Abstract
The area of smart homes is one of the most popular for deploying smart connected devices. One of the most vulnerable aspects of smart homes is access control. Recent advances in IoT have led to several access control models being developed or adapted to IoT from other domains, with few specifically designed to meet the challenges of smart homes. Most of these models use role-based access control (RBAC) or attribute-based access control (ABAC) models. As of now, it is not clear what the advantages and disadvantages of ABAC over RBAC are in general, and in the context of smart-home IoT in particular. In this paper, we introduce HABAC, an attribute-based access control model for smart-home IoT. We formally define and demonstrate its features through two use-case scenarios and a proof-of-concept implementation. Furthermore, we present an analysis of as compared to the previously published EGRBAC (extended generalized role-based access control) model for smart-home IoT by first describing approaches for constructing specification from EGRBAC and vice versa in order to compare the theoretical expressiveness power of these models, and second, analyzing and EGRBAC models against standard criteria for access control models. Our findings suggest that a hybrid model that combines both and EGRBAC capabilities may be the most suitable for smart-home IoT, and probably more generally.
1. Introduction and Motivation
The Internet of Things (IoT) describes the network of physical objects (things) that are embedded with sensors, software, and other technologies to connect and exchange data with other devices and systems over the Internet [1]. IoT has been used in a wide variety of applications, including infrastructure applications (smart cities, energy management), consumer applications (smart homes, elder care), organizational applications (medical and health care, vehicular communication systems), industrial applications (manufacturing, agriculture), and military applications (Internet of Battlefield Things).
In 2017, the global market for the Internet of Things (IoT) surpassed USD 100 billion in revenue for the first time, and forecasts suggest that the figure will rise to USD 1.6 trillion by 2025. As a result of such a prognosis, it is predicted that the technology will reach heights that no one could imagine. However, with the growing popularity of IoT devices, there will be an increase in IoT security concerns.
Smart homes are among the most popular areas for deploying smart connected devices. They are changing our lifestyles. However, with new opportunities come new challenges. Surprisingly little attention has been paid to access control policy specification and authentication in home IoT. Smart homes differ from traditional computing domains in many notable ways [2]. Home-IoT users have complex social relationships and use the same devices. In addition, most smart-home devices lack screens and keyboards, which makes them more convenient, but makes access control management more difficult. Several real-world examples of the deficiencies of current policies and authentication procedures for controlling access to home-IoT devices have emerged [2,3,4].
To attain the best results and minimize risks and threats, an organization must select an appropriate access control model in light of its diverse structure, requirements, and specifications. Several access control models have been described in the literature for IoT in general, a few of which have been developed specifically for smart homes. Most of the proposed IoT AC models are based on ABAC or RBAC. According to some researchers, RBAC is better suited for IoT since it is easier to manage and review, whereas ABAC is more challenging [5,6,7]. Other researchers assert that ABAC models are more scalable and dynamic because they can capture information about different devices and contexts. However, RBAC models can be extended to be dynamic and fine-grained. For example, the recent EGRBAC (extended generalized role-based access control) model [8] for smart-home IoT. EGRBAC can express environment and device characteristics and is suitable for constrained home environments. Therefore, in the case of smart homes, it is not completely clear what the advantages of ABAC over RBAC are, and vice versa.
In this paper, we introduce , an attribute-based access control model for smart-home IoT. Our model is dynamic and fine-grained. It captures users, environment, operations, and devices characteristics. We provide a detailed formal definition of our model and illustrate its features through two use-case scenarios and a proof-of-concept implementation.
Furthermore, we compare to the previously published EGRBAC model for smart-home IoT [8]. We chose to compare against EGRBAC for the following reason. EGRBAC is a dynamic contextual-aware RBAC-based access control model specifically designed to meet smart-home challenges. Our primitive insight is that a hybrid approach will better address smart-home IoT access control requirements, as this was the case for some traditional access control domains. However, this insight needs to be further explored by comparing RBAC and ABAC-based models specifically defined to meet smart-home challenges. In addition, this comparison will serve as a guide in developing appropriate hybrid models. Toward this goal, in this paper, we provide approaches for constructing specification from EGRBAC and vice versa to compare the theoretical expressiveness power of these models. Then, we evaluate these models against standard criteria for access control models adapted from [9]
The paper is organized as follows. In Section 2, we provide an analysis and review of related work, including an overview of EGRBAC [8]. In Section 3, we introduce the model along with two use-case scenarios and a proof-of-concept implementation. Furthermore, we conducted different test scenarios to depict the performance of our implementation. In Section 4 we compare between EGRBAC and in terms of theoretical expressiveness power. In Section 5 we conduct a comprehensive theoretical comparison between EGRBAC and against standard criteria for access control models. Section 6 discusses the insights of this work. Finally, Section 7 concludes the paper.
2. Related Work
Presently, IoT is one of the most researched topics in the literature. However, the entire IoT ecosystem still faces security challenges, from manufacturers to users. A number of researchers have studied IoT security and privacy issues [10,11,12,13,14,15]. Furthermore, some researchers have investigated the security risks and design concerns of IoT frameworks [15,16,17,18,19,20]. Most researchers generally accept that access control is a critical service in IoT.
The literature has presented many access control solutions (users to devices and/or devices to devices) that apply to different IoT applications. In [21], the authors extensively surveyed access control in IoT environments. However, few of them explicitly addressed smart-home challenges.
Some solutions rely on RBAC [22,23] (as in [5,8,24,25,26,27,28,29]). Other solutions, however, rely on ABAC [30,31]. For instance, the authors in [32] introduced an ABAC-based model that focuses on device-to-device access control. However, they did not illustrate their model through a performance analysis or at least a use-case scenario. In [33,34] the authors focused on providing sophisticated attribute-based encryption (ABE) models for smart grids, while they did not discuss the ABAC models that they consider. Additionally, for computationally constrained smart-home devices, an ABE model may not be appropriate. In [35] the authors introduced a formalized dynamic and fine-grained ABAC model for smart cars, which does not apply to the smart-home case. Recently, Bhatt et al. [36] proposed a conceptual attribute-based access control and communication control model for IoT. However, their access control model does not capture environment attributes. Our proposed model is an ABAC-based model that is dynamic and fine-grained. Moreover, it captures the characteristics of users, environments, operations, and devices.
Some researchers argue that contrary to ABAC-based models, RBAC-based models fail to capture changing characteristics such as environment attributes (time of the day, weather information) and device characteristics (device type, device state). However, the authorization process in RBAC is much simpler. Therefore, a combined access control model has been proposed by [6].
Additionally, the literature proposes several models that are based on blockchain technology [37,38,39,40,41]. However, as described by [39], blockchain technology possesses some technical characteristics that could limit its application, such as processing time and cryptocurrency fees. Only a few solutions based on UCON [42,43,44] have been presented in the literature, e.g., [45,46,47]. There have been some other access control models proposed for the Internet of Things. For example, in [48] the authors presented a certificate-based device access control scheme in an IoT environment. Researchers in [7,21,49,50,51] conducted surveys on different IoT access control models in the literature.
The authors of [2] presented a new perspective on home-IoT access control policies. They argued that smart-home IoT has unique characteristics that necessitate a rethinking of access control. However, few solutions in the literature are proposed specifically to meet smart-home IoT challenges. Here are some examples. In [32], the authors provided a device-to-device ABAC access control framework for smart homes. The authors in [24] introduced an RBAC-based access control model for aware homes. Moreover, in [52] the authors used identity-based encryption to implement a function-based access control model in smart homes. In [53], the authors proposed a protocol for authentication and key exchange in smart homes. Researchers in [54] developed a high-level access control mechanism for a multi-user and multi-device smart-home environment.
Based on analysis by He et al. [2] and a survey by Ouddah et al [21], Ameer et al [8] recently presented criteria for home-IoT access control models. Moreover, the same authors proposed the EGRBAC model. It is a policy model for smart-home IoT access control, which is based on RBAC and conforms to both of the [2,8] characteristics. As opposed to traditional RBAC, EGRBAC captures contextual environmental changes and different devices characteristics. Therefore, it refutes the argument that RBAC-based models are unsuitable and rigid when dealing with changes in the environment and device or permissions characteristics. Therefore, it is not entirely clear what the advantages of ABAC over RBAC are, and vice versa, in the setting of home IoT. In this paper, we analyze (our proposed ABAC-based model) compared to EGRBAC [8] (a dynamic, fine-grained RBAC-based model), and vice versa. We briefly review this model below since it is relevant to Section 4.1 and Section 4.2.
2.1. Background: EGRBAC Model
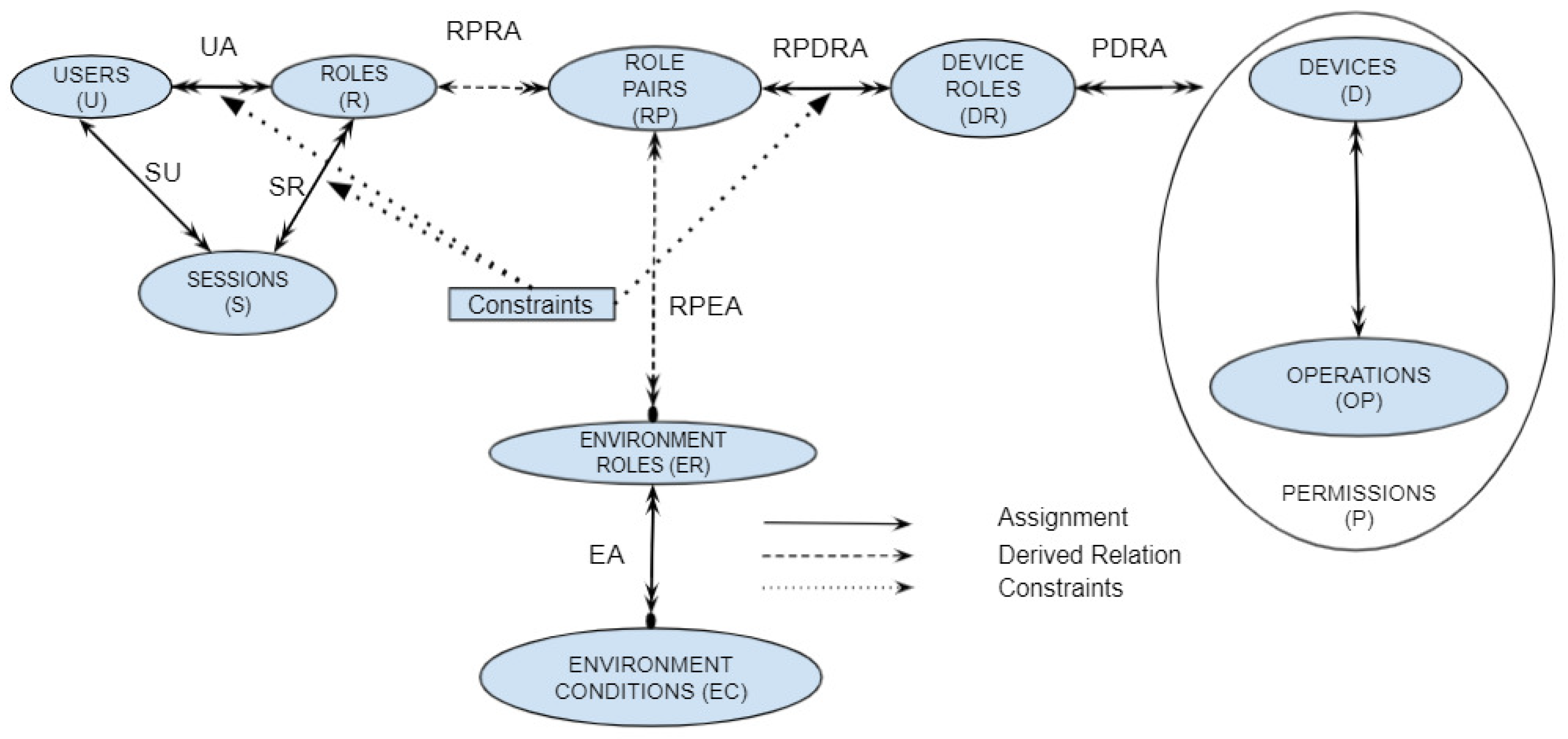
Ameer et al introduced the extended generalized role-based access control model [8]. It is a dynamic, fine-grained RBAC-based model that grants access based on the specific permission required rather than at device granularity. In addition to the usual concept of user roles, EGRBAC incorporates the notion of device roles and environment roles. This is illustrated in Figure 1.
