SMS-I: Intelligent Security for Cyber–Physical Systems
Abstract
:1. Introduction
- detail the SMS-I tool capabilities. The different components of this investigation tool are fully described in this work, presenting its different features;
- present all the different experiments done regarding the SMS-I Machine Learning Engine. Some of these results are already presented in the previous papers; however, in this work, we detail all the work carried out and the results obtained;
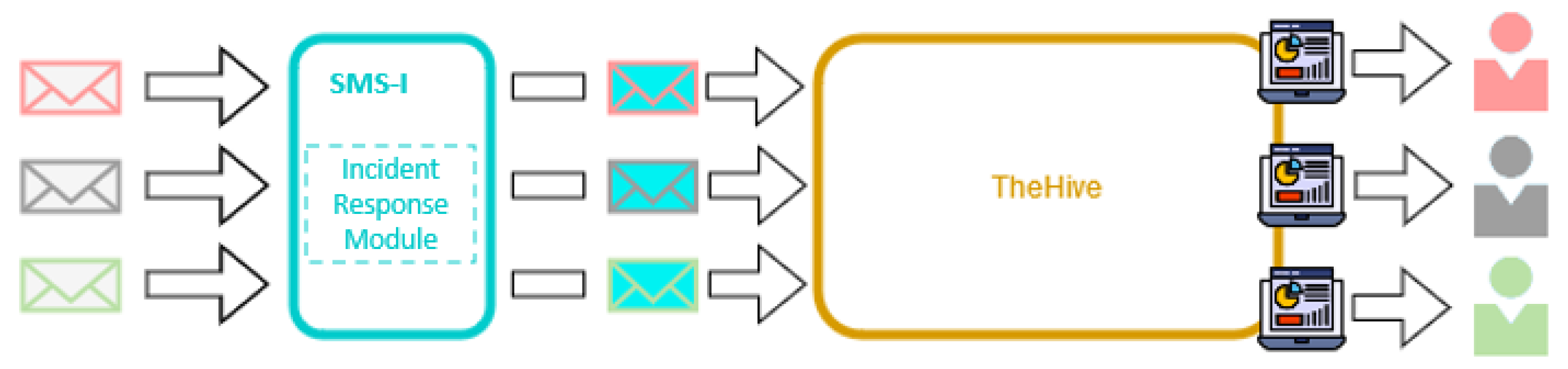
- introduce the Incident response capability of SMS-I tool. This is a new SMS-I capability that promotes the sharing of information between organizations. The integration of this feature with TheHive is also detailed in this work;
- show SMS-I Intelligent dashboard in detail, highlighting the added value for the security analysts of each view;
- demonstrate the convenience and usefulness of the SMS-I tool in the decision-making process of security analysts, using a very simple and realistic example.
2. SMS-I Tool Overview
2.1. SMS-I Integration
- Events are discrete change of state or status of an Asset or group of Assets. They can have multiple heterogeneous sources and are categorized as either cyber or physical, depending on the system that originated them. They contain low-level information about the system’s activity, such as network traffic or baggage handling system data. Specific Events may trigger Alerts.
