Abstract
Edge–fog computing and IoT have the ability to revolutionize businesses across all sectors and functions, from customer engagement to manufacturing, which is what makes them so fascinating and emerging. On the basis of research methodology by Webster and Watson (2020), 124 peer-reviewed articles were discussed. According to the literature, these technologies lead to reduced latency, costs, bandwidth, and disruption, but at the same time, they improved response time, compliance, security and greater autonomy. The results of this review revealed the open issues and topics which call for further research/examination in order for edge–fog computing to unveil new business value streams along with IoT capabilities for the organizations. Only by adopting and implementing precisely these revolutionary will new solutions organizations succeed in the digital transformation of the modern era. Despite the fact that they are cutting-edge solutions to business operations and knowledge creation, there are still practical implementation issues to be dealt with and a lack of experience in the strategic integration of the variable architectures, which hinder efforts to generate business value.
1. Introduction
The emergence of an intelligent society and the ongoing increase in societal demands have affected a variety of businesses and people’s everyday lives. The use of edge devices has impacted every element of society, including intelligent manufacturing, smart homes, autonomous vehicles, intelligent robots, etc. The outcome is a significant growth in the number of devices linked to the Internet. As it incorporates physical things into the networked society, the Internet of Things (IoT) is one of the most disruptive technologies presently available [1,2]. Sensors and actuators integration to “things” has been linked to exponential growth and great economic possibilities. As mentioned in [3], forecasts and reports show that by 2025, it is anticipated that there will be over 40 billion connected devices worldwide, with a related economic potential up to 1 trillion USD annually (with a growth rate more than 20 percent every year).
Data are the primary commodity in this new information technology era, and having more data often creates bigger value in firms that are data driven. Moving massive data from IoT devices to the cloud may not be effective or, in some situations, may even be impossible, owing to bandwidth limitations due to the data velocity and volume increase. However, as time-sensitive and location-aware applications (such as real-time manufacturing, cognitive assistance, patient monitoring, self-driving cars, or flocks of drones) become more prevalent, the distant cloud will not be able to scale to meet their data production needs or meet their ultra-low latency requirements [4]. Additionally, due to privacy concerns in certain applications, transmitting the data to the cloud might not be a viable option. There is a fundamental requirement for computing paradigms that occur closer to the connected devices in order to resolve the problems of high-bandwidth, geographically scattered, ultra-low latency, and privacy-sensitive applications. In order to address the aforementioned problems and to satisfy the demand for the foretold paradigms, both industry and academics commend to edge–fog computing [4,5,6]. By providing computing, networking, storage, and data management on network nodes in close proximity to IoT devices, edge–fog computing fills the gap between the cloud and IoT devices. Consequently, as data travel from IoT devices to the cloud, computing, storage, networking, decision making, and data management take place along the way [7].
IoT-related profits continue to be far lower than anticipated despite its significant value potential [3]. This gap is explained by Bilgeri and Wortmann [8] using 16 barriers to IoT business model innovation, including industrialization and the ensuing requirement for IoT solution value assessments. IoT solutions link tangible goods with digital services, shifting value generation to the latter and benefiting several stakeholders directly and indirectly [9,10,11,12]. Nonetheless, IoT solutions are employed in a wide range of process activities, such as process improvement or monitoring [13,14], in addition to numerous products and services. IoT solutions have substantial and ongoing development expenses but almost no costs for replication, distribution, and individual usage, which sets them apart from conventional physical products in a number of ways [15]. Therefore, IoT solutions must be submitted with a value assessment and business models that go beyond those used to evaluate traditional products, which frequently place more emphasis on one-time production costs than the true value generated [16,17].
Despite the fact that recent Information Systems (IS) research has produced a mature theoretical background on the business value of IT with regard to organizational effectiveness and competitive advantage [3,18], there is likewise agreement in the literature that value assessment of IoT solutions is essential [8,19]. For the cloud-, edge-, and fog computing-based IoT, a variety of survey approaches have been put out. However, as [8] notes, the value attributes of IoT solutions are currently not adequately identified, despite the fact that efficient commercialization requires a solid theoretical knowledge of the value provided by IoT solutions.
Earlier researchers on edge–fog computing, in particular, have focused their attention on the following topics: infrastructure and platform requirements; architecture benefits; use cases and applications; challenges, open issues, and opportunities; evaluation criteria; resource management and service allocation; as well as, IoT–edge–fog computing integration [7,20,21,22,23,24,25,26,27,28,29,30,31,32]. Two recent studies on edge–fog computing [4,7] provide a broad summary of the latest ongoing research projects and the long-term goals associated with them, covering all the points of interest, the pros and cons among with the limitations of most of these aforementioned work. However, neither these complete studies nor the cited surveys include in their findings and learned lessons a business aspect evaluation of these technologies, to highlight their potential value in promotion of their strategic implementation.
On the other hand, prior IoT research has mostly emphasized on the IoT’s technological components [6,33]. Additionally, previous studies have examined the IoT’s potential for integrating intelligent interfaces into the information network [33,34], increasing resource efficiency [35], and optimizing production mechanisms, services, and decision-making procedures [1,36]. Moreover, there are just a few contributions that map the business value of IoT or identify the factors that create value in IoT solutions [3,7,19,37,38]. Advanced domains of application, including data-driven monitoring, control, and predictive applications for enhanced transparency, problem prediction, and the creation of efficient countermeasures, have become available as a result of the introduction of IoT solutions in the industrial setting. Reviewing the cited literature, IoT has been proven to enable greater process flexibility, quality, and efficiency, which has resulted in improvements to overall performance and a decrease in unproductive activities among businesses. The advantages of IoT solutions go beyond process improvements, since they also present cutting-edge options for physical product customization or automation. According to Whitmore et al. [39] though, IoT is not adequately portrayed in management literature, and we still understand very little about how the IoT affects value creation, value streams, and value capturing from a business perspective.
Meanwhile, due to the nature of innovative business potential, parties engaged, customer needs, the changing business environment, and associated risks, evaluating and selecting from the various strategic options may be difficult [40]. Every organization uses a variety of procedures and operations to generate value [41,42]. The traditional approach often primarily emphasizes the company’s contribution to value creation, while the emerging stance additionally values the importance of customers and other business associates as equally important stakeholders [40]. The lifecycle value and business gains of collaborative solutions must be taken into account in a way that encompasses relationships, exchanges, and interactions between parties because the concept of value creation varies from different viewpoints and for multiple parties [41]. Realizing the potential for collaboration in value creation is crucial in this situation. Identifying how business models of different organizations might interact and locating a middle ground and win–win scenario in the value chain are the challenges at hand [2,40]. In the capital-intensive market, there continues to be comparatively limited innovation in joint proposal development.
Offering precise compositions for IoT optimization and strategic implementation with future networks, such as edge–fog computing, 5G networks, and further on, remains a significant task in addition to the numerous technical studies around the new technological innovations, that acted as the motivation for this report. The previous literature does not give a thorough overview of the different stages, problems, drivers, and enablers required for value generation through edge and fog computing and IoT; instead, it only addresses a part of the issue or focuses on a small number of use cases. Consequently, a roadmap for the IoT–edge–fog business value must include clearly defined phases, streams and explanations of each of these components. It is not difficult to comprehend the rationale behind edge and fog computing’s efforts to treat the pursuit of value as a matter of the utmost importance. [37,43,44,45,46,47,48].
As a result, the purpose of this paper is to highlight key aspects of the contribution of edge and fog computing to various viewpoints on the business value realized through IoT, and to address this noticeable research gap in the foretold link. In total, 124 sources were examined after being analyzed through the lens of the Webster and Watson methodology [49]. Companies all over the world face the challenging implementation of IoT, which is constantly evolving and necessitates special attention to all of its various value axes. As the IoT moves from conventional architectures to the revolutionary edge and fog computing, it is essential to keep a record of the current state of research on the business value generated through IoT at this time.
The present work is organized as follows: Section 2 describes the methodology that was utilized in order to carry out the literature review. Section 3. This section contains a discussion of the outcomes that were obtained from the analysis of the articles. Finally, Section 4 summarizes the findings of the research, presents the limitations, pronounces implications of this work, and concludes by inviting the scientific community to study in more detail the issues and relationships described in this conceptual model.
2. Methodology and Data
We conducted our research in accordance with the methodology of Webster and Watson’s [49] systematic literature review. It is a process that takes place in three stages: (1) An analysis of the most recent literature reviews was performed in order to locate databases and keywords. (2) After this, a comprehensive backward search was conducted to investigate citations, and a forward search was conducted to identify citations of the articles that had been chosen. (3) At the end of the process, all of the articles were categorized by concept, according to the content of each one, and potential research opportunities were found.
2.1. Prior Literature Reviews
To the best of our knowledge, no recent literature review has specifically discussed how edge and fog computing opens new potential in the business value of IoT. Rather, these reviews have investigated the phenomenon by investigating a wide range of factors that can affect this relationship. Existing literature reviews, on the other hand, place a greater emphasis on mapping the business value of IoT; a systematic review of the benefits and risks of IoT adoption (which uses Webster and Watson methodology); a comprehensive survey on sustainable edge computing development and a comprehensive survey on fog computing which provides the state of the art and research challenges of this technological field. All of these reviews are presented below (Table 1).

Table 1.
Prior literature reviews.
Data analytics, predicting, process management, intelligent manufacturing, planning and scheduling, visualization, and data security are the seven strategic key elements that Rajnoha and Hadac [44] identify as driving forces for higher value in the context of IoT intelligent manufacturing. The context of these elements in Industry 4.0 is currently being studied and will need to be further utilized. These seven strategic essential components and their correlation to the implementation of recent technologies and methods in IoT manufacturing can lead to higher levels of stability, productivity, and growth, which in turn can create higher levels of business value and a competitive advantage. However, this work does not provide any analysis on edge–fog computing solutions.
A systematic literature review was carried out by Brous and Janssen [45], based on the methodology developed by Watson and Webster [49], which provided an overview of the potential benefits and risks of IoT as well as insight into the duality of IoT. In particular, they present in depth (a) the benefits of adopting IoT within organizations, categorizing them as follows: automation of decision making, reduction in operational costs, etc., (b) the six organizational conditions of the IoT, which include the implementation of a data quality framework, data governance, the development of technical skills, etc., and (c) the organizational consequences, which include structural changes to data management departments, procurement policies, business processes, and strategy, among other things. Nevertheless, despite the fact that this study is focused on the strategic implementation of IoT, it also does not rely on or present any cited literature based on edge–fog computing.
Using a reference architecture model for edge computing, Hamm, Willner, and Schieferdecker [46] analyzed current initiatives by using explorative content analysis. Their work resulted in two major contributions to the field of study. First, they gave a presentation that characterized how current initiatives are, and second, they proposed a roadmap for sustainable edge computing by relating three dimensions of sustainable development to four cross-concerns of edge computing. Their research reveals that the majority of initiatives take the form of internationally coordinated software development projects; the telecom and industrial sectors are currently important branches; and the network virtualization layer is the topic that receives the most attention. The roadmap reveals a wide variety of opportunities and dangers associated with edge computing in relation to sustainable development. These include the utilization of renewable energy sources; biases; new business models; increases and decreases in energy consumption; responsiveness; monitoring; and traceability. However, no connection of further suggestion is made between this work and the potential value generation that is being studied around edge computing.
Mouradian et al. [23] present a comprehensive survey on fog computing. In it, they critically review the state of the art, and they identify related concepts and highlight the differences between them. They begin by introducing illustrative use cases that cover two distinct application domains, namely, the Internet of Things and Content Delivery Network, and then use these use cases as a foundation to derive a set of evaluation criteria for fog systems. They discuss the architectures as well as the algorithms that are used to make fog systems, and they provide insights regarding the challenges and research directions for this topic. In conclusion, they discuss the prospects in terms of the significant role that fog is likely to play in developing technologies such as the tactile Internet. Although the authors included several significant principles, the study is lacking other crucial elements, such as security and privacy.
2.2. Article Selection
The articles were retrieved from the Scopus, Science Direct and Web of Science databases by using a combination of the keywords Internet of Things (IoT), Industry 4.0, fog computing, edge computing, business value, and business strategy in the title, keyword, and abstract fields of the search queries. Each article was published in a journal that had been reviewed by other researchers or in the proceedings of a conference. Regarding the year of publication, there were no limitations imposed.
