Analysis of Insider Threats in the Healthcare Industry: A Text Mining Approach
Abstract
:1. Introduction
2. Related Works
3. Research Methodology
3.1. Step1: Data Collection
3.2. Step 2: Data Pre-Processing and Cleaning
3.3. Step 3: Segmentation of Data
3.4. Step 4: Measurement of Keyword Co-Occurrences and Clustering of the Keywords
3.5. Step 5: Analysis of Descriptions of Data Breaches
4. Analysis of Data Breach Types
4.1. Analysis of Hacking/IT Incident
4.2. Analysis of Theft
5. Conclusions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Vora, J.; Italiya, P.; Tanwar, S.; Tyagi, S.; Kumar, N.; Obaidat, M.S.; Hsiao, K.F. Ensuring Privacy and Security in E-Health Records. In Proceedings of the 2018 International Conference on Computer, Information and Telecommunication Systems (CITS), Colmar, France, 11–13 July 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Bowman, M.A.; Maxwell, R.A. A beginner’s guide to avoiding Protected Health Information (PHI) issues in clinical research—With how-to’s in REDCap Data Management Software. J. Biomed. Inform. 2018, 85, 49–55. [Google Scholar] [CrossRef] [PubMed]
- Bai, G.; Jiang, J.X.; Flasher, R. Hospital Risk of Data Breaches. JAMA Intern. Med. 2017, 177, 878–880. [Google Scholar] [CrossRef] [PubMed]
- Choi, S.; Martins, J.T.; Bernik, I. Information security: Listening to the perspective of organisational insiders. J. Inf. Sci. 2018, 44, 752–767. [Google Scholar] [CrossRef]
- In Healthcare, Breach Dangers Come from inside the House. Modern Healthcare, 9 April 2018. Available online: https://www.modernhealthcare.com/article/20180410/NEWS/180419999/in-healthcare-breach-dangers-come-from-inside-the-house (accessed on 24 January 2022).
- Capital One Says Breach Hit 100 Million Individuals in U.S. Bloomberg, 29 July 2019. Available online: https://www.bloomberg.com/news/articles/2019-07-29/capital-one-data-systems-breached-by-seattle-woman-u-s-says (accessed on 15 February 2022).
- Security Tracker 2018. Available online: https://www.shredit.com/en-us/resource-center/original-research/security-tracker-2018 (accessed on 24 January 2022).
- Yaraghi, N.; Gopal, R.D. The Role of HIPAA Omnibus Rules in Reducing the Frequency of Medical Data Breaches: Insights from an Empirical Study. Milbank Q. 2018, 96, 144–166. [Google Scholar] [CrossRef]
- McCoy, T.H.; Perlis, R.H. Temporal Trends and Characteristics of Reportable Health Data Breaches, 2010–2017. JAMA 2018, 320, 1282–1284. [Google Scholar] [CrossRef]
- Gabriel, M.H.; Noblin, A.; Rutherford, A.; Walden, A.; Cortelyou-Ward, K. Data breach locations, types, and associated characteristics among US hospitals. Am. J. Manag. Care 2018, 24, 78–84. [Google Scholar]
- Ayyagari, R. An Exploratory Analysis of Data Breaches from 2005–2011: Trends and Insights. J. Inf. Priv. Secur. 2012, 8, 33–56. [Google Scholar] [CrossRef]
- Wikina, S.B. What Caused the Breach? An Examination of Use of Information Technology and Health Data Breaches. Perspect. Health Inf. Manag. 2014, 11, PMC4272442. [Google Scholar]
- Elbattah, M.; Arnaud, É.; Gignon, M.; Dequen, G. The Role of Text Analytics in Healthcare: A Review of Recent Developments and Applications. August 2022, pp. 825–832. Available online: https://www.scitepress.org/Link.aspx?doi=10.5220/0010414508250832 (accessed on 13 July 2022).
