1. Introduction
Paperless or folder-less system is a common term used to denote the adoption of full electronic health records (EHR) systems used by hospitals in Ghana. In paperless systems, the hospitals do not use hard copy papers or folders to document and store patient care processes. Instead, all the patient activities at the healthcare facility (such as OPD visits, medical investigations, diagnosis and treatments, inpatient and outpatient documentation, referrals, and ordering of tests) are carried out in the EHR system [
1,
2]. The benefits of paperless systems cannot be overemphasized, as the systems improve the efficient management of patients’ information, reduce physical storage space for medical records, and improve clinical decision support [
3,
4,
5].
In hindsight, cyber security incidents remain a threat to the use of these information systems [
6] of which healthcare systems are among the most targeted systems. Several reasons account for this. Firstly, information security solutions have traditionally been focused on technical measures such as firewall configurations, demilitarize zone, intrusion detection and prevention systems, authentication, and authorizations in mitigating risks; however, the human aspect of IS management (also called the human firewall) has received less attention as an important factor in mitigating security issues [
7,
8]. Meanwhile, current dynamics in security issues cannot be resolved with only technical measures especially in an era where humans are considered the weakest link in the security chain [
8,
9,
10]. Secondly, healthcare is most suitable for cyber criminals due to the urgency requirement by healthcare staff to access patients records. For instance, in a ransomware attack scenario of the healthcare sector, the authorities would be willing to pay the ransom for the timely access of patients records.
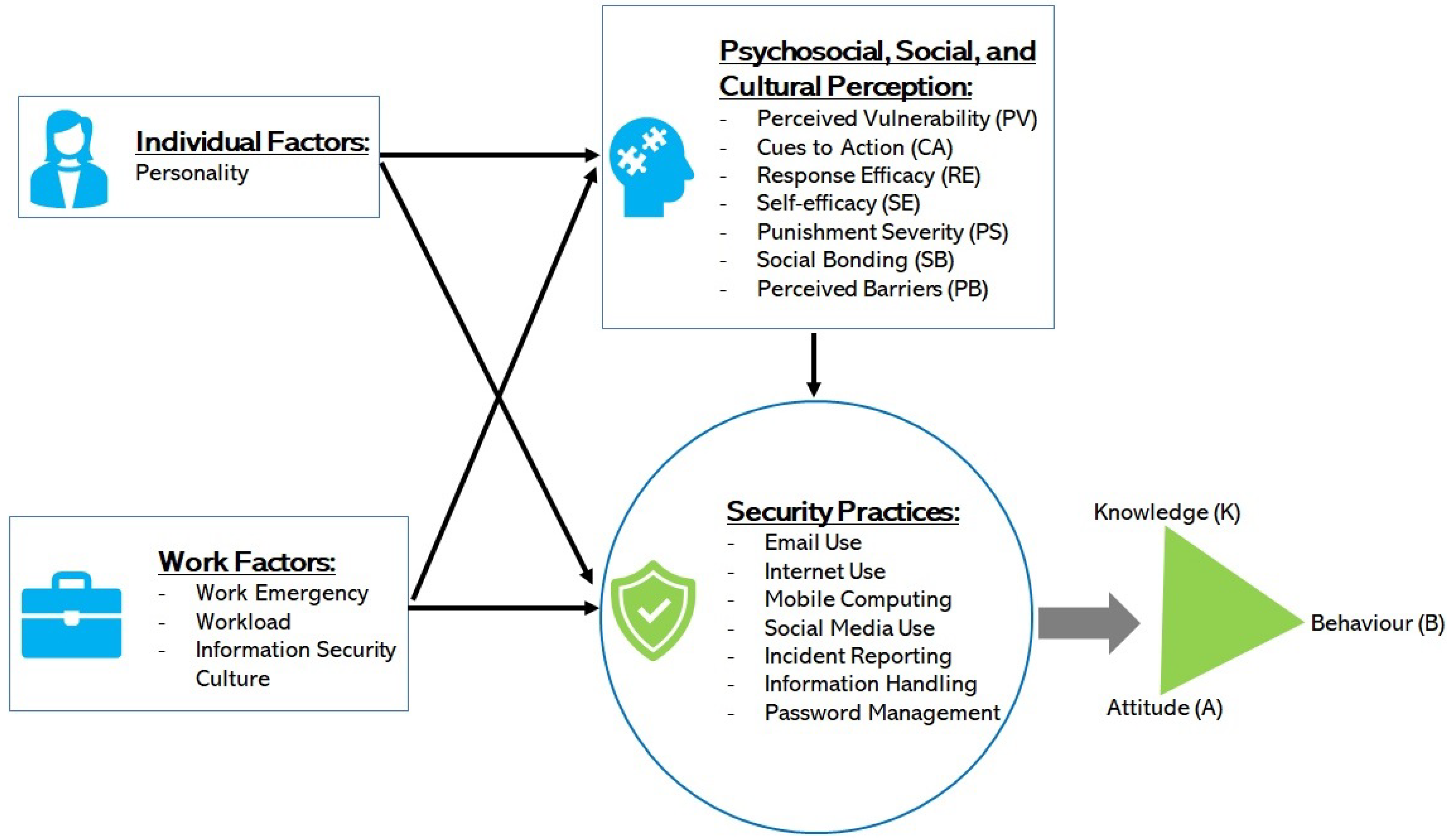
There is a broad range of human factors that contribute to security violations in healthcare. These include psychological, social, cultural, work factors and individual factors [
11]. Security researchers often investigate these factors toward enhancing security practices; however, the assessments are not often comprehensively performed, leaving possible gaps of vulnerabilities in the human element. For instance, Anwar et al. investigated the significance of gender factors in security practice [