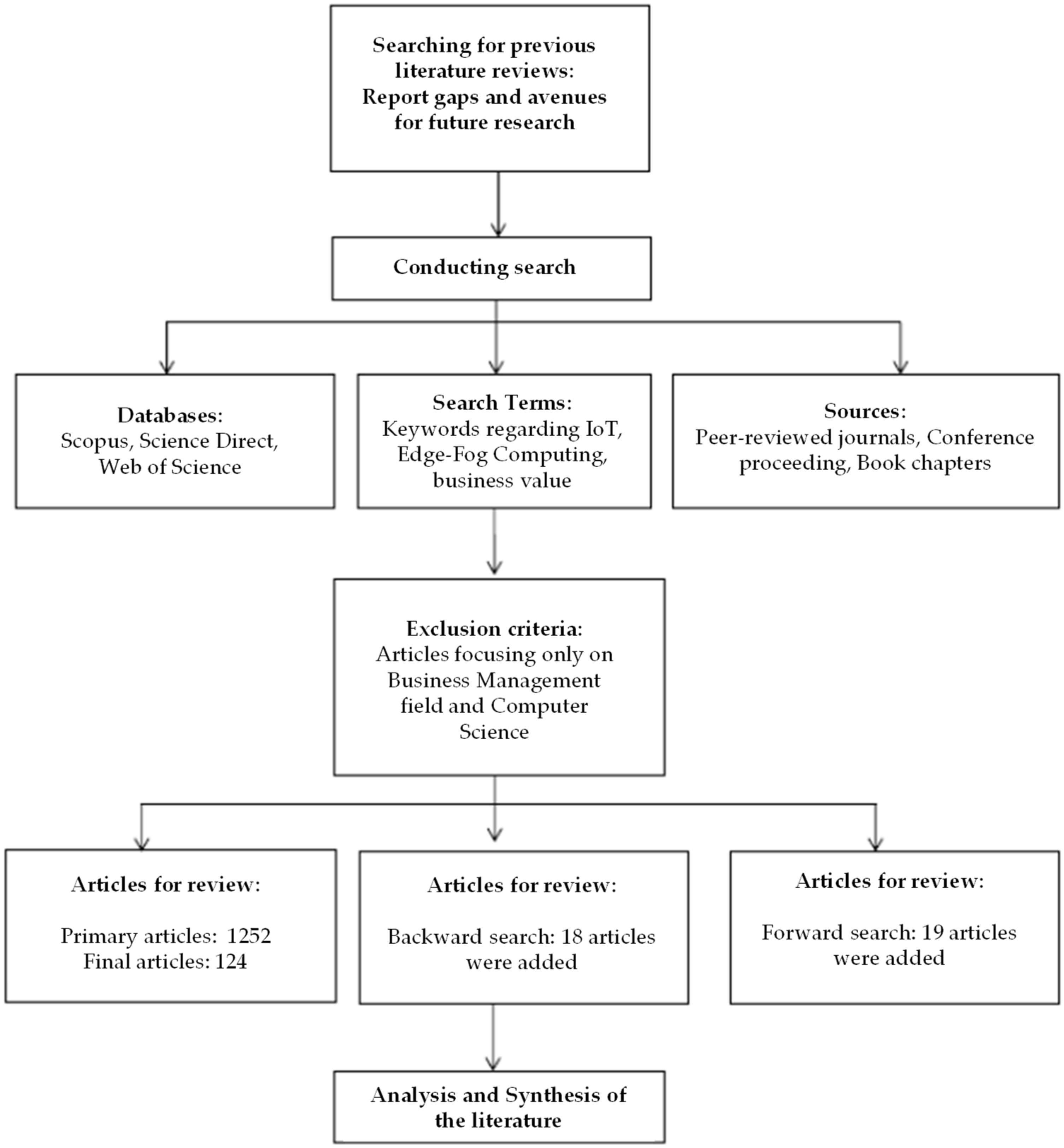
The search for the aforementioned keywords resulted in the collection of a total of 1252 articles. Following the application of the language, source, and category restrictions, there were a total of 810 articles remaining. After reviewing the contents of the remaining articles, we decided not to include 453 articles because of their titles, 177 articles because of their abstracts, and 89 articles because of their actual content. After that, four duplicate articles were eliminated, bringing the total number of articles down to 87. In addition to these, 19 articles were added as a result of the forward search, and 18 articles were added as a result of the backward search. This resulted in 124 articles being available for examination (Figure 1).
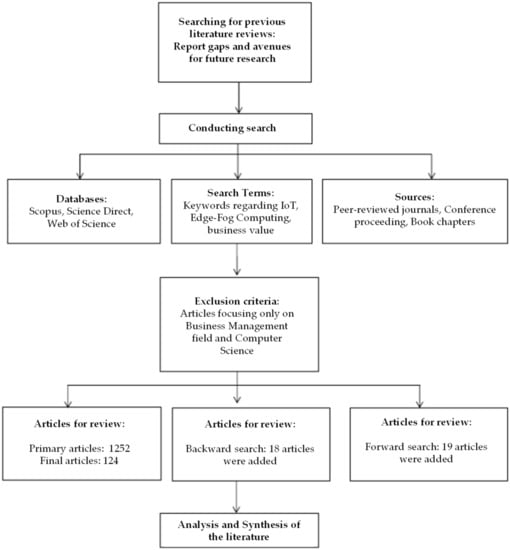
Figure 1.
Article selection process.
When recurring articles for the various keyword combinations were discovered, the search was completed. As a result, the appropriate quantity of articles had been acquired [49]. The final sample was analyzed using an Excel data extraction sheet in which the main outcomes and contributions for each publication were assembled along with the illustrative elements.
2.3. Classification Framework
A classification framework was applied to the investigation of one hundred twenty-four articles. All of the articles were organized into three overarching concepts, which are as follows: 1. edge and fog computing as value drivers of IoT; 2. challenges and resolutions to value generation; 3. value levers and streams. These concepts will assist future researchers and academics in expanding the associated research body by offering more information in this area and will deliver a better insight into the role of edge–fog computing in the business value achieved through IoT.
3. Results
3.1. Edge and Fog Computing as Value Drivers of IoT
We begin our study by describing both edge and fog computing from several viewpoints in order to address the confusion regarding the distinction between the two types of Computing. In the same way that fog and edge analytics bring useful insights closer to users, fog and edge computing processes data in close proximity to the source of the data [6,7,8,9,50,51,52,53,54]. It is no longer necessary to upload all of one’s data into the cloud in order to process it; instead, data can now be processed in close proximity to the location where it was originally created. This suggests that not all of the data produced by sensors should be considered significant. Edge analytics thus seeks to distinguish between important and irrelevant knowledge. Thus, some networks can save storage space and bandwidth by not transferring all of their data to the cloud [1], such as the facial recognition or movement detection algorithms running on the fog/edge layer. Fog–edge computing will therefore constitute the ideal choice for applications that need impermanent storage. Additionally, the fog–edge paradigm can have an impact in the IoT and wireless sensor networks of the future when they integrate heterogeneous devices and protocols to improve services [55].
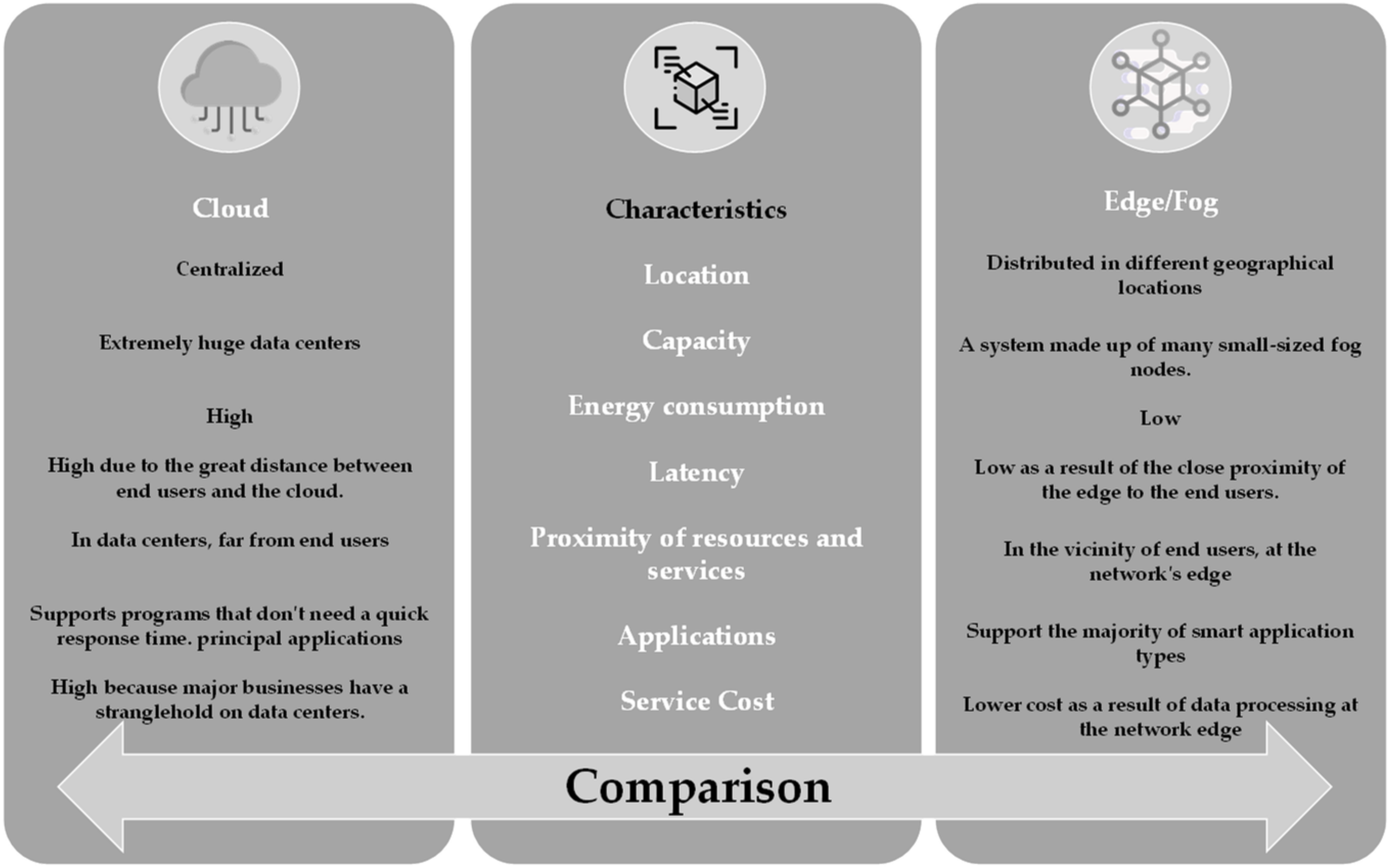
Edge computing and fog computing are defined by some academics as the same (similar or identical) concepts with just slight nomenclature differences [50], while many distinguish them as two distinct conceptions. Some of the differences between the key characteristics of Cloud and edge–fog computing are presented below at Figure 2. Edge computing focuses on data processing at the edge of a network, whereas fog computing is located between the cloud and the edge cloud and therefore includes the edge. This is according to Goscinski et al. [56], who state that fog computing incorporates the edge. Contrarily, fog computing, according to Chiang et al. [57], is a throughout architecture that allocates computing, control, storage, and networking functions nearer to end users along the cloud-to-things continuum, whereas the edge refers to the edge network, which includes devices such as edge routers, house gateways, and base stations. Moreover, according to Pan et al. [58], fog computing is the foundation of the IoT in which cloud computing and other services are extended to gadgets such as routers, switches, etc. According to the core-edge topology, edge computing moves data, services, and applications from the core to the network edge [4,22,59]. Examples of edge computing applications include cloud offloading, smart cities, smart homes, and video analytics.
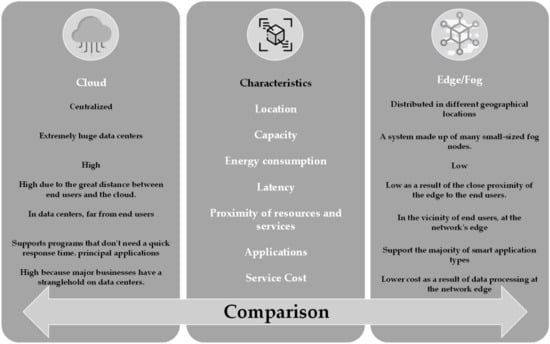
Figure 2.
Illustrates the primary differences between cloud computing and edge–fog computing.
In essence, edge computing and fog computing share the similar research interests and mutually attempt to decentralize data processing from the cloud to the edge of the network. The following key elements are found in the fog/edge layer, which is typically situated between the cloud and the end users [50,60,61]: (a) Authentication and Authorization: identification of the regulations and policies for access control; (b) Offloading Management: outlines the different types of information that are offloaded, the partitions used for offloading, and how to create the best offloading scheme; (c) Location Services: that frequently learns the mobility model by relating the network to the physical spots; (d) System Monitor: to give the other components various information such as use, workload, and energy; (e) Resource Management, which is in charge of resource allocation, dynamic joining and departing of the fog node, resource maintenance, and resource provisioning; (f) VM Scheduling: This program tries to give users an ideal method for scheduling virtual machines. Fog computing operates its services across multiple layers, in contrast to edge computing, which operates its services in a single logical location [62]. Fog computing generally has more devices than edge computing, which is typically limited to a lesser number of peripherals [63].
Numerous billions or trillions of devices could be connected by the IoT [64]. As previously stated, these devices collectively produce enormous amounts of data [65]. Additionally, due to the limited resources of IoT devices, which are unable to perform computation and processing locally, energy consumption is a significant problem in wireless communication for new-generation applications that need quick response times, such video streaming, etc. [65,66]. Therefore, by offering storage, compute, and networking resources in data centers owned by big corporations such as Google, the centralized design does not satisfy the criteria of IoT application development. Additionally, the processing of the generated and processed data requires transferring it to the cloud. This requires a lengthy response time and has the potential to affect both the quality of the experience that the end user has and the overall experience. The IoT and cloud are two key technologies that improve our day-to-day lives by providing users of IoT with a variety of different services. This allows us to combine them into a single, worldwide technology known as the Cloud-IoT paradigm [7,67]. In an effort to integrate the cloud and the IoT, Botta et al. [68] allowed the cloud to offer IoT devices the necessary services, such as computation and storage. Along these same lines, Neagu et al. [51] proposed the idea of a health monitoring service that they called the HM-oriented Sensing Service scenario. This service would provide expansive medical facilities that were built on Cloud-IoT architecture. Ismail et al. [52] conducted research to determine how effective a task-scheduling algorithm and a virtual machine placement algorithm in the Cloud-IoT architecture were in reducing the amount of power required by data centers. Almolhis et al. [69] recently published an article that provided an analysis of the security flaws that are present in the Cloud-IoT system. The Cloud-IoT paradigm calls for users to connect directly to the cloud via the Internet and then begin transferring data over the network. This results in the rapid production of an enormous amount of data. The centralized cloud architecture, on the other hand, is inefficient when it comes to processing the enormous volume of data generated by IoT devices, which necessitates a very rapid response time. Edge computing is an alternative paradigm that processes data on linked devices or local gateways, and it has been utilized in order to get around this problem [4,22,28,47,59,62].
As it enables high-level communication and increased efficiency in edge networks rather than in clouds, the edge–fog computing paradigm is ideally suited for the current iteration of the Internet in general and the Internet of Things in particular [4]. It provides a wide array of IoT applications used today, notably those that call for quick responses. The goal of edge computing is to be the IoT solution of the future that addresses various problems, particularly those related to time-sensitive and computation-based applications. Six key factors for fog and edge environments have been identified by complementary studies [70,71], including task partitioning and offloading [71,72,73,74], sustainable power consumption [53,54], edge analytics [54,55], edge security [75,76,77,78,79], edge node and data exploration [80,81,82], and edge quality of service [83,84,85]. The advantages of data processing at the network edge include lowering networking load and communication latency, splitting the monopoly of large inventors [64], providing small and medium inventors the opportunity to support future innovations, lowering energy consumption of mobile nodes, relieving congestion inside the core network, and enhancing reliability, security, and privacy protection. As a counterpoint to the fragility of cloud computing, edge–fog computing has arisen as a promising alternative to fulfill the emergent demand to increase the processing, network, and storage capacity closer to end users [5]. Low latency, wide geographic distribution, heterogeneity, interoperability, real-time interactions, and scalability are edge–fog computing’s key qualities [63]. Nevertheless, there are still numerous obstacles to be solved in the research on the implementation of this contemporary computational paradigm [86].