- Xue, J.; Chen, J.; Chen, C.; Zheng, C.; Li, S.; Zhu, T. Public discourse and sentiment during the COVID-19 pandemic: Using Latent Dirichlet Allocation for topic modeling on Twitter. PLoS ONE 2020, 15, e0239441. [Google Scholar] [CrossRef]
- Gourisaria, M.K.; Chandra, S.; Das, H.; Patra, S.S.; Sahni, M.; Leon-Castro, E.; Singh, V.; Kumar, S. Semantic Analysis and Topic Modelling of Web-Scrapped COVID-19 Tweet Corpora through Data Mining Methodologies. Healthcare 2022, 10, 881. [Google Scholar] [CrossRef]
- Chakraborty, K.; Bhatia, S.; Bhattacharyya, S.; Platos, J.; Bag, R.; Hassanien, A.E. Sentiment Analysis of COVID-19 tweets by Deep Learning Classifiers—A study to show how popularity is affecting accuracy in social media. Appl. Soft Comput. 2020, 97, 106754. [Google Scholar] [CrossRef] [PubMed]
- Imran, A.S.; Daudpota, S.M.; Kastrati, Z.; Batra, R. Cross-Cultural Polarity and Emotion Detection Using Sentiment Analysis and Deep Learning on COVID-19 Related Tweets. IEEE Access 2020, 8, 181074–181090. [Google Scholar] [CrossRef]
- CERT Definition of ‘Insider Threat’—Updated. SEI Blog. Available online: https://insights.sei.cmu.edu/blog/cert-definition-of-insider-threat-updated/ (accessed on 19 July 2022).
- Dang, Q.-V. Intrusion Detection in Software-Defined Networks. In Future Data and Security Engineering; Springer: Cham, Switzerland, 2021; pp. 356–371. [Google Scholar] [CrossRef]
- Alkadi, O.; Moustafa, N.; Turnbull, B. A Review of Intrusion Detection and Blockchain Applications in the Cloud: Approaches, Challenges and Solutions. IEEE Access 2020, 8, 104893–104917. [Google Scholar] [CrossRef]
- Ellerby, Z.; McCulloch, J.; Wilson, M.; Wagner, C. Exploring How Component Factors and Their Uncertainty Affect Judgements of Risk in Cyber-Security. In Critical Information Infrastructures Security; Springer: Cham, Switzerland, 2020; pp. 31–42. [Google Scholar] [CrossRef]
- Al-Mhiqani, M.N.; Ahmad, R.; Zainal Abidin, Z.; Yassin, W.; Hassan, A.; Abdulkareem, K.H.; Ali, N.S.; Yunos, Z. A Review of Insider Threat Detection: Classification, Machine Learning Techniques, Datasets, Open Challenges, and Recommendations. Appl. Sci. 2020, 10, 5208. [Google Scholar] [CrossRef]
- Homoliak, I.; Toffalini, F.; Guarnizo, J.; Elovici, Y.; Ochoa, M. Insight into Insiders and IT: A Survey of Insider Threat Taxonomies, Analysis, Modeling, and Countermeasures. ACM Comput. Surv. 2019, 52, 30:1–30:40. [Google Scholar] [CrossRef]
- Soh, C.; Yu, S.; Narayanan, A.; Duraisamy, S.; Chen, L. Employee profiling via aspect-based sentiment and network for insider threats detection. Expert Syst. Appl. 2019, 135, 351–361. [Google Scholar] [CrossRef]
- Saxena, N.; Hayes, E.; Bertino, E.; Ojo, P.; Choo, K.-K.R.; Burnap, P. Impact and Key Challenges of Insider Threats on Organizations and Critical Businesses. Electronics 2020, 9, 1460. [Google Scholar] [CrossRef]
- Ajayi, O.; Abouali, M.; Saadawi, T. Secured Inter-Healthcare Patient Health Records Exchange Architecture. In Proceedings of the 2020 IEEE International Conference on Blockchain (Blockchain), Rhodes, Greece, 2–6 November 2020; pp. 456–461. [Google Scholar] [CrossRef]
- Nathiya, T.; Suseendran, G. An Effective Hybrid Intrusion Detection System for Use in Security Monitoring in the Virtual Network Layer of Cloud Computing Technology. In Data Management, Analytics and Innovation; Springer: Singapore, 2019; pp. 483–497. [Google Scholar] [CrossRef]
- Deep, G.; Mohana, R.; Nayyar, A.; Sanjeevikumar, P.; Hossain, E. Authentication Protocol for Cloud Databases Using Blockchain Mechanism. Sensors 2019, 19, 4444. [Google Scholar] [CrossRef]
- Prabhu, S.; Thompson, N. A primer on insider threats in cybersecurity. Inf. Secur. J. A Glob. Perspect. 2021, 2021, 1971802. [Google Scholar] [CrossRef]
- Gunasekhar, T.; Rao, K.T.; Basu, M.T. Understanding insider attack problem and scope in cloud. In Proceedings of the 2015 International Conference on Circuits, Power and Computing Technologies [ICCPCT-2015], Nagercoil, India, 19–20 March 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Liu, L.; de Vel, O.; Han, Q.-L.; Zhang, J.; Xiang, Y. Detecting and Preventing Cyber Insider Threats: A Survey. IEEE Commun. Surv. Tutor. 2018, 20, 1397–1417. [Google Scholar] [CrossRef]