- Alerts are notifications that a specific attack has been directed at an organization’s information systems. They are triggered when abnormal activity is detected. They are usually related to several Events that have triggered security rules.
- An Incident results from the classification of Alerts by the SOC operator. They represent real identified threats to the system. Additionally, it has some sort of impact within the organization, which is described by its severity and completion level.
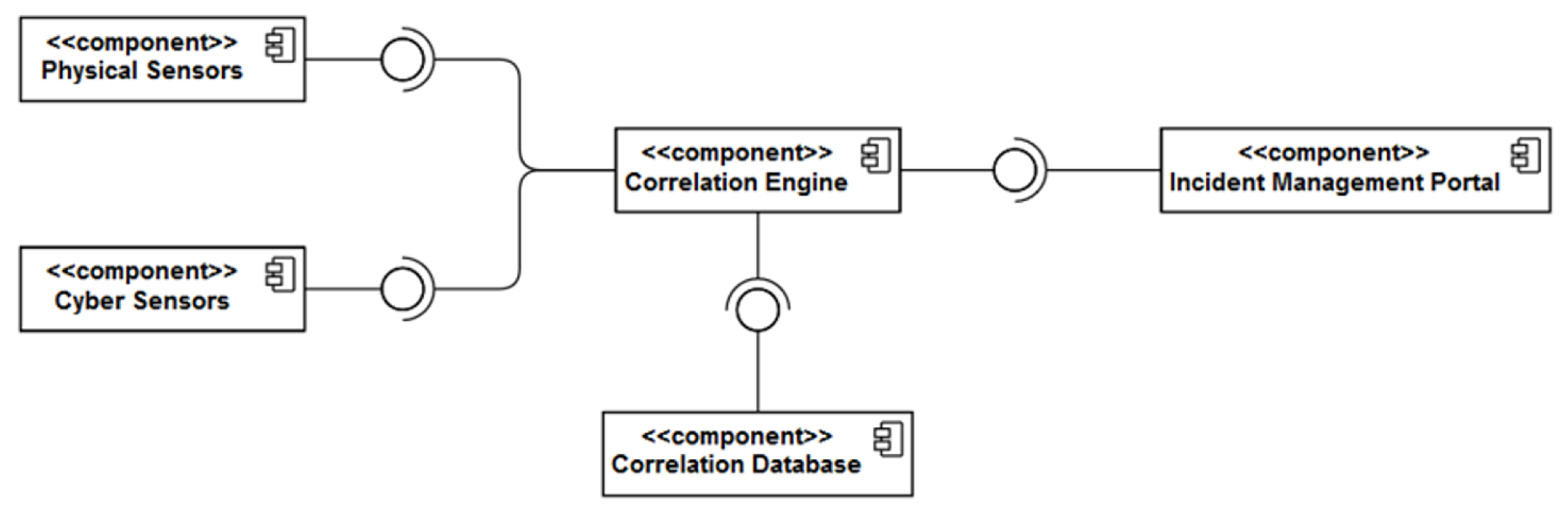
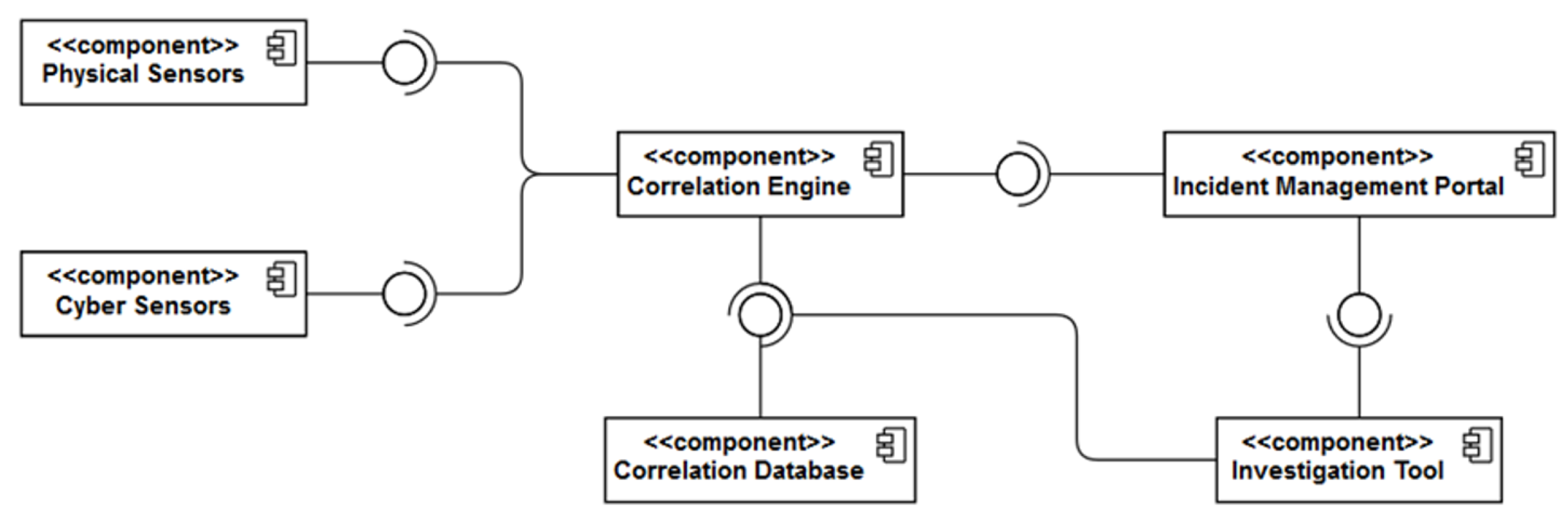
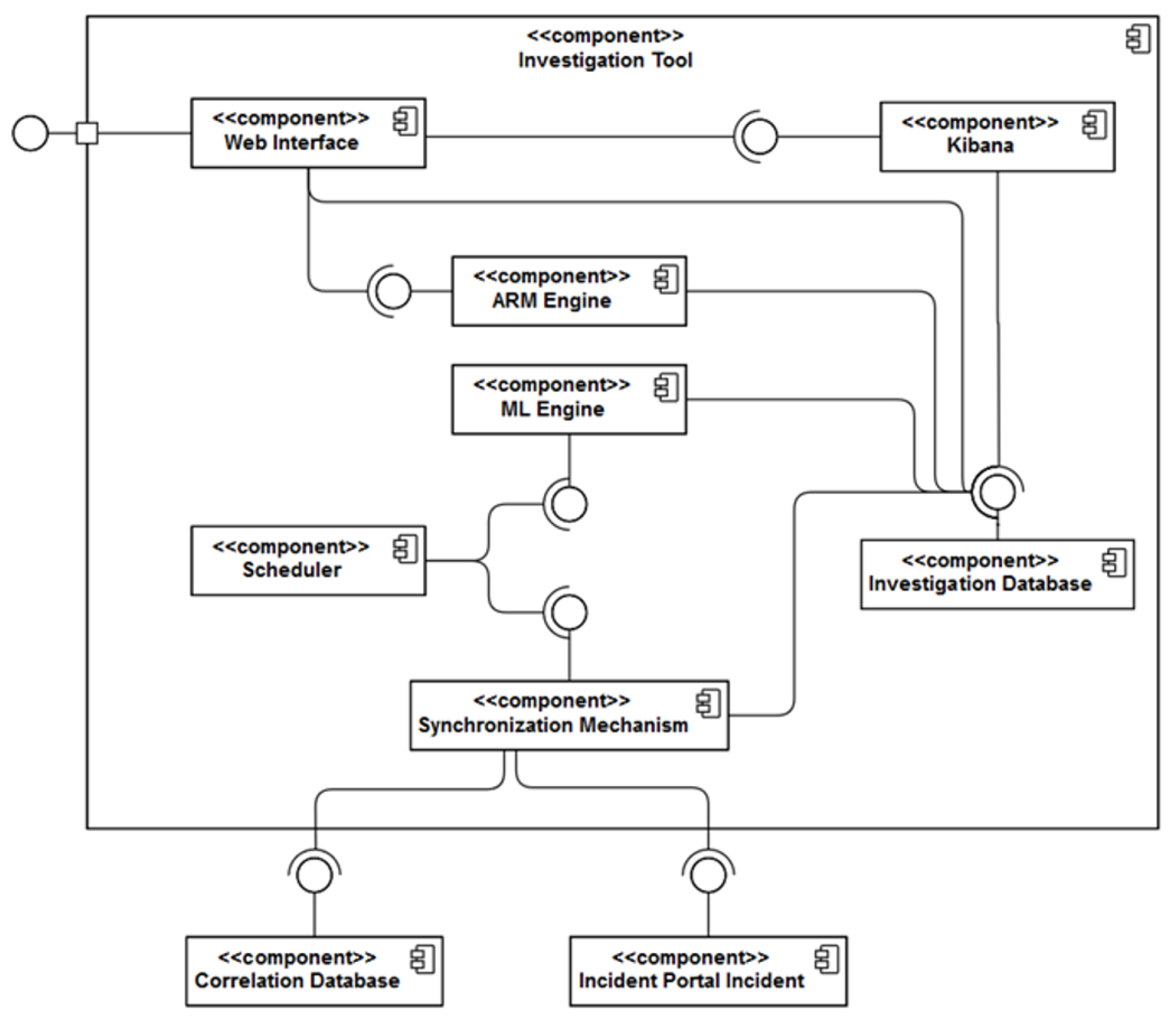
2.2. SMS-I Internal Architecture
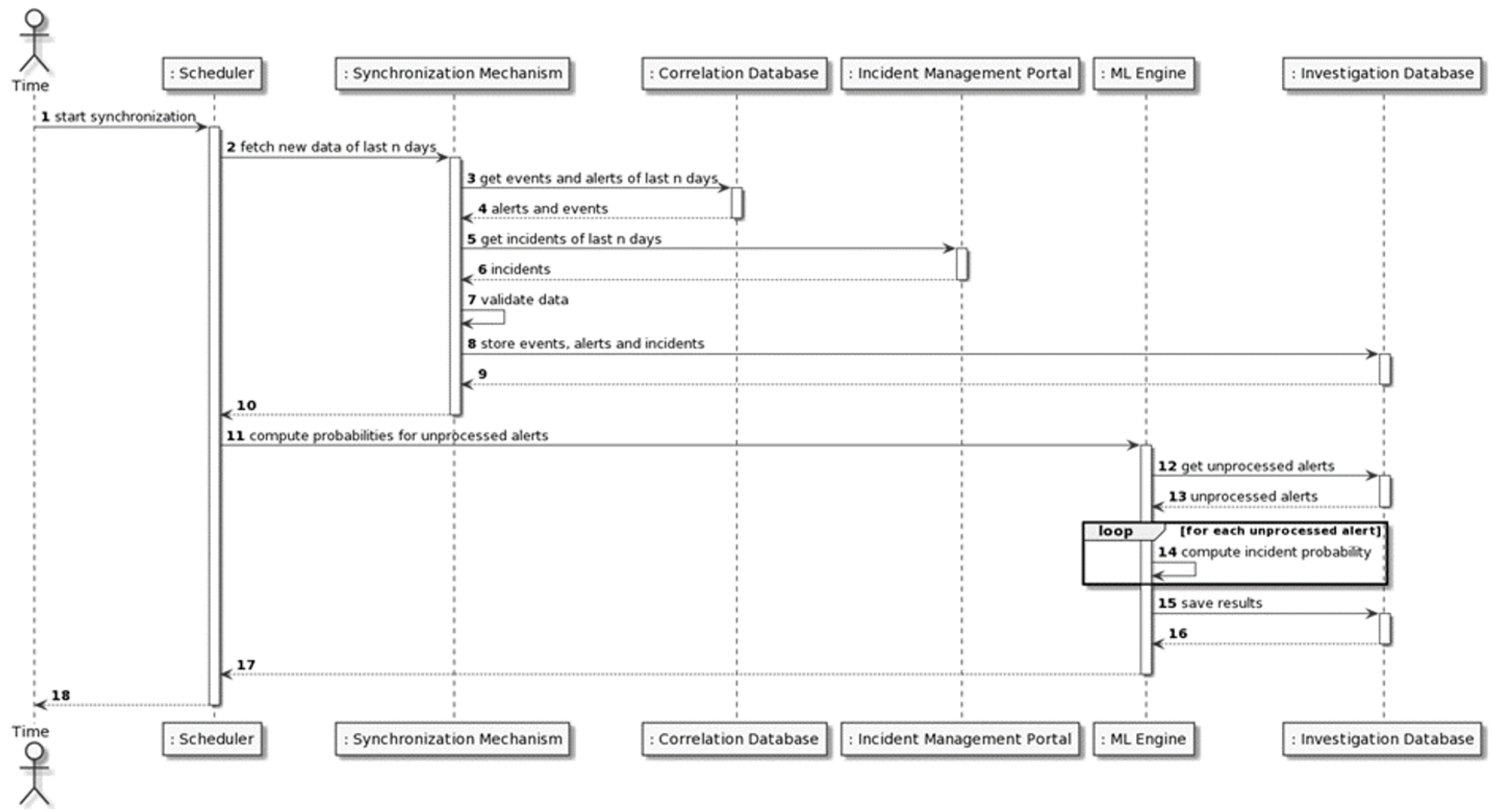
- Synchronization Mechanism: It is the component responsible for acquiring new Events, Alerts and Incidents from the Correlation Engine and the Incident Management Portal, parsing them into predefined formats and storing them into specific indexes of the Investigation Database. The synchronization mechanism is one of the most critical processes of the SMS-I since it allows the system to keep track of the new data generated within the SATIE Environment. Additionally, as new Alerts are added to the database, they are also processed by the ML Engine. The synchronization process is represented in Figure 5.
