Data Security Protocol with Blind Factor in Cloud Environment
Abstract
:1. Introduction
2. Preliminaries
2.1. Indistinguishability
- Adversary input , output a pair of messages of the same length.
- Run to generate a key , select a random bit , , ciphertext is computed and given , is the challenge ciphertext.
- outputs a bit , .
- If output 1, otherwise output 0.
- If , it means success.
2.2. Indistinguishability of Chosen Ciphertext Attack
- Key generation: .
- Adversary input , using the oracle and , output two messages of equal length .
- Elect a random bit , , let , send to adversary .
- Adversary continues to use oracle and . Restriction: Cannot query the plaintext of ciphertext . Output a bit .
- Use output: If output 1, otherwise output 0.
2.3. Large Integer Factorization
2.4. FADE Security
2.5. DaSCE Protocol
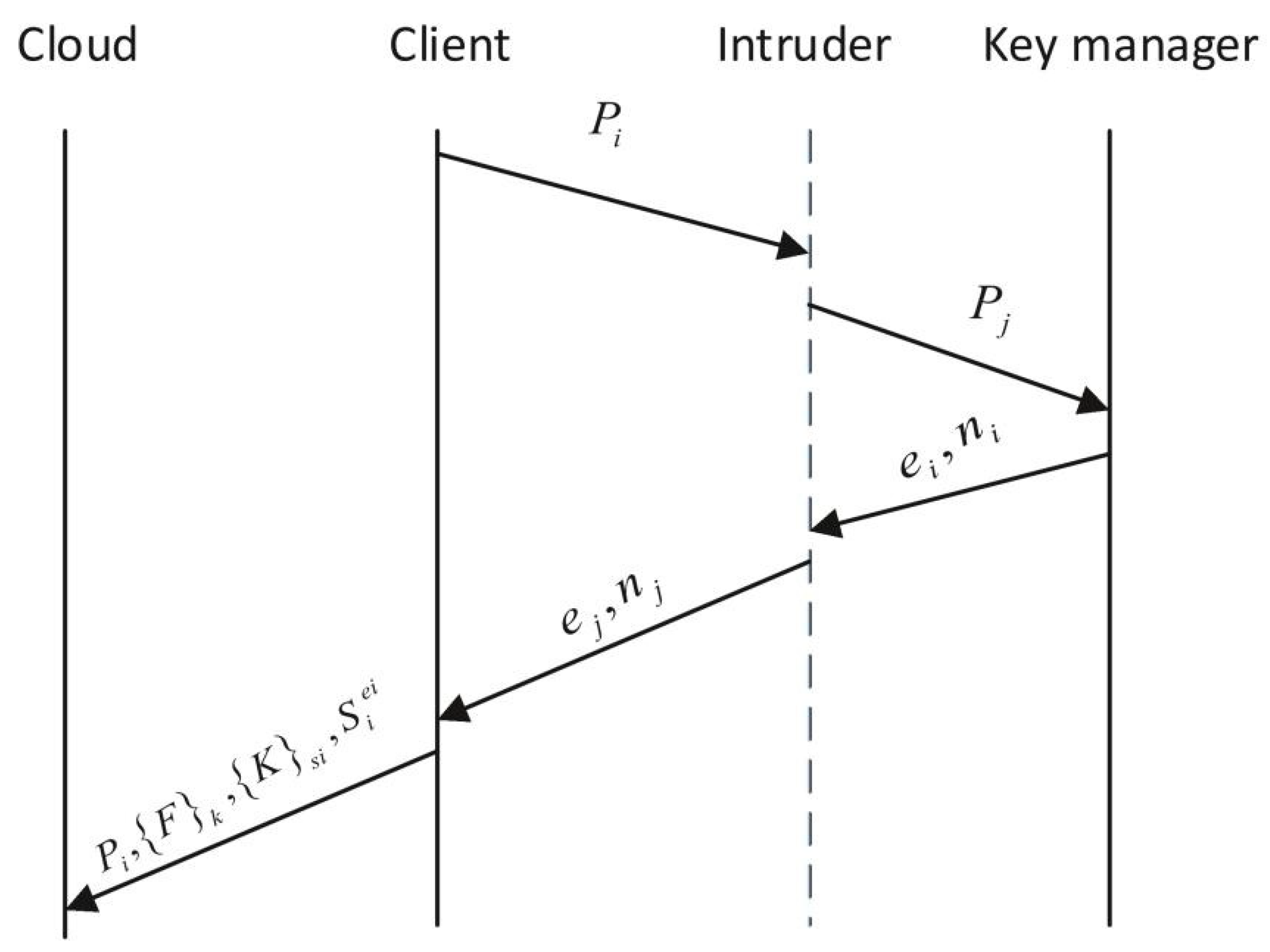
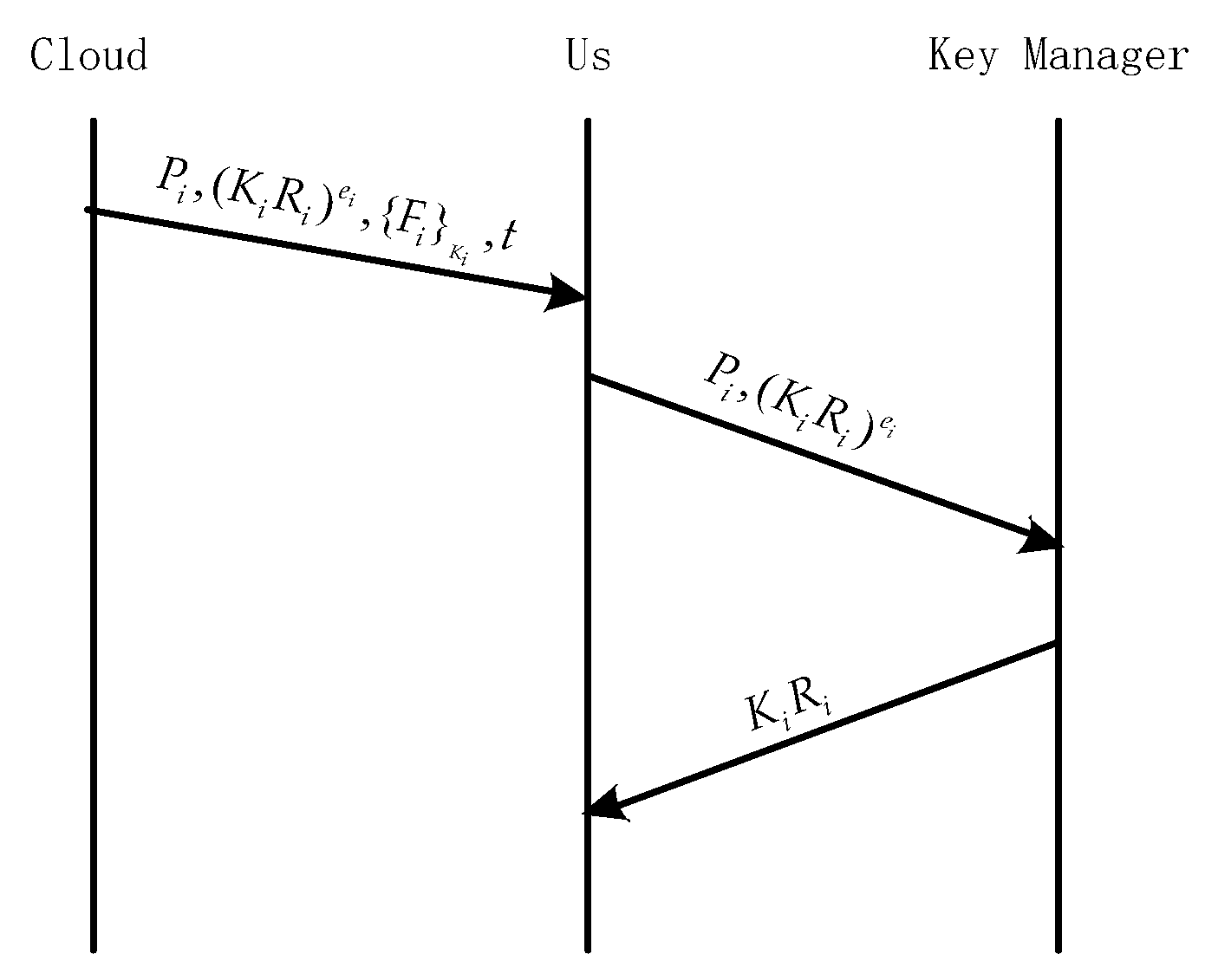
2.5.1. DaSCE File Upload
- The client generates a random number and calculates , and sends it to KM.
- KM generates a random number and computes . KM also computes as the session key between him and the client.
- KM generates digital signature and uses the session key to generate encryption .
- KM sends to the client.
- The client first computes the session key , and declassifies , then verifies the signature.
- The client calculates and , and sends them to KM.
- KM verifies the digital signature of the client, after which KM declassified and generates related to and saves .
- KM calculates and sends it to the client.
- The client encrypts the file with the data key , computes the MAC with (to verify the integrity of ), encrypted and , then uses to encrypt , and the client uploads the encrypted data to the cloud.
- The client deletes all keys except the public key parameters sent by KM.
