A Distributed RF Threat Sensing Architecture
Abstract
1. Introduction
- Design of a low-cost RF monitoring sensor, based on a wideband, wide dynamic range logarithmic amplifier, to be utilized for multi-band interference, RF jamming monitoring, with distributed and collaborative capabilities.
- Interconnection of the proposed sensor with a security operations center (SOC), providing raw RF data and alerts, per monitored frequency band, in case of an anomaly—either interference or jamming activity.
- Provision of an automated calibration process, allowing reliable, long-term RF recordings and RSS threshold analysis, for optimizing sensor operation in typical rural, suburban, and urban environments.
- Analysis of the main radio contributing factors for detecting drone operations, in the scope of this work.
2. Related Work
2.1. Jamming Attacks
- Constant Jamming: the attacker continuously transmits a high-power signal to disrupt the communication channel. In constant jamming attacks, the jammer may either target the whole channel bandwidth or a specific fraction of it, destroying the packet reception of legitimate users and preventing them from accessing the channel [9]. As a reference, based on work presented in [12] on WiFi communications, when the network is attacked by a constant broadband jammer, a 100% packet error rate occurs when the received desired signal power is 4 dB less than the jamming signal. Respectively, when the jamming occurs with only a bandwidth of one sub-carrier spacing, WiFi communications fail when dB [13]. This type of jamming is more easy to detect due to the constant interference it creates.
- Deceptive Jamming: the malicious device sends regular, meaningful signals that mimic legitimate communications, causing the receiving devices to think they are receiving valid data. The main purpose of this type of attack is to waste the resources of the wireless network to prevent the legitimate devices from accessing the channel [14]. This can be harder to detect than constant jamming.
- Random Jamming: the jammer alternates between jamming and non-jamming periods, making it more difficult to detect the source of the interference [15]. This type is not as efficient as constant jamming, but may endure for long periods as it conserves the attacker’s energy while still disrupting communications.
- Reactive Jamming: the attacker only transmits signals when legitimate communication is detected [16]. Due to this concept, reactive jammers are considered an energy-efficient attack strategy; however, they require tide timing constraints in order to rapidly switch from sensing mode to jamming. In practice, this can be achieved by implementing a built-in part of signal sensing or utilizing a third-party packet detection module. More detailed research work in this direction is presented in [17,18]. This method makes it harder to identify the jammer since the interference only occurs intermittently.
- Selective Jamming: the attacker targets specific types of communications, such as control channels or particular frequencies, by exploiting their knowledge of the targeted wireless network and the implementation details of network protocols at various layers of the protocol stack [19]. This can cause significant disruption with minimal effort, as critical components of the network are affected.