12]. While this is essential, other variables, such as work factors, were not considered in the study. This means if findings in Anwar et al. were to be considered for enhancing security practice in a typical hospital, issues on the individual difference in terms of gender among healthcare staff will be detected and resolved. However, issues relating to other factors of the human element will not be covered. This may still leave a security gap among the staff’s security practice. This study contributed to bridging this gap, having adopted a comprehensive approach where a broad range of factors, including psychological, social, cultural, individual, and work factors were assessed in a comprehensive way.
In view of the above, the objectives of this study include the following:
To comprehensively assess the effect of individual factors and perceptions, including psychological, social, and cultural aspects on IS knowledge, attitude and behavior among healthcare staff.
To examine the effect of work factors (such as workload and work emergency) on cyber security knowledge, attitude, and the intended security conscious care behavior (ISCCB) of healthcare workers.
To assess the effect of cyber security knowledge and attitude on the intended security conscious care behavior of healthcare staff.
Factors found to have significant risks on conscious care security practices can be discouraged with extrinsic motivation (motivations based on external factors, e.g., financial or punishment) [
13,
14,
15] and intrinsic motivations (incentives that stem out of one’s self) [
16,
17] while promoting factors that have a positive impact on IS security practice.
The remaining part of the paper is organized to include the theoretical background and hypotheses. In this section, related theories that were used in similar studies have been reviewed. Subsequently, the theoretical model and hypotheses were developed. This section is followed by the study approach and the method section, which explained how the study was conducted. The results were then described in the Results section. Finally, the results were then discussed and concluded in the Conclusions section.