2.5.2. DaSCE File Download
3. ADSS Model Definition
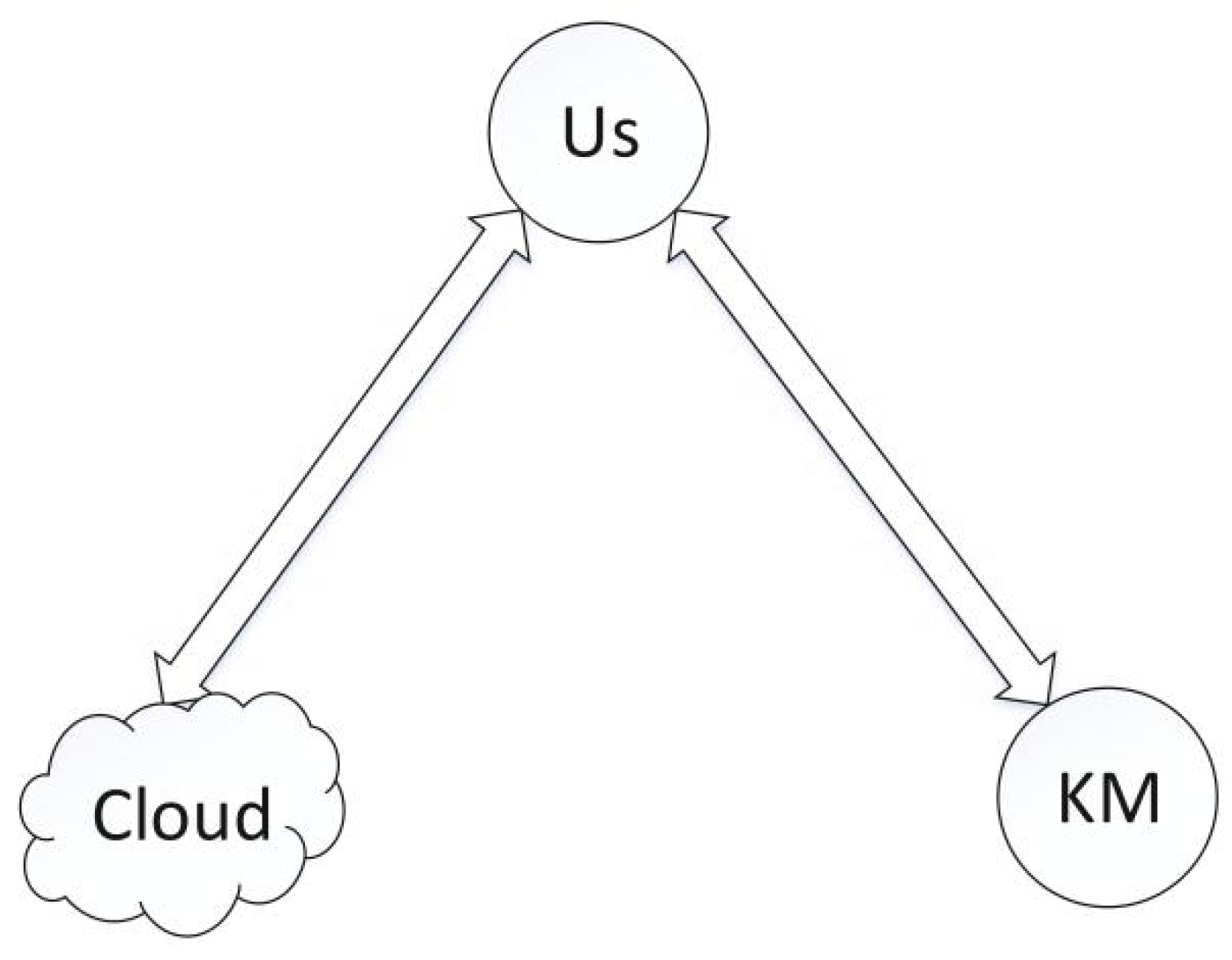
3.1. System Model
- The user encrypts the data by using the public key provided by the key manager KM, and then uploads the ciphertext to the cloud, then clears a large number of local keys and files, and only stores the blind factor and associated information in its USB-key (UKey).
- After downloading the ciphertext from the cloud, the user transmits some ciphertext to KM for decryption, and then the user decrypts the plain text by using its blind factor.
3.2. Security Model
- Initialization. Challenger generation system ADSS, adversary obtains the public key of ADSS.
- Ask. Adversary makes a decryption inquiry to the challenger. After the challenger decrypts, he will give the plain text to adversary .
- Challenge. Adversary outputs two messages of the same length , and then receives ciphertext from the challenger, where the random value .
- Guess. Adversary output , if , then the adversary attack is successful.
