The Role of Trustworthiness Facets for Developing Social Media Applications: A Structured Literature Review
Abstract
:1. Introduction
2. Theoretical Background
2.1. Trustworthiness Facets
2.2. Placing Trustworthiness Facets in the Context of Trust
2.3. Trust-Building through Software in the Past
3. Literature Review of Trustworthiness Facets
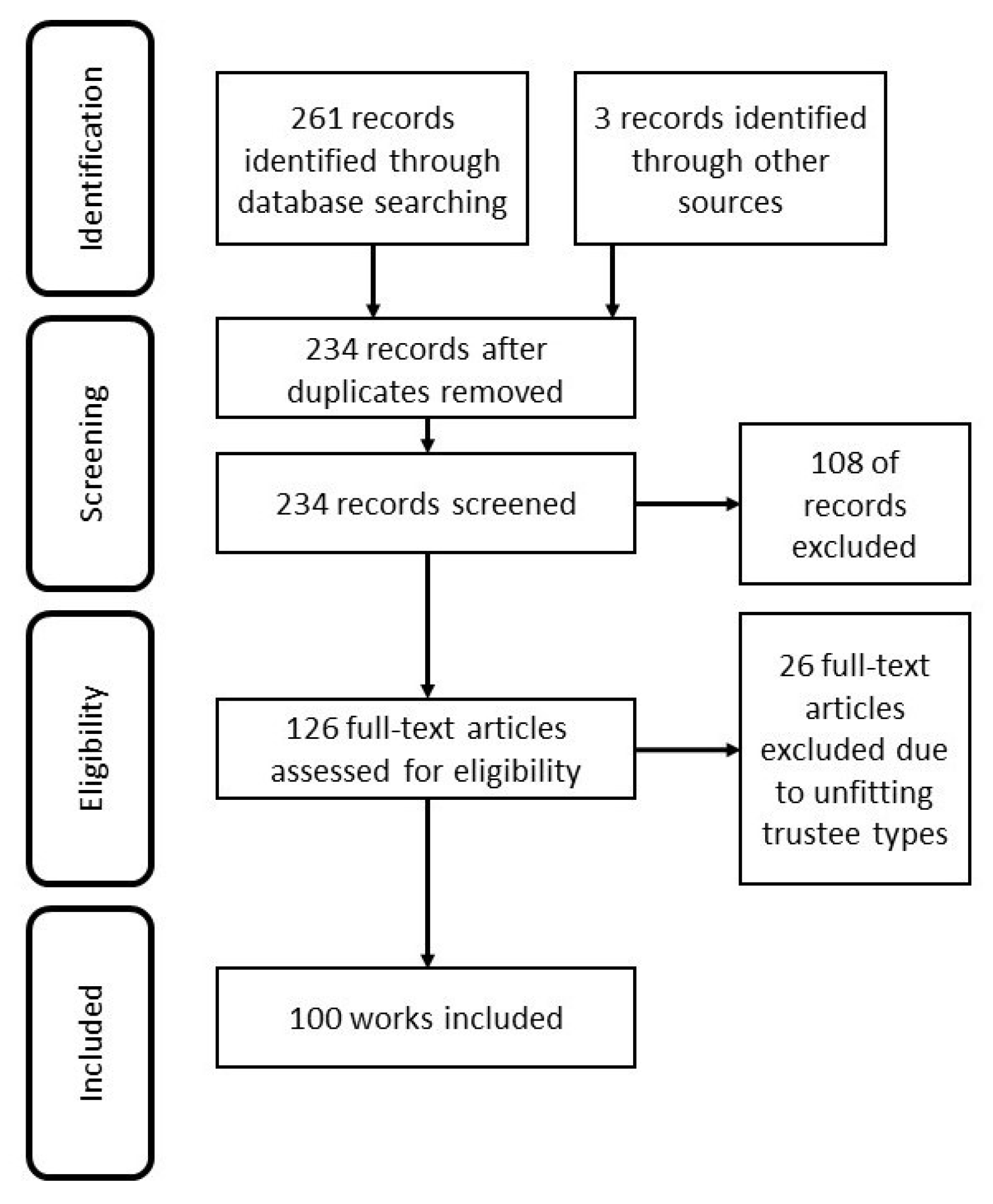
3.1. Methodology
3.2. Results
4. Guideline for Selecting Trustworthiness Facets for CMI Applications
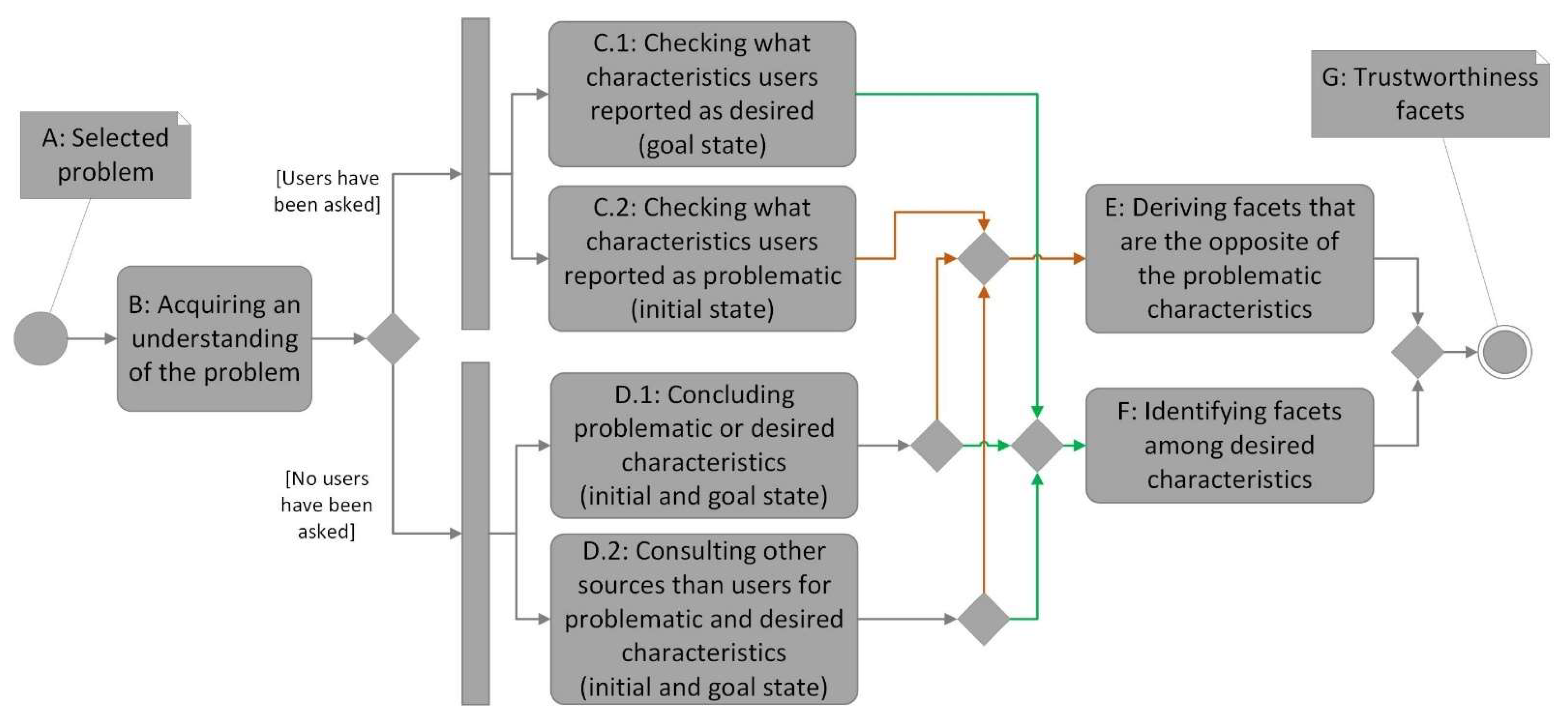
4.1. The Problem
4.2. Acquiring an Understanding
4.3. Identifying Facets Based on User Statements
4.4. Identifying Facets Based on Other Sources
5. Example: Applying the Guideline and the Overview to Catfishing
6. Discussion
6.1. Trustworthiness Facets in Regard to the Reviewed Literature
6.2. Evaluating the Guideline Regarding the Catfishing Example
6.3. Trustworthiness Facets in Regard to Initial Trust and Knowledge-Based Trust within CMI Applications
6.4. Misuse of Trustworthiness Facets
6.5. Limitation and Future Work
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| CMI | Computer-Mediated Introduction |
| TrustSoft | Method for Trust-Related Software Features |
| PRISMA-P | Preferred Reporting Items for Systematic Review and Meta-Analysis Protocols |
| UML | Unified Modeling Lanuage |
Appendix A
| Trustworthiness Facets | Definition | References |
|---|---|---|
| Ability, competence, expertise, knowledge, skill, wisdom, business sense, influence, power | Skills or characteristics that enable to fulfill obligations or to have impact in a specific domain. | [5,65,66,67,68,69,70,71,72,73,74,75] |
| Accessibility, approachability, attentiveness, availability, openness, receptivity | Being physically present when needed, mentally open and receptive, easy to talk to and a careful listener. | [20,26,68,69,71,74,75,76] |
| Attractiveness | Being appealing to others. | [20,73,77] |
| Benevolence, availability, candor, care, loyalty, openness, receptivity, agreeableness, selflessness, honesty, altruism, goodwill | Having concerns about others, wanting something good for others and acting in their interest without an egocentric motive. | [5,20,24,26,69,71,73,74,75,76,78,79] |
| Confidentiality, discreetness | Entrusted knowledge is kept in confidence. | [68,69,80] |
| Emotional stability | “[B]eing calm, enthusiastic, free from anxiety, depression and insecurity” [68] | [73] |
| Empathy | The ability to comprehend feelings of others. | [26] |
| Extraversion, dynamism | Talkativeness, sociability, friendliness | [73,74] |
| Honesty, credibility, truthfulness, authenticity, openness, accuracy, willingness to disclose | Correctness of information and freely sharing information and ideas | [20,26,66,68,70,71,72,76] |
| Humbleness | The notion to not take oneself more important than others | [27] |
| Integrity, fairness, consistency, reliability, discreetness, morality, ethicality, credibility, honesty | The trustee complies to the trustor’s accepted principles (e.g., moral, ethical) that are predictable and reliable leading to equity. | [7,26,65,67,68,69,72,73,74,75,78,81] |
| Justice, fairness | The trustee morally respects the trustor’s interests and the trustor herself—especially concerning provided information and interactions. | [68,82,83] |
| Likability, rapport | Friendliness, high sympathy and a person with whom the trustor wants to spend time together and cooperate. | [71,84,85] |
| Predictability, consistency, reliability, good judgement, promise fulfillment, dependability, conscientiousness, performance | A stability in one’s actions that is based on recurring behaviour, the ability to make good decisions, being productive and carrying out responsibilities reliably. | [68,69,73,74,75,76,79,86] |
| Popularity, social desirability | Social or cultural approval, socially desirable | [74,79] |
| Reputation | The perceived identity of a trustee which reflects personality traits, behaviour or presented images that is based on the trustor’s own observations over a period of time or on secondary sources. | [19,87] |