- Yen, T.F.; Oprea, A.; Onarlioglu, K.; Leetham, T.; Robertson, W.; Juels, A.; Kirda, E. Beehive: Large-scale log analysis for detecting suspicious activity in enterprise networks. In Proceedings of the 29th Annual Computer Security Applications Conference, New Orleans, LA, USA, 9–13 December 2013; pp. 199–208. [Google Scholar] [CrossRef]
- Allodi, L.; Massacci, F. Security Events and Vulnerability Data for Cybersecurity Risk Estimation. Risk Anal. 2017, 37, 1606–1627. [Google Scholar] [CrossRef] [PubMed]
- Malatji, M.; Marnewick, A.; von Solms, S. Validation of a socio-technical management process for optimising cybersecurity practices. Comput. Secur. 2020, 95, 101846. [Google Scholar] [CrossRef]
- Švábenský, V.; Čeleda, P.; Vykopal, J.; Brišáková, S. Cybersecurity knowledge and skills taught in capture the flag challenges. Comput. Secur. 2021, 102, 102154. [Google Scholar] [CrossRef]
- Esteves, J.; Ramalho, E.; de Haro, G. To Improve Cybersecurity, Think Like a Hacker. MIT Sloan Manag. Rev. 2017, 58, 71–77. [Google Scholar]
- Jeremiah, P.; Samy, G.N.; Shanmugam, B.; Ponkoodalingam, K.; Perumal, S. Potential Measures to Enhance Information Security Compliance in the Healthcare Internet of Things. In Recent Trends in Data Science and Soft Computing; Springer: Cham, Switzerland, 2019; pp. 726–735. [Google Scholar] [CrossRef]
- Dorasamy, M.; Joanis, G.C.; Jiun, L.W.; Jambulingam, M.; Samsudin, R.; Cheng, N.J. Cybersecurity Issues Among Working Youths in an IoT Environment: A Design Thinking Process for Solution. In Proceedings of the 2019 6th International Conference on Research and Innovation in Information Systems (ICRIIS), Johor Bahru, Malaysia, 2–3 December 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Dang-Pham, D.; Pittayachawan, S.; Bruno, V. Impacts of security climate on employees’ sharing of security advice and troubleshooting: Empirical networks. Bus. Horiz. 2016, 59, 571–584. [Google Scholar] [CrossRef]
- Yeng, P.K.; Fauzi, M.A.; Yang, B. A Comprehensive Assessment of Human Factors in Cyber Security Compliance toward Enhancing the Security Practice of Healthcare Staff in Paperless Hospitals. Information 2022, 13, 335. [Google Scholar] [CrossRef]
- Hughes-Lartey, K.; Qin, Z.; Botchey, F.E.; Dsane-Nsor, S. An Assessment of Data Location Vulnerability for Human Factors Using Linear Regression and Collaborative Filtering. Information 2020, 11, 449. [Google Scholar] [CrossRef]
- Rothrock, R.A.; Kaplan, J.; van der Oord, F. The Board’s Role in Managing Cybersecurity Risks. MIT Sloan Manag. Rev. 2018, 59, 12–15. [Google Scholar]
- Hasan, S.; Ali, M.; Kurnia, S.; Thurasamy, R. Evaluating the cyber security readiness of organizations and its influence on performance. J. Inf. Secur. Appl. 2021, 58, 102726. [Google Scholar] [CrossRef]
- Sharma, S.; Warkentin, M. Do I really belong? Impact of employment status on information security policy compliance. Comput. Secur. 2019, 87, 101397. [Google Scholar] [CrossRef]
- AlGhamdi, S.; Win, K.T.; Vlahu-Gjorgievska, E. Information security governance challenges and critical success factors: Systematic review. Comput. Secur. 2020, 99, 102030. [Google Scholar] [CrossRef]
- Nasir, A.; Arshah, R.A.; Hamid, M.R.A.; Fahmy, S. An analysis on the dimensions of information security culture concept: A review. J. Inf. Secur. Appl. 2019, 44, 12–22. [Google Scholar] [CrossRef]
- Georgiadou, A.; Mouzakitis, S.; Bounas, K.; Askounis, D. A Cyber-Security Culture Framework for Assessing Organization Readiness. J. Comput. Inf. Syst. 2020, 2020, 1845583. [Google Scholar] [CrossRef]
- Bodeau, D.J.; Graubart, R.D. Cyber Prep 2.0: Motivating Organizational Cyber Strategies in Terms of Threat Preparedness. February 2017. Available online: https://www.mitre.org/publications/technical-papers/cyber-prep-20-motivating-organizational-cyber-strategies-in-terms-of (accessed on 24 January 2022).