3.2. Open Issues, Challenges, and Resolutions
3.2.1. Overview of the Open Issues
First of all, many promising IoT applications are still in the early stages of development. The IoT offers similar opportunities for research to create new algorithms and systems, much as work in analytics/data science and AI led to a wide range of creative applications. Interesting applications of IoT have started to emerge in smart cities, healthcare, smart supply chains, smart grids, smart transportation systems, and more [7]. The three Vs, or volume, variety, and velocity that are frequently associated with big data are essential components for creating these applications. Massive amounts of data are now being produced by sensors of various kinds, providing a variety of data streams that must be gathered, analyzed, and used as a basis for action. Each of these three Vs opens up a variety of research opportunities. Some of the challenges are identified in this study [87]. They break down all IoT applications into various subcategories, including real-time, offline, memory level, BI analytics, and enormous data, in order to contextualize the data challenges. Since data change quickly, the first subcategory of applications focuses on real-time analytics, which demands low-latency response times. In this subcategory, autonomous cars would be appropriate. Such IoT analytics applications are analogous to “complex event processing”. With CEP, one can examine numerous data streams as they come in and deduce an event or opportunity to take additional action from them. Complex event processing is a technique that researchers have been working on for a while [88] to assess data streams, generate alerts, and perhaps even start actions. Such analytics applications demand extremely effective modeling and storage techniques. The data and models one picks will also depend on the domain needs. Researchers are still looking into this topic.
Massive datasets used by the applications were also emphasized by authors in [89]. Overall, data volumes are increasing, necessitating the constant need for effective data-storage and management methods, as well as hardware for gathering, storing, curating, and getting rid of extra data. When working with IoT data, the data processing stage of the data mining process [7,9,12] is probably going to be much longer and more iterative. Even in the most basic data mining projects, there is a great deal of complexity involved in integrating the data from numerous sources, initially looking at or exploring the data, and deciding what to do with the data once it has been collected. Because of the significant increase in the volume of data coming from myriad sensors, the scale of the problem has significantly expanded [44,90].
The challenging field of the edge–fog computing paradigm is multidimensional. Along with the numerous technological obstacles and solutions, there is also a wide range of economic and political concerns, such as the change in the markets for information and communication technology or the development of a state’s digital economy [3,35,46,88]. These factors contribute to the complexity and ambiguity of words, standards, conventions, and understandings in the field of edge computing. Several initiatives addressing various facets of edge computing have emerged during the past few years. Among these are cross-border business partnerships, community-based software initiatives, or business-driven software projects. Fog computing, mobile edge computing, mobile cloud computing, and other paradigms were covered in the survey [77] of the partially concurrent edge computing paradigms. Due to the early adoption of the decentralized computing, many standards pertaining to the current concept of edge computing have been declared or are currently under active consideration. The most common and significant issues and objectives of fog computing are summarized in a recent article [63]. In the framework of this work, their analysis allowed for the identification of unresolved issues that call for additional study and research recommendations.
The difficulties in the area of fog and edge computing have been addressed in a number of surveys, ideas, and recommendations that have attempted to provide an overview of the papers in the field of fog computing, edge computing, or MEC (multi-access edge computing) [4,20,22,35]. With a focus on fog system architectures and techniques, the authors of [23] give a thorough assessment of recent research in fog computing. They go on to outline the potential uses of fog computing in relation to innovative technology, with a focus on the tactile internet. Baktir et al. [32] emphasize the value of collaboration between edge and cloud computing and explain how edge computing can be enhanced by software-defined networking (SDN). They mention the general technical difficulties in implementing an edge computing infrastructure and suggest using SDN as a solution. Additionally, the authors review publications that focus exclusively on edge computing and SDN to bolster their claims and provide guidance for SDN development in the future. Likewise, the authors in [29] gather a comprehensive review of current efforts in fog-enabled network architectures and provide numerous network applications of fog computing. Moreover, the authors in [30] look more closely at fog-assisted IoT applications, deliberate security and privacy challenges in fog computing, and review-analyze promising techniques to resolve both security and privacy issues in fog-assisted IoT applications. In addition, there are a few surveys in the area of MEC that also talk over related concepts to edge–fog computing [31,35,91]. These surveys introduce a thorough overview of computing technologies, including fog, cloudlets, micro data centers, and mobile edge and focus on the fundamental key enabling points in MEC. Furthermore, they evaluate the MEC reference architecture, list ongoing standardization initiatives, and provide key deployment scenarios.
3.2.2. Edge–Fog–IoT Capabilities Orchestration and Points of Concern
The real-time capability of edge–fog computing and the low-latency characteristics that it possesses are the primary factors that are driving its rapid expansion [4,46]. A social advantage of edge apps’ higher responsiveness when compared to cloud applications is the ability to respond in real time to user requests. Nonetheless, the widespread use of IoT and edge computing may result in ongoing scoring and monitoring, which could be harmful to people’s freedoms. In order to determine whether or not real-time data transfer contributes to a reduction in the amount of energy consumed, or whether it ultimately results in greater energy consumption, real-time applications need to be developed using a holistic approach [7,35,47]. Permanent data analysis and archiving would waste resources and energy in some applications. Several innovations, particularly those in the industrial or transportation sectors, call for a very consistent and efficient method of data processing that is physically no longer possible using the cloud or mobile data. Thus, providing edge computing solutions would provide current cloud computing solutions a significant competitive advantage. For instance, local vision-based human activity identification can be done using smart phone computing capabilities [1,38]. However, if responses occur too quickly or need to be readjusted, edge computing-dependent control circuits directing processes, such as microtrading in the financial industry, may become unstable. Implementing real-time solutions could jeopardize the stability of such control circuits because they need time to level their processes.
As previously explained, edge and fog computing technologies offer opportunities to improve data collecting and analysis [4,46,92]. When semantics are incorporated into the data, it is much easier to differentiate between data coming from different sources that are comparable to one another. For instance, very small edge devices are only able to suppress redundant data, whereas devices of a medium size or larger can provide software that is application specific [53]. Some edge technologies enable code mobility or maybe even the deployment of the same cloud-deployed containers on edge devices. From a sociological standpoint, caution is advised: There is a high risk of biases towards social groupings and the corresponding discrimination and exclusion when using people-related training data for predictions [3,7]. Several instances where machine-generated algorithm-based decisions have severely prejudiced persons and amplified racist and sexist behaviors have made media headlines. One must be conscious of the dangers that could arise if the training data is invalid or unreliable. For example, a facial recognition-based automated access system may operate flawlessly in a training environment, but it may not function properly in the real world, where people in wheelchairs or young children might not be able to use an interface that was designed for adults standing in front of a door. In addition, applications of learning can be used to promote environmental sustainability, such as optimizing and lowering energy use in homes and buildings [88,93]. To be able to compare energy usage holistically, it is necessary to take into account not only the energy used during implementation but also the energy used during the development of the learning algorithm, training, and storage of the training data. If one taught algorithm can reduce energy consumption by an amount greater than the energy it took to generate and train it, then this is positive for sustainable development. The utilization of learning and intelligent skills may facilitate the impact of scale economies. Once an algorithm can accurately anticipate specific behaviors, it may be applied to a variety of use cases, increasing the efficiency of many products or services without needing to make further investments [48].
Data visualization is typically one of the first outputs from analytics programs and is also a crucial step in the data processing process. It is already quite challenging to visualize massive datasets in analytics projects, and the challenge is exacerbated when we take into account IoT data with its variety of forms, immense volume, and variable collection rate [47,89]. One must create unique ways to show the data, look into techniques to minimize dimensionality, and come up with new ways to evaluate visualization results in order to find anything meaningful from visualizing such data streams. Automated Insights [60], for instance, has developed various pre-formatted methods for understanding Tableau graphics. The need of automated data interpretation will increase as IoT data volume and variety increase, necessitating further research.
The promotion and successful integration of the edge and fog computing is another significant management task [9,27,86]. Management techniques enhanced by edge computing may entail accessibility issues. Persons with special needs may experience difficulties using automatically managed systems without close human assistance. For example, blind people may be unable to understand textual instructions to use an edge application, and children or people in wheelchairs may be unable to access an interface. Decentralization should extend to the power supply as well as the computer capacity. Renewable energy sources may be locally utilized by decentralized power systems [48]. For instance, solar or wind energy could be used to power applications in cities. A nearby water power plant might be linked to intelligent manufacturing. At the same time, it is possible that the digitization of formerly analog processes will result in a rise in energy consumption. Additionally, researchers stress the need to take into account material consumption, in particular that of plastics and rare metals, as well as the concerns with recycling and global health brought on by e-waste [82]. At any level and hierarchy, the administration of an edge computing solution must be taken into account [46]. This mostly relates to agreements on edge computing efforts but also to applications generally. It concerns standards and interoperability. This goal includes not only technological solutions but also corporate cooperation and its effects on business decision making.
A cross-cutting surplus of edge computing for social, ecological, and economic sustainability is the potential for improvements in measuring and monitoring indicators for the sustainability dimensions, which can be used to trace back and forth between root causes and quantitative and qualitative impacts [93]. In order to be able to foresee and prepare for non-linear, unpredictable, or unanticipated changes in gradually complex social environments, monitoring might serve as the foundation for adaptive sustainable governance [46]. Careful consideration of these sustainability challenges makes determining whether or not an edge computing application is worthwhile being created in light of sustainability. Nevertheless, such systemic considerations must be made to guarantee that edge computing not only contributes to social and ecological well-being but also serves as a further engine for economic growth. This guideline is merely a preliminary idea for sustainable edge computing and needs further elaboration. It invites modifications and more discussion because it is neither exhaustive nor complete. Cloud computing generally utilizes a federation of public and private business providers connected via the Internet [94,95], extending resource availability as management complexity rises. Studies on this topic are few in the context of fog computing. Research on the use of standardized execution environments that facilitate error-free service execution through federated fog providers is particularly important because of the variety of devices that go into making up a fog environment.
Another concern to making IoT more practical and helpful is figuring out how to use (the) current analytics methodologies to more effectively manage data collecting and compilation techniques or to create a more accurate predictive model. For instance, researchers have looked into optimization models to identify the best locations for sensors in order to maximize coverage or minimize cost [96,97]. Researchers have additionally used analytical models to create improved data management techniques. For instance, to reduce data redundancy in a sensor network, the authors of [98] suggest and contrast a data-mining strategy with alternative strategies. Despite the fact that numerous papers have suggested an architecture for orchestration and presented the interactions between its modules, very few have used simulators to assess and contrast their suggestions with competing ones, and even fewer have evaluated their suggestions on actual testbeds [63]. It is impossible to build a database containing the history of service implementation on actual fog nodes using simulators. These databases, when used in conjunction with AI, can make it possible to develop prediction algorithms that can then be utilized by the optimization module of an orchestration framework [35,99]. As a result, only a small number of research papers that have been published have evaluated how their concepts for fog computing orchestration work in actual implementation contexts.
The infrastructure is now in place for enterprises to take advantage of the hyper-connectivity of the predicted 64 to 73 billion IoT-connected devices by 2025 [100,101], with 4G now available and 5G on the horizon. The smart home and healthcare markets hold the most promise for IoT development in the future, despite the fact that industrial IoT has already proved to be a profitable business model. While there are many benefits presented by this massive infrastructure of linked devices, we must address mounting privacy and security concerns [69,77]. The IoT extends previously constructed infrastructure as a technology, which raises the stakes in terms of security hazards for network administrators. IoT establishes numerous links to networks that were previously solely accessible by consumers through their own devices [97,102]. These extensions have the capacity to connect any device via automated processes without requiring human contact, resulting in a large number of access points from diverse devices that need to be guarded in order to safeguard the network. According to Gartner’s predictions, IoT-based devices will be involved in more than 25% of all cyber-attacks against enterprises [103]. Additionally, as connectivity grows, the variety, velocity, and volume of data will expand exponentially, further fueling the expansion of big data. Concerns over privacy will arise in relation to the types of data that businesses gather, handle, and keep as a result of this expansion but are further discussed in the next part of the article.
One of the most frequently mentioned objectives of fog orchestration is proper and effective resource management [104,105,106,107,108,109,110,111]. Indeed, there is a significant relationship between resource availability and operations such as service placement and computation offloading [112]. The assurance of Service Level Agreements is a further objective that is commonly stated (SLAs). This objective is referred to as delay reduction in several works [35,113]. Others have set the objective as an increase in application performance or reaction time [114,115], and some have said that they want to guarantee SLAs or Quality of Service (QoS) [109,116,117,118,119]. Some articles [90,120,121] mention service life cycle management as an additional objective. When a service is enrolled, its images are stored on a repository, delivered to an executing platform when requested, monitored for availability, and the appropriate actions are taken as needed (e.g., updating the image, migrating, or replicating the service), all while attending to previously agreed-upon requirements. Additionally, there are references in the papers analyzed to other particular objectives such as cost reduction [117,122], reduced energy use [114,117], increased application resilience [35,123], trustworthy orchestration [124], and implementation of the convergence of NFV, 5G, and fog [125].
3.2.3. Privacy and Security
When it comes to matters of privacy and safety, we have to be able to classify different kinds of worries and assess how urgently we need to take action. Data vary in their sensitivity even though their volume and variety are both expanding. Low-to-high sensitivity and harm categories can be used to classify privacy concerns [102]. Security risks can range from annoyances, such as a denial-of-sleep attack that keeps one’s phone battery from charging to physical threats, such as a hacker taking control of one’s IoT-enabled car and causing an accident [126]. A threat’s potential harm and its sensitivity are both subjective because they depend on the users’ perception of the potential outcomes [103]. Users may, for instance, view a denial-of-service attack as a physical threat if they are unable to access their application, and they may view an attack on an IoT pacemaker as a comparable threat if it endangers their lives. However, stakeholders other than end users, such as those that design IoT devices, offer IoT services, and other parties, may also be affected by the hazards. Therefore, we must decide who to protect before thinking about how to respond to risks to privacy and security.
