A Quantum-Safe Software-Defined Deterministic Internet of Things (IoT) with Hardware-Enforced Cyber-Security for Critical Infrastructures
Abstract
1. Introduction
- (1)
- Ultra-high reliability/availability, with at least 99.999% availability (with less than 1 h of down-time in 10 years of operation);
- (2)
- “Ultra-low-latency” (ULL) communications;
- (3)
- Deterministic end-to-end QoS guarantees, i.e., delay and jitter guarantees; and
- (4)
- Guaranteed immunity to external cyber-attacks, especially layer-3 DoS/DDoS attacks.
- (1)
- (2)
- (3)
- (4)
- Packets are encrypted and authenticated with quantum-safe ciphers, to withstand attacks by Quantum Computers [32];
- (5)
- Each nation can significantly strengthen its national security. The annual number of successful “external” cyber-attacks targeting a nation’s critical infrastructure can be reduced to zero [32].
- (6)
- The global costs of cyber-crime to society, estimated to exceed USD 10 trillion annually (in 2025), can be significantly reduced [32].
- (7)
- (8)
- The security of an SDD-WAN is significantly improved compared with existing classical networks, and is determined by the computational hardness of cracking Symmetric (secret) Key Cryptography (SKC) (see Section 5).
- (9)
- The SDD-WANs can enable a hybrid Classical-Quantum network by integrating a QKD network with a classical forwarding-plane with “authenticated channels” with full-immunity to external cyber-attacks (see Section 5). It is well-known that QKD networks require “authenticated classical channels” for control [37].
- (10)
- According to the US “National Security Agency” (NSA), QKD networks suffer from several vulnerabilities. The solutions typically require the use of Symmetric Key Cryptography, which lowers the security of QKD networks to the computational hardness of cracking SKC. As a result of these vulnerabilities, the US NSA does not recommend QKD networks. The SDD-WANs offer comparable security to QKD networks in practice, secured by the computational hardness of cracking SKC. Hence, the SDD-WANs can provide a solution to today’s cyber-security crisis, until that future time when QKD networks are ready to be deployed on a large-scale to millions/billions of users worldwide at a reasonable cost (see Section 5).
2. Review
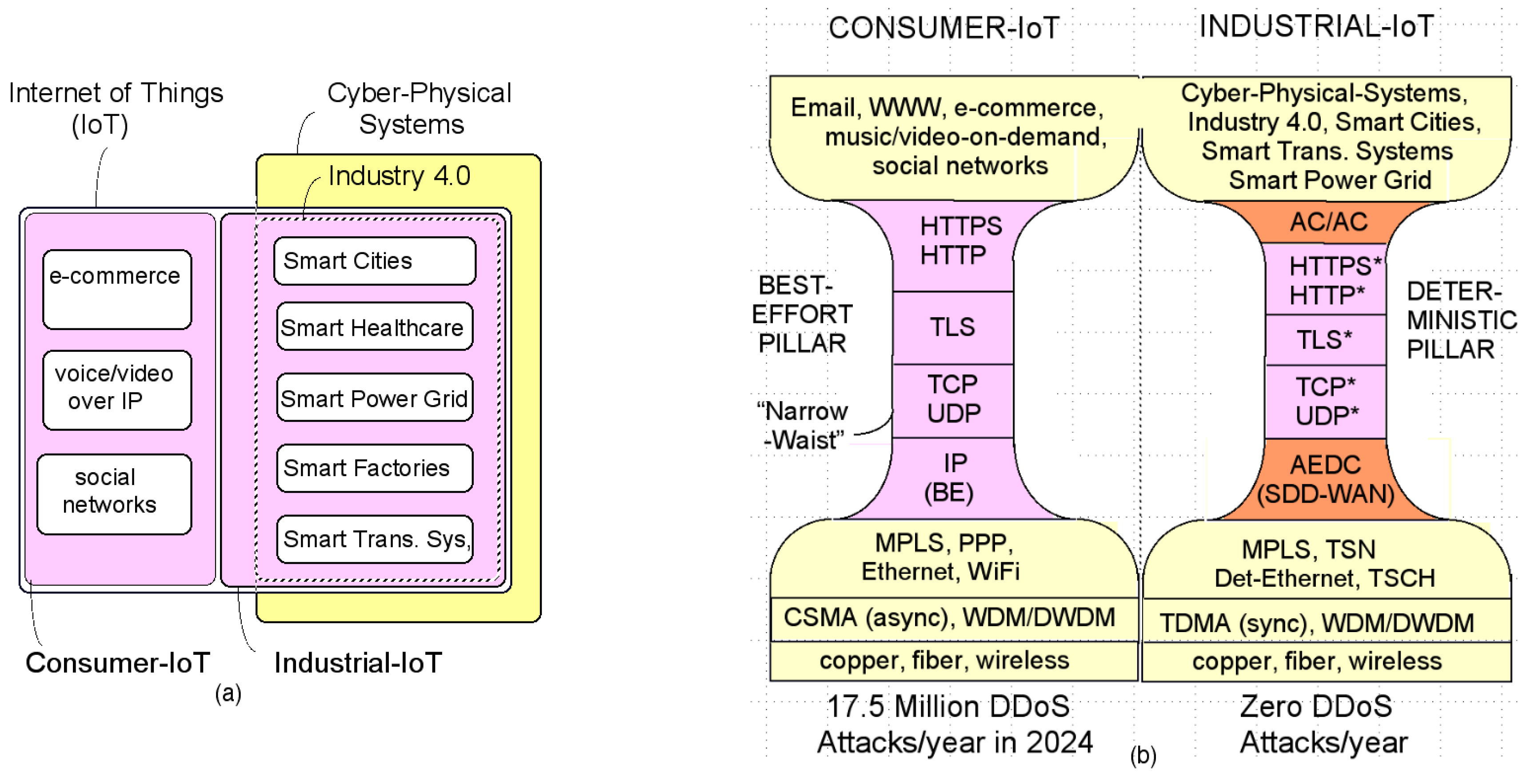
2.1. Problems with the Consumer IoT
2.1.1. The Narrow-Waist Best-Effort Service Model
2.1.2. DDoS Attacks against Servers and Networks
2.1.3. TLS—Does It Provide Security or Confidentiality?
2.1.4. TLS—Provides No Protection against “LOG4J” Cyber-Attacks
2.2. TCP, TLS, and HTTPS in the Deterministic Pillar
2.3. Access-Control Systems and Intrusion Detection Systems
2.4. Cryptography
2.4.1. Symmetric (Secret) Key Cryptography (SKC)
2.4.2. “Authenticated Encryption” (AE)
2.4.3. “Public Key Cryptography” (PKC)
2.4.4. Post-Quantum Cryptography (PQC)
2.5. QoS Guarantees in the IoT
2.5.1. QoS Guarantees for Best-Effort Traffic
2.5.2. IEEE and IETF Activities for Improved QoS
2.5.3. The Search for Ultra-Low-Latency Layer-3 Networks
2.5.4. Birkhoff–von Neumann (BVN) Stochastic Matrix Decomposition
2.5.5. The SDD-IIoT
2.6. FPGAs with Terabits of IO Capacity
- (1)
- The tasks of routing and scheduling of D-flows have been removed from layer-3 routers and have been migrated to the SDN control plane;
- (2)
- (3)
- D-switches do not need gigabytes of high-speed memory to store insecure layer-3 routing tables;
- (4)
- D-switches do not need a processor or a Linux operating system running the insecure layer-3 “Berkeley Sockets” software to implement insecure layer-3 protocols such as BGP.
- (5)
- D-switches are also much easier to secure, compared to a layer-3 BE-IP router.
- (6)
- One-time-programmable FPGAs can also be used to improve security, as their functionality cannot be modified.
The Intel Stratix FPGAs
3. The Deterministic IIoT—Key Features
3.1. Secured Components
3.2. Deterministic Schedules (D-Schedules)
3.3. Deterministic Transceivers
3.4. IP Packet Fragmentation
3.5. Deterministic VPNs (D-VPNs)
The “Admission-Control/Access-Control” (AC/AC) System
- the IoT Controllers, the WAN Controllers, and the Enterprise Controllers.
- Employees; secured computers; secured databases;
- D-Transceivers; DVNs; D-VPNs.
3.6. Authorization Check
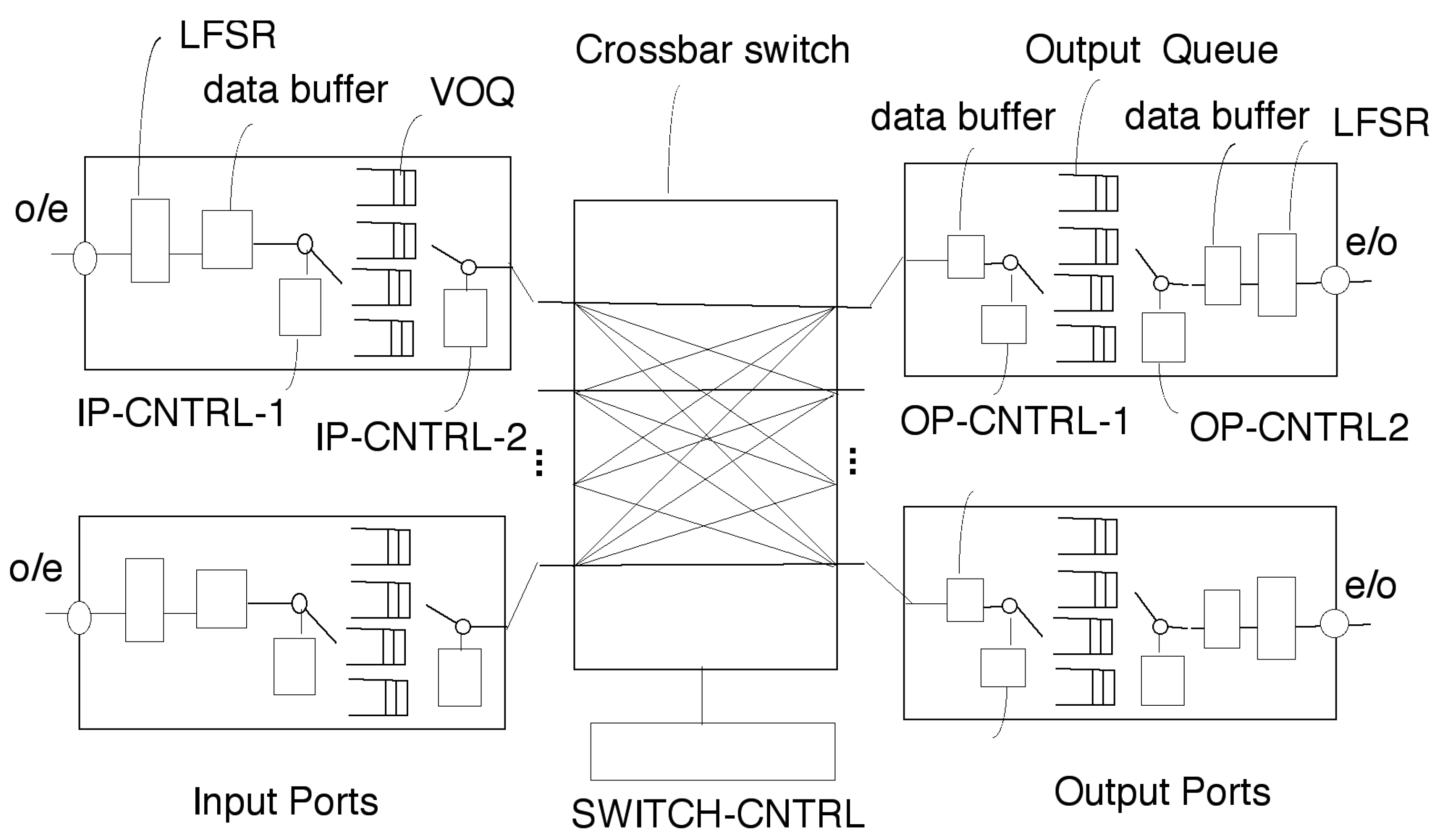
3.7. The D-Switch—CIOQ Architecture
3.7.1. Configuring the D-Switches and D-Transceivers
3.7.2. Synchronization
3.8. Using MPLS-like Flow Labels in Sub-Layer 3a
3.9. D-Switches and D-Transceivers Secured with Quantum-Safe Ciphers
- (1)
- Reset all the controllers to a known initial state.