| Respectfulness | The trustee regards “others and their perspective as valuable” [26] | [26] |
| Similarity, shared understanding, share of values | Perception of shared interests, values, appearance, lifestyle, status or culture | [20,65,71,72,85,88] |
| Trustworthiness Facets | Definition | References |
|---|---|---|
| Ability, competence, expertise, credibility | The system is believed to have the skills and expertise to perform and act effectively in specific domains and to fulfill its promised services and responsibilities. Based on that, the user accepts its advice and believes its output. | [14,21,56,57,85,89,90,91,92] |
| Benevolence, helpfulness, goodwill | The system acts in the user’s interests, cares for him/her, is well-intentioned and provides help or guidance when needed. | [14,21,56,57,85,89] |
| Information quality, content quality, data-related quality (consists of data integrity, data reliability, data timeliness, data validity), usefulness | The system provides sufficient information that is accurate, understandable, useful, complete, relevant and timely updated so that the user is able to evaluate the context (e.g., product, service, seller). | [14,24,63,85,93,94] |
| Integrity, compliance, compatibility | The system complies with standards (e.g., industry specific standards) or regulations, adheres to the user’s accepted ethical or moral codes and is compatible with his/her beliefs or values. | [14,21,24,56,57,77,90] |
| Non-Repudiation | Ability to prove to sender that data has been delivered and to prove to receiver the sender identity for an unambiguous data transmission. | [24] |
| Openness, transparency | The system provides how it works and complies to standards and regulations. | [24,93] |
| Performance, reliability, predictability, dependability, functionality, accuracy, availability, failure tolerance, accountability, responsiveness, result demonstrability, correctness | The system executes correctly to accomplish the service that it promises. It is predictable despite potential failures and delivers proper outputs. | [14,15,21,24,56,77,85,95,96,97,98,99] |
| Privacy, confidentiality | Privacy refers to the provision of information and the risk of its exposure to unintended parties. Systems, which respect their users’ privacy, limit the access of the users’ data to only authorized agents and enable users to take control of its usage. | [24,63,85,92,96,98,99] |
| Reputation, image, brand strength, visibility | On the one hand, the technology’s recognition and how much it might enhance the user’s social status. On the other hand, an “easy identification of the [associated] company and its activity sector” [98]. | [77,92,97,98,100] |
| Safety | The system operates in a way that keeps its users’ life and property safe and does not risk any harm or injuries. | [15,24,63] |
| Security, confidentiality | The system knows its users’ vulnerabilities and protects them and their resources against attacks, misuses and unauthorized access. | [15,24,63,85,92,95,96,99,101,102] |
| Situational normality, social presence | The perception that the system is “normal, proper, or suited to a successful venture” as well as “personal, sociable, and [has] sensitive human elements, creating a feeling of human touch” [58]. | [20,21,63] |
| Usability, comprehensibility, effectiveness, ease-of-use, efficiency | A system designed in a way that enables users to effortlessly use it with easy access to understandable information that supports users in the usage. | [21,24,57,92,93,94,96,97,102] |
| Website quality, completeness, perceived usefulness, web site design, interface design, likeability | On the one hand, the extent to which the implemented set of software features meet the needs of its users. One the other hand, an attractive graphical design in terms of structure, navigation and content. | [14,21,24,63,85,94,96,97,102] |
| Trustworthiness Facets | Definition | References |
|---|---|---|