Author Contributions
Conceptualization, B.Y. and P.K.Y.; methodology, P.K.Y. and M.A.F.; validation, B.Y., P.K.Y. and M.A.F.; formal analysis, P.K.Y. and M.A.F.; investigation, P.K.Y.; data curation, P.K.Y. and B.Y.; writing—original draft preparation, P.K.Y., M.A.F. and B.Y.; writing—review and editing, P.K.Y., M.A.F. and B.Y.; visualization, B.Y.; supervision, B.Y.; project administration, P.K.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Informed Consent Statement
Informed consent was obtained from all subjects involved in the study.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Schumaker, R.P.; Reganti, K.P. Implementation of electronic health record (EHR) system in the healthcare industry. Int. J. Priv. Health Inf. Manag. (IJPHIM) 2014, 2, 57–71. [Google Scholar] [CrossRef]
- Zandieh, S.O.; Yoon-Flannery, K.; Kuperman, G.J.; Langsam, D.J.; Hyman, D.; Kaushal, R. Challenges to EHR implementation in electronic-versus paper-based office practices. J. Gen. Intern. Med. 2008, 23, 755–761. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Miriovsky, B.J.; Shulman, L.N.; Abernethy, A.P. Importance of health information technology, electronic health records, and continuously aggregating data to comparative effectiveness research and learning health care. J. Clin. Oncol. 2012, 30, 4243–4248. [Google Scholar] [CrossRef] [PubMed]
- Hossain, A.; Quaresma, R.; Rahman, H. Investigating factors influencing the physicians’ adoption of electronic health record (EHR) in healthcare system of Bangladesh: An empirical study. Int. J. Inf. Manag. 2019, 44, 76–87. [Google Scholar] [CrossRef]
- Dagliati, A.; Malovini, A.; Tibollo, V.; Bellazzi, R. Health informatics and EHR to support clinical research in the COVID-19 pandemic: An overview. Briefings Bioinform. 2021, 22, 812–822. [Google Scholar] [CrossRef]
- Yeng, P.K.; Yang, B.; Snekkenes, E.A. Framework for healthcare security practice analysis, modeling and incentivization. In Proceedings of the 2019 IEEE International Conference on Big Data (Big Data), Los Angeles, CA, USA, 9–12 December 2019; IEEE: Piscataway, NJ, USA, 2019; pp. 3242–3251. [Google Scholar]
- Furnell, S.; Clarke, N. Power to the people? The evolving recognition of human aspects of security. Comput. Secur. 2012, 31, 983–988. [Google Scholar] [CrossRef]
- Wiley, A.; McCormac, A.; Calic, D. More than the individual: Examining the relationship between culture and Information Security Awareness. Comput. Secur. 2020, 88, 101640. [Google Scholar] [CrossRef]
- Parsons, K.; Calic, D.; Pattinson, M.; Butavicius, M.; McCormac, A.; Zwaans, T. The human aspects of information security questionnaire (HAIS-Q): Two further validation studies. Comput. Secur. 2017, 66, 40–51. [Google Scholar] [CrossRef]
- Van Niekerk, J.; Von Solms, R. Information security culture: A management perspective. Comput. Secur. 2010, 29, 476–486. [Google Scholar] [CrossRef]
- Yeng, P.K.; Yang, B.; Snekkenes, E.A. Healthcare Staffs’ Information Security Practices Towards Mitigating Data Breaches: A Literature Survey. pHealth 2019, 239–245. [Google Scholar]
- Anwar, M.; He, W.; Ash, I.; Yuan, X.; Li, L.; Xu, L. Gender difference and employees’ cybersecurity behaviors. Comput. Hum. Behav. 2017, 69, 437–443. [Google Scholar] [CrossRef] [Green Version]
- Herath, T.; Rao, H.R. Encouraging information security behaviors in organizations: Role of penalties, pressures and perceived effectiveness. Decis. Support Syst. 2009, 47, 154–165. [Google Scholar] [CrossRef]
- D’Arcy, J.; Lowry, P.B. Cognitive-affective drivers of employees’ daily compliance with information security policies: A multilevel, longitudinal study. Inf. Syst. J. 2019, 29, 43–69. [Google Scholar] [CrossRef] [Green Version]
- Safa, N.S.; Maple, C.; Watson, T.; Von Solms, R. Motivation and opportunity based model to reduce information security insider threats in organisations. J. Inf. Secur. Appl. 2018, 40, 247–257. [Google Scholar] [CrossRef] [Green Version]
- Posey, C.; Roberts, T.L.; Lowry, P.B. The impact of organizational commitment on insiders’ motivation to protect organizational information assets. J. Manag. Inf. Syst. 2015, 32, 179–214. [Google Scholar] [CrossRef]