- (2)
- Update the control vector for one specific controller.
- (3)
- Reset the flow table to a known initial state (if a flow table is used).
- (4)
- Write a new row of data into the flow table (if a flow table is used).
- (5)
- Update a D-schedule for an input port.
4. The SDN Control Plane
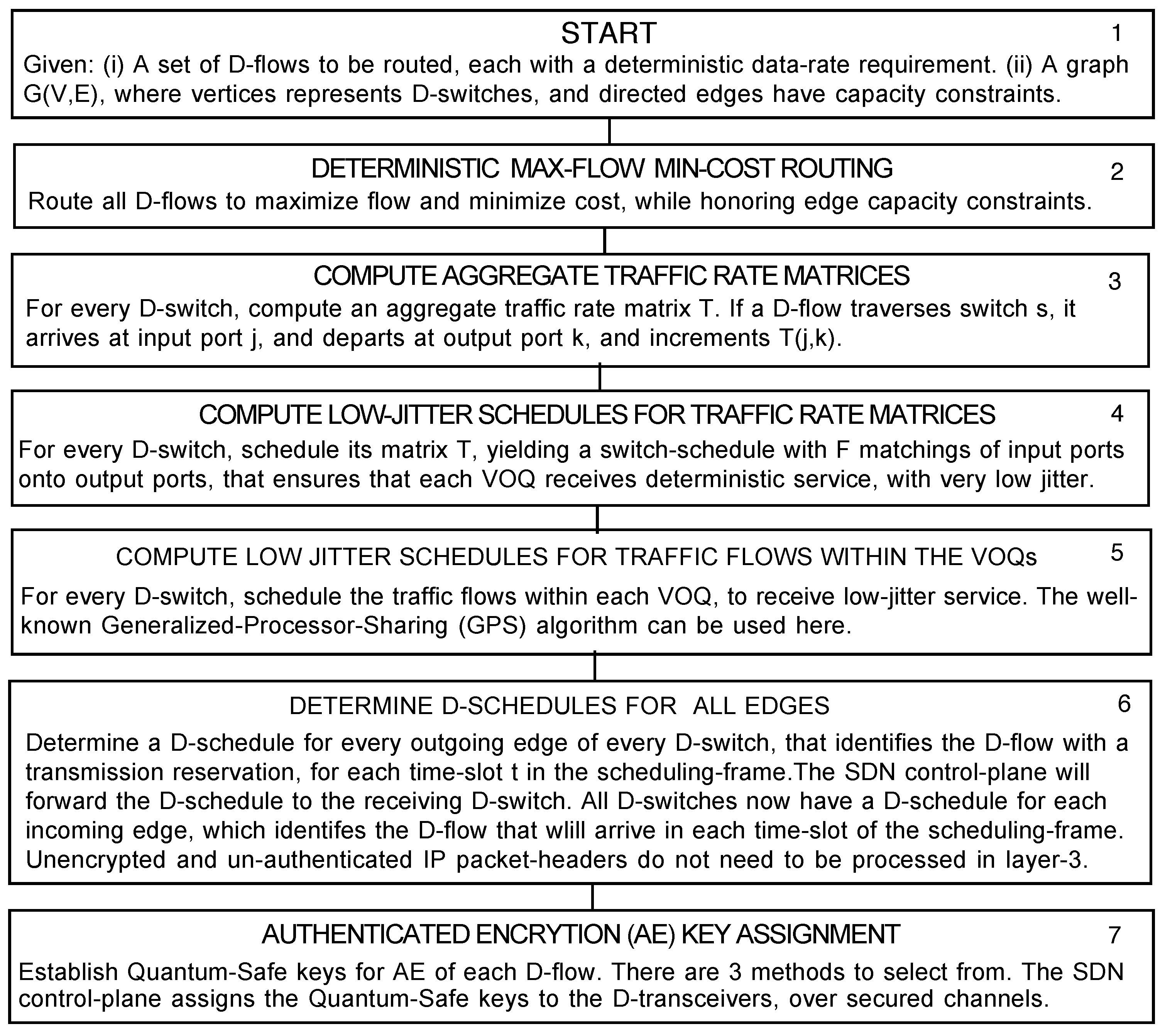
4.1. Max-Flow–Min-Cost Routing of D-Flows
4.2. Compute Aggregate Traffic Rate Matrices
4.3. Compute Low-Jitter Schedules for VOQs
4.4. Compute Low-Jitter Schedules for D-Flows
4.5. Compute D-Schedules for D-Switches
4.6. Forward D-Schedules to Neighbours
4.7. Authenticated Encryption (AE) Key Assignment
4.8. Summary—SDN Flowchart
- (1)
- D-switches to process unencrypted and unauthenticated IP packet headers to perform insecure layer-3 routing;
- (2)
- Many gigabytes of high-speed RAM to store insecure layer-3 routing tables for the layer-3 routing protocol BGP;
- (3)
- Each D-switch to contain a processor running a Linux operating system and the insecure Berkeley Sockets software to maintain insecure layer-3 protocols such as ICMP (“Internet Control Message Protocol”) and BGP;
- (4)