| Ability, competence, financial balance, quality assurance | Knowledge and skills to provide the service or product promised by the organization (while being both effective and efficient in regard to expended costs) | [19,20,22,23,75,92] |
| Benevolence, concern, goodness, morality, caring, interactional courtesy, responsibility to inform | Respecting and showing respect to the interests of the consumers and not taking advantage of their vulnerability. | [19,20,22,75] |
| Familiarity, similarity | Perception of same values or interests | [66,78,85,103] |
| Integrity, (procedural) fairness, justice, legal compliance, structural assurance | The existence of principles, values, standards or regulations (e.g., law, organizational policies, organizational procedures, contracts) to which an organization corresponds as promised. This most often relates to a high quality of treatment and equity. | [19,20,22,23,68,81,83,95,104,105] |
| Openness, honesty, transparency, confidential information sharing, responsibility to inform, comprehensibility | The availability, simplicity or clarity of information disclosed by an organization that allow individuals to comprehend the performance or internal workings of that organization. | [19,22,71,74,75,106] |
| Performance | Current actions for providing a service or product, which may involve the delivery, relative costs and the performance of the service/product itself. | [71] |
| Reliability, credibility, consistency, dependability, responsibility, predictability | The organization complies by its actions with its promises and offers guidance and support in times of crisis. | [19,23,75,102,104] |
| Reputation, prototypical organizational identity, brand image | Perception of an organization’s culture, attributes, beliefs, values or prestige based on customer’s own experience or hearsay from secondary sources. | [20,71,74,78,83,93,96,97] |
| Responsiveness, interactivity | Being responsive to the customers’ requests and providing rapid feedback | [22,85,93,98] |
| Security | The organization provides a comfortable, assured and safe feeling | [20] |
| Situational normality | The individual’s belief of an organization’s success based on the perception how customary a situation with the organization seems to be | [19,102] |
| Size | The larger a company overall size and its market share position, the more experience it seems to have leading to a higher perception of trustworthiness. | [71,96,97,102] |
| Willingness to customize, service customization | Specialized equipment or adaptation of production processes or services to meet the customer’s needs. | [71,93,96,97,98,102] |
References
- Lewicki, R.J.; Wiethoff, C. Trust, trust development, and trust repair. In The Handbook of Conflict Resolution: Theory and Practice; Jossey-Bass: San Francisco, CA, USA, 2000; Volume 1, pp. 86–107. [Google Scholar]
- Meyerson, D.; Weick, K.E.; Kramer, R.M. Swift Trust and Temporary Groups. In Trust in Organizations: Frontiers of Theory and Research, 3rd ed.; Sage: Thousand Oaks, CA, USA, 1996; Volume 166. [Google Scholar]
- Kapanova, K.; Koidl, K. Towards a model of interpersonal trust in Social Media Applications. In Proceedings of the 5th EAI International Conference on Smart Objects and Technologies for Social Good, Valencia, Spain, 25–27 September 2019; pp. 120–123. [Google Scholar]
- Obada-Obieh, B.; Somayaji, A. Can I believe you? Establishing trust in computer mediated introductions. In Proceedings of the 2017 New Security Paradigms Workshop, Santa Cruz, CA, USA, 1–4 October 2017; pp. 94–106. [Google Scholar]
- Mayer, R.C.; Davis, J.H.; Schoorman, F.D. An integrative model of organizational trust. Acad. Manag. Rev. 1995, 20, 709–734. [Google Scholar] [CrossRef]
- Jozsa, K.; Kraus, A.; Korpak, A.K.; Birnholtz, J.; Moskowitz, D.A.; Macapagal, K. “Safe Behind My Screen”: Adolescent Sexual Minority Males’ Perceptions of Safety and Trustworthiness on Geosocial and Social Networking Apps. Arch. Sex. Behav. 2021, 50, 2965–2980. [Google Scholar] [CrossRef]