- Villegas-Ch, W.; Ortiz-Garces, I.; Sánchez-Viteri, S. Proposal for an Implementation Guide for a Computer Security Incident Response Team on a University Campus. Computers 2021, 10, 102. [Google Scholar] [CrossRef]
- Ani, U.P.D.; He, H.M.; Tiwari, A. Review of cybersecurity issues in industrial critical infrastructure: Manufacturing in perspective. J. Cyber Secur. Technol. 2017, 1, 32–74. [Google Scholar] [CrossRef] [Green Version]
- Shojaeshafiei, M.; Etzkorn, L.; Anderson, M. Cybersecurity Framework Requirements to Quantify Vulnerabilities Based on GQM. In National Cyber Summit (NCS) Research Track; Springer: Cham, Switzerland, 2020; pp. 264–277. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- O. for C. Rights (OCR). Breach Notification Rule. HHS, 14 September 2009. Available online: https://www.hhs.gov/hipaa/for-professionals/breach-notification/index.html (accessed on 2 May 2022).
- van Eck, N.J.; Waltman, L. VOSviewer Manual. p. 51. Available online: https://www.vosviewer.com/documentation/Manual_VOSviewer_1.6.8.pdf (accessed on 5 May 2022).
- Unintentional Insider Threats: A Foundational Study. Available online: https://resources.sei.cmu.edu/library/asset-view.cfm?assetid=58744 (accessed on 13 July 2022).
- Moore, A.P.; Cappelli, D.M.; Trzeciak, R.F. The ‘Big Picture’ of Insider IT Sabotage Across U.S. Critical Infrastructures. In Insider Attack and Cyber Security; Springer: Boston, MA, USA, 2008; p. 46. [Google Scholar]
- December 2021 Healthcare Data Breach Report. HIPAA Journal, 18 January 2022. Available online: https://www.hipaajournal.com/december-2021-healthcare-data-breach-report/ (accessed on 15 February 2022).
- IBM Report: Cost of a Data Breach Hits Record High During Pandemic. IBM Newsroom. Available online: https://newsroom.ibm.com/2021-07-28-IBM-Report-Cost-of-a-Data-Breach-Hits-Record-High-During-Pandemic (accessed on 15 February 2022).
- 2021 Data Breach Investigations Report. Verizon Business. Available online: https://www.verizon.com/business/resources/reports/dbir/ (accessed on 15 February 2022).
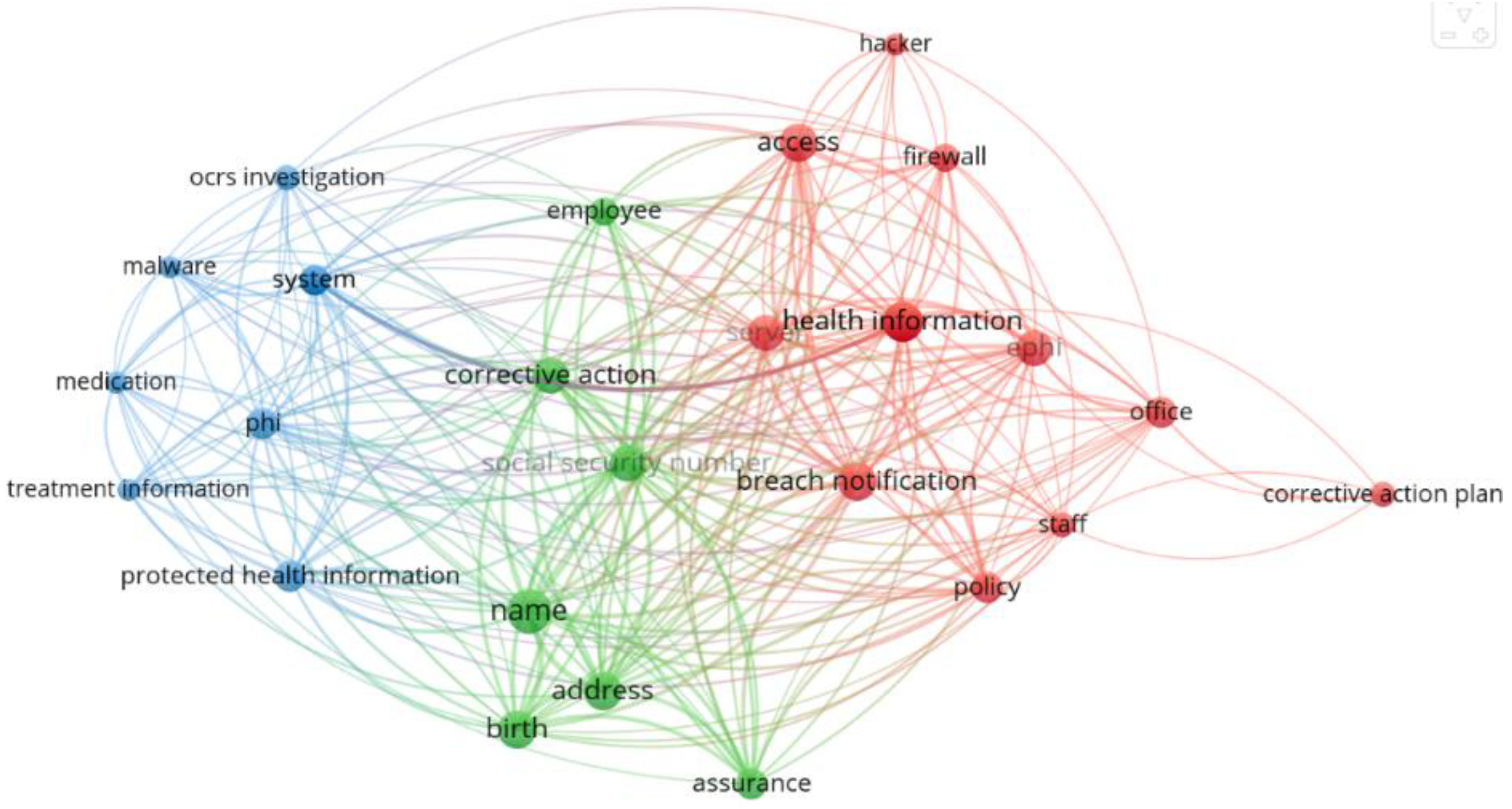
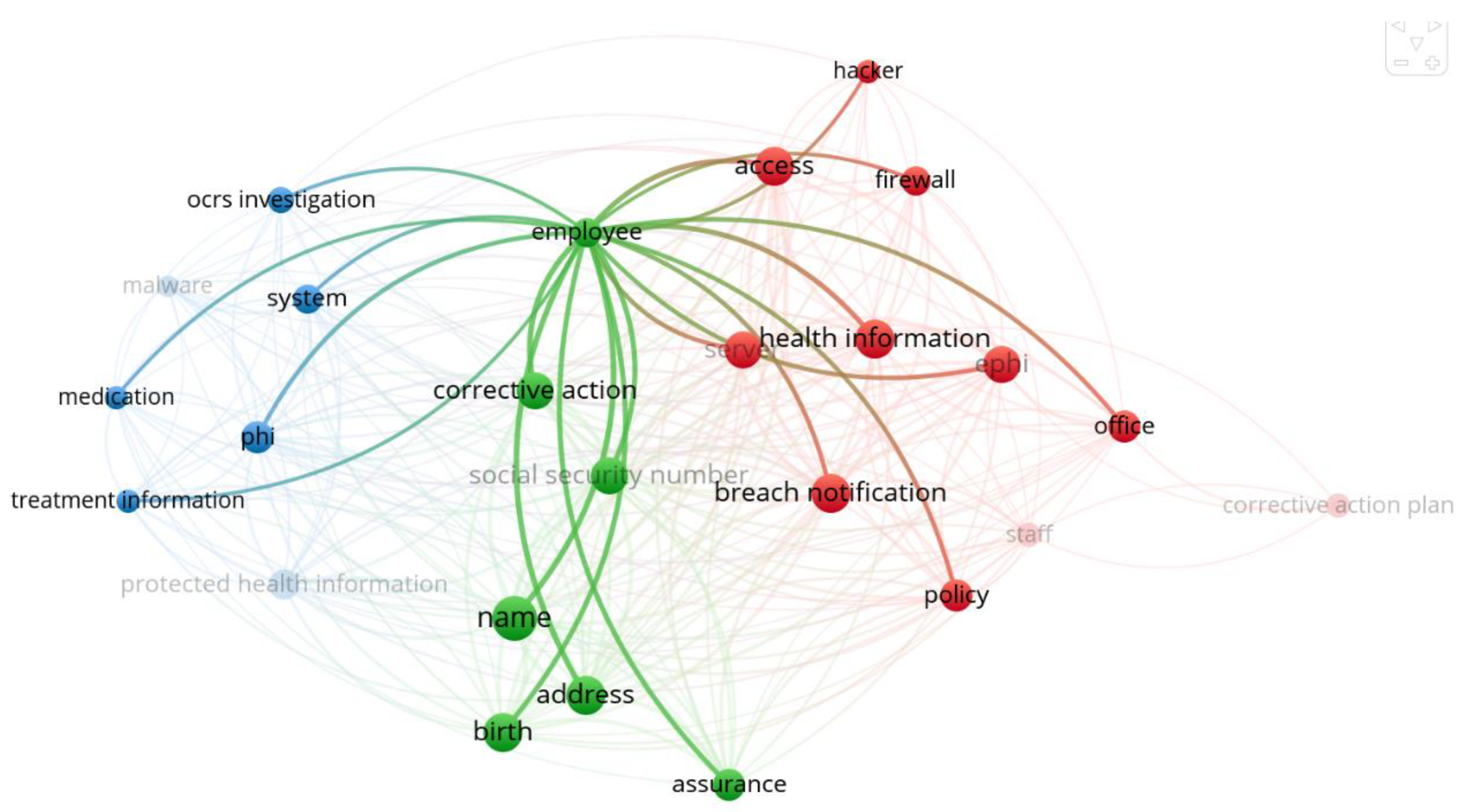
| Period 1 | Period 2 | Period 3 |
|---|---|---|
| 25 items (3 clusters) | 25 items (3 clusters) | 27 items (3 clusters) |
| Cluster 1 (11 items) | Cluster 1 (10 items) | Cluster 1 (13 items) |
| access | address | access |
| breach notification | assurance | assurance |
| corrective action plan | birth | clinical information |
| ephi | breach notification | computer server |
| firewall | corrective action | corrective action |
| hacker | employee | ephi |
| health information | name | health information |
| office | phi | policy |
| policy | protected health information | ransomware |
| server | social security number | ransomware attack |
| staff | risk analysis | |
| safeguard | ||
| server | ||
| Cluster 2 (7 items) | Cluster 2 (9 items) | Cluster 2 (8 items) |
| address | clinical information | breach notification |
| assurance | ephi | business associate |
| birth | health information | employee |
| corrective action | malware | ocrs investigation |
| employee | ocrs investigation | phi |
| name | policy | protected health information |