- Layer-3 “middle boxes”, which perform the “Network Address Translation” (NAT) needed for insecure layer-3 routing;
- (5)
- Layer-3 “Domain-Name-Servers”, which perform address resolution needed for insecure layer-3 routing.
Communications of the SDN control plane
5. Security Properties of the Deterministic IIoT
5.1. Vulnerabilities of QKD Networks
5.2. The SDD-WANs Can Enable Hybrid Classical-Quantum Networks
5.3. The SDD-WANs Can Supplant QKD Networks in the Near-Term
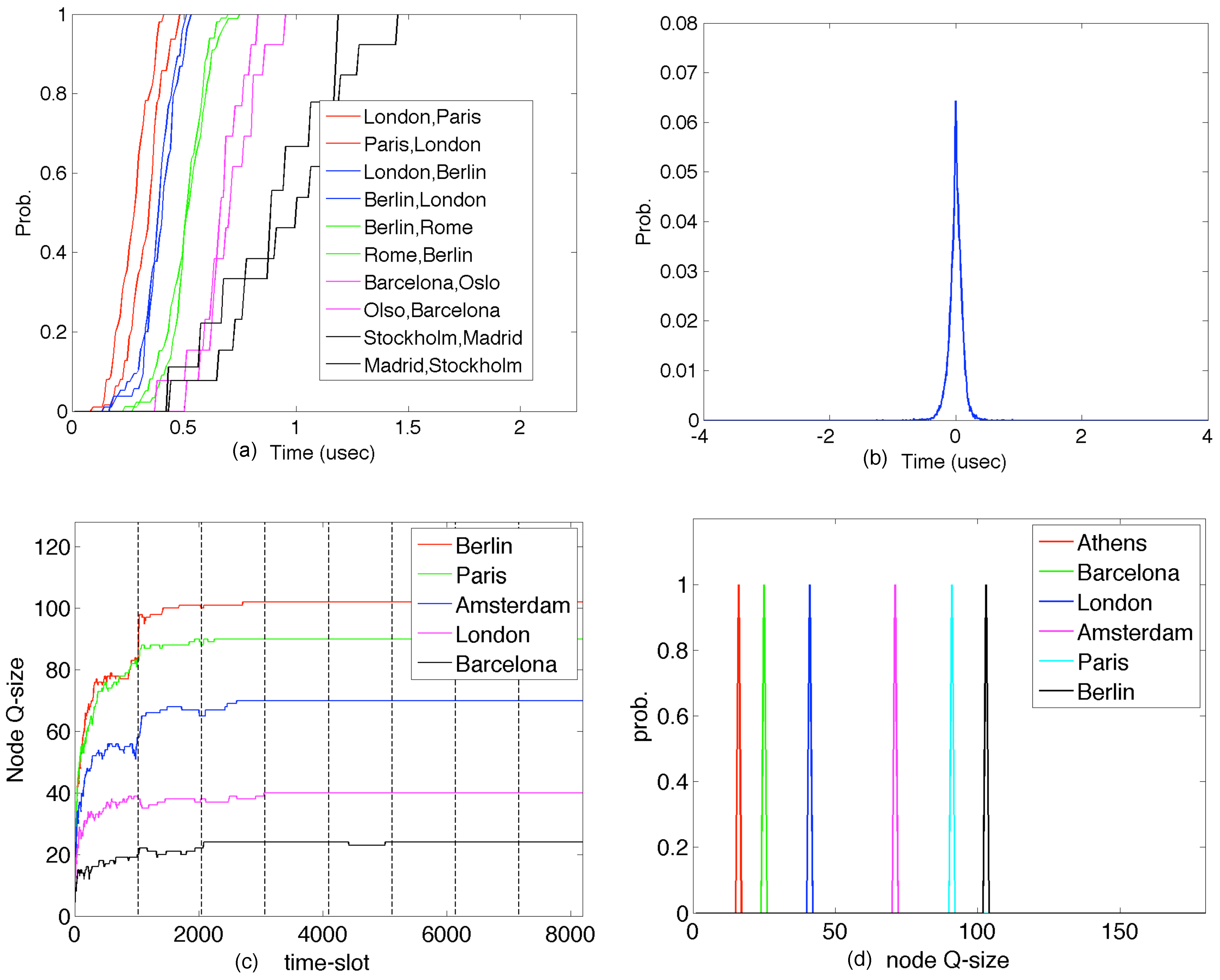
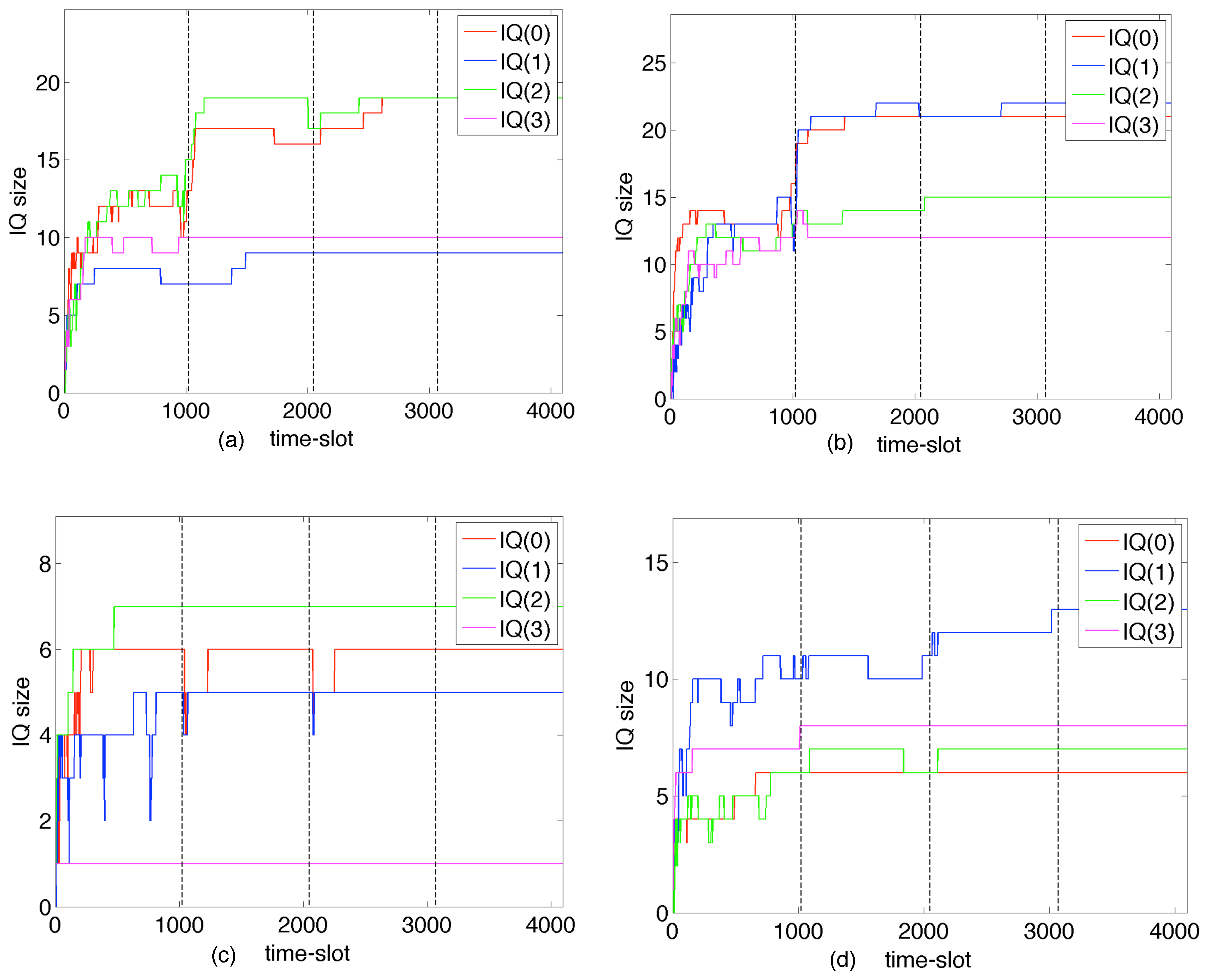
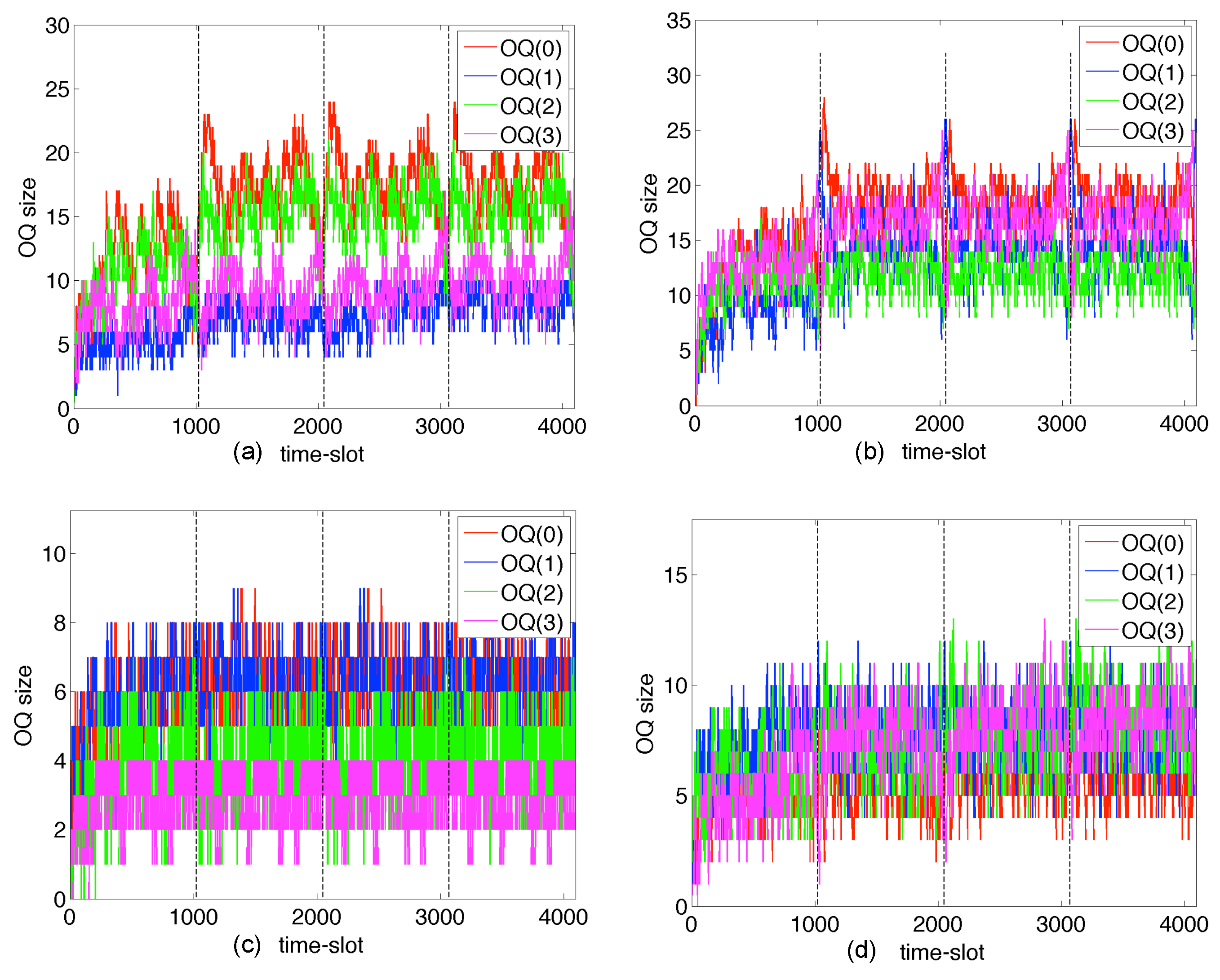
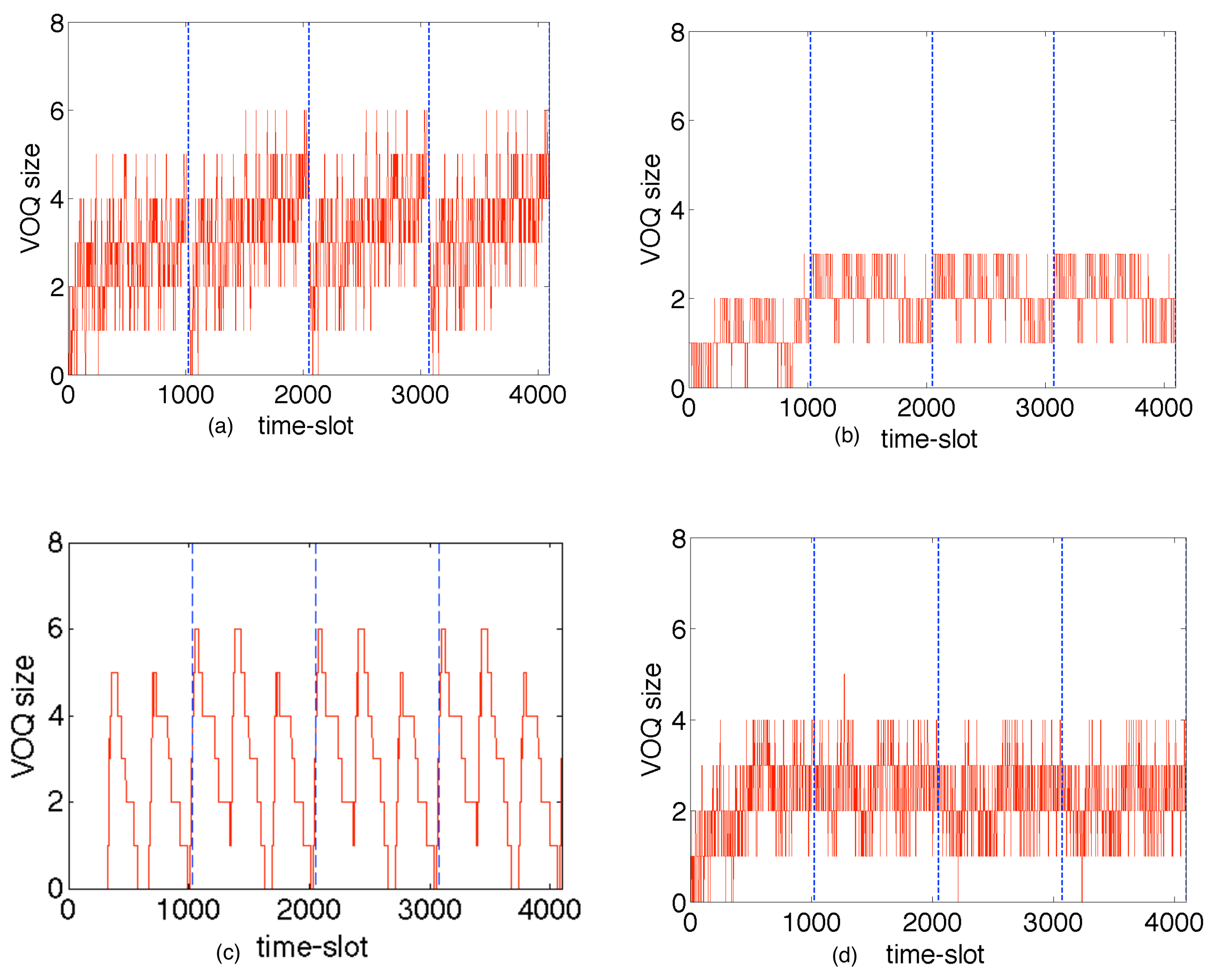
6. Experimental Results from the European Union
6.1. The BDP Buffer-Sizing Rule for BE-IP Routers
6.2. The Small Buffer-Sizing Rule for BE-IP Routers
6.3. A Deterministic Buffer-Sizing Rule for D-Switches
7. The Costs of the Layer-3 BE-IP Network
8. Conclusions
- (1)
- Fine-grain access-control to network bandwidth will eliminate all congestion, BufferBloat, and DoS/DDoS attacks in sub-layer-3a, reduce buffer-sizes by 100,000–1,000,000 times, and reduce end-to-end delays to the speed-of-light in fiber.