Given that consumers have straight interaction with IoT devices and the personal data they supply, it is easy to understand the threat that privacy and security problems can pose to users. The use of IoT-enabled devices may expose users to security concerns or breaches of their personal information [127]. Due to an IoT security breach, their home security may be jeopardized or they may lose access to the services they depend on. IoT privacy and security breaches may have serious repercussions for the service provider or device manufacturer as well. It is the duty of providers to keep users and their devices secure [69,97]. Security breaches may lead to lawsuits, reputational damage, or even the closure of the organization. As previously stated, they also threaten outside parties who do not utilize IoT devices or were not involved in their development. Manufacturers have a binding obligation to “build in” security as much as feasible, even if they frequently place the cost of security on consumers. In today’s IT security industry, terms such as “cyber-physical systems” and “industrial IoT (IIoT) cyber-security” have gained popularity [103]. From automated manufacturing to IoT-enabled power grids, IIoT is still expanding [44,48]. An IoT manufacturing breach might cost a business millions of dollars and increase the cost of its consumers’ goods and services. Service interruptions or production shutdowns could have more serious effects, limiting or removing the customers’ right of entry to the products and services they require. Customers that depend on electricity from IoT-enabled power grids could lose power as a result of security breaches.
Edge computing in particular includes numerous security and safety concerns. It must be resistant to criminal attacks and unintentional applications, as well as robust and durable. Edge computing systems that operate safely and securely can guarantee fair processes in which all people are treated equally [1,7], for example, security cameras that analyze facial photos on-the-spot, which can increase societal stability. The ability to analyze and store data close to the data sources resolves a number of privacy-related problems because the data no longer need to be transmitted to a centralized server [78,87]. Data about people are therefore protected because they can no longer be aggregated and held centrally, which is advantageous for a socially sustainable development that complies with data protection and privacy laws. Permanent monitoring, though, raises privacy concerns, particularly when the procedures used to implement it are opaque to society or even undemocratic.
Edge computing requires the proper encryption and authentication based on the criticality, especially when installed in environments such as traffic or industrial production [48]. Due to the enormous number of IoT devices and sensors due to their ubiquity, higher energy consumptions would be required than for devices that are not secured. The best solution to this rise would be to use renewable energy sources, such as energy harvesting. In this regard, edge computing can inherently be put to use to consume energy where it is generated, thereby reducing the number of problems associated with the supply of energy at centralized data centers [7]. This is due to the fact that renewable sources of energy will be sourced in a decentralized manner, and it is difficult to distribute energy that comes from a multitude of small sources. Additionally, choosing encryption can result in resource savings. In this study [128], the authors analyzed and demonstrated that using elliptic curve cryptography to secure IoT situations can reduce energy usage by up to 50% when compared to Rivest–Shamir–Adleman.
Because computing is carried out over a distributed network in a decentralized architecture, it is more difficult to keep the same security standards than it is in a centralized computing center [99]. The security status of many field actors, and consequently, the circumstances for their clients, would be improved by the consistent and forceful adoption of the relevant standards. Additionally, security advancements for edge computing may serve as the foundation for fresh business strategies and a resilient digital economy [16]. In addition to being beneficial for customers and business partners, diversity in component, service, and application sources would also increase security because the same failures would not be repeated. Yet, the absence or shallow technological levels of security regulations could also be considered as an invitation to hackers, which is a matter requiring immediate attention [46].
The concerns of privacy and information security in the context of orchestration in fog computing also require further focus from academia. There are not many studies in the literature that have used authentication and authorization to confirm the identity of service requesters and protect data privacy [63,129]. Reallocations, replication, and migration of services might be required [35,130] in light of the tactics employed by an orchestration framework to handle user mobility, handle faults, and assure adequate service availability and performance. The risk of larceny or misappropriation may be significant [131] given the number of hops that data take or the number of machines they are copied to or shared with. Numerous ideas [63] have been put forward to address the situation of using the cloud layer when there are insufficient resources in the fog layer. One preferable option might be a federation of fog computing domains, because it can guarantee the benefits of fog computing, including lower latency. To increase data privacy, however, authentication and authorization must be strictly enforced. The literature on a federation of fog settings is extremely scant [104,105]; therefore, more research needs to be conducted on this scenario.
3.2.4. Influence on People
In addition to the previously mentioned factors, IoT developers have a mindset that is more concerned with gaining market dominance than improving people’s quality of life, even though the IoT and increased connectivity hold considerable promise for improving our quality of life and making it safer and more comfortable [132]. IoT technology has likewise developed as a machine-to-person technology with a variety of human interactions, while being first thought of as a machine-to-machine technology. Research demonstrates that as more areas adopt the IoT and change as a result, human interactions with it continue to change. Nevertheless, the authors of [133] note that research regarding how the IoT will affect people is still in its adolescence. As we have already explained, there are several human-centered concerns and what might be regarded as best practices for an effective, efficient, and secure IoT design. We examined the IoT literature from the perspective of human interaction with an emphasis on design issues that are human-centered [11]. In this study, we identified five groups of IoT traits and issues that designers should consider when creating IoT products and applications for human contact. These categories are: (a) types of environmental interactions, (b) semantic data selection, (c) smart device design, (d) interaction levels of smart devices, and (e) application trustworthiness. Individual expectations, values, and beliefs influence whether or not people trust IoT apps. To give IoT developers a wider view while creating IoT apps for human interaction, we summarize the following important criteria [11,103]. In particular, in the areas of human factors and computer–human interactions, these same five categories offer prospects for IS study. These areas are focused on how people engage with IoT devices, what information people or machines require to understand situations and respond appropriately, and how people perceive the legitimacy of those interactions [132]. All of these challenges pose a lot of questions, but they also present a lot of research opportunities for appropriate IoT goods, services, and solutions across the business value chain of modern enterprises.
3.3. Value Levers and Streams
Whether an organization chooses to use IoT to serve its internal or its external customers, the expenditure can only be considered justifiable if the produced value outweighs the investment that is required [3]. However, the idea of value must be broadened to cover the overall value generated for all stakeholders (such as employees, consumers, investors, and suppliers) in order to conduct a thorough investment appraisal of IoT [133]. Real world visibility and business process deconstruction are the two key ways in which organizations can derive business value from the IoT, according to [36]. The ability of IoT to connect physical and digital words is related to real words being visible. This allows for more effective optimization and better decision making by giving businesses real-time insights on what is happening in the outside world. Business process decomposition refers to the reality that more decentralized business processes are made possible by the dispersed nature of the IoT infrastructure, leading to improved scalability, performance, and creativity [37].
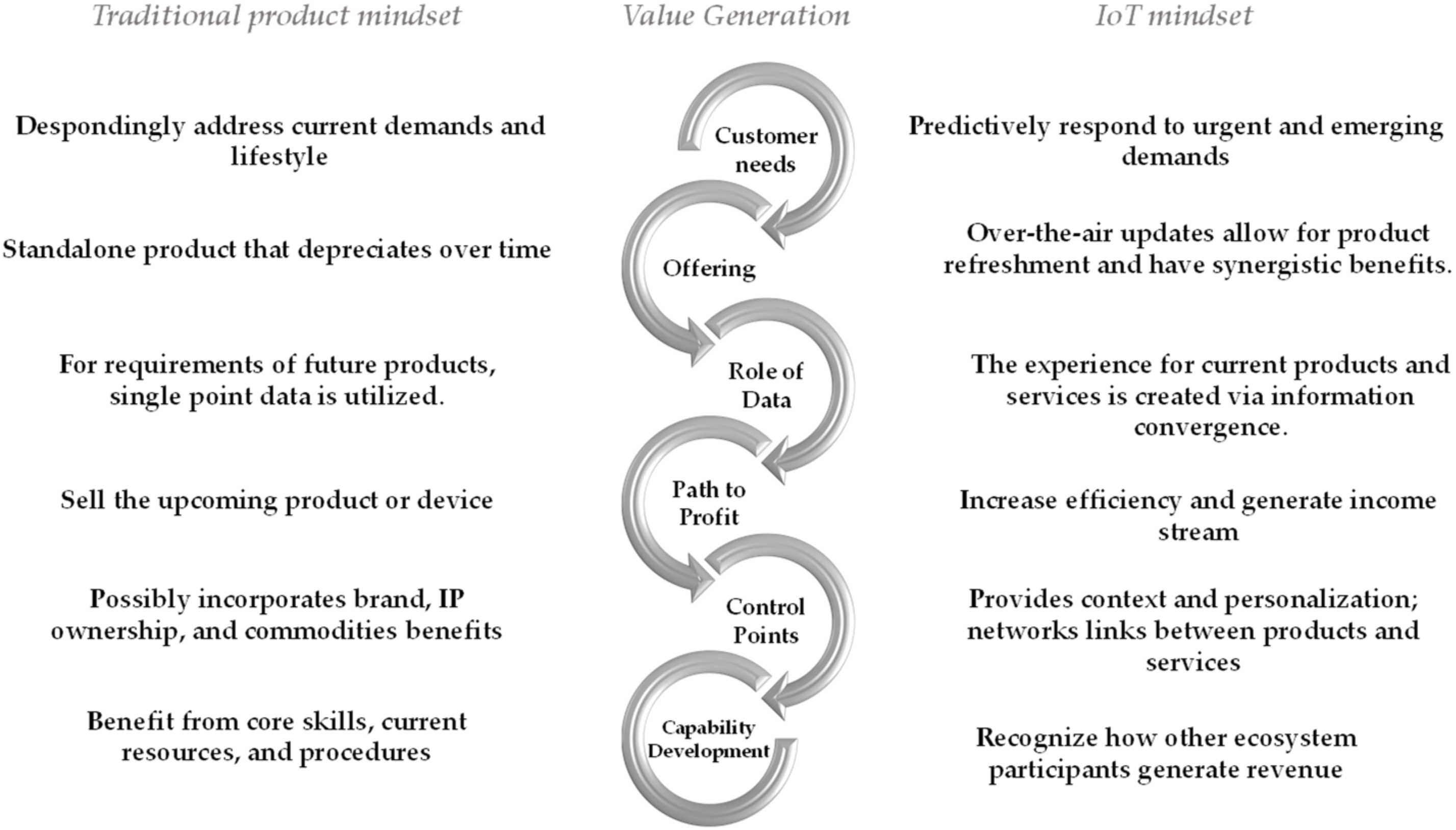
Unfortunately, adding value alone is insufficient. Value is only meaningful in an enterprise environment when it is captured and monetized [134,135] either directly or indirectly (as tangible benefits or intangible benefits). According to research such as [37], the primary forces behind value generation and value capture for traditional and IoT products can be captured (see Figure 3).
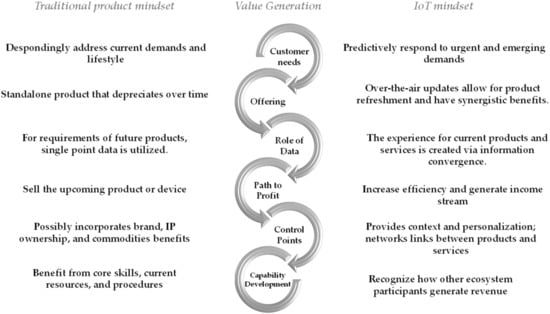
Figure 3.
Comparison between traditional product and IoT mindset considering value generation.
IoT solutions, in contrast to conventional products and services, generally generate value for many stakeholders [19,136] as they span organizational boundaries and intimately connect suppliers and consumers in ongoing interactions beyond the moment of sale [38,137]. IoT solutions, for instance, deliver value to both the provider and the user by offering at the same time several benefits. Additionally, the value therefore produced is greater than monetary compensation [138,139]. According to [140], when the IoT promotes ongoing client contacts, it creates a situation where both users and providers are influenced. Nonetheless, the authors of [45] demonstrated in their comprehensive study on the advantages and hazards of IoT adoption in enterprises that the lower acceptance rate of IoT solutions is related to associated risks (e.g., by policies, regulations, challenges, or mistrust). It is crucial to show the consumer the value and possible benefits of the IoT solution in order to mitigate these risks.
