Digital Transformation in Energy Sector: Cybersecurity Challenges and Implications
Abstract
1. Introduction
2. Materials and Methods
- The paper is published in the time period of 2019–2024;
- The paper is focusing on both digital transformation and cybersecurity implications in energy sector;
- The paper is available in the English language;
- The paper is a not a review paper, book, or thesis.
3. Results
3.1. Cybersecurity Implications in Oil and Gas Industry
3.2. Cybersecurity Implications in Electricity
3.3. Cybersecurity Implications in Nuclear Energy
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- IEA. 2024. Available online: https://www.iea.org/reports/electricity-2024/executive-summary (accessed on 25 September 2024).
- Xu, Q.; Zhong, M.; Li, X. How does digitalization affect energy? International evidence. Energy Econ. 2022, 107, 105879. [Google Scholar] [CrossRef]
- Maroufkhani, P.; Desouza, K.C.; Perrons, R.K.; Iranmanesh, M. Digital transformation in the resource and energy sectors: A systematic review. Resour. Policy 2022, 76, 102622. [Google Scholar] [CrossRef]
- Akberdina, V.; Osmonova, A. Digital transformation of energy sector companies. E3S Web Conf. 2021, 250, 06001. [Google Scholar] [CrossRef]
- Nazari, Z.; Musilek, P. Impact of digital transformation on the energy sector: A review. Algorithms 2023, 16, 211. [Google Scholar] [CrossRef]
- Oudina, Z.; Derdour, M.; Dib, A.; Yaakoubi, M.A. Identifying and Addressing Trust Concerns in Cyber-Physical Systems for the Oil and Gas Industry. Ing. Syst. D’inform. 2024, 29, 469–478. [Google Scholar] [CrossRef]
- Gutman, S.; Brazovskaia, V. Tool Development for Assessing the Strategic Development of Territorial Socio-Economic Systems for the Purposes of Energy Sector Digital Transformation. Energies 2023, 16, 5269. [Google Scholar] [CrossRef]
- Saeed, S.; Altamimi, S.A.; Alkayyal, N.A.; Alshehri, E.; Alabbad, D.A. Digital transformation and cybersecurity challenges for businesses resilience: Issues and recommendations. Sensors 2023, 23, 6666. [Google Scholar] [CrossRef]
- Saeed, S. Usable Privacy and Security in Mobile Applications: Perception of Mobile End Users in Saudi Arabia. Big Data Cogn. Comput. 2024, 8, 162. [Google Scholar] [CrossRef]
- Gull, H.; Saeed, S.; Alaied, H.A.; Alajmi, A.N.; Saqib, M.; Iqbal, S.Z.; Almuhaideb, A.M. Digital Transformation of Marketing Processes, Customer Privacy, Data Security, and Emerging Challenges in Fostering Sustainable Digital Marketing. In Ethical AI and Data Management Strategies in Marketing; Saluja, S., Nayyar, V., Rojhe, K., Sharma, S., Eds.; IGI Global Scientific Publishing: Hershey, PA, USA, 2024; pp. 71–88. [Google Scholar] [CrossRef]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Hobbs, A. The Colonial Pipeline Hack: Exposing Vulnerabilities in US Cybersecurity; SAGE Publications: SAGE Business Cases Originals: London, UK, 2021. [Google Scholar]
- Cunningham, C. A Russian Federation Information Warfare Primer; The Henry M. Jackson School of International Studies, Washington University: Seattle, WA, USA, 2020. [Google Scholar]
- Alqurashi, R.K.; AlZain, M.A.; Soh, B.; Masud, M.; Al-Amri, J. Cyber attacks and impacts: A case study in Saudi Arabia. Int. J. Adv. Trends Comput. Sci. Eng. 2020, 9, 217–224. [Google Scholar] [CrossRef]
- Bhattacharjee, S.; Das, S.K. Detection and forensics against stealthy data falsification in smart metering infrastructure. IEEE Trans. Dependable Secur. Comput. 2018, 18, 356–371. [Google Scholar] [CrossRef]
- Oudina, Z.; Dib, A.; Yakoubi, M.A.; Derdour, M. Comprehensive Risk Classification and Mitigation in the Petroleum Cyber-Physical Systems of the Oil and Gas Industry. Int. J. Saf. Secur. Eng. 2024, 14, 99–113. [Google Scholar] [CrossRef]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, n71. [Google Scholar] [CrossRef] [PubMed]
- Google Scholar. Available online: https://scholar.google.com/schhp?hl=en (accessed on 26 September 2024).