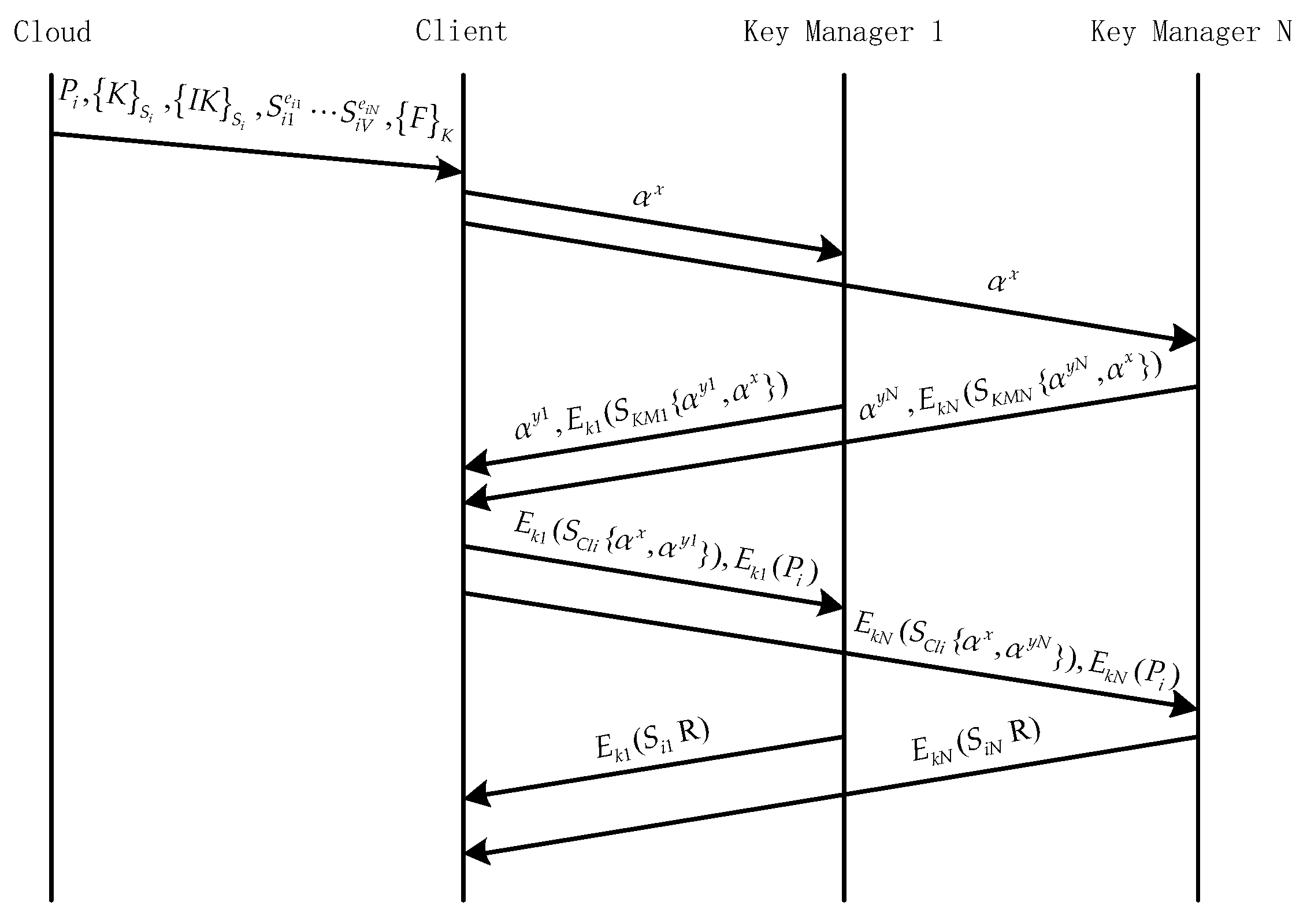
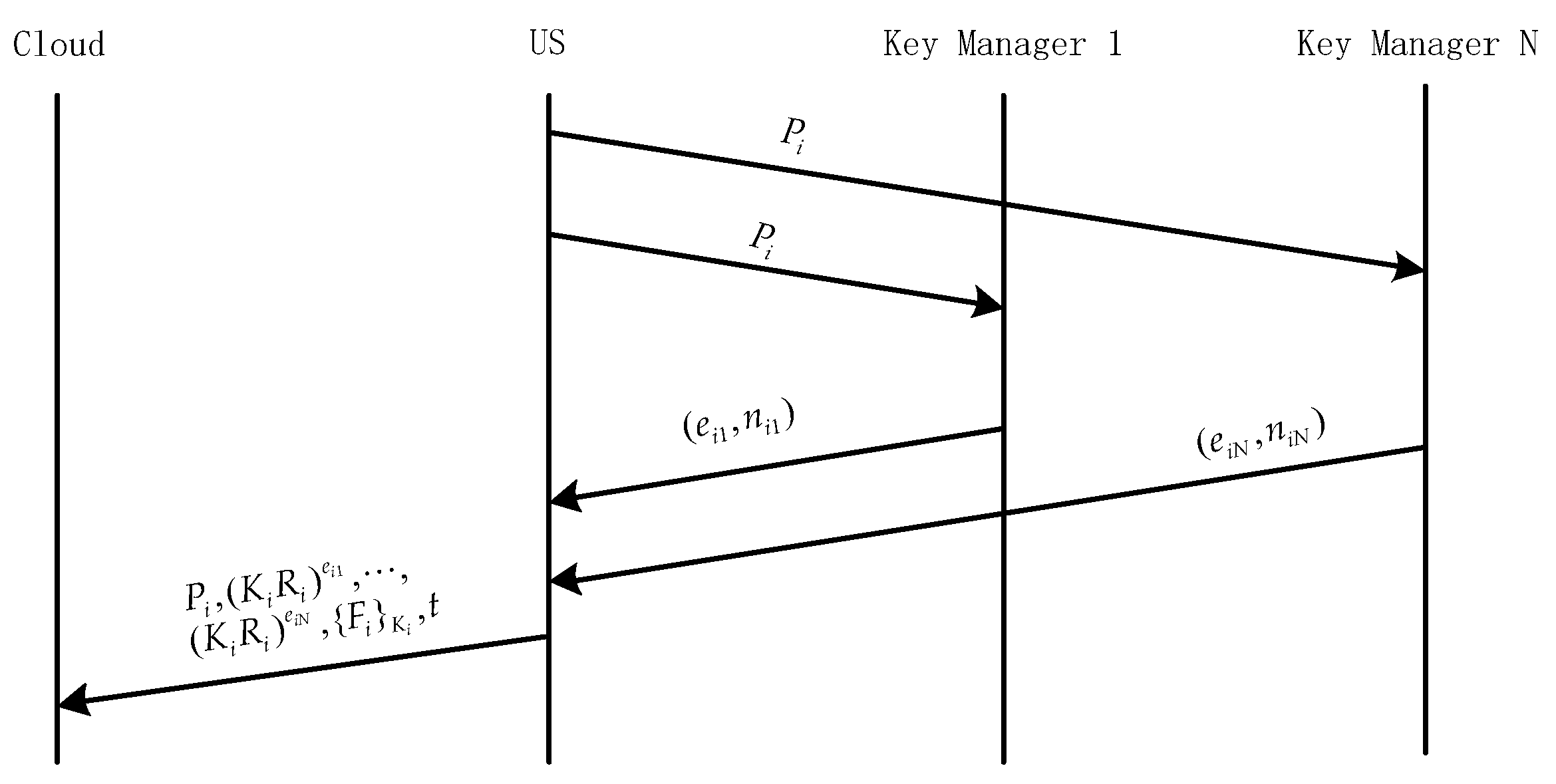
3.3. ADSS Protocol
3.4. File Upload
3.5. File Download
4. Security Analysis
- Run to generate , where are known, and are unknown;
- Adversary obtains message ;
- Randomly select a bit , let ;
- Send to , outputs .
- Choose a random number as a guess for (but does not actually know ), and give to .
- asked: creates a list , the element type is triple , and the initial value is , where indicates that the value of the component is currently unknown. can ask at any time. Let query , calculate and make the following response:
- If there is one item in , answer with .
- If there is one item in , answer with and replace with in .
- Otherwise, select a random number , answer with and store in the table.
- Decryption inquiry: When asks to ask , responds below:
- If there is a first term in , and the second element is (the term or ), then is used to answer.
- Otherwise, select a random number , answer with and store in .
- Challenge: output message , random selection , calculate and answer with . Continue to answer ’s query and decryption query ( cannot query ).
- Guess: output guesses , checks , and if there are items , then output .