- Pulse Jamming: the attacker sends short bursts of high-power signals. This type of jamming can be very effective against certain types of modulation schemes and is challenging to counteract. Several countermeasure methods have been presented in the research community. For example, [20] investigates the challenge of anti-jamming communication in a random pulse jamming environment. The authors employ the Markov decision process (MDP) to model and analyze the countermeasure in the time domain, proposing an anti-pulse jamming algorithm based on reinforcement learning. In this way, they enable the transmitter to switch between two states—“active” and “silent”—to avoid random pulse jamming. Researchers in [21] propose the Swarm intelligence algorithm to adapt change in network topology and traffic, especially for IEEE 802.15.4 wireless networks. Based on this technique, the forward ants unicast or broadcast depending on the availability of the channel information for the end of the channel. If the channel information is available, the ants randomly choose the next hop. The source on receiving the channel information verifies the prevalence of the attacker and avoids the particular channel for transmission.
- Spot Jamming: the attacker focuses all their power on a single frequency or a narrow band of frequencies. In [22], the authors investigate the effects of interference in mmWave radar by utilizing another identical device to emulate spot jamming. Spot jamming effects, among other jamming attacks on GPS, are investigated in [23,24]. This can be very effective if the targeted frequency is critical for communication.
- Sweep Jamming: in sweep jamming, the attacker rapidly changes the frequency of the jamming signal across a range of frequencies. Different waveforms can be used for the sweeping signal, such as sinusoidal, square, triangle, saw-tooth, and chirp. This can disrupt communication over a broad spectrum and is harder to mitigate. In [25], researchers propose an anti-jamming algorithm based on distributed multi-agent reinforcement learning, for sweep and smart jamming strategies. Each terminal take the spectrum state of the environment as an input. Then the proposed algorithm employs Q-learning, along with the primary and backup channel allocation rules, to select the optimum communication channel.
- Barrage Jamming: the attacker jams multiple frequencies simultaneously. This type of jamming is very effective. It requires significant power and is typically used to disrupt communication across a wide band of frequencies and systems. Barrage jamming detection and classification for Synthetic Aperture Radar (SAR), based on a convolutional neural network (CNN), is presented in [26].
- Intelligent Jamming: the attacker uses advanced techniques, such as machine learning algorithms, to adapt their jamming strategy based on the network’s current state and responses. The evolution of AI/ML has been heavily implemented in jamming strategies as well, which makes such jamming techniques much more effective and harder to counter. Reference [27] presents intelligent jamming in LTE networks, while intelligent anti-jamming is discussed in [28].
2.2. Jamming Sensing
3. Proposed Approach
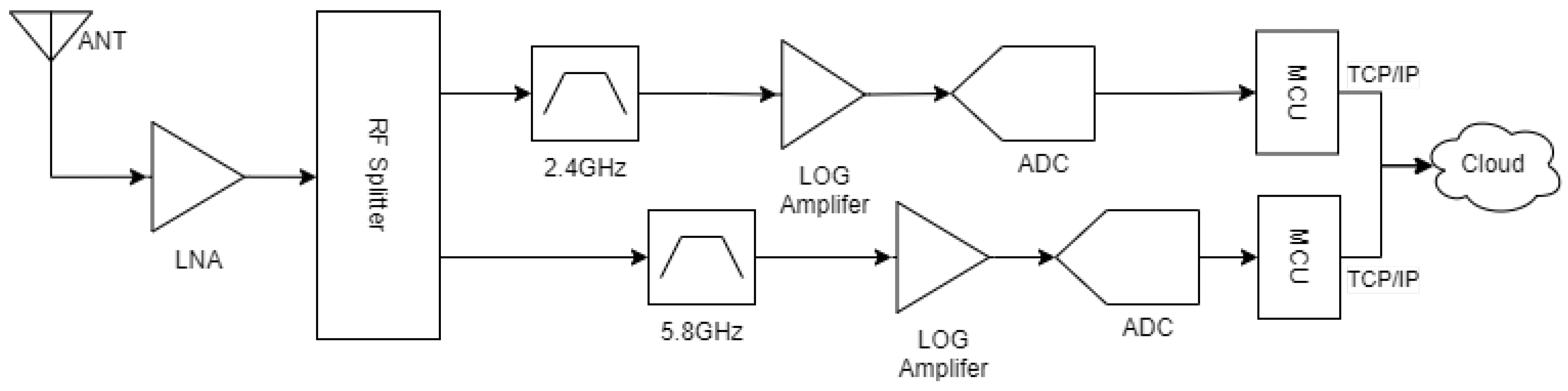
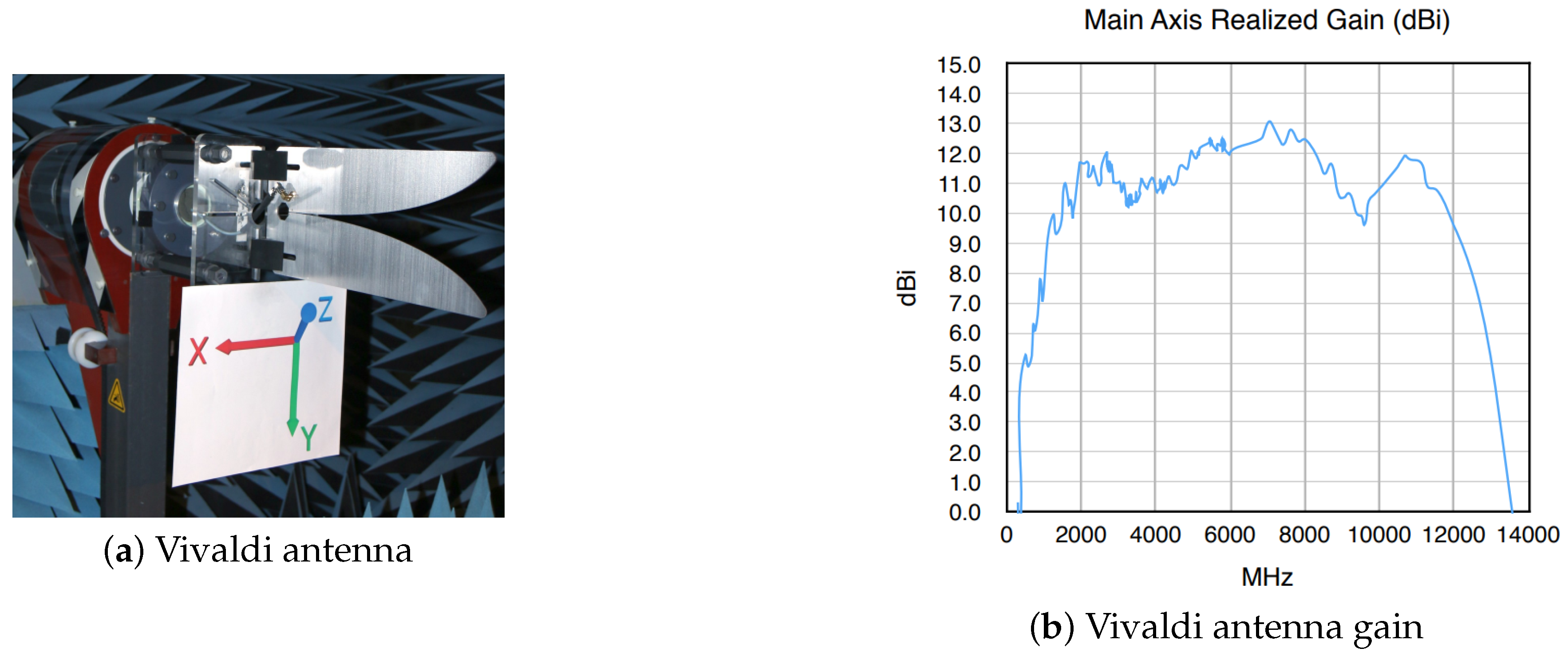
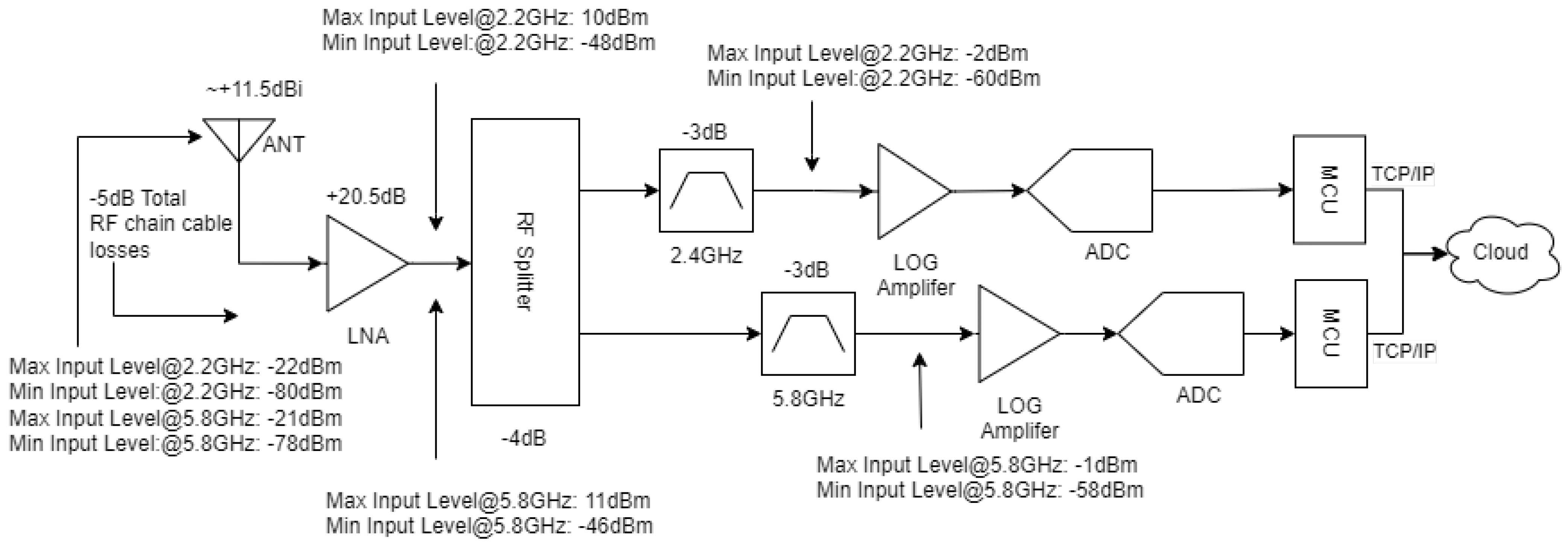
3.1. Low-Cost RF Sensor Design Using a Logarithmic Amplifier
- Connecting the device to the module manager.
- Accessing the network and configuring the module IP for SOC interconnection.
- Monitoring the module status.
- Configuring the module parameters (general information, configuring the system clock and the reporting server, and calibrating the modules of the RF sensor).
- Setting up active RF measurement and RF jamming monitoring.