- ML Engine: The ML Engine is responsible for executing the ML models capable of determining, for each Alert, the probability of it being an Incident based on its own features, features of related Events and the features of other Alerts of a regarded time window. The employed models are expected to grow smarter over time with system usage. The ML engine also analyses the data received from an Incident response point of view, taking into account a collaborative approach and providing confidence scores over other related cases.
- Scheduler: The Scheduler performs the orchestration of both Synchronization Mechanism and ML Engine by triggering their execution by a configurable time constraint (e.g., every five minutes, every hour, every day).
- ARM Engine: The Association Rule Mining (ARM) Engine provides an API endpoint for executing rule mining algorithms on the Investigation Database data according to a set of parameters specified in the request header. It retrieves the list of generated rules.
- Investigation Database: It corresponds to an Elastic Search database that stores all system data—Events, Alerts, Incidents, ML probabilities and association rules.
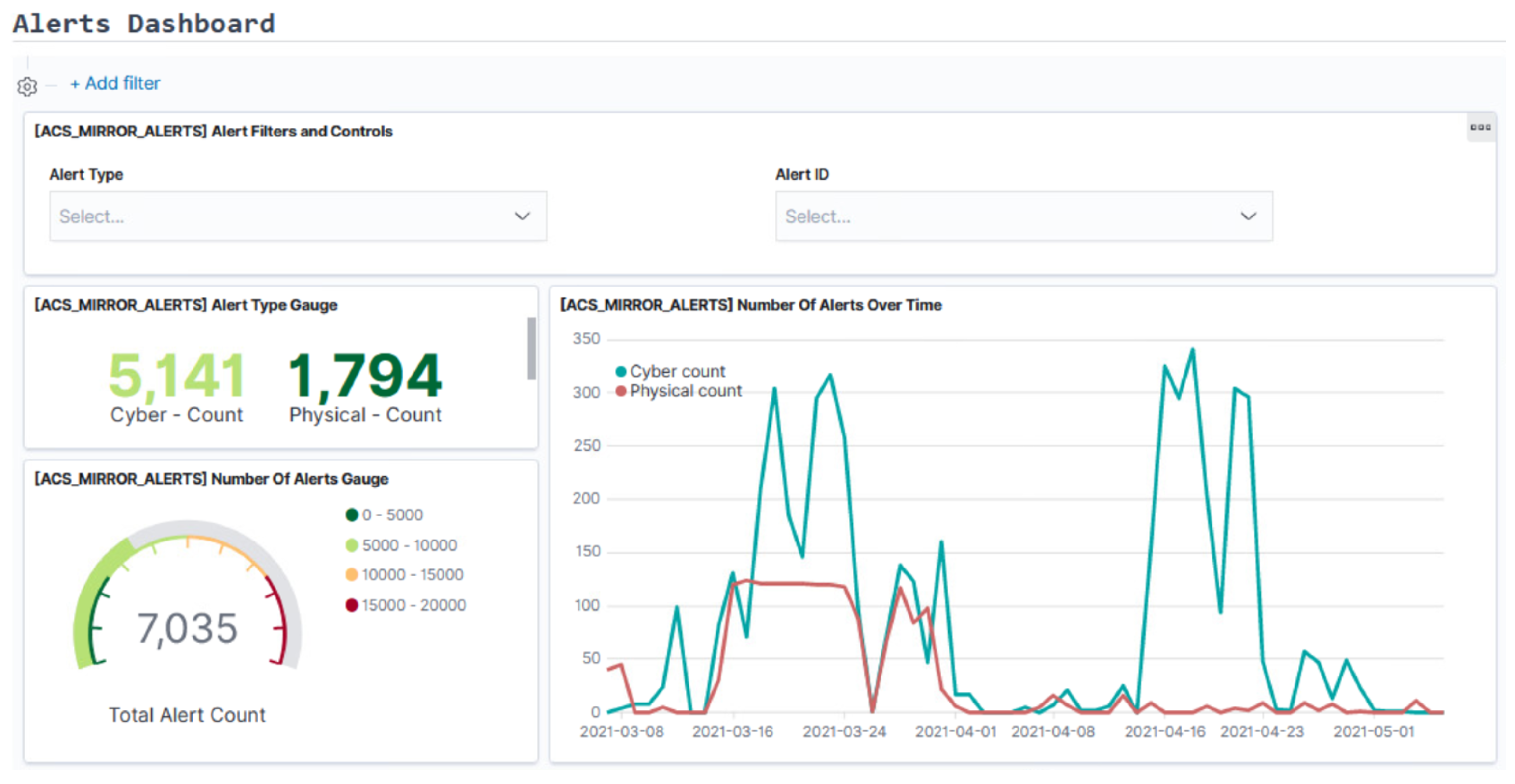
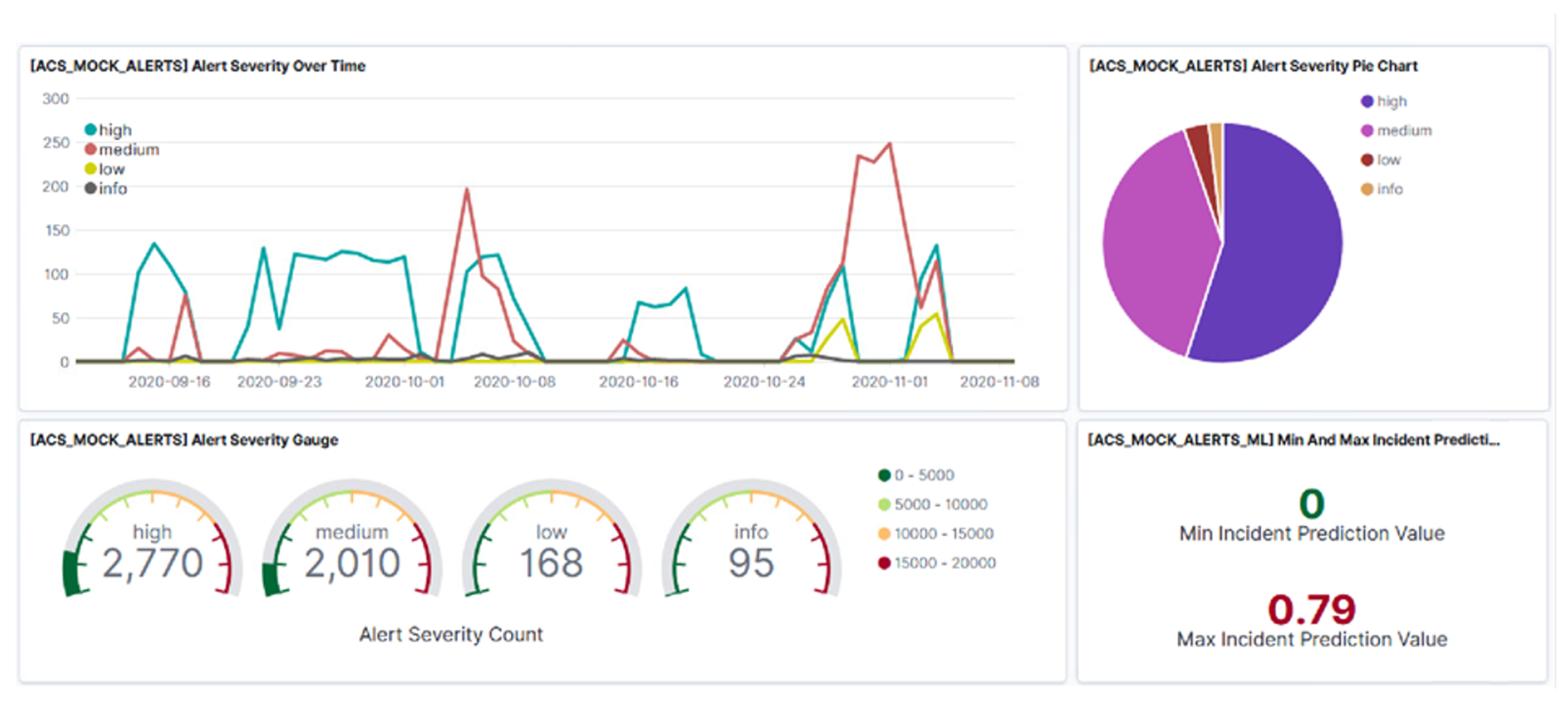
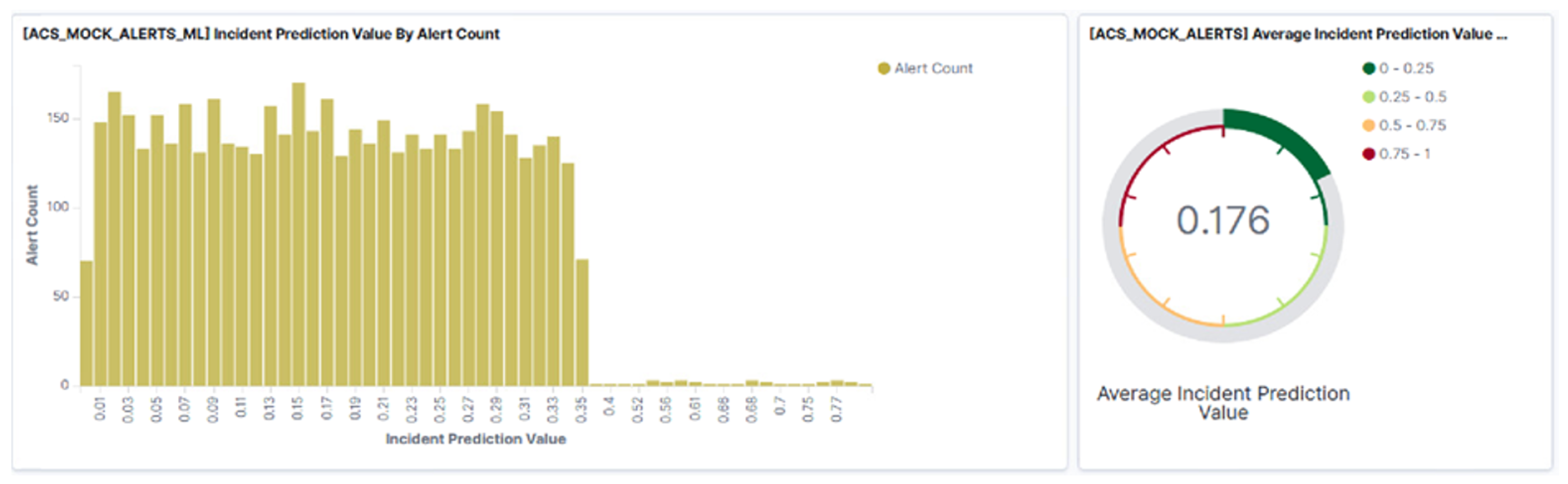
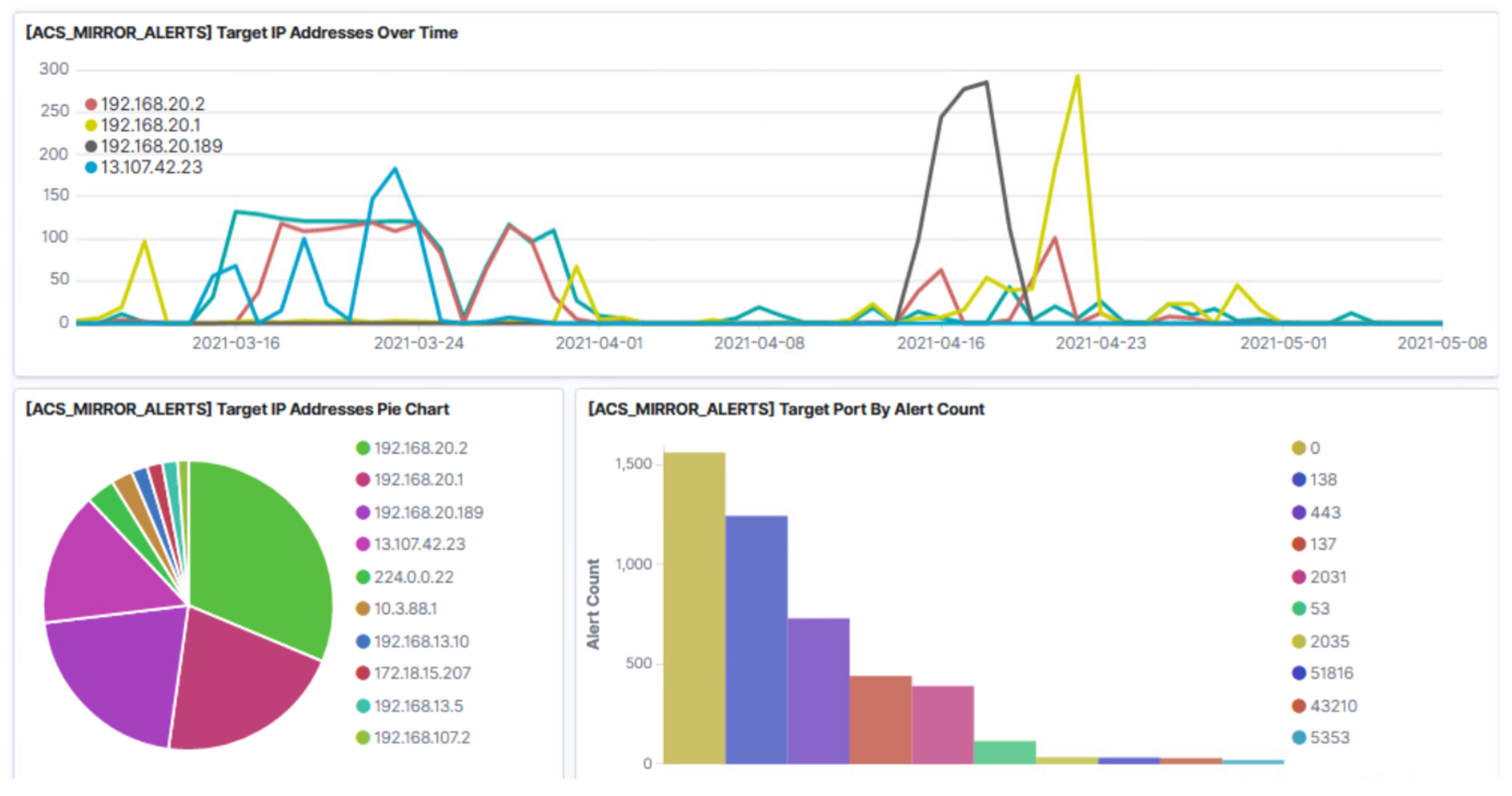
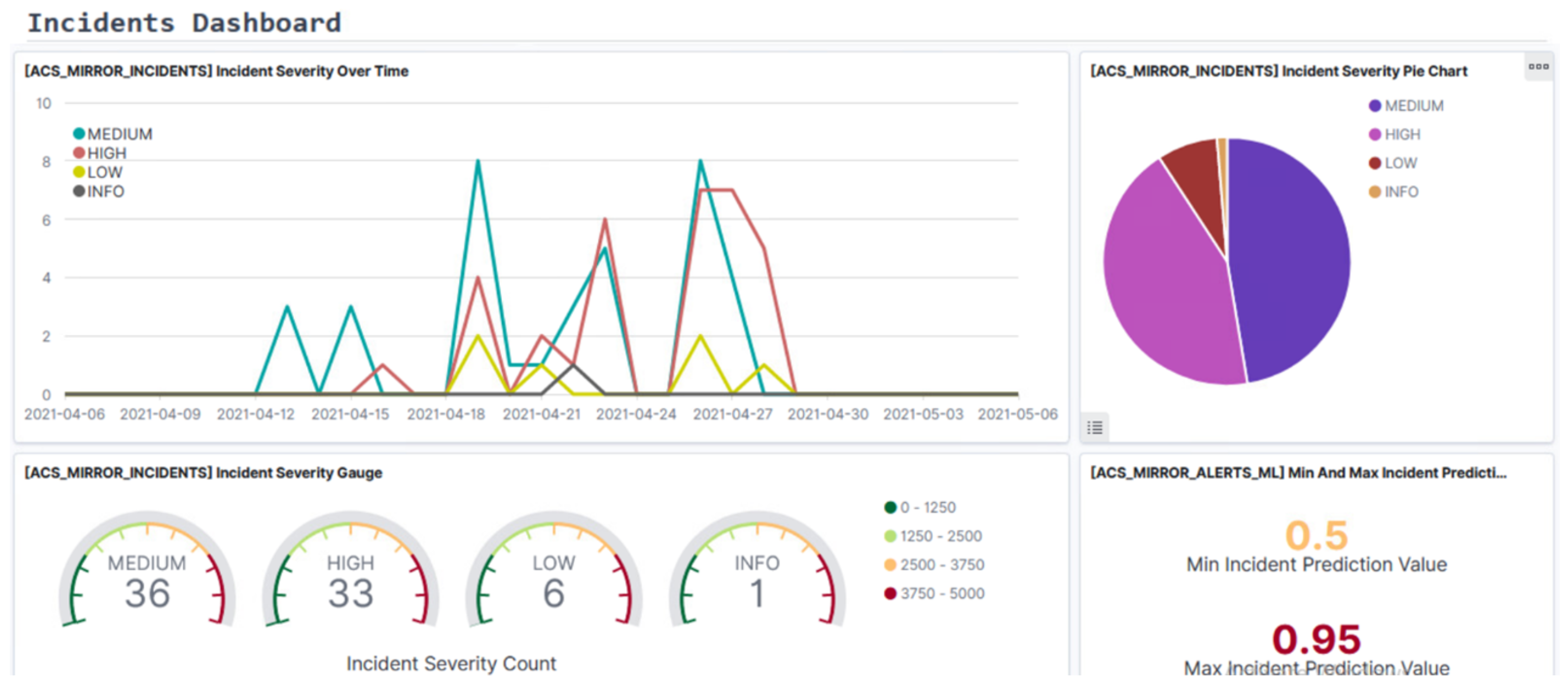
- Kibana: It is part of the ELK Stack and can be described as an interface to the Investigation Database. It provides several methods to build interesting visualizations that are combined to produce intuitive and informative dashboards for inspecting the system’s behaviour over time.