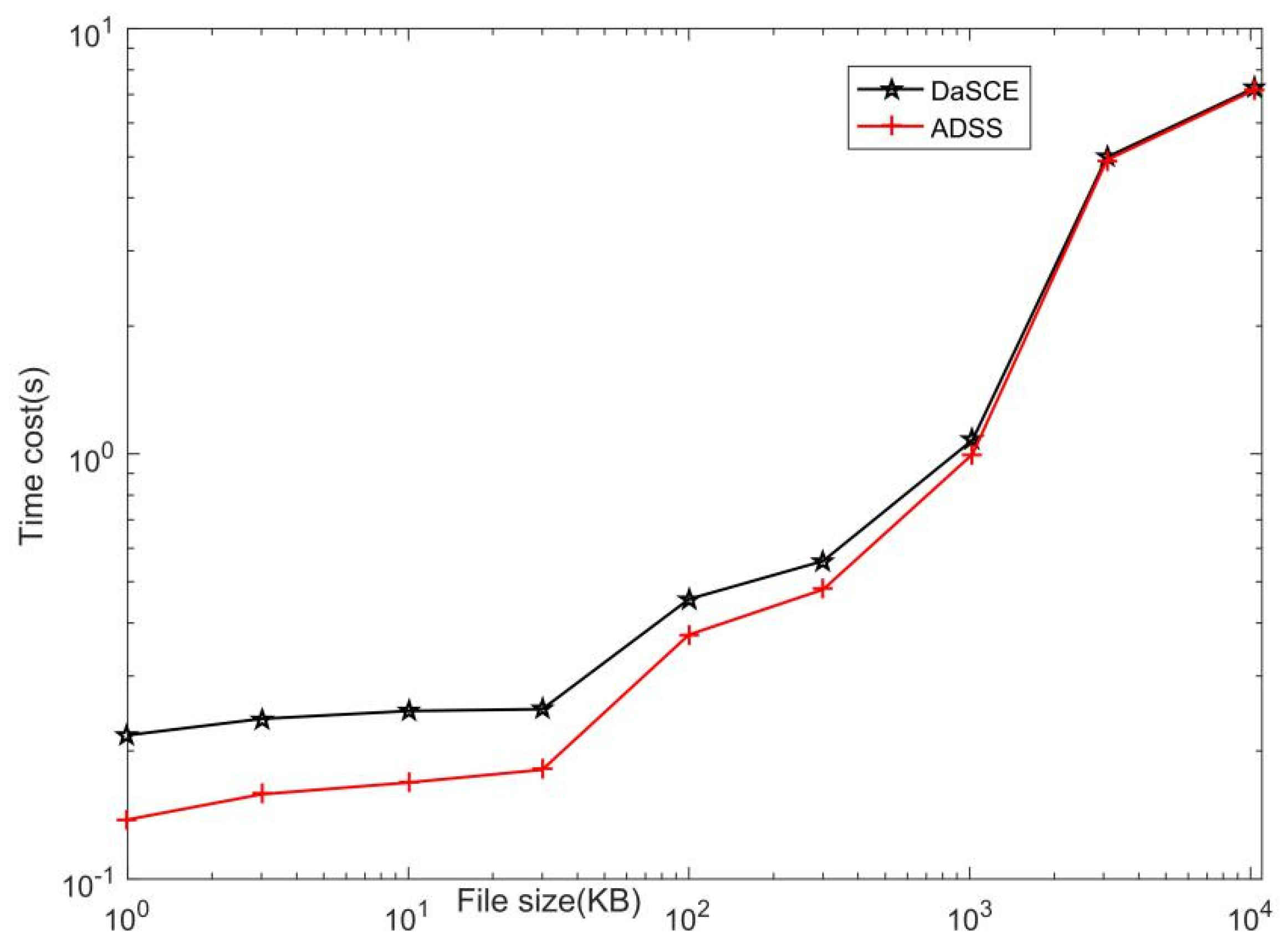
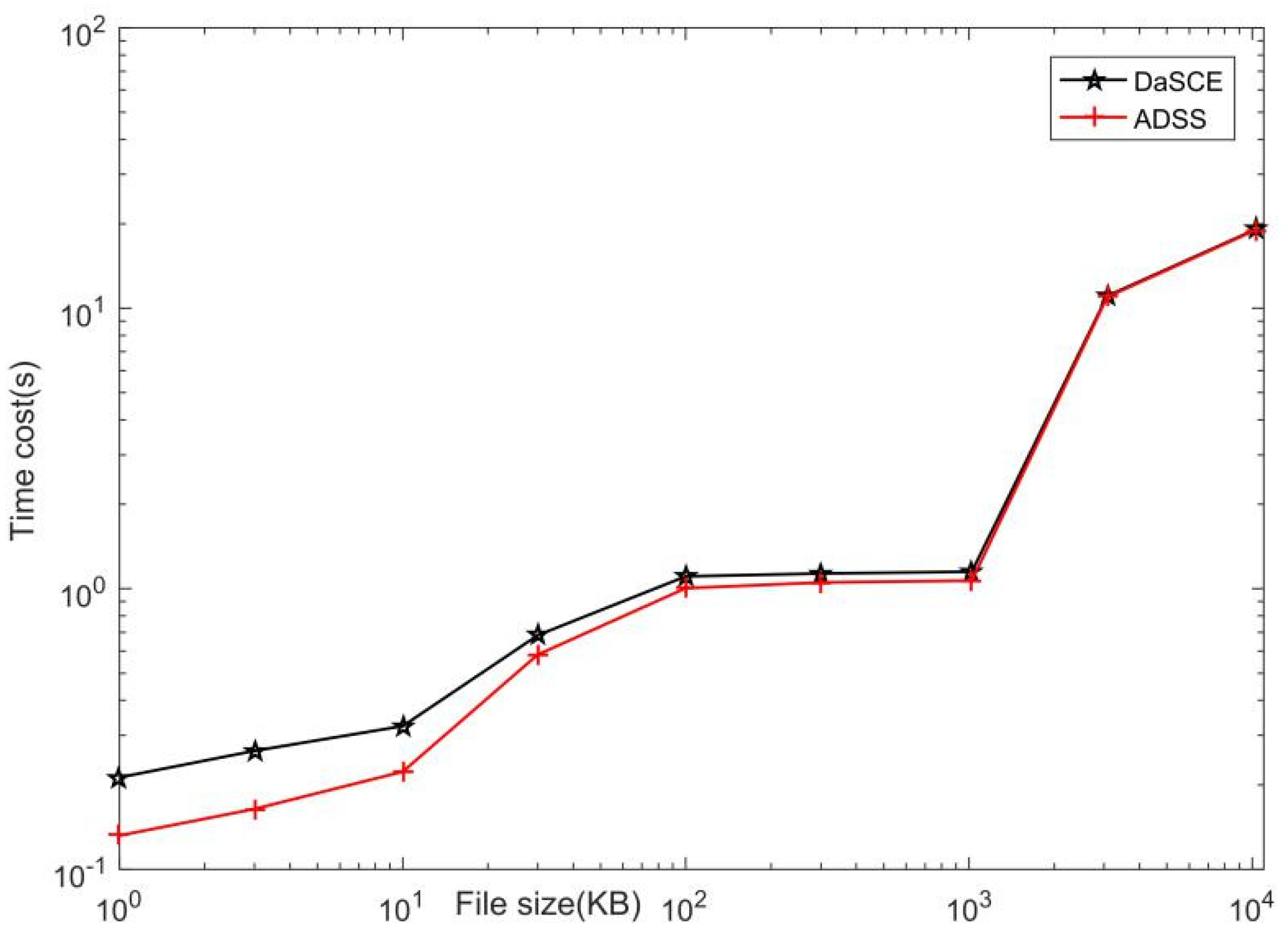
5. Performance Evaluation
5.1. Simulation Experiment
5.2. Performance Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Davood, R. Secure computation for cloud data storage. {IACR} Cryptol. ePrint Arch. 2019, 2019, 709. [Google Scholar]
- Anbuchelian, S.; Sowmya, C.M.; Ramesh, C. Efficient and secure auditing scheme for privacy preserving data storage in cloud. Clust. Comput. 2017, 22, 9767–9775. [Google Scholar] [CrossRef]
- Xian, H.; Liu, H.; Zhang, S.; Hou, R. Verifiable secure data deduplication method in cloud storage. J. Softw. 2020, 31, 455–470. [Google Scholar]
- Nalini, C.; Suresh, R.G. The service of trusted third party in multiple public clouds in dual encryption security mechanism. Int. J. Pure Appl. Math. 2018, 119, 10847–10856. [Google Scholar]
- Song, H.; Li, J.; Li, H. A Cloud Secure Storage Mechanism Based on Data Dispersion and Encryption. IEEE Access 2021, 9, 63745–63751. [Google Scholar] [CrossRef]
- Ali, M.; Bilal, K.; Khan, S.U.; Veeravalli, B.; Li, K.; Zomaya, A. DROPS: Division and Replication of Data in Cloud for Optimal Performance and Security. IEEE Trans. Cloud Comput. 2015, 6, 303–315. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Shen, X.S. Data Security in Cloud Storag; Springer: Berlin/Heidelberg, Germany, 2020; pp. 1–171. [Google Scholar]
- Ogiela, L.; Ogiela, M.R.; Ko, H. Intelligent Data Management and Security in Cloud Computing. Sensors 2020, 20, 3458. [Google Scholar] [CrossRef] [PubMed]
- Han, P.; Liu, C.; Wang, J. Research on data encryption system and technology for cloud storage. J. Commun. 2020, 41, 55–65. [Google Scholar]
- Pan, J. Privacy Protection and Data Security in Cloud Computing: {A} Survey, Challenges, and Solutions. IEEE Access 2019, 7, 147420–147452. [Google Scholar]