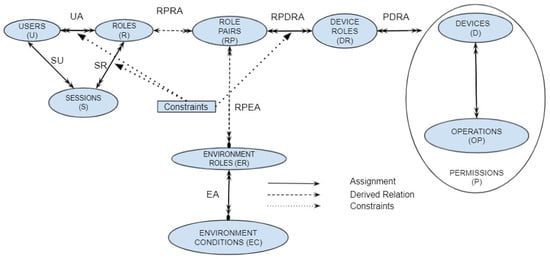
Figure 1.
EGRBAC model components.
EGRBAC uses the familiar User (U), Role (R), and Session (S) sets in RBAC [22,23]. The term “user” refers to a person who uses smart-home devices as authorized. Roles (R) are similar to the traditional RBAC user roles. Nevertheless, in the case of smart homes, a role explicitly represents the relationship between a user and his or her family. Roles are assigned to different users through the many-to-many relationship UA. The system allows users to establish sessions to activate a subset of the roles they have been assigned to. A user may have more than one session active at the same time. SU is a many-to-one relationship that maps each session to its unique, controlling user. SR is a many-to-many relationship that maps each session to the set of roles associated with it.
A Device (D) is a smart-home device such as a smart door lock. Operations (OP) represent actions performed on devices according to manufacturer specifications. A permission is an approval to perform an operation on one device, i.e., it is a device–operation pair. Furthermore, as a way of categorizing permissions for different devices, device roles (DR) are defined. For example, we can categorize the dangerous permissions of various smart devices by creating a device role called dangerous devices and assigning dangerous permissions (such as turning on the oven, turning on the mower, and opening and closing the front door lock) to it. The many-to-many PDRA relationship specifies this assignment.
Environmental contexts, such as daytime/nighttime and winter/summer, are captured through the environment roles (ER) component. Environment roles are turned on/off (i.e., triggered) by environment conditions (EC). EA maps each environment role to the subset of related environment conditions . It implies that when each is active, the environment role is also active. For example, suppose the environment role should be active on weekend evenings. To express this environment role in EGRBAC, we create the environment condition , which will be active during the weekend, and the environment condition , which will be active during the evening and add the relationship , to the set EA.
Each role pair combines a role and a subset of environment roles. A role pair has a role part that is the single role associated with , and an environment role part denotes the set of environment roles associated with and is a subset of . RPRA associates each role to one or more role pairs. RPEA associates each role pair to a subset of ER. A role pair is active, when each environment role in the set of environment role is active, where is associated with through the relation RPEA.
All these components are brought together by RPDRA, which assigns device roles to role pairs. Therefore, for each role pair , the single role associated with it through RPRA can access all device roles assigned to it through RPDRA, as long as the set of environment roles associated with through RPEA, which is is active.
Essentially, the basic idea in EGRBAC is that a user is assigned a subset of roles and, according to the current active roles in a session and the current active environment roles, some role pairs will be active, giving the user access to the permissions assigned to the device roles assigned to the currently active role pairs. Figure 1 illustrates EGRBAC.
EGRBAC describes three types of constraints. (a) Permission–role constraints. These constraints prevent specific roles from accessing specific permissions during assignment time. This type of constraint is applied to the RPDRA relationship. For example, if we have a permission–role constraint , where . This constraint prevents any assignment relation from being added to the set RPDRA, if gives the role access to the permission . (b) Static Separation of Duty (SSD) is the familiar SSD in RBAC. It enforces constraints on the assignment of users to roles. This type of constraint is applied to the UA relationship. (c) Dynamic Separation of Duty (DSD) is the familiar DSD in RBAC. With DSD, it is permissible for a user to be authorized as a member of a set of roles that do not constitute a conflict of interest when acted independently but produce policy concerns when allowed to be acted simultaneously [55] in the same session. This type of constraint is applied to the SR relationship.
3. HABACα Model for Smart-Home IoT
Models based on ABAC are arguably well-suited for sophisticated domains, such as smart homes. By using attributes of users, sessions (subjects), environments, operations, and objects, they can specify dynamic, flexible, and fine-grained authorization policies. This section introduces our (Home-IoT Attribute-Based Access Control) model. This model governs smart-home user-to-device interactions.
3.1. Formal Definition
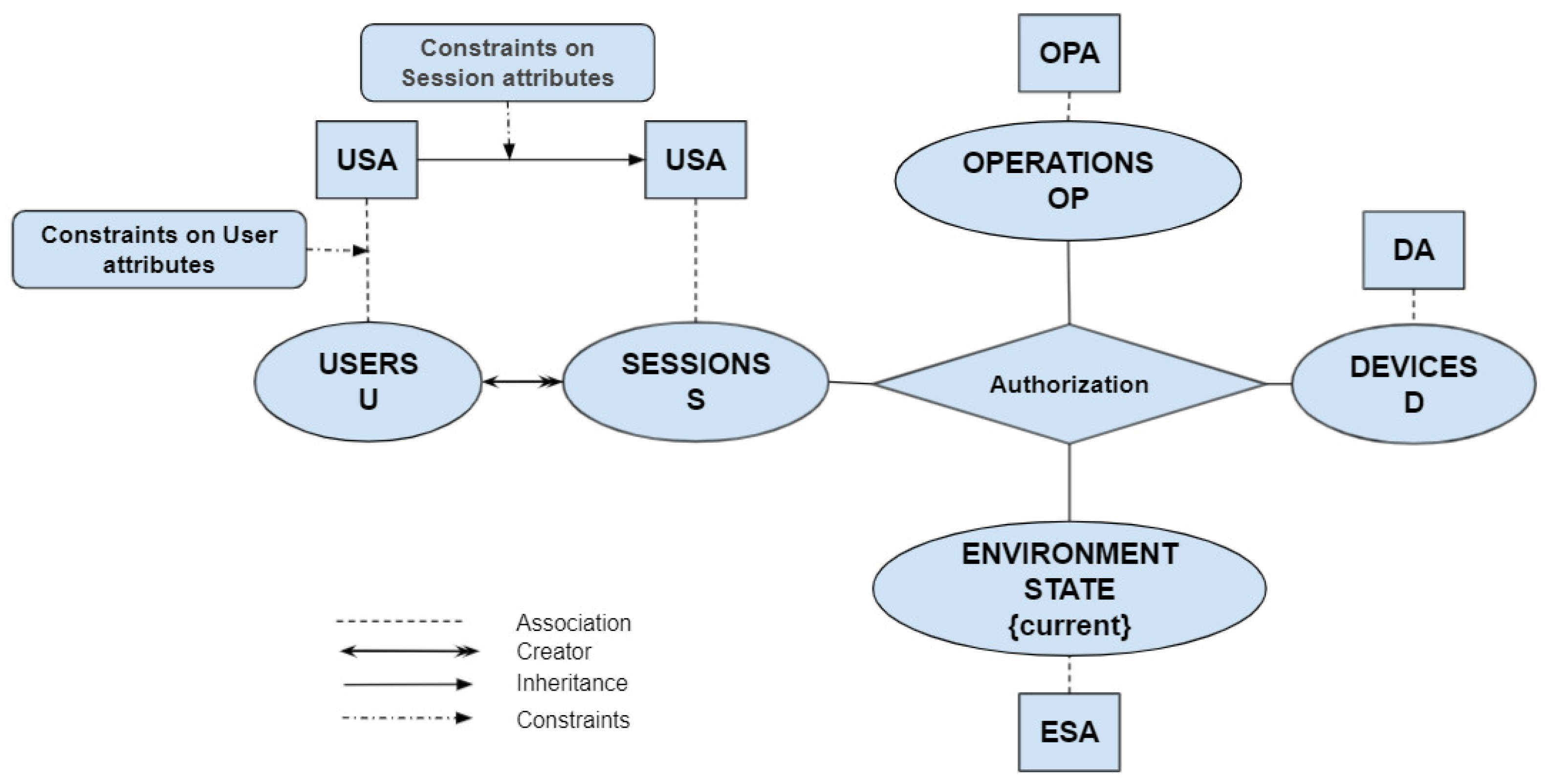
The model is inspired by [31,56]. The basic model components are illustrated in Figure 2 and are formally defined in Table 1 and Table 2. It consists of four sets as follows: Users (U), Environment States (ES), Operations (OP), and Devices (D). These sets are presented in ovals. Moreover, attribute functions are presented in squares. We have four attribute functions, User/Session Attributes (USA), Environment-State Attributes (ESA), Operation Attributes (OPA), and Device Attributes (DA). The rectangles indicate two types of constraints: constraints on user attributes and constraints on session attributes.
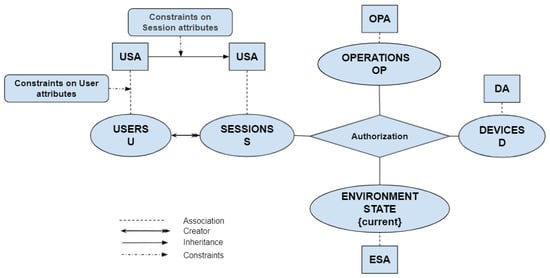
Figure 2.
Model.

Table 1.
Model formalization part I: basic components.

Table 2.
Model formalization part II: attribute authorization function.
3.1.1. Basic Sets and Functions
User set (U) refers to human beings communicating directly with smart objects (things). The system allows users to create sessions during which they can perform some operations on the system. Sessions (S) operate similarly to subjects in [31]. Only the user who initiates the session has the authority to terminate it. Each session s is associated with its unique user creator by the function .
Devices (D) refer to smart-home devices (smart things); for instance, smart TV. Operations () are activities performed on devices in accordance with manufacturer specifications. The function maps each device d to the set of valid operations on d.
The Environment States set () is a singleton set that only includes the state “current”. The state denotes the picture of the environment at the current time instant. However, future extensions of this component, for instance, may be , which include other instants of time such as yesterday and last week. However, such generalization requires a careful investigation on how we will track time and to what extent.
3.1.2. Attribute Functions and Values
Each of the users, sessions, environment states, devices, and operations possess characteristics that are expressed as their attributes. An attribute is a function that takes an element such as a user and returns a certain value from its range. User/Session attribute functions set () is the set of attributes associated with both users and sessions. Each session s inherits a subset of the attributes of its unique user creator. This is controlled by the unique user creator . If a session s inherited a user session attribute from his user , then it is required that . The device attribute functions set () consists of attributes related to smart devices, such as “kitchen devices” and “Alex devices”. The operation attribute functions set () is a collection of attributes corresponding to different operations. For example, if you wish to characterize kid-friendly operations, you may create an operation attribute entitled “Kid-Friendly Operations” and associate it with those operations. Environment-state attribute functions set () describes the environment condition of the current instance of time. For example, “day”, “time”, and “weather condition”.
To better demonstrate the concept of attributes, we will use the use case illustrated in Figure 3. We should mention that this use case is incomplete since it does not contain an authorization function. However, the main purpose is to illustrate the concept of attributes. In this use case, we have three users , , and . The user/session attribute function captures the user relationship to the home. From Figure 3 we can notice that is the parent, is the kid, and is the teenager in the house. The user/session attribute function captures the user’s current location inside the house. Moreover, we have four devices , , , and . We have one device attribute function . captures whether the device is a dangerous kitchen device or not. Finally, we have two environment-state attribute functions, and , which capture the current day and users inside the house, respectively.

Figure 3.
Attributes Use Case.
The main reason for using different sets of attribute functions for different components in our model is that different components have different attribute functions. For instance, the user/session attribute function is not relevant to the set of devices D. Moreover, the device attribute function does not apply to the set of users. We cannot consider a specific user as a dangerous kitchen device; the evaluation
is not semantically correct.