- Aubuchon, T.; Susanto, I.; Peterson, B.T. Oil and Gas Industry Partnership with Government to Improve Cybersecurity. In Proceedings of the SPE International Oil and Gas Conference and Exhibition in China, Beijing, China, 5–7 December 2006; p. SPE-104284. [Google Scholar]
- Goel, A. Cybersecurity in O&G Industry. In Proceedings of the Offshore Technology Conference, Houston, TX, USA, 1–4 May 2017; pp. 6–9. [Google Scholar]
- Mohammed, A.S.; Reinecke, P.; Burnap, P.; Rana, O.; Anthi, E. Cybersecurity challenges in the offshore oil and gas industry: An industrial cyber-physical systems (ICPS) perspective. ACM Trans. Cyber-Phys. Syst. (TCPS) 2022, 6, 28. [Google Scholar] [CrossRef]
- Frederick, B.A.; Taylor, O.E. Analysis on Cybersecurity Control and Monitoring Techniques in Industrial IoT: Industrial Control Systems. Internet Things and Cloud Comput. 2023, 11, 1–17. [Google Scholar]
- Villarreal, R.; Alarcón, F.; Torrejón, L. Implementing NIST CSF and CIS CSC in Gas Industry: A Model’s Effectiveness and Acceptance Analysis. In Proceedings of the 2023 International Conference on Electrical, Computer and Energy Technologies (ICECET), Cape Town, South Africa, 16–17 November 2023; pp. 1–6. [Google Scholar]
- Houmb, S.H.; Iversen, F.; Ewald, R.; Færaas, E. Intelligent risk based cybersecurity protection for industrial systems control—A feasibility study. In Proceedings of the International Petroleum Technology Conference, Bangkok, Thailand, 1–3 March 2023; p. D021S014R001. [Google Scholar]
- Tariq, A.; Elhadef, M.; Ghani Khan, M.U. Optimizing Cybersecurity in the Oil and Gas Industry with Machine Learning-Based Ids. Available online: https://ssrn.com/abstract=4630706 (accessed on 26 September 2024).
- Pettersen, S.; Grøtan, T.O. Exploring the grounds for cyber resilience in the hyper-connected oil and gas industry. Saf. Sci. 2024, 171, 106384. [Google Scholar] [CrossRef]
- Obonna, U.O.; Opara, F.K.; Mbaocha, C.C.; Obichere, J.K.C.; Akwukwaegbu, I.O.; Amaefule, M.M.; Nwakanma, C.I. Detection of Man-in-the-Middle (MitM) Cyber-Attacks in Oil and Gas Process Control Networks Using Machine Learning Algorithms. Future Internet 2023, 15, 280. [Google Scholar] [CrossRef]
- Shohoud, M. Study the Effectiveness of ISO 27001 to Mitigate the Cyber Security Threats in the Egyptian Downstream Oil and Gas Industry. J. Inf. Secur. 2023, 14, 152–180. [Google Scholar] [CrossRef]
- ISO 27001 Standard. Available online: https://www.iso.org/standard/27001 (accessed on 26 September 2024).
- Progoulakis, I.; Nikitakos, N.; Rohmeyer, P.; Bunin, B.; Dalaklis, D.; Karamperidis, S. Perspectives on cyber security for offshore oil and gas assets. J. Mar. Sci. Eng. 2021, 9, 112. [Google Scholar] [CrossRef]
- Avanzini, G.B.; Spessa, A. Cybersecurity verification approach for the oil & gas industry. In Proceedings of the Offshore Mediterranean Conference and Exhibition, Ravenna, Italy, 27–29 March 2019. Paper number OMC-2019. [Google Scholar]
- Mohammed, A.S.; Anthi, E.; Rana, O.; Saxena, N.; Burnap, P. Detection and mitigation of field flooding attacks on oil and gas critical infrastructure communication. Comput. Secur. 2023, 124, 103007. [Google Scholar] [CrossRef]
- Gueye, T.; Iqbal, A.; Wang, Y.; Mushtaq, R.T.; Petra, M.I. Bridging the Cybersecurity Gap: A Comprehensive Analysis of Threats to Power Systems, Water Storage, and Gas Network Industrial Control and Automation Systems. Electronics 2024, 13, 837. [Google Scholar] [CrossRef]
- Patel, S. Cybersecurity in Electric Distribution: The One Weak Link in an Interconnected Power Grid and the Threat It Poses. Georg. Wash. J. Energy Environ. Law 2023, 14, 138. [Google Scholar]
- Naiho HN, N.; Layode, O.; Adeleke, G.S.; Udeh, E.O.; Labake, T.T. Addressing cybersecurity challenges in smart grid technologies: Implications for sustainable energy infrastructure. Eng. Sci. Technol. J. 2024, 5, 1995–2015. [Google Scholar] [CrossRef]
- Jiang, Y.; Jeusfeld, M.A.; Ding, J.; Sandahl, E. Model-Based Cybersecurity Analysis: Extending Enterprise Modeling to Critical Infrastructure Cybersecurity. Bus. Inf. Syst. Eng. 2023, 65, 643–676. [Google Scholar] [CrossRef]
- Kazancı, B.A. The Strategic Importance of Cyber Security in Electric Energy Policies. Int. J. Energy Econ. Policy 2024, 14, 599–605. [Google Scholar] [CrossRef]
- Ratnam, E.L.; Baldwin, K.G.; Mancarella, P.; Howden, M.; Seebeck, L. Electricity system resilience in a world of increased climate change and cybersecurity risk. Electr. J. 2020, 33, 106833. [Google Scholar] [CrossRef]
- Sun, C.C.; Cardenas DJ, S.; Hahn, A.; Liu, C.C. Intrusion detection for cybersecurity of smart meters. IEEE Trans. Smart Grid 2020, 12, 612–622. [Google Scholar] [CrossRef]
- Shaaban, M.; Tariq, U.; Ismail, M.; Almadani, N.A.; Mokhtar, M. Data-driven detection of electricity theft cyberattacks in PV generation. IEEE Syst. J. 2021, 16, 3349–3359. [Google Scholar] [CrossRef]