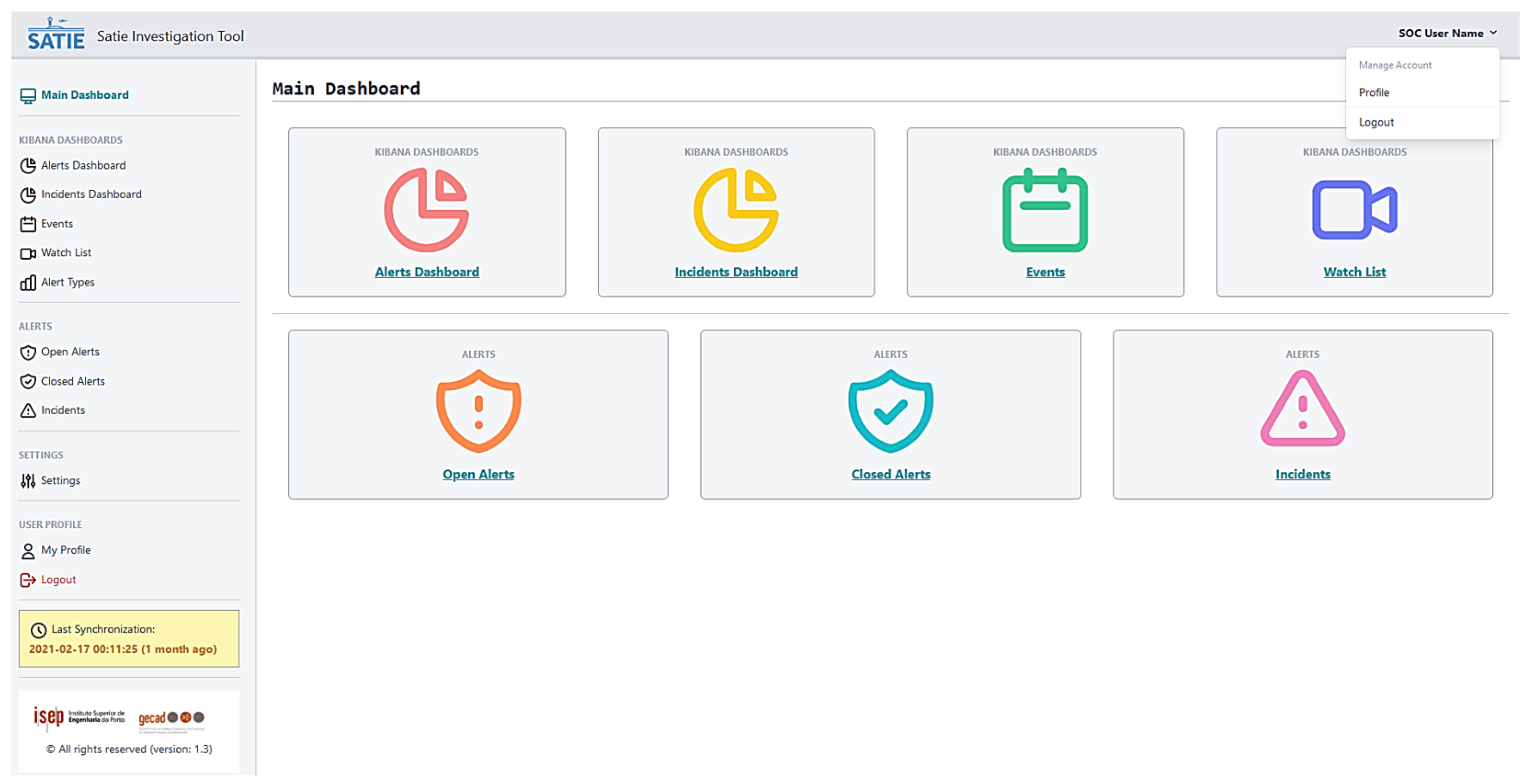
- Web Application: It provides a Graphical User Interface (GUI) that handles the interaction with the SOC operator. It encapsulates the Kibana dashboards and allows the operator to make use of several functionalities such as consulting Alert lists, performing filtration, mining new association rules, managing association rule base and consulting Alert details.
3. SMS-I Machine Learning Engine
3.1. Incident Probabilities
3.1.1. Incident Probabilities Testbed
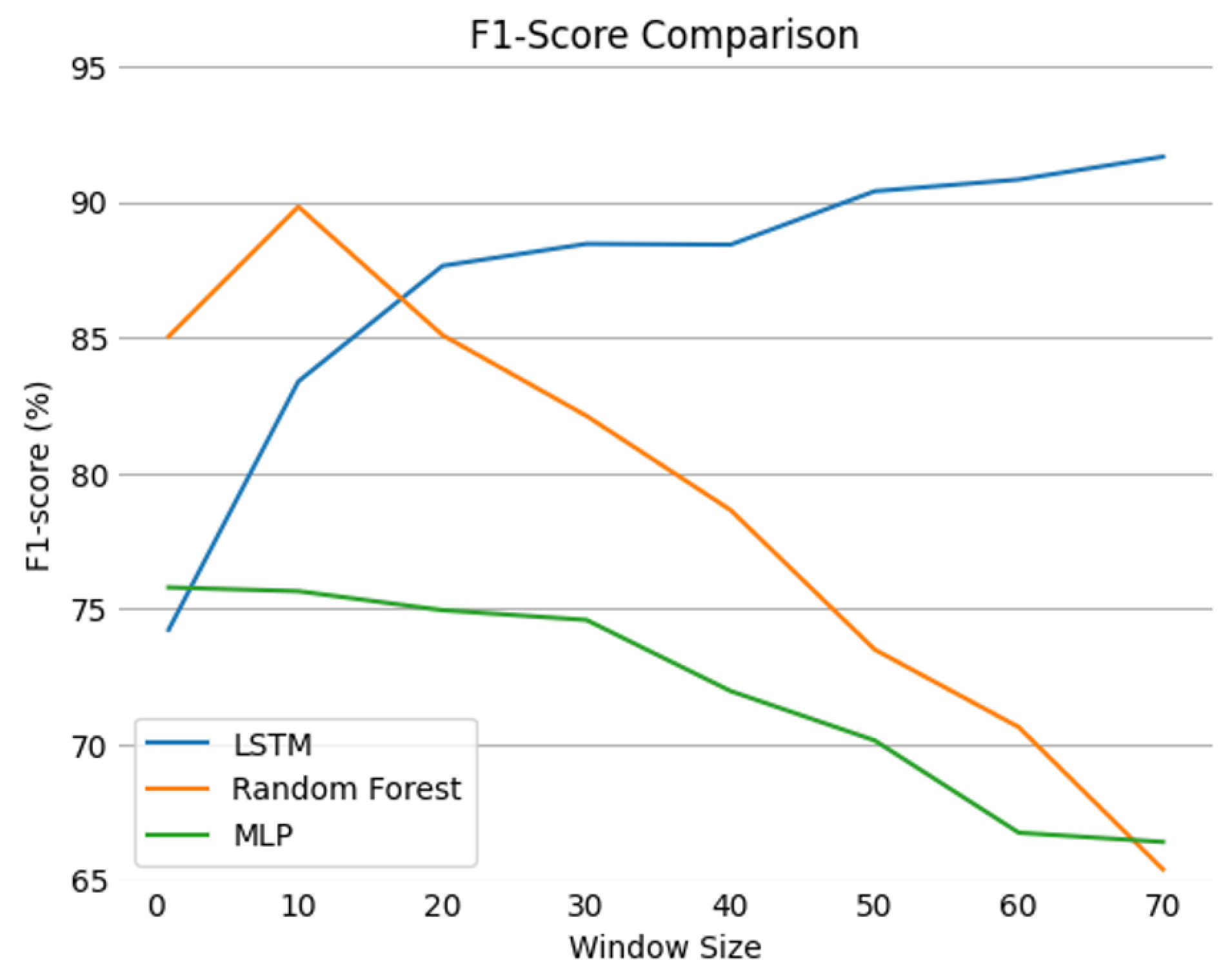
3.1.2. TestBed Results
| , | , |
| , | , |
| . | |
3.1.3. SATIE Toolkit Preliminary Results
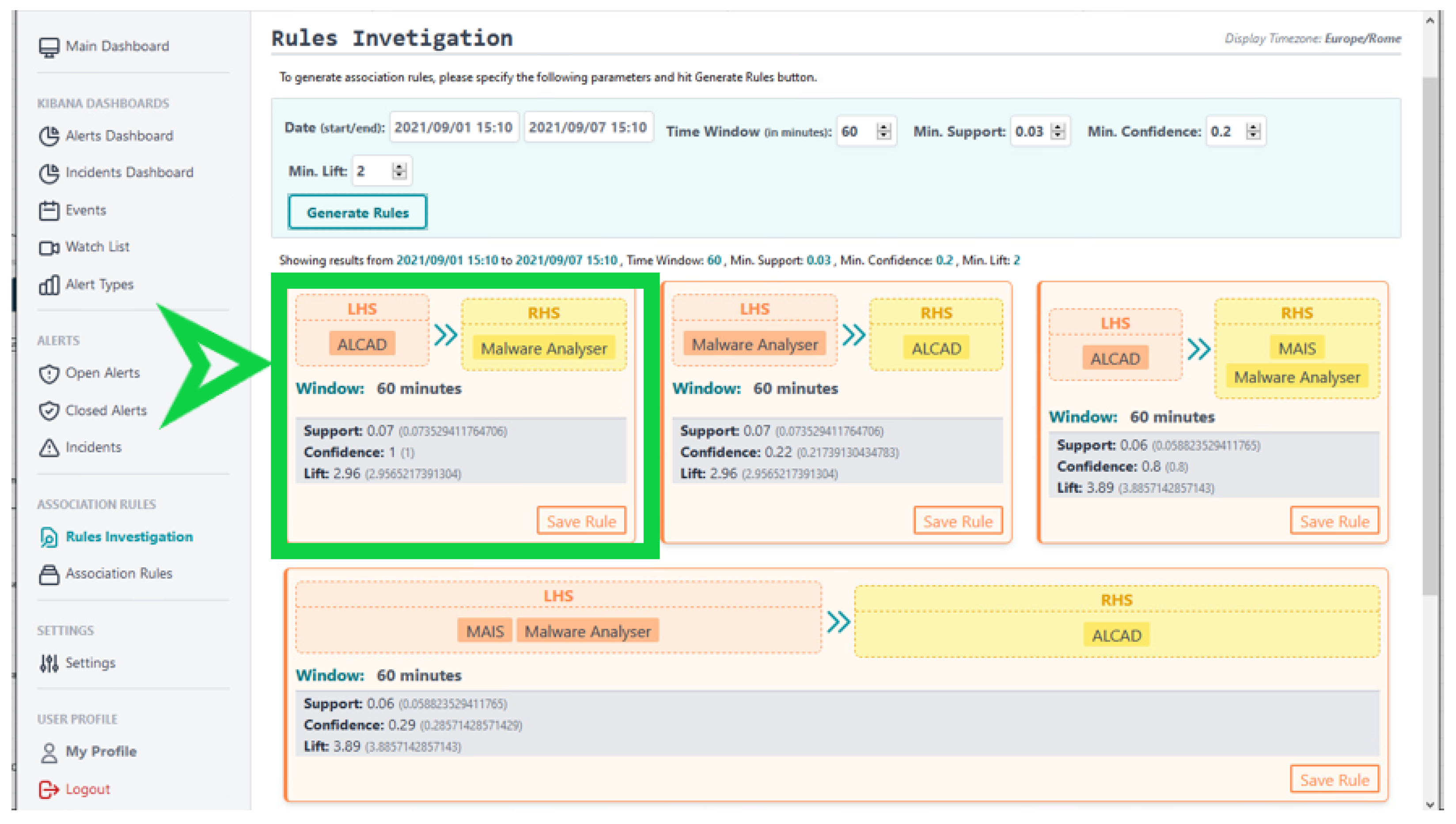
3.2. Association Rule Mining
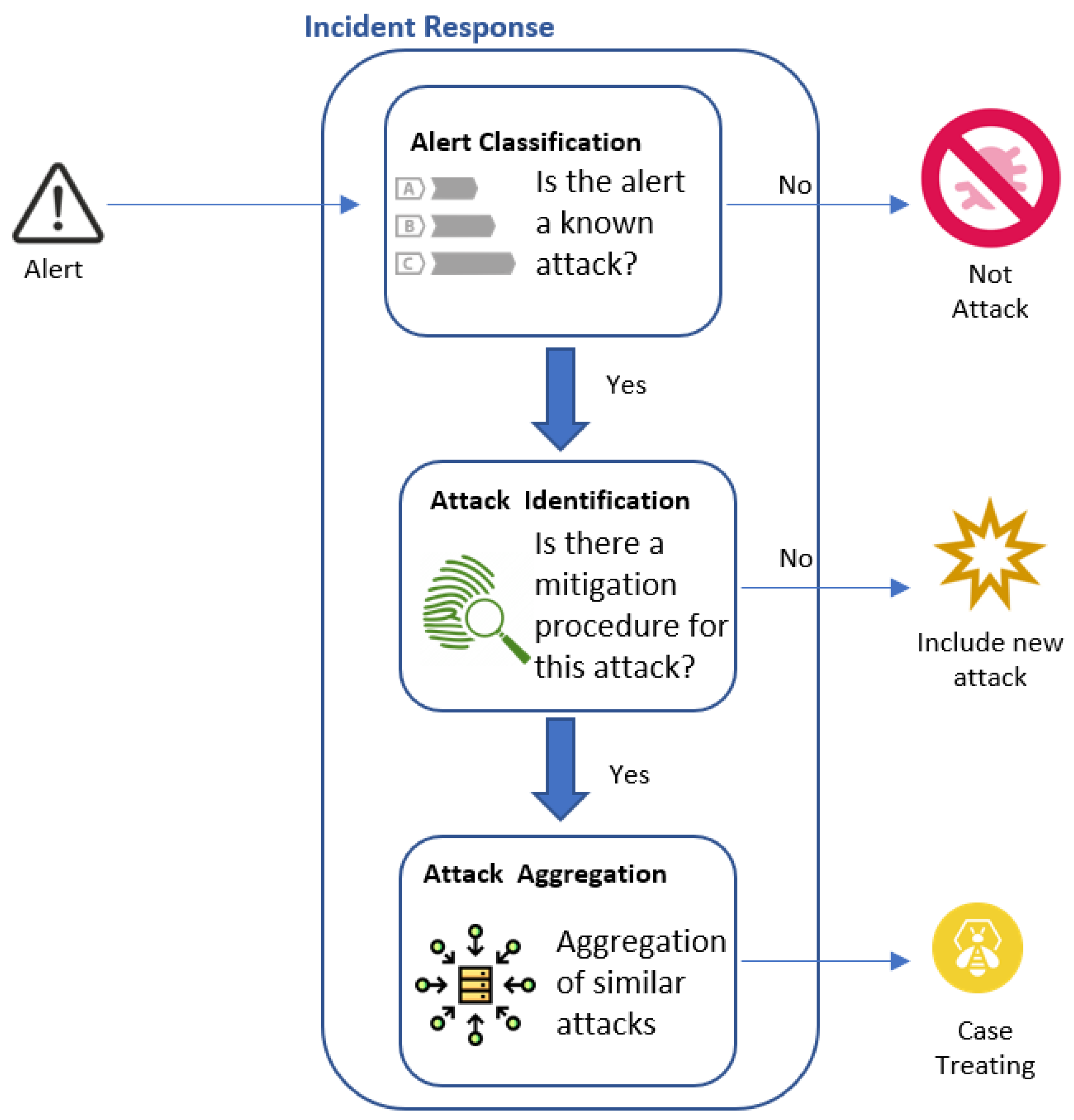
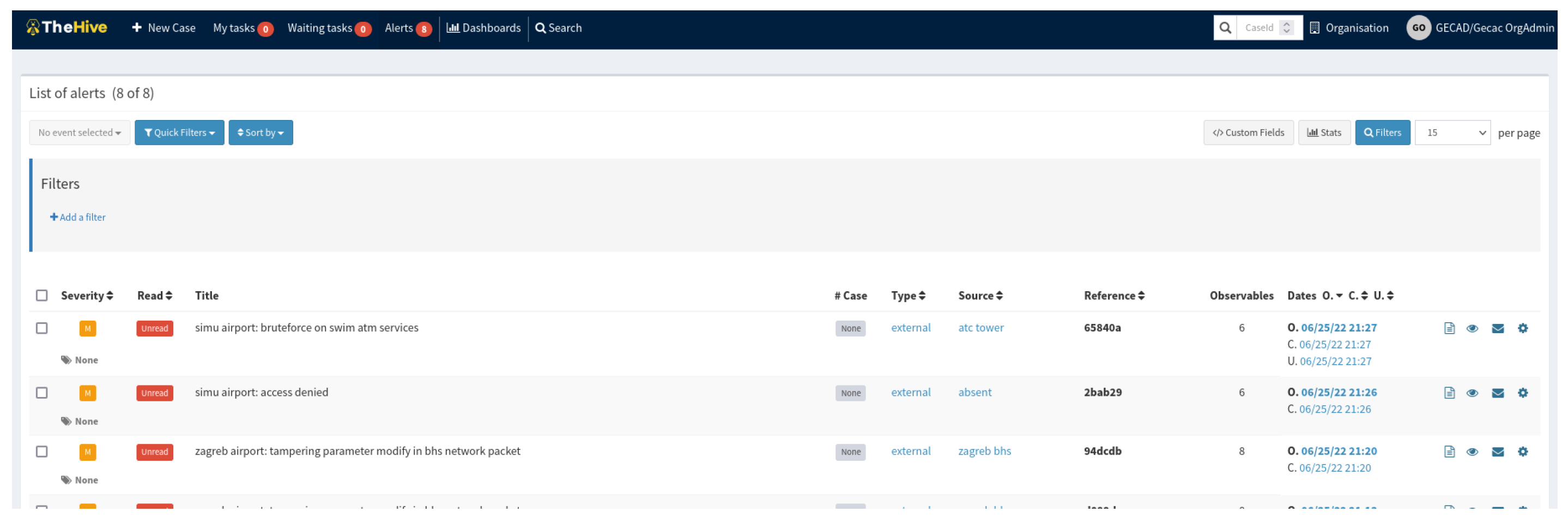
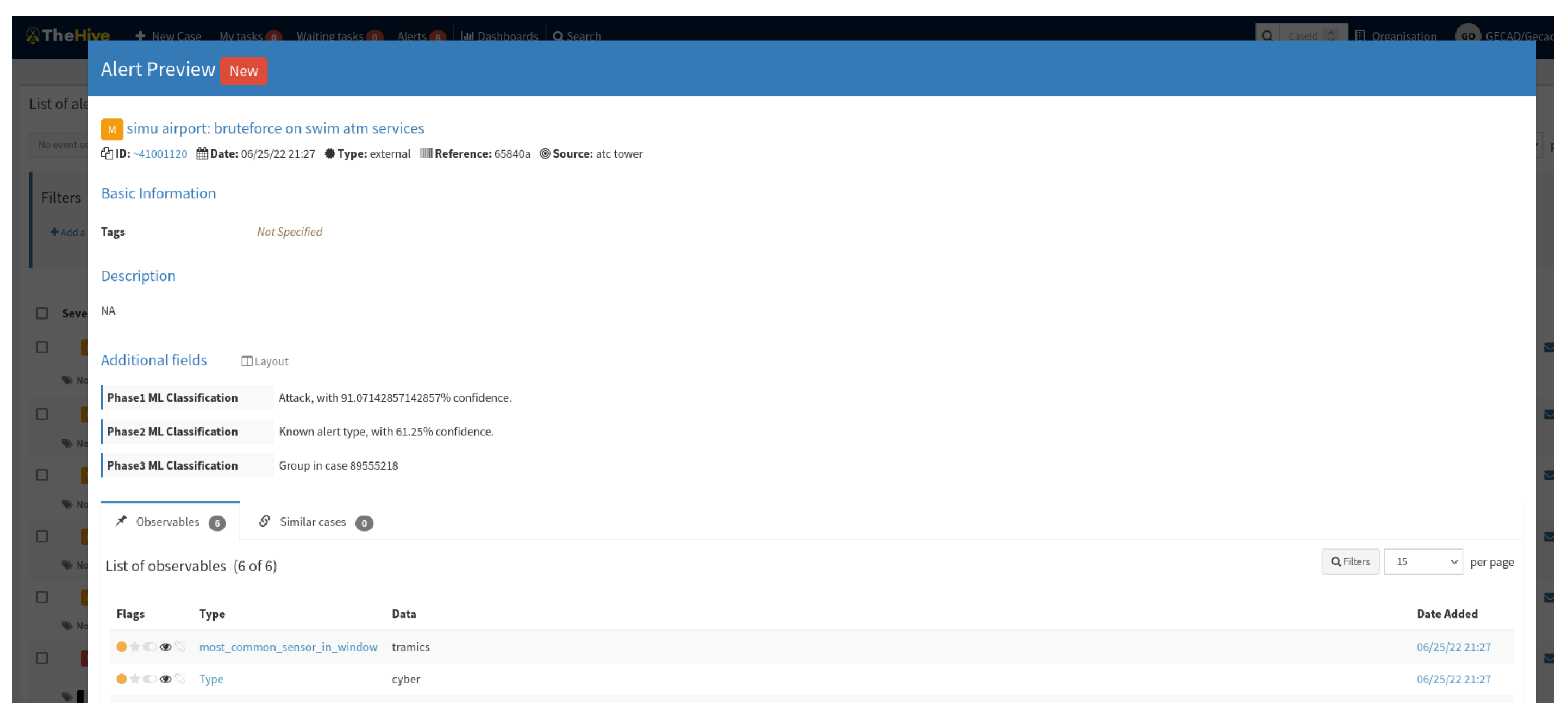
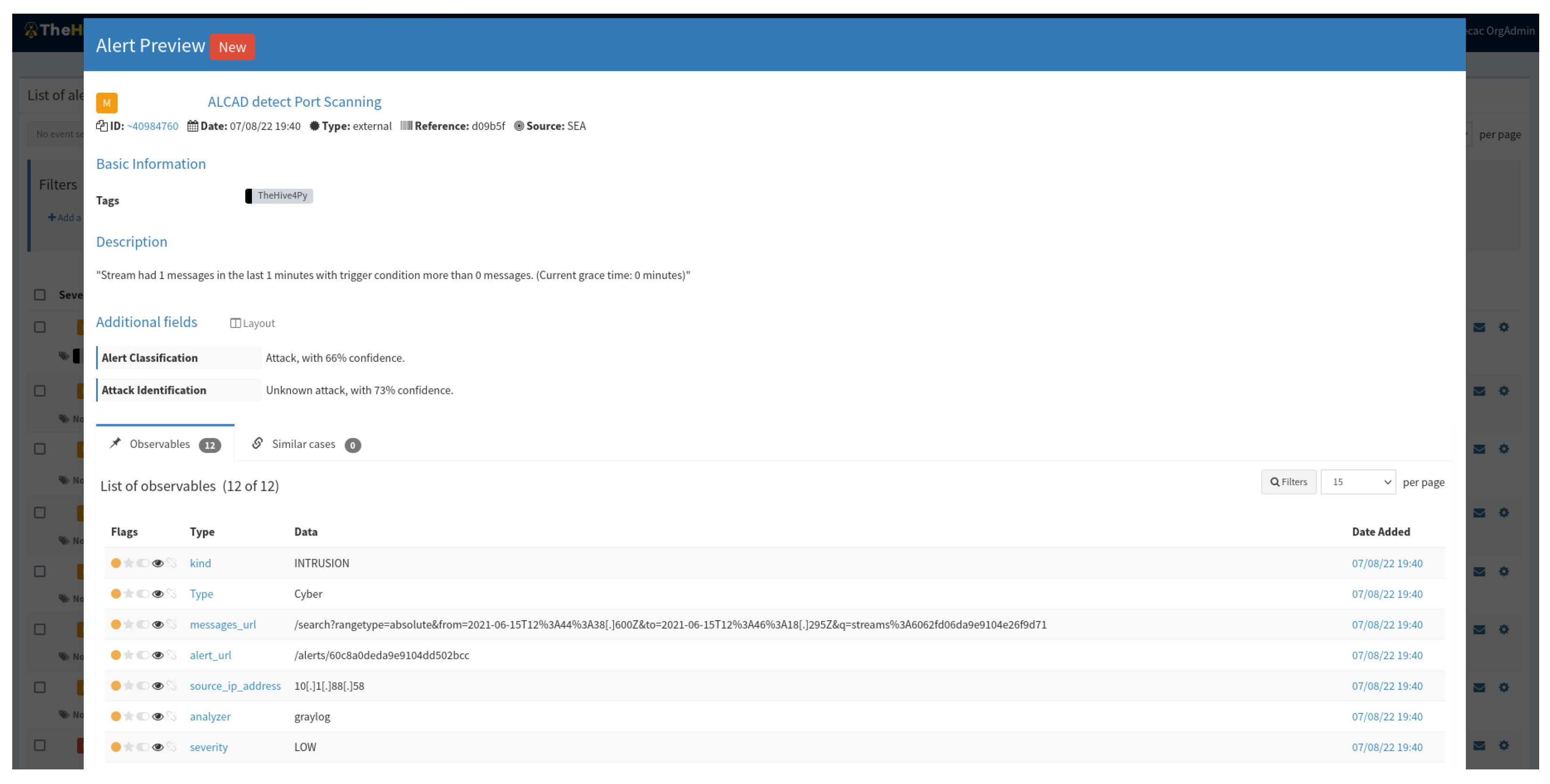
3.3. Incident Response
3.3.1. Alert Classification
- Random Forest, as already mentioned, is a tree based model, employing a set of decision trees and taking in account the output of each one. A decision tree aggregates datapoints by iteratively splitting the features of a given dataset into consecutive binary nodes, ending each branch on its outcome, or label. Although very good with low complexity data, higher sized trees can lead to overfitting. Random Forest models mitigate this issue by using an ensemble of unrelated decision trees and consolidating their results, achieving significant results in the literature for both classification and regression problems.
- Support-Vector Machines (SVM) [41] is a probabilistic model that maps training data to points in space, and finds the hyperplane with the maximum margin that separates the two classes. Newer data points are mapped in space in the same way and classified according to which side of the hyperplane they have landed. This model is a very robust classifier with the caveat that it is limited to binary-class classification.
- Similarly to Random Forest, XgBoost [42] is an ensemble of decision trees, but using a gradient boosting algorithm. Instead of concurrently training a group of decision tree models and averaging their output, models are trained consecutively using the residuals from each iteration to train the next one.
3.3.2. Attack Identification
