IoTBChain: Adopting Blockchain Technology to Increase PLC Resilience in an IoT Environment
Abstract
1. Introduction
2. A Background on IoT Security and Privacy
2.1. IoT Architecture
2.2. IoT Issues in Security and Privacy
- Confidentiality: Only authorized individuals can view and retrieve personal data. Confidentiality is violated when confidential data is accessible due to a data leak.
- Data integrity guarantees that unauthorized entities have not altered or tampered with data. Among the many assaults that might jeopardize integrity, a man-in-the-middle attack is an example in which the data transmitted by one party to another could be intercepted and even altered by a “man-in-the-middle.”
- Availability guarantees that data are always available to those who require it. Attacks such as denial-of-service (DoS) attacks impede availability and prevent authorized individuals from obtaining information.
- Authentication is the process of confirming the legitimacy of the entities demanding access to data. Achieving these goals is crucial for any system. Multiple variables, such as weak passwords or password reuse that facilitate password-breaking operations by hackers, might undermine authentication. Because of this, protocols, like the FIDO protocol [13], that offer passwordless authentication are becoming increasingly common. Using such elements in an IoT system presents several difficulties [12].
- Node Capture describes a hacked node that causes the release of sensitive data. The hacker compromises the IoT system by adding a fake node, which allows for intrusive code attacks and compromises the system.
- A denial-of-service (DoS) attack could consume all available capacity and render the operations unavailable.
- A few assaults that may be encountered on the next layer, the network layer, are [12]:
- ○
- Jamming attack: By blocking the communication link, a jamming attack greatly slows down the nodes’ ability to communicate. A continuous jamming attack is an illustration of a jamming attack. A continuous jamming assault prevents legitimate nodes from using the communication link by emitting a radio signal.
- ○
- Reactive jamming attacks are more challenging to identify than continuous jamming attacks because the assault is dormant until it detects interaction on the communication link, after which it begins releasing the radio signal.
- ○
- In a selective forwarding attack, the attacking nodes will disable the network’s routing pathways by refusing to send some, all or portions of the packages.
- ○
- A sinkhole/wormhole attack consists of a malicious node answering routing queries, forcing communication to pass via a malicious node. The wormhole attack consists of a tunnel connecting two nodes while disregarding intermediary nodes.
- ○
- In a Sybil attack, a malicious node will impersonate several nodes to gain control over network spaces or impair the operation of the IoT system by copying their identities. Denial of service might be brought on by a rogue node, replicating the identity of some other node.
- ○
- The data’s confidentiality is compromised by a traffic analysis attack, which records and examines data chunks.
- ○
- In a “Man in the Middle” attack, an attacker or a malicious node listens in on exchanged information between two nodes. The attacker must intercept all pertinent communications sent and received by the two victims. This enables the malicious node or attacker to insert modified messages or data undetected. “Man in the middle” attacks only succeed if the malicious node successfully impersonates the endpoint by meeting the recipients’ or protocol’s expectations, as it aims to circumvent authentication.
- Unauthorized access by attackers to sensitive data. By accessing data as they are being delivered to their destination, malicious insiders might violate confidentiality and privacy.
- Insecure software service: Malware-infected software services are provided via the processing layer. An IoT system’s security features are in danger due to this. Third parties offer services with an unknown risk profile with an uncertain risk level in the processing layer. Lastly, the primary hazards [13,14] at the application level in which the consumers’ demands are addressed are:
- A social engineering attack involves mentally coercing people into divulging sensitive data or unwittingly carrying out destructive deeds. For instance, phishing scams.
- Software attacks are assaults that strike software, such as backdoors and buffer overflows.
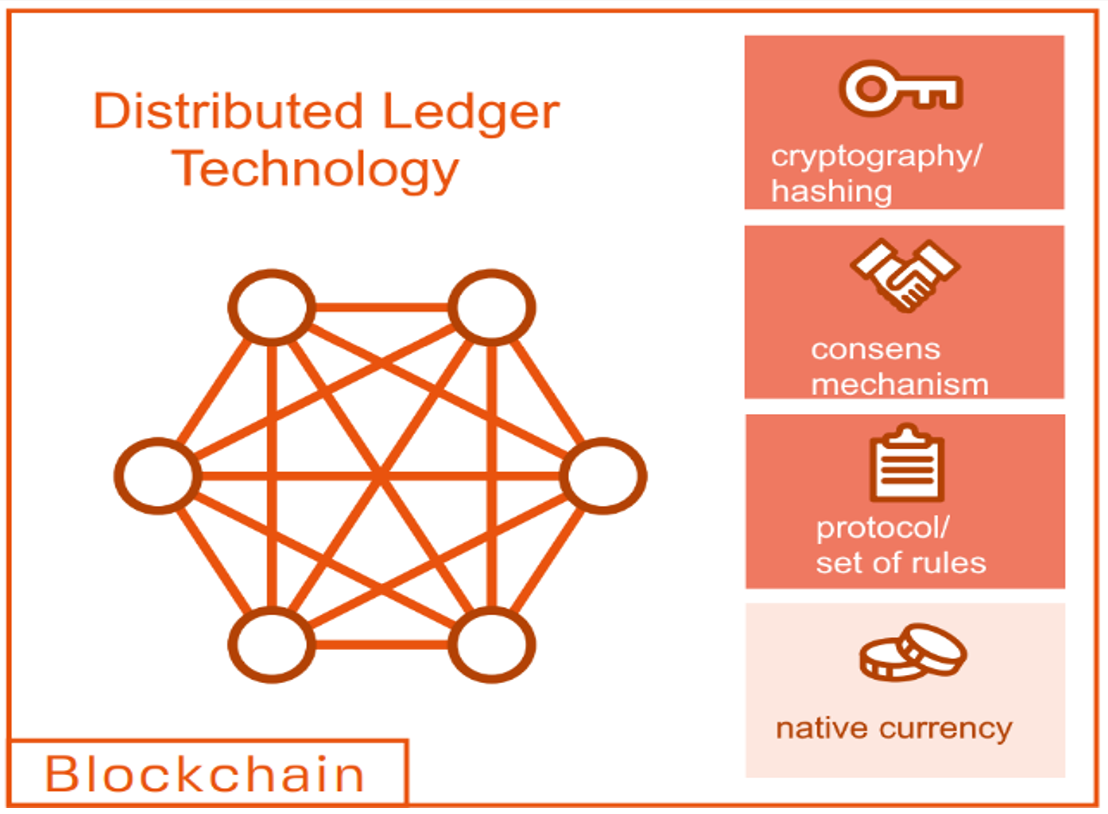
3. Blockchain-Based Systemt
3.1. Types of Blockchains
- B: block data (e.g., binary input and output signals of the PLC)
- N: nonce (a random value)
- H: hash value (with Z leading zeros).