3.2. Sensor Calibration
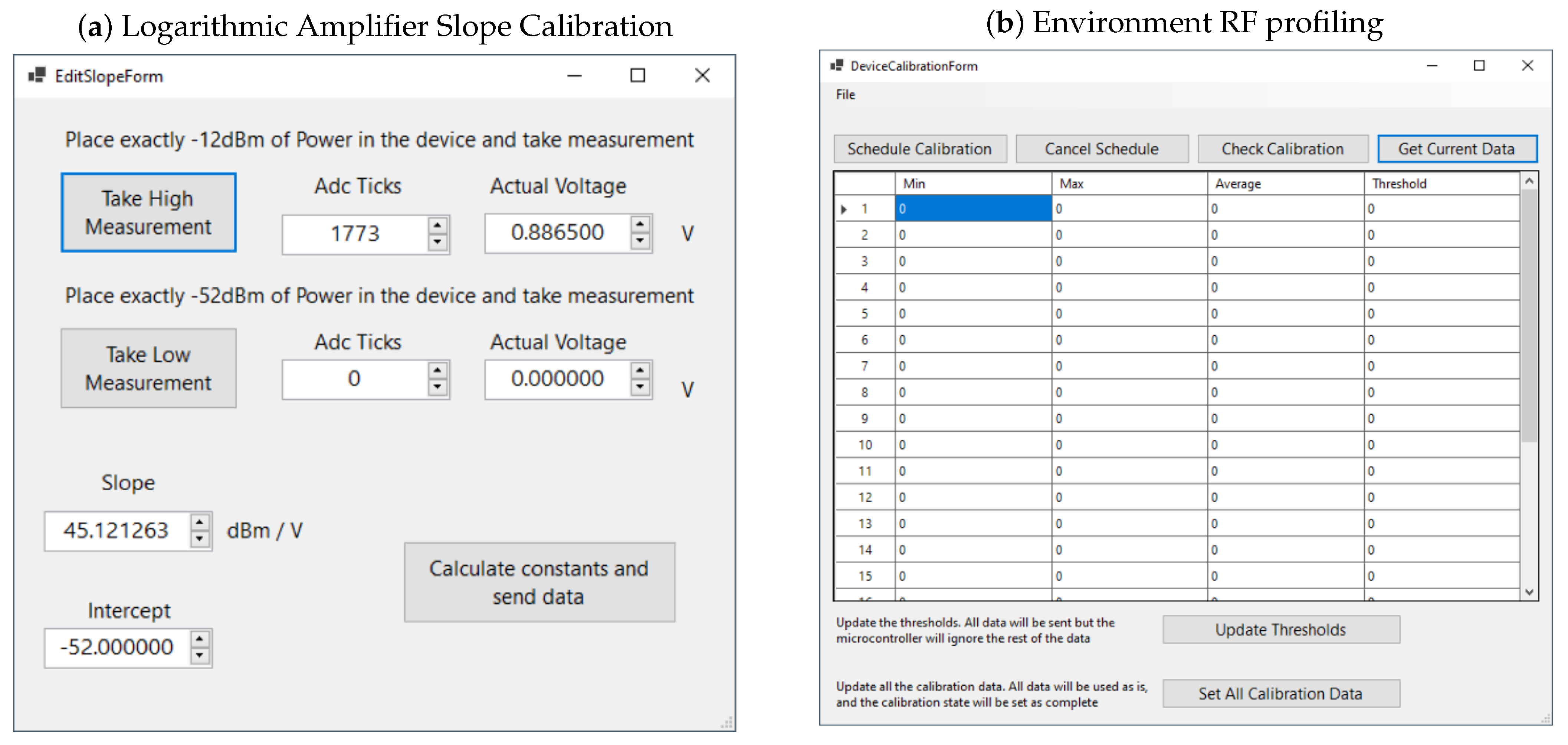
3.2.1. Calibrating the Logarithmic Amplifier
3.2.2. Environment RF Profiling
3.3. Sensor Expected Performance and Alarm Threshold Level
| Algorithm 1: ATL Algorithm for RF Jamming Detection |
 |
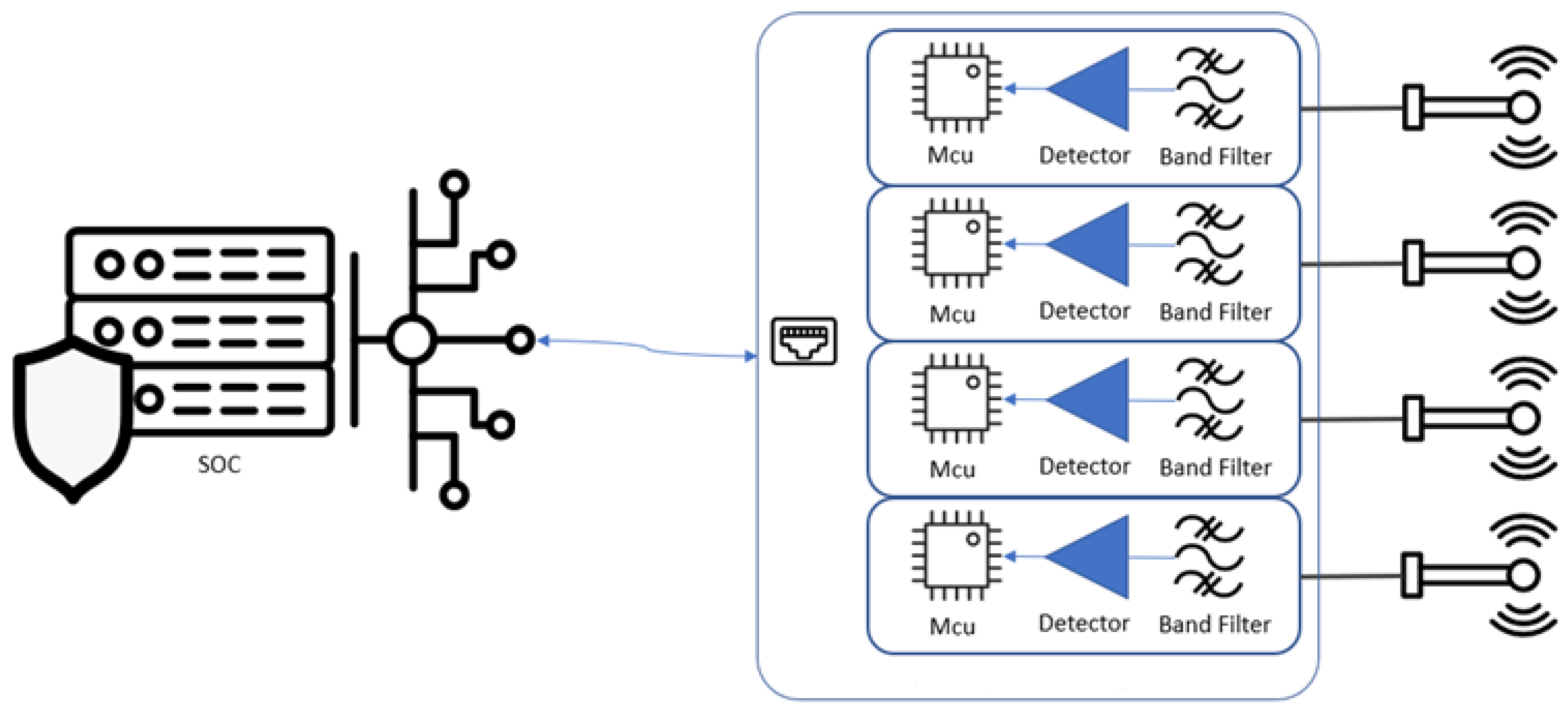
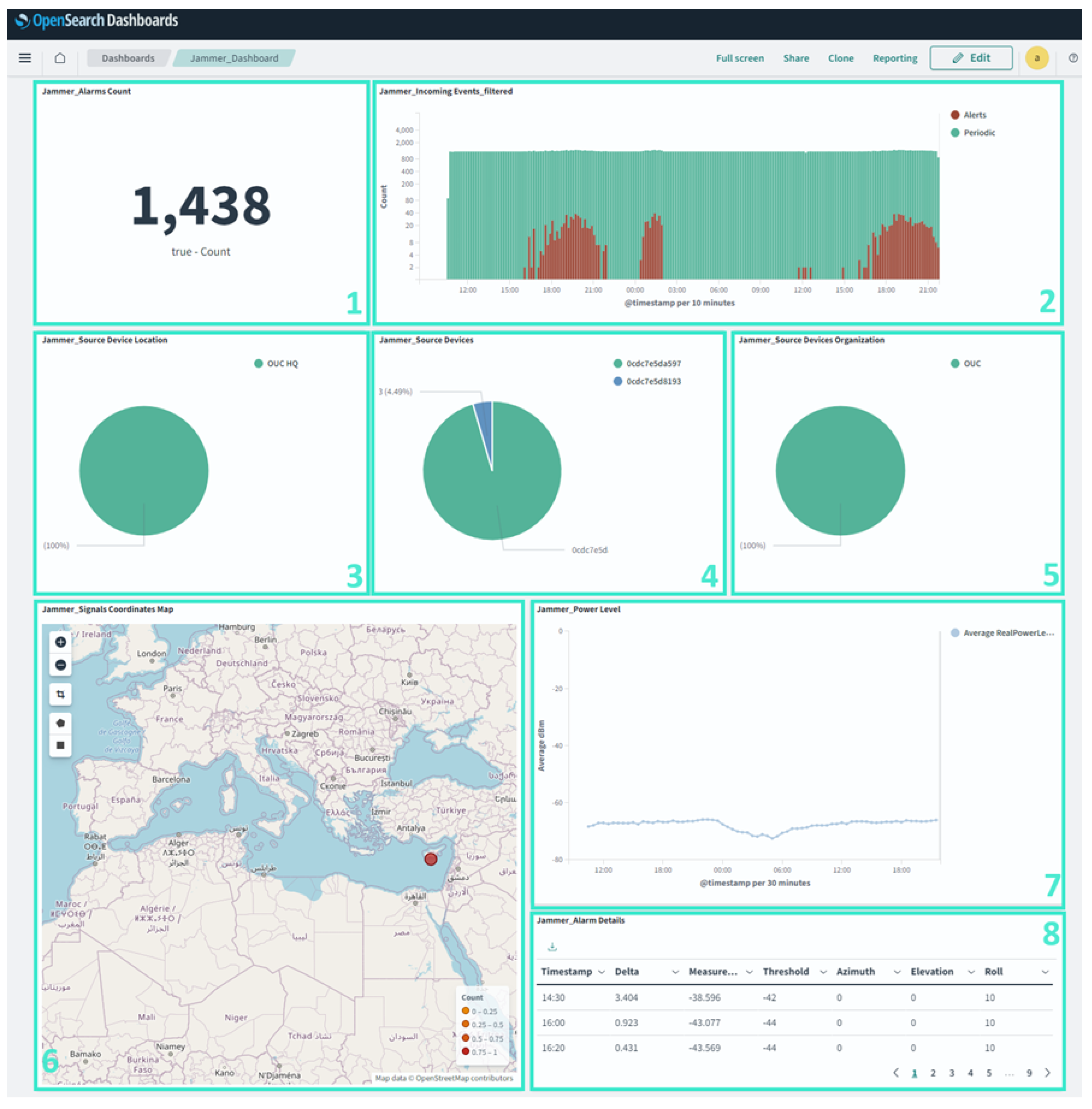
3.4. Sensor Interconnection with a SOC
- Device name and hostname.
- Device ID and IP addresses.
- Various measurement values, including threshold, delta, and geographic coordinates (longitude and latitude).
- Antenna orientation details (azimuth, elevation, roll).
- Measurement settings (samples, period).
- Alarm status.
- Sensor attenuation and actual measurement values.
- Device information (location, band, name, group).
- Timestamp and version.
4. Test Environment and Experiment Setup
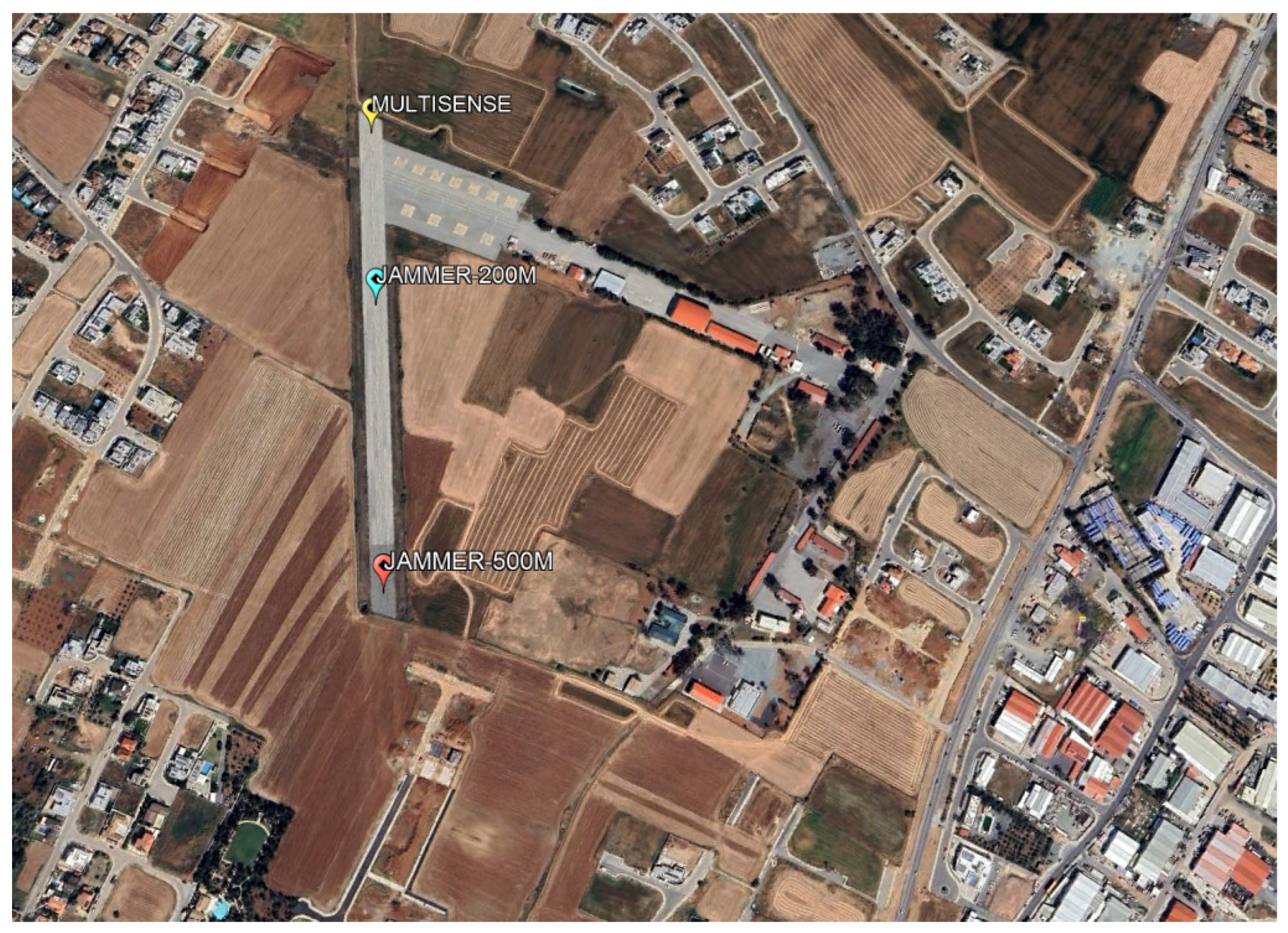
4.1. Test Environment
4.2. Experiment Setup and Measurements
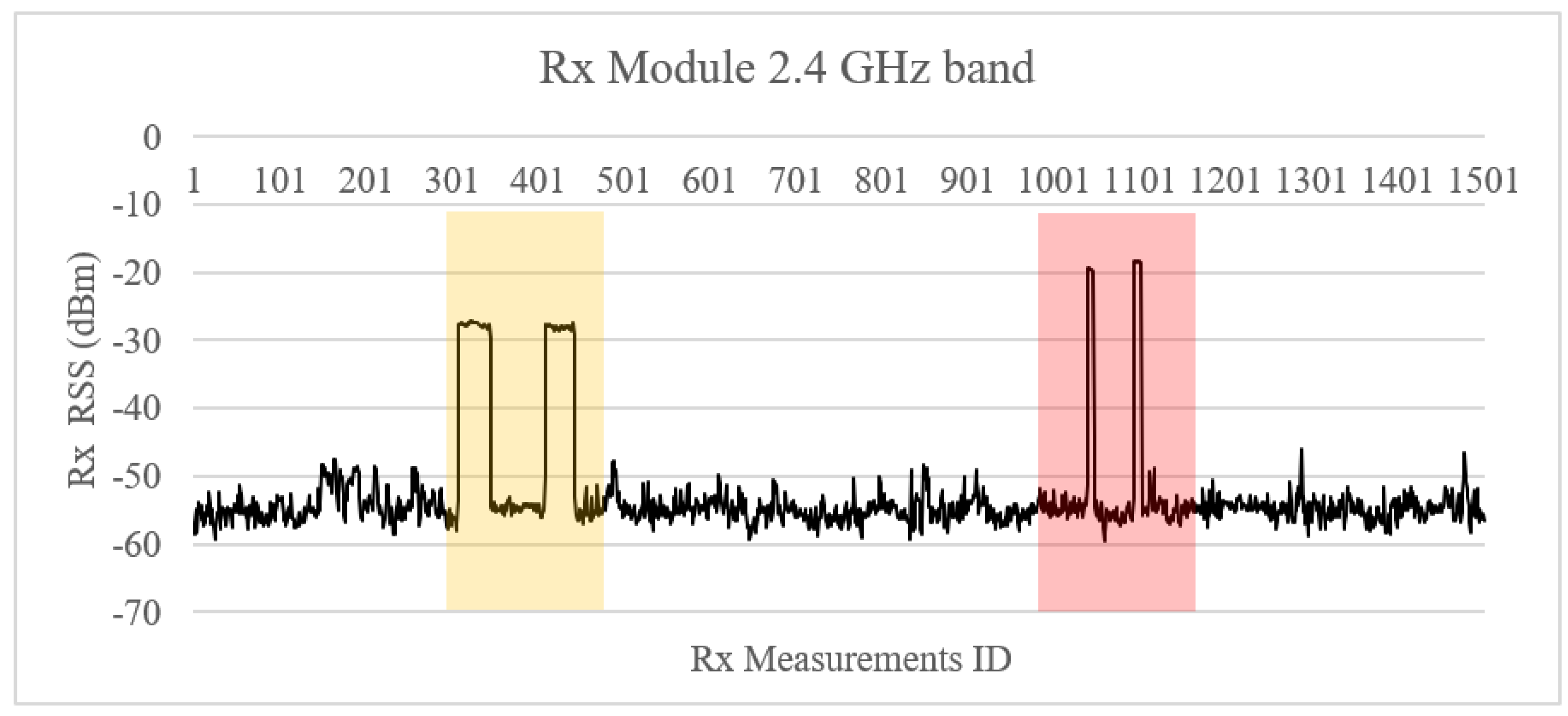
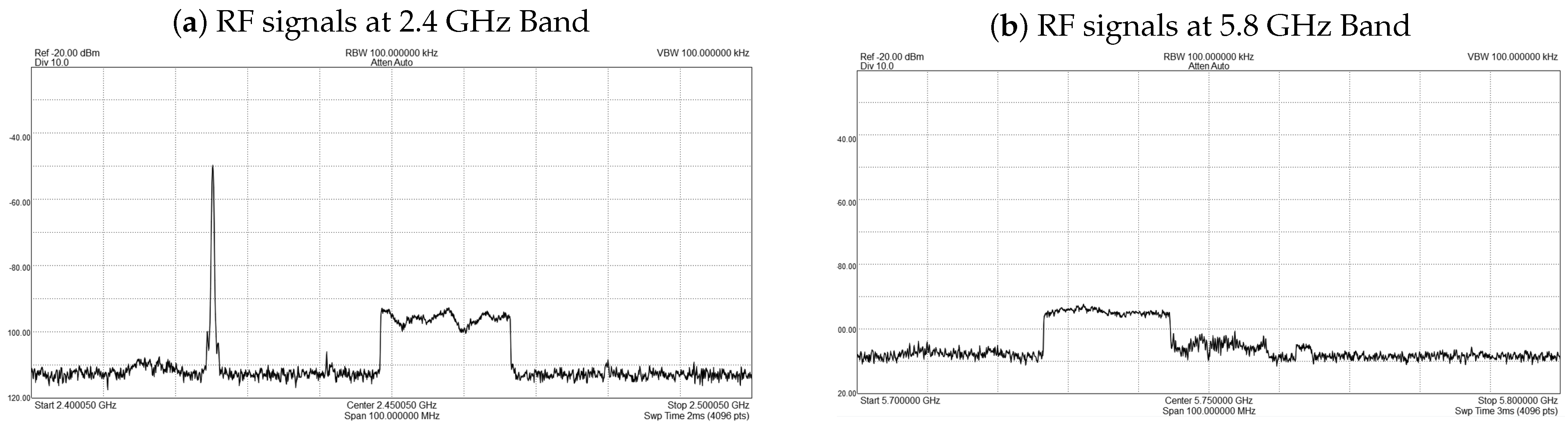
4.2.1. High-Power Frequency Sweep Jamming Attack in Both 2.4 GHz and 5.8 GHz Frequency Bands
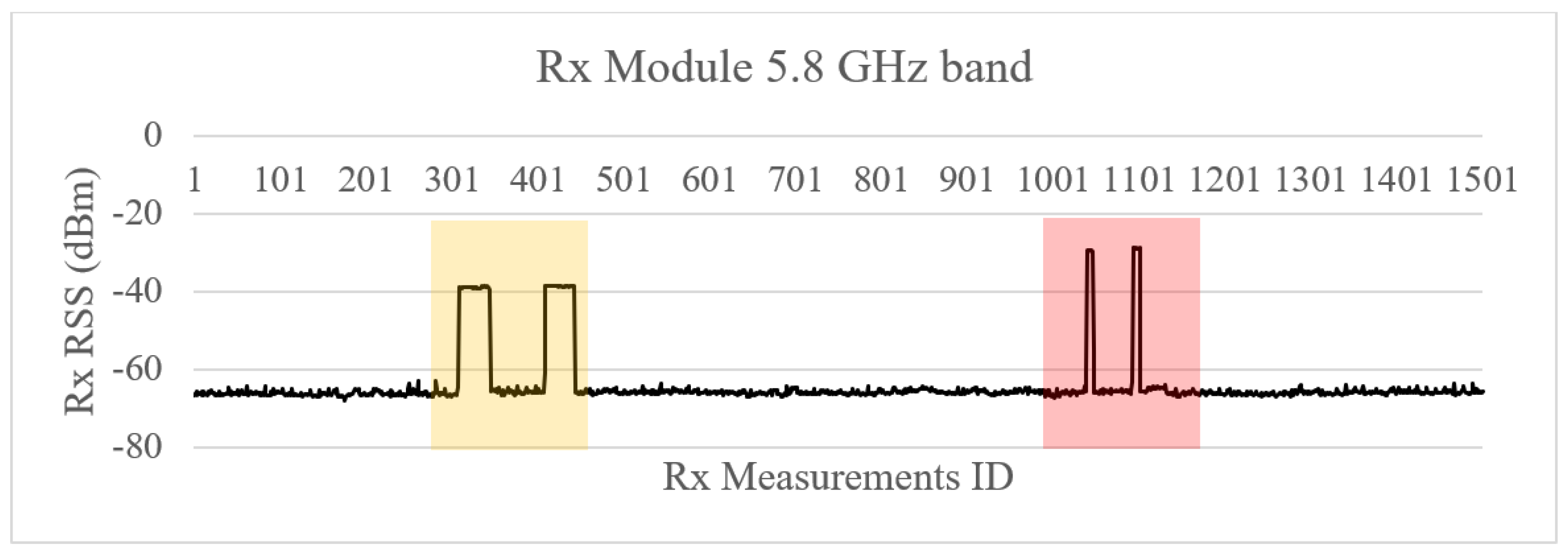
4.2.2. Low-Power Constant Jamming Attack in 5.8 GHz Frequency Band
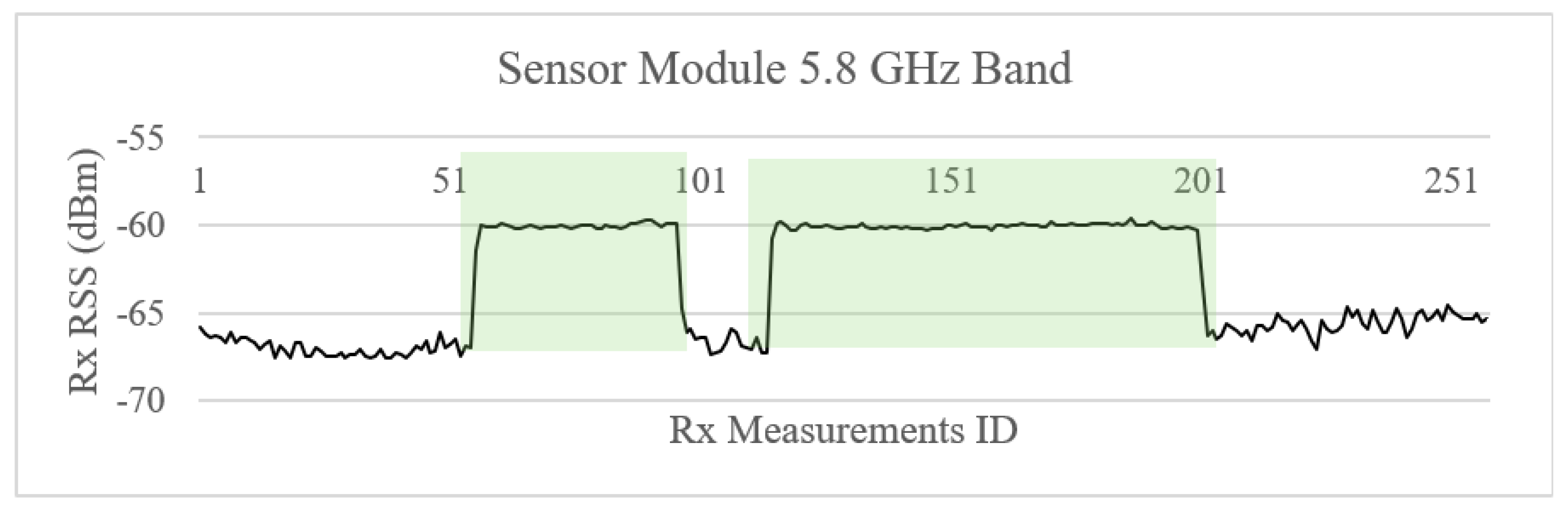
4.2.3. Drone Detection RF Profiling
5. Performance Evaluation
5.1. Jamming Detection
5.2. Drone Detection
5.3. Limitations
6. Conclusions
- The deployment and testing of several collaborative sensors utilizing multiple direction antennas for jamming source localization with AoA/DoA and triangulation techniques.
- Implementation of an RF down-converting receiver chain and integration of sharper RF filters to improve the system sensitivity for the purpose of supporting simple drone activity detection at longer distances.
- Implementation of AI/ML techniques at the SOC level for optimized detection of RF spectrum anomalies from several distributed sensors.
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| 5G | 5th generation |
| AoA | Angle of arrival |
| AI | Artificial Intelligence |
| BER | Bit error rate |
| C/No | Carrier-to-Noise density power ratio |
| CRN | Cognitive radio networks |
| DL | Deep learning |
| DoA | Direction of arrival |
| DoS | Denial of Service |
| ECC | Error-correcting code |
| GNSS | Global Navigation Satellite System |
| GPS | Global Positioning System |
| GUI | Graphical User Interface |
| IoT | Internet of Things |
| IoE | Internet of Everything |
| JI | Jamming index |
| LNA | Low-noise amplifier |
| LOS | Line-of-sight |
| MDPI | Multidisciplinary Digital Publishing Institute |
| MaMIMO | Massive MIMO |
| MIMO | Multiple-input multiple-output |
| ML | Machine learning |