- Yi, J.; Yuan, G.; Yoo, C. The effect of the perceived risk on the adoption of the sharing economy in the tourism industry: The case of Airbnb. Inf. Process. Manag. 2020, 57, 102108. [Google Scholar] [CrossRef]
- Malhotra, A.; Van Alstyne, M. The dark side of the sharing economy … and how to lighten it. Commun. ACM 2014, 57, 24–27. [Google Scholar] [CrossRef]
- Couch, D.; Liamputtong, P.P. Online dating and mating: Perceptions of risk and health among online users. Health Risk Soc. 2007, 9, 275–294. [Google Scholar] [CrossRef]
- Lee, Z.W.Y.; Chan, T.K.; Balaji, M.; Chong, A.Y.-L. Why people participate in the sharing economy: An empirical investigation of Uber. Internet Res. 2018, 28, 829–850. [Google Scholar] [CrossRef]
- Son, J.Y.; Kim, S.S. Internet users’ information privacy-protective responses: A taxonomy and a nomological model. MIS Q. 2008, 32, 503–529. [Google Scholar] [CrossRef] [Green Version]
- Hang, L.; Kim, D.-H. SLA-Based Sharing Economy Service with Smart Contract for Resource Integrity in the Internet of Things. Appl. Sci. 2019, 9, 3602. [Google Scholar] [CrossRef] [Green Version]
- Borchert, A.; Ferreyra, N.; Heisel, M. A Conceptual Method for Eliciting Trust-related Software Features for Computer-mediated Introduction. In Proceedings of the ENASE 2020, Prague, Czech Republic, 5–6 May 2020; pp. 269–280. [Google Scholar]
- Mcknight, D.H.; Carter, M.; Thatcher, J.B.; Clay, P.F. Trust in a specific technology: An investigation of its components and measures. ACM Trans. Manag. Inf. Syst. (TMIS) 2011, 2, 1–25. [Google Scholar] [CrossRef]
- Ding, S.; Yang, S.-L.; Fu, C. A novel evidential reasoning based method for software trustworthiness evaluation under the uncertain and unreliable environment. Expert Syst. Appl. 2012, 39, 2700–2709. [Google Scholar] [CrossRef]
- Guadagno, R.E.; Okdie, B.M.; Kruse, S.A. Dating deception: Gender, online dating, and exaggerated self-presentation. Comput. Hum. Behav. 2012, 28, 642–647. [Google Scholar] [CrossRef]
- Kotonya, G.; Sommerville, I. Requirements engineering with viewpoints. Softw. Eng. J. 1996, 11, 5–18. [Google Scholar] [CrossRef] [Green Version]
- Becerra, M.; Gupta, A.K. Perceived Trustworthiness within the Organization: The Moderating Impact of Communication Frequency on Trustor and Trustee Effects. Organ. Sci. 2003, 14, 32–44. [Google Scholar] [CrossRef] [Green Version]
- McKnight, D.H.; Cummings, L.L.; Chervany, N.L. Initial trust formation in new organizational relationships. Acad. Manag. Rev. 1998, 23, 473–490. [Google Scholar] [CrossRef] [Green Version]
- McKnight, D.H.; Chervany, N.L. What Trust Means in E-Commerce Customer Relationships: An Interdisciplinary Conceptual Typology. Int. J. Electron. Commer. 2001, 6, 35–59. [Google Scholar] [CrossRef]
- Paravastu, N. Dimensions of Technology Trustworthiness and Technology Trust Modes. In Encyclopedia of Information Science and Technology, 3rd ed.; IGI Global: Hershey, PA, USA, 2015; pp. 4301–4309. [Google Scholar]
- Caldwell, C.; Clapham, S.E. Organizational Trustworthiness: An International Perspective. J. Bus. Ethics 2003, 47, 349–364. [Google Scholar] [CrossRef]
- Carnevale, D.G. Trustworthy Government: Leadership and Management Strategies for Building Trust and High Performance; Jossey-Bass: San Francisco, CA, USA, 1995. [Google Scholar]
- Mohammadi, N.G.; Paulus, S.; Bishr, M.; Metzger, A.; Koennecke, H.; Hartenstein, S.; Pohl, K. An Analysis of Software Quality Attributes and Their Contribution to Trustworthiness. In Proceedings of the CLOSER, Aachen, Germany, 8–10 May 2013; pp. 542–552. [Google Scholar]
- Kan, S.H. Metrics and Models in Software Quality Engineering; Addison-Wesley Professional: San Francisco, CA, USA, 2003. [Google Scholar]
- Wilkins, C.H. Effective Engagement Requires Trust and Being Trustworthy. Med. Care 2018, 56, S6–S8. [Google Scholar] [CrossRef] [PubMed]
- Ferrin, D.L.; Bligh, M.C.; Kohles, J.C. It takes two to tango: An interdependence analysis of the spiraling of perceived trustworthiness and cooperation in interpersonal and intergroup relationships. Organ. Behav. Hum. Decis. Process. 2008, 107, 161–178. [Google Scholar] [CrossRef]