- S_i: stake deposited by validator i
- Σ(S_all): total stake deposited by all validators.

3.2. Blockchain Architectures
3.2.1. Public Blockchain
3.2.2. Private Blockchain
3.2.3. Consortium Blockchain
3.3. Blockchain Security and Privacy Characteristics
4. Literature Review
4.1. Software Update Approach
4.2. Access Control Systems
4.3. Protection Approach
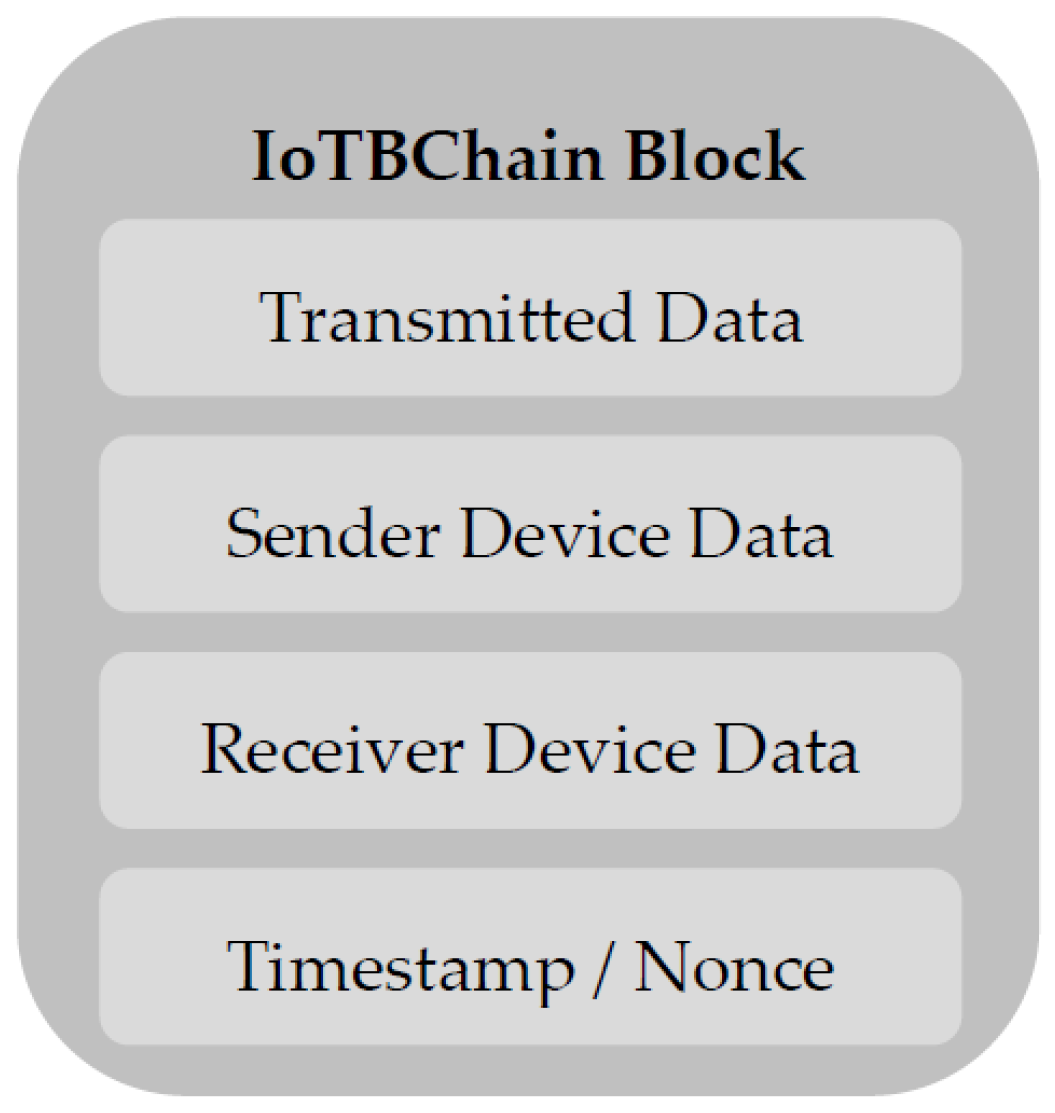
5. The Proposed Approach: IoTBChain