- (2)
- Each nation can significantly strengthen its national security by reducing the annual number of external cyber-attacks against its critical infrastructure to zero, secured by the computational hardness of cracking SKC/PQC. With a sufficiently strong knowledge base, each nation can also reduce or eliminate the number of internal cyber-attacks against its critical infrastructure. This benefit can have geo-political implications, i.e., Ukraine, Iran, and Israel could achieve immunity to external cyber-attacks relatively quickly.
- (3)
- It innovates the layer-3 infrastructure to include a deterministic pillar of communications and a forwarding plane for M2M traffic flows, using low-cost FPGAs. Network operators can save USD 100s of billions per year in reduced capital, energy, and operational costs.
- (4)
- It can reduce the global costs of cyber-crime to society, estimated to exceed USD 10 trillion per year in 2025. If the global costs of cyber-crime can be reduced by a modest 25%, the savings potentially exceed USD 2.5 trillion per year.
- (5)
- It can support the Metaverse by providing large increases in layer-3 capacity and security, while decreasing the capital and operational costs by USD 100s of billions per year.
- (6)
- In practice, the SDD-WANs can have comparable security to QKD networks, as determined by the computational hardness of cracking SKC/PKC. The SDD-WANs thus provide a classical network with exceptionally strong cyber-security.
- (7)
- The SDD-WANs can enable hybrid Classical-Quantum networks by integrating a QKD network with a programmable SDD-WAN that provides “authenticated classical channels” and immunity to external cyber-attacks. Such channels are needed for the control of QKD networks and the future Quantum Internet. Given a sufficiently strong knowledge base for the Zero Trust Architectures, the number of internal cyber-attacks can also be significantly reduced or eliminated.
- (8)
- According to the US “National Security Agency”, QKD networks have several vulnerabilities, i.e., they cannot authenticate the source and are vulnerable to insider attacks and DoS attacks. The solutions typically require the use of SKC/PQC, which lowers the security of QKD to the computational hardness of cracking SKC/PQC. As a result of these vulnerabilities, three national security agencies representing thousands of cyber-security experts (the American NSA, the British NSCS, and French ANSSI) agree that QKD networks should not be recommended at this time. In practice, SDD-WANs can have comparable security to QKD networks, as determined by the computational hardness of cracking SKC/PKC. The SDD-WANs can thus provide a solution to today’s cyber-security crisis until that future time when QKD networks are ready to be deployed on a large-scale to millions/billions of users worldwide in a cost-effective manner.
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Abbreviation | Description |
|---|---|
| AE | Authenticated Encryption |
| AEDC | Authenticated and Encrypted Deterministic Channel (i.e., a D-flow) |
| AES | Advanced Encryption Standard (a cipher) |
| BE | Best Effort |
| BE-IP, BE-flow | Best-Effort Internet Protocol, Best-Effort Traffic Flow |
| BE-VPN | Best-Effort “Virtual Private Network” (in the Consumer IoT) |
| BGP | “Border Gateway Routing Protocol” (to Route Packets) |
| BSD | “Berkeley Sockets Distribution” Software (to Program “Sockets”) |
| C-IoT | Consumer IoT |
| D, D-flow, | Deterministic, Deterministic Traffic Flow (i.e., AEDC) |
| D-switch, D-IIoT | Deterministic Packet Switch, Deterministic Industrial IoT |
| D-Schedule | a ;“Gine-Grain” Deterministic Periodic Schedule, to Control a D-Switch |
| DetNet | “Deterministic Networking” Group in the IETF |
| DetNet Converged WAN | Converged WAN Network (Proposed by the DetNet Group of the IETF) |
| D-VPN | Deterministic Virtual Private Network |
| ETSI | European Telecommunications Standards Institute |
| IETF | Internet Engineering Task Force |
| ICMP, IGP | Internet Control Message Protocol, Interior Gateway Protocol |
| IDS, IDPS | Intrusion Detection System, Intrusion Detection and Prevention System |
| IKEV1, IKEV2 | IETF Internet Key Exchange, Version 1 and Version 2 |
| NIST | US National Institute for Standards in Technology |
| NSA | US National Security Agency |
| PKC, PKI | Public Key Cryptography, Public Key Infrastructure |
| PSK | Pre-Shared (Secret) Key |
| PQC | Post-Quantum Cryptography |
| SDN | Software-Defined Networking |
| SDD-WAN | Software-Defined Deterministic Wide-Area Network |
| SDD-IIoT | Software-Defined Deterministic Industrial Internet of Things |
| SKC | Symmetric Key Cryptography |
| TLS | Transport Layer Security ([42]) |
| ULL | Ultra-Low Latency |
| ZTA | Zero Trust Architecture |
| Threat/Attack Name | Type of Threat/Attack in Consumer IoT | Type of Threat/Attack in SDD-IIoT |
|---|---|---|
| DoS/DDoS Attack | Overloads server(s) with many malicious IP traffic flows from many compromised devices | —Effectively eliminated— SDD-IIoT does not use IP (or IP packet headers) |
| Spoofing attack | Modifies IP packet headers to masquerade as a trusted peer | —Effectively eliminated— SDD-IIoT does not use IP (or IP packet headers) |
| Phishing attack | Provides malicious email or link to malicious website | —Effectively eliminated— Links to malicious websites will not be pre-approved |
| Spear phishing attacks | Personalizes contact to individual; provides malicious email; or links to malicious website | —Effectively eliminated— links to malicious websites will not be pre-approved |
| Man-in-the-Middle (MITM) attack | Cyber-attacker is interposed between two communicating entities by spoofing | —Effectively eliminated— spoofing attacks eliminated (IP is not used) |
| Replay attack | A valid encrypted packet is observed and recorded, and re-introduced at a later time, as a malicious packet | —Effectively eliminated— Authorization check detects all malicious packets |
| Reconnaissance attack (Harvest-Now–Decrypt-Later attack) | Eavesdropping on encrypted TLS flows | —Effectively Eliminated— by quantum-safe ciphers |
| Malware attack (remote code execution attack) (application vulnerability attack) (cross-site scripting attack) (Ransomware attack) | Vulnerable host-computer can render control to cyber-attacker under special circumstances (i.e., Java remote code execution) | —Effectively eliminated— Links to malicious websites will not be pre-approved |
References
- Li, Z.; Uusitalo, M.A.; Shariatmadari, H.; Singh, B. 5G URLLC: Design Challenges and System Concepts. In Proceedings of the 2018 15th International Symposium on Wireless Communication Systems (ISWCS), Lisbon, Portugal, 28–31 August 2018; pp. 1–6. [Google Scholar]
- Pokhrel, S.R.; Ding, J.; Park, J.; Park, O.S.; Choi, J. Towards Enabling Critical mMTC: A Review of URLLC within mMTC. IEEE Access 2020, 8, 131796–131813. [Google Scholar] [CrossRef]
- Park, J.; Samarakoon, S.; Shiri, H.; Abdel-Aziz, M.K.; Nishio, T.; Elgabli, A.; Bennis, M. Extreme Ultra-Reliable and Low-Latency Communication. Nat. Electron. 2022, 5, 133–141. [Google Scholar] [CrossRef]
- Gevros, P.; Crowcroft, J.; Kirstein, P.; Bhatti, S. Congestion Control Mechanisms and the Best Effort Service Model. IEEE Netw. 2001, 15, 16–26. [Google Scholar] [CrossRef]
- Lefelhocz, C.; Lyles, B.; Shenker, S.; Zhang, L. Congestion Control for Best-Effort Service: Why we need a New Paradigm. IEEE Netw. 1996, 10, 10–19. [Google Scholar] [CrossRef]
- Afanasyev, A.; Tilly, N.; Reiher, P.; Kleinrock, L. Host-to-Host Congestion Control for TCP. IEEE Commun. Surv. Tutor. 2010, 12, 304–342. [Google Scholar] [CrossRef]
- Gettys, J.; Nichols, K. BufferBloat: Dark Buffers in the Internet. ACM Queue 2011, 9, 40–54. [Google Scholar] [CrossRef]
- Butler, K.; Farley, T.R.; McDaniel, P.; Rexford, J. A Survey of BGP Security Issues and Solutions. Proc. IEEE 2009, 98, 100–122. [Google Scholar] [CrossRef]
- Goldberg, S. Why is it Taking So Long to Secure Internet Routing? Commun. ACM 2014, 57, 56–63. [Google Scholar] [CrossRef]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, Opportunities, and Directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- CISCO. Cisco Annual Internet Report (2018–2023). Available online: https://www.cisco.com/c/en/us/solutions/collateral/executive-perspectives/annual-internet-report/white-paper-c11-741490.html (accessed on 7 March 2024).
- CISCO. Global—2021 Forecast Highlights. Available online: https://www.cisco.com/c/dam/m/en_us/solutions/service-provider/vni-forecast-highlights/pdf/Global_2021_Forecast_Highlights.pdf (accessed on 7 March 2024).
- US National Academy of Engineering. NAE Grand Challenges for Engineering: Secure Cyberspace. Available online: https://www.engineeringchallenges.org/challenges/cyberspace.aspx (accessed on 7 March 2024).