- Maharajan, K.; Paramasivan, B. Membrane computing inspired protocol to enhance security in cloud network. J. Supercomput. 2018, 75, 2181–2192. [Google Scholar] [CrossRef]
- Wu, Y.; Ling, J. An improved data integrity verification method for cloud storage. Comput. Eng. 2019, 45, 36–40. [Google Scholar]
- Zhan, Y.; Nie, W. The design of a security cloud storage system based on the trusted third party Providers. Softw. Guide 2018, 17, 186–188. [Google Scholar]
- He, Z.; Li, N.; Xu, X. Data Security Scheme for a Trusted Third Party Platform Based on RSA One-time Key. IOP Conf. Ser. Earth Environ. Sci. 2019, 234, 012046. [Google Scholar] [CrossRef]
- Qian, C.; Xie, F. Cloud storage access control scheme using cp-abe based on trusted third party. Comput. Digit. Eng. 2017, 45, 122–126. [Google Scholar]
- Zhou, S.; Chen, G.; Huang, G. Research on multi-authority cp-abe access control model in multicloud. China Commun. 2020, 17, 220–233. [Google Scholar] [CrossRef]
- Akhila, M.; Hemalatha, E.; Parvathi, S.; Karthikeyan, L. Data security in cloud using semi trusted third party key manager. Int. J. Sci. Res. Sci. Technol. 2016, 111–113. [Google Scholar]
- Jin, Y.; Cai, C.; He, H.; Li, P. BTDA: Dynamic cloud data updating audit scheme based on semi-trusted third party. Comput. Sci. 2018, 45, 144–155. [Google Scholar]
- Tang, Y.; Lee, P.P.C.; Lui, J.C.; Perlman, R. Secure Overlay Cloud Storage with Access Control and Assured Deletion. IEEE Trans. Dependable Secur. Comput. 2012, 9, 903–916. [Google Scholar] [CrossRef] [Green Version]
- Ali, M.; Malik, S.U.R.; Khan, S.U. DaSCE: Data Security for Cloud Environment with Semi-Trusted Third Party. IEEE Trans. Cloud Comput. 2015, 5, 642–655. [Google Scholar] [CrossRef]
- Ali, M.; Dhamotharan, R.; Khan, E.; Khan, S.U.; Vasilakos, A.V.; Li, K.; Zomaya, A.Y. SeDaSC: Secure Data Sharing in Clouds. IEEE Syst. J. 2015, 11, 395–404. [Google Scholar] [CrossRef]