- Isolation Forest [43] is a tree based model that uses distance between data points to detect outliers, hinging on the principle that outliers are distinct from normal data. During the construction of the binary tree, data are grouped into branches according to their similarity, with more similar entries needing longer branches to differentiate them. As such, data closer to the root of the tree can be considered an anomaly since it was easily distinguishable from the rest.
- One-Class Support-Vector Machines [44] is a similar implementation to SVM but instead of using an hyperplane to separate two classes, it uses an hypersphere around normal data and classifies new data based on its distance to the sphere.
3.3.3. Attack Aggregation
- Random Forest due to its robust results and straightforward implementation, behaving no differently in binary and multiclass classification problems.
- Although models such as Support-Vector Machines in its most simple type only supports binary classification, implementations exist where the problem is compartmentalized into multiple binary classification problems followed by the same principle: discovering the hyperplane that linearly separates classes [45,46].
- K-Nearest Neighbors (KNN) [47] uses distance between datapoints to identify clusters of similar data. Despite its good results it is not very scalable due to being computationally demanding.
3.4. Preliminary Results
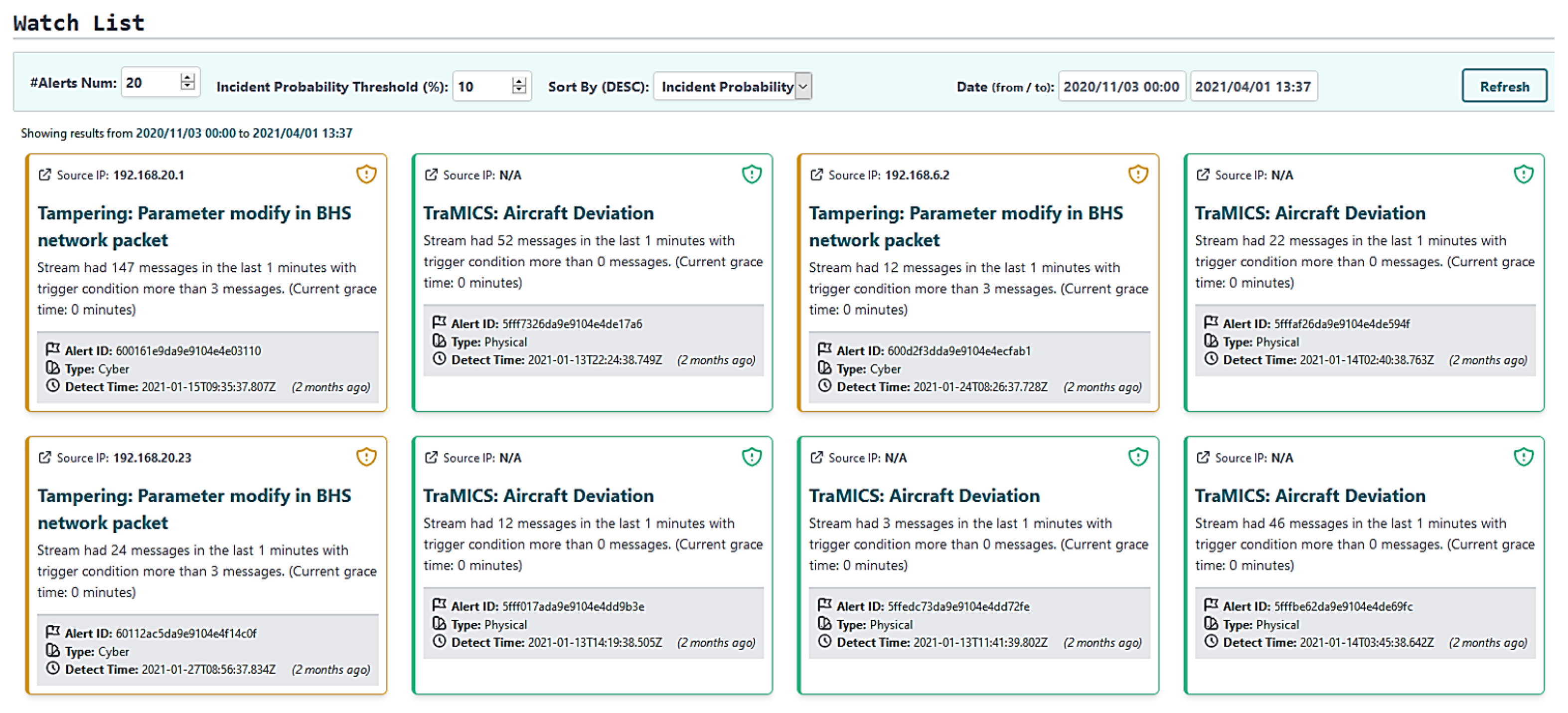
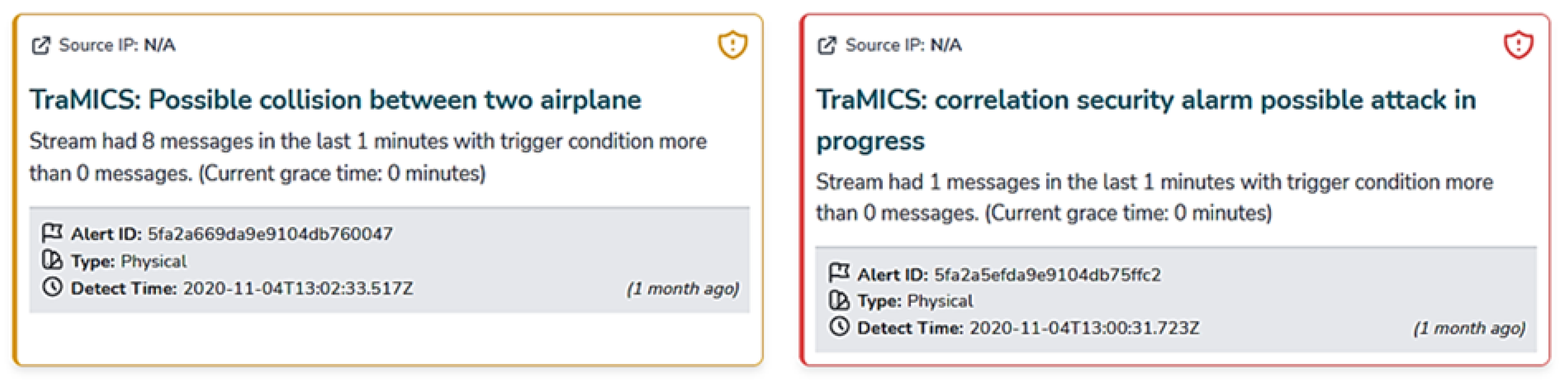
4. SMS-I Intelligent Dashboard
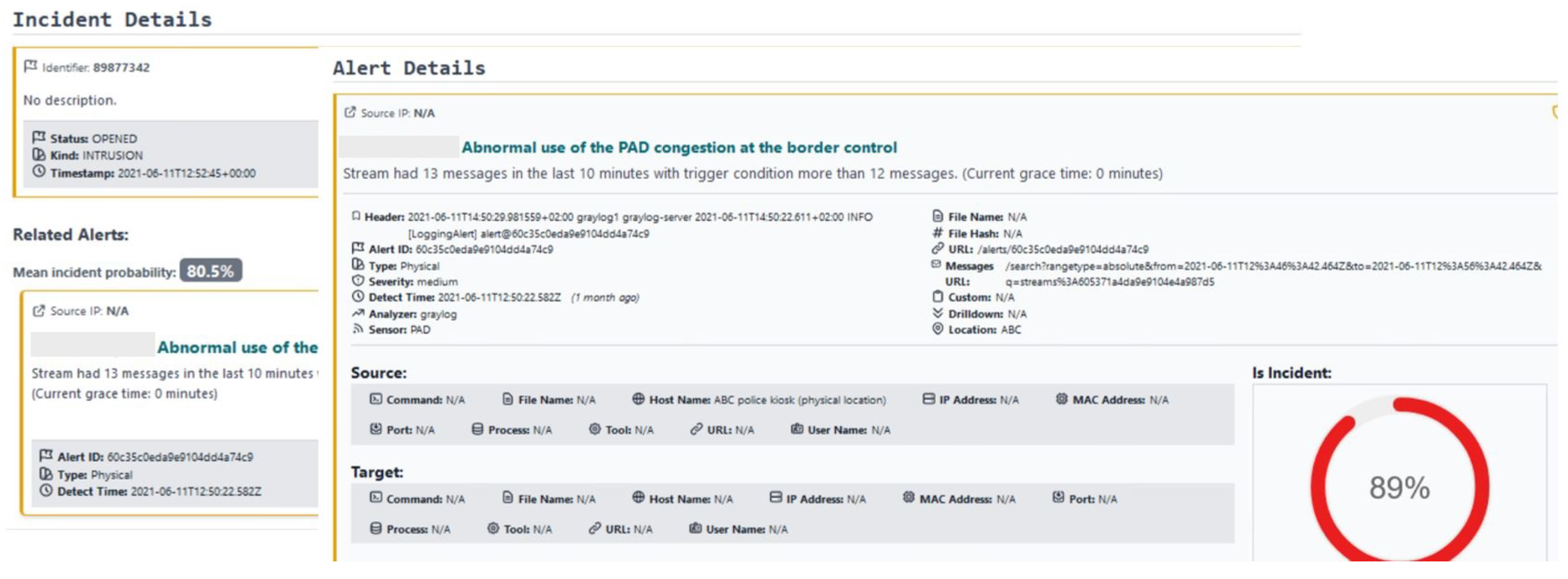
5. SMS-I Incident Response Integration
6. SMS-I Demonstration
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Conflicts of Interest
References
- Lee, E.A. Cyber Physical Systems: Design Challenges. In Proceedings of the 2008 11th IEEE International Symposium on Object and Component-Oriented Real-Time Distributed Computing (ISORC), Orlando, FL, USA, 5–7 May 2008; pp. 363–369. [Google Scholar] [CrossRef]
- Gunes, V.; Peter, S.; Givargis, T.; Vahid, F. A Survey on Concepts, Applications, and Challenges in Cyber–physical Systems. KSII Trans. Internet Inf. Syst. 2014, 8, 4242–4268. [Google Scholar]
- Oks, S.J.; Jalowski, M.; Lechner, M.; Mirschberger, S.; Merklein, M.; Vogel-Heuser, B.; Möslein, K.M. Cyber–physical systems in the context of Industry 4.0: A review, categorization and outlook. Inf. Syst. Front. 2022; early access. [Google Scholar]