- Ibrahem, M.I.; Mahmoud, M.M.; Alsolami, F.; Alasmary, W.; Al-Ghamdi AS, A.M.; Shen, X. Electricity-theft detection for change-and-transmit advanced metering infrastructure. IEEE Internet Things J. 2022, 9, 25565–25580. [Google Scholar] [CrossRef]
- Tolba, A.; Al-Makhadmeh, Z. A cybersecurity user authentication approach for securing smart grid communications. Sustain. Energy Technol. Assess. 2021, 46, 101284. [Google Scholar] [CrossRef]
- Johnson, J.; Anderson, B.; Wright, B.; Quiroz, J.; Berg, T.; Graves, R.; Daley, J.; Phan, K.; Kunz, M.; Pratt, R.; et al. Cybersecurity for Electric Vehicle Charging Infrastructure; No. SAND2022-9315; Sandia National Lab. (SNL-NM): Albuquerque, NM, USA, 2022. [Google Scholar]
- Bai, Y.; Sun, H.; Zhang, L.; Wu, H. Hybrid CNN–Transformer Network for Electricity Theft Detection in Smart Grids. Sensors 2023, 23, 8405. [Google Scholar] [CrossRef]
- Musleh, A.S.; Ahmed, J.; Ahmed, N.; Xu, H.; Chen, G.; Kerr, S.; Jha, S. Experimental Cybersecurity Evaluation of Distributed Solar Inverters: Vulnerabilities and Impacts on the Australian Grid. IEEE Trans. Smart Grid 2024, 15, 5139–5150. [Google Scholar] [CrossRef]
- Erkek, İ.; Irmak, E. Enhancing Cybersecurity of a Hydroelectric Power Plant Using Its Digital Twin Model. In Proceedings of the 2024 12th International Conference on Smart Grid (icSmartGrid), Setubal, Portugal, 27–29 May 2024; pp. 372–377. [Google Scholar]
- Ismail, M.; Shaaban, M.F.; Naidu, M.; Serpedin, E. Deep learning detection of electricity theft cyber-attacks in renewable distributed generation. IEEE Trans. Smart Grid 2020, 11, 3428–3437. [Google Scholar] [CrossRef]
- Takiddin, A.; Ismail, M.; Zafar, U.; Serpedin, E. Variational auto-encoder-based detection of electricity stealth cyber-attacks in AMI networks. In Proceedings of the 2020 28th European Signal Processing Conference (EUSIPCO), Amsterdam, The Netherlands, 18–21 January 2021; pp. 1590–1594. [Google Scholar]
- Takiddin, A.; Ismail, M.; Nabil, M.; Mahmoud, M.M.; Serpedin, E. Detecting electricity theft cyber-attacks in AMI networks using deep vector embeddings. IEEE Syst. J. 2020, 15, 4189–4198. [Google Scholar] [CrossRef]
- Tang, D.; Fang, Y.P.; Zio, E. Vulnerability analysis of demand-response with renewable energy integration in smart grids to cyber-attacks and online detection methods. Reliab. Eng. Syst. Saf. 2023, 235, 109212. [Google Scholar] [CrossRef]
- Heymann, F.; Henry, S.; Galus, M. Cybersecurity and resilience in the swiss electricity sector: Status and policy options. Util. Policy 2022, 79, 101432. [Google Scholar] [CrossRef]
- Ge, P.; Chen, B.; Teng, F. Cyber-Resilient Self-Triggered Distributed Control of Networked Microgrids Against Multi-Layer DoS Attacks. IEEE Trans. Smart Grid 2023, 14, 3114–3124. [Google Scholar] [CrossRef]
- Liu, M.; Teng, F.; Zhang, Z.; Ge, P.; Sun, M.; Deng, R.; Cheng, P.; Chen, J. Enhancing Cyber-Resiliency of DER-Based Smart Grid: A Survey. IEEE Trans. Smart Grid 2024, 15, 4998–5030. [Google Scholar] [CrossRef]
- Nafees, M.N.; Saxena, N.; Cardenas, A.; Grijalva, S.; Burnap, P. Smart Grid Cyber-Physical Situational Awareness of Complex Operational Technology Attacks: A Review. ACM Comput. Surv. 2023, 55, 215. [Google Scholar] [CrossRef]
- Zhang, Z.; Liu, M.; Sun, M.; Deng, R.; Cheng, P.; Niyato, D.; Chow, M.Y.; Chen, J. Vulnerability of Machine Learning Approaches Applied in IoT-Based Smart Grid: A Review. IEEE Internet Things J. 2024, 11, 18951–18975. [Google Scholar] [CrossRef]
- Inayat, U.; Zia, M.F.; Mahmood, S.; Berghout, T.; Benbouzid, M. Cybersecurity Enhancement of Smart Grid: Attacks, Methods, and Prospects. Electronics 2022, 11, 3854. [Google Scholar] [CrossRef]
- Ayodeji, A.; Mohamed, M.; Li, L.; Di Buono, A.; Pierce, I.; Ahmed, H. Cyber security in the nuclear industry: A closer look at digital control systems, networks and human factors. Prog. Nucl. Energy 2023, 161, 104738. [Google Scholar] [CrossRef]
- Greiman, V. Nuclear Cyber Attacks: A Study of Sabotage and Regulation of Critical Infrastructure. In Proceedings of the International Conference on Cyber Warfare and Security, Towson, MD, USA, 9–10 March 2023; Volume 18, pp. 103–110. [Google Scholar]
- Falowo, O.I.; Kropczynski, J.; Li, C. Protecting Critical Infrastructure: Strategies for Managing Cybersecurity Risks in Nuclear Fusion Facilities. In Proceedings of the 2023 IEEE Intl Conf on Parallel & Distributed Processing with Applications, Big Data & Cloud Computing, Sustainable Computing & Communications, Social Computing & Networking (ISPA/BDCloud/SocialCom/SustainCom), Wuhan, China, 21–24 December 2023; pp. 1050–1061. [Google Scholar]
- Jung, D.; Shin, J.; Lee, C.; Kwon, K.; Seo, J.T. Cyber security controls in nuclear power plant by technical assessment methodology. IEEE Access 2023, 11, 15229–15241. [Google Scholar] [CrossRef]