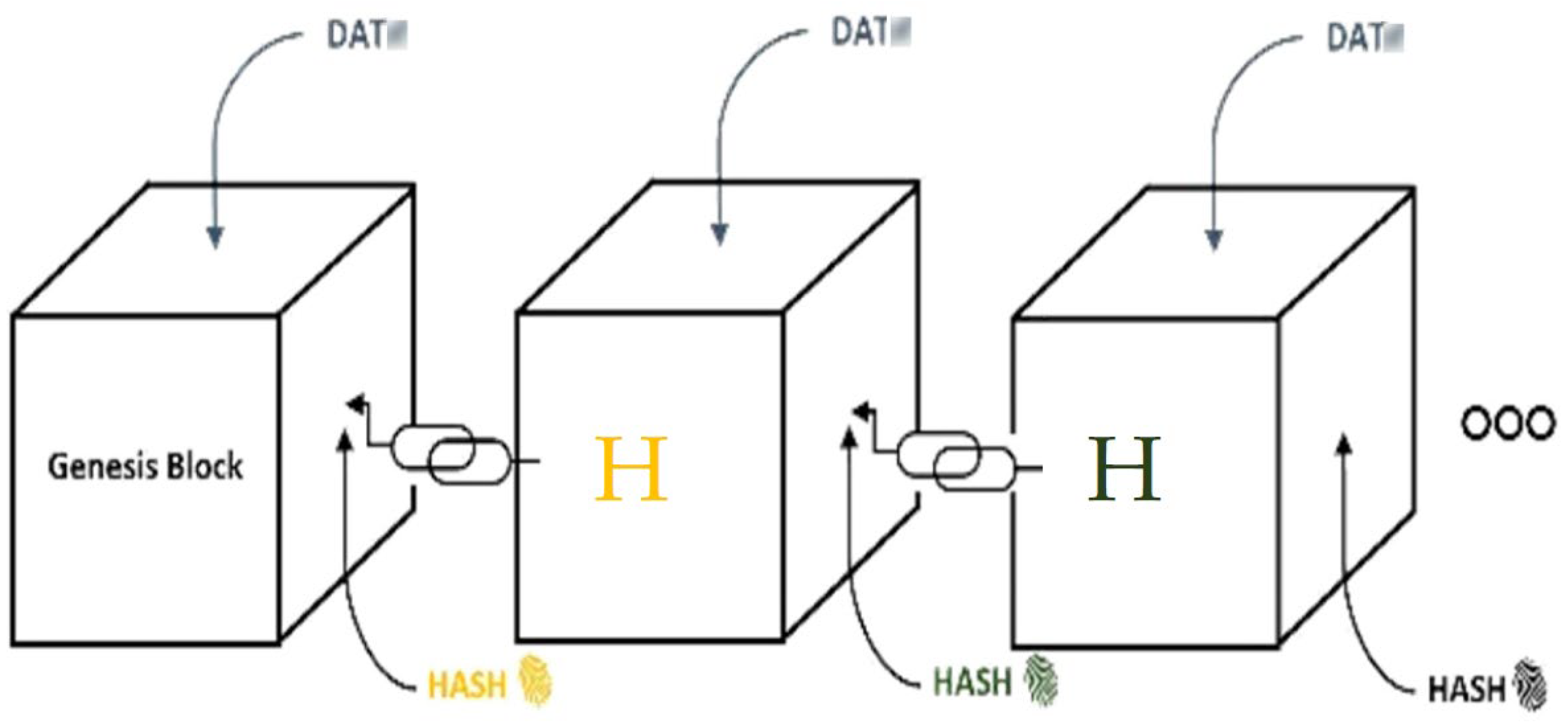
5.1. Proposed Model—Block Structure
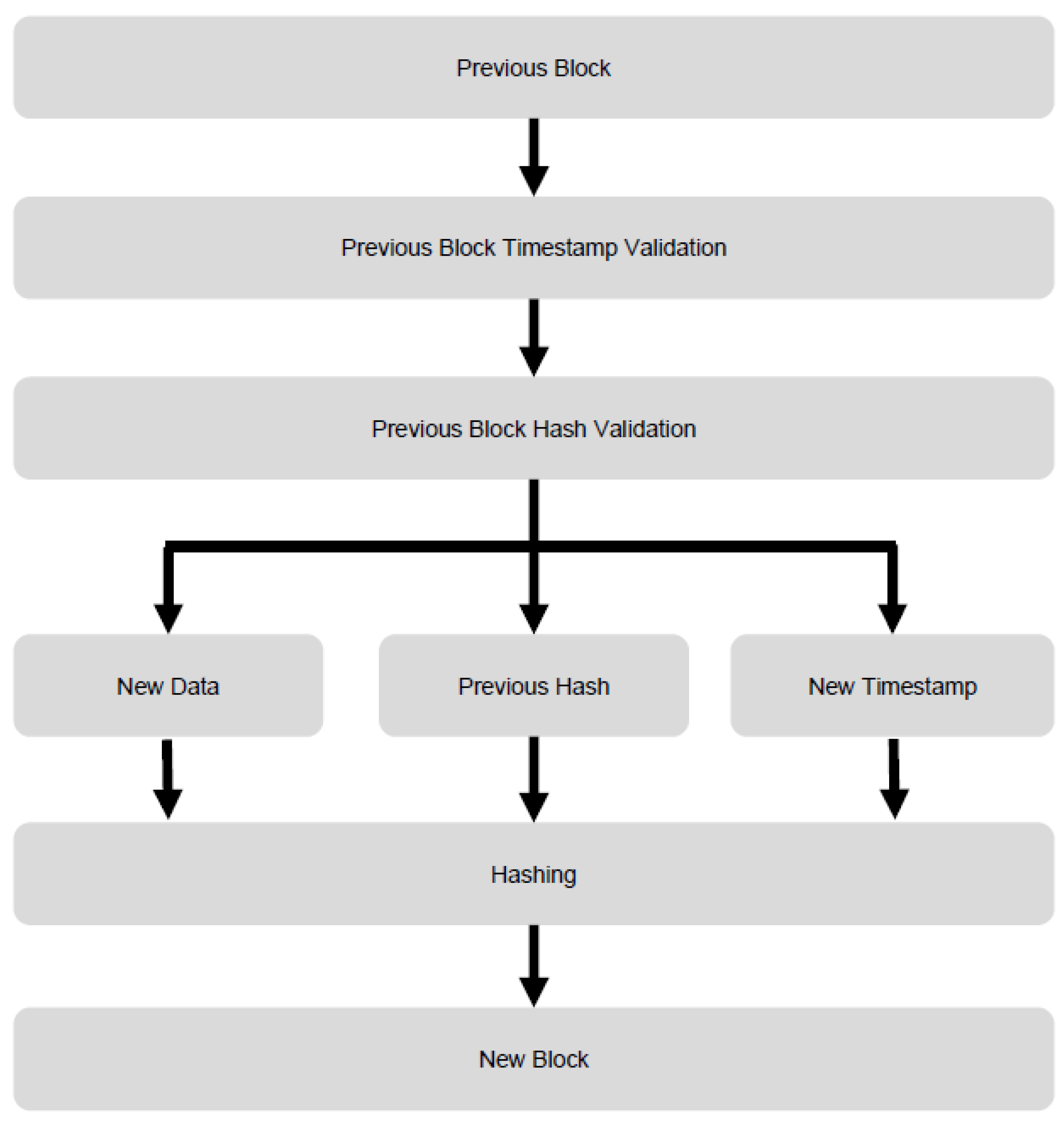
5.2. Proposed Model Implementation
- Ti: timestamp of the current block
- T(i − 1): timestamp of the previous block
- Block generation: when generating a new block, the protocol calculates the hash of the current block data (S), the new nonce (N) and the hash value of the previous block (H_(i − 1)).