- Vance, A.; Siponen, M.; Pahnila, S. Motivating IS security compliance: Insights from habit and protection motivation theory. Inf. Manag. 2012, 49, 190–198. [Google Scholar] [CrossRef]
- Grassegger, T.; Nedbal, D. The Role of Employees’ Information Security Awareness on the Intention to Resist Social Engineering. Procedia Comput. Sci. 2021, 181, 59–66. [Google Scholar] [CrossRef]
- Yeng, P.K.; Szekeres, A.; Yang, B.; Snekkenes, E.A. Mapping the Psycho-social-cultural Aspects of Healthcare Professionals’ Information Security Practices: Systematic Mapping Study. JMIR Hum. Factors 2021, 8, e17604. [Google Scholar] [CrossRef]
- Safa, N.S.; Sookhak, M.; Von Solms, R.; Furnell, S.; Ghani, N.A.; Herawan, T. Information security conscious care behaviour formation in organizations. Comput. Secur. 2015, 53, 65–78. [Google Scholar] [CrossRef] [Green Version]
- Yeng, P.; Fauzi, M.A.; Sun, L.; Yang, B. Legal Aspects of Information Security Requirements for Healthcare in Three Countries: A scoping Review as a Benchmark towards Assessing Healthcare Security Practices. JMIR Hum. Factors 2022, 9, e30050. [Google Scholar] [CrossRef]
- Lebek, B.; Uffen, J.; Breitner, M.H.; Neumann, M.; Hohler, B. Employees’ information security awareness and behavior: A literature review. In Proceedings of the 2013 46th Hawaii International Conference on System Sciences, Maui, HI, USA, 7–10 January 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 2978–2987. [Google Scholar]
- Fernández-Alemán, J.L.; Sánchez-Henarejos, A.; Toval, A.; Sánchez-García, A.B.; Hernández-Hernández, I.; Fernandez-Luque, L. Analysis of health professional security behaviors in a real clinical setting: An empirical study. Int. J. Med Inform. 2015, 84, 454–467. [Google Scholar] [CrossRef] [PubMed]
- Albarrak, A.I. Evaluation of Users Information Security Practices at King Saud University Hospitals. Glob. Bus. Manag. Res. 2011, 3, 1–6. [Google Scholar]
- Ajzen, I.; Madden, T.J. Prediction of goal-directed behavior: Attitudes, intentions, and perceived behavioral control. J. Exp. Soc. Psychol. 1986, 22, 453–474. [Google Scholar] [CrossRef]
- Abawajy, J. User preference of cyber security awareness delivery methods. Behav. Inf. Technol. 2014, 33, 237–248. [Google Scholar] [CrossRef]
- Leonard, L.N.; Cronan, T.P.; Kreie, J. What influences IT ethical behavior intentions—Planned behavior, reasoned action, perceived importance, or individual characteristics? Inf. Manag. 2004, 42, 143–158. [Google Scholar] [CrossRef]
- Albrechtsen, E. A qualitative study of users’ view on information security. Comput. Secur. 2007, 26, 276–289. [Google Scholar] [CrossRef]
- Thirumalai, C.; Chandhini, S.A.; Vaishnavi, M. Analysing the concrete compressive strength using Pearson and Spearman. In Proceedings of the 2017 International Conference of Electronics, Communication and Aerospace Technology (ICECA), Coimbatore, India, 20–22 April 2017; IEEE: Piscataway, NJ, USA, 2017; Volume 2, pp. 215–218. [Google Scholar]
- DeVita, T.; Brett-Major, D.; Katz, R. How are healthcare provider systems preparing for health emergency situations? World Med. Health Policy 2021, 14, 102–120. [Google Scholar] [CrossRef]
- Khalid, M.; Awais, M.; Singh, N.; Khan, S.; Raza, M.; Malik, Q.B.; Imran, M. Autonomous Transportation in Emergency Healthcare Services: Framework, Challenges, and Future Work. IEEE Internet Things Mag. 2021, 4, 28–33. [Google Scholar] [CrossRef]
- Asamani, J.A.; Amertil, N.P.; Chebere, M. The influence of workload levels on performance in a rural hospital. Br. J. Healthc. Manag. 2015, 21, 577–586. [Google Scholar] [CrossRef]
- Nyamtema, A.S. Bridging the gaps in the Health Management Information System in the context of a changing health sector. BMC Med. Inform. Decis. Mak. 2010, 10, 36. [Google Scholar] [CrossRef] [Green Version]
- Gratian, M.; Bandi, S.; Cukier, M.; Dykstra, J.; Ginther, A. Correlating human traits and cyber security behavior intentions. Comput. Secur. 2018, 73, 345–358. [Google Scholar] [CrossRef]
- Omsorgsdepartementet. How Does Personality Influence Your Cyber Risk? 2021. Available online: https://www.cybsafe.com/community/blog/how-does-personality-influence-your-cyber-risk/ (accessed on 22 June 2022).