| social security number | risk analysis | technical assistance |
| staff | technical safeguard | |
| technical assistance | ||
| Cluster 3 (7 items) | Cluster 3 (6 items) | Cluster 3 (6 items) |
| malware | business associate | address |
| medication | computer server | birth |
| ocrs investigation | diagnosis | name |
| phi | server | social security number |
| protected health information | treatment information | unauthorized user |
| system | unauthorized access | workforce member |
| treatment information |
| Hacking/IT Incident | Cluster | Insider/Outsider Threats | Vulnerabilities | Breach Incidents | Impacts | Responses |
|---|---|---|---|---|---|---|
| Period 1 | Cluster 1 | hacker; staff | lack of firewall; weak security control | hacking | ePHI; health information | a settlement with the OCR; corrective action plan |
| Cluster 2 | employee | lack of a security management process | email phishing | date of birth; name; social security number | risk analysis; corrective action; a settlement with OCR | |
| Cluster 3 | unknown outsider | unencrypted software; lack of technical security measures | malware | medication; PHI; treatment information | OCR’s investigation; security software to detect, prevent, and mitigate malware on computers | |
| Period 2 | Cluster 1 | employee | lack of social engineering awareness | email phishing | address; date of birth; name; PHI; social security number | assurance of corrective action; software to scan Internet addresses in employees’ emails |
| Cluster 2 | staff | weak safeguards for a system | malware | ePHI; health information | technical assistance by OCR; risk analysis; OCR’s investigation; upgraded antivirus software | |
| Cluster 3 | business associate | weak security control | unauthorized access to the system | diagnosis; treatment information | identity recovery services; stricter password policies; the installation of an active traffic-monitoring solution for its network | |
| Period 3 | Cluster 1 | ransomware attacker | weak firewall system; open firewall port | ransomware | clinical information; ePHI health information | risk analysis; replacement of firewall; anti-malware software; assurance of corrective action; revised policy and procedures |
| Cluster 2 | business associate; employee | malicious partners (e.g., vendors); lack of security awareness of employee | email phishing, impermissible access to PHI | PHI | OCR’s investigation; technical assistance by OCR; technical safeguard to PHI | |
| Cluster 3 | workforce member | lack of social engineering awareness | email phishing | address; date of birth; name; social security number | improved safeguards; updated policies and procedures; training of its workforce members on better practices to safeguard PHI |
| Period 1 | Period 2 | Period 3 |
|---|---|---|
| 26 items (3 clusters) | 25 items (2 clusters) | 24 items (3 clusters) |
| Cluster 1 (12 items) | Cluster 1 (13 items) | Cluster 1 (12 items) |
| computer | address | assurance |
| encryption | assurance | breach notification |
| ephi | birth | clinical information |
| health information | breach notification | computer |
| laptop | corrective action | corrective action |
| laptop computer | employee | employee |