- Yockey, P.; Erickson, A.; Spirito, C. Cyber threat assessment of machine learning driven autonomous control systems of nuclear power plants. Prog. Nucl. Energy 2023, 166, 104960. [Google Scholar] [CrossRef]
- Morstyn, T.; Hredzak, B.; Agelidis, V.G. Control strategies for microgrids with distributed energy storage systems: An overview. IEEE Trans. Smart Grid 2016, 9, 3652–3666. [Google Scholar] [CrossRef]
- Blaabjerg, F.; Teodorescu, R.; Liserre, M.; Timbus, A.V. Overview of control and grid synchronization for distributed power generation systems. IEEE Trans. Ind. Electron. 2006, 53, 1398–1409. [Google Scholar] [CrossRef]
- Khan, S.; Madnick, S.; Moulton, A. Cybersafety Analysis of Industrial Control System for Gas Turbines; Cybersecurity Interdisciplinary Systems Laboratory (CISL): Cambridge, MA, USA, 2018. [Google Scholar]
- Coakley, D.; Raftery, P.; Keane, M. A review of methods to match building energy simulation models to measured data. Renew. Sustain. Energy Rev. 2014, 37, 123–141. [Google Scholar] [CrossRef]
- Bhattarai, B.P.; Paudyal, S.; Luo, Y.; Mohanpurkar, M.; Cheung, K.; Tonkoski, R.; Zhang, X. Big data analytics in smart grids: State-of-the-art, challenges, opportunities, and future directions. IET Smart Grid 2019, 2, 141–154. [Google Scholar] [CrossRef]
- vom Scheidt, F.; Medinová, H.; Ludwig, N.; Richter, B.; Staudt, P.; Weinhardt, C. Data analytics in the electricity sector–A quantitative and qualitative literature review. Energy AI 2020, 1, 100009. [Google Scholar] [CrossRef]
- Available online: https://www.ieee.org/ (accessed on 20 June 2024).
- Available online: https://www.acm.org/ (accessed on 20 June 2024).
- Fernandez, E.B.; Brazhuk, A. A critical analysis of Zero Trust Architecture (ZTA). Comput. Stand. Interfaces 2024, 89, 103832. [Google Scholar] [CrossRef]
- Lombardi, F.; Fanton, A. From DevOps to DevSecOps is not enough. CyberDevOps: An extreme shifting-left architecture to bring cybersecurity within software security lifecycle pipeline. Softw. Qual. J. 2023, 31, 619–654. [Google Scholar] [CrossRef]
- Nygård, A.R.; Katsikas, S.K. Ethical hardware reverse engineering for securing the digital supply chain in critical infrastructure. Inf. Comput. Secur. 2024, 32, 365–377. [Google Scholar] [CrossRef]
- Al Obaidan, F.; Saeed, S. Digital transformation and cybersecurity challenges: A study of malware detection using machine learning techniques. In Handbook of Research on Advancing Cybersecurity for Digital Transformation; IGI Global: Hershey, PA, USA, 2021; pp. 203–226. [Google Scholar]
- Alohali, M.A.; Alasmari, N.; Maashi, M.; Nouri, A.M.; Rizwanullah, M.; Yaseen, I.; Alneil, A.A. Metaheuristics with deep learning driven phishing detection for sustainable and secure environment. Sustain. Energy Technol. Assess. 2023, 56, 103114. [Google Scholar]
- Georgiadou, A.; Michalitsi-Psarrou, A.; Askounis, D. A security awareness and competency evaluation in the energy sector. Comput. Secur. 2023, 129, 103199. [Google Scholar] [CrossRef]
- Sharma, A.; Gupta, B.B.; Singh, A.K.; Saraswat, V.K. Advanced persistent threats (apt): Evolution, anatomy, attribution and countermeasures. J. Ambient Intell. Humaniz. Comput. 2023, 14, 9355–9381. [Google Scholar] [CrossRef]
- Guo, Y. A review of Machine Learning-based zero-day attack detection: Challenges and future directions. Comput. Commun. 2023, 198, 175–185. [Google Scholar] [CrossRef] [PubMed]
- Alzaabi, F.R.; Mehmood, A. A review of recent advances, challenges, and opportunities in malicious insider threat detection using machine learning methods. IEEE Access 2024, 12, 30907–30927. [Google Scholar] [CrossRef]
- Kurii, Y.; Opirskyy, I. Analysis and Comparison of the NIST SP 800-53 and ISO/IEC 27001: 2013. In Proceedings of the CPITS-2022: Cybersecurity Providing in Information and Telecommunication Systems, Kyiv, Ukraine, 13 October 2022. [Google Scholar]
- Kitsios, F.; Chatzidimitriou, E.; Kamariotou, M. The ISO/IEC 27001 information security management standard: How to extract value from data in the IT sector. Sustainability 2023, 15, 5828. [Google Scholar] [CrossRef]
- Heluany, J.B.; Galvão, R. IEC 62443 standard for hydro power plants. Energies 2023, 16, 1452. [Google Scholar] [CrossRef]
- Mortensen, B.O.G.; Hjerrild, L. Legal Overview of Latest Developments in the Energy Sector Regarding Data Protection and Cybersecurity. In Proceedings of the Energy Informatics Academy Conference, Kuta, Bali, Indonesia, 23–25 October 2024; Springer Nature: Cham, Switzerland, 2025; pp. 112–119. [Google Scholar]
- Avramidou, M.; Biasin, E.; Kamenjasevic, E.; Kun, E.; Nisevic, M. Cybersecurity and the NIS2 Directive: Regulatory aspects and sectoral perspectives. In Proceedings of the Second ECSCI Workshop on Critical Infrastructure Protection and Resilience, Online, 27–29 April 2022; Steinbeis-Edition: Stuttgart, Germany, 2023; pp. 91–92. [Google Scholar]
- Available online: https://www.energy.gov/ceser/presidential-policy-directive-21 (accessed on 25 July 2024).