- Lozano, C.V.; Vijayan, K.K. Literature review on Cyber Physical Systems Design. Procedia Manuf. 2020, 45, 295–300. [Google Scholar] [CrossRef]
- Loukas, G. Cyber–Physical Attacks: A Growing Invisible Threat. Butterworth-Heinemann Is an Imprint of Elsevier. 2015. Available online: https://www.elsevier.com/books/cyber-physical-attacks/loukas/978-0-12-801290-1 (accessed on 4 July 2022).
- Kim, S.; Park, K.J. A Survey on Machine-Learning Based Security Design for Cyber–physical Systems. Appl. Sci. 2021, 11, 5458. [Google Scholar] [CrossRef]
- Karnouskos, S. Stuxnet worm impact on industrial cyber–physical system security. In Proceedings of the 37th Annual Conference of the IEEE Industrial Electronics Society, Melbourne, VIC, Australia, 7–10 November 2011; pp. 4490–4494. [Google Scholar]
- Plumer, C. It’s Way too Easy to Cause a Massive Blackout in the US. 2014. Available online: https://www.vox.com/2014/4/14/5604992/us-power-grid-vulnerability (accessed on 4 July 2022).
- Colatin, S.D.T. Steel Mill in Germany. 2014. Available online: https://cyberlaw.ccdcoe.org/wiki/Steel_mill_in_Germany_(2014) (accessed on 4 July 2022).
- Lee, R.M.; Assante, M.J.; Conway, T. Analysis of the Cyber Attack on the Ukrainian Power Grid. E-ISAC. 2016. Available online: https://nsarchive.gwu.edu/sites/default/files/documents/3891751/SANS-and-Electricity-Information-Sharing-and.pdf (accessed on 4 July 2022).
- Kardon, S. Florida Water Treatment Plant Hit with Cyber Attack. 2021. Available online: https://www.industrialdefender.com/florida-water-treatment-plant-cyber-attack/ (accessed on 4 July 2022).
- Sanger, D.E.; Krauss, C.; Perlroth, N. Cyberattack Forces a Shutdown of a Top U.S. Pipeline. 2021. Available online: https://www.nytimes.com/2021/05/08/us/politics/cyberattack-colonial-pipeline.html (accessed on 4 July 2022).
- Jin, A.S.; Hogewood, L.; Fries, S.; Lambert, J.H.; Fiondella, L.; Strelzoff, A.; Boone, J.; Fleckner, K.; Linkov, I. Resilience of Cyber–physical Systems: Role of AI, Digital Twins, and Edge Computing. IEEE Eng. Manag. Rev. 2022, 50, 195–203. [Google Scholar] [CrossRef]
- Mohamed, N.; Al-Jaroodi, J.; Jawhar, I. Cyber–Physical Systems Forensics: Today and Tomorrow. J. Sens. Actuator Netw. 2020, 9, 37. [Google Scholar] [CrossRef]
- Fausto, A.; Gaggero, G.B.; Patrone, F.; Girdinio, P.; Marchese, M. Toward the Integration of Cyber and Physical Security Monitoring Systems for Critical Infrastructures. Sensors 2021, 21, 6970. [Google Scholar] [CrossRef] [PubMed]