Basically, an attribute range is composed of a finite set of atomic values. Each attribute function has a range , where represents the range of values to which the attribute function can be evaluated. For example, in Figure 3, the user/session attribute function range is , the user/ session attribute function range is . Similarly, the device attribute function range is , the environment-state attribute function range is , and finally the environment-state attribute function range is the set of users U.
Each attribute function is an atomic-valued attribute or a set-valued attribute. An atomic-valued attribute will return exactly one value from its range. In the use case given in Figure 3, the user/session attribute functions and are both atomic-valued attributes since they map different users into one value only from the attribute range. The device attribute function is an atomic-valued attribute too. It takes one device as an input and returns only one value from the attribute function range as an output, either or , since one device cannot be dangerous and non-dangerous at the same time. Similarly, the environment-state attribute function is an example of an atomic-valued attribute.
On the other hand, a set-valued attribute will return a subset of the range, and not only one value from the range as in the case of atomic-valued attribute functions. For instance, in the use case given in Figure 3, the environment-state attribute function is a set-valued attribute. attribute function has a range equal to the set of users U, and it maps the environment state to a subset of values from that range. It returns a set with the names of users who are currently inside the house.
Moreover, we distinguish between two types of attributes: static and dynamic. All attributes indeed may change over a long time. However, some attributes are “relatively” static, as they tend to remain static (they evaluate to the same values) over a long period of time. Setting and changing the values of static attributes may require administrator intervention. For example, in our use case, the user/session attribute function is considered static. To further illustrate this, let us consider the user . The attribute function , in this case, evaluates to , which tends to remain constant for a long time till grows up and becomes a teenager, at which point an administrator action is required to change the value of this attribute to ; as a result, will evaluate to . Similarly, is considered a static device attribute too.
On the other hand, dynamic attributes are always changing due to various circumstances, such as time of the day, user location, etc. In our use case, , , and are all considered to be dynamic attributes. Values of dynamic attributes are automatically determined by sensors deployed in the smart home and under homeowner control.
User/session attribute functions, device attribute functions, operation attribute functions, and environment-state attribute functions can all be classified as static or dynamic attribute functions. Moreover, all attribute functions can be classified as static or dynamic, whether atomic-valued or set-valued. However, the differentiation between static and dynamic attribute functions is unnecessary for how the model works formally. The process for triggering different attributes is outside the scope of our model.
Operation and device attribute functions are partial functions. Hence, some devices or operations will not be associated with some attributes. User/Session and environment-state attributes, on the other hand, are total functions.
In mathematics, a partial function f from a set X to a set Y is a function from a subset S of X (possibly X itself) to Y [57]. Since operation attribute functions and device attribute functions are defined as partial functions, in the use case illustrated in Figure 3, the device attribute function does not have to map each device d in the set of devices D into a value from the range . The attribute function only maps the devices and into the values and respectively. However, it does not map the devices and into any value. In other words, will be evaluated to be undefined.
On the other hand, total functions are defined for all elements in its domain. That being said, any static or dynamic attribute function in the set of user/session attribute functions is defined for every user in the set of users U. For instance, the user/session attribute function is defined for every user u in the set of users U. Moreover, any static or dynamic environment-state attribute function in the set of environment-state attribute functions is defined for every environment state in the set of environment state .
3.1.3. Constraints
These are invariants that must never be violated. There are two types of constraints defined by . First is constraints on user attributes. These constraints impose restrictions on user attributes. In other words, if a specific attribute value is assigned to a user, the user is prohibited from being assigned to another attribute value. For example, consider the following user attribute constraint:
The above constraint implies that for any user u if , then it is required that .
The second type of constraint is constraints on session attributes. These constraints restrict the attributes that may be used in sessions. Here, it is permissible for a user to be assigned to different attribute values that do not constitute a conflict of interest when inherited independently by different sessions but produce policy concerns when allowed to be inherited together in the same session.
The concept of constraints is an integral part of , and it is a powerful mechanism for laying out higher-level policy. When specific attribute values are declared to be mutually exclusive, there is less concern about assigning conflicting or mutually exclusive attribute values to individual users. is an operational access control model. Managing and enforcing constraints is part of the administrative access control, which is outside the scope of this manuscript.
3.1.4. Attributes Authorization Function
A two-valued Boolean function is evaluated for each access decision. It is defined using the grammar of Table 2. For a specific session , operation , and device the authorization function is evaluated by substituting the actual attribute values of , , and for the corresponding symbolic placeholders and evaluating the resulting logical formula to be true or false. Any term that references an undefined attribute value is evaluated as false.
The term refers to any atomic logical declarative sentence. An atomic sentence is a type of declarative sentence that is either true or false and which cannot be broken down into other simpler sentences [58]. Consider Use Case A for more illustration.
is an operational access control model. Authorization function creation, check, and management tasks are considered part of administrative access control, hence outside the scope of this model.
3.1.5. Check Access Predicate
The predicate is evaluated in each access request. When a session attempts operation on device in the context of environment-state the predicate evaluates to be true if the following conditions are satisfied:
- The operation is assigned to the device by the device manufacturer.
- The authorization function is evaluated to be true.
3.2. Use Cases
In this section, we describe two use cases to illustrate the components and configurations of .
3.2.1. Use Case A
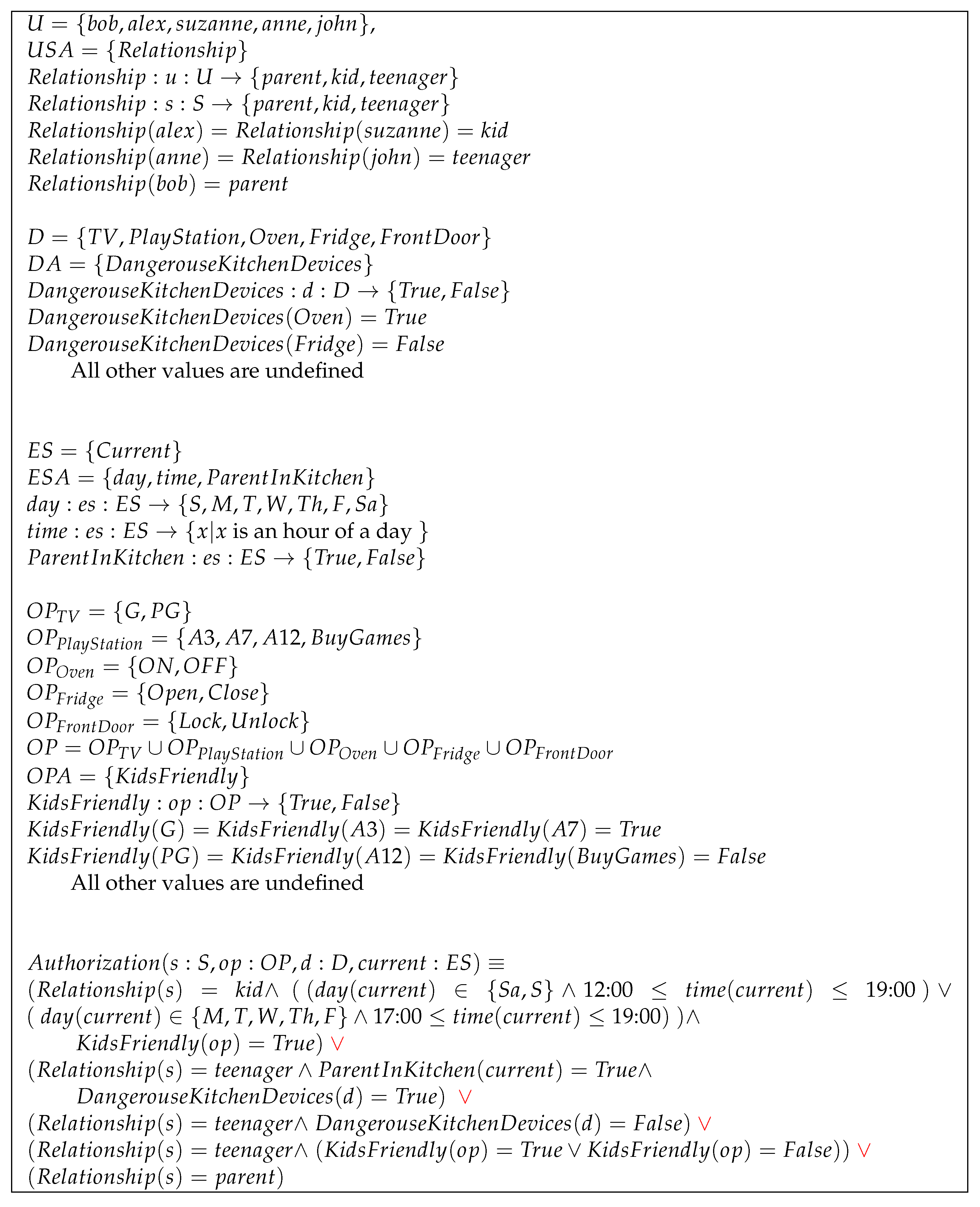
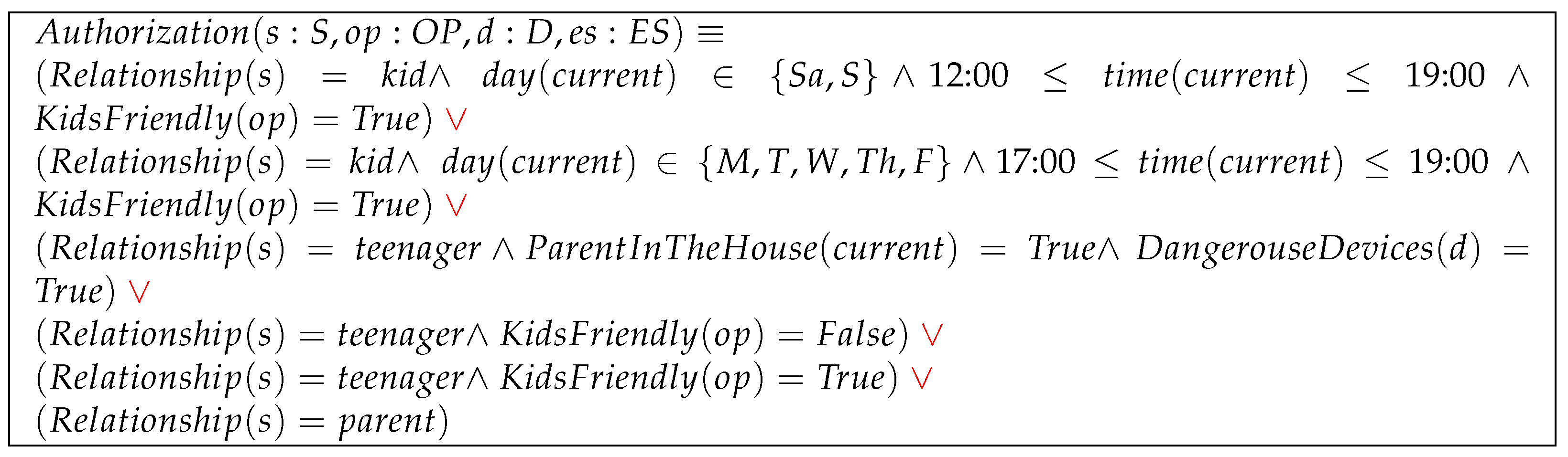
In this use case, the goals are as follows: (a) Kids should be allowed to use kid-friendly operations on entertainment devices (G and contents on TV, (games for group aged below three years old), and (games for children under the age of seven) on PlayStation) during a specific time (weekend afternoons and evenings, and weekday evenings). (b) Teenagers should only be permitted to use dangerous kitchen devices (Oven) if one of their parents is present in the kitchen. (c) Provide teenagers with unconditional permission to use non-dangerous kitchen devices (Fridge). (d) Provide teenagers with unconditional access to entertainment devices. (e) Parents should be permitted to use any operation on any device without restrictions.
