A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption
Abstract
1. Introduction
1.1. Motivation and Contribution
- A secure multi-party computation scheme based on NTRU-type [5] multi-key fully homomorphic encryption proxy re-encryption is proposed. The use of proxy re-encryption solves the problem that the multi-key homomorphic encryption scheme cannot be decrypted separately when the result is obtained, and the data owner can go offline after encrypting the uploaded data and does not have to stay online during secure multi-party computation.
- A scheme combining the blockchain with an NTRU multi-key fully homomorphic encryption agent re-encryption secure multi-party computing scheme is proposed. The decentralized, transparent, and non-tamper characteristics of the blockchain are utilized to achieve the traceability and verifiability of the scheme and prevent collusion of the participants.
- The security proof and comparison with other solutions demonstrate that this secure multi-party computing solution meets the requirements of being independent of trusted third parties, verifiable, privacy-protected, collusion-proof, individually decryptable by the querier, and resistant to quantum attacks.
1.2. Paper Structure
2. Related Work
3. SMPC Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption
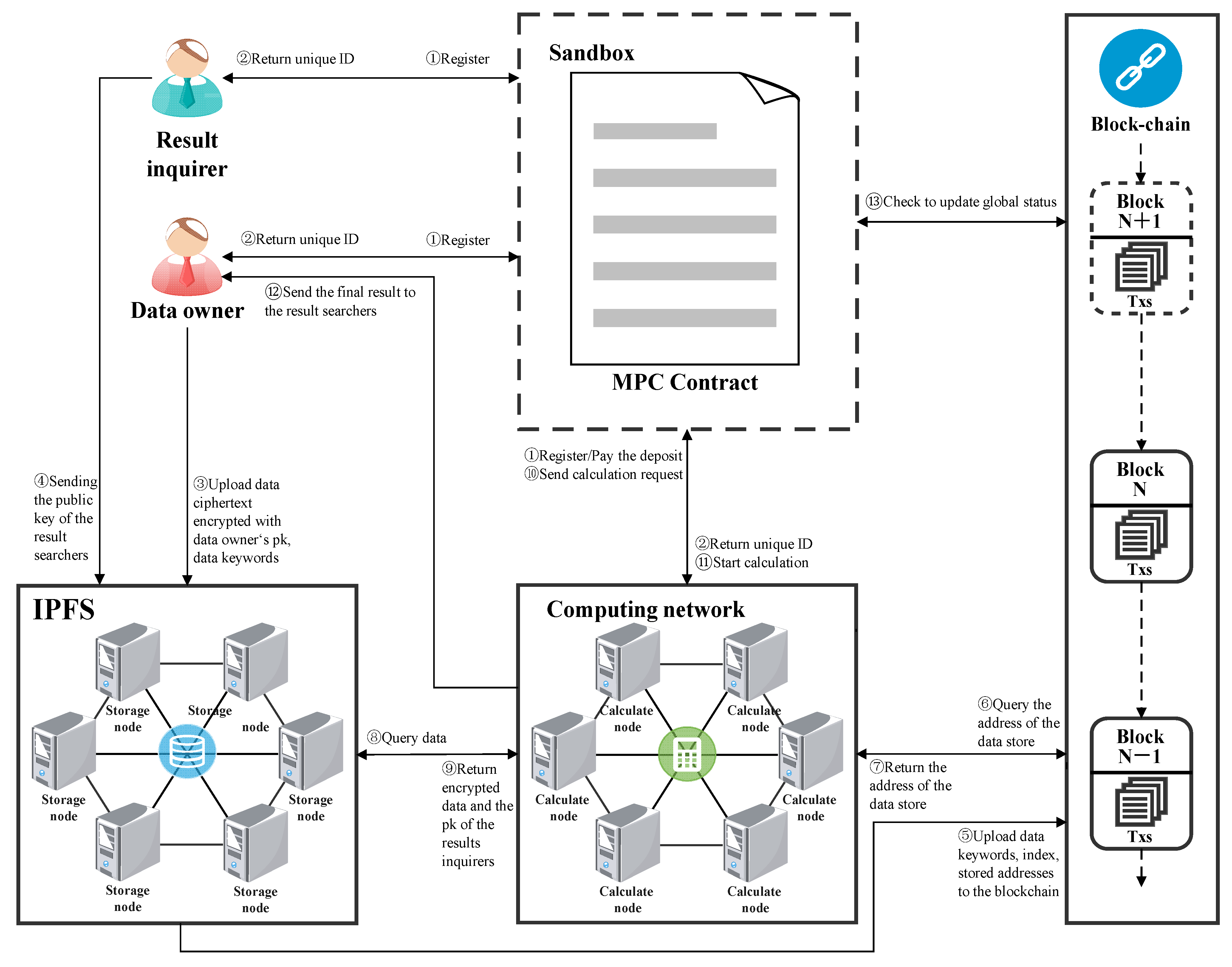
3.1. System Model
- Data owner
- Result inquirer
- Blockchain
- IPFS
- SMPC Contracts
- Computing networks
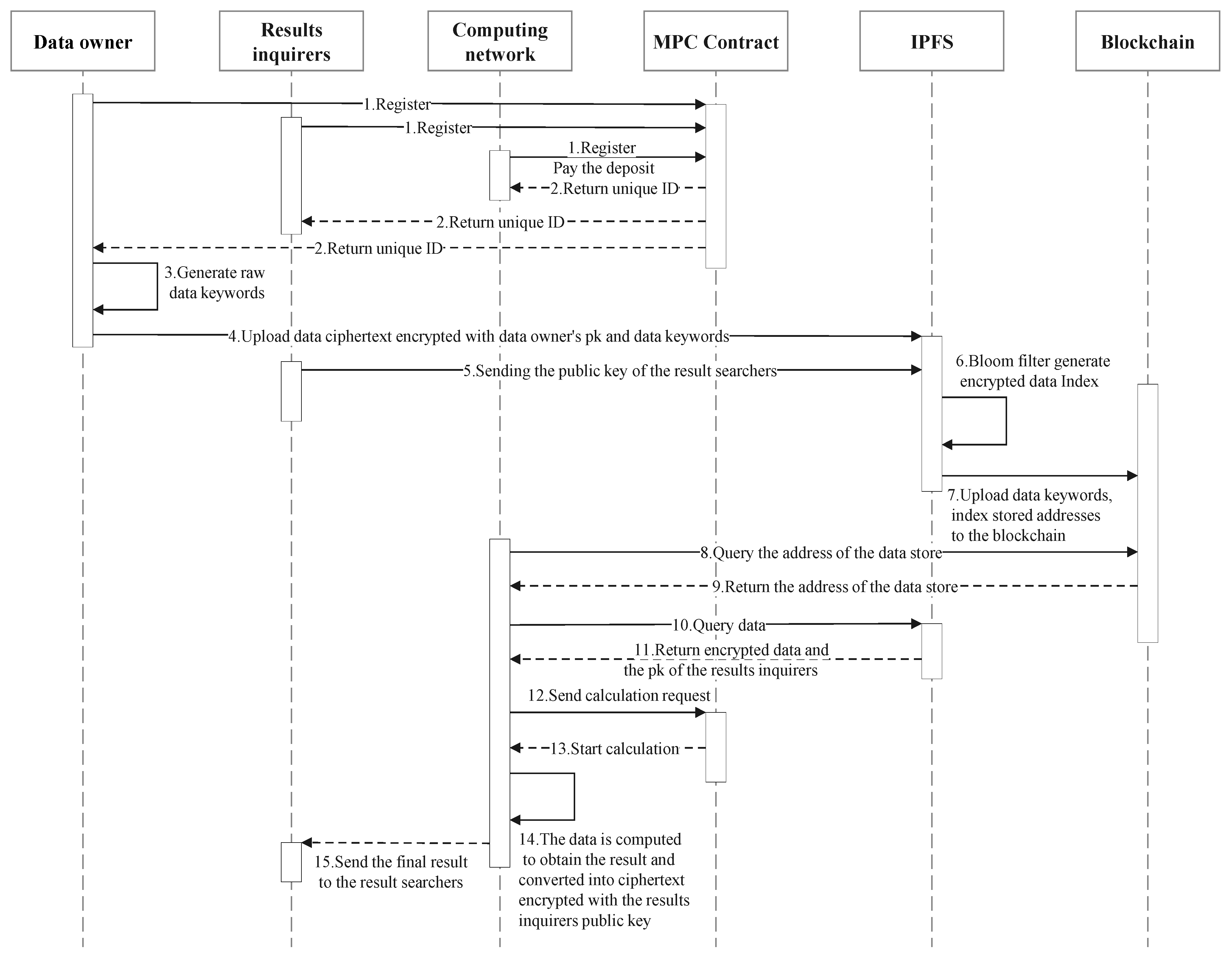
3.2. Program Steps
- Initially, the data owner, the data querier, and the SMPC node register with the SMPC contract, which distributes a unique ID to each registered node, while the SMPC node pays a deposit to the contract.