| physical security | laptop computer | ocrs investigation |
| police report | name | phi |
| policy | phi | physical security |
| risk analysis | protected health information | policy |
| safeguard | social security number | protected health information |
| workforce member | staff | substitute notice |
| substitute notice | ||
| Cluster 2 (8 items) | Cluster 2 (12 items) | Cluster 2 (9 items) |
| assurance | computer | address |
| breach notification | diagnosis | birth |
| corrective action | ephi | ephi |
| employee | health information | health information |
| phi | laptop | laptop |
| privacy | ocrs investigation | laptop computer |
| protected health information | password | name |
| staff | policy | social security number |
| safeguard | workforce member | |
| technical assistance | ||
| unencrypted laptop | ||
| workforce member | ||
| Cluster 3 (6 items) | Cluster 3 (3 items) | |
| address | diagnosis | |
| birth | medical record number | |
| diagnosis | staff | |
| name | ||
| ocrs investigation | ||
| social security number |
| Theft | Cluster | Insider/Outsider Threats | Vulnerabilities | Breach Incidents | Impacts | Responses |
|---|---|---|---|---|---|---|
| Period 1 | Cluster 1 | workforce member | deficiencies in HIPAA compliance program; unencrypted laptop computer; weak physical security; unencrypted ePHI; negligence of employees | theft of laptop and computer | health information; ePHI | The settlement with OCR; encryption of laptop computers; ongoing security awareness training for all staff; enhanced physical security; risk analysis; comprehensive compliance program |
| Cluster 2 | employees; staff | negligence of employees | theft of laptop and computer | PHI | retraining of all staff on privacy and security policies and procedures; remote access policy; electronic data backup policy | |
| Cluster 3 | employees | unencrypted portable computer drive; unencrypted desktop computer; malicious employees; unsecured disposal of PHI | theft of medical files | address; date of birth; name; social security number; diagnosis | encryption-capable USB drives; securely locked storage facilities for mobile devices; policies preventing the removal of devices from the office | |
| Period 2 | Cluster 1 | employee; staff | unencrypted laptop; unencrypted ePHI | theft of laptop | address; date of birth; name; social security number; PHI | assurance of corrective action; encryption of all unencrypted electronic devices; update of the policy on safeguarding ePHI |
| Cluster 2 | workforce member | unencrypted laptop; unencrypted desktop computer; backup computer hard drive | theft of laptop and desktop | diagnosis; health information | technical assistance by OCR; procedures for safeguarding mobile devices; retraining of the employee on the physical security of laptops; retraining of relevant IT personnel on standard encryption configuration processes; update of password policy; revision of HIPAA policies and procedures | |
| Period 3 | Cluster 1 | employee | unencrypted desktop computer; external computer hard drives | theft of desktop and hard drive | clinical information; PHI | encrypted workstations and computers; enhanced network security; encrypting data at rest on computers; physical safeguards such as surveillance cameras and locks to deter and prevent unauthorized access; complimentary credit monitoring and identity theft protection services |