- Rajivan, P.; Cooke, N. Impact of team collaboration on cybersecurity situational awareness. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2017; Volume 10030, pp. 203–226. [Google Scholar] [CrossRef]
- Parliament, E. The NIS2 Directive: A High Common Level of Cybersecurity in the EU. 2022. Available online: https://www.europarl.europa.eu/thinktank/en/document/EPRS_BRI(2021)689333 (accessed on 4 July 2022).
- European Union Agency for Network; Information Security. The NIS2 DiDetect, SHARE, Protect. Solutions for Improving Threat Data Exchange among CERTs. 2013. Available online: https://www.enisa.europa.eu/publications/detect-share-protect-solutions-for-improving-threat-data-exchange-among-certs/at_download/fullReport (accessed on 4 July 2022).
- Settanni, G.; Skopik, F.; Shovgenya, Y.; Fiedler, R.; Carolan, M.; Conroy, D.; Boettinger, K.; Gall, M.; Brost, G.; Ponchel, C.; et al. A collaborative cyber incident management system for European interconnected critical infrastructures. J. Inf. Secur. Appl. 2017, 34, 166–182. [Google Scholar] [CrossRef]
- Bernal, A.E.; Monterrubio, S.M.M.; Fuente, J.P.; Crespo, R.G.; Verdu, E. Methodology for Computer Security Incident Response Teams into IoT Strategy. KSII Trans. Internet Inf. Syst. 2021, 15, 1909–1928. [Google Scholar] [CrossRef]
- Köpke, C. Impact Propagation in Airport Systems. In Proceedings of the 2nd International Workshop on Cyber–physical Security for Critical Infrastructures Protection (CPS4CIP 2021), Darmstadt, Germany, 4–8 October 2021; Springer International Publishing: Cham, Switzerland, 2021; pp. 191–206. [Google Scholar]
- Macedo, I.; Wanous, S.; Oliveira, N.; Sousa, O.; Praça, I. A Tool to Support the Investigation and Visualization of Cyber and/or Physical Incidents. In Proceedings of the WorldCIST 9th World Conference on Information Systems and Technologies, Azores, Portugal, 30 March–2 April 2021; Rocha, Á., Ed.; Springer International Publishing: Cham, Switzerland, 2021; pp. 130–140. [Google Scholar]
- Maia, E.; Sousa, N.; Oliveira, N.; Wannous, S.; Praça, I. SMS-I: An Intelligent Correlation tool for Cyber–physical Systems. In Proceedings of the 2022 5th International Conference DPSC2022, Porto, Portugal, 19–20 January 2022. [Google Scholar]
- Brown, S. The C4 Model for Visualising Software Architecture. 2022. Available online: https://c4model.com/ (accessed on 4 July 2022).