| mmWave | Millimeter Wave |
| MQTTs | Secure Message Queuing Telemetry Transport |
| NLOS | Non-line-of-sight |
| NOMA | Non-orthogonal multiple access |
| OFDM | Orthogonal frequency division multiplexing |
| RSS | Received signal strength |
| RSSI | Received signal strength indicator |
| SDR | Software-defined radio |
| SDN | Software-defined networking |
| SNR | Signal-to-noise ratio |
| SoI | Signal of interest |
| SOC | Security operations center |
| TAL | (RSS) Threshold Alert Level |
| UAV | Unmanned aerial vehicle |
| WLAN | Wireless Local Area Network |
| WSN | Wireless Sensors Network |
References
- Sinha, D.; Verma, A.K.; Kumar, S. Software defined radio: Operation, challenges and possible solutions. In Proceedings of the 2016 10th International Conference on Intelligent Systems and Control (ISCO), Coimbatore, India, 7–8 January 2016; pp. 1–5. [Google Scholar] [CrossRef]
- Xia, W.; Wen, Y.; Foh, C.H.; Niyato, D.; Xie, H. A Survey on Software-Defined Networking. IEEE Commun. Surv. Tutorials 2015, 17, 27–51. [Google Scholar] [CrossRef]
- Shen, X.; Liu, Y.; Zhao, L.; Huang, G.L.; Shi, X.; Huang, Q. A Miniaturized Microstrip Antenna Array at 5G Millimeter-Wave Band. IEEE Antennas Wirel. Propag. Lett. 2019, 18, 1671–1675. [Google Scholar] [CrossRef]
- Björnson, E.; Sanguinetti, L. Scalable Cell-Free Massive MIMO Systems. IEEE Trans. Commun. 2020, 68, 4247–4261. [Google Scholar] [CrossRef]
- Makki, B.; Chitti, K.; Behravan, A.; Alouini, M.S. A Survey of NOMA: Current Status and Open Research Challenges. IEEE Open J. Commun. Soc. 2020, 1, 179–189. [Google Scholar] [CrossRef]
- Naderializadeh, N.; Maddah-Ali, M.A.; Avestimehr, A.S. Cache-Aided Interference Management in Wireless Cellular Networks. IEEE Trans. Commun. 2019, 67, 3376–3387. [Google Scholar] [CrossRef]
- Yu, P.; Zhou, F.; Zhang, X.; Qiu, X.; Kadoch, M.; Cheriet, M. Deep Learning-Based Resource Allocation for 5G Broadband TV Service. IEEE Trans. Broadcast. 2020, 66, 800–813. [Google Scholar] [CrossRef]
- Pelechrinis, K.; Iliofotou, M.; Krishnamurthy, S.V. Denial of Service Attacks in Wireless Networks: The Case of Jammers. IEEE Commun. Surv. Tutorials 2011, 13, 245–257. [Google Scholar] [CrossRef]
- KanikaLim, G.; Qing, A. Jamming and Anti-jamming and Techniques in Wireless Networks: A Survey. Int. J. Hoc Ubiquitous Comput. 2014, 17, 197–215. [Google Scholar]
- Ali, A.S.; Baddeley, M.; Bariah, L.; Lopez, M.A.; Lunardi, W.T.; Giacalone, J.P.; Muhaidat, S. JamRF: Performance Analysis, Evaluation, and Implementation of RF Jamming over Wi-Fi. IEEE Access 2022, 10, 133370–133384. [Google Scholar] [CrossRef]