- McCormac, A.; Zwaans, T.; Parsons, K.; Calic, D.; Butavicius, M.; Pattinson, M. Individual differences and information security awareness. Comput. Hum. Behav. 2017, 69, 151–156. [Google Scholar] [CrossRef]
- Uffen, J.; Guhr, N.; Breitner, M.H. Personality Traits and Information Security Management: An Empirical Study of Information Security Executives. In Proceedings of the International Conference on Information Systems, ICIS 2012, Orlando, FL, USA, 16–19 December 2012. [Google Scholar]
- Shropshire, J.; Warkentin, M.; Sharma, S. Personality, attitudes, and intentions: Predicting initial adoption of information security behavior. Comput. Secur. 2015, 49, 177–191. [Google Scholar] [CrossRef]
- Prentice-Dunn, S.; Rogers, R.W. Protection motivation theory and preventive health: Beyond the health belief model. Health Educ. Res. 1986, 1, 153–161. [Google Scholar] [CrossRef]
- Rosenstock, I.M. The health belief model and preventive health behavior. Health Educ. Monogr. 1974, 2, 354–386. [Google Scholar] [CrossRef]
- Cheng, L.; Li, Y.; Li, W.; Holm, E.; Zhai, Q. Understanding the violation of IS security policy in organizations: An integrated model based on social control and deterrence theory. Comput. Secur. 2013, 39, 447–459. [Google Scholar] [CrossRef]
- Berinsky, A.J.; Margolis, M.F.; Sances, M.W. Separating the shirkers from the workers? Making sure respondents pay attention on self-administered surveys. Am. J. Political Sci. 2014, 58, 739–753. [Google Scholar] [CrossRef]
- Curran, P.; Hauser, D. Understanding responses to check items: A verbal protocol analysis. In Proceedings of the 30th Annual Conference of the Society for Industrial and Organizational Psychology, Philadelphia, PA, USA, 23–25 April 2015. [Google Scholar]
- Huang, J.L.; Bowling, N.A.; Liu, M.; Li, Y. Detecting insufficient effort responding with an infrequency scale: Evaluating validity and participant reactions. J. Bus. Psychol. 2015, 30, 299–311. [Google Scholar] [CrossRef]
- Kung, F.Y.; Kwok, N.; Brown, D.J. Are attention check questions a threat to scale validity? Appl. Psychol. 2018, 67, 264–283. [Google Scholar] [CrossRef] [Green Version]
- Gosling, S.D.; Rentfrow, P.J.; Swann, W.B., Jr. A very brief measure of the Big-Five personality domains. J. Res. Personal. 2003, 37, 504–528. [Google Scholar] [CrossRef]
- Yeng, P.; Yang, B.; Snekkenes, E. Observational Measures for Effective Profiling of Healthcare Staffs’ Security Practices. In Proceedings of the 2019 IEEE 43rd Annual Computer Software and Applications Conference (COMPSAC), Milwaukee, WI, USA, 15–19 July 2019; IEEE: Piscataway, NJ, USA, 2019; Volume 2, pp. 397–404. [Google Scholar]
- Parsons, K.; McCormac, A.; Butavicius, M.; Pattinson, M.; Jerram, C. The Development of the Human Aspects of Information Security Questionnaire (HAIS-Q). In Proceedings of the 24th Australasian Conference on Information Systems (ACIS), Melbourne, Australia, 4–6 December 2013. [Google Scholar]
- Drennan, J. Cognitive interviewing: Verbal data in the design and pretesting of questionnaires. J. Adv. Nurs. 2003, 42, 57–63. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Schechter, S.; Beatty, P.; Block, A. Cognitive issues and methodological implications in the development and testing of a traffic safety questionnaire. In Proceedings of the 49th Annual Conference of the American Association for Public Opinion Research, Danvers, MA, USA, 11–15 May 1994; pp. 1215–1219. [Google Scholar]
- Martin, E.; Schechter, S.; Tucker, C. Interagency Collaboration among the Cognitive Laboratories: Past Efforts and Future Opportunities. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.147.94&rep=rep1&type=pdf (accessed on 22 June 2022).