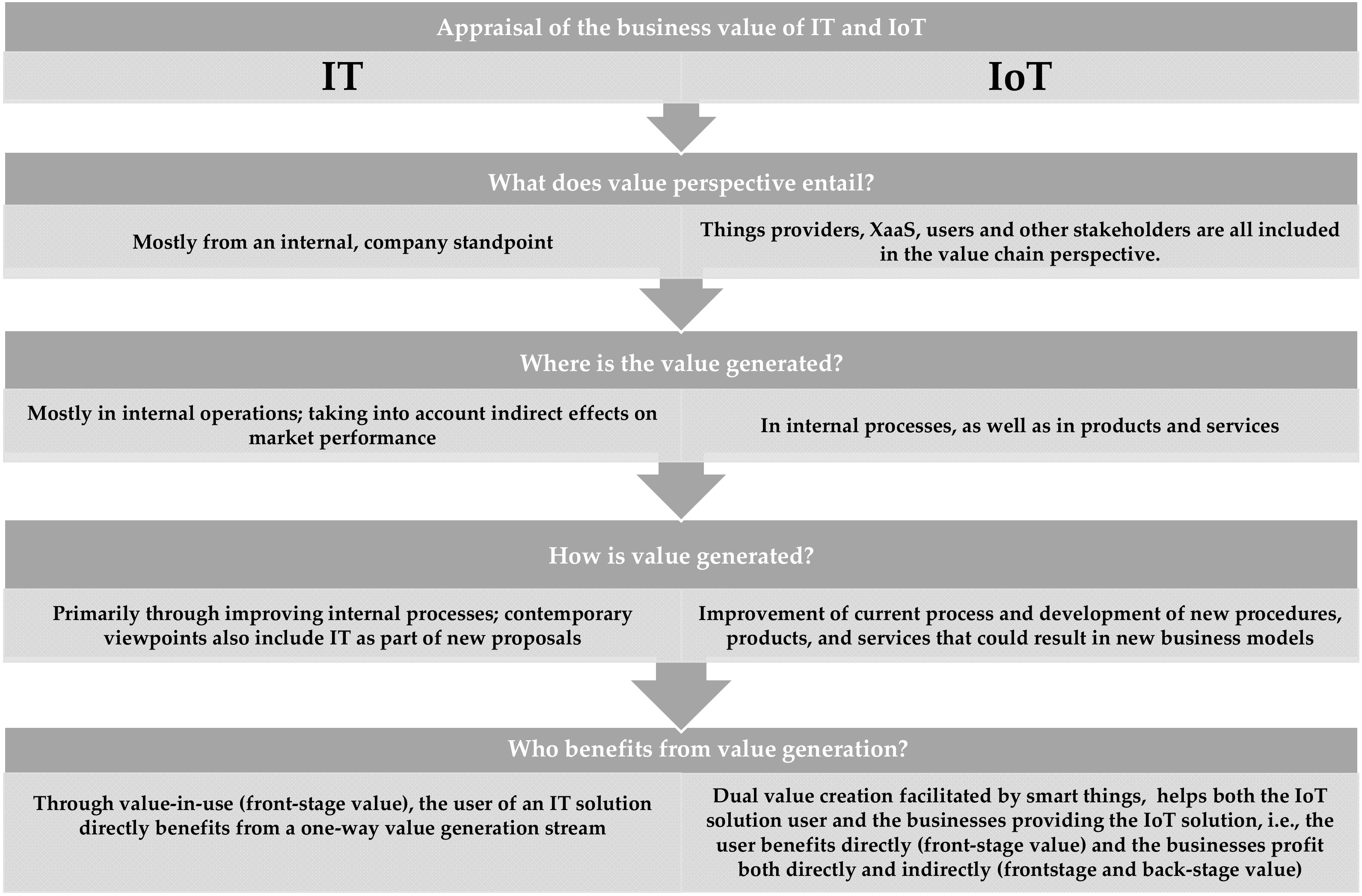
In light of this, the authors of [141] recommend that IoT solutions be conceptualized in a way that smart things are viewed as boundary objects that enable dual value creation. First, the user gains from the product’s front-stage usage by generating and capturing value while it is being used, whether through remote control, monitoring, or optimization. The supplier, on the other hand, profits from backstage analytics, such as data aggregation, data analytics, or decision making [141,142]. The vendor of the solution can then create value in the future by creating new and improved offerings based on ongoing client relationships and information learned from backstage analytics [140]. In turn, this raises the value of upcoming procedures, products and services. IoT solutions, sometimes referred to as front-stage value and backstage value, respectively, create value for both customers and enterprises (providers and XaaS). Figure 4 summarizes the main distinctions between the business value perspectives on IT and IoT.
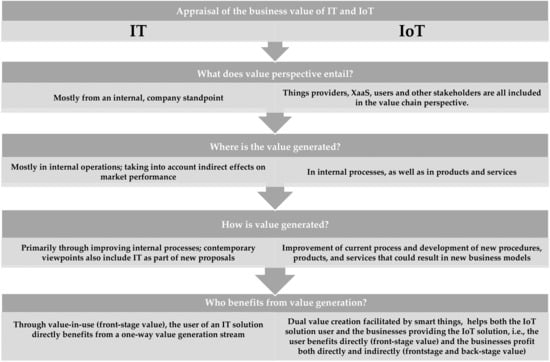
Figure 4.
Appraisal of the business value of IT and IoT.
Faster time-to-market and the availability of data and information undoubtedly influence value development significantly. Valuable IoT solutions decouple the information flow produced by the device from its physical attributes [133] and mix and integrate “thing”-based and IT-based capabilities [37]. As a result, information (data) generates value in and of itself by enabling data-driven service innovation, real-time customer interactions, and improved customer prediction [143]. The functionality of IoT devices that is based on IT undoubtedly contributes the most value, and the point that each device is linked to the network but also to one another enables the introduction of updates and new features “over the air”. This significantly shortens the innovation time to market, which is crucial for physical products with a longer lifespan than software.
IoT technologies also make it possible to build digital platforms where a variety of actors can profit from the astronomical amount of data that linked devices generate. The value of information is not limited in any way. Quite the opposite, it worsens as more of these technologies are utilized in daily life. IoT is the ideal platform for fostering inter-organizational partnerships and innovation, as well as for utilizing network effects that would eventually benefit all stakeholders due to the abundance of information available there [38]. Additionally, the IoT enables businesses to switch from unit-based revenue streams to value-based pricing, which is more adaptable and is based on the value of the service and the information offered to the end user [144]. This, however, suggests that the provider of the service can quantify the value considerations connected to particular services and offer clients a visible and understandable value proposition.
Eventually, the organization should be able to build a competitive advantage on the back of its IoT investments. This is not as easy as it seems to be in the IoT environment, success resides on the precipice between internal information management and open innovation and collaboration [145]. When the technology and competitive scene is constantly changing, this becomes even more difficult. The authors of [146] contend that organizations should enhance their capacity for integrating, constructing, and reconfiguring internal and external competencies in order to adapt to settings that change quickly. Potential configurations, meanwhile, depend on the particular context that an organization operates in [144]. Given that the effects of technology investments go much beyond the technical aspects of the business model, it is recommended that managers should establish and evaluate their own strategic approach to IoT.
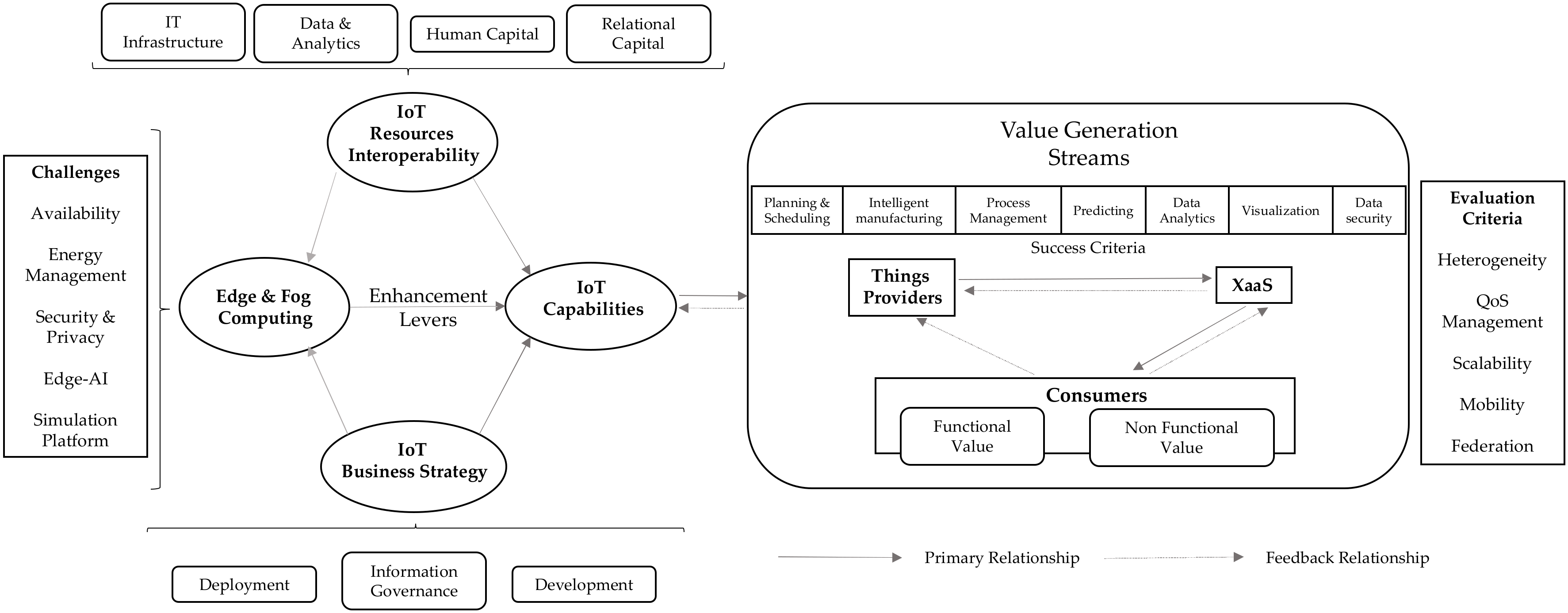
To sum up all of the above, we provide a conceptual model that describes all the foretold relationships. Figure 5 gives a graphic overview of our methodology for value mapping in the IoT, which was modified based on the earlier sections of pertinent literature. This framework was created expressly to assist managers in determining the value of complicated IoT investments while also taking into account edge–fog computing in the foreseen relationship.
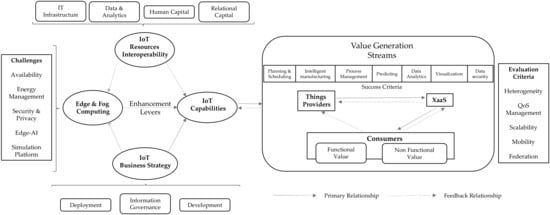
Figure 5.
Conceptual framework.
4. Conclusions
This article sought to investigate the role that edge and fog computing plays as a driver and enabler of an organization’s IoT-driven business value. We conducted a systematic literature review using a particular technique that has been widely utilized in the past to investigate information systems strategy and subjects related to digital transformation. According to our research, technical advancements in a firm’s surroundings frequently compel it to make technological changes, which amounts to a digital transformation. The ability of the organization to interact with its environment and adhere to new regulatory frameworks is no longer a choice, it is an urgent necessity. At the same time, edge and fog computing have been emphasized as significant enablers for the creation of new business value through IoT capabilities. In light of their usage frequency, particular challenges, resolutions, levers, and streams can be identified. Anyhow, implemented IoT solutions combined with edge–fog computing unlock new paths of value creation that must be studied from various complex perspectives to be able to offer businesses a substantial competitive advantage.
In order to summarize the literature and convey the theoretical and practical implications of this study topic, we built a conceptual model for evaluating the various aspects of value in IoT solutions, as it is also increased through edge–fog computing. It was observed that previous literature researches either emphasized on the technological aspect of the edge–fog computing and IoT or systematic mapping studies that provided narrative amount of knowledge in the strategic alignment of these technologies to business value. In order to serve as a springboard for future research, this paper is a study that offers a broader perspective on the research area, its evolution, and links across studies. This literature review is helpful to academics, practitioners, and general researchers who are already engaged in digital transformation research but are interested in examining more detailed insights into the area of current research topics in this literature and how they might contribute to them.
In terms of the theoretical implications of our research, it should be noted that the current investigation contributes to the solution of the problem posed by the lack of theoretical foundations for the interpretation and application of edge–fog–IoT technologies on a business scale. First, we have contributed to the existing body of research on the business value of IoT as well as the well-established IS research topic on the business value of IT by providing a conceptual framework for evaluating the three-way interaction of edge–fog, IoT, and value. In doing so, we have added to both of these areas of research. Our framework integrates the perspective on the front-stage and backstage value of IoT solutions with the perspective on value through IoT in internal processes and/or products and services. This allows us to provide a more comprehensive analysis of the value of IoT solutions. In addition to this, our work contributes to the existing body of knowledge on IoT-enabled business models by strategically integrating edge and fog computing. In the same vein, it serves as a starting point for additional theoretical and empirical investigations into how IoT solutions impact business performance and competitive advantage, which is a continuation of the tradition of the business value of IT research. In particular, in addition to front-stage value, backstage value should be further examined because it may result in a competitive advantage through long-term insights and ongoing client interactions. This is one of the reasons why front-stage value is important.
This research offers useful practical implications for firms to build and maintain a competitive advantage by proactively coordinating IoT resources and strategies, in addition to its theoretical contribution. Our results indicate that many value streams require further investigation in order to actually analyze the potential impact of IoT capabilities. In this way, it will help managers to evaluate possible investments in such technologies and businesses to foster greater performance and innovation. In the context of IoT, networks and data together are a major force behind digital transformation. If only the right organizational environment is built, IoT capabilities can have a beneficial impact (e.g., skills, management strategy, organizational structure, and methodological approach to business processes improvement). A high level of data quality can create significant value by increasing the transparency of information (completeness, accuracy, format, and currency). Edge computing enables fast access to the vast amounts of recent and pertinent data that are necessary for machine learning algorithms. With IoT sensors, adjustments to workflows and processes can also be performed instantly, allowing businesses to make informed decisions more quickly. It is possible to process and access data as near to the source as is practical in order to automate processes. Businesses can make and automate data-driven decisions thanks to the stability and reliability offered by edge and fog computing. Any situation where instant data processing is necessary might benefit from reduced latency, resulting in overall reduced response times. Additionally, edge and fog computing can help businesses avoid costs on computing expenses while also providing a cost-effective way to guarantee data quality, speed, and accuracy. Companies can handle data much more effectively by merely transferring data over short distances and carrying out the majority of the processing in a decentralized way. When raw data is managed at the network’s edge, less computational power and bandwidth are needed, which translates into lower expenses. The ability to process, analyze, and categorize data before sending it can result in significant savings in network and computation resources when managing the large amounts of data generated by sensors in an industrial setting. Further, edge and fog computing, which keeps sensitive data close to the source before transferring them, can benefit the cyber security efforts of businesses. This enables sensitive data to be examined and anonymized close to the source rather than transferring potentially revealing information to the cloud, bringing cloud accessibility to some companies with strong security and compliance standards. While non-sensitive data can be transferred to the cloud for processing, personal or sensitive data can be separated at the source, close to the device and handled locally there.
For academia, edge and fog computing provide a rare chance to refocus their research efforts on applied distributed computing in general, with a concentration on cloud and mobile computing in particular. It is challenging for academic research to concentrate on magnitude without creating conjectures that might not always be accurate. This is merely a result of the fact that numerous academic institutions and researchers are unable to use infrastructure that is owned by industry or the government to confirm and improve their findings. However, top academic institutions with trustworthy corporate and governmental relationships have generated more significant and useful research. An open coalition of business partners, including cloud service providers, equipment developers, and mobile operators, as well as interested academic partners, can spearhead research in the areas of edge–fog computing and the Internet of Things.
Regarding the limitations of this article, there might still be publications referencing IoT, edge–fog computing, and business value that do not include the term, or variations of it, in their title or abstract even though we looked for many combinations of the linked terms. Moreover, we rejected more technical papers by restricting our search to business-related topics. Additionally, we only looked at English-language papers, excluding works that contributed to the state of the art in other languages. Furthermore, we believe that the applications of IoT in industry, such as smart cities, the health sector, manufacturing, etc., deserve a lot more attention and needs a distinctive survey comparing the necessities, challenges and resolutions between the different fields.