- Hossein, P.; Huacheng, Z. Jamming Attacks and Anti-Jamming Strategies in Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutorials 2022, 24, 767–809. [Google Scholar] [CrossRef]
- Karhima, T.; Silvennoinen, A.; Hall, M.; Haggman, S.G. IEEE 802.11b/g WLAN tolerance to jamming. In Proceedings of the IEEE MILCOM 2004, Military Communications Conference, Monterey, CA, USA, 31 October–3 November 2004. [Google Scholar]
- Jun, L.; Andrian, J.H.; Zhou, C. Bit Error Rate Analysis of jamming for OFDM systems. In Proceedings of the 2007 Wireless Telecommunications Symposium, Pomona, CA, USA, 26–28 April 2007; pp. 1–8. [Google Scholar] [CrossRef]
- Gvozdenovic, S.; Becker, J.K.; Mikulskis, J.; Starobinski, D. Truncate after preamble: PHY-based starvation attacks on IoT networks. In Proceedings of the 13th ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec’20), New York, NY, USA, 8–10 July 2020; pp. 89–98. [Google Scholar] [CrossRef]
- Bayraktaroglu, E.; King, C.; Liu, X.; Noubir, G.; Rajaraman, R.; Thapa, B. Performance of IEEE 802.11 under jamming. Mob. Netw. Appl. 2013, 18, 678–696. [Google Scholar] [CrossRef]
- Cai, Y.; Pelechrinis, K.; Wang, X.; Krishnamurthy, P.; Mo, Y. Joint reactive jammer detection and localization in an enterprise WiFi network. Comput. Netw. 2013, 57, 3799–3811. [Google Scholar] [CrossRef]
- Yan, Q.; Zeng, H.; Jiang, T.; Li, M.; Lou, W.; Hou, Y.T. Jamming Resilient Communication Using MIMO Interference Cancellation. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1486–1499. [Google Scholar] [CrossRef]
- Schulz, M.; Gringoli, F.; Steinmetzer, D.; Koch, M.; Hollick, M. Massive reactive smartphone-based jamming using arbitrary waveforms and adaptive power control. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks, New York, NY, USA, 18–20 July 2017; pp. 111–121. [Google Scholar]
- Proaño, A.; Lazos, L. Selective Jamming Attacks in Wireless Networks. In Proceedings of the 2010 IEEE International Conference on Communications, Cape Town, South Africa, 23–27 May 2010; pp. 1–6. [Google Scholar] [CrossRef]
- Zhou, Q.; Li, Y.; Niu, Y. A Countermeasure Against Random Pulse Jamming in Time Domain Based on Reinforcement Learning. IEEE Access 2020, 8, 97164–97174. [Google Scholar] [CrossRef]
- Sudha, I.; Mustafa, M.A.; Suguna, R.; Karupusamy, S.; Ammisetty, V.; Shavkatovich, S.N.; Ramalingam, M.; Kanani, P. Pulse jamming attack detection using swarm intelligence in wireless sensor networks. Optik 2023, 272, 170251. [Google Scholar] [CrossRef]
- Kumuda, D.K.; Vandana, G.S.; Pardhasaradhi, B.; Raghavendra, B.S.; Srihari, P.; Cenkeramaddi, L.R. Multitarget Detection and Tracking by Mitigating Spot Jammer Attack in 77-GHz mm-Wave Radars: An Experimental Evaluation. IEEE Sens. J. 2023, 23, 5345–5361. [Google Scholar] [CrossRef]