Figure 4 illustrates how can be configured to achieve these objectives. Here, we have five users, , , , , and with user attribute respectively assigned to the values , , , , and . Upon creation of a session s, this session will automatically inherit a subset of attributes from . There are five devices and . , and are assigned the following device attributes by the house owner , and . There are 12 operations G, , , , , , , , , , , and . These operations are assigned to operation attributes as follows: , and , while , , . Since device attribute functions and operation attribute functions are partial functions, all other operations and devices attributes values are undefined. Any term that references an undefined attribute value is evaluated as false. The environment-state has three attribute functions , and .

Figure 4.
Use Case A configuration.
The authorization function is a disjunction of five propositional statements. The disjunctions between different propositional statements are marked red for semantic illustration purposes only. In the first statement, children have access to kid-friendly operations on weekday evenings or weekends in the afternoons and evenings. Here, we have six terms (atomic declarative sentences) which are: (a) , (b) , (c) , (d) , , (e) , (f) . In the second propositional statement, teenagers are only permitted access to dangerous kitchen devices when one of their parents is present in the kitchen. Here, we have three terms, which are: (a) , (b) , (c) . The third statement permits teenagers to use non-dangerous kitchen devices unconditionally. It contains two terms, which are: (a) (b) . According to the fourth statement, teenagers are allowed to access both kid-friendly and non-kid-friendly operations without restriction. It contains three terms, which are: (a) , (b) , (c) . Finally, the fifth statement guarantees parents access to anything at any time and contains one term: (a) .
3.2.2. Use Case B
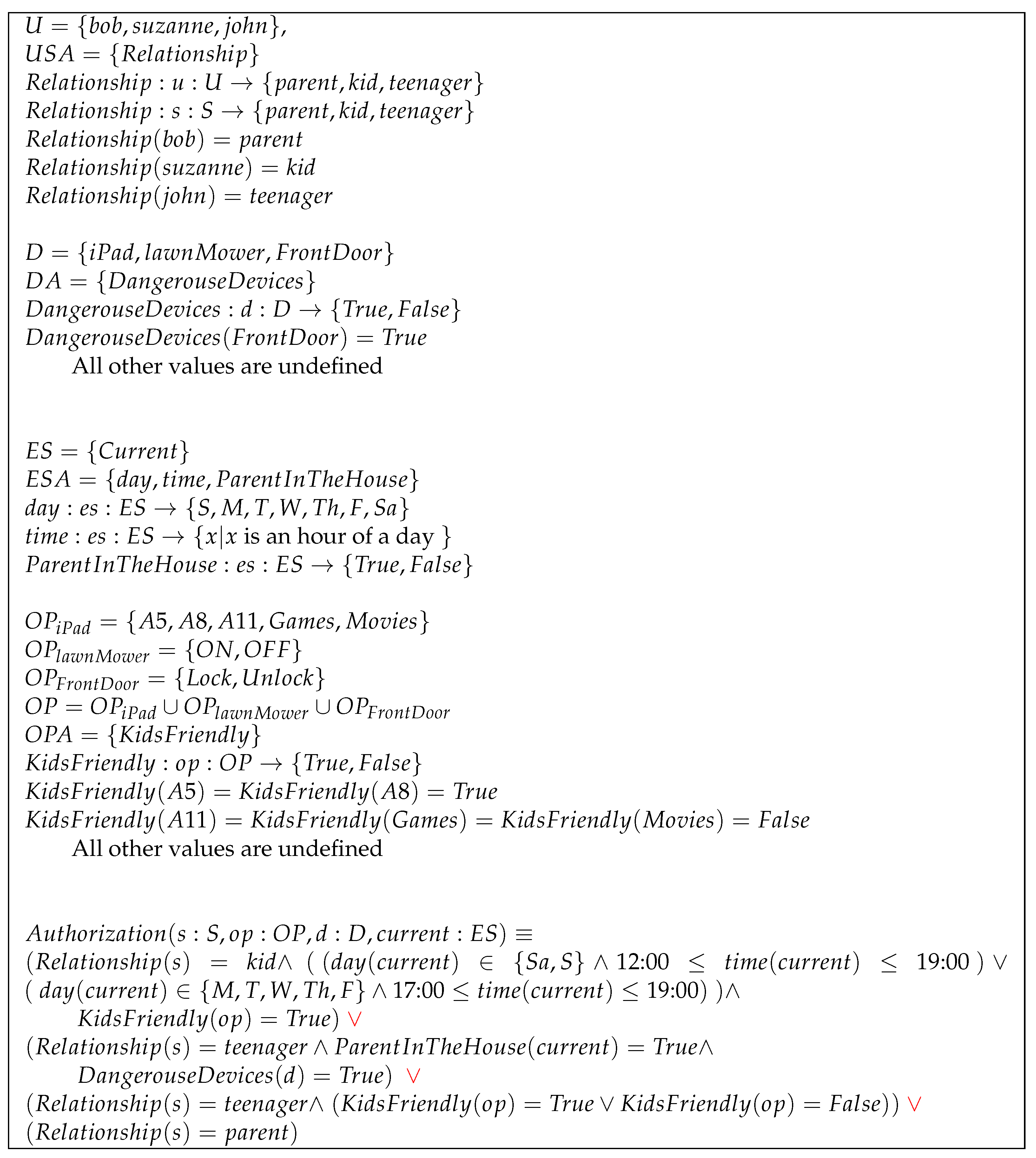
The objectives of this use case are as follows: (a) Kids should be allowed to use kid-friendly operations on the iPad (, and contents (applications for the group aged below five years old and below eight years old, respectively) during a specific time (weekends afternoons and evenings, and weekdays evenings). (b) If a parent is not present in the house, a teenager should not use dangerous devices (FrontDoor). (c) Give teenagers unconditional access to the iPad. (d) Parents should be permitted to use any operation on any device without restrictions.
Figure 5 illustrates how can be configured to achieve these objectives. Here, we have three users, , , and with user attribute respectively assigned to the values , , and . Upon creation of a session s, this session will automatically inherit a subset of attributes from . There are three devices and . is assigned to the following device attributes by the house owner . There are nine operations , , , , , , , , and . These operations are assigned to operation attributes as follows: and , while , , and . Since device attribute functions and operation attribute functions are partial functions, all other operations and devices attributes values are undefined. Any term that references an undefined attribute value is evaluated as false. The environment-state has three attribute functions , and .

Figure 5.
Use Case B configuration.
The authorization function is a disjunction of four propositional statements configured to maintain the four objectives of this use case.
3.3. Proof-of-Concept Implementation
3.3.1. Enforcement Architecture
is an abstract policy model that can be used with different enforcement models. Each enforcement model can use different implementation models which incorporate different underlying technologies.
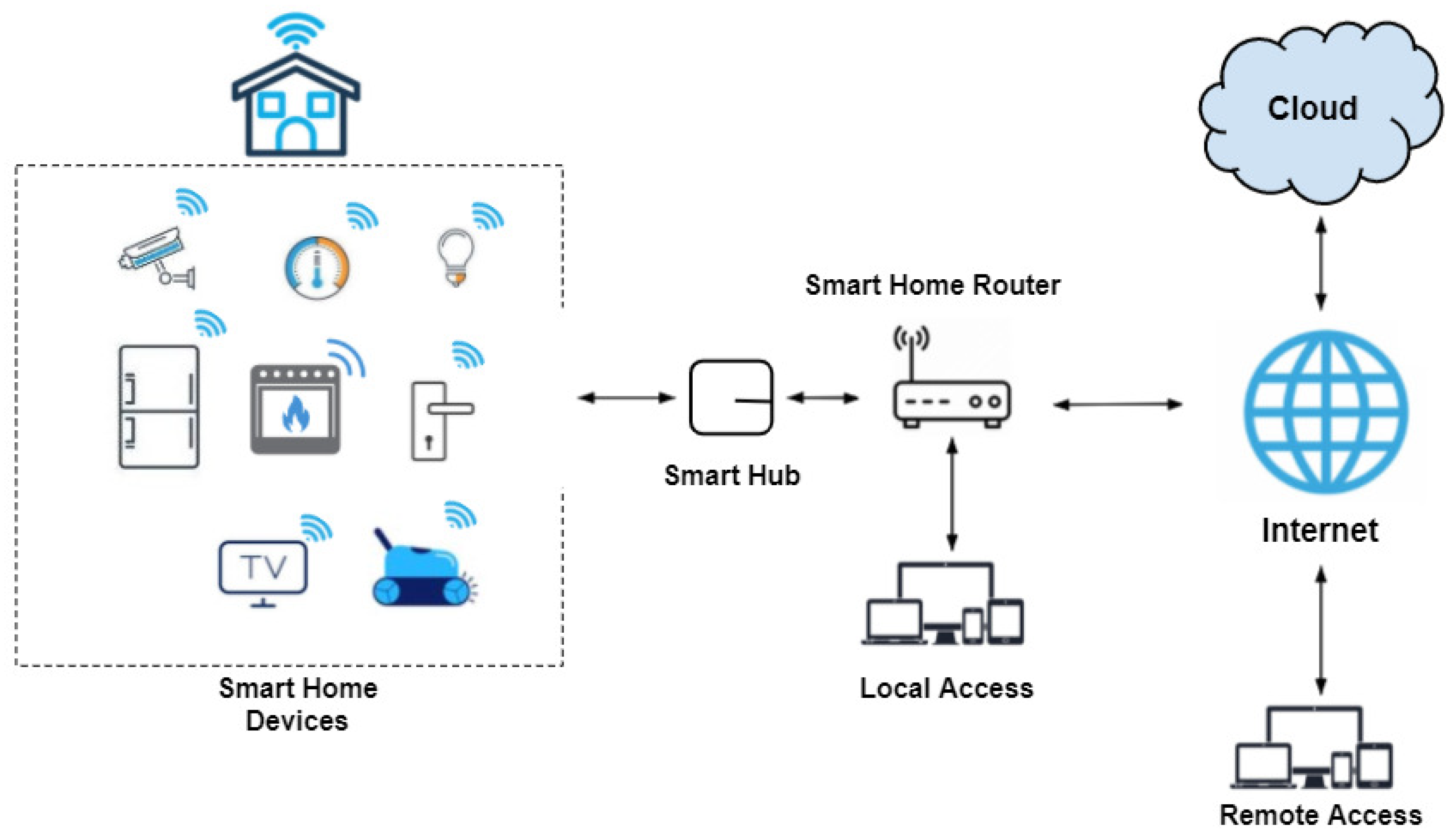
Here, we adopted the smart-home IoT enforcement architecture shown in Figure 6, which was first introduced by Geneiatakis et al. [59]. According to this architecture, IoT devices are directly connected to a corresponding hub. Thus, other devices and users cannot access them directly. Here, there are two types of access. Local access provides users with direct access to the IoT devices through the connectivity services provided by the hub. Remote access allows users to access IoT devices remotely via cloud services. These cloud services then communicate with the smart hub over the Internet.
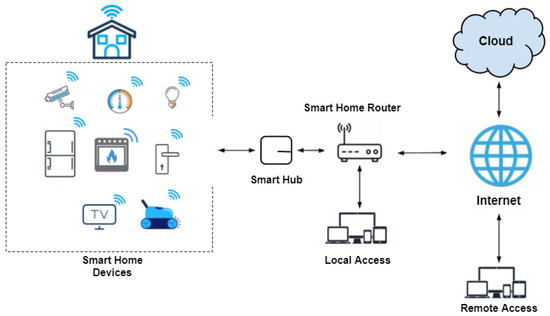
Figure 6.
Enforcement architecture [59].
Moreover, we used the Amazon Web Services (AWS) IoT service [60] as an implementation technology to implement Use Case A presented in Section 3.2. However, in our enforcement, we only handled local access.