- Butun, I.; Osterberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, Attacks, and Countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Khan, M.A.; Salah, K. IoT Security: Review, Blockchain Solutions, and Open Challenges, Elsevier. Future Gener. Comput. Syst. 2018, 82, 395–411. [Google Scholar] [CrossRef]
- Hassija, V.; Chamola, V.; Saxena, V.; Jain, D.; Goyal, P.; Sikdar, B. A Survey on IoT Security: Application Areas, Security Threats, and Solution Architectures. IEEE Access 2019, 7, 82721–82743. [Google Scholar] [CrossRef]
- Neshenko, N.; Bou-Harb, E.; Crichigno, J.; Kaddoum, G.; Ghani, N. Demystifying IoT Security: An Exhaustive Survey on IoT Vulnerabilities and a First Empirical Look on Internet-Scale IoT Exploitations. IEEE Commun. Surv. Tutor. 2019, 21, 2702–2733. [Google Scholar] [CrossRef]
- Karie, N.M.; Sahri, N.M.; Yang, W.; Valli, C.; Kebande, V.R. A Review of Security Standards and Frameworks for IoT-Based Smart Environments. IEEE Access 2021, 9, 121975–121995. [Google Scholar] [CrossRef]
- Xin, Y.; Kong, L.; Chen, Y.; Li, Y.; Zhu, H.; Gao, M.; Hou, H.; Wang, C. Machine Learning and Deep Learning Methods for Cybersecurity. IEEE Access 2018, 6, 35365–35381. [Google Scholar] [CrossRef]
- Al-Garadi, M.A.; Mohamed, A.; Al-Ali, A.K.; Du, X.; Ali, I.; Guizani, M. A Survey of Machine and Deep Learning Methods for Internet of Things (IoT) Security. IEEE Commun. Surv. Tutor. 2020, 22, 1646–1685. [Google Scholar] [CrossRef]
- Hussain, F.; Hussain, R.; Hassan, S.A.; Hossain, E. Machine Learning in IoT Security: Current Solutions and Future Challenges. IEEE Commun. Surv. Tutor. 2020, 22, 1686–1721. [Google Scholar] [CrossRef]
- Demertzi, V.; Demertzis, S.; Demertzis, K. An Overview of Cyber Threats, Attacks and Countermeasures on the Primary Domains of Smart Cities. Appl. Sci. 2023, 13, 790. [Google Scholar] [CrossRef]
- De Azambuja, A.J.; Plesker, C.; Schützer, K.; Anderl, R.; Schleich, B.; Almeida, V.R. Artificial Intelligence-Based Cyber Security in the Context of Industry 4.0—A Survey. Electronics 2023, 12, 1920. [Google Scholar] [CrossRef]
- US NSA (National Security Agency). Quantum Computing and Post Quantum Cryptography, FAQs (Frequently Asked Questions), Document PP-21-1120, 4 August 2021. Available online: https://media.defense.gov/2021/Aug/04/2002821837/-1/-1/1/Quantum_FAQs_20210804.PDF (accessed on 7 March 2024).
- US NSA (National Security Agency). Quantum Key Distribution (QKD) and Quantum Cryptography (QC). Available online: https://www.nsa.gov/Cybersecurity/Quantum-Key-Distribution-QKD-and-Quantum-Cryptography-QC/ (accessed on 10 March 2024).
- US CISA (Cybersecurity and Infrastructure Security Agency). Critical Infrastructure Security and Resilience; USA CISA: Arlington, VA, USA, 2023. Available online: https://www.cisa.gov/topics/critical-infrastructure-security-and-resilience (accessed on 8 March 2024).
- NATO, EU-NATO Task Force on the Resilience of Critical Infrastructure, Final Assessment Report. Available online: https://commission.europa.eu/system/files/2023-06/EU-NATO_Final%20Assessment%20Report%20Digital.pdf (accessed on 8 March 2024).
- Tehranipoor, M.; Wang, C. (Eds.) Introduction to Hardware Security and Trust; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2011. [Google Scholar]
- Maistri, P. Countermeasures against Fault Attacks: The Good, the Bad, and the Ugly. In Proceedings of the 2011 IEEE 17th International On-Line Testing Symposium, Athens, Greece, 13–15 July 2011; pp. 134–137. [Google Scholar]
- Jin, Y. Introduction to Hardware Security. Electronics 2015, 4, 763. [Google Scholar] [CrossRef]
- Alioto, M. Trends in Hardware Security: From Basics to ASICs. IEEE Solid-State Circuits Mag. 2019, 11, 56–74. [Google Scholar] [CrossRef]
- Szymanski, T.H. The Cyber Security via Determinism Paradigm for a Quantum Safe Zero Trust Deterministic Internet of Things (IoT). IEEE Access 2022, 10, 45893–45930. [Google Scholar] [CrossRef]
- Szymanski, T.H. An Ultra Low Latency Guaranteed-Rate Internet for Cloud Services. IEEE Trans. Netw. 2014, 24, 123–136. [Google Scholar] [CrossRef]
- Szymanski, T.H. Supporting Consumer Services in a Deterministic Industrial Internet Core Network. IEEE Commun. Mag. 2016, 54, 110–117. [Google Scholar] [CrossRef]
- Szymanski, T.H. Securing the Industrial-Tactile Internet of Things with Deterministic Silicon Photonic Switches. IEEE Access 2016, 4, 8236–8249. [Google Scholar] [CrossRef]
- Szymanski, T.H. Security and Privacy for a Green Internet of Things. IEEE IT Prof. 2017, 19, 34–41. [Google Scholar] [CrossRef]
- Wang, L.J.; Zhang, K.Y.; Wang, J.Y.; Cheng, J.; Yang, Y.H.; Tang, S.B.; Yan, D.; Tang, Y.L.; Liu, Z.; Yu, Y.; et al. Experimental Authentication of Quantum Key Distribution with Post-Quantum Cryptography. NPJ Quantum Inf. 2021, 7, 67. [Google Scholar] [CrossRef]
- Kleinrock, L.; National Research Council; NRENAISSANCE Committee. Realizing the Internet Future: The Internet and Beyond; National Academy Press: Washington, DC, USA, 1994. [Google Scholar]
- Popa, L.; Ghodsi, A.; Stoica, I. HTTP as the Narrow Waist of the Future Internet. In Proceedings of the 9th ACM SIGCOMM Workshop on Hot Topics in Networks, Monterey, CA, USA, 20–21 October 2010; pp. 1–6. [Google Scholar]
- Akhshabi, S.; Dovrolis, C. The Evolution of Layered Protocol Stacks leads to an Hourglass-Shaped Architecture. In Proceedings of the ACM SIGCOMM 2011 Conference, Toronto, ON, Canada, 15–19 August 2011; pp. 206–217. [Google Scholar]
- Beck, M. On the Hourglass Model. Commun. ACM 2019, 62, 48–57. [Google Scholar] [CrossRef]
- Rescorla, E. IETF (Internet Engineering Task Force) RFC (Request for Comments) 8446, The Transport Layer Security (TLS) Protocol Version 1.3; 2018; pp. 1–160. Available online: https://datatracker.ietf.org/doc/html/rfc8446 (accessed on 8 March 2024).
- Douligeris, C.; Mitrokotsa, A. DDoS Attacks and Defense Mechanisms: Classification and State-of-the-Art. Comput. Netw. 2004, 44, 643–666. [Google Scholar] [CrossRef]
- Yan, Q.; Yu, F.R. Distributed Denial of Service Attacks in Software-Defined Networking with Cloud Computing. IEEE Commun. Mag. 2015, 53, 52–59. [Google Scholar] [CrossRef]
- Somani, G.; Gaur, M.S.; Sanghi, D.; Conti, M.; Buyya, R. DDoS Attacks in Cloud Computing: Issues, Taxonomy, and Future Directions. Comput. Commun. 2017, 107, 30–48. [Google Scholar] [CrossRef]
- Zlomislić, V.; Fertalj, K.; Sruk, V. Denial of Service Attacks, Defences and Research Challenges. Clust. Comput. 2017, 20, 661–671. [Google Scholar] [CrossRef]
- Bawany, N.Z.; Shamsi, J.A.; Salah, K. DDoS Attack Detection and Mitigation using SDN: Methods, Practices, and Solutions. Arab. J. Sci. Eng. 2017, 42, 425–441. [Google Scholar] [CrossRef]
- Praseed, A.; Thilagam, P.S. DDoS Attacks at the Application Layer: Challenges and Research Perspectives for Safeguarding Web Applications. IEEE Commun. Surv. Tutor. 2018, 21, 661–685. [Google Scholar] [CrossRef]
- Osterweil, E.; Stavrou, A.; Zhang, L. 21 Years of Distributed Denial-of-Service: A Call to Action. IEEE Comput. 2020, 53, 94–99. [Google Scholar] [CrossRef]
- Vishwakarma, R.; Jain, A.K. A Survey of DDoS Attacking Techniques and Defence Mechanisms in the IoT Network. Telecommun. Syst. 2020, 73, 3–25. [Google Scholar] [CrossRef]
- Eliyan, L.F.; Di Pietro, R. DoS and DDoS Attacks in Software Defined Networks: A Survey of Existing Solutions and Research Challenges. Future Gener. Comput. Syst. 2021, 122, 149–171. [Google Scholar] [CrossRef]
- Bhargavan, K.; Fournet, C.; Kohlweiss, M.; Pironti, A.; Strub, P.Y. Implementing TLS with Verified Cryptographic Security. In Proceedings of the 2013 IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 19–22 May 2013; pp. 445–459. [Google Scholar]
- Bürstinghaus-Steinbach, K.; Krauß, C.; Niederhagen, R.; Schneider, M. Post-quantum TLS on Embedded Systems: Integrating and Evaluating Kyber and Sphincs+ with mbed tTLS. In Proceedings of the 15th ACM Asia Conference on Computer and Communications Security, Taipei, Taiwan, 5–9 October 2020; pp. 841–852. [Google Scholar]
- Mell, P.; Marks, D.; McLarnon, M. A Denial-of-Service Resistant Intrusion Detection Architecture. Comput. Netw. 2000, 34, 641–658. [Google Scholar] [CrossRef]
- Jager, T.; Kohlar, F.; Schäge, S.; Schwenk, J. On the Security of TLS-DHE in the Standard Model. In Advances in Cryptology—CRYPTO 2012, Proceedings of the 32nd Annual Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2012; Springer: Berlin/Heidelberg, Germany, 2012; pp. 273–293. [Google Scholar]
- Krawczyk, H.; Paterson, K.G.; Wee, H. On the Security of the TLS Protocol: A Systematic Analysis. In Advances in Cryptology—CRYPTO 2013, Proceedings of the 33rd Annual Cryptology Conference, Santa Barbara, CA, USA, 18–22 August 2013; Springer: Berlin/Heidelberg, Germany, 2013; pp. 429–448. [Google Scholar]
- Eldewahi, A.E.; Sharfi, T.M.; Mansor, A.A.; Mohamed, N.A.; Alwahbani, S.M. SSL/TLS Attacks: Analysis and Evaluation. In Proceedings of the 2015 International Conference on Computing, Control, Networking, Electronics and Embedded Systems Engineering (ICCNEEE), Khartoum, Sudan, 7–9 September 2015; pp. 203–208. [Google Scholar]
- Sirohi, P.; Agarwal, A.; Tyagi, S. A Comprehensive Study on Security Attacks on SSL/TLS Protocol. In Proceedings of the 2016 2nd International Conference on Next Generation Computing Technologies (NGCT), Dehradun, India, 14–16 October 2016; pp. 893–898. [Google Scholar]
- Waked, L.; Mannan, M.; Youssef, A. The Sorry State of TLS Security in Enterprise Interception Appliances. Digit. Threat. Res. Pract. 2020, 1, 1–26. [Google Scholar] [CrossRef]
- Paracha, M.T.; Dubois, D.J.; Vallina-Rodriguez, N.; Choffnes, D. IoTLS: Understanding TLS Usage in Consumer IoT Devices. In Proceedings of the 21st ACM Internet Measurement Conference, New York, NY, USA, 2–4 November 2021; pp. 165–178. [Google Scholar]
- Meyer, C.; Schwenk, J. SoK: Lessons Learned from SSL/TLS Attacks. In International Workshop on Information Security Applications; Springer International Publishing: Cham, Switzerland, 2013; pp. 189–209. [Google Scholar]
- Sandhu, R.; Ferraiolo, D.; Kuhn, R. The NIST Model for Role-Based Access Control: Towards a Unified Standard. In Proceedings of the ACM Workshop Role-Based Access Control, Berlin, Germany, 26–27 July 2000; Volume 10, pp. 344287–344301. [Google Scholar]
- Kuhn, D.R.; Coyne, E.J.; Weil, T.R. Adding Attributes to Role-Based Access Control. IEEE Comput. 2010, 43, 79–81. [Google Scholar] [CrossRef]
- Hu, V.C.; Ferraiolo, D.; Kuhn, R.; Friedman, A.R.; Lang, A.J.; Cogdell, M.M.; Schnitzer, A.; Sandlin, K.; Miller, R.; Scarfone, K. Guide to Attribute Based Access Control (ABAC) Definition and Considerations (Draft). NIST Spec. Publ. 2013, 800, 1–54. [Google Scholar]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-Based Access Control. IEEE Comput. 2015, 16, 85–88. [Google Scholar] [CrossRef]
- The White House. Executive Order on Improving the Nation’s Cybersecurity; The White House: Washington, DC, USA, 2021. Available online: https://www.whitehouse.gov/briefing-room/presidential-actions/2021/05/12/executive-order-on-improving-the-nations-cybersecurity/ (accessed on 8 March 2024).