- Khubrani, M.M.; Alam, S. Blockchain-based microgrid for safe and reliable power generation and distribution: A case study of Saudi Arabia. Energies 2023, 16, 5963. [Google Scholar] [CrossRef]
- Mangla, C.; Rani, S.; Qureshi NM, F.; Singh, A. Mitigating 5G security challenges for next-gen industry using quantum computing. J. King Saud Univ.-Comput. Inf. Sci. 2023, 35, 101334. [Google Scholar] [CrossRef]
- Siluk JC, M.; de Carvalho, P.S.; Thomasi, V.; Pappis CD, O.; Schaefer, J.L. Cloud-based energy management systems: Terminologies, concepts and definitions. Energy Res. Soc. Sci. 2023, 106, 103313. [Google Scholar] [CrossRef]
- Carreiro, A.; Silva, C.; Antunes, M. The use of gamification on cybersecurity awareness of healthcare professionals. Procedia Comput. Sci. 2024, 239, 526–533. [Google Scholar] [CrossRef]
- Saeed, S.; Suayyid, S.A.; Al-Ghamdi, M.S.; Al-Muhaisen, H.; Almuhaideb, A.M. A systematic literature review on cyber threat intelligence for organizational cybersecurity resilience. Sensors 2023, 23, 7273. [Google Scholar] [CrossRef] [PubMed]
- Mohammed, A. Detection and Mitigation Strategies for Cyber-Attacks in Offshore Oil and Gas Industrial Networks. Ph.D. Dissertation, Cardiff University, Cardiff, UK, 2024. [Google Scholar]
- Saeed, S. Digital Workplaces and Information Security Behavior of Business Employees: An Empirical Study of Saudi Arabia. Sustainability 2023, 15, 6019. [Google Scholar] [CrossRef]
- Ahmad, A.; Maynard, S.B.; Motahhir, S.; Anderson, A. Case-based learning in the management practice of information security: An innovative pedagogical instrument. Pers. Ubiquitous Comput. 2021, 25, 853–877. [Google Scholar] [CrossRef]
- Patterson, C.M.; Nurse, J.R.; Franqueira, V.N. “I don’t think we’re there yet”: The practices and challenges of organisational learning from cyber security incidents. Comput. Secur. 2024, 139, 103699. [Google Scholar] [CrossRef]
- Hussain, M. An Effective Cybersecurity Risk Assessment Framework for a Public Sector Gas Production/Distribution Company. Ph.D. Dissertation, National College of Ireland, Dublin, Ireland, 2023. [Google Scholar]
- Bergset, S.; Nyland, A.J. Ensuring Safe and Secure Operations in the Norwegian Petroleum Industry: A Study on Assessing Trends in Cyber Risk Levels. Master’s Thesis, NTNU, Trondheim, Norway, 2023. [Google Scholar]
- Leppäsalo, N. Enhancing Cybersecurity Considerations in Plant-Level Safety Design of Nuclear Power Plant. Master’s Thesis, Aalto University, Espoo, Finland, 2024. [Google Scholar]
- Lee, S.W.; Lee, J.H. Improving the Efficiency of Cybersecurity Risk Analysis Methods for Nuclear Power Plant Control Systems. J. Korea Inst. Inf. Secur. Cryptol. 2024, 34, 537–552. [Google Scholar]
- Fuller, C.R. Shortening the Skills Gap: An Exploratory Study of Cybersecurity Professional Experience. Ph.D. Thesis, Capella University, Minneapolis, MN, USA, 2016. [Google Scholar]
- Anderson, A.; Ahmad, A.; Chang, S. Case-Based Learning for Cybersecurity Leaders: A Systematic Review and Research Agenda. Inf. Manag. 2024, 61, 104015. [Google Scholar] [CrossRef]
- Saeed, S.; Bajwa, I.S.; Mahmood, Z. Human Factors in Software Development and Design; IGI Global: Hershey, PA, USA, 2014. [Google Scholar]

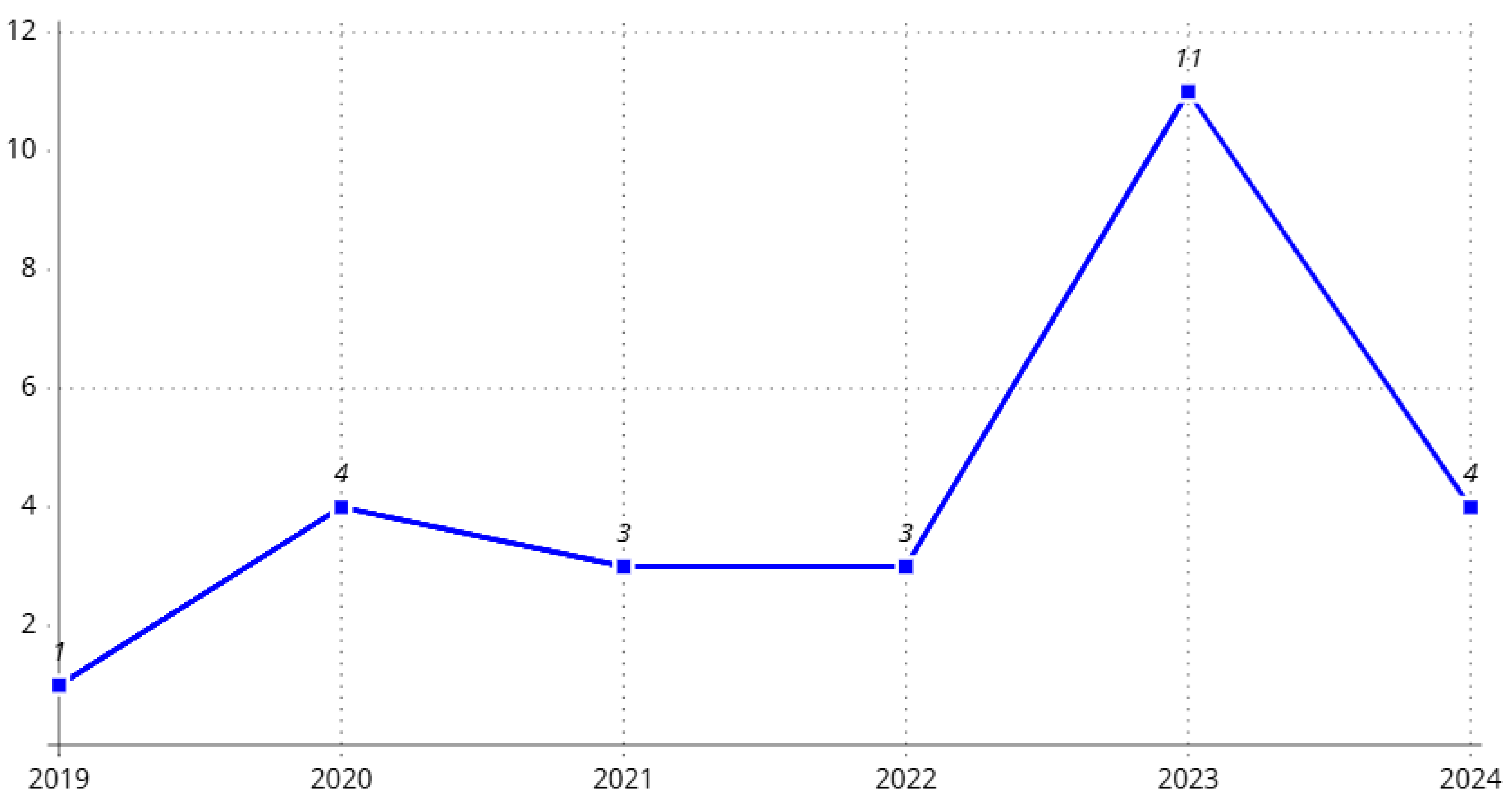

| S. No | Publication Year | Main Contribution | Technology/Method |
|---|---|---|---|
| [23] | 2023 |
Context and Problem:
Highlighted that the global cyberattacks increased by 50% in 2021 as a result of the pandemic’s intensification in 2020. This scenario has been made worse by the conflict in Ukraine since 2022, especially in the oil and gas sector, which is considered essential infrastructure, confronts cybersecurity issues that necessitate a proactive strategy that combines technology and behavioral controls. Solution and Result: Proposed a cybersecurity framework model that was assessed through implementation control and staff survey and showed 92.69% efficacy and 81.55% acceptance by staff. | Derived from the Center for Internet Security Critical Security Controls (CIS CSC) and the National Institute of Standards and Technology Cybersecurity Framework (NIST CSF). |