| Cluster 2 | workforce member | unencrypted hard drive of a laptop; unencrypted external hard drive; negligence of workforce member | theft of hard drive | address; date of birth; name; social security number; ePHI; health information | sanction of its workforce member; update of security rule policy; encryption software on all laptops and media storage devices; retraining of workforce members; encryption of a laptop; a cloud-based electronic health record system; risk analysis | |
| Cluster 3 | staff | negligence of employee; unencrypted laptop | theft of laptops | diagnosis; medical record number | notifying local law enforcement of the breach; retraining staff; blocking the laptop from accessing the internal computer network |
| Period 1 | Period 2 | Period 3 |
|---|---|---|
| 22 items (3 clusters) | 24 items (3 clusters) | 24 items (3 clusters) |
| Cluster 1 (8 items) | Cluster 1 (9 items) | Cluster 1 (11 items) |
| corrective action plan | birth | assurance |
| ephi | clinical information | breach notification |
| health information | diagnosis | corrective action |
| ocrs investigation | employee | |
| policy | ephi | email address |
| risk | health information | ocrs investigation |
| staff | social security number | policy |
| technical assistance | technical assistance | staff |
| workforce member | substitute notice | |
| technical assistance | ||
| workforce member | ||
| Cluster 2 (7 items) | Cluster 2 (8 items) | Cluster 2 (8 items) |
| access | access | address |
| assurance | assurance | birth |
| breach notification | breach notification | business associate |
| corrective action | business associate | diagnosis |
| employee | corrective action | ephi |
| phi | name | health information |
| protected health information | phi | name |
| protected health information | social security number | |
| Cluster 3 (7 items) | Cluster 3 (7 items) | Cluster 3 (5 items) |
| address | address | access |
| birth | clinical information | |
| credit monitoring | ocrs investigation | employee |
| diagnosis | policy | phi |
| name | safeguard | protected health information |
| social security number | staff | |
| workforce member | substitute notice |
| Unauthorized Access/Disclosure | Cluster | Insider/Outsider Threats | Vulnerabilities | Breach Incidents | Impacts | Responses |
|---|---|---|---|---|---|---|
| Period 1 | Cluster 1 | staff | insecure website; malicious staff | unauthorized access to PHI via the public website | ePHI | a settlement to OCR; a corrective action plan |
| Cluster 2 | employee | weak access termination protocol; malicious employee | unauthorized access to an appointment reminder system after employment ended; identity theft | PHI | updated access termination protocol; termination of the offending employee; retraining of the workforce on HIPAA policies; improvement of HIPAA training materials, risk analysis procedure, operation software, and auditing methods | |