First, we created an AWS account, then we configured and deployed Greengrass [61]. Through Greengrass SDK (Software Development Kit), cloud capabilities can be extended to the edge, which is the smart home. Hence, Greengrass acts as a hub and a policy engine within the smart home. Greengrass was installed on a dedicated virtual machine with one virtual CPU, two GB of RAM, and running on Ubuntu server 18.04 LTS. Second, we simulated the five users (the devices which users use to access the smart things, e.g., their phones) and the five devices (the smart things that users want to access) of Use Case A using the AWS IoT device SDK for Python [62] provided by AWS on different virtual machines. Each machine has one virtual CPU and two GB of RAM running Ubuntu server 18.04.5 LTS. Third, we created one virtual object (digital shadow) for each physical device (smart thing devices needing access or a user access device) using the AWS IoT management console. Each physical device is cryptographically linked to its shadow by a digital certificate accompanied by authorization policies. Devices and users communicate with the AWS IoT service using MQTT protocol [63] with TLS security [64]. The MQTT standard is a lightweight machine-to-machine (M2M) publish/subscribe messaging protocol designed explicitly for use by constrained devices. Each shadow has a set of predefined MQTT topics/channels to interact with other IoT devices and applications.
3.3.2. Use Case A Enforcement
To enforce Use Case A, we created four json files as follows, UsersAttributes.json, DevicesAttributes.json, OperationAttributes.json, and EnvironmnetAttributes.json to capture different users/session attributes, devices attributes, operations attributes, and environment attributes, respectively. How to automatically update different attributes values in these files is outside the scope of this work. Moreover, we used the AWS IoT lambda function to receive different user requests, analyze those requests according to the contents of the json files, allow or deny the requested accesses, and then trigger the corresponding devices to carry out the desired action. The code is written in Python 3.7 and runs on a long-lived lambda function with a memory limit of 500 MB and a timeout of 30 s.
3.3.3. Local Communication Handling
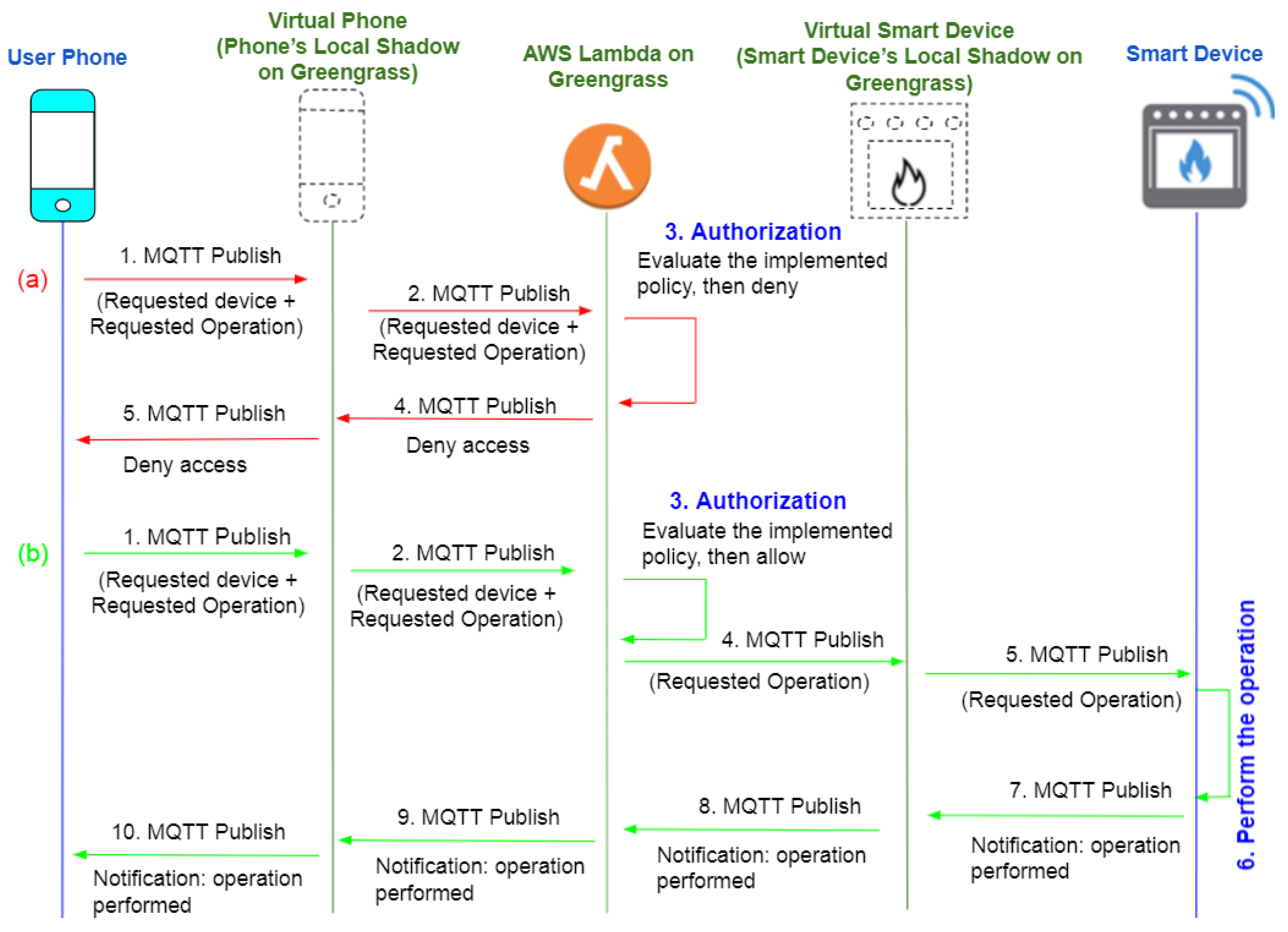
Figure 7 depicts the sequence of actions in our local communication implementation. Sequence (a) illustrated in red demonstrates the sequence of actions when a request is denied. Sequence (b) in green illustrates the sequence of actions when a request is authorized. For instance, if the user wishes to turn on the smart oven using his smartphone from inside the house, first, through the publish/subscribe relationship between the user’s phone and the local shadow, a request is initially sent via MQTT protocol to the virtual object (or local shadow) corresponding to the user phone in Greengrass. Upon receiving the request, the local shadow sends the message to the lambda function using the MQTT publish/subscribe protocol. After that, the lambda function analyzes the request based on UsersAttributes.json, DevicesAttributes.json, OperationAttributes.json, and EnvironmnetAttributes.json files and makes the decision.
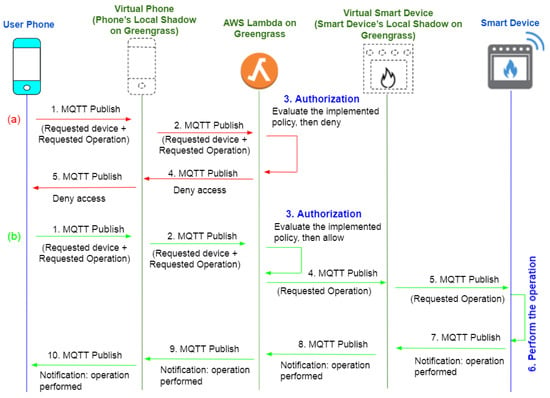
Figure 7.
Local Request handling in our system.
If the request is denied, the lambda function publishes to the user’s shadow update topic. When the local shadow becomes aware of this, it updates the user’s phone. During this scenario, the smart oven does not receive any indication that someone is attempting to access it. In the event that the request is granted, the local shadow of the smart oven will be notified through its update topic, and the smart oven will be updated accordingly. Once the oven is turned on, it publishes a message to the shadow update topic. A notification is sent from the oven’s local shadow to the lambda function, which in turn notifies the user phone’s local shadow. As a final step, the shadow of the user’s phone informs the user’s phone that the smart oven has been turned on successfully.
3.3.4. Performance Results
In this section, we evaluate the performance of our implementation by conducting multiple test cases. We examined three different situations with three different sets of requests. Each set of requests was executed ten times to determine the average lambda processing time.
Table 3 shows the average lambda function execution time measured when one user sends requests to more than one device at once. The first row shows the average lambda execution time when Bob requests to lock the front door lock. The second row shows the average lambda execution time when Bob requests to lock the front door lock, turn on the TV, and turn on the PlayStation simultaneously. Finally, the third row shows the average lambda execution time when Bob requests to lock the front door lock, open the fridge, and turn on the oven, the TV, and the PlayStation. All the requests were approved as they were supposed to according to our configured policies.

Table 3.
One user sending requests to multiple devices.
The values presented in Table 4 represent the measured average execution time of the lambda function when multiple users are sending requests to multiple devices at the same time (one user per device). The first row describes the average execution time when the parent Bob requests to lock the front door lock. The second row shows the execution time when Bob requests to lock the front door lock, the kid Alex requests to turn on the oven, and the teenager Anne requests to open the fridge simultaneously. Additionally, the third row describes the average time when the access requests tested in the second row are repeated, the kid Suzanne requests to turn on the TV, and the teenager John requests to open the oven while one of the parents is in the kitchen. The majority of the requests were approved except for those when Alex attempted to turn on the oven, which is not allowed according to our configuration, and when Suzanne tried to turn on the television, which is not permitted according to our configuration since testing was performed on a Monday morning.

Table 4.
Multiple concurrent instances of one user sending request to one device.
Table 5 displays the average execution time of the lambda function when multiple users simultaneously send requests to one device. The first, second, and third rows show the average time when one user (the parent Bob), three users (the parent and the two kids), and five users (the parent, the two kids, and the two teenagers) respectively all request to lock the front door lock at the same time. All the requests were denied except for when the parent Bob requested to lock the front door lock.

Table 5.
Multiple users sending requests to one device.
4. HABACα vs. EGRBAC in Terms of Theoretical Expressiveness Power
Our goal in this section is to determine if any EGRBAC configuration can be expressed fully in the model, and vice versa, and if not, which model is more expressive and in which terms. The approach used in this section is an extension of the previously published approach in [56].
4.1. From EGRBAC to
Here, we introduce the configuration that translates EGRBAC configuration to be implemented by model.
In this configuration, for differentiation purposes, every EGRBAC component is followed with the suffix . Similarly, every component is followed with the suffix . The configuration of for a given EGRBAC configuration is shown in Table 6.

Table 6.
EGRBAC configuration in .
Essentially, the objective is to be able to translate any EGRBAC configuration towards its equivalent configuration, so that the authorizations in the match those under EGRBAC. The inputs are EGRBAC component sets , , , and . The outputs are , , and the authorization function .
Both systems have the same users, devices, and operations. In , roles are expressed using the user/session attribute . This attribute takes as an input a user or session and returns a set of roles that have been assigned to that user or session.
Constraints related to the static separation of duties are mapped into constraints related to user attributes in . Similarly, constraints related to the dynamic separation of duties are mapped into session attribute constraints in .
Environment roles are mapped into atomic environment-state attributes that have a range of possible values equal to . indicates that the environment state is currently satisfied or the equivalent environment role in EGRBAC should be active. indicates that the environment state is currently not satisfied or the equivalent environment role in EGRBAC should be inactive. It is outside the scope of this model to explain how to trigger different attributes of the environment state in response to changes in the environment.
In EGRBAC, device roles are ways of categorizing permissions. In , we do not have permissions. Hence, we translate device roles in EGRBAC into atomic operation attributes and atomic device attributes with a range of values equal to . If a permission , where is assigned to the device role , where , then and , where , , and and are the operation and device attributes which were created to be equivalent to the device role .
In the final step, we construct the authorization policies. In EGRBAC, the provides specific role pairs and consequently users with access to specific device roles and therefore permissions. Therefore, an authorization function is created for each . Each authorization function is then a disjunct in the final authorization function.
At the end of the translation process, there is a single user/session attribute, which is . The number of user attribute constraints is equal to the number of . The number of subject attribute constraints is equal to the number of . The number of operation attributes and the number of device attributes equals the number of device roles. The number of environment-state attributes is equal to the number of environment roles.