Our study is concentrated upon the role that edge–fog computing plays in the generation of business value through IoT. Future research is advised to examine the aforementioned conceptual model both theoretically and empirically, paying close attention to each model substitution. This article offers a review of the literature from a different point of view, not actualized in current studies, while covering issues such as edge–fog computing, IoT, and business strategies. It might be seen as the first stage of further investigation, while future researchers might expand on this assessment of the literature and perform a bibliometric analysis, such as co-author or co-citation. Since we conducted an analysis of the most significant benefits and challenges of these technologies across industries, it could be also interesting for future studies to categorize the relationships and value streams that are created based on different use cases and applications for better strategic implementation among different scenarios.
Author Contributions
Conceptualization, N.-A.P.; methodology, N.-A.P. and F.K.; investigation, N.-A.P.; data curation, F.K.; writing—original draft preparation, N.-A.P. and F.K.; writing—review and editing, N.-A.P. and F.K.; visualization, N.-A.P.; supervision, F.K. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
This study did not report any data.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Oberländer, A.M.; Röglinger, M.; Rosemann, M.; Kees, A. Conceptualizing Business-to-Thing Interactions—A Sociomaterial Perspective on the Internet of Things. Eur. J. Inf. Syst. 2018, 27, 486–502. [Google Scholar] [CrossRef]
- Puschel, L.C.; Roglinger, M.; Brandt, R. Unblackboxing Smart Things—A Multilayer Taxonomy and Clusters of Nontechnical Smart Thing Characteristics. IEEE Trans. Eng. Manag. 2022, 69, 2129–2143. [Google Scholar] [CrossRef]
- Baltuttis, D.; Häckel, B.; Jonas, C.M.; Oberländer, A.M.; Röglinger, M.; Seyfried, J. Conceptualizing and Assessing the Value of Internet of Things Solutions. J. Bus. Res. 2022, 140, 245–263. [Google Scholar] [CrossRef]
- Yousefpour, A.; Fung, C.; Nguyen, T.; Kadiyala, K.; Jalali, F.; Niakanlahiji, A.; Kong, J.; Jue, J.P. All One Needs to Know about Fog Computing and Related Edge Computing Paradigms: A Complete Survey. J. Syst. Archit. 2019, 98, 289–330. [Google Scholar] [CrossRef]
- Bonomi, F.; Milito, R.; Zhu, J.; Addepalli, S. Fog Computing and It’s Role in the Internet of Things. In Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing (MCC’12), New York, NY, USA, 17 August 2012; ACM: New York, NY, USA, 2012; pp. 13–16. [Google Scholar]
- Alli, A.A.; Alam, M.M. The Fog Cloud of Things: A Survey on Concepts, Architecture, Standards, Tools, and Applications. Internet Things 2020, 9, 100–177. [Google Scholar] [CrossRef]
- Laroui, M.; Nour, B.; Moungla, H.; Cherif, M.A.; Afifi, H.; Guizani, M. Edge and Fog Computing for IoT: A Survey on Current Research Activities & Future Directions. Comput. Commun. 2021, 180, 210–231. [Google Scholar]
- Bilgeri, D.; Wortmann, F. Barriers to IoT Business Model Innovation. In Proceedings of the der 13. Internationalen Tagung Wirtschaftsinformatik, St. Gallen, Switzerland, 12–15 February 2017; pp. 987–990. [Google Scholar]
- Del Giudice, M. Discovering the Internet of Things (IoT) within the Business Process Management: A Literature Review on Technological Revitalization. Bus. Process Manag. J. 2016, 22, 263–270. [Google Scholar] [CrossRef]
- Huber, R.X.R.; Püschel, L.C.; Röglinger, M. Capturing Smart Service Systems: Development of a Domain-specific Modelling Language. Inf. Syst. J. 2019, 29, 1207–1255. [Google Scholar] [CrossRef]
- Kasilingam, D.; Krishna, R. Understanding the Adoption and Willingness to Pay for Internet of Things Services. Int. J. Consum. Stud. 2022, 46, 102–131. [Google Scholar] [CrossRef]
- Sheth, A. Internet of Things to Smart IoT through Semantic, Cognitive, and Perceptual Computing. IEEE Intell. Syst. 2016, 31, 108–112. [Google Scholar] [CrossRef]
- Bilgeri, D.; Fleisch, E.; Gebauer, H.; Wortmann, F. Driving Process Innovation with IoT Field Data. MISQE 2019, 18, 191–207. [Google Scholar] [CrossRef] [Green Version]
- Côrte-Real, N.; Ruivo, P.; Oliveira, T. Leveraging Internet of Things and Big Data Analytics Initiatives in European and American Firms: Is Data Quality a Way to Extract Business Value? Inf. Manag. 2020, 57, 103–141. [Google Scholar] [CrossRef]
- Fichman, R.G.; Dos Santos, B.L.; Zheng, Z.; Boston College; University of Louisville. University of Texas at Dallas Digital Innovation as a Fundamental and Powerful Concept in the Information Systems Curriculum. MISQ 2014, 38, 329–343. [Google Scholar] [CrossRef]
- Haaker, T.; Ly, P.T.M.; Nguyen-Thanh, N.; Nguyen, H.T.H. Business Model Innovation through the Application of the Internet-of-Things: A Comparative Analysis. J. Bus. Res. 2021, 126, 126–136. [Google Scholar] [CrossRef]
- Paiola, M.; Gebauer, H. Internet of Things Technologies, Digital Servitization and Business Model Innovation in BtoB Manufacturing Firms. Ind. Mark. Manag. 2020, 89, 245–264. [Google Scholar] [CrossRef]
- Kohli, R.; Grover, V.; College of William and Mary, USA; Clemson University. USA Business Value of IT: An Essay on Expanding Research Directions to Keep up with the Times. JAIS 2008, 9, 23–39. [Google Scholar] [CrossRef]
- Nicolescu, R.; Huth, M.; Radanliev, P.; De Roure, D. Mapping the Values of IoT. J. Inf. Technol. 2018, 33, 345–360. [Google Scholar] [CrossRef]
- Yi, S.; Li, C.; Li, Q. A Survey of Fog Computing: Concepts, Applications and Issues. In Proceedings of the 2015 Workshop on Mobile Big Data, Hangzhou China, 21 June 2015; ACM: New York, NY, USA, 2015; pp. 37–42. [Google Scholar]
- Chiang, M.; Zhang, T. Fog and IoT: An Overview of Research Opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Shi, W.; Cao, J.; Zhang, Q.; Li, Y.; Xu, L. Edge Computing: Vision and Challenges. IEEE Internet Things J. 2016, 3, 637–646. [Google Scholar] [CrossRef]
- Mouradian, C.; Naboulsi, D.; Yangui, S.; Glitho, R.H.; Morrow, M.J.; Polakos, P.A. A Comprehensive Survey on Fog Computing: State-of-the-Art and Research Challenges. IEEE Commun. Surv. Tutor. 2018, 20, 416–464. [Google Scholar] [CrossRef]
- Khan, W.Z.; Ahmed, E.; Hakak, S.; Yaqoob, I.; Ahmed, A. Edge Computing: A Survey. Future Gener. Comput. Syst. 2019, 97, 219–235. [Google Scholar] [CrossRef]
- Naha, R.K.; Garg, S.; Georgakopoulos, D.; Jayaraman, P.P.; Gao, L.; Xiang, Y.; Ranjan, R. Fog Computing: Survey of Trends, Architectures, Requirements, and Research Directions. IEEE Access 2018, 6, 47980–48009. [Google Scholar] [CrossRef]
- Omoniwa, B.; Hussain, R.; Javed, M.A.; Bouk, S.H.; Malik, S.A. Fog/Edge Computing-Based IoT (FECIoT): Architecture, Applications, and Research Issues. IEEE Internet Things J. 2019, 6, 4118–4149. [Google Scholar] [CrossRef]
- Mahmud, R.; Kotagiri, R.; Buyya, R. Fog Computing: A Taxonomy, Survey and Future Directions. In Internet of Everything; Di Martino, B., Li, K.-C., Yang, L.T., Esposito, A., Eds.; Internet of Things; Springer: Singapore, 2018; pp. 103–130. ISBN 978-981-10-5860-8. [Google Scholar]
- Yu, W.; Liang, F.; He, X.; Hatcher, W.G.; Lu, C.; Lin, J.; Yang, X. A Survey on the Edge Computing for the Internet of Things. IEEE Access 2018, 6, 6900–6919. [Google Scholar] [CrossRef]
- Mukherjee, M.; Shu, L.; Wang, D. Survey of fog Computing: Fundamental, network applications, and research challenges. IEEE Commun. Surv. Tutor. 2018, 20, 1826–1831. [Google Scholar] [CrossRef]
- Ni, J.; Zhang, K.; Lin, X.; Shen, X. Securing Fog Computing for Internet of Things Applications: Challenges and Solutions. IEEE Commun. Surv. Tutor. 2018, 20, 601–628. [Google Scholar] [CrossRef]
- Hu, P.; Dhelim, S.; Ning, H.; Qiu, T. Survey on Fog Computing: Architecture, Key Technologies, Applications and Open Issues. J. Netw. Comput. Appl. 2017, 98, 27–42. [Google Scholar] [CrossRef]
- Baktir, A.C.; Ozgovde, A.; Ersoy, C. How Can Edge Computing Benefit from Software-Defined Networking: A Survey, Use Cases, and Future Directions. IEEE Commun. Surv. Tutor. 2017, 19, 2359–2391. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The Internet of Things: A Survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Berman, S.J.; Kesterson-Townes, L. Connecting with the Digital Customer of the Future. Strategy Leadersh. 2012, 40, 29–35. [Google Scholar] [CrossRef]
- Velasquez, K.; Abreu, D.P.; Assis, M.R.M.; Senna, C.; Aranha, D.F.; Bittencourt, L.F.; Laranjeiro, N.; Curado, M.; Vieira, M.; Monteiro, E.; et al. Fog Orchestration for the Internet of Everything: State-of-the-Art and Research Challenges. J. Internet Serv. Appl. 2018, 9, 14. [Google Scholar] [CrossRef] [Green Version]
- Haller, S.; Karnouskos, S.; Schroth, C. The Internet of Things in an Enterprise Context. In Future Internet—FIS 2008; Domingue, J., Fensel, D., Traverso, P., Eds.; Lecture Notes in Computer Science; Springer: Berlin/Heidelberg, Germany, 2009; Volume 5468, pp. 14–28. ISBN 978-3-642-00984-6. [Google Scholar]
- Rosati, P.; Lynn, T. Mapping the Business Value of the Internet of Things. In The Cloud-to-Thing; Palgrave Studies in Digital Business & Enabling Technologies; Springer International Publishing: Cham, Switzerland, 2020; pp. 141–157. ISBN 978-3-030-41109-1. [Google Scholar]
- Mejtoft, T. Internet of Things and Co-Creation of Value. In Proceedings of the 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, Dalian, China, 19–22 October 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 672–677. [Google Scholar]
- Whitmore, A.; Agarwal, A.; Da Xu, L. The Internet of Things—A Survey of Topics and Trends. Inf. Syst. Front. 2015, 17, 261–274. [Google Scholar] [CrossRef]
- Räikkönen, M.; Saari, L.; Valkokari, K.; Rantala, A.; Kortelainen, H. Creating Value and Business Benefits from Joint Offerings of Asset Performance Management Tools in the Capital-Intensive Industries. In 15th WCEAM Proceedings; Pinto, J.O.P., Kimpara, M.L.M., Reis, R.R., Seecharan, T., Upadhyaya, B.R., Amadi-Echendu, J., Eds.; Lecture Notes in Mechanical Engineering; Springer International Publishing: Cham, Switzerland, 2022; pp. 126–136. ISBN 978-3-030-96793-2. [Google Scholar]
- Grönroos, C.; Voima, P. Critical Service Logic: Making Sense of Value Creation and Co-Creation. J. Acad. Mark. Sci. 2013, 41, 133–150. [Google Scholar] [CrossRef]
- Bowman, C.; Ambrosini, V. Firm Value Creation and Levels of Strategy. Manag. Decis. 2007, 45, 360–371. [Google Scholar] [CrossRef]
- Khan, A.; Pohl, M.; Bosse, S.; Hart, S.W.; Turowski, K. A Holistic View of the IoT Process from Sensors to the Business Value. In Proceedings of the 2nd International Conference on Internet of Things, Big Data and Security, Porto, Portugal, 24–26 April 2017; SCITEPRESS—Science and Technology Publications: Porto, Portugal, 2017; pp. 392–399. [Google Scholar]
- Rajnoha, R.; Hadac, J. Strategic Key Elements in Big Data Analytics as Driving Forces of IoT Manufacturing Value Creation: A Challenge for Research Framework. IEEE Trans. Eng. Manag. 2022, 1–16. [Google Scholar] [CrossRef]
- Brous, P.; Janssen, M.; Herder, P. The Dual Effects of the Internet of Things (IoT): A Systematic Review of the Benefits and Risks of IoT Adoption by Organizations. Int. J. Inf. Manag. 2020, 51, 101952. [Google Scholar] [CrossRef]
- Hamm, A.; Willner, A.; Schieferdecker, I. Edge Computing: A comprehensive survey of current initiatives and a roadmap for a sustainable edge Computing development. In Proceedings of the 15th International Conference on Business Information Systems 2020 “Developments, Opportunities and Challenges of Digitization”, WIRTSCHAFTSINFORMATIK, Potsdam, Germany, 9–11 March 2020. [Google Scholar]
- Ai, Y.; Peng, M.; Zhang, K. Edge Computing Technologies for Internet of Things: A Primer. Digit. Commun. Netw. 2018, 4, 77–86. [Google Scholar] [CrossRef]
- Kagermann, H. Change through Digitization—Value Creation in the Age of Industry 4.0. In Management of Permanent Change; Albach, H., Meffert, H., Pinkwart, A., Reichwald, R., Eds.; Springer Fachmedien Wiesbaden: Wiesbaden, Germany, 2015; pp. 23–45. ISBN 978-3-658-05013-9. [Google Scholar]
- Watson, R.T.; Webster, J. Analysing the Past to Prepare for the Future: Writing a Literature Review a Roadmap for Release 2.0. J. Decis. Syst. 2020, 29, 129–147. [Google Scholar] [CrossRef]
- Aazam, M.; Huh, E.-N. Fog Computing: The Cloud-IoT\/IoE Middleware Paradigm. IEEE Potentials 2016, 35, 40–44. [Google Scholar] [CrossRef]