- Elezi, E.; Çankaya, G.; Boyacı, A.; Yarkan, S. A detection and identification method based on signal power for different types of Electronic Jamming attacks on GPS signals. In Proceedings of the 2019 IEEE 30th Annual International Symposium on Personal, Indoor and Mobile Radio Communications (PIMRC), Istanbul, Turkey, 8–11 September 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Purwar, A.; Joshi, D.; Chaubey, V.K. GPS signal jamming and anti-jamming strategy—A theoretical analysis. In Proceedings of the 2016 IEEE Annual India Conference (INDICON), Bangalore, India, 16–18 December 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Ma, D.; Wang, Y.; Wu, S. Against Jamming Attack in Wireless Communication Networks: A Reinforcement Learning Approach. Electronics 2024, 13, 1209. [Google Scholar] [CrossRef]
- Junfei, Y.; Jingwen, L.; Bing, S.; Yuming, J. Barrage Jamming Detection and Classification Based on Convolutional Neural Network for Synthetic Aperture Radar. In Proceedings of the IGARSS 2018—2018 IEEE International Geoscience and Remote Sensing Symposium, Valencia, Spain, 22–27 July 2018; pp. 4583–4586. [Google Scholar] [CrossRef]
- Capotă, C.; Popescu, M.; Bădulă, E.M.; Halunga, S.; Fratu, O.; Popescu, M. Intelligent Jammer on Mobile Network LTE Technology: A Study Case in Bucharest. Appl. Sci. 2023, 13, 12286. [Google Scholar] [CrossRef]
- Zhou, Q.; Niu, Y. From Adaptive Communication Anti-Jamming to Intelligent Communication Anti-Jamming: 50 Years of Evolution. Adv. Intell. Syst. 2024, 6. [Google Scholar] [CrossRef]
- Lu, Z.; Wang, W.; Wang, C. Modeling, Evaluation and Detection of Jamming Attacks in Time-Critical Wireless Applications. IEEE Trans. Mob. Comput. 2014, 13, 1746–1759. [Google Scholar] [CrossRef]
- Yang, H.; Shi, M.; Xia, Y.; Zhang, P. Security Research on Wireless Networked Control Systems Subject to Jamming Attacks. IEEE Trans. Cybern. 2019, 49, 2022–2031. [Google Scholar] [CrossRef] [PubMed]
- Cheng, M.; Ling, Y.; Wu, W.B. Time Series Analysis for Jamming Attack Detection in Wireless Networks. In Proceedings of the GLOBECOM 2017—2017 IEEE Global Communications Conference, Singapore, 4–8 December 2017; pp. 1–7. [Google Scholar] [CrossRef]
- Reyes, H.; Kaabouch, N. Jamming and Lost Link Detection in Wireless Networks with Fuzzy Logic. Int. J. Sci. Eng. Res. 2013, 4, 1–7. [Google Scholar]
- Abdulkawi, A.; Saleh, T.S.; Khattab, S.; Farag, I. Anti-jamming defense in wireless networks using channel hopping and error correcting code. In Proceedings of the 2012 8th International Conference on Informatics and Systems (INFOS), Giza, Egypt, 14–16 May 2012; pp. NW-12–NW-17. [Google Scholar]