- Poole, C.; Huisman, J. Using extreme programming in a maintenance environment. IEEE Softw. 2001, 18, 42–50. [Google Scholar] [CrossRef]
- Martin, R.C. Agile Software Development: Principles, Patterns and Practices; Prentice Hall PTR: Englewood Cliffs, NJ, USA, 2003. [Google Scholar]
- Taormina, R.; Galelli, S.; Tippenhauer, N.; Salomons, E.; Ostfeld, A.; Eliades, D.; Aghashahi, M.; Sundararajan, R.; Pourahmadi, M.; Banks, M.; et al. Battle of the Attack Detection Algorithms: Disclosing cyber attacks on water distribution networks. J. Water Resour. Plan. Manag. 2018, 144, 04018048. [Google Scholar] [CrossRef]
- Ring, M.; Wunderlich, S.; Grüdl, D.; Landes, D.; Hotho, A. Flow-Based Benchmark Data Sets for Intrusion Detection. In Proceedings of the 16th European Conference on Cyber Warfare and Security (ECCWS), Dublin, Ireland, 29–30 June 2017; pp. 361–369. [Google Scholar]
- Moustafa, N.; Slay, J. UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In Proceedings of the 2015 Annual Military Communications and Information Systems (MilCIS), Canberra, Australia, 10–12 November 2015; pp. 1–6. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Habibi Lashkari, A.; Ghorbani, A.A. Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization. In Proceedings of the 4th International Conference on Information Systems Security and Privacy (ICISSP), Funchal, Madeira, 22–24 January 2018; SciTePress: Setúbal, Portugal, 2018; pp. 108–116. [Google Scholar]
- Oliveira, N.; Praça, I.; Maia, E.; Sousa, O. Intelligent Cyber Attack Detection and Classification for Network-Based Intrusion Detection Systems. Appl. Sci. 2021, 11, 1674. [Google Scholar] [CrossRef]
- Zhang, C.; Ma, Y. Ensemble Machine Learning: Methods and Applications; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Gardner, M.W.; Dorling, S. Artificial neural networks (the multilayer perceptron)—A review of applications in the atmospheric sciences. Atmos. Environ. 1998, 32, 2627–2636. [Google Scholar] [CrossRef]
- Gwon, H.; Lee, C.; Keum, R.; Choi, H. Network intrusion detection based on LSTM and feature embedding. arXiv 2019, arXiv:1911.11552. [Google Scholar]
- Agrawal, R.; Srikant, R. Fast Algorithms for Mining Association Rules in Large Databases. In Proceedings of the 20th International Conference on Very Large Data Bases (VLDB ’94), Santiago de Chile, Chile, 12–15 September 1994; Morgan Kaufmann Publishers Inc.: San Francisco, CA, USA, 1994; pp. 487–499. [Google Scholar]
- Han, J.; Kamber, M.; Pei, J. Data Mining Concepts and Techniques, 3rd ed.; Morgan Kaufmann Publishers: Waltham, MA, USA, 2012. [Google Scholar]
- Applebaum, A.; Johnson, S.; Limiero, M.; Smith, M. Playbook oriented cyber response. In Proceedings of the 2018 National Cyber Summit (NCS), Huntsville, AL, USA, 5–7 June 2018; pp. 8–15. [Google Scholar]
- Martínez Torres, J.; Iglesias Comesaña, C.; García-Nieto, P.J. Machine learning techniques applied to cybersecurity. Int. J. Mach. Learn. Cybern. 2019, 10, 2823–2836. [Google Scholar] [CrossRef]
- Alqahtani, H.; Sarker, I.H.; Kalim, A.; Hossain, M.; Md, S.; Ikhlaq, S.; Hossain, S. Cyber intrusion detection using machine learning classification techniques. In International Conference on Computing Science, Communication and Security; Springer: Berlin/Heidelberg, Germany, 2020; pp. 121–131. [Google Scholar]
- Sarker, I.H.; Abushark, Y.B.; Alsolami, F.; Khan, A.I. Intrudtree: A machine learning based cyber security intrusion detection model. Symmetry 2020, 12, 754. [Google Scholar] [CrossRef]
- Mammone, A.; Turchi, M.; Cristianini, N. Support vector machines. In Wiley Interdisciplinary Reviews: Computational Statistics; Wiley: Hoboken, NJ, USA, 2009; pp. 283–289. [Google Scholar]
- Chen, T.; He, T.; Benesty, M.; Khotilovich, V.; Tang, Y.; Cho, H.; Chen, K. Xgboost: Extreme Gradient Boosting; R Package Version 0.4-2. 2015. Available online: https://cran.r-project.org/web/packages/xgboost/vignettes/xgboost.pdf (accessed on 4 July 2022).
- Liu, F.T.; Ting, K.M.; Zhou, Z.H. Isolation forest. In Proceedings of the 2008 Eighth IEEE International Conference on Data Mining, Pisa, Italy, 15–19 December 2008; pp. 413–422. [Google Scholar]
- Schölkopf, B.; Williamson, R.C.; Smola, A.; Shawe-Taylor, J.; Platt, J. Support vector method for novelty detection. Adv. Neural Inf. Process. Syst. 1999, 12, 582–588. [Google Scholar]
- Wang, Z.; Xue, X. Multi-class support vector machine. In Support Vector Machines Applications; Springer: Berlin/Heidelberg, Germany, 2014; pp. 23–48. [Google Scholar]
- Franc, V.; Hlavác, V. Multi-class support vector machine. In Proceedings of the 2002 International Conference on Pattern Recognition, Quebec City, QC, Canada, 11–15 August 2002; Volume 2, pp. 236–239. [Google Scholar]
- Guo, G.; Wang, H.; Bell, D.; Bi, Y.; Greer, K. KNN model-based approach in classification. In OTM Confederated International Conferences on the Move to Meaningful Internet Systems; Springer: Berlin/Heidelberg, Germany, 2003; pp. 986–996. [Google Scholar]
- Casey, T. Survey: 27 Percent of IT Professionals Receive More than 1 Million Security Alerts Daily. 2018. Available online: https://www.imperva.com/blog/27-percent-of-it-professionals-receive-more-than-1-million-security-alerts-daily/ (accessed on 4 July 2022).
- Schaper, M.; Gluchshenko, O.; Muth, K.; Tyburzy, L.; Rusko, M.; Trnka, M. The Traffic Management Intrusion and Compliance System as Security Situation Assessment System at an Air Traffic Controller’s Working Position. In Proceedings of the 31st European Safety and Reliability Conference ESREL, Angers, France, 19–23 September 2021; pp. 2825–2831. [Google Scholar]
- Barnum, S.; Martin, R.; Worrell, B.; Kirillov, I. The Cybox Language Specification; The MITRE Corporation: McLean, VA, USA, 2012. [Google Scholar]
- SATIE_Consortium. D6.3 Test and Validation Results on the Simulation Platform. Technical Report. 2021. Available online: https://satie-h2020.eu/wp-content/uploads/2022/01/SATIE_D6.3_Test-and-validation-results-on-the-simulation-platform_PU_v1.0_compressed.pdf (accessed on 4 July 2022).
- SATIE_Consortium. D6.5 Report about Demonstration and Results in Athens Airport. Technical Report. 2021. Available online: https://satie-h2020.eu/wp-content/uploads/2022/01/SATIE_D6.5_Report-about-demonstration-and-results-in-Athens-airport_PU_v1.0_compressed.pdf (accessed on 4 July 2022).
- SATIE_Consortium. D6.6 Report about Demonstration and Results in Milan Airport. Technical Report. 2021. Available online: https://satie-h2020.eu/wp-content/uploads/2022/01/SATIE_D6.6_Report-about-demonstration-and-results-in-Milan-airport_PU_v1.0_compressed-1.pdf (accessed on 4 July 2022).
- IBM Security. Cost of a Data Breach Report 2021; IBM Security: Tulsa, OK, USA, 2021. [Google Scholar]
- Vielberth, M.; Böhm, F.; Fichtinger, I.; Pernul, G. Security Operations Center: A Systematic Study and Open Challenges. IEEE Access 2020, 8, 227756–227779. [Google Scholar] [CrossRef]
- Daniel, C.; Gill, T.; Hevner, A.; Mullarkey, M. A Deep Neural Network Approach to Tracing Paths in Cybersecurity Investigations. In Proceedings of the 2020 International Conference on Data Mining Workshops (ICDMW), Sorrento, Italy, 17–20 November 2020; pp. 472–479. [Google Scholar]
- Reuschling, F.; Carstengerdes, N.; Stelkens-Kobsch, T.H.; Burke, K.; Oudin, T.; Schaper, M.; Apolinário, F.; Praca, I.; Perlepes, L. Toolkit to Enhance Cyber-Physical Security of Critical Infrastructures in Air Transport; Now Publishers: Norwell, MA, USA, 2021. [Google Scholar]





| Dataset | Year | Format | Count | Duration | Kind |
|---|---|---|---|---|---|
| NSW-NB15 | 2015 | packet, other | 2 M | 31 h | Emulated |
| CICIDS2017 | 2017 | uni. flow | 3.1 M | 5 Days | Emulated |
| CIDDS-001 | 2017 | uni. flow | 33 M | 28 Days | Emulated and Real |
| Model | Accuracy | Precision | Recall | F1-Score | FPR |
|---|---|---|---|---|---|
| LSTM | 99.91 | 98.37 | 71.40 | 74.23 | 00.05 |
| RF | 99.90 | 79.43 | 95.68 | 85.04 | 00.02 |
| MLP | 99.92 | 78.68 | 73.75 | 75.79 | 00.06 |
| Model | Accuracy | Precision | Recall | F1-Score | FPR |
|---|---|---|---|---|---|
| LSTM-70 | 99.94 | 94.03 | 89.71 | 91.66 | 00.04 |
| RF-10 | 99.95 | 96.83 | 85.65 | 89.82 | 00.04 |
| Steps | Models | Accuracy | F1-Score | Macro F1-Score |
|---|---|---|---|---|
| Alert Classification | RF | 97.1 | 69.2 | 96.8 |
| SVM | 97.3 | 63.1 | 96.5 | |
| XgBoost | 97.3 | 70.4 | 96.9 | |
| Attack Identification | IF | 80.9 | 82.8 | 80.8 |
| One Class SVM | 67.6 | 73.7 | 65.6 | |
| Attack Aggregation | RF | 80.2 | 58.5 | 77.8 |
| SVM | 80.2 | 59.2 | 78.3 | |
| KNN | 88.3 | 54.9 | 85.4 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Maia, E.; Sousa, N.; Oliveira, N.; Wannous, S.; Sousa, O.; Praça, I. SMS-I: Intelligent Security for Cyber–Physical Systems. Information 2022, 13, 403. https://doi.org/10.3390/info13090403
Maia E, Sousa N, Oliveira N, Wannous S, Sousa O, Praça I. SMS-I: Intelligent Security for Cyber–Physical Systems. Information. 2022; 13(9):403. https://doi.org/10.3390/info13090403
Chicago/Turabian StyleMaia, Eva, Norberto Sousa, Nuno Oliveira, Sinan Wannous, Orlando Sousa, and Isabel Praça. 2022. "SMS-I: Intelligent Security for Cyber–Physical Systems" Information 13, no. 9: 403. https://doi.org/10.3390/info13090403
APA StyleMaia, E., Sousa, N., Oliveira, N., Wannous, S., Sousa, O., & Praça, I. (2022). SMS-I: Intelligent Security for Cyber–Physical Systems. Information, 13(9), 403. https://doi.org/10.3390/info13090403