- Neagu, G.; Preda, S.; Stanciu, A.; Florian, V. A Cloud-IoT Based Sensing Service for Health Monitoring. In Proceedings of the 2017 E-Health and Bioengineering Conference (EHB), Sinaia, Romania, 22–24 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 53–56. [Google Scholar]
- Ismail, L.; Materwala, H. Energy-Aware VM Placement and Task Scheduling in Cloud-IoT Computing: Classification and Performance Evaluation. IEEE Internet Things J. 2018, 5, 5166–5176. [Google Scholar] [CrossRef]
- Beloglazov, A.; Abawajy, J.; Buyya, R. Energy-Aware Resource Allocation Heuristics for Efficient Management of Data Centers for Cloud Computing. Future Gener. Comput. Syst. 2012, 28, 755–768. [Google Scholar] [CrossRef] [Green Version]
- Morabito, R. Inspecting the Performance of Low-Power Nodes during the Execution of Edge Computing Tasks. In Proceedings of the 2017 14th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 8–11 January 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 148–153. [Google Scholar]
- Maduako, I.; Cao, H.; Hernandez, L.; Wachowicz, M. Combining Edge and Cloud Computing for Mobility Analytics: Poster Abstract. In Proceedings of the Second ACM/IEEE Symposium on Edge Computing, San Jose, CA, USA, 12 October 2017; ACM: New York, NY, USA, 2017; pp. 1–3. [Google Scholar]
- Goscinski, A.M.; Tari, Z.; Aziz, I.A.; Alzahrani, E.J. Fog Computing as a Critical Link Between a Central Cloud and IoT in Support of Fast Discovery of New Hydrocarbon Reservoirs. In Mobile Networks and Management; Hu, J., Khalil, I., Tari, Z., Wen, S., Eds.; Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering; Springer International Publishing: Cham, Switzerland, 2018; Volume 235, pp. 247–261. ISBN 978-3-319-90774-1. [Google Scholar]
- Chiang, M.; Ha, S.; Risso, F.; Zhang, T.; Chih-Lin, I. Clarifying Fog Computing and Networking: 10 Questions and Answers. IEEE Commun. Mag. 2017, 55, 18–20. [Google Scholar] [CrossRef]
- Pan, Y.; Thulasiraman, P.; Wang, Y. Overview of Cloudlet, Fog Computing, Edge Computing, and Dew Computing. In Proceedings of the 3rd International Workshop on Dew Computing, Toronto, ON, Canada, 29–30 October 2018; pp. 20–23. [Google Scholar]
- Satyanarayanan, M. The Emergence of Edge Computing. Computer 2017, 50, 30–39. [Google Scholar] [CrossRef]
- Yi, S.; Hao, Z.; Qin, Z.; Li, Q. Fog Computing: Platform and Applications. In Proceedings of the 2015 Third IEEE Workshop on Hot Topics in Web Systems and Technologies (HotWeb), Washington, DC, USA, 12–13 November 2015; IEEE: Piscataway, NJ, USA; pp. 73–78. [Google Scholar]
- Bonomi, F.; Milito, R.; Natarajan, P.; Zhu, J. Fog Computing: A Platform for Internet of Things and Analytics. In Big Data and Internet of Things: A Roadmap for Smart Environments; Bessis, N., Dobre, C., Eds.; Studies in Computational Intelligence; Springer International Publishing: Cham, Switzerland, 2014; Volume 546, pp. 169–186. ISBN 978-3-319-05028-7. [Google Scholar]
- Cao, K.; Liu, Y.; Meng, G.; Sun, Q. An Overview on Edge Computing Research. IEEE Access 2020, 8, 85714–85728. [Google Scholar] [CrossRef]
- Costa, B.; Bachiega, J.; de Carvalho, L.R.; Araujo, A.P.F. Orchestration in Fog Computing: A Comprehensive Survey. ACM Comput. Surv. 2022, 55, 1–34. [Google Scholar] [CrossRef]
- Pan, J.; McElhannon, J. Future Edge Cloud and Edge Computing for Internet of Things Applications. IEEE Internet Things J. 2018, 5, 439–449. [Google Scholar] [CrossRef]
- Nour, B.; Mastorakis, S.; Mtibaa, A. Compute-Less Networking: Perspectives, Challenges, and Opportunities. IEEE Netw. 2020, 34, 259–265. [Google Scholar] [CrossRef]
- Senyo, P.K.; Addae, E.; Boateng, R. Cloud Computing Research: A Review of Research Themes, Frameworks, Methods and Future Research Directions. Int. J. Inf. Manag. 2018, 38, 128–139. [Google Scholar] [CrossRef]
- Cavalcante, E.; Pereira, J.; Alves, M.P.; Maia, P.; Moura, R.; Batista, T.; Delicato, F.C.; Pires, P.F. On the Interplay of Internet of Things and Cloud Computing: A Systematic Mapping Study. Comput. Commun. 2016, 89–90, 17–33. [Google Scholar] [CrossRef]
- Botta, A.; de Donato, W.; Persico, V.; Pescapé, A. Integration of Cloud Computing and Internet of Things: A Survey. Future Gener. Comput. Syst. 2016, 56, 684–700. [Google Scholar] [CrossRef]
- Almolhis, N.; Alashjaee, A.M.; Duraibi, S.; Alqahtani, F.; Moussa, A.N. The Security Issues in IoT—Cloud: A Review. In Proceedings of the 2020 16th IEEE International Colloquium on Signal Processing & Its Applications (CSPA), Langkawi, Malaysia, 28–29 February 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 191–196. [Google Scholar]
- Hurbungs, V.; Bassoo, V.; Fowdur, T.P. Fog and Edge Computing: Concepts, Tools and Focus Areas. Int. J. Inf. Technol. 2021, 13, 511–522. [Google Scholar] [CrossRef]
- Varghese, B.; Wang, N.; Barbhuiya, S.; Kilpatrick, P.; Nikolopoulos, D.S. Challenges and Opportunities in Edge Computing. In Proceedings of the International Conference on Smart Cloud, New York, NY, USA, 18–20 November 2016; IEEE: Piscataway, NJ, USA, 2016. [Google Scholar]
- Hao, Z.; Novak, E.; Yi, S.; Li, Q. Challenges and Software Architecture for Fog Computing. IEEE Internet Comput. 2017, 21, 44–53. [Google Scholar] [CrossRef]
- Du, J.; Zhao, L.; Feng, J.; Chu, X. Computation Offloading and Resource Allocation in Mixed Fog/Cloud Computing Systems with Min-Max Fairness Guarantee. IEEE Trans. Commun. 2018, 66, 1594–1608. [Google Scholar] [CrossRef]
- Yangui, S.; Ravindran, P.; Bibani, O.; Glitho, R.H.; Ben Hadj-Alouane, N.; Morrow, M.J.; Polakos, P.A. A Platform as-a-Service for Hybrid Cloud/Fog Environments. In Proceedings of the 2016 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Rome, Italy, 13–15 June 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–7. [Google Scholar]
- Harth, N.; Delakouridis, K.; Anagnostopoulos, C. Convey Intelligence to Edge Aggregation Analytics. In New Advances in the Internet of Things; Yager, R.R., Pascual Espada, J., Eds.; Studies in Computational Intelligence; Springer International Publishing: Cham, Switzerland, 2018; Volume 715, pp. 25–44. ISBN 978-3-319-58189-7. [Google Scholar]
- Ferdowsi, A.; Challita, U.; Saad, W. Deep Learning for Reliable Mobile Edge Analytics in Intelligent Transportation Systems: An Overview. IEEE Veh. Technol. Mag. 2019, 14, 62–70. [Google Scholar] [CrossRef]
- Roman, R.; Lopez, J.; Mambo, M. Mobile Edge Computing, Fog et al.: A Survey and Analysis of Security Threats and Challenges. Future Gener. Comput. Syst. 2018, 78, 680–698. [Google Scholar] [CrossRef]
- Dsouza, C.; Ahn, G.-J.; Taguinod, M. Policy-Driven Security Management for Fog Computing: Preliminary Framework and a Case Study. In Proceedings of the 2014 IEEE 15th International Conference on Information Reuse and Integration (IEEE IRI 2014), Redwood City, CA, USA, 13–15 August 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 16–23. [Google Scholar]
- Ibrahim, M.H. Octopus: An Edge-Fog Mutual Authentication Scheme. Int. J. Netw. Secur. 2016, 18, 1089–1101. [Google Scholar]
- Rejiba, Z.; Masip-Bruin, X.; Marin-Tordera, E. Towards a Context-Aware Wi-Fi-Based Fog Node Discovery Scheme Using Cellular Footprints. In Proceedings of the 2018 14th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Limassol, Cyprus, 15–17 October 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Venanzi, R.; Kantarci, B.; Foschini, L.; Bellavista, P. MQTT-Driven Sustainable Node Discovery for Internet of Things-Fog Environments. In Proceedings of the 2018 IEEE International Conference on Communications (ICC), Kansas City, MO, USA, 20–24 May 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Dautov, R.; Distefano, S.; Bruneo, D.; Longo, F.; Merlino, G.; Puliafito, A. Data Processing in Cyber-Physical-Social Systems through Edge Computing. IEEE Access 2018, 6, 29822–29835. [Google Scholar] [CrossRef]
- Brogi, A.; Forti, S. QoS-Aware Deployment of IoT Applications through the Fog. IEEE Internet Things J. 2017, 4, 1185–1192. [Google Scholar] [CrossRef]
- Skarlat, O.; Nardelli, M.; Schulte, S.; Dustdar, S. Towards QoS-Aware Fog Service Placement. In Proceedings of the 2017 IEEE 1st International Conference on Fog and Edge Computing (ICFEC), Madrid, Spain, 14–15 May 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 89–96. [Google Scholar]
- Yousefpour, A.; Patil, A.; Ishigaki, G.; Kim, I.; Wang, X.; Cankaya, H.C.; Zhang, Q.; Xie, W.; Jue, J.P. FOGPLAN: A Lightweight QoS-Aware Dynamic Fog Service Provisioning Framework. IEEE Internet Things J. 2019, 6, 5080–5096. [Google Scholar] [CrossRef]
- Toczé, K.; Nadjm-Tehrani, S. A Taxonomy for Management and Optimization of Multiple Resources in Edge Computing. Wirel. Commun. Mob. Comput. 2018, 2018, 7476201. [Google Scholar] [CrossRef]
- Negash, B.; Rahmani, A.M.; Liljeberg, P.; Jantsch, A. Fog Computing fundamentals in the Internet-of-Things. In Fog Computing in the Internet of Things; Springer: Cham, Switzerland, 2018; pp. 3–13. [Google Scholar]
- Bittencourt, L.; Immich, R.; Sakellariou, R.; Fonseca, N.; Madeira, E.; Curado, M.; Villas, L.; DaSilva, L.; Lee, C.; Rana, O. The Internet of Things, Fog and Cloud Continuum: Integration and Challenges. Internet Things 2018, 3–4, 134–155. [Google Scholar] [CrossRef]
- Marjani, M.; Nasaruddin, F.; Abdullah, G.; Karim, A.; Hashem, I.; Siddiqa, A.; Yaqoob, I. Big IoT data analytics: Architecture, opportunities, and open research challenges. IEEE Access 2017, 5, 5247–5261. [Google Scholar]
- Díaz-de-Arcaya, J.; Miñon, R.; Torre-Bastida, A.I. Towards an Architecture for Big Data Analytics Leveraging Edge/Fog Paradigms. In Proceedings of the 13th European Conference on Software Architecture—ECSA, Paris, France, 9–13 September 2019; ACM Press: New York, NY, USA, 2019; Volume 2, pp. 173–176. [Google Scholar]
- Bilal, K.; Khalid, O.; Erbad, A.; Khan, S.U. Potentials, Trends, and Prospects in Edge Technologies: Fog, Cloudlet, Mobile Edge, and Micro Data Centers. Comput. Netw. 2018, 130, 94–120. [Google Scholar] [CrossRef] [Green Version]
- Ali, O.; Ishak, M.K.; Bhatti, M.K.L.; Khan, I.; Kim, K.-I. A Comprehensive Review of Internet of Things: Technology Stack, Middlewares, and Fog/Edge Computing Interface. Sensors 2022, 22, 995. [Google Scholar] [CrossRef] [PubMed]
- Chen, C.; Cook, D.J.; Crandall, A.S. The User Side of Sustainability: Modeling Behavior and Energy Usage in the Home. Pervasive Mob. Comput. 2013, 9, 161–175. [Google Scholar] [CrossRef]
- De Carvalho, L.R.; Patricia Favacho de Araujo, A. Performance Comparison of Terraform and Cloudify as Multicloud Orchestrators. In Proceedings of the 2020 20th IEEE/ACM International Symposium on Cluster, Cloud and Internet Computing (CCGRID), Melbourne, Australia, 11–14 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 380–389. [Google Scholar]
- Rosa, M.J.F.; Araujo, A.P.F.; Mendes, F.L.S. Cost and Time Prediction for Efficient Execution of Bioinformatics Workflows in Federated Cloud. In Proceedings of the 2018 IEEE International Conference on Bioinformatics and Biomedicine (BIBM), Madrid, Spain, 3–6 December 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1703–1710. [Google Scholar]
- Faragardi, H.R.; Vahabi, M.; Fotouhi, H.; Nolte, T.; Fahringer, T. An Efficient Placement of Sinks and SDN Controller Nodes for Optimizing the Design Cost of Industrial IoT Systems: Sink-Controller Placement in Industrial IoT Systems. Softw. Pract. Exper. 2018, 48, 1893–1919. [Google Scholar] [CrossRef]
- Rullo, A.; Serra, E.; Bertino, E.; Lobo, J. Optimal Placement of Security Resources for the Internet of Things. In The Internet of Things for Smart Urban Ecosystems; Cicirelli, F., Guerrieri, A., Mastroianni, C., Spezzano, G., Vinci, A., Eds.; Internet of Things; Springer International Publishing: Cham, Switzerland, 2019; pp. 95–124. ISBN 978-3-319-96549-9. [Google Scholar]
- Kumar, S.; Chaurasiya, V.K. A Strategy for Elimination of Data Redundancy in Internet of Things (IoT) Based Wireless Sensor Network (WSN). IEEE Syst. J. 2019, 13, 1650–1657. [Google Scholar] [CrossRef]
- Asensio, A.; Masip-Bruin, X.; Durán, R.J.; de Miguel, I.; Ren, G.; Daijavad, S.; Jukan, A. Designing an Efficient Clustering Strategy for Combined Fog-to-Cloud Scenarios. Future Gener. Comput. Syst. 2020, 109, 392–406. [Google Scholar] [CrossRef]
- Columbus, L. 2018 roundup of Internet of things forecasts and market estimates. Forbes 2018. Available online: https://www.forbes.com/sites/louiscolumbus/2018/12/13/2018-roundup-of-internet-of-things-forecasts-and-market-estimates/ (accessed on 18 April 2022).