- The data owner generates keywords for the original data to be involved in the operation and then encrypts the data to be involved in the operation with its own public key and uploads them to IPFS, where a Bloom filter generates the index value of the encrypted data. The data owner uploads the keywords generated from the original data and the storage address of the encrypted data.
- The computing network node interacts with the blockchain by querying keywords, querying the corresponding block to obtain the storage address of the required encrypted information, and obtaining the encrypted data from the IPFS data storage address for calculation.
- The data querier sends its public key to the SMPC contract, and the ciphertext result after the homomorphic calculation is converted into the ciphertext result encrypted by the data querier’s public key through the NTRU proxy re-encryption algorithm. To obtain the final calculation result, the data querier only needs to decrypt the calculation result returned by the computing network with its own private key. The contract is carried out in a sandbox isolation environment, and the blockchain rewards or deducts the deposit based on whether the node is honest or not.
- At the end of the calculation, the blockchain validation node checks whether any dishonest nodes have committed mischief before or after the calculation process. If this does not happen, the deposit of each node will be returned as is; if this happens, the deposit of the honest node will be returned, and the deposit of the dishonest node will be deducted and distributed as a reward to the honest node as a punishment.
3.3. Algorithm Construction
- Initialization algorithm
- Key generation algorithm
- Multi-key homomorphic encryption algorithm
- : Compute and output the ciphertext .
- : Calculate and output the ciphertext .
- Proxy re-encryption algorithm
3.4. Security Model
- Preparation phase
- Inquiry phase
- Challenge phase.
- Judgment phase.
4. Proof of Safety
- Preparation phase
- Inquiry phase.
- Challenge phase.
- Judgment phase.
5. Comparison of Programs
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Yang, Y.; Huang, X.; Liu, X. A Comprehensive Survey on Secure Outsourced Computation and Its Applications. IEEE Access 2019, 7, 159426–159465. [Google Scholar] [CrossRef]
- Akl, S.G.; Assem, I. Fully homomorphic encryption: A general framework and implementations. Int. J. Parallel Emergent Distribted Syst. 2020, 35, 493–498. [Google Scholar] [CrossRef]
- López-Alt, A.; Tromer, E.; Vaikuntanathan, V. Multikey fully homomorphic encryption and applications. SIAM J. Comput. 2017, 46, 1827–1892. [Google Scholar] [CrossRef]
- Yasuda, S.; Koseki, Y.; Hiromasa, R. Multi-key homomorphic proxy re-encryption. In Proceedings of the International Conference on Information Security, Guildford, UK, 9–12 September 2018; Springer: Berlin/Heidelberg, Germany, 2018; pp. 328–346. [Google Scholar] [CrossRef]
- Stehlé, D.; Steinfeld, R. Making NTRU as secure as worst-case problems over ideal lattices. In Proceedings of the Annual International Conference on the Theory and Applications of Cryptographic Techniques, Tallinn, Estonia, 15–19 May 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 27–47. [Google Scholar] [CrossRef]
- Yao, A.C. Protocols for secure computations. In Proceedings of the 23rd Annual Symposium on Foundations of Computer Science, Chicago, IL, USA, 3–5 November 1982; pp. 160–164. [Google Scholar] [CrossRef]
- Micali, S.; Goldreich, O.; Wigderson, A. How to play any mental game. In Proceedings of the Nineteenth ACM Symp. on Theory of Computing, STOC, NY, USA, 25–27 May 1987; ACM: New York, NY, USA, 1987; pp. 218–229. [Google Scholar] [CrossRef]
- Wu, Y.; Wang, X.; Susilo, W. Generic server-aided secure multi-party computation in cloud computing. Comput. Stand. Interfaces 2022, 79, 103552. [Google Scholar] [CrossRef]