EGRBAC grants access to a specific set of permissions through a series of assignments, as explained in Section 2.1. is the most important assignment, which assigns device roles to role pairs. To put it another way, controlling allows us to decide which role pairs and, therefore, roles are authorized to access specific device roles and, subsequently, permissions. In , however, no such point of vulnerability or "attack point" can be controlled to prevent specific access. Therefore, we are unable to create something equivalent to EGRBAC in . Only by checking individual requests to access permissions and searching for prohibited users will it be possible to ensure that particular prohibited users will not be granted access to particular permissions. EGRBAC offers the advantage of the ability to enforce such constraints at the time of assignment, whereas -like models would need to enforce them at the time of enforcement.
To summarize, the construction of shown in Table 6 is equivalent to the given EGRBAC configuration, including static and dynamic separation of duty constraints. Since the construction is straightforward and one-for-one, the claim of equivalence is intuitively logical. Ref. [65] can be used for a formal argument.
4.2. From to EGRBAC
Throughout this section, we will describe our methodology for generating EGRBAC components and configurations from configuration. This methodology is inspired by the approach proposed in [56], which follows a bottom-up role engineering approach. It applies for policies containing environment attributes and static user/session, operation, and device attribute functions. However, it is incapable of handling policies that compare two different types of attributes. As a result of certain limitations in EGRBAC, it is either impossible to capture policies involving dynamic user/session, operation, and device attribute functions or extremely expensive (resulting in a role explosion).
In the following sections, we describe our approach and demonstrate it step by step. Our demonstration starts from Use Case B introduced in Figure 5 and applies our methodology to construct its equivalent EGRBAC configuration.
4.2.1. From Authorization Function to Authorization Array
Here, as a preliminary step, we first transform the authorization function into a disjunctive normal form (DNF). In Figure 8, we display the authorization function of Use Case B, which is presented in Figure 5 after transforming it into a DNF format by following the standard approach.
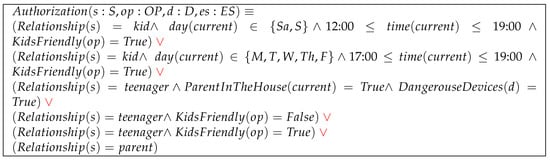
Figure 8.
The authorization function of Use Case B in DNF format.
We call each conjuncted term a condition. We have the session, environment, device, operation, and mix conditions, which receptively involve user/session, environment, device, operation, and more than one type of attribute. In Figure 8 we have six conjunctive clauses. There is one conjunctive clause per access authorization rule.
To build the authorization array we examine every , , and combination against each conjunctive clause, whenever a combination satisfies every term (condition) in a conjunctive clause except those conditions that involve environment-state attributes, where we create a row , , , , for that combination in the authorization array. C denotes the set of session and environment-related conditions in the evaluated conjunctive clause. When evaluating a combination against a conjunctive clause, unsatisfying a device condition means that either the condition is not true for the evaluated device , or the condition references an undefined attribute value for the evaluated device . Similarly, unsatisfying an operation condition means either the condition is not true for the evaluated operation , or the condition references an undefined attribute value for the evaluated operation . Finally, unsatisfying a user condition means that the condition is not true for the evaluated user .
Authorizations array (AA): an authorization of row , , , , denotes that the user is allowed to perform an operation on a device during the environment state whenever the set of environment and session conditions in C are satisfied. Table 7 provides the AA for Use Case B. Different colors represent authorization fields for different users.

Table 7.
AA for Use Case B (Different colors represent authorization fields for different users).
4.2.2. Approach
The goal is to construct EGRBAC elements, assignments, and derived relationships from policies so that the authorizations are the same as those under . In this construction, for differentiation purposes, every EGRBAC component is followed with the suffix . Similarly, every component is followed with the suffix .
The inputs are components , , , , , , and the authorization array . The outputs are EGRBAC components , and . The steps are following:
Step 1: Initialization. Both systems have the same set of users, devices, and operations, hence and . For every operation , and device pair, where is assigned to by the device manufacturers, create a permission.
Step 2: Create the set of device roles . (a) Create a device role for each operation attribute instance or device attribute instance. here are represented as a condition of the form , or . Where x is an instance of the attribute value. (b) Create one device role called remaining permissions for all the permissions , where is not assigned to any device attributes, and is not assigned to any operation attribute. This device role captures the cases where some users have access to specific permissions directly without involving the device’s or operation’s attributes.
Step 3: Build the permission device role assignment array . It is a many-to-many mapping of set and set (constructed in Step 2). To construct we first make a column for each , and make a row for each permission . Then, we fill the array , where in two cases, first if for the permission (corresponding to the row i) or satisfies the condition corresponding to the device role of the column j . Second, if is not assigned to any operation attribute, and is not assigned to any device attribute, and the device role corresponding to this column is . otherwise. For every , add the pair to the set of EGRBAC. See Table 8 for the array of Use Case B.

Table 8.
PDRA array for Use Case B.
Step 4: Build the user device role authorization array from the authorization array , and . , a many-to-many mapping between and . To construct , we first make a row for each user, and a column for each device role. Then, for every we check the for every and combination, where . is the user corresponding to the row i, while is the device role corresponding to the column j in . Here, we have three cases: (a) if user can access all the permissions assigned to the device role without any condition. (b) , where Y is a set of conditions sets. Each conditions set is a set of session, and environment conditions that need to be satisfied together for a to access all the permissions assigned to . Please note that these sets of conditions must be the same for each permission assigned to . (c) Finally, if user is not allowed to access all the permissions assigned to the device role , or is allowed to access different permissions in but under different set of conditions. Table 9 shows for Use Case B.

Table 9.
UDRAA for Use Case B.
Step 5: Follow the EGRBAC users and environment roles constructing algorithm presented in Section 4.2.3 to construct the rest of the EGRBAC components , , , assignments , and derived relations . The set of user roles constructed here is the set of candidate user roles.
Step 6: Combine similar user roles. To achieve this, we run the role combining algorithm described in Section 4.2.4.
4.2.3. EGRBAC Users and Environment Roles Constructing Algorithm
The goal is to construct EGRBAC elements , , , assignments , and derived relations from . See Algorithm 1 for the full algorithm. The input is . The outputs are , , , , , and . The steps are shown as follows:
| Algorithm 1 EGRBAC Users and Environment Roles Construction |
| Require: Require:: return the device role corresponding to the column j in . Require:: return the user corresponding to the row i in . Require:: Return True if c is an environment-state condition. Require: Convert x into a string format.
|
Step 1: Initialize the following EGRBAC sets , and the following constants Number of device roles, Number of users.
Step 2: Loop through the columns of , Table 9 for Use Case B. Each column corresponds to user access rights to a specific device role. Inside each column, loop through the fields of different rows. Here we have two cases:
A. , according to the way was constructed, this means the user corresponding to this row can access the device role of this column unconditionally. In this case, the algorithm does the following:
- Create an environment role and add it to the set . Create an environment condition and add it to the set . Add to the set , this implies that the environment role will always be active. Create a set of environment roles and add to it .
- Create a role which corresponds to accessing this column device role anytime and unconditionally. Add this role to the set .
- Define a role pair , where and . Add to the set .
- Assign the role pair to the device role corresponding to this column by adding the pair to the set .
- Assign the role to the user corresponding to this row by adding the pair to the set .
B. , which means that the user can access the device role under specific a set of user and environment conditions defined by . Here, is a set of sets of conditions, where each set of conditions defines a group of session, and environment conditions that need to be satisfied together for the user to be able to access the device role . Loop through each set of conditions ; for each X perform the following steps:
- Loop through each condition . If y is an environment-state attribute condition, the algorithm creates a corresponding environment condition and adds it to the set , environment role and adds it to the set . Adds to the set . Moreover, the algorithm adds to the set of environment roles .
- After looping through each condition in X, if the set is empty, this means this set of conditions does not contain an environment-state condition. In other words, the user of this row can access the device role of this column without any environment condition. In this case the algorithm creates an environment role and add it to the set , an environment condition and add it to the set . Add to the set , this implies that the environment role will always be active. Add to it .
- The algorithm creates a corresponding user role which represents accessing this column device role when the set of conditions that form X is satisfied. Add this role to the set .
- Define a role pair , where and . Add to the set .
- Assign the role pair to the device role corresponding to this column by adding the pair to the set .
- Finally, assign the role to the user corresponding to this row by adding the pair to the set .
4.2.4. Users Roles Combining Algorithm
This algorithm is designed to combine roles with similar user assignments. When two roles are assigned to the same set of users, the algorithm performs the following:
- For every role pair , in which the role part of it is equal to , change the role part of it to ().
- Remove from the set of roles .
- For every , remove the pair from the set .
- For every , remove from the set, and instead add the pair to the set . For the detailed algorithm, please refer to Algorithm 2.
Upon implementing the first five steps outlined in Section 4.2.2, we will end up with a set of nine roles, as shown in Figure 9. Different roles will be assigned to different users as follows:
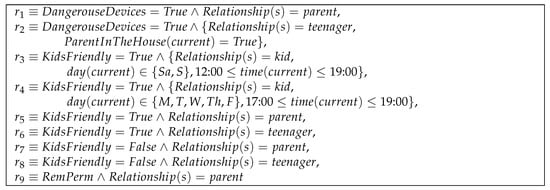
Figure 9.
Initial Set of Roles Before Running the Role Merging Algorithm.
As a result of the user role-combining algorithm, the constructed nine roles will be merged into three roles. Moreover, the user role assignment set will be composed of three pairs, as follows:
| Algorithm 2 Users Roles Combining Algorithm |
| Require:: : The set of roles Require:: Returns the set of users assigned to the role r. Require:: Returns the set of role pairs associated with the role r.
|
4.2.5. The output of EGRBAC Constructing Approach on Use Case B
The output of EGRBAC role constructing algorithm for Use Case B is shown in Table 10.

Table 10.
The output of EGRBAC constructing approach on Use Case B.
The maximum number of created device roles is . Since we create an environment role and an environment condition for each logical environment condition, the maximum number of environment roles and conditions is . Finally, the maximum number of user roles is .
5. Comprehensive Theoretical Comparison
In this section, we compare and analyze and EGRBAC against access control criteria adapted from [9]. These criteria are classified into two types: (a) Basic and main criteria. (b) Quality criteria.
5.1. Basic and Main Criteria
Six elements are included in this type of criteria. Each element will be discussed below. Table 11 summarizes this type of criteria comparison.

Table 11.
Evaluating and against basic and main criteria.
5.1.1. Constraints
These are invariants that must be maintained. EGRBAC supports three constraints: static separation of duty, dynamic separation of duty, and permission–role constraints. , however, cannot support permission–role constraints, as we will discuss in Section 6.
5.1.2. Attributed-Based Specifications
As explained in Section 3.1, we have two types of attributes, static and dynamic. Both models can support environment attributes. Furthermore, they both support static users, devices, and operations attributes. Dynamic users, devices, and operations attributes, however, are not supported by .
5.1.3. Least Privilege Principle
Under this principle, a subject of a system should only be permitted to have access to the least privileges required for performing the user duties. Both models adhere to this principle. They both include the component session, and a user belonging to several roles (in ), or has different attributes corresponding to his roles in the house (in ) can invoke any subset of them that enables tasks to be accomplished in a session. Accordingly, a powerful user can keep some roles or attributes deactivated and activate them when necessary.
5.1.4. Authentication
Both models support positive (closed) authentication. They allow access only when there is an affirmative authorization for it and deny it in other circumstances.
5.1.5. Access Administration
Our comparison here is based on two administrative tasks, user provisioning and policy provisioning. Provisioning users is easier in RBAC-based models (including ) than in ABAC-based models (including ). In RBAC models, user provisioning requires the administrator (the homeowner) to assign roles. Alternatively, in ABAC-based models, the administrator must configure different attribute values for newly provisioned users and devices. On the contrary, in ABAC-based model, policy provisioning only requires the addition of those policies to the authorization function. By contrast, in the RBAC-based model, this requires configuring a series of assignments as in .
5.1.6. Access Review
In RBAC-based models (such as ), to calculate the maximum permission available for a user, it is sufficient to look into his roles, while this could be more complicated in ABAC-based models (such as ) [66].
5.1.7. Administrative Policies
To determine how administrative privileges are organized in any model, an access control administration model is required. In both models, it is assumed that the homeowner is responsible for granting or revoking permissions. Accordingly, we can conclude that they both support centralized administrative policies.