| [24] | 2023 | Context and Problem: Emphasized that the industrial control systems (ICS) and industrial automation and control systems, which have traditionally been protected from cyberspace, are at risk of cyberattack. They highlighted attacks such as the US Colonial Pipeline attack, Ukraine Grid Attack, and Norway Oil Platform attack. Solution and Results: Proposed a context-based detection approach integrated with a knowledge-based approach to mitigate the effect of cyberattacks. Existing monitoring applications can be utilized to identify and differentiate between various cyberattack types. This shows that it is feasible to monitor the ICS system’s IT and control components in order to develop risk-based cybersecurity decision support systems. | Integrating, a process-sensitive threat assessment for attack response with a context-based detection approach. |
| [25] | 2023 | Context and Problem: Emphasized the significance of selecting suitable machine learning algorithms for intrusion detection systems (IDS) in the oil and gas industry. Four machine learning algorithms were evaluated in this context. Solution and Results: Highlighted that the 1DCNN model achieved the highest performance with 96% accuracy. | Machine learning algorithms for intrusion detection in oil and gas industry using intrusion detection dataset. |
| [26] | 2024 | Context and Problem: Mentioned that the oil and gas industry is vulnerable to cyberattacks because of the digital transformation. They explored the degree of resilience by evaluating the oil and gas industry’s current cybersecurity procedures. Solution and Results: Examined the empirical data by proposing a “resilience ABC” which takes into account a significant difference between resilience based on adaptive capacity and robustness. | Empirical study. |
| [27] | 2023 | Context and Problem: Highlighted the dangers of cyber-attack (such as DoS, DDoS and MitM) on process control network (PCN) of the oil and gas industry. The PCN is exposed by its incapacity to identify these dangerous cyberattacks, and a successful attack could have disastrous consequences. Solution and Results: Performance evaluation of various machine learning techniques for detection of MitM attacks in a process control network in an oil and gas installation. Coarse tree algorithm showed high performance for identifying the MitM attack. | Machine learning techniques for detection of MitM attacks using real time dataset. |
| [28] | 2023 | Context and Problem: Underscored that the Egyptian oil and gas industry have gone through a digital transformation which led to several security breaches. Solution and Results: Investigated the benefits of implementing ISO 27001 for reducing cyber threats in Egypt’s downstream oil and gas industry and also raised cybersecurity awareness in the oil and gas industry. | Empirical study. |
| [30] | 2021 | Context and Problem: Highlighted the offshore oil and gas industry is facing cyber threats because of digitization. Solution and Results: Explored the risks to cyber security through a survey study and recommended organizational (such as cybersecurity awareness and training) and technical safeguards (such as real-time monitoring) that the oil and gas sector should implement. | Empirical study/survey. |
| [31] | 2019 | Context and Problem: The oil and Gas industry is vulnerable to various high-profile cyberattacks because of its critical infrastructure. This may lead to heavy economic damage as well as a threat to people’s security and the environment. Solution and Results: It outlines a comprehensive strategy to cybersecurity designed specifically for the oil and gas industry. This strategy addresses issues concerning technologies, people, and procedures, or the “three pillars” of cybersecurity. Moreover, devised cybersecurity strategy guidelines by integrating operational and organizational standpoint. | Proposed holistic framework and recommendations for cybersecurity resilience. |
| [32] | 2023 | Context and Problem: The oil and gas industry rely heavily on SCADA system which uses insecure communication protocols. It leads to several cyberattacks such as DoS. Solution and Results: Presented a unique field flooding attack by conducting an experimental study and highlighted that the PLC often used in the oil and gas field are particularly susceptible, since a single erroneous packet caused a 59 min denial of service. This algorithm showed 99% accuracy. | Evaluation of Field flooding attack on the network based on 4 h of network capture traffic from three testbeds to formulae dataset. |