- Gao, H.; Ma, Z.; Luo, S.; Wang, Z. BFR-MPC: A Blockchain-Based Fair and Robust Multi-Party Computation Scheme. IEEE Access 2019, 7, 110439–110450. [Google Scholar] [CrossRef]
- Yang, Y.; Wei, L.; Wu, J. Block-smpc: A blockchain-based secure multi-party computation for privacy-protected data sharing. In Proceedings of the 2020 2nd International Conference on Blockchain Technology 2020, Hilo, HI, USA, 12–14 March 2020; pp. 46–51. [Google Scholar] [CrossRef]
- Liu, F.; Yang, J.; Kong, D.; Qi, J. A Secure Multi-party Computation Protocol Combines Pederson Commitment with Schnorr Signature for Blockchain. In Proceedings of the 2020 IEEE 20th International Conference on Communication Technology (ICCT), Nanning, China, 28–31 October 2020; pp. 57–63. [Google Scholar] [CrossRef]
- Liu, F.; Yang, J.; Li, Z.; Qi, J. A secure multi-party computation protocol for universal data privacy protection based on blockchain. J. Computer. Res. Dev. 2021, 58, 281–290. [Google Scholar]
- Che, X.; Zhou, T.; Li, N. Optimization of NTRU multi-key homomorphic encryption scheme. Eng. Sci. Technol. 2020, 52, 186–193. [Google Scholar]
- Che, X.; Zhou, T.; Li, N. Modified multi-key fully homomorphic encryption based on NTRU cryptosystem without key-switching. Tsinghua Sci. Technol. 2020, 25, 564–578. [Google Scholar] [CrossRef]
- Daniel, E.; Tschorsch, F. IPFS and Friends: A Qualitative Comparison of Next Generation Peer-to-Peer Data Networks. IEEE Commun. Surveys. Tutor. 2022, 24, 31–52. [Google Scholar] [CrossRef]
- Hua, W.; Gao, Y.; Lyu, M.; Xie, P. Research on Bloom filter: A survey. J. Comput. Appl. 2022, 42, 1729–1747. [Google Scholar]
- Wan, S.; Li, M.; Liu, G.; Wang, C. Recent advances in consensus protocols for blockchain: A survey. Wirel. Netw. 2020, 26, 5579–5593. [Google Scholar] [CrossRef]
- Xu, G.; Bai, H.; Xing, J. SG-PBFT: A secure and highly efficient distributed blockchain PBFT consensus algorithm for intelligent Internet of vehicles. J. Parallel Distrib. Comput. 2022, 164, 1–11. [Google Scholar] [CrossRef]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On ideal lattices and learning with errors over rings. In Theory and Application of Cryptographic Techniques; Springer: Berlin/Heidelberg, Germany, 2010; Volume 6110, pp. 1–23. [Google Scholar] [CrossRef]
- López-Alt, A.; Tromer, E.; Vaikuntanathan, V. On-the-fly multiparty computation on the cloud via multikey fullyhomomorphic encryption. In Proceedings of the Forty-Fourth Annual ACM Symposium on Theory of Computing, New York, NY, USA, 20–22 May 2012; pp. 1219–1234. [Google Scholar] [CrossRef]
| Literature | Not Relying on Trusted Third Parties | Verifiable | Privacy | Anti-Conspiracy | Individual Decryption Available to Enquirers | Resistant to Quantum Attacks |
|---|---|---|---|---|---|---|
| [8] | × | × | √ | × | × | × |
| [9] | √ | √ | √ | √ | × | × |
| [10] | √ | √ | √ | √ | × | × |
| [11] | √ | √ | √ | - | × | × |
| [12] | √ | √ | √ | - | √ | × |
| This paper | √ | √ | √ | √ | √ | √ |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Y.; Zhou, Y.; Feng, T. A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption. Information 2022, 13, 481. https://doi.org/10.3390/info13100481
Jiang Y, Zhou Y, Feng T. A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption. Information. 2022; 13(10):481. https://doi.org/10.3390/info13100481
Chicago/Turabian StyleJiang, Yongbo, Yuan Zhou, and Tao Feng. 2022. "A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption" Information 13, no. 10: 481. https://doi.org/10.3390/info13100481
APA StyleJiang, Y., Zhou, Y., & Feng, T. (2022). A Blockchain-Based Secure Multi-Party Computation Scheme with Multi-Key Fully Homomorphic Proxy Re-Encryption. Information, 13(10), 481. https://doi.org/10.3390/info13100481






