service (DDoS) Attack Recognition in the Internet of Things (IoT). Electronics 2022, 11, 494. [Google Scholar] [CrossRef]
- Abbasi, F.; Naderan, M.; Alavi, S.E. Intrusion Detection in IoT With Logistic Regression and Artificial Neural Network: Further Investigations on N-BaIoT Dataset Devices. J. Comput. Secur. 2021, 8, 27–42. [Google Scholar] [CrossRef]
- Daghighi, A. Integrating Deep Learning and Meta-Heuristics for Enhanced IoT Security and Energy Efficiency. Int. J. Ind. Eng. Constr. Manag. 2025, 1, 39–50. [Google Scholar]
- Maazalahi, M.; Hosseini, S. Machine learning and metaheuristic optimization algorithms for feature selection and botnet attack detection. Knowl. Inf. Syst. 2025, 67, 3549–3597. [Google Scholar] [CrossRef]
- Maazalahi, M.; Hosseini, S. A Novel Hybrid Method Using Grey Wolf Algorithm and Genetic Algorithm for IoT Botnet DDoS Attacks Detection. Int. J. Comput. Intell. Syst. 2025, 18, 61. [Google Scholar] [CrossRef]
- Rabie, O.B.J.; Selvarajan, S.; Hasanin, T.; Alshareef, A.M.; Yogesh, C.K.; Uddin, M. A novel IoT intrusion detection framework using Decisive Red Fox optimization and descriptive back propagated radial basis function models. Sci. Rep. 2024, 14, 386. [Google Scholar] [CrossRef]
- Alqahtany, S.S.; Shaikh, A.; Alqazzaz, A. Enhanced Grey Wolf Optimization (EGWO) and random forest based mechanism for intrusion detection in IoT networks. Sci. Rep. 2025, 15, 1916. [Google Scholar] [CrossRef]
- Doshi, R.; Apthorpe, N.; Feamster, N. Machine Learning DDoS Detection for Consumer Internet of Things Devices. In Proceedings of the 2018 IEEE Security and Privacy Workshops (SPW), San Francisco, CA, USA, 24 May 2018; IEEE: San Francisco, CA, USA, 2018; pp. 29–35. [Google Scholar] [CrossRef]
- Anthi, E.; Williams, L.; Burnap, P. Pulse: An adaptive intrusion detection for the internet of things. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT—2018, London, UK, 28–29 March 2018; Institution of Engineering and Technology: London, UK, 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Shukla, P. ML-IDS: A machine learning approach to detect wormhole attacks in Internet of Things. In Proceedings of the 2017 Intelligent Systems Conference (IntelliSys), London, UK, 7–8 September 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 234–240. [Google Scholar] [CrossRef]
- Deshmukh, A.; Ravulakollu, K. An Efficient CNN-Based Intrusion Detection System for IoT: Use Case Towards Cybersecurity. Technologies 2024, 12, 203. [Google Scholar] [CrossRef]
- Marques Da Silva Cardoso, A.; Fernandes Lopes, R.; Soares Teles, A.; Benedito Veras Magalhaes, F. Poster Abstract: Real-Time DDoS Detection Based on Complex Event Processing for IoT. In Proceedings of the 2018 IEEE/ACM Third International Conference on Internet-of-Things Design and Implementation (IoTDI), Orlando, FL, USA, 17–20 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 273–274. [Google Scholar] [CrossRef]
- Idrissi, I.; Boukabous, M.; Azizi, M.; Moussaoui, O.; El Fadili, H. Toward a deep learning-based intrusion detection system for IoT against botnet attacks. IAES Int. J. Artif. Intell. 2021, 10, 110. [Google Scholar] [CrossRef]
- Saba, T.; Rehman, A.; Sadad, T.; Kolivand, H.; Bahaj, S.A. Anomaly-based intrusion detection system for IoT networks through deep learning model. Comput. Electr. Eng. 2022, 99, 107810. [Google Scholar] [CrossRef]
- De La Torre Parra, G.; Rad, P.; Choo, K.-K.R.; Beebe, N. Detecting Internet of Things attacks using distributed deep learning. J. Netw. Comput. Appl. 2020, 163, 102662. [Google Scholar] [CrossRef]
- Choudhary, V.; Tanwar, S.; Choudhury, T.; Kotecha, K. Towards secure IoT networks: A comprehensive study of metaheuristic algorithms in conjunction with CNN using a self-generated dataset. MethodsX 2024, 12, 102747. [Google Scholar] [CrossRef] [PubMed]