- H(i): hash value of the current block (Block i)
- S: block data (PLC signals)
- N: nonce for the current block
- H(i − 1): hash value of the previous block (Block i − 1)
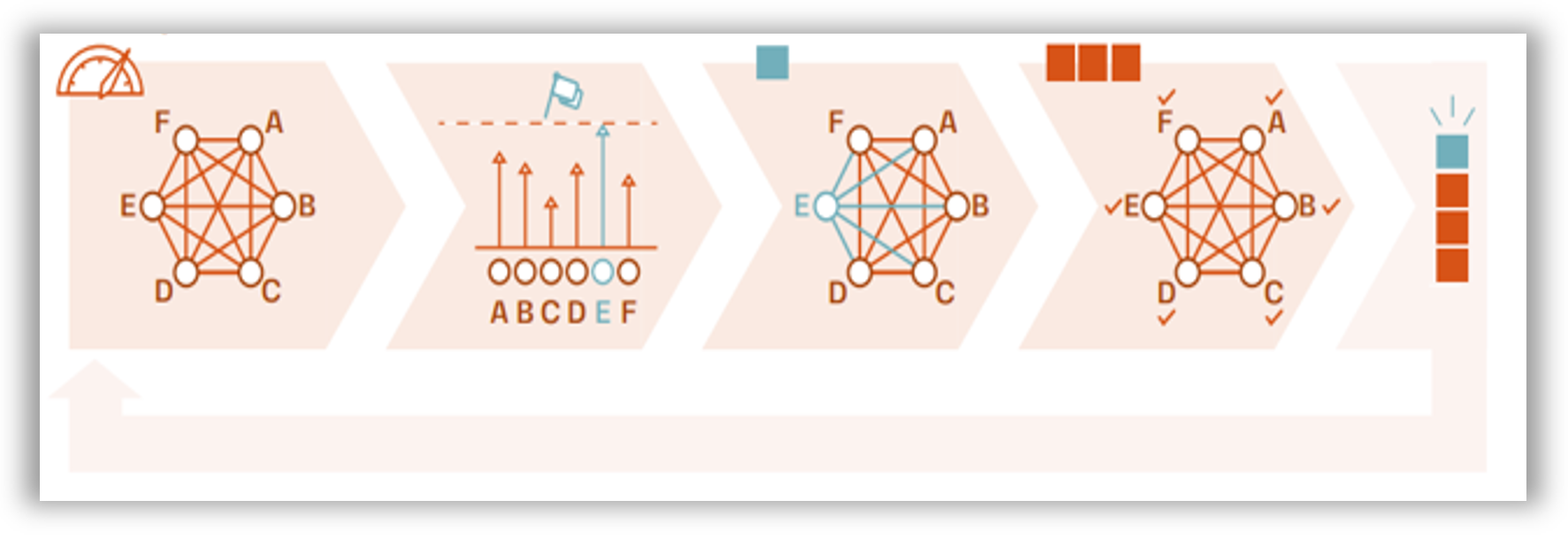
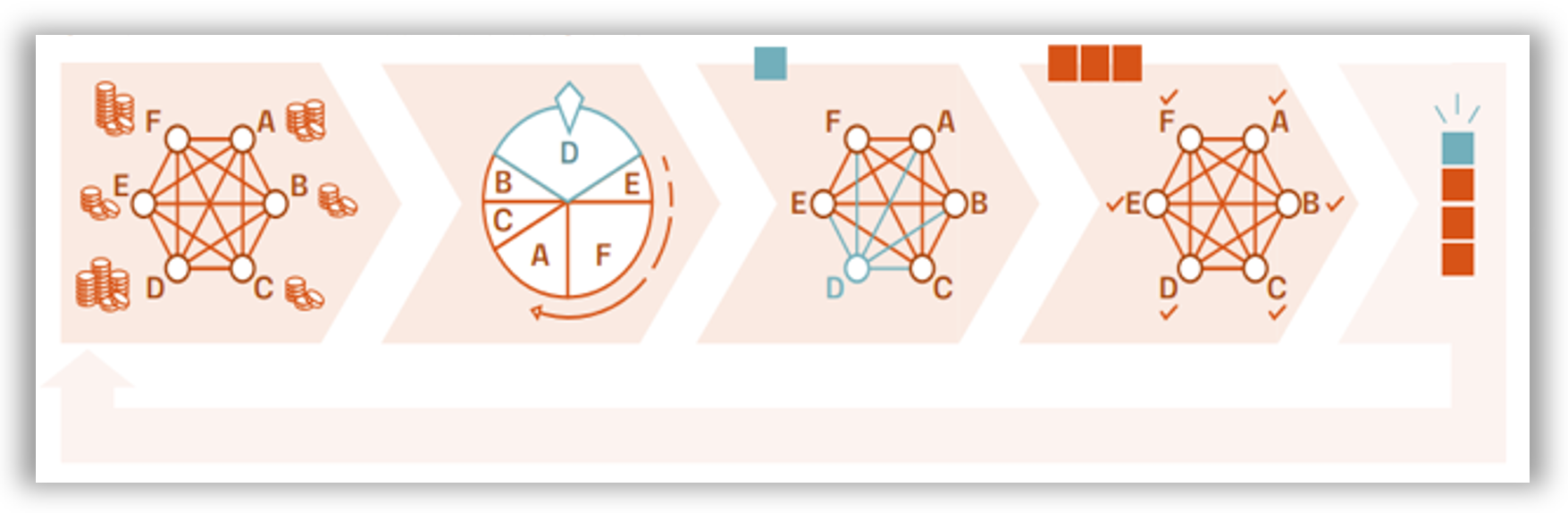
6. Performance Evaluation
6.1. System Parameters
6.2. Experimental Factors
6.3. Block Generation Speed
6.4. Simulation Procedure
7. Simulation Results
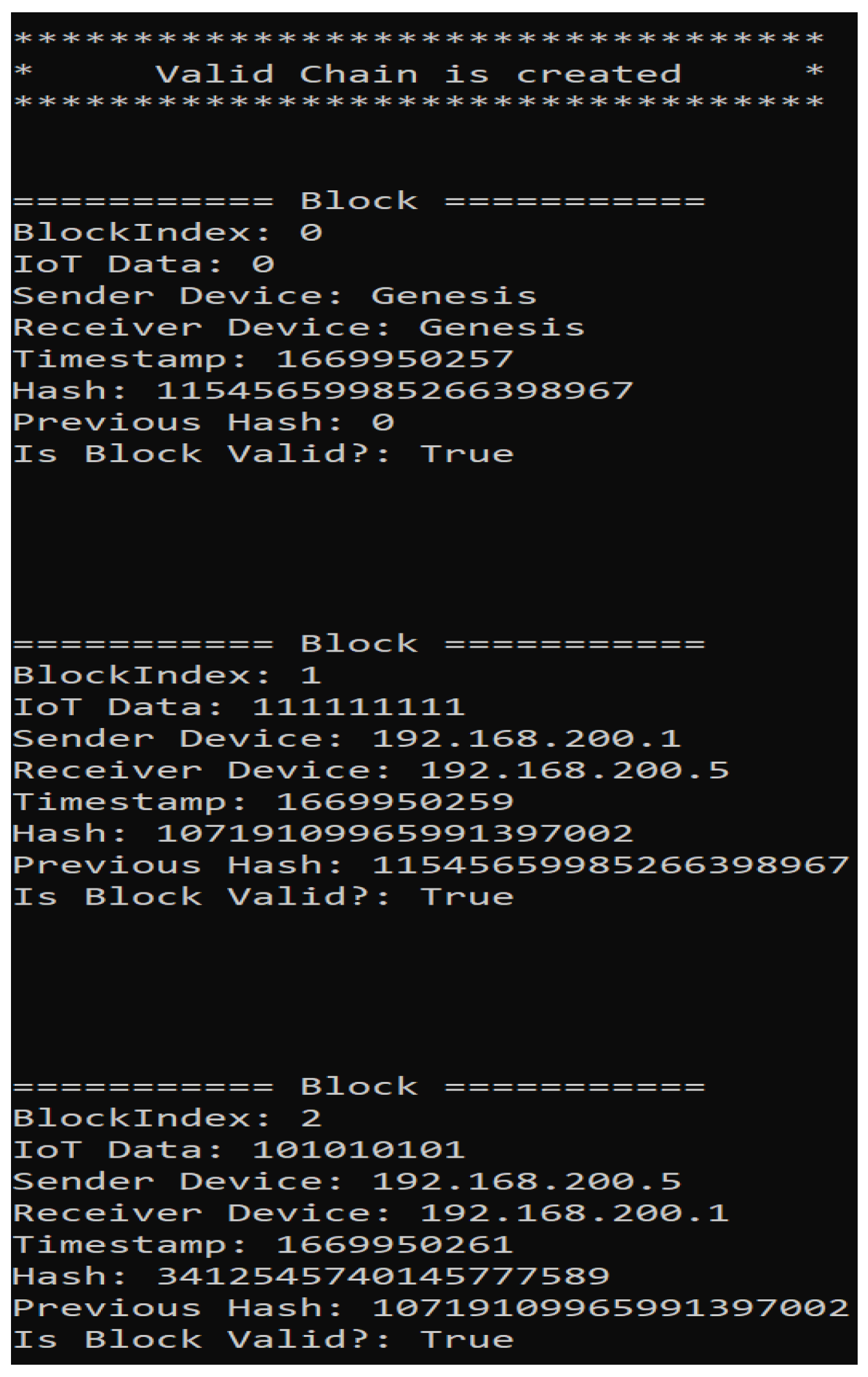
7.1. Valid Chain
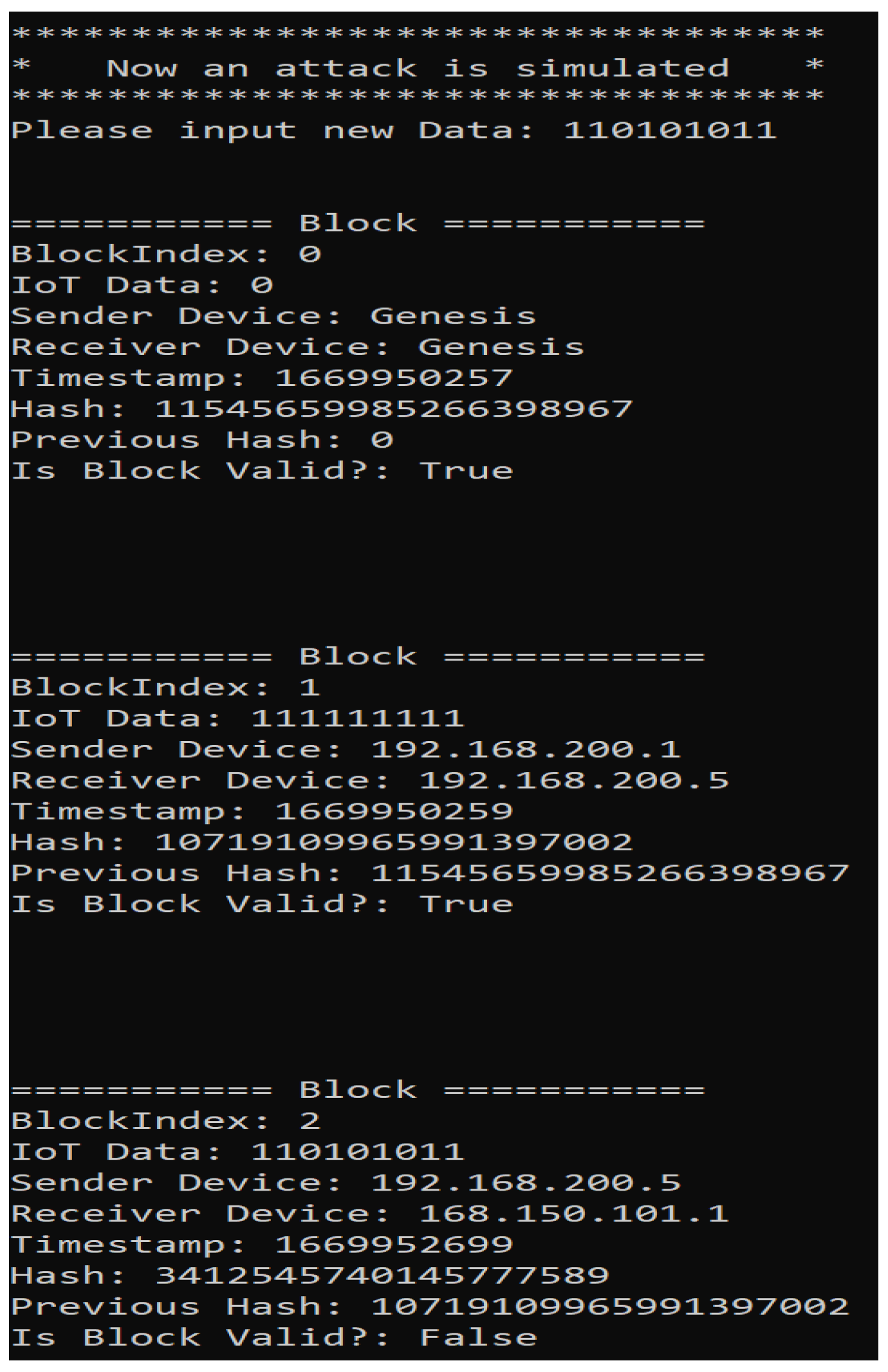
7.2. Corrupted Chain
- D_original = original data in the last block
- D_altered = altered data after the MIM attack
- ID_original = original sender device ID
- ID_altered = altered sender device ID
- V(D_original, ID_original) = valid (block remains unchanged)
- V(D_altered, ID_altered) = invalid (block detected as compromised)
7.3. Discussion and Comparative Analysis
8. Conclusions and Future Directions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kumar, N.M.; Mallick, P.K. Blockchain technology for security issues and challenges in IoT. Procedia Comput. Sci. 2018, 132, 1815–1823. [Google Scholar]
- Hung, M. Leading the IoT, Gartner Insights on How to Lead in a Connected World. 2017. Available online: https://www.securityweek.com/mirai-basedbotnet-launches-massive-ddos-attack-streaming-service (accessed on 12 November 2022).