- Stallings, W. Cryptography and Network Security: Principles and Practice, 6th ed.; Publishing House of Electronics Industry: Beijing, China, 2014. [Google Scholar]




| Symbol | Meaning |
|---|---|
| Data file | |
| A symmetric key, data key | |
| Policy file | |
| Forged strategic files | |
| KM generated public key parameters | |
| Public private key pair | |
| Encryption with symmetric key | |
| A symmetric key corresponding to |
| File Size | 1 KB | 3 KB | 10 KB | 30 KB | 100 KB | 300 KB | 1 MB | 3 MB | 10 MB | |
|---|---|---|---|---|---|---|---|---|---|---|
| Protocol | ||||||||||
| DaSCE | 0.217 | 0.238 | 0.249 | 0.250 | 0.455 | 0.560 | 1.078 | 4.989 | 7.238 | |
| ADSS | 0.138 | 0.158 | 0.168 | 0.181 | 0.376 | 0.479 | 0.998 | 4.909 | 7.159 | |
| File Size | 1 KB | 3 KB | 10 KB | 30 KB | 100 KB | 300 KB | 1 MB | 3 MB | 10 MB | |
|---|---|---|---|---|---|---|---|---|---|---|
| Protocol | ||||||||||
| DaSCE | 0.212 | 0.265 | 0.324 | 0.683 | 0.456 | 1.135 | 1.149 | 11.049 | 19.059 | |
| ADSS | 0.131 | 0.164 | 0.223 | 0.181 | 0.582 | 1.106 | 1.068 | 10.967 | 18.960 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, P.; Chi, H.; Wang, J.; Shang, Y. Data Security Protocol with Blind Factor in Cloud Environment. Information 2021, 12, 340. https://doi.org/10.3390/info12090340
Zhang P, Chi H, Wang J, Shang Y. Data Security Protocol with Blind Factor in Cloud Environment. Information. 2021; 12(9):340. https://doi.org/10.3390/info12090340
Chicago/Turabian StyleZhang, Ping, Huanhuan Chi, Jiechang Wang, and Youlin Shang. 2021. "Data Security Protocol with Blind Factor in Cloud Environment" Information 12, no. 9: 340. https://doi.org/10.3390/info12090340
APA StyleZhang, P., Chi, H., Wang, J., & Shang, Y. (2021). Data Security Protocol with Blind Factor in Cloud Environment. Information, 12(9), 340. https://doi.org/10.3390/info12090340