| Cluster 3 | workforce member | malicious employee | unauthorized access to patient medical records | PHI | free credit monitoring services for a year; a program to track anomalies to detect inappropriate use or access; termination of the offending employee and criminal charges against him | |
| Period 2 | Cluster 1 | employee; workforce member | malicious employee; negligent physician | suspicious access to ePHI; accidental disclosure of medical files via email | ePHI; medical records; patients’ names and clinical information | assurance of corrective action; termination of the responsible individuals’ employment; employee sanctions according to its policy and procedure |
| Cluster 2 | business associate | a malicious business associate (BA); errors of BA | unauthorized access to PHI; erroneous disclosure of another patient’s name in letters to patients | PHI | employee sanctions; HIPAA refresher training; a new workflow in mailing processes to reduce the number of manual steps | |
| Cluster 3 | staff | errors of a staff member; negligent employee | erroneous emailing; unsecured email file transfer | PHI; email addresses | retraining staff on its encryption policy; a revised policy regarding electronic transmission of patient information; password protection for electronic files; sanction of the staff member, retraining the entire department; revision of email policies | |
| Period 3 | Cluster 1 | staff | errors of employees | disclosure of email address; phishing email | email addresses of patients; PHI; | a secure online portal; training staff; two-factor email authentication; technical assistance by OCR; restricted workforce access to the patient folder; employee sanctions |
| Cluster 2 | business associate | errors of BA; malicious BA; disgruntled former BA; security hole of applications | illegal access to ePHI; mailing error; hacking | ePHI | identity theft protection services to affected individuals; encryption and tools to monitor Internet traffic and compliance | |
| Cluster 3 | workforce member | malicious employee; negligent employee; malicious former employees; insecure records room | impermissibly accessed ePHI as well as paper PHI; access to the records room | demographic and clinical information; ePHI; paper PHI | employee sanctions; revised policy to detect inappropriate access; increased restrictions to access to PHI based on workforce member role and work location; training to all its employees regarding role-based access; measures to improve internal security and limit employee access to records rooms. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, I. Analysis of Insider Threats in the Healthcare Industry: A Text Mining Approach. Information 2022, 13, 404. https://doi.org/10.3390/info13090404
Lee I. Analysis of Insider Threats in the Healthcare Industry: A Text Mining Approach. Information. 2022; 13(9):404. https://doi.org/10.3390/info13090404
Chicago/Turabian StyleLee, In. 2022. "Analysis of Insider Threats in the Healthcare Industry: A Text Mining Approach" Information 13, no. 9: 404. https://doi.org/10.3390/info13090404
APA StyleLee, I. (2022). Analysis of Insider Threats in the Healthcare Industry: A Text Mining Approach. Information, 13(9), 404. https://doi.org/10.3390/info13090404