| [33] | 2024 | Context and Problem: Cyberattacks can destroy and damage critical infrastructures such as power, water, and gas because of the lack of real-world industrial control and automation systems. Solution and Results: Assessed the effectiveness of cybersecurity techniques used in industrial control systems using real-time data and formed a combined dataset. Results showed that the dataset quality affects the model’s performance. | Machine learning applications on three datasets of power system, freshwater tank, and gas pipeline. |
| [39] | 2020 | Context and Problem: Advanced metering infrastructure is vulnerable to cyberattacks because of digitization and can affect consumers. Solution and Results: Introduced two-stage intrusion detection mechanisms for the cybersecurity of smart meters in power grids which effectively identified the cyberattacks in smart meters. | Two staged intrusion detection for smart meters. |
| [40] | 2021 | Context and Problem: Electricity units are at risk of cyberattack by malicious consumers who may change their data reading in smart meters leading to electricity theft. Solution and Results: Focused on detecting electricity theft in photovoltaic (PV) generation using a data-driven method based on a regression tree. Performance of regression tree is compared with other models which showed better performance by regression tree. | Data-driven detection of cyberattacks in PV generation |
| [41] | 2022 | Context and Problem: The change and transit approach is very commonly used in smart metering systems, but it has brought challenges of vulnerability to cyberattacks which can lead to electricity theft, financial loss, and grid instability. Solution and Results: Deep learning-based solutions for detecting electricity theft in Advanced Metering Infrastructure (AMI) systems which outperform the traditional methods. | Deep learning-based change and transmit detection techniques in AMI networks |
| [42] | 2021 | Context and Problem: Common challenges in digitizing the power grid include security threats such as false data injection, which diminish the predicted assimilation performance. Solution and Results: Presented a user authentication approach to secure smart grid communications which improves the detection of false data injection more effectively. | Cybersecurity user authentication for smart grids. |
| [43] | 2022 | Context and Problem: Electric vehicle chargers when interacting with grid stations pose several cybersecurity vulnerabilities that can lead to financial loss and grid instability. Solution and Results: Analyzed cybersecurity threats related to electric vehicle charging infrastructure and proposed measures for securing EV chargers from attack. | Cybersecurity measures for electric vehicle charging infrastructure. |
| [44] | 2023 | Context and Problem: Electricity theft is a major factor in power outages. In recent years, there has been rising recognition of using neural network models in electrical theft detection (ETD). However, conventional techniques have a limited ability to gather deep properties, making it difficult to spot abnormalities in power consumption data consistently. Solution and Results: A model that aimed to enhance the precision of power theft detection using a transformer network with a Gaussian-weighted self-attention mechanism to capture global and temporal dependencies in electricity consumption data. | An experimental study using two datasets, including the State Grid Corporation of China (SGCC) and another dataset obtained from the Canadian Institute for Cybersecurity. |
| [45] | 2024 | Context and Problem: Combining solar distributed generation (DG) devices into the electricity grid adds complexity that might affect the grid’s dependability and security. Solution and Results: Evaluation of cybersecurity vulnerabilities and impacts of distributed solar inverters on the Australian grid. | Experimental evidence of cybersecurity vulnerabilities of distributed commercial solar inverters |
| [46] | 2024 | Context and Problem: Hydroelectric power plants face cyberattacks because they integrate into digital systems. Solution and Results: Enhancing cybersecurity of a hydroelectric power plant in Turkey using a digital twin model to detect and analyze attacks. Results showed that it improves threat detection. | Digital twin model. |
| [47] | 2020 | Context and Problem: The distributed generation domain is vulnerable to attack as malicious user can change the meeting readings, leading to electricity theft. Solution and Results: Developed a deep learning–based system to detect electricity theft in renewable distributed generation (DG) using novel cyber-attack functions. The model has the highest detection rate (99.3%) and the fewest false alarms (0.22%). | Utilized deep feed forward, deep recurrent, and deep convolutional recurrent neural networks for detection. Created datasets from smart meter readings, meteorological (solar irradiance) data, and SCADA metering data, simulating an IEEE 123 bus test system. |