- Lewis, T.; Liwen, W.; Safa, O.; Moayad, A.; Jalel Ben, O. Blockchain for managing heterogeneous internet of things: A perspective architecture. IEEE Netw. 2020, 34, 16–23. [Google Scholar]
- Ali, F.; Aloqaily, M.; Alfandi, O.; Ozkasap, O. Cyberphysical blockchain-enabled peer-to-peer energy trading. Computer 2020, 53, 56–65. [Google Scholar]
- Aloqaily, M.; Boukerche, A.; Bouachir, O.; Khalid, F.; Jangsher, S. An energy trade framework using smart contracts: Overview and challenges. IEEE Netw. 2020, 34, 119–125. [Google Scholar]
- Hassan, W.H. Current research on internet of things (IoT) security: A survey. Comput. Netw. 2019, 148, 283–294. [Google Scholar]
- Kushner, D. The Real Story of Stuxnet. 2013. Available online: https://spectrum.ieee.org/telecom/security/the-real-story-of-stuxnet (accessed on 20 December 2022).
- Arghire, I. Mirai-Based Botnet Launches Massive DDOS Attack on Streaming Service. 2019. Available online: https://www.securityweek.com/mirai-based-botnet-launches-massive-ddos-attack-streaming-service/ (accessed on 22 December 2022).
- Subramanian, H. Decentralized blockchain-based electronic marketplaces. Commun. ACM 2017, 61, 78–84. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar]