- Reeve, B.B.; Mâsse, L.C. Item response theory modeling for questionnaire evaluation. In Methods for Testing and Evaluating Survey Questionnaires; John Wiley & Sons: Hoboken, NJ, USA, 2004; pp. 247–273. [Google Scholar]
- Biemer, P. Modeling measurement error to identify flawed questions. In Methods for Testing and Evaluating Survey Questionnaires; John Wiley & Sons: Hoboken, NJ, USA, 2004; pp. 225–246. [Google Scholar]
- Hauke, J.; Kossowski, T. Comparison of Values of Pearson’s and Spearman’s Correlation Coefficient on the Same Sets of Data. 2011. Available online: https://sciendo.com/downloadpdf/journals/quageo/30/2/article-p87.pdf?pdfJsInlineViewToken=1302953392&inlineView=true (accessed on 22 June 2022).
- Arachchilage, N.A.G.; Love, S. A game design framework for avoiding phishing attacks. Comput. Hum. Behav. 2013, 29, 706–714. [Google Scholar] [CrossRef]
- Shamsuddin, A.; Mubin, N.A.B.A.; Zain, N.A.B.M.; Akil, N.A.B.M.; Aziz, N.A.B.A. Perception of Managers on the Effectiveness of the Internal Audit Functions: A Case Study in TNB. 2015. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.1040.1676&rep=rep1&type=pdf (accessed on 22 June 2022).
- Hair, J.F.; Page, M.; Brunsveld, N. Essentials of Business Research Methods; Routledge: Oxfordshire, UK, 2019. [Google Scholar]
- Pallant, J. SPSS Survaival Manual: A Step by Step Guide to Data Analysis Using SPSS; Routledge: Oxfordshire, UK, 2010. [Google Scholar]
- Briggs, S.R.; Cheek, J.M. The role of factor analysis in the development and evaluation of personality scales. J. Personal. 1986, 54, 106–148. [Google Scholar] [CrossRef]
- Vaske, J.J.; Beaman, J.; Sponarski, C.C. Rethinking internal consistency in Cronbach’s alpha. Leis. Sci. 2017, 39, 163–173. [Google Scholar] [CrossRef]
- Groeneveld, R.A.; Meeden, G. Measuring skewness and kurtosis. J. R. Stat. Soc. Ser. D (Stat.) 1984, 33, 391–399. [Google Scholar] [CrossRef]
- Fairburn, N.; Shelton, A.; Ackroyd, F.; Selfe, R. Beyond Murphy’s Law: Applying Wider Human Factors Behavioural Science Approaches in Cyber-Security Resilience. In Proceedings of the International Conference on Human-Computer Interaction, Málaga, Spain, 22–24 September 2021; Springer: Berlin/Heidelberg, Germany, 2021; pp. 123–138. [Google Scholar]
- Bowen, B.M.; Devarajan, R.; Stolfo, S. Measuring the human factor of cyber security. In Proceedings of the 2011 IEEE International Conference on Technologies for Homeland Security (HST), Waltham, MA, USA, 15–17 November 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 230–235. [Google Scholar]
- Taylor, R. Interpretation of the correlation coefficient: A basic review. J. Diagn. Med. Sonogr. 1990, 6, 35–39. [Google Scholar] [CrossRef]
- Parsons, K.; McCormac, A.; Butavicius, M.; Pattinson, M.; Jerram, C. Determining employee awareness using the human aspects of information security questionnaire (HAIS-Q). Comput. Secur. 2014, 42, 165–176. [Google Scholar] [CrossRef]
- Torres, H.G.; Gupta, S. The Misunderstood Link: Information Security Training Strategy. In Proceedings of the 24th Americas Conference on Information Systems, New Orleans, LA, USA, 16–18 August 2018. [Google Scholar]
- Zafar, H. Cybersecurity: Role of Behavioral Training in Healthcare. 2016. Available online: https://core.ac.uk/download/pdf/301368936.pdf (accessed on 22 June 2022).