| [48] | 2020 | Context and Problem: AMI networks face cyberattacks because of the malicious data given to them. Traditional models are unable to deal with this issue and are unable to detect electricity theft. Solution and Results: Detection of stealth cyber-attacks in AMI networks using variational auto-encoder-based techniques. Improve the detection rate by 11–15%, false alarm rate by 9–22%, and highest difference by 27–37% over existing detectors. | Variational auto-encoder. |
| [49] | 2020a | Context and Problem: Electricity theft is difficult to identify because of false energy consumption data and the legacy ML models are unable to identify these thefts. Solution and Results: Detection of electricity theft cyber-attacks in AMI networks using deep vector embeddings. The proposed model outperforms the shallow detectors showing high performance and accuracy. | Deep vector embeddings. |
| [50] | 2023 | Context and Problem: Integration of demand response programs in smart grids poses cyber security threats due to false data injection. Solution and Results: Explored vulnerabilities in demand-response systems with renewable energy integration under cyberattacks and proposed an online detector for cyberattacks. Results showed that detectors helped in effectively mitigating the attacks. | Vulnerability analysis of demand-response in smart grids. |
| [51] | 2022 | Context and Problem: The Swiss electricity system is prone to cyberattacks because of digital transformation. Solution and Results: Cybersecurity and resilience measures in the Swiss electricity sector, offering policy options for enhancement, which showed that the cybersecurity system needs improvement. | Participant feedback, cybersecurity, and resilience analysis. |
| [52] | 2023 | Context and Problem: Network microgrids face cyberattacks, especially from multi-layer DoS attacks. Solution and Results: Construct an online self-adaptive strategy of the control parameters to fully use the most recent information of all data transmission channels, hence mitigating the conservativeness of offline design against the worst-case attack across all devices. | Cyber-resilient self-triggered distributed control to mitigate multi-layer DoS attacks. |
| [60] | 2023 | Context and Problem: The nuclear industry is introduced to cybersecurity attacks because of digitization. Solution and Results: Devised a methodology for cybersecurity controls assessment of nuclear powerplant which offers a comprehensive understanding of cyberattacks. | Cybersecurity assessment framework. |
| [61] | 2023 | Context and Problem: Nuclear power plants and energy plants are becoming vulnerable to cyberattacks Solution and Results: Developed a cyber-physical testbed using digital twin technologies. The testbed included two plant-level and digital twins and two component-level digital twins for reactor malfunction/control action and component states/forecasting component input/output, respectively. | Digital twin, machine learning |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Saeed, S.; Gull, H.; Aldossary, M.M.; Altamimi, A.F.; Alshahrani, M.S.; Saqib, M.; Zafar Iqbal, S.; Almuhaideb, A.M. Digital Transformation in Energy Sector: Cybersecurity Challenges and Implications. Information 2024, 15, 764. https://doi.org/10.3390/info15120764
Saeed S, Gull H, Aldossary MM, Altamimi AF, Alshahrani MS, Saqib M, Zafar Iqbal S, Almuhaideb AM. Digital Transformation in Energy Sector: Cybersecurity Challenges and Implications. Information. 2024; 15(12):764. https://doi.org/10.3390/info15120764
Chicago/Turabian StyleSaeed, Saqib, Hina Gull, Muneera Mohammad Aldossary, Amal Furaih Altamimi, Mashael Saeed Alshahrani, Madeeha Saqib, Sardar Zafar Iqbal, and Abdullah M. Almuhaideb. 2024. "Digital Transformation in Energy Sector: Cybersecurity Challenges and Implications" Information 15, no. 12: 764. https://doi.org/10.3390/info15120764
APA StyleSaeed, S., Gull, H., Aldossary, M. M., Altamimi, A. F., Alshahrani, M. S., Saqib, M., Zafar Iqbal, S., & Almuhaideb, A. M. (2024). Digital Transformation in Energy Sector: Cybersecurity Challenges and Implications. Information, 15(12), 764. https://doi.org/10.3390/info15120764