- Marttinen, A.; Wyglinski, A.M.; Jantti, R. Statistics-Based Jamming Detection Algorithm for Jamming Attacks against Tactical MANETs. In Proceedings of the 2014 IEEE Military Communications Conference, Baltimore, MD, USA, 6–8 October 2014. [Google Scholar] [CrossRef]
- Akhlaghpasand, H.; Razavizadeh, S.M.; Bjornson, E.; Do, T.T. Jamming Detection in Massive MIMO Systems. IEEE Wirel. Commun. Lett. 2018, 7, 242–245. [Google Scholar] [CrossRef]
- Borio, D.; Gioia, C. Real-time jamming detection using the sum-of-squares paradigm. In Proceedings of the 2015 International Conference on Localization and GNSS (ICL-GNSS), Gothenburg, Sweden, 22–24 June 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Zahra, F.T.; Bostanci, Y.S.; Soyturk, M. Real-Time Jamming Detection in Wireless IoT Networks. IEEE Access 2023, 11, 70425–70442. [Google Scholar] [CrossRef]
- Strasser, M.; Danev, B.; Čapkun, S. Detection of reactive jamming in sensor networks. ACM Trans. Sens. Netw. 2010, 7, 1–29. [Google Scholar] [CrossRef]
- Puñal, O.; Aktaş, I.; Schnelke, C.J.; Abidin, G.; Wehrle, K.; Gross, J. Machine learning-based jamming detection for IEEE 802.11: Design and experimental evaluation. In Proceedings of the Proceeding of IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks 2014, Sydney, NSW, Australia, 19 June 2014; pp. 1–10. [Google Scholar] [CrossRef]
- Arjoune, Y.; Salahdine, F.; Islam, M.S.; Ghribi, E.; Kaabouch, N. A Novel Jamming Attacks Detection Approach Based on Machine Learning for Wireless Communication. In Proceedings of the 2020 International Conference on Information Networking (ICOIN), Barcelona, Spain, 7–10 January 2020; pp. 459–464. [Google Scholar] [CrossRef]
- Hussain, A.; Abughanam, N.; Qadir, J.; Mohamed, A. Jamming Detection in IoT Wireless Networks: An Edge-AI Based Approach. In Proceedings of the 12th International Conference on the Internet of Things, New York, NY, USA, 7–10 November 2022. [Google Scholar] [CrossRef]
- Sciancalepore, S.; Kusters, F.; Abdelhadi, N.K.; Oligeri, G. Jamming Detection in Low-BER Mobile Indoor Scenarios via Deep Learning. IEEE Internet Things J. 2024, 11, 14682–14697. [Google Scholar] [CrossRef]
- Li, Y.; Pawlak, J.; Price, J.; Al Shamaileh, K.; Niyaz, Q.; Paheding, S.; Devabhaktuni, V. Jamming Detection and Classification in OFDM-Based UAVs via Feature- and Spectrogram-Tailored Machine Learning. IEEE Access 2022, 10, 16859–16870. [Google Scholar] [CrossRef]
- Greco, C.; Pace, P.; Basagni, S.; Fortino, G. Jamming detection at the edge of drone networks using Multi-layer Perceptrons and Decision Trees. Appl. Soft Comput. 2021, 111, 107806. [Google Scholar] [CrossRef]