5.2. Quality Criteria
Here we have three essential criteria, as explained in the following.
5.2.1. Expressiveness and Meaningfulness
We believe that for an AC model to be expressive, it must maintain at least the following three characteristics. First, it must be formally defined to have a precise and rigorous specification of the intended behavior. Second, it must be sufficiently meaningful and expressive to support different types of constraints. Finally, The model should capture different types of static and dynamic attributes. Both models are formally defined. Moreover, they both maintain different constraints except for the permission–role constraints, which are not supported by . Finally, as explained in the Attributed-based specifications criterion in Section 5.1, they both capture environment attributes and different types of static attributes. , however, does not capture the user’s and device’s dynamic attributes.
5.2.2. Flexibility
Several factors need to be evaluated to determine whether an AC model is flexible. Here, we identify three of them. First, the model must be flexible enough to meet the requirements of smart-home IoT. Furthermore, the model should support delegation, which is the ability for a subject to delegate some or all his privileges to another user. Additionally, the model should provide flexibility for adding new users or policies.
According to the criteria proposed in [8] for an access control model to fulfill smart-home IoT requirements, it should be dynamic, fine-grained, and suitable for constrained smart-home devices. Moreover, The model should be constructed specifically for smart-home IoT or interpreted for the smart-home domain, using appropriate use cases. The model should be demonstrated in a proof-of-concept to be credible using commercially available technology. Finally, the model should have a formal definition so that the intended behavior is precise and rigorous. As discussed in [8], meets these criteria. However, as we discussed earlier, EGRBAC is not dynamic enough to capture dynamic attributes. On the other hand, the is dynamic, fine-grained, suitable for the constrained home environment, designed specifically for smart-home IoT, illustrated with two use-case demonstrations, has proof-of-concept implementation, and is formally defined. Hence, it meets the criteria proposed in [8].
As for delegation support, it is not feasible to determine this without an administration model for access control. In general, though, it has been demonstrated that RBAC-based and ABAC-based models are capable of delegation.
Both models are capable of provisioning new users and policies. Although new users are more easily provisioned in RBAC-based models (including ) than in ABAC-based models (including ), it is more challenging to provision new policies in RBAC-based models than in ABAC-based models.
5.2.3. Efficiency Level and Scalability
The access control model should address two main factors regarding efficiency and scalability. The model’s validity in the real world will be questionable if it cannot be expanded easily. In addition, the development of the model should not adversely affect its efficiency. To analyze these factors accurately, a more detailed study needs to be performed. Generally, however, smart-home IoT involves a relatively small number of users and devices. Furthermore, organizations of different sizes have widely adopted ABAC-based models and RBAC-based models, proving their scalability.
6. Discussion
In this paper, we present . An attribute-based access control model for smart-home IoT that governs user-to-device authorization. User authentication is outside the scope of this model. The model captures the characteristics of different users, environments, operations, and devices. Furthermore, can give user access to some operations within a single device without giving them access to the entire device. Therefore, it is a fine-grained model.
We illustrated our model with two use-case scenarios and demonstrated its applicability with a proof-of-concept implementation on the Amazon Web Services (AWS) platform. Overall, our model is functional and can be easily applied. We can notice that the captured average lambda processing times are generally low. We understand that practical smart homes will have different and more complicated scenarios. A detailed performance evaluation is ultimately required by simulating a large set of smart things; however, our proof-of-concept implementation in AWS is meant to demonstrate the practical applicability and effectiveness of fine-grained security policies in the context of smart homes. Incorporating many scenarios from the real world will not result in a change in security policy evaluation. Nevertheless, we are considering the possibility of a more detailed performance analysis as an extension of this study. The expressiveness of the model is discussed in Section 5.1. However, to deploy this model for commercial use, a more general sophisticated expressiveness study should be conducted.
Furthermore, we carefully investigated against . Both models are specifically designed to meet smart-home challenges. Towards this goal, we first compared the theoretical expressiveness power of these models in Section 5.2. Then, we evaluated both models against access control models criteria adapted from [9].
In comparing the theoretical expressiveness power of and , we introduced approaches for translating configuration into an equivalent setting so that the authorization rights are the same in both systems and vice versa. These approaches are adapted from [56]. Nevertheless, as discussed in Section 4.1, in , it is not possible to create something similar to EGRBAC . Therefore, it is difficult to prevent future authorization of specific users to access particular devices or operations as this can only be done dynamically when the user is attempting to access the prohibited operation, as opposed to in EGRBAC, which permits this prevention to be implemented upon assignment. It can be challenging to determine the role structure in EGRBAC, but once it has been determined, it is straightforward to determine which users have what permissions and which users do not have future access to such privileges.
The EGRBAC construction approach is capable of handling policies containing environment attributes in addition to users/sessions, devices, and operations static attributes. However, due to certain limitations in EGRBAC, our approach cannot handle policies that deal with users, sessions, or devices with dynamic attributes. According to Section 3.1, dynamic attributes are those attributes that are rapidly changing. For instance, device temperature. According to our approach, attribute instances of the devices and permissions are translated into device roles. A device role in EGRBAC is a way to categorize permissions of different devices based on relatively static characteristics. Whenever permission is assigned to a specific device role, it remains associated with that role until an administration change is made. It is impossible to activate and deactivate device roles dynamically or activate and deactivate permissions assignments to different device roles. For instance, in we can create a device attribute . We can easily configure an access policy that authorizes some users to access a device only if . To do so in EGRBAC, we have two options. The first is to create two device roles, one for high temperature and another for low temperature for each device. For many devices and dynamic attributes, this option may lead to a role explosion. The second option is for those devices which have similar access conditions. We create a device role for low-temperature devices and a device role for high-temperature devices. However, there is no way to dynamically activate or deactivate devices membership in different device roles according to their temperatures. Furthermore, no mechanism in EGRBAC can dynamically activate ’s high-temperature device role while deactivating the low-temperature device role when the temperature of is high and vice versa. A similar argument holds when we deal with dynamic user/session attributes.
In the process of constructing the EGRBAC, we did not take into account the following: (1) Policies that compare two types of attributes. (2) configurations that involve user attribute constraints and session attribute constraints. However, this may be a potential future development.
In Section 5 we conducted a comprehensive theoretical comparison between and EGRBAC. We analyzed each model against the access control model criteria adapted from [9].
Based on the above analysis, a hybrid model that incorporates and EGRBAC features is likely to be the most suitable for smart-home IoT, and probably more generally. Future directions could involve the development of a combined model that will prevent a “role explosion” while providing access authorizations that cover different users, environment, operations, or devices characteristics while maintaining the advantages of EGRBAC, such as ease of access review.
7. Conclusions
In this paper, we defined the access control model for smart homes. The model captures different user, environment, operation, and device characteristics based on a dynamic, fine-grained ABAC approach. Additionally, we presented two use-case scenarios for our model and demonstrated its applicability through a proof-of-concept implementation in Amazon Web Services. Furthermore, we provided a performance test to demonstrate how our system responds in different scenarios. Based on the evaluation, we can conclude that our model is applicable and functional.
Moreover, we assessed the theoretical expressiveness power of our model in comparison to EGRBAC [8], a dynamic contextually aware RBAC-based access control model. We accomplished this by providing approaches for the conversion of specifications into EGRBAC and vice versa. According to our findings, EGRBAC can handle relatively static attributes of devices and users as well as those of the environment but is incapable of handling relatively dynamic attributes of users and devices. However, unlike EGRBAC, it is difficult for to prevent future authorizations of specific users from accessing specific operations on particular devices.
Finally, we conducted a comprehensive theoretical comparison between EGRBAC and against previously published criteria for access control models. We concluded that a hybrid model incorporating and EGRBAC features would be most appropriate for use in IoT-enabled smart homes, as well as more broadly.
Author Contributions
Conceptualization, S.A. and R.S.; methodology, S.A. and R.S.; software, S.A. and J.B.; validation, S.A. and R.S.; formal analysis, S.A. and R.S.; investigation, S.A. and R.S.; resources, S.A., R.S. and J.B.; data curation, S.A.; writing—original draft preparation, S.A.; writing—review and editing, S.A.; visualization, S.A.; supervision, R.S.; project administration, S.A.; funding acquisition, S.A. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by NSF CREST Grant HRD1736209 and NSF CREST-PRF Award 2112590.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
This work is partially supported by NSF CREST Grant HRD1736209 and NSF CREST-PRF Award 2112590.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study; in the collection, analyses, or interpretation of data; in the writing of the manuscript, or in the decision to publish the results.
References
- Internet of Things. Available online: https://en.wikipedia.org/wiki/Internet_of_things (accessed on 18 January 2022).
- He, W.; Golla, M.; Padhi, R.; Ofek, J.; Dürmuth, M.; Fernandes, E.; Ur, B. Rethinking access control and authentication for the home internet of things (IoT). In Proceedings of the 27th USENIX Security Symposium (USENIX Security 18), Baltimore, MD, USA, 15–17 August 2018. [Google Scholar]
- Tilley, A. How a Few Words to Apple’s Siri Unlocked a Man’s Front Door. 2016. Available online: https://www.forbes.com/sites/aarontilley/2016/09/21/apple-homekit-siri-security/?sh=4f5270c862e5y (accessed on 18 January 2022).
- Hill, K. Baby Monitor Hack Could Happen To 40,000 Other Foscam Users. 2013. Available online: https://www.forbes.com/sites/kashmirhill/2013/08/27/baby-monitor-hack-could-happen-to-40000-other-foscam-users/?sh=51b3cb2f58b5 (accessed on 18 January 2022).