- US NIST (National Institute of Standards and Technology). Zero Trust Architecture, Publication SP-800-207. August 2020. Available online: https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-207.pdf (accessed on 7 March 2024).
- Kerman, A.; Scarfone, K.; Symington, S.; Barker, W. Implementing a Zero Trust Architecture; NIST (National Institute of Standards and Technology): Gaithersburg, MD, USA, 2022. Available online: https://www.nccoe.nist.gov/sites/default/files/2022-12/zta-nist-sp-1800-35e-preliminary-draft.pdf (accessed on 8 March 2024).
- Bace, R.; Mell, P.; NIST Special Publication on Intrusion Detection Systems. 1 November 2001. Available online: https://www.nist.gov/publications/intrusion-detection-systems (accessed on 7 March 2024).
- Scarfone, K.; Mell, P. Guide to Intrusion Detection and Prevention Systems (IDPS), NIST Special Publication 800-94. 2007; pp. 1–127. Available online: https://nvlpubs.nist.gov/nistpubs/legacy/sp/nistspecialpublication800-94.pdf (accessed on 7 March 2024).
- Mukherjee, B.; Heberlein, T.D.; Levitt, K.N. Network Intrusion Detection. IEEE Netw. 1994, 8, 26–41. [Google Scholar] [CrossRef]
- Debar, H.; Dacier, M.; Wespi, A. Towards a Taxonomy of Intrusion-Detection Systems. Comput. Netw. 1999, 31, 805–822. [Google Scholar] [CrossRef]
- Hubballi, N.; Suryanarayanan, V. False Alarm Minimization Techniques in Signature-Based Intrusion Detection Systems: A Survey. Comput. Commun. 2014, 49, 1–17. [Google Scholar] [CrossRef]
- Masdari, M.; Khezri, H. A Survey and Taxonomy of the Fuzzy Signature-based Intrusion Detection Systems. Appl. Soft Comput. 2020, 92, 106301. [Google Scholar] [CrossRef]
- Garcia-Teodoro, P.; Diaz-Verdejo, J.; Macia-Fernandez, G.; Vazquez, E. Anomaly-based Network Intrusion Detection: Techniques, Systems and Challenges. Comput. Secur. 2009, 28, 18–28. [Google Scholar] [CrossRef]
- Jyothsna, V.; Prasad, R.; Prasad, K.M. A Review of Anomaly Based Intrusion Detection Systems. Int. J. Comput. Appl. 2011, 28, 26–35. [Google Scholar] [CrossRef]
- Javaid, A.; Niyaz, Q.; Sun, W.; Alam, M. A Deep Learning Approach for Network Intrusion Detection System. In Proceedings of the 9th EAI International Conference on Bio-Inspired Information and Communications Technologies (Formerly BIONETICS), New York, NY, USA, 24 May 2016; Volume 3, p. 2. [Google Scholar]
- Yin, C.; Zhu, Y.; Fei, J.; He, X. A Deep Learning Approach for Intrusion Detection using Recurrent Neural Networks. IEEE Access 2017, 5, 21954–21961. [Google Scholar] [CrossRef]
- Shone, N.; Ngoc, T.N.; Phai, V.D.; Shi, Q. A Deep Learning Approach to Network Intrusion Detection. IEEE Trans. Emerg. Top. Comp. Intell. 2018, 2, 41–50. [Google Scholar] [CrossRef]
- Vinayakumar, R.; Alazab, M.; Soman, K.P.; Poornachandran, P.; Al-Nemrat, A.; Venkatraman, S. Deep Learning Approach for Intelligent Intrusion Detection System. IEEE Access 2019, 7, 41525–41550. [Google Scholar] [CrossRef]
- US NIST (National Institute of Standards and Technology). Federal Information Processing Standards (FIPS), Publication 197, Announcing the Advanced Encryption Standard (AES). 26 November 2001. Available online: https://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.197-upd1.pdf (accessed on 7 March 2024).
- Daemen, J.; Rijmen, V. The Design of Rijndael; Springer: New York, NY, USA, 2002. [Google Scholar]
- Nir, Y.; Langley, A. Chacha20 and Poly1305 for IETF Protocols; IETF (Internet Engineering Task Force) RFC 8439; 2018; pp. 1–46. Available online: https://datatracker.ietf.org/doc/rfc8439/ (accessed on 8 March 2024).
- Grover, L.K. Quantum Mechanics Helps in Searching for a Needle in a Haystack. Phys. Rev. Lett. 1997, 79, 325. [Google Scholar] [CrossRef]
- Grover, L.K. A Fast Quantum Mechanical Algorithm for Database Search. In Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, Philadelphia, PA, USA, 22–24 May 1996; pp. 212–219. [Google Scholar]
- McGrew, D. An Interface and Algorithms for Authenticated Encryption; IETF (Internet Engineering Task Force), RFC 5116; 2008. Available online: https://datatracker.ietf.org/doc/html/rfc5116/ (accessed on 8 March 2024).
- Perlner, R.A.; Cooper, D.A. Quantum Resistant Public Key Cryptography: A Survey. In Proceedings of the 8th Symposium on Identity and Trust on the Internet, Gaithersburg, MD, USA, 14–16 April 2009; pp. 85–93. [Google Scholar]
- Chen, L.; Jordan, S.; Liu, Y.K.; Moody, D.; Peralta, R.; Perlner, R.; Smith-Tone, D. Report on Post-Quantum Cryptography. US NIST Interagency/Internal Report (NISTIR)—8105. April 2016. Volume 12, 10 pages. Available online: https://nvlpubs.nist.gov/nistpubs/ir/2016/nist.ir.8105.pdf (accessed on 8 March 2024).
- ETSI (European Telecommunications Standards Institute). Quantum Safe Public Key Encryption and Key Encapsulation; ETSI TR 103 823 v1.1.2; Technical Report; October 2021. Available online: https://www.etsi.org/deliver/etsi_tr/103800_103899/103823/01.01.01_60/tr_103823v010101p.pdf (accessed on 8 March 2024).
- ETSI (European Telecommunications Standards Institute). Quantum Safe Virtual Private Networks; ETSI TR 103 617 v1.1.1; Technical Report; August 2018. Available online: https://www.etsi.org/deliver/etsi_tr/103600_103699/103617/01.01.01_60/tr_103617v010101p.pdf (accessed on 8 March 2024).
- Xiao, X.; Ni, L.M. Internet QoS: A Big Picture. IEEE Netw. 1999, 13, 8–18. [Google Scholar] [CrossRef]
- Nong, G.; Hamdi, M. On the Provision of Quality-of-Service Guarantees for Input Queued Switches. IEEE Commun. Mag. 2000, 38, 62–69. [Google Scholar]
- Meddeb, A. Internet QoS: Pieces of the Puzzle. IEEE Commun. Mag. 2010, 48, 86–94. [Google Scholar] [CrossRef]
- Parekh, A.K.; Gallager, R.G. A Generalized Processor Sharing Approach to Flow Control in Integrated Services Networks: The Single-Node Case. IEEE/ACM Trans. Netw. 1993, 1, 344–357. [Google Scholar] [CrossRef]
- Parekh, A.K.; Gallager, R.G. A Generalized Processor Sharing Approach to Flow Control in Integrated Services Networks: The Multiple Node Case. IEEE/ACM Trans. Netw. 1994, 2, 137–150. [Google Scholar] [CrossRef]
- Appenzeller, G.; Keslassy, I.; McKeown, N. Sizing Router Buffers. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 281–292. [Google Scholar] [CrossRef]
- Iyer, S.; Kompella, R.R.; Mckeown, N. Designing Packet Buffers for Router Linecards. IEEE Trans. Netw. 2008, 16, 705–717. [Google Scholar] [CrossRef]
- Anantharam, V.; McKeown, N.; Mekittikul, A.; Walrand, J. Achieving 100% Throughput in an Input Queued Switch. IEEE Trans. Commun. 1999, 47, 1260–1267. [Google Scholar]
- Mckeown, N. The iSLIP Scheduling Algorithm for Input-Queued Switches. IEEE/ACM Trans. Netw. 1999, 7, 188–201. [Google Scholar] [CrossRef]
- Odlyzko, A. Data Networks are Lightly Utilized, and Will Stay That Way. Rev. Netw. Econ. 2003, 2. [Google Scholar] [CrossRef]
- Hassidim, A.; Raz, D.; Segalov, M.; Shaqed, A. Network Utilization: The Flow View. In Proceedings of the 2013 Proceedings IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1429–1437. [Google Scholar]
- Braken, R.; Clark, D.; Shenker, S. Integrated Services in the Internet Architecture—An Overview; IETF (Internet Engineering Task Force) RFC 1633; 1994. Available online: https://datatracker.ietf.org/doc/html/rfc1633 (accessed on 8 March 2024).
- Black, D.; Jones, P. Differentiated Services (DiffServ) and Real-Time Communications; IETF (Internet Engineering Task Force) RFC 7657; 2015. Available online: https://datatracker.ietf.org/doc/html/rfc7657 (accessed on 8 March 2024).