- Lee, I. The internet of things for enterprises: An ecosystem, architecture, and IoT service business model. Internet Things 2019, 7, 100078. [Google Scholar]
- Radoglou Grammatikis, P.; Sarigiannidis, P.; Moscholios, I. Securing the internet of things: Challenges, threats and solutions. Internet Things 2019, 5, 41–70. [Google Scholar]
- FIDO Alliance. How Fido Works. Available online: https://fidoalliance.org/howfido-works/ (accessed on 15 December 2022).
- Tewari, A.; Gupta, B. Security, privacy and trust of different layers in internet-of-things (IOTS) framework. Future Gener. Comput. Syst. 2018, 108, 909–920. [Google Scholar]
- Salman, T.; Zolanvari, M.; Erbad, A.; Jain, R.; Samaka, M. Security services using blockchains: A state of the art survey. IEEE Commun. Surv. Tutor. 2019, 21, 850–880. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: http://bitcoin.org/bitcoin.pdf (accessed on 13 December 2022).
- Antonopoulos, A.M. Mastering Bitcoin: Unlocking Digital Cryptocurrencies; O’Reilly Media Inc.: New York, NY, USA, 2014. [Google Scholar]
- Tschorsch, F.; Scheuermann, B. Bitcoin and beyond: A technical survey on decentralized digital currencies. IEEE Commun. Surv. Tutor. 2016, 18, 2084–2123. [Google Scholar]
- Ethereum Blockchain App Platform. 2017. Available online: www.ethereum.org/ (accessed on 22 December 2022).