- Newman, P. IoT report: How Internet of things technology growth is reaching mainstream companies and consumers. Business Insider 2019, 28. Available online: https://www.businessinsider.in/tech/news/iot-report-how-internet-of-things-technology-growth-is-reaching-mainstream-companies-and-consumers/articleshow/73133090.cms (accessed on 19 April 2022).
- Shah, D.R.; Dhawan, D.A.; Thoday, V. An Overview on Security Challenges in Cloud, Fog, and Edge Computing. In Data Science and Security; Shukla, S., Gao, X.-Z., Kureethara, J.V., Mishra, D., Eds.; Lecture Notes in Networks and Systems; Springer: Singapore, 2022; Volume 462, pp. 337–345. ISBN 978-981-19221-0-7. [Google Scholar]
- Shim, J.P.; Sharda, R.; French, A.M.; Syler, R.A.; Patten, K.P. The Internet of Things: Multi-Faceted Research Perspectives. CAIS 2020, 46, 511–536. [Google Scholar] [CrossRef]
- Cheng, B.; Kovacs, E.; Kitazawa, A.; Terasawa, K.; Hada, T.; Takeuchi, M. FogFlow: Orchestrating IoT services over cloud and edges. NEC Tech. J. 2018, 13, 48–53. [Google Scholar]
- Zanzi, L.; Giust, F.; Sciancalepore, V. M2EC: A Multi-Tenant Resource Orchestration in Multi-Access Edge Computing Systems. In Proceedings of the 2018 IEEE Wireless Communications and Networking Conference (WCNC), Barcelona, Spain, 15–18 April 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Avasalcai, C.; Dustdar, S. Latency-Aware Decentralized Resource Management for IoT Applications. In Proceedings of the 8th International Conference on the Internet of Things, Santa Barbara, CA, USA, 15 October 2018; ACM: New York, NY, USA, 2018; pp. 1–4. [Google Scholar]
- Daoud, W.B.; Obaidat, M.S.; Meddeb-Makhlouf, A.; Zarai, F.; Hsiao, K.-F. TACRM: Trust Access Control and Resource Management Mechanism in Fog Computing. Hum. Centric Comput. Inf. Sci. 2019, 9, 28. [Google Scholar] [CrossRef]
- Donassolo, B.; Fajjari, I.; Legrand, A.; Mertikopoulos, P. Fog Based Framework for IoT Service Provisioning. In Proceedings of the 2019 16th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Gedeon, J.; Zengerle, S.; Alles, S.; Brandherm, F.; Muhlhauser, M. Sunstone: Navigating the Way through the Fog. In Proceedings of the 2020 IEEE 4th International Conference on Fog and Edge Computing (ICFEC), Melbourne, Australia, 11–14 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 49–58. [Google Scholar]
- Salem, A.; Nadeem, T. LAMEN: Towards Orchestrating the Growing Intelligence on the Edge. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 508–513. [Google Scholar]
- Wang, N.; Varghese, B.; Matthaiou, M.; Nikolopoulos, D.S. ENORM: A Framework For Edge NOde Resource Management. IEEE Trans. Serv. Comput. 2017, 13, 1086–1099. [Google Scholar] [CrossRef]
- Majeed, A.A.; Kilpatrick, P.; Spence, I.; Varghese, B. Modelling Fog Offloading Performance. In Proceedings of the 2020 IEEE 4th International Conference on Fog and Edge Computing (ICFEC), Melbourne, Australia, 11–14 May 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 29–38. [Google Scholar]
- Javaid, S.; Javaid, N.; Saba, T.; Wadud, Z.; Rehman, A.; Haseeb, A. Intelligent Resource Allocation in Residential Buildings Using Consumer to Fog to Cloud Based Framework. Energies 2019, 12, 815. [Google Scholar] [CrossRef]
- Jalali, F.; Lynar, T.; Smith, O.J.; Kolluri, R.R.; Hardgrove, C.V.; Waywood, N.; Suits, F. Dynamic Edge Fabric EnvironmenT: Seamless and Automatic Switching among Resources at the Edge of IoT Network and Cloud. In Proceedings of the 2019 IEEE International Conference on Edge Computing (EDGE), Milan, Italy, 8–13 July 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 77–86. [Google Scholar]
- Nath, S.B.; Chattopadhyay, S.; Karmakar, R.; Addya, S.K.; Chakraborty, S.; Ghosh, S.K. PTC: Pick-Test-Choose to Place Containerized Micro-Services in IoT. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 1–6. [Google Scholar]
- Östberg, P.-O.; Byrne, J.; Casari, P.; Eardley, P.; Anta, A.F.; Forsman, J.; Kennedy, J.; Le Duc, T.; Marino, M.N.; Loomba, R.; et al. Reliable Capacity Provisioning for Distributed Cloud/Edge/Fog Computing Applications. In Proceedings of the 2017 European Conference on Networks and Communications (EuCNC), Oulu, Finland, 12–15 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Wamser, F.; Lombardo, C.; Vassilakis, C.; Dinh-Xuan, L.; Lago, P.; Bruschi, R.; Tran-Gia, P. Orchestration and Monitoring in Fog Computing for Personal Edge Cloud Service Support. In Proceedings of the 2018 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Washington, DC, USA, 25–27 June 2018; IEEE: Piscataway, NJ, USA, 2018; pp. 91–96. [Google Scholar]
- Yigitoglu, E.; Liu, L.; Looper, M.; Pu, C. Distributed Orchestration in Large-Scale IoT Systems. In Proceedings of the 2017 IEEE International Congress on Internet of Things (ICIOT), Honolulu, HI, USA, 25–30 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 58–65. [Google Scholar]
- Viswanathan, H.; Pandey, P.; Pompili, D. Maestro: Orchestrating Concurrent Application Workflows in Mobile Device Clouds. In Proceedings of the 2016 IEEE International Conference on Autonomic Computing (ICAC), Wuerzburg, Germany, 17–22 July 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 257–262. [Google Scholar]
- Cozzolino, V.; Ott, J.; Ding, A.Y.; Mortier, R. ECCO: Edge-Cloud Chaining and Orchestration Framework for Road Context Assessment. In Proceedings of the 2020 IEEE/ACM Fifth International Conference on Internet-of-Things Design and Implementation (IoTDI), Sydney, Australia, 21–24 April 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 223–230. [Google Scholar]
- Gogouvitis, S.V.; Mueller, H.; Premnadh, S.; Seitz, A.; Bruegge, B. Seamless Computing in Industrial Systems Using Container Orchestration. Future Gener. Comput. Syst. 2020, 109, 678–688. [Google Scholar] [CrossRef]
- Etemadi, M.; Ghobaei-Arani, M.; Shahidinejad, A. A Cost-Efficient Auto-Scaling Mechanism for IoT Applications in Fog Computing Environment: A Deep Learning-Based Approach. Clust. Comput. 2021, 24, 3277–3292. [Google Scholar] [CrossRef]
- Pradhan, S.; Dubey, A.; Khare, S.; Nannapaneni, S.; Gokhale, A.; Mahadevan, S.; Schmidt, D.C.; Lehofer, M. CHARIOT: Goal-Driven Orchestration Middleware for Resilient IoT Systems. ACM Trans. Cyber Phys. Syst. 2018, 2, 1–37. [Google Scholar] [CrossRef]
- Pahl, C.; Ioini, N.E.; Helmer, S.; Lee, B. An Architecture Pattern for Trusted Orchestration in IoT Edge Clouds. In Proceedings of the 2018 Third International Conference on Fog and Mobile Edge Computing (FMEC), Barcelona, Spain, 23–26 April 2018; pp. 63–70. [Google Scholar]
- Van Lingen, F.; Yannuzzi, M.; Jain, A.; Irons-Mclean, R.; Lluch, O.; Carrera, D.; Perez, J.L.; Gutierrez, A.; Montero, D.; Marti, J.; et al. The Unavoidable Convergence of NFV, 5G, and Fog: A Model-Driven Approach to Bridge Cloud and Edge. IEEE Commun. Mag. 2017, 55, 28–35. [Google Scholar] [CrossRef]
- Takefuji, Y. Connected Vehicle Security Vulnerabilities [Commentary]. IEEE Technol. Soc. Mag. 2018, 37, 15–18. [Google Scholar] [CrossRef]
- Hossain, M.M.; Fotouhi, M.; Hasan, R. Towards an Analysis of Security Issues, Challenges, and Open Problems in the Internet of Things. In Proceedings of the 2015 IEEE World Congress on Services, New York, NY, USA, 27 June–2 July 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 21–28. [Google Scholar]
- Suárez-Albela, M.; Fernández-Caramés, T.; Fraga-Lamas, P.; Castedo, L. A Practical Evaluation of a High-Security Energy-Efficient Gateway for IoT Fog Computing Applications. Sensors 2017, 17, 1978. [Google Scholar] [CrossRef]
- Martin, J.P.; Kandasamy, A.; Chandrasekaran, K.; Joseph, C.T. Elucidating the Challenges for the Praxis of Fog Computing: An Aspect-Based Study. Int. J. Commun. Syst. 2019, 32, e3926. [Google Scholar] [CrossRef]
- Wen, Z.; Yang, R.; Garraghan, P.; Lin, T.; Xu, J.; Rovatsos, M. Fog orchestration for Internet of Things services. IEEE Internet Comput. 2017, 21, 16–24. [Google Scholar] [CrossRef]
- Aazam, M.; Zeadally, S.; Harras, K.A. Offloading in Fog Computing for IoT: Review, Enabling Technologies, and Research Opportunities. Future Gener. Comput. Syst. 2018, 87, 278–289. [Google Scholar] [CrossRef]
- Agarwal, Y.; Dey, A.K. Toward Building a Safe, Secure, and Easy-to-Use Internet of Things Infrastructure. Computer 2016, 49, 88–91. [Google Scholar] [CrossRef]
- Wolf, V.; Stumpf-Wollersheim, J.; Schott, L. The Internet of Things in a Business Context: Implications with Respect to Value Creation, Value Drivers, and Value Capturing. In Digital Entrepreneurship; Baierl, R., Behrens, J., Brem, A., Eds.; FGF Studies in Small Business and Entrepreneurship; Springer International Publishing: Cham, Switzerland, 2019; pp. 185–197. ISBN 978-3-030-20137-1. [Google Scholar]
- Osterwalder, A.; Pigneur, Y.; Tucci, C.L. Clarifying Business Models: Origins, Present, and Future of the Concept. CAIS 2005, 16, 1. [Google Scholar] [CrossRef] [Green Version]
- Zott, C.; Amit, R.; Massa, L. The Business Model: Recent Developments and Future Research. J. Manag. 2011, 37, 1019–1042. [Google Scholar]
- Kindström, D. Towards a Service-Based Business Model—Key Aspects for Future Competitive Advantage. Eur. Manag. J. 2010, 28, 479–490. [Google Scholar] [CrossRef]
- Agostini, L.; Nosella, A. Industry 4.0 and Business Models: A Bibliometric Literature Review. BPMJ 2021, 27, 1633–1655. [Google Scholar] [CrossRef]
- Hagen, S.; Thomas, O. Expectations vs. Reality—Benefits of Smart Services in the Field of Tension between Industry and Science. In Proceedings of the 14th International Conference on Wirtschaftsinformatik, Siegen, Germany, 24–27 February 2019; pp. 647–660. [Google Scholar]
- Van der Vegte, W.F. Taking Advantage of Data Generated by Products: Trends, Opportunities and Challenges. In Proceedings of the ASME 2016 International Design Engineering Technical Conferences and Computers and Information in Engineering Conference, Charlotte, NC, USA, 21–24 August 2016; Volume 36. [Google Scholar]
- Siggelkow, N.; Terwiesch, C. The Age of Continuous Connection. Harv. Bus. Rev. 2019, 97, 64–73. [Google Scholar]
- Beverungen, D.; Müller, O.; Matzner, M.; Mendling, J.; vom Brocke, J. Conceptualizing Smart Service Systems. Electron. Mark. 2019, 29, 7–18. [Google Scholar] [CrossRef]
- Gimpel, G. Bringing Dark Data into the Light: Illuminating Existing IoT Data Lost within Your Organization. Bus. Horiz. 2020, 63, 519–530. [Google Scholar] [CrossRef]
- Bucherer, E.; Uckelmann, D. Business Models for the Internet of Things. In Architecting the Internet of Things; Springer: Berlin/Heidelberg, Germany, 2011; pp. 253–277. [Google Scholar]
- Santoro, G.; Vrontis, D.; Thrassou, A.; Dezi, L. The Internet of Things: Building a Knowledge Management System for Open Innovation and Knowledge Management Capacity. Technol. Forecast. Soc. Chang. 2018, 136, 347–354. [Google Scholar] [CrossRef]
- Teece, D.J.; Pisano, G.; Shuen, A. Dynamic Capabilities and Strategic Management. Strateg. Manag. J. 1997, 18, 509–533. [Google Scholar] [CrossRef]
- Pavlou, P.A.; El Sawy, O.A. The “Third Hand”: IT-Enabled Competitive Advantage in Turbulence through Improvisational Capabilities. Inf. Syst. Res. 2010, 21, 443–471. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).