- Levin, D.Z.; Whitener, E.M.; Cross, R. Perceived trustworthiness of knowledge sources: The moderating impact of relationship length. J. Appl. Psychol. 2006, 91, 1163–1171. [Google Scholar] [CrossRef] [Green Version]
- Lewicki, R.J.; Bunker, B.B. Developing and maintaining trust in work relationships. In Trust in Organizations: Frontiers of Theory and Research; Kramer, R.M., Tyler, T.R., Eds.; Sage: Thousand Oaks, CA, USA, 1996; pp. 114–139. [Google Scholar]
- Lewis, J.D.; Weigert, A. Trust as a social reality. Soc. Forces 1985, 63, 967–985. [Google Scholar] [CrossRef]
- Shi, Y.; Sia, C.L.; Chen, H. Leveraging social grouping for trust building in foreign electronic commerce firms: An exploratory study. Int. J. Inf. Manag. 2013, 33, 419–428. [Google Scholar] [CrossRef]
- Lewicki, R.J.; Bunker, B.B. Trust in Relationships: A Model of Development and Decline; Jossey-Bass: San Francisco, CA, USA; Wiley: Hoboken, NJ, USA, 1995. [Google Scholar]
- Coleman, J.S. Foundations of Social Theory; Harvard University Press: Cambridge, MA, USA, 1994. [Google Scholar]
- Fiore, A.T.; Taylor, L.S.; Mendelsohn, G.; Hearst, M. Assessing attractiveness in online dating profiles. In Proceedings of the Twenty-Sixth Annual CHI Conference on Human Factors in Computing Systems, Florence, Italy, 5–10 April 2008; pp. 797–806. [Google Scholar]
- Chappetta, K.C.; Barth, J.M. How gender role stereotypes affect attraction in an online dating scenario. Comput. Hum. Behav. 2016, 63, 738–746. [Google Scholar] [CrossRef] [Green Version]
- Siau, K.; Shen, Z. Building customer trust in mobile commerce. Commun. ACM 2003, 46, 91–94. [Google Scholar] [CrossRef]
- Jia, L.; Cegielski, C.; Zhang, Q. The Effect of Trust on Customers’ Online Repurchase Intention in Consumer-to-Consumer Electronic Commerce. J. Organ. End User Comput. 2014, 26, 65–86. [Google Scholar] [CrossRef]
- Jones, S.; Marsh, S. Human-computer-human interaction: Trust in CSCW. ACM SIGCHI Bull. 1997, 29, 36–40. [Google Scholar] [CrossRef]
- Tran, T. Protecting buying agents in e-marketplaces by direct experience trust modelling. Knowl. Inf. Syst. 2010, 22, 65–100. [Google Scholar] [CrossRef]
- Moher, D.; Liberati, A.; Tetzlaff, J.; Altman, D.G.; PRISMA Group. Preferred reporting items for systematic reviews and meta-analyses: The PRISMA Statement. PLoS Med. 2009, 6, e1000097. [Google Scholar] [CrossRef] [Green Version]
- Moher, D.; Shamseer, L.; Clarke, M.; Ghersi, D.; Liberati, A.; Petticrew, M.; Shekelle, P.; Stewart, L.A.; PRISMA-P Group. Preferred reporting items for systematic review and meta-analysis protocols (PRISMA-P) 2015 statement. Syst. Rev. 2015, 4, 1. [Google Scholar] [CrossRef] [Green Version]
- Vom Brocke, J.; Simons, A.; Riemer, K.; Niehaves, B.; Plattfaut, R.; Cleven, A. Standing on the shoulders of giants: Challenges and recommendations of literature search in information systems research. Commun. Assoc. Inf. Syst. 2015, 37, 9. [Google Scholar] [CrossRef]
- Fulmer, C.A.; Gelfand, M.J. At what level (and in whom) we trust: Trust across multiple organizational levels. J. Manag. 2012, 38, 1167–1230. [Google Scholar] [CrossRef] [Green Version]
- Beldad, A.; de Jong, M.; Steehouder, M. How shall I trust the faceless and the intangible? A literature review on the antecedents of online trust. Comput. Hum. Behav. 2010, 26, 857–869. [Google Scholar] [CrossRef]
- Razzouk, R.; Shute, V.J. What Is Design Thinking and Why Is It Important? Rev. Educ. Res. 2012, 82, 330–348. [Google Scholar] [CrossRef] [Green Version]
- Lindberg, T.; Meinel, C.; Wagner, R. Design Thinking: A Fruitful Concept for It Development? In Design Thinking; Springer: Berlin/Heidelberg, Germany, 2011; pp. 3–18. [Google Scholar]
- Newell, A. Reasoning, Problem Solving and Decision Processes: The Problem Space as a Fundamental Category; Nickerson, R.S., Ed.; Attention and Performance VIII; Lawrence Erlbaum Associates: Hillsdale, NJ, USA, 1979. [Google Scholar]