- Andreas, C.; Johannes, P.; Nikolas, S. Eine Marktübersicht der Blockchain in der Energiewirtschaft. Von der Idee zum Geschäftsmodell, von der Technologie zur aktuellen Anwendung. 2020. Available online: https://d-nb.info/121815991X/34 (accessed on 15 December 2022).
- Khalilov, M.C.K.; Levi, A. A survey on anonymity and privacy in bitcoin-like digital cash systems. IEEE Commun. Surv. Tutor. 2018, 20, 2543–2585. [Google Scholar]
- Baraniuk, C. Bitfinex Users to Share 36% of Bitcoin Losses after Hack. BBC News. Available online: https://www.bbc.com/news/technology-37009319 (accessed on 20 October 2022).
- Saad, M.; Spaulding, J.; Njilla, L.; Kamhoua, C.; Shetty, S.; Nyang, D.; Mohaisen, A. Exploring the attack surface of blockchain: A systematic overview. arXiv 2019, arXiv:1904.03487. [Google Scholar]
- Hyperledger. 2017. Available online: https://www.hyperledger.org (accessed on 11 December 2022).
- Castro, M.; Liskov, B. Practical byzantine fault tolerance. OSDI 1999, 99, 173–186. [Google Scholar]
- Sachs, G. Blockchain’ Putting Theory into Practice. Available online: https://www.blockchain.com/ (accessed on 14 December 2022).
- Gu, J.; Sun, B.; Du, X.; Wang, J.; Zhuang, Y.; Wang, Z. Consortium blockchain based malware detection in mobile devices. IEEE Access 2018, 6, 12118–12128. [Google Scholar]
- Zhang, A.; Lin, X. Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. J. Med. Syst. 2018, 42, 140. [Google Scholar]
- Tao, F.; Wang, Y.; Zuo, Y.; Yang, H.; Zhang, M. Internet of things in product life-cycle energy management. J. Ind. Inf. Integr. 2016, 1, 26–39. [Google Scholar]
- Gaetani, E.; Aniello, L.; Baldoni, R.; Lombardi, F.; Margheri, A.; Sassone, V. Blockchain-based database to ensure data integrity in cloud computing environment. In Proceedings of the Italian Conference on Cybersecurity, Venice, Italy, 17–20 January 2017. [Google Scholar]
- Xie, S.; Zheng, Z.; Chen, W.; Wu, J.; Dai, H.N.; Imran, M. Blockchain for cloud exchange: A survey. Comput. Electr. Eng. 2020, 81, 106526. [Google Scholar] [CrossRef]
- Lee, B.; Lee, J.H. Blockchain-based secure firmware update for embedded devices in an internet of things environment. J. Supercomput. 2017, 73, 1152–1167. [Google Scholar]
- Boudguiga, A.; Bouzerna, N.; Granboulan, L.; Olivereau, A.; Quesnel, F.; Roger, A.; Sirdey, R. Towards better availability and accountability for IoT updates by means of a blockchain. In Proceedings of the IEEE European Symposium on Security and Privacy Workshops (EuroS and PW), Paris, France, 26–28 April 2017; pp. 50–58. [Google Scholar]
- Dukkipati, C.; Zhang, Y.; Cheng, L.C. Decentralized, blockchain based access control framework for the heterogeneous internet of things. In Proceedings of the Third ACM Workshop on Attribute-Based Access Control, Tempe, AZ, USA, 21 March 2018. [Google Scholar]
- Lone, A.H.; Naaz, R. Applicability of Blockchain smart contracts in securing Internet and IoT: A systematic literature review. Comput. Sci. Rev. 2021, 39, 100360. [Google Scholar]
- Maesa, D.D.F.; Mori, P.; Ricci, L. A blockchain based approach for the definition of auditable access control systems. Comput. Secur. 2019, 84, 93–119. [Google Scholar]
- Zhang, Y.; Yutaka, M.; Sasabe, M.; Kasahara, S. Attribute-based access control for smart cities: A smart-contract-driven framework. IEEE Internet Things J. 2020, 8, 6372–6384. [Google Scholar]
- Nakamura, Y.; Zhang, Y.; Sasabe, M.; Kasahara, S. Exploiting smart contracts for capability-based access control in the internet of things. Sensors 2020, 20, 1793. [Google Scholar]
- Abdi, A.I.; Eassa, F.E.; Jambi, K.; Almarhabi, K.; Khemakhem, M.; Basuhail, A.; Yamin, M. Hierarchical blockchain-based multi-chaincode access control for securing IoT systems. Electronics 2022, 11, 711. [Google Scholar]
- Si, H.; Sun, C.; Li, Y.; Qiao, H.; Shi, L. IoT information sharing security mechanism based on blockchain technology. Future Gener. Comput. Syst. 2019, 101, 1028–1040. [Google Scholar] [CrossRef]
- Jia, B.; Zhang, X.; Liu, J.; Zhang, Y.; Huang, K.; Liang, Y. Blockchain-enabled federated learning data protection aggregation scheme with differential privacy and homomorphic encryption in IIoT. IEEE Trans. Ind. Inform. 2021, 18, 4049–4058. [Google Scholar]
- Alzubi, J.A. Blockchain-based Lamport Merkle digital signature: Authentication tool in IoT healthcare. Comput. Commun. 2021, 170, 200–208. [Google Scholar] [CrossRef]
- Cha, J.; Singh, S.K.; Kim, T.W.; Park, J.H. Blockchain-empowered cloud architecture based on secret sharing for smart city. J. Inf. Secur. Appl. 2021, 57, 102686. [Google Scholar]
- Sheron, P.F.; Sridhar, K.P.; Baskar, S.; Shakeel, P.M. A decentralized scalable security framework for end-to-end authentication of future IoT communication. Trans. Emerg. Telecommun. Technol. 2020, 31, e3815. [Google Scholar]
- Chen, Y.; Li, M.; Zhu, X.; Fang, K.; Ren, Q.; Guo, T.; Chen, X.; Li, C.; Zou, Z.; Deng, Y. An improved algorithm for practical byzantine fault tolerance to large-scale consortium chain. Inf. Process. Manag. 2022, 59, 102884. [Google Scholar]
- SHA 256 Algorithm Explained by a Cyber Security Consultant. Available online: https://sectigostore.com/blog/sha-256-algorithm-explained-by-a-cyber-security-consultant/ (accessed on 20 December 2022).