- Allahham, M.S.; Al-Sa’d, M.F.; Al-Ali, A.; Mohamed, A.; Khattab, T.; Erbad, A. DroneRF dataset: A dataset of drones for RF-based detection, classification and identification. Data Brief 2019, 26, 104313. [Google Scholar] [CrossRef]
| Jamming Attack Type | Strengths | Limitations |
|---|---|---|
| Constant Jamming |
|
|
| Deceptive Jamming |
|
|
| Random Jamming |
|
|
| Reactive Jamming |
|
|
| Selective Jamming |
|
|
| Pulse Jamming |
|
|
| Spot Jamming |
|
|
| Sweep Jamming |
|
|
| Barrage Jamming |
|
|
| Intelligent Jamming |
|
|
| No | Component | Loss (dB) |
|---|---|---|
| 1 | Internal RF cables and connectors | −5.0 |
| 2 | RF Coupler loss | −4.0 |
| 3 | RF Filter loss | −3.0 |
| TOTAL | −12.0 |
| Interference@2.4 GHz | Interference@5.8 GHz | |
|---|---|---|
| Min (dBm) | −67.4 | −70.2 |
| Max (dBm) | −47.3 | −61.5 |
| Average (dBm) | −57.2 | −66.3 |
| Interference@2.4 GHz | Interference@5.8 GHz | |
|---|---|---|
| Min (dBm) | −79.5 | −71.8 |
| Max (dBm) | −71.5 | −65.3 |
| Average (dBm) | −78.8 | −70.9 |
| Tx-Rx Distance (m) | 2.4 GHz | 5.8 GHz |
|---|---|---|
| 200 | 2.50 m | 1.61 m |
| 500 | 3.95 m | 2.54 m |
| Method | Triggers | False Positives | False-Positive Rate (FPR) | Precision (%) |
|---|---|---|---|---|
| Env. Max | 169 | 82 | 2.90% | 51.48% |
| ATL (k = 2) | 120 | 33 | 1.17% | 72.50% |
| ATL (k = 4) | 113 | 26 | 0.92% | 77.00% |
| ATL (k = 6) | 109 | 22 | 0.78% | 79.82% |
| ATL (k = 8) | 89 | 2 | 0.07% | 97.75% |
| Method | Triggers | False Positives | False-Positive Rate (FPR) | Precision (%) |
|---|---|---|---|---|
| Env. Max | 162 | 75 | 2.65% | 53.70% |
| ATL (k = 2) | 147 | 60 | 2.12% | 59.18% |
| ATL (k = 4) | 125 | 38 | 1.35% | 69.60% |
| ATL (k = 6) | 102 | 15 | 0.53% | 85.29% |
| ATL (k = 8) | 101 | 14 | 0.50% | 86.14% |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2024 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Michalis, G.; Rousias, A.; Kanaris, L.; Kokkinis , A.; Kanaris , P.; Stavrou, S. A Distributed RF Threat Sensing Architecture. Information 2024, 15, 752. https://doi.org/10.3390/info15120752
Michalis G, Rousias A, Kanaris L, Kokkinis A, Kanaris P, Stavrou S. A Distributed RF Threat Sensing Architecture. Information. 2024; 15(12):752. https://doi.org/10.3390/info15120752
Chicago/Turabian StyleMichalis, Georgios, Andreas Rousias, Loizos Kanaris, Akis Kokkinis , Pantelis Kanaris , and Stavros Stavrou. 2024. "A Distributed RF Threat Sensing Architecture" Information 15, no. 12: 752. https://doi.org/10.3390/info15120752
APA StyleMichalis, G., Rousias, A., Kanaris, L., Kokkinis , A., Kanaris , P., & Stavrou, S. (2024). A Distributed RF Threat Sensing Architecture. Information, 15(12), 752. https://doi.org/10.3390/info15120752