- Specification, OMG Available. Meta Object Facility (MOF) 2.0 Core Specification. Available online: https://www.omg.org/spec/MOF/2.0/PDF (accessed on 11 December 2021).
- Mohammadi, N.G. Patterns for Documenting Trust and Trustworthiness. In Trustworthy Cyber-Physical Systems; Springer Vieweg: Wiesbaden, Germany, 2019; pp. 145–166. [Google Scholar]
- Kipnis, D. Trust and technology. In Trust in Organizations: Frontiers of Theory and Research; Sage: Thousand Oaks, CA, USA, 1996; Volume 39, p. 50. [Google Scholar]
- Yousuf, M.; Asger, M. Comparison of Various Requirements Elicitation Techniques. Int. J. Comput. Appl. 2015, 116, 8–15. [Google Scholar] [CrossRef]
- Cobb, C.; Kohno, T. How public is my private life? Privacy in online dating. In Proceedings of the 26th International Conference on World Wide Web, Perth, Australia, 3–7 April 2017; pp. 1231–1240. [Google Scholar]
- Simmons, M.; Lee, J.S. Catfishing: A Look into Online Dating and Impersonation. In Proceedings of the International Conference on Human-Computer Interaction, Copenhagen, Denmark, 19–24 July; pp. 349–358.
- Schulman, N. In Real Life: Love, Lies & Identity in the Digital Age; Grand Central Publishing: New York, NY, USA, 2014. [Google Scholar]
- Roy, M.C.; Dewit, O.; Aubert, B.A. The impact of interface usability on trust in Web retailers. Internet Res. 2001, 11, 388–398. [Google Scholar] [CrossRef]
- Liu, X.; Yuan, C.; Hafeez, M.; Faisal, C.M.N. Digital Trust Mediated by the Platform in the Sharing Economy from a Consumer Perspective. In Proceedings of the International Conference on Management Science and Engineering Management, Toledo, Spain, 30 July–2 August 2020; pp. 670–684. [Google Scholar]
- Tan, C.W.; Benbasat, I.; Cenfetelli, R.T. Building citizen trust towards e-government services: Do high quality websites matter? In Proceedings of the 41st Annual Hawaii International Conference on System Sciences (HICSS 2008), Waikoloa, HI, USA, 7–10 January 2008; p. 217. [Google Scholar]
- Licoppe, C. Liquidity and attachment in the mobile hookup culture. A comparative study of contrasted interactional patterns in the main uses of Grindr and Tinder. J. Cult. Econ. 2019, 13, 73–90. [Google Scholar] [CrossRef]
- Sharabi, L.L.; Caughlin, J.P. Deception in online dating: Significance and implications for the first offline date. New Media Soc. 2018, 21, 229–247. [Google Scholar] [CrossRef]
- Sullivan, A. Love in the Time of Coronavirus: COVID-19 Changes the Game for Online Dating; Deutsche Welle: Bonn, Germany, 2020. [Google Scholar]
- Di Gangi, P.M.; Wasko, M.M. Social media engagement theory: Exploring the influence of user engagement on social media usage. J. Organ. End User Comput. (JOEUC) 2016, 28, 53–73. [Google Scholar] [CrossRef] [Green Version]
- Mao, Z.E.; Jones, M.F.; Li, M.; Wei, W.; Lyu, J. Sleeping in a stranger’s home: A trust formation model for Airbnb. J. Hosp. Tour. Manag. 2019, 42, 67–76. [Google Scholar] [CrossRef]
- Magdy, W.; Elkhatib, Y.; Tyson, G.; Joglekar, S.; Sastry, N. Fake it till you make it: Fishing for Catfishes. In Proceedings of the 2017 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining (ASONAM), Sydney, Australia, 31 July–3 August 2017; pp. 497–504. [Google Scholar]
- Borchert, A.; Wainakh, A.; Krämer, N.; Mühlhäuser, M.; Heisel, M. Mitigating Privacy Concerns by Developing Trust-related Software Features for a Hybrid Social Media Application. In Proceedings of the ENASE, Online, 26–27 April 2021; pp. 269–280. [Google Scholar]
- Golesorkhi, B. Gender differences and similarities in judgments of trustworthiness. Women Manag. Rev. 2006, 21, 195–210. [Google Scholar] [CrossRef]
- Colquitt, J.A.; Scott, B.A.; Lepine, J.A. Trust, trustworthiness, and trust propensity: A meta-analytic test of their unique relationships with risk taking and job performance. J. Appl. Psychol. 2007, 92, 909–927. [Google Scholar] [CrossRef]
- Jones, S.L.; Shah, P.P. Diagnosing the locus of trust: A temporal perspective for trustor, trustee, and dyadic influences on perceived trustworthiness. J. Appl. Psychol. 2016, 101, 392–414. [Google Scholar] [CrossRef]