- Ghazvini, A.; Shukur, Z. Review of information security guidelines for awareness training program in healthcare industry. In Proceedings of the 2017 6th International Conference on Electrical Engineering and Informatics (ICEEI), Langkawi, Malaysia, 25–27 November 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Alami, H.; Gagnon, M.P.; Ahmed, M.A.A.; Fortin, J.P. Digital health: Cybersecurity is a value creation lever, not only a source of expenditure. Health Policy Technol. 2019, 8, 319–321. [Google Scholar] [CrossRef]
- Koppel, R.; Smith, S.; Blythe, J.; Kothari, V. Workarounds to computer access in healthcare organizations: You want my password or a dead patient. In Driving Quality in Informatics: Fulfilling the Promise; IOS Press: Amsterdam, The Netherlands, 2015; pp. 215–220. [Google Scholar]
- Stobert, E.; Barrera, D.; Homier, V.; Kollek, D. Understanding cybersecurity practices in emergency departments. In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems, Honolulu, HI, USA, 25–30 April 2020; pp. 1–8. [Google Scholar]
- Middaugh, D.J. Cybersecurity Attacks during a Pandemic: It Is Not Just IT’s Job! Medsurg Nurs. 2021, 30, 65–66. [Google Scholar]
- Shappie, A.T.; Dawson, C.A.; Debb, S.M. Personality as a predictor of cybersecurity behavior. Psychol. Pop. Media 2020, 9, 475. [Google Scholar] [CrossRef]
- Halevi, T.; Memon, N.; Lewis, J.; Kumaraguru, P.; Arora, S.; Dagar, N.; Aloul, F.; Chen, J. Cultural and psychological factors in cyber-security. In Proceedings of the 18th International Conference on Information Integration and Web-based Applications and Services, Singapore, 28–30 November 2016; pp. 318–324. [Google Scholar]
- Skorek, M.; Song, A.V.; Dunham, Y. Self-esteem as a mediator between personality traits and body esteem: Path analyses across gender and race/ethnicity. PLoS ONE 2014, 9, e112086. [Google Scholar] [CrossRef] [PubMed]
- Box, D.; Pottas, D. Improving information security behaviour in the healthcare context. Procedia Technol. 2013, 9, 1093–1103. [Google Scholar] [CrossRef] [Green Version]
- Gurusamy, K.; Aggarwal, R.; Palanivelu, L.; Davidson, B. Systematic review of randomized controlled trials on the effectiveness of virtual reality training for laparoscopic surgery. J. Br. Surg. 2008, 95, 1088–1097. [Google Scholar] [CrossRef] [PubMed]
- Larsen, C.R.; Oestergaard, J.; Ottesen, B.S.; Soerensen, J.L. The efficacy of virtual reality simulation training in laparoscopy: A systematic review of randomized trials. Acta Obstet. Gynecol. Scand. 2012, 91, 1015–1028. [Google Scholar] [CrossRef]
| Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).