- Alserhani, F.M. Integrating deep learning and metaheuristics algorithms for blockchain-based reassurance data management in the detection of malicious IoT nodes. Peer-Peer Netw. Appl. 2024, 17, 3856–3882. [Google Scholar] [CrossRef]
- Hsieh, T.-H.; Chou, C.-L.; Lan, Y.-P.; Ting, P.-H.; Lin, C.-T. Fast and Robust Infrared Image Small Target Detection Based on the Convolution of Layered Gradient Kernel. IEEE Access 2021, 9, 94889–94900. [Google Scholar] [CrossRef]
- Hinton, G.E.; Srivastava, N.; Krizhevsky, A.; Sutskever, I.; Salakhutdinov, R.R. Improving neural networks by preventing co-adaptation of feature detectors. arXiv 2012, arXiv:1207.0580. [Google Scholar] [CrossRef]




| Value | Statistics |
|---|---|
| Size of the outgoing package | Mean and variance |
| count of Packet | Number |
| Jittering packets | Variance, mean, and number |
| The combined packet sizes of incoming and outgoing packet arrivals | Covariance, magnitude, correlation coefficient, and radius |
| Hyper-Parameters | An Explanation | Range of Values | Type of Data |
|---|---|---|---|
| Con1-filter | Convolutional kernel count | [100,600] | Integer |
| Con1-length | Convolutional filter length | [1,5] | Integer |
| Con1-activation | The convolutional layer’s activation function | ReLU, Tanh, Sigmoid | Integer |
| Con1-F2 dropout | The likelihood of dropouts between layers | [0.4, 0.8] | Float |
| F2-neuron | The second layer’s neuron count | [256,1024] | Integer |
| F2-activation | Activation function in layer two | ReLU, Tanh, Sigmoid | Integer |
| F3-neuron | Neuron count in the layer three | [256,1024] | Integer |
| F3-activation | Activation function in the layer three | ReLU, Tanh, Sigmoid | Integer |
| Batch size | Batch size for training | [16,200] | Integer |
| Learning rate | Weight update learning rate | [0.01, 1] | Float |
| Hyperparameter | Value |
|---|---|
| num_filters | 58 |
| kernel_size | 4 |
| conv_activation | relu |
| dropout_rate | 0.1210841870703586 |
| fc2_neurons | 685 |
| fc2_activation | Relu |
| fc3_neurons | 887 |
| fc3_activation | relu |
| batch_size | 33 |
| learning_rate | 0.00041245518708514576 |
| Accuracy | Average Precision | Kappa Coefficient | Hamming Loss | Jaccard Similarity Coefficient |
|---|---|---|---|---|
| 0.9556 | 0.9697 | 0.9500 | 0.0444 | 0.9226 |
| Techniques | Accuracy | Average Accuracy | Coefficient of Kappa | Loss of Hamming | Jaccard Similarity Coefficient |
|---|---|---|---|---|---|
| SVM (Support Vector Machine) | 0.91 | 0.92 | 0.81 | 0.92 | 0.84 |
| APSO-WOA-Enhanced FNN | 0.59 | 0.81 | 0.54 | 0.597 | 0.42 |
| APSO-Enhanced FNN | 0.83 | 0.85 | 0.81 | 0.84 | 0.72 |
| APSO-Enhanced CNN | 0.931 | 0.942 | 0.822 | 0.932 | 0.88 |
| APSO-WOA-Enhanced CNN | 0.9454 | 0.952 | 0.936 | 0.944 | 0.9 |
| FW-CNN | 0.9556 | 0.9697 | 0.9500 | 0.0444 | 0.9226 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Elsayed, E.B.; Yassin, A.S.; Fahmy, H. A Novel Hybrid GWO-RFO Metaheuristic Algorithm for Optimizing 1D-CNN Hyperparameters in IoT Intrusion Detection Systems. Information 2025, 16, 1103. https://doi.org/10.3390/info16121103
Elsayed EB, Yassin AS, Fahmy H. A Novel Hybrid GWO-RFO Metaheuristic Algorithm for Optimizing 1D-CNN Hyperparameters in IoT Intrusion Detection Systems. Information. 2025; 16(12):1103. https://doi.org/10.3390/info16121103
Chicago/Turabian StyleElsayed, Eslam Bokhory, Abdalla Sayed Yassin, and Hanan Fahmy. 2025. "A Novel Hybrid GWO-RFO Metaheuristic Algorithm for Optimizing 1D-CNN Hyperparameters in IoT Intrusion Detection Systems" Information 16, no. 12: 1103. https://doi.org/10.3390/info16121103
APA StyleElsayed, E. B., Yassin, A. S., & Fahmy, H. (2025). A Novel Hybrid GWO-RFO Metaheuristic Algorithm for Optimizing 1D-CNN Hyperparameters in IoT Intrusion Detection Systems. Information, 16(12), 1103. https://doi.org/10.3390/info16121103