- Butler, J.K., Jr. Toward understanding and measuring conditions of trust: Evolution of a conditions of trust inventory. J. Manag. 1991, 17, 643–663. [Google Scholar] [CrossRef]
- Gabarro, J.J. The Development of Trust, Influence and Expectations. Interpersonal Behavior: Communication and Understanding in Relationships; Prentice Hall: Englewood Cliffs, NJ, USA, 1978; pp. 290–303. [Google Scholar]
- Roberts, K.H.; O’Reilly, C.A. Measuring organizational communication. J. Appl. Psychol. 1974, 59, 321–326. [Google Scholar] [CrossRef]
- Doney, P.M.; Cannon, J.P. An examination of the nature of trust in buyer–seller relationships. J. Mark. 1997, 61, 35–51. [Google Scholar]
- Crosby, L.A.; Evans, K.R.; Cowles, D. Relationship quality in services selling: An interpersonal influence perspective. J. Mark. 1990, 54, 68–81. [Google Scholar] [CrossRef]
- Giffin, K. The contribution of studies of source credibility to a theory of interpersonal trust in the communication process. Psychol. Bull. 1967, 68, 104–120. [Google Scholar] [CrossRef]
- Bews, N.F.; Rossouw, G.J. A Role for Business Ethics in Facilitating Trustworthiness. J. Bus. Ethics 2002, 39, 377–390. [Google Scholar] [CrossRef]
- Mishra, A.K. Organizational responses to crisis. Trust in organizations. Front. Theory Res. 1996, 261, 1996. [Google Scholar]
- Jennings, E.E. Routes to the Executive Suite; McGraw Hill: New York City, NY, USA, 1971. [Google Scholar]
- Van Slyke, C.; Comunale, C.L.; Belanger, F. Gender differences in perceptions of web-based shopping. Commun. ACM 2002, 45, 82–86. [Google Scholar] [CrossRef]
- Klotz, A.C.; Veiga, S.P.D.M.; Buckley, M.R.; Gavin, M.B. The role of trustworthiness in recruitment and selection: A review and guide for future research. J. Organ. Behav. 2013, 34, S104–S119. [Google Scholar] [CrossRef]
- Rotter, J.B. Generalized expectancies for interpersonal trust. Am. Psychol. 1971, 26, 443–452. [Google Scholar] [CrossRef]
- Sofer, C.; Dotsch, R.; Wigboldus, D.H.; Todorov, A. What is typical is good: The influence of face typicality on perceived trustworthiness. Psychol. Sci. 2015, 26, 39–47. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Holtz, B.C. Trust primacy: A model of the reciprocal relations between trust and perceived justice. J. Manag. 2013, 39, 1891–1923. [Google Scholar] [CrossRef] [Green Version]
- Chiaburu, D.S.; Lim, A.S. Manager Trustworthiness or Interactional Justice? Predicting Organizational Citizenship Behaviors. J. Bus. Ethics 2007, 83, 453–467. [Google Scholar] [CrossRef]
- Ferris, G.R.; Blass, F.R.; Douglas, C.; Kolodinsky, R.W.; Treadway, D.C. Personal Reputation in Organizations; Lawrence Erlbaum Associates: Mahwah, NJ, USA, 2003. [Google Scholar]
- Jap, S.; Robertson, D.C.; Hamilton, R. The Dark Side of Rapport: Agent Misbehavior Face-to-Face and Online. Manag. Sci. 2011, 57, 1610–1622. [Google Scholar] [CrossRef] [Green Version]
- Corbitt, B.J.; Thanasankit, T.; Yi, H. Trust and e-commerce: A study of consumer perceptions. Electron. Commer. Res. Appl. 2003, 2, 203–215. [Google Scholar] [CrossRef]
- McAllister, D.J. Affect-and cognition-based trust as foundations for interpersonal cooperation in organizations. Acad. Manag. J. 1995, 38, 24–59. [Google Scholar]
- Merluzzi, T.V.; Brischetto, C.S. Breach of confidentiality and perceived trustworthiness of counselors. J. Couns. Psychol. 1983, 30, 245. [Google Scholar] [CrossRef]
- Jiang, C.X.; Chua, R.Y.; Kotabe, M.; Murray, J.Y. Effects of cultural ethnicity, firm size, and firm age on senior executives’ trust in their overseas business partners: Evidence from China. J. Int. Bus. Stud. 2011, 42, 1150–1173. [Google Scholar] [CrossRef]
- Tseng, S.; Fogg, B.J. Credibility and computing technology. Commun. ACM 1999, 42, 39–44. [Google Scholar] [CrossRef]
- Wang, W.; Benbasat, I. Trust in and adoption of online recommendation agents. J. Assoc. Inf. Syst. 2005, 6, 4. [Google Scholar]
- Fogg, B.J.; Tseng, H. The elements of computer credibility. In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems, Pittsburgh, PA, USA, 15–20 May 1999; pp. 80–87. [Google Scholar]