- IEEE 802.org. Deterministic Ethernet: 802.1 Standards for Real-Time Process Control, Industrial Automation, and Vehicular Networks. 2012. Available online: https://www.ieee802.org/802_tutorials/2012-11/8021-tutorial-final-v4.pdf (accessed on 8 March 2024).
- Hermeto, R.T.; Gallais, A.; Theoleyre, F. Scheduling for IEEE-802.15.4-TSCH and Slow Channel Hopping MAC in Low Power Industrial Wireless Networks: A Survey. Comput. Commun. 2017, 114, 84–105. [Google Scholar] [CrossRef]
- Dujovne, D.; Watteyne, T.; Vilajosana, X.; Thubert, P. 6TiSCH: Deterministic IP-enabled Industrial Internet (of Things). IEEE Commun. Mag. 2014, 52, 36–41. [Google Scholar] [CrossRef]
- Finn, N.; Thubert, P. Deterministic Networking Problem Statement (09); IETF Internet-Draft, Standards Track; December 2018; pp. 1–20. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-detnet-problem-statement (accessed on 8 March 2024).
- Grossman, E. Deterministic Networking Use Cases; IETF (Internet Engineering Task Force)draft; May 2019. Available online: https://www.rfc-editor.org/rfc/pdfrfc/rfc8578.txt.pdf (accessed on 8 March 2024).
- Finn, N.; Thubert, P.; Varga, B.; Farkas, J. Deterministic Networking Architecture; IETF (Internet Engineering Task Force) Internet RFC 8655; 2019. Available online: https://datatracker.ietf.org/doc/rfc8655/ (accessed on 8 March 2024).
- Liu, B.; Ren, S.; Wang, C.; Angilella, V.; Medagliani, P.; Martin, S.; Leguay, J. Towards Large-Scale Deterministic IP Networks. In Proceedings of the 2021 IFIP Networking Conference (IFIP Networking), Espoo and Helsinki, Finland, 21–24 June 2021; pp. 1–9. [Google Scholar]
- Singla, A.; Chandrasekaran, B.; Godfrey, P.B.; Maggs, B. The Internet at the Speed of Light. In Proceedings of the 13th ACM Workshop on Hot Topics in Networks, Los Angeles, CA, USA, 27–28 October 2014; pp. 1–7. [Google Scholar]
- Fettweis, G.; Boche, H.; Wiegand, T.; Zielinski, E.; Schotten, H.; Merz, P.; Hirche, S.; Festag, A.; Häffner, W.; Meyer, M.; et al. The Tactile Internet, ITU-T Technology Watch Report; ITU: Geneva, Switzerland, 2014; pp. 1–24. Available online: https://www.itu.int/dms_pub/itu-t/opb/gen/T-GEN-TWATCH-2014-1-PDF-E.pdf (accessed on 8 March 2024).
- Nasrallah, A.; Thyagaturu, A.S.; Alharbi, Z.; Wang, C.; Shao, X.; Reisslein, M.; ElBakoury, H. Ultra-Low Latency (ULL) Networks: The IEEE TSN and IETF DetNet Standards and Related 5G ULL Research. IEEE Commun. Surv. Tutor. 2018, 21, 88–145. [Google Scholar] [CrossRef]
- Chen, W.J.; Chang, C.S.; Huang, H.Y. Birkoff-von Neumann Input Buffered Crossbar Switches for Guaranteed-Rate Services. IEEE Trans. Commun. 2001, 49, 1145–1147. [Google Scholar]
- Chang, C.S.; Lee, D.S.; Yue, C.Y. Providing Guaranteed Rate Services in the Load Balanced Birkhoff-von Neumann Switches. IEEE/ACM Trans. Netw. 2008, 14, 644–656. [Google Scholar] [CrossRef]
- Koksal, C.E.; Gallager, R.G.; Rohrs, C.E. Rate Quantization and Service Quality over Single Crossbar Switches. In Proceedings of the IEEE INFOCOM 2004, Hong Kong, China, 7–11 March 2004; Volume 3, pp. 1962–1973. [Google Scholar]
- Keslassy, I.; Kodialam, M.; Lakshman, T.V.; Stilliadis, D. On Guaranteed Smooth Scheduling for Input-Queued Switches. IEEE/ACM Trans. Netw. 2005, 13, 1364–1375. [Google Scholar] [CrossRef]
- Mohanty, S.R.; Bhuyan, L.N. Guaranteed Smooth Switch Scheduling with Low Complexity. In Proceedings of the GLOBECOM’05, IEEE Global Telecommunications Conference, St. Louis, MO, USA, 28 November–2 December 2005; Volume 1, p. 5. [Google Scholar]
- Szymanski, T.H. A Low Jitter Guaranteed Rate Scheduling Algorithm for Packet Switched IP Routers. IEEE Trans. Commun. 2009, 57, 3446–3459. [Google Scholar] [CrossRef]
- Szymanski, T.H.; Gilbert, D. Internet multicasting of IPTV with essentially-zero delay jitter. IEEE Trans. Broadcast. 2009, 55, 20–30. [Google Scholar] [CrossRef]
- Szymanski, T.H.; Gilbert, D. Provisioning Mission-Critical Telerobotic Control Systems over Internet backbone Networks with Essentially-Perfect QoS. IEEE J. Sel. Areas Commun. 2010, 28, 630–643. [Google Scholar] [CrossRef]
- Szymanski, T.H. Max-Flow Min-Cost Routing in a Future Internet with Improved QoS Guarantees. IEEE Trans. Commun. 2013, 61, 1485–1497. [Google Scholar] [CrossRef]
- Szymanski, T.H. Method to Achieve Bounded Buffer Sizes and Quality of Service Guarantees in the Internet Network. US Patent 8,665,722 B2, 4 March 2014. [Google Scholar]
- Szymanski, T.H. Method to Achieve Bounded Buffer Sizes and Quality of Service Guarantees in the Internet Network. US Patent 9,584,431 B2, 28 February 2017. [Google Scholar]
- Szymanski, T.H. Reduced-Complexity Integrated Guaranteed-Rate Optical Packet Switch. US Patent 10,687,128 B2, 16 June 2020. [Google Scholar]
- Szymanski, T.H. Methods to Strengthen Cyber-Security and Privacy in a Deterministic Internet of Things. US Patent 11,019,038 B2, 25 May 2021. [Google Scholar]
- Kaufman, C.; Hoffman, P.; Nir, Y.; Eronen, P.; Kivinen, T. Internet Key Exchange Protocol Version 2 (IKEV2); IETF (Internet Engineering Task Force) RFC 7296; 2014; pp. 1–138. Available online: https://datatracker.ietf.org/doc/html/rfc7296 (accessed on 8 March 2024).
- Fluhrer, S.; Kampanakis, P.; McGrew, D.; Smyslov, V. Mixing Preshared Keys in IKEV2 for Post Quantum Security; IETF (Internet Engineering Task Force) RFC 8774; 2020; pp. 1–20. Available online: https://datatracker.ietf.org/doc/html/rfc8784 (accessed on 8 March 2024).
- Bos, J.W.; Costello, C.; Naehrig, M.; Stebila, D. Post-Quantum Key Exchange for the TLS Protocol from the Ring Learning with Errors Problem. In Proceedings of the 2015 IEEE Symposium on Security and Privacy, San Jose, CA, USA, 17–21 May 2015; pp. 553–570. [Google Scholar]
- Karakus, M.; Durresi, A. A Survey: Control Plane Scalability Issues and Approaches in Software-Defined Networking (SDN). Comput. Netw. 2017, 12, 279–293. [Google Scholar] [CrossRef]
- Bannour, F.; Souihi, S.; Mellouk, A. Distributed SDN Control: Survey, Taxonomy, and Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 333–354. [Google Scholar] [CrossRef]
- Diamanti, E.; Lo, H.K.; Qi, B.; Yuan, Z. Practical Challenges in Quantum Key Distribution. NPJ Quantum Inf. 2016, 2, 1–12. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The Evolution of Quantum Key Distribution Networks: On the Road to the Qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Tsai, C.W.; Yang, C.W.; Lin, J.; Chang, Y.C.; Chang, R.S. Quantum Key Distribution Networks: Challenges and Future Research Issues in Security. Appl. Sci. 2021, 11, 3767. [Google Scholar] [CrossRef]
- Lella, E.; Schmid, G. On the Security of Quantum Key Distribution Networks. Cryptography 2023, 7, 53. [Google Scholar] [CrossRef]
- Mehic, M.; Niemiec, M.; Rass, S.; Ma, J.; Peev, M.; Aguado, A.; Martin, V.; Schauer, S.; Poppe, A.; Pacher, C.; et al. Quantum Key Distribution: A Networking Perspective. ACM Comput. Surv. 2020, 53, 1–41. [Google Scholar] [CrossRef]
- James, P.; Laschet, S.; Ramacher, S.; Torresetti, L. Key Management Systems for Large-Scale Quantum Key Distribution Networks. In Proceedings of the 18th International Conference on Availability, Reliability and Security, Benevento, Italy, 29 August–1 September 2023; pp. 1–9. [Google Scholar]
- ETSI GS QKD 004 2020; Quantum Key Distribution (QKD); Application Interface, Group Specification v2.1.1. European Telecommunications Standards Institute (ETSI), Industry Specification Groups (ISG): Sophia-Antipolis, France, 2020. Available online: https://www.etsi.org/deliver/etsi_gs/QKD/001_099/004/02.01.01_60/gs_QKD004v020101p.pdf (accessed on 8 March 2024).