- Jia, J.; Qiu, X.; Cheng, C. Access control method for web of things based on role and sns. In Proceedings of the 2012 IEEE 12th International Conference on Computer and Information Technology, Chengdu, China, 27–29 October 2012. [Google Scholar]
- Kaiwen, S.; Lihua, Y. Attribute-role-based hybrid access control in the internet of things. In Asia-Pacific Web Conference; Springer: Changsha, China, 2014. [Google Scholar]
- Alramadhan, M.; Sha, K. An overview of access control mechanisms for internet of things. In Proceedings of the 2017 26th International Conference on Computer Communication and Networks (ICCCN), Vancouver, BC, Canada, 31 July–3 August 2017. [Google Scholar]
- Ameer, S.; Benson, J.; Sandhu, R. The EGRBAC Model for Smart Home IoT. In Proceedings of the 2020 IEEE 21st International Conference on Information Reuse and Integration for Data Science (IRI), Las Vegas, NV, USA, 11–13 August 2020. [Google Scholar]
- Hasani, S.M.; Modiri, N. Criteria specifications for the comparison and evaluation of access control models. Int. J. Comput. Netw. Inf. Secur. 2013, 5, 19. [Google Scholar] [CrossRef][Green Version]
- Arias, O.; Wurm, J.; Hoang, K.; Jin, Y. Privacy and security in internet of things and wearable devices. IEEE Trans. Multi-Scale Comput. Syst. 2015, 1, 99–109. [Google Scholar] [CrossRef]
- Ur, B.; Jung, J.; Schechter, S. The current state of access control for smart devices in homes. In Proceedings of the Workshop on Home Usable Privacy and Security (HUPS), Newcastle, UK, 24 July 2013. [Google Scholar]
- Granjal, J.; Monteiro, E.; Silva, J.S. Security for the internet of things: A survey of existing protocols and open research issues. IEEE Comm. Surv. Tutor. 2015, 17, 1294–1312. [Google Scholar] [CrossRef]
- Denning, T.; Kohno, T.; Levy, H.M. Computer security and the modern home. Commun. ACM 2013, 56, 94–103. [Google Scholar] [CrossRef]
- Cui, A.; Stolfo, S.J. A quantitative analysis of the insecurity of embedded network devices: Results of a wide-area scan. In Proceedings of the 26th Annual Computer Security Applications Conference, Austin, TX, USA, 6–10 December 2010. [Google Scholar]
- Oluwafemi, T.; Kohno, T.; Gupta, S.; Patel, S. Experimental security analyses of non-networked compact fluorescent lamps: A case study of home automation security. In Proceedings of the Learning from Authoritative Security Experiment Results (LASER) 2013, Arlington, VA, USA, 16–17 October 2013. [Google Scholar]
- Fernandes, E.; Jung, J.; Prakash, A. Security analysis of emerging smart home applications. In Proceedings of the 2016 IEEE Symposium on Security and Privacy (SP), San Jose, CA, USA, 22–26 May 2016. [Google Scholar]
- Ho, G.; Leung, D.; Mishra, P.; Hosseini, A.; Song, D.; Wagner, D. Smart locks: Lessons for securing commodity internet of things devices. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security, Xi’an, China, 30 May–3 June 2016. [Google Scholar]
- Fernandes, E.; Paupore, J.; Rahmati, A.; Simionato, D.; Conti, M.; Prakash, A. Flowfence: Practical data protection for emerging IoT application frameworks. In Proceedings of the 25th USENIX Security Symposium (USENIX Security 16), Austin, TX, USA, 10–12 August 2016. [Google Scholar]
- Morgner, P.; Mattejat, S.; Benenson, Z. All your bulbs are belong to us: Investigating the current state of security in connected lighting systems. arXiv 2016, arXiv:1608.03732. [Google Scholar]
- Gupta, M.; Sandhu, R. Authorization framework for secure cloud assisted connected cars and vehicular internet of things. In Proceedings of the 23nd ACM on Symposium on Access Control Models and Technologies, Indianapolis, IN, USA, 13–15 June 2018. [Google Scholar]
- Ouaddah, A.; Mousannif, H.; Elkalam, A.A.; Ouahman, A.A. Access control in the Internet of Things: Big challenges and new opportunities. Comput. Netw. 2017, 112, 237–262. [Google Scholar] [CrossRef]
- Ferraiolo, D.F.; Sandhu, R.; Gavrila, S.; Kuhn, D.R.; Chandramouli, R. Proposed NIST standard for role-based access control. ACM Trans. Inf. Syst. Secur. (TISSEC) 2001, 4, 224–274. [Google Scholar] [CrossRef]
- Sandhu, R.S. Role-based access control. In Advances in Computers; Elsevier: Amsterdam, The Netherlands, 1998; Volume 46, pp. 237–286. [Google Scholar]
- Covington, M.J.; Moyer, M.J.; Ahamad, M. Generalized Role-Based Access Control for Securing Future Applicationsl Technical Report; Georgia Tech: Atlanta, GA, USA, 2000. [Google Scholar]
- Zhang, G.; Tian, J. An extended role based access control model for the Internet of Things. In Proceedings of the 2010 International Conference on Information, Networking and Automation (ICINA), Kunming, China, 18–19 October 2010. [Google Scholar]
- Barka, E.; Mathew, S.S.; Atif, Y. Securing the web of things with role-based access control. In International Conference on Codes, Cryptology, and Information Security; Springer: Rabat, Morocco, 2015. [Google Scholar]
- Bandara, S.; Yashiro, T.; Koshizuka, N.; Sakamura, K. Access control framework for api-enabled devices in smart buildings. In Proceedings of the 2016 22nd Asia-Pacific Conference on Communications (APCC), Yogyakarta, Indonesia, 25–27 August 2016. [Google Scholar]
- Liu, J.; Xiao, Y.; Chen, C. Authentication and access control in the internet of things. In Proceedings of the 2012 32nd International Conference on Distributed Computing Systems Workshops, Macau, China, 18–21 June 2012. [Google Scholar]
- Bhatt, S.; Patwa, F.; Sandhu, R. Access control model for AWS internet of things. In Proceedings of the International Conference on Network and System Security, Helsinki, Finland, 21–23 August 2017. [Google Scholar]
- Hu, V.C.; Kuhn, D.R.; Ferraiolo, D.F.; Voas, J. Attribute-based access control. Computer 2015, 48, 85–88. [Google Scholar] [CrossRef]
- Jin, X.; Krishnan, R.; Sandhu, R. A unified attribute-based access control model covering DAC, MAC and RBAC. In Proceedings of the IFIP Annual Conference on Data and Applications Security and Privacy, Paris, France, 11–13 July 2012. [Google Scholar]
- Bezawada, B.; Haefner, K.; Ray, I. Securing Home IoT Environments with Attribute-Based Access Control. In Proceedings of the Third ACM Workshop on Attribute-Based Access Control, Tempe, AZ, USA, 19–21 March 2018. [Google Scholar]
- Mutsvangwa, A.; Nleya, B.; Nleya, B. Secured access control architecture consideration for smart grids. In Proceedings of the 2016 IEEE PES Power Africa, Livingstone, Zambia, 28 June–3 July 2016. [Google Scholar]
- Xie, Y.; Wen, H.; Wu, J.; Jiang, Y.; Meng, J.; Guo, X.; Xu, A.; Guan, Z. Three-layers secure access control for cloud-based smart grids. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference (VTC2015-Fall), Boston, MA, USA, 6–9 September 2015. [Google Scholar]
- Gupta, M.; Benson, J.; Patwa, F.; Sandhu, R. Dynamic groups and attribute-based access control for next-generation smart cars. In Proceedings of the Ninth ACM Conference on Data and Application Security and Privacy, Richardson, TX, USA, 25–27 March 2019. [Google Scholar]
- Bhatt, S.; Sandhu, R. ABAC-CC: Attribute-Based Access Control and Communication Control for Internet of Things. In Proceedings of the 25th ACM Symposium on Access Control Models and Technologies, Barcelona, Spain, 10–12 June 2020. [Google Scholar]
- Ali, G.; Ahmad, N.; Cao, Y.; Asif, M.; Cruickshank, H.; Ali, Q.E. Blockchain based permission delegation and access control in Internet of Things (BACI). Comput. Secur. 2019, 86, 318–334. [Google Scholar] [CrossRef]
- Ouaddah, A.; Elkalam, A.A.; Ouahman, A.A. Towards a novel privacy-preserving access control model based on blockchain technology in IoT. In Europe and MENA Cooperation Advances in Information and Communication Technologies; Springer: Saidia, Marocco, 2017. [Google Scholar]
- Novo, O. Blockchain meets IoT: An architecture for scalable access management in IoT. IEEE IoT J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Dorri, A.; Kanhere, S.S.; Jurdak, R.; Gauravaram, P. Blockchain for IoT security and privacy: The case study of a smart home. In Proceedings of the 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (PerCom Workshops), Kona, HI, USA, 13–17 March 2017. [Google Scholar]
- Ding, S.; Cao, J.; Li, C.; Fan, K.; Li, H. A novel attribute-based access control scheme using blockchain for IoT. IEEE Access 2019, 7, 38431–38441. [Google Scholar] [CrossRef]
- Park, J.; Sandhu, R. Towards usage control models: Beyond traditional access control. In Proceedings of the Seventh ACM Symposium on Access Control Models and Technologies, Monterey, CA, USA, 3–4 June 2002. [Google Scholar]
- Park, J. Usage Control: A Unified Framework for Next Generation Access Control. Ph.D. Thesis, George Mason University, Fairfax, VA, USA, 2003. [Google Scholar]
- Zhang, X.; Parisi-Presicce, F.; Sandhu, R.; Park, J. Formal model and policy specification of usage control. ACM Trans. Inf. Syst. Secur. (TISSEC) 2005, 8, 351–387. [Google Scholar] [CrossRef]
- Guoping, Z.; Wentao, G. The research of access control based on UCON in the internet of things. J. Softw. 2011, 6, 724–731. [Google Scholar]
- La Marra, A.; Martinelli, F.; Mori, P.; Saracino, A. Implementing usage control in internet of things: A smart home use case. In Proceedings of the 2017 IEEE Trustcom/BigDataSE/ICESS, Sydney, NSW, Australia, 1–4 August 2017. [Google Scholar]
- Martinelli, F.; Michailidou, C.; Mori, P.; Saracino, A. Too long, did not enforce: A qualitative hierarchical risk-aware data usage control model for complex policies in distributed environments. In Proceedings of the 4th ACM Workshop on Cyber-Physical System Security, Incheon, Korea, 4 June 2018. [Google Scholar]
- Malani, S.; Srinivas, J.; Das, A.K.; Srinathan, K.; Jo, M. Certificate-based anonymous device access control scheme for IoT environment. IEEE Internet Things J. 2019, 6, 9762–9773. [Google Scholar] [CrossRef]
- Qiu, J.; Tian, Z.; Du, C.; Zuo, Q.; Su, S.; Fang, B. A survey on access control in the age of internet of things. IEEE Internet Things J. 2020, 7, 4682–4696. [Google Scholar] [CrossRef]
- Ravidas, S.; Lekidis, A.; Paci, F.; Zannone, N. Access control in Internet-of-Things: A survey. J. Netw. Comput. Appl. 2019, 144, 79–101. [Google Scholar] [CrossRef]
- Zhang, Y.; Wu, X. Access control in internet of things: A survey. arXiv 2016, arXiv:1610.01065. [Google Scholar] [CrossRef]
- Yan, H.; Wang, Y.; Jia, C.; Li, J.; Xiang, Y.; Pedrycz, W. IoT-FBAC: Function-based access control scheme using identity-based encryption in IoT. Future Gener. Comput. Syst. 2019, 95, 344–353. [Google Scholar] [CrossRef]
- Alshahrani, M.; Traore, I. Secure mutual authentication and automated access control for IoT smart home using cumulative keyed-hash chain. J. Inf. Secur. Appl. 2019, 45, 156–175. [Google Scholar] [CrossRef]
- Sikder, A.K.; Babun, L.; Celik, Z.B.; Acar, A.; Aksu, H.; McDaniel, P.; Kirda, E.; Uluagac, A.S. Multi-user multi-device-aware access control system for smart home. arXiv 2019, arXiv:1911.10186. [Google Scholar]
- Sandhu, R.; Ferraiolo, D.; Kuhn, R. The NIST model for role-based access control: Towards a unified standard. In Proceedings of the ACM Workshop on Role-Based Access Control, Berlin, Germany, 26–28 July 2000. [Google Scholar]
- Ameer, S.; Sandhu, R. The HABAC Model for Smart Home IoT and Comparison to EGRBAC. In Proceedings of the ACM Workshop on Secure and Trustworthy Cyber-Physical Systems (SAT-CPS), Online, 28 April 2021. [Google Scholar]
- Partial Function. Available online: https://en.wikipedia.org/wiki/Partial_function (accessed on 20 January 2022).
- Atomic Sentence. Available online: https://en.wikipedia.org/wiki/Atomic_sentence (accessed on 20 January 2022).
- Geneiatakis, D.; Kounelis, I.; Neisse, R.; Nai-Fovino, I.; Steri, G.; Baldini, G. Security and privacy issues for an IoT based smart home. In Proceedings of the 2017 40th International Convention on Information and Communication Technology, Electronics and Microelectronics (MIPRO), Opatija, Croatia, 22–26 May 2017. [Google Scholar]
- AWS-IoT. Available online: https://aws.amazon.com/iot/ (accessed on 20 January 2022).
- AWS IoT Greengrass. Available online: https://docs.aws.amazon.com/greengrass/latest/developerguide/what-is-gg.html (accessed on 20 January 2022).
- AWS IoT Device SDK for Python. Available online: https://docs.aws.amazon.com/greengrass/latest/developerguide/IoT-SDK.html (accessed on 20 January 2022).
- MQTT.fx—A JavaFX based MQTT Client. Available online: https://softblade.de/en/welcome/ (accessed on 20 January 2022).
- The Transport Layer Security (TLS) Protocol. Available online: https://tools.ietf.org/html/rfc5246 (accessed on 20 January 2022).
- Tripunitara, M.; Li, N. A theory for comparing the expressive power of access control models. J. Comput. Secur. 2007, 15, 231–272. [Google Scholar] [CrossRef]
- Kuhn, D.R.; Coyne, E.J.; Weil, T.R. Adding attributes to role-based access control. Computer 2010, 43, 79–81. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).