- He, K.; Chen, J.; Zhou, Q.; Du, R.; Xiang, Y. Secure dynamic searchable symmetric encryption with constant client storage cost. IEEE Trans. Inf. Forensics Secur. 2020, 16, 1538–1549. [Google Scholar]
- Yao, Z.; Tan, L.; She, K. 5G-BSS: 5G-Based Universal Blockchain Smart Sensors. Sensors 2022, 22, 4607. [Google Scholar]
- Farahmandi, F.; Huang, Y.; Mishra, P. System-on-Chip Security: Validation and Verification; Springer: Cham, Switzerland, 2020. [Google Scholar]
- Franco, C.; Walter, C.; Marco, R. Man-in-the-Middle Attack to the HTTPS Protocol. IEEE Secur. Priv. Mag. 2009, 7, 78–81. [Google Scholar]
- Yeh, T.Y.; Kashef, R. Trust-Based collaborative filtering recommendation systems on the blockchain. Adv. Internet Things 2020, 10, 37–56. [Google Scholar]
- Jebamikyous, H.; Li, M.; Suhas, Y.; Kashef, R. Leveraging machine learning and blockchain in E-commerce and beyond: Benefits, models, and application. Discov. Artif. Intell. 2023, 3, 3. [Google Scholar]
- Saleminezhadl, A.; Remmele, M.; Chaudhari, R.; Kashef, R. IoT Analytics and Blockchain. arXiv 2021, arXiv:2112.13430. [Google Scholar]

| Paper | Method | Limitations | Strengths |
|---|---|---|---|
| Lee et al. [32] | Blockchain-based secure firmware update for embedded devices | Lack of real-world deployment evaluation | Enhances security of firmware updates for embedded IoT devices |
| Boudguiga et al. [33] | Accountability for IoT updates by means of a blockchain | Limited discussion on scalability and performance considerations | Improves availability and accountability of IoT updates through blockchain |
| Dukkipati et al. [34] | Blockchain-based access control framework for the heterogeneous IoT | Need for efficient mechanisms to handle a large number of access control transactions | Provides a decentralized and secure access control framework for IoT |
| Lone et al. [35] | Applicability of blockchain smart contracts in securing Internet | Systematic literature review without specific experiments | Highlights the use of smart contracts for securing Internet and IoT |
| Maesa et al. [36] | Blockchain-based for auditable access control systems | Lacks discussion of scalability and performance aspects | Provides auditable access control system using blockchain |
| Zhang et al. [37] | A smart-contract-driven framework | Limited discussion of scalability and performance | Utilizes smart contracts for secure access control |
| Nakamura et al. [38] | Exploiting smart contracts for capability-based IoT access control | Need for further evaluation in real-world IoT environments | Leverages smart contracts for capability-based access control in IoT |
| Abdi et al. [39] | Hierarchical blockchain-based multi-chaincode access | No specific experimental evaluation; the need for further assessment of IoT | Presents a hierarchical access control framework for securing IoT |
| Si et al. [40] | IoT information-sharing security mechanism based on blockchain | Inefficient storage and processing of blockchain in resource-constrained IoT | Provides a secure mechanism for IoT information sharing using blockchain |
| Jia et al. [41] | Blockchain-enabled federated learning data protection aggregation | Need for further evaluation in real-world IoT environments | Ensures data protection in federated learning using blockchain |
| Alzubi [42] | Blockchain-based Lamport Merkle digital signature: | Limited discussion of scalability and performance considerations | Presents a blockchain-based authentication tool for IoT healthcare |
| Cha et al. [43] | Blockchain-empowered cloud architecture based on secret sharing | No specific experimental evaluation; lack of real-world deployment evaluation | Proposes a blockchain-based cloud architecture for smart cities |
| Sheron et al. [44] | Decentralized scalable security framework for end-to-end authentication communication | Scalability challenges of blockchain networks | Provides a decentralized security framework for IoT communication |
| Chen et al. [45] | Improved algorithm for practical Byzantine fault tolerance to large-scale consortium chain | Focuses on Byzantine fault tolerance, not specific to IoT; need for further evaluation in real-world IoT consortium chain scenarios | Presents an improved algorithm for practical Byzantine fault tolerance |
| Corusa et al. [20] | Marktübersicht der Blockchain in der Energiewirtschaft | Market overview, not specific to IoT; limited discussion of technical limitations and challenges | Provides a market overview of blockchain in the energy industry |
| Symmetric Encryption | Security Chip | PKI and Digital Certificate | IoTBChain | |
|---|---|---|---|---|
| Security | 0 | ++ | ++ | ++ |
| Speed | 0 | − | −− | − |
| Processing consumption | 0 | − | −− | − |
| Additional hardware | 0 | −− | ++ | ++ |
| Transfer limit | 0 | 0 | 0 | − |
| Total score | 0 | −− | 0 | + |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Schmid, P.; Schaffhäuser, A.; Kashef, R. IoTBChain: Adopting Blockchain Technology to Increase PLC Resilience in an IoT Environment. Information 2023, 14, 437. https://doi.org/10.3390/info14080437
Schmid P, Schaffhäuser A, Kashef R. IoTBChain: Adopting Blockchain Technology to Increase PLC Resilience in an IoT Environment. Information. 2023; 14(8):437. https://doi.org/10.3390/info14080437
Chicago/Turabian StyleSchmid, Philipp, Alisa Schaffhäuser, and Rasha Kashef. 2023. "IoTBChain: Adopting Blockchain Technology to Increase PLC Resilience in an IoT Environment" Information 14, no. 8: 437. https://doi.org/10.3390/info14080437
APA StyleSchmid, P., Schaffhäuser, A., & Kashef, R. (2023). IoTBChain: Adopting Blockchain Technology to Increase PLC Resilience in an IoT Environment. Information, 14(8), 437. https://doi.org/10.3390/info14080437