- Green, A.; Lawrence, J.; Siopsis, G.; Peters, N.A.; Passian, A. Quantum Key Distribution for Critical Infrastructures: Towards Cyber-Physical Security for Hydropower and Dams. Sensors 2023, 23, 9818. [Google Scholar] [CrossRef]
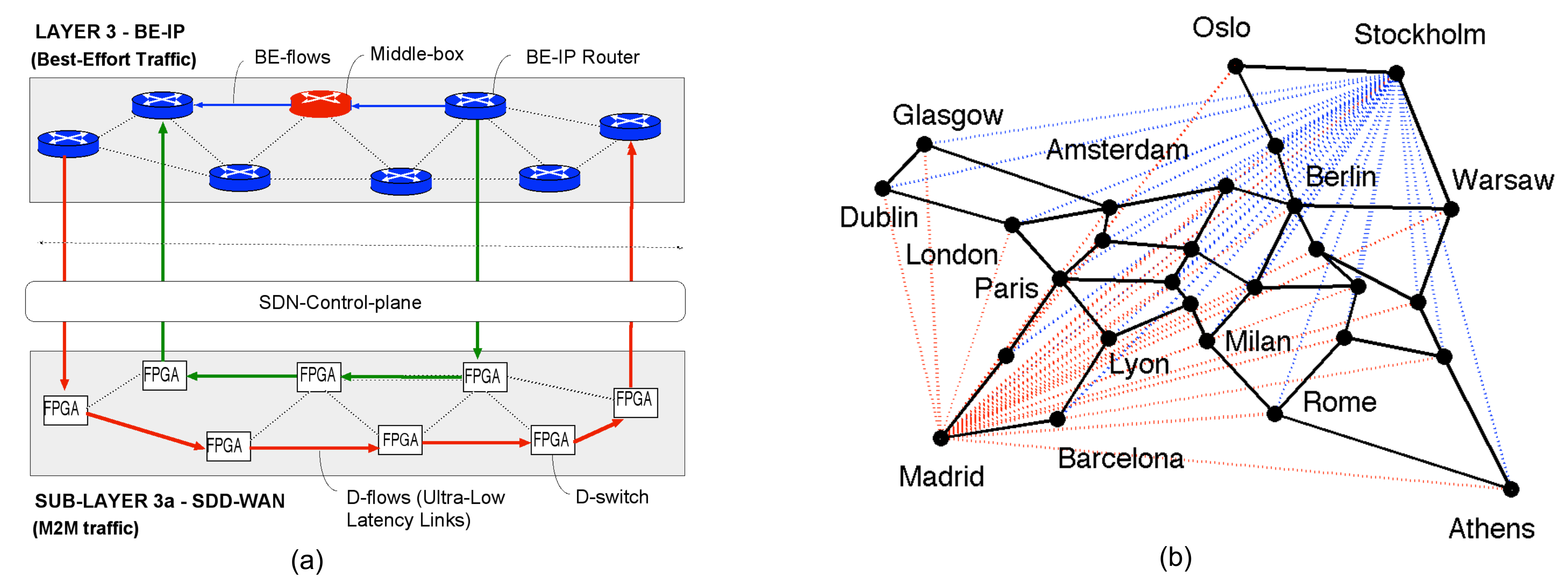
| Sector | Features |
|---|---|
| Chemical | Hundreds of thousands of chemical facilities, developing 70,000 diverse products. Un-interrupted transportation of chemical products. |
| Communications | Comprising satellite, wireless, and wireline systems. CRITICAL (enables all other sectors). |
| Critical Manufacturing | Protect nation’s manufacturing base against natural disasters and cyber-attacks. Comprises metals, machinery, electrical, and transportation equipment. |
| Dams | Control 90,000+ dams. Protect hydro-electric generating capacity. Protect 43% of population from flooding. |
| Defense Industry | Over 100,000 companies provide products/services to the US military. Essential to mobilize, deploy, and sustain military operations. |
| Energy | Electricity, oil, and natural gas resources, to ensure energy for the nation. CRITICAL (enables all other sectors). Over 6400 power plants generating over 1 Terawatt of power. Numerous pipelines to distribute fuels. |
| Nuclear reactor | Ninety-two active reactors generate 20% of US energy. Eight fuel facilities, producing Uranium-235 for reactors. Over 3 million shipments/year of radioactive materials. |
| Water and waste water | Over 150,000 public water systems, supplying 80% of population with safe water. |
| QKD networks | Quantum key distribution networks may distribute “perfectly secret” keys. |
| Quantum Internet | The future Quantum Internet may support nearly unconditional security and privacy, and will achieve super-computing power. |
| Vulnerability | Summary |
|---|---|
| Best-effort (BE) service model | Provides “best-effort” service (no deterministic QoS guarantees). Inconsistent transmission rates, causing interference and congestion. |
| Access-control or rate-control | Estimated 33 billion devices in the Consumer IoT in 2024. No “Admission- Control/Access-Control” to control transmissions. Any device can transmit to any other device, at any data-rate, at any-time, causing congestion. |
| Congestion and BufferBloat | Congestion causes “BufferBloat”; Buffer-sizes given by “Bandwidth-Delay- Product” rule. A 4 Tbps IP router with a 1/4 s delay requires 1 Terabit buffer. Impossible to fit a BE-IP router with 4 Tbps capacity onto a single FPGA. |
| Un-encrypted and Unauthenticated IP packet headers | IP uses unencrypted and unauthenticated packet headers. IP cannot “authenticate” the sender (verify that it is who it claims to be). IoT users can modify IP packet headers to masquerade as trusted peers. Cyber-attackers can modify IP packet headers to masquerade as trusted peers. |
| Layer-3 routing | Layer-3 routing is performed in every BE-IP router. A router processes unencrypted and unauthenticated IP packet headers. Routing is insecure. Cyber-attackers can easily re-route traffic to a destination they control. |
| Middle boxes | Middle boxes perform essential functions, i.e., address translation, Intrusion Detection Systems, and firewalls. Middle boxes are also insecure. |
| Domain Name Servers (DNSs) | Domain Name Servers perform essential functions, i.e., address-resolution. DNSs are also insecure. |
| DoS and DDoS attacks | A cyber-attacker in a compromised middle boxes can generate millions of malicious IP packets causing DoS attacks. A cyber-attacker controlling many compromised IoT devices can generate millions of IP packets, causing DDoS attacks. DDoS attacks are among “the most significant weapons on the Internet”. ≈17.5 million DDoS attacks occurred in the Consumer IoT in 2024 (Cisco). The average DDoS attack lasted for 8 h in 2022 (Cloudflare). |
| “Isolation control” | Cannot isolate sub-networks within the BE-IP, to contain cyber-attacks. |
| Over-provisioning | The IoT is “over-provisioned” and operates at ≤40% of peak capacity; ≥60% of IoT capacity is unused (for very-high capital and energy costs). |
| Source | Quotes Supporting TLS Security |
|---|---|
| Internet Society | “TLS is a cryptographic protocol that provides end-to-end security of data sent between applications over the Internet”. Please see definition of “security” below. |
| NIST | “TLS and SSL are widely used in the Internet to provide a safe communications channel for sending sensitive information”. |
| IETF [42] | “TLS allows client/server applications to communicate over the Internet in a way that is designed to prevent eavesdropping, tampering, and message forgery”. |
| IEEE [52] | “TLS is possibly the most used protocol for secure communications, with a 18-year history of flaws and fixes”. |
| ACM [53] | TLS “is the defacto standard for secure communication on the internet”. |
| Source | Quotes questioning TLS security. |
| NIST [54] | “There are no known ways to prevent flooding DoS attacks against hosts visible on the Internet”. |
| IEEE [48] | “DDoS attacks are some of the most devastating attacks against Web applications”. Application- layer DoS attacks are “a major threat because of the difficulty in adopting the defenses”. |
| Norton | “A DDoS attack is one of the most powerful weapons in the Internet”. It is an attack against a web-server or network that floods it with more Internet traffic than it can handle. Sophisticated cyber-criminals sell and lease software (i.e., Botnets) to create DDoS attacks on the Dark Web. |
| Dictionary | Definition of a word. |
| Oxford | Security: “The activities involved in protecting a country, building or person against attack, danger, etc”. |
| Oxford | Privacy: “The state or condition of being free from being observed or disturbed by other people”. |
| Oxford | Confidentiality: “The state of keeping or being kept secret or private”. |
| Service | Date | Description | External/Internal |
|---|---|---|---|
| Yahoo | August 2013 | 3 billion accounts | External |
| MySpace | 2013 | 360 million accounts | External |
| Yahoo | 2014 | 500 million accounts | External |
| Adult Friend Finder | October 2016 | 412 million accounts | External |
| Aadhaar | January 2018 | 1.1 billion accounts | External |
| Marriott International | September 2018 | 500 million accounts | External |
| April 2019 | 533 million accounts | Internal | |
| Alibaba | November 2019 | 1.1 billion pieces of user data | Internal |
| Sina Weibo | March 2020 | 538 million accounts | External |
| June 2021 | 700 million accounts | External |
| Drawback | Summary |
|---|---|
| QKD is a partial solution | QKD cannot authenticate the source. Authentication typically requires the use of “pre-shared secret keys” and SKC. |
| Special-purpose equipment | QKD relies upon unique physical layer communications, i.e., dedicated point-to-point fiber connections, or satellite communications. |
| Insider (internal) cyber-attacks | QKD requires trusted relays, which increases costs and security risks from insider cyber-attacks. This prospect eliminates many use cases of QKD. |
| Validating QKD is a challenge | Security of QKD is limited by constraints of hardware and engineering designs. Tolerance for design errors is orders of magnitude smaller than for traditional systems. Several commercial QKD systems have been attacked. |
| Denial of service (DoS) attacks | QKD is sensitive to eavesdroppers (i.e., “photon number splitting attack”), and “Denial of Service” (DoS) attacks are a significant risk for QKD systems. |
| Vulnerability | Consumer IoT w/o PQC | Consumer IoT with PQC | IETF Converged WAN | SDD WAN | QKD Networks | Hybrid QKD and SDD-WAN |
|---|---|---|---|---|---|---|
| Unencrypted IP pkt. headers | Vuln. | Vuln. | Vuln. | Safe | Safe | Safe |
| Unauthenticated sources | Vuln. | Vuln. | Vuln. | Safe | Vuln. * | Safe |
| Middle boxes | Vuln. | Vuln. | Vuln. | Safe | Safe | Safe |
| DNS servers | Vuln. | Vuln. | Vuln. | Safe | Safe | Safe |
| Layer-3 routing | Vuln. | Vuln. | Vuln. | Safe | Safe | Safe |
| DoS attacks | Vuln. | Vuln. | Vuln. | Safe | Vuln. * | Safe |
| DDoS attacks | Vuln. | Vuln. | Vuln. | Safe | Vuln. * | Safe |
| Insider attacks | Vuln. | Vuln. | Vuln. | Safe | Vuln. * | Safe |
| TLS cryptographic attacks | Vuln. | Safe | Safe | Safe | Safe | Safe |
| Harvest Now–Decrypt Later | Vuln. | Safe | Safe | Safe | Safe | Safe |
| Company | 2022 Annual Revenue |
|---|---|
| Arista | USD 4.381 billion |
| Cisco | USD 51.6 billion |
| Huawei | USD 92.380 billion |
| Juniper | USD 5.301 billion |
| Nokia | USD 26.251 billion |
| Total | USD 179.91 billion |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Szymanski, T.H. A Quantum-Safe Software-Defined Deterministic Internet of Things (IoT) with Hardware-Enforced Cyber-Security for Critical Infrastructures. Information 2024, 15, 173. https://doi.org/10.3390/info15040173
Szymanski TH. A Quantum-Safe Software-Defined Deterministic Internet of Things (IoT) with Hardware-Enforced Cyber-Security for Critical Infrastructures. Information. 2024; 15(4):173. https://doi.org/10.3390/info15040173
Chicago/Turabian StyleSzymanski, Ted H. 2024. "A Quantum-Safe Software-Defined Deterministic Internet of Things (IoT) with Hardware-Enforced Cyber-Security for Critical Infrastructures" Information 15, no. 4: 173. https://doi.org/10.3390/info15040173
APA StyleSzymanski, T. H. (2024). A Quantum-Safe Software-Defined Deterministic Internet of Things (IoT) with Hardware-Enforced Cyber-Security for Critical Infrastructures. Information, 15(4), 173. https://doi.org/10.3390/info15040173