- Egger, F.N. Affective design of e-commerce user interfaces: How to maximise perceived trustworthiness. In Proceedings of the International Conference on Affective Human Factors Design, Singapore, 27–29 June 2001; pp. 317–324. [Google Scholar]
- Suki, N.M. A structural model of customer satisfaction and trust in vendors involved in mobile commerce. Int. J. Bus. Sci. Appl. Manag. (IJBSAM) 2011, 6, 18–30. [Google Scholar]
- Akhmedova, A.; Vila-Brunet, N.; Mas-Machuca, M. Building trust in sharing economy platforms: Trust antecedents and their configurations. Internet Res. 2021, 31, 1463–1490. [Google Scholar] [CrossRef]
- Kim, K.K.; Prabhakar, B. Initial trust and the adoption of B2C e-commerce: The case of internet banking. ACM SIGMIS Database DATABASE Adv. Inf. Syst. 2004, 35, 50–64. [Google Scholar] [CrossRef]
- Sahney, S.; Ghosh, K.; Shrivastava, A. Conceptualizing consumer “trust” in online buying behaviour: An empirical inquiry and model development in Indian context. J. Asia Bus. Stud. 2013, 7, 278–298. [Google Scholar] [CrossRef]
- Chen, C. Identifying Significant Factors Influencing Consumer Trust in an Online Travel Site. Inf. Technol. Tour. 2006, 8, 197–214. [Google Scholar] [CrossRef]
- Gu, H.; Zhang, T.; Lu, C.; Song, X. Assessing Trust and Risk Perceptions in the Sharing Economy: An Empirical Study. J. Manag. Stud. 2021, 58, 1002–1032. [Google Scholar] [CrossRef]
- Medeiros, N.; Ivaki, N.; Da Costa, P.N.; Vieira, M. Towards an Approach for Trustworthiness Assessment of Software as a Service. In Proceedings of the 2017 IEEE International Conference on Edge Computing (EDGE), Honolulu, HI, USA, 25–30 June 2017; pp. 220–223. [Google Scholar]
- Grimmelikhuijsen, S.G.; Meijer, A.J. Effects of Transparency on the Perceived Trustworthiness of a Government Organization: Evidence from an Online Experiment. J. Public Adm. Res. Theory 2012, 24, 137–157. [Google Scholar] [CrossRef]
- Bart, Y.; Shankar, V.; Sultan, F.; Urban, G.L. Are the Drivers and Role of Online Trust the Same for All Web Sites and Consumers? A Large-Scale Exploratory Empirical Study. J. Mark. 2005, 69, 133–152. [Google Scholar] [CrossRef] [Green Version]
- Koufaris, M.; Hampton-Sosa, W. The development of initial trust in an online company by new customers. Inf. Manag. 2004, 41, 377–397. [Google Scholar] [CrossRef] [Green Version]
- Gefen, D. E-commerce: The role of familiarity and trust. Omega 2020, 28, 725–737. [Google Scholar] [CrossRef] [Green Version]
- Chathoth, P.K.; Mak, B.; Sim, J.; Jauhari, V.; Manaktola, K. Assessing dimensions of organizational trust across cultures: A comparative analysis of U.S. and Indian full service hotels. Int. J. Hosp. Manag. 2011, 30, 233–242. [Google Scholar] [CrossRef]
- Colquitt, J.A.; Greenberg, J.; Zapata-Phelan, C.P. What is Organizational Justice? A Historical Overview; Lawrence Erlbaum Associates Publishers: Mahwah, NJ, USA, 2005. [Google Scholar]
- AnKee, A.W.; Yazdanifard, R. The review of the ugly truth and negative aspects of online dating. Glob. J. Manag. Bus. Res. E Mark. 2015, 15, M39. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Borchert, A.; Heisel, M. The Role of Trustworthiness Facets for Developing Social Media Applications: A Structured Literature Review. Information 2022, 13, 34. https://doi.org/10.3390/info13010034
Borchert A, Heisel M. The Role of Trustworthiness Facets for Developing Social Media Applications: A Structured Literature Review. Information. 2022; 13(1):34. https://doi.org/10.3390/info13010034
Chicago/Turabian StyleBorchert, Angela, and Maritta Heisel. 2022. "The Role of Trustworthiness Facets for Developing Social Media Applications: A Structured Literature Review" Information 13, no. 1: 34. https://doi.org/10.3390/info13010034
APA StyleBorchert, A., & Heisel, M. (2022). The Role of Trustworthiness Facets for Developing Social Media Applications: A Structured Literature Review. Information, 13(1), 34. https://doi.org/10.3390/info13010034






