Abstract
TFHE is a fast fully homomorphic encryption scheme proposed by Chillotti et al. in Asiacrypt’ 2018. Integer-wise TFHE is a generalized version of TFHE that can encrypt the plaintext of an integer that was implicitly presented by Chillotti et al., and Bourse et al. presented the actual form of the scheme in CRYPTO’ 2018. However, Bourse et al.’s scheme provides only homomorphic integer additions and homomorphic evaluations of a sign function. In this paper, we construct a technique for operating any 1-variable function in only one bootstrapping of the integer-wise TFHE. For applications of the scheme, we also construct a useful homomorphic evaluation of several integer arithmetics: division, equality test, and multiplication between integer and binary numbers. Our implementation results show that our homomorphic division is approximately times faster than any existing work and that its run time is less than 1 second for 4-bit integer inputs.
1. Introduction
Gentry first proposed a fully homomorphic encryption (FHE) construction in 2009 [1,2], and a variety of new features and hardness assumptions for FHE schemes [3,4,5,6,7,8,9,10,11,12,13] have been considered. The FHE performs computations on encrypted data without decryption of the data.
One notable application is secure computation in order to protect the secrecy of data against computation servers. An example of secure computation services is privacy-preserving machine learning as a service (MLaaS) [14,15]. In such a service, users want to hide sensitive data (e.g., genomic, anamnesis data, etc.) from the server and the server does not want to provide its cognitive models to users. FHE should be a fundamental component of secure multi-party computation (MPC). However, most applications are constructed without FHE operations because the MPC may require FHE operations many times and the run time of the operations would be substantial due to the inefficiency of FHE schemes.
Most FHE schemes consist of bit-wise or integer-wise encryption operations; the plaintext space is in bit-wise encryption, and the plaintext space is for some in integer-wise encryption [16,17,18]. Some schemes have been executed via integer arithmetics, but bit-wise integer addition and multiplication are not practical even though the bit-wise integer comparison algorithm is efficient [19]. In particular, the full adder algorithm has to execute homomorphic multiplication l times for an l-bit length integer. Thus, homomorphic integer multiplication based on the full adder must execute approximately [18] operations.
On the other hand, integer-wise FHE schemes can efficiently perform addition and multiplication because the construction of those calculations in a homomorphic manner is merely integer addition and multiplication. Recent studies [14,15,20,21] on secure MLaaS used integer-wise homomorphic encryption. Secure integer-wise comparison [22] and integer-wise division [23] have recently been proposed; however, arithmetic operations such as division are remain impractical. The design of efficient algorithms for basic arithmetic operations is an open issue required to reduce computational costs of the operations.
HElib [24], HEAAN [25], PALISADE [26], SEAL [27], and TFHE [6,7,8] are open-source implementations of homomorphic encryption. TFHE is a variant of the FHEW scheme [28] in which the bootstrapping procedure can be performed in less than 0.1 seconds, which is a major bottleneck of FHE. TFHE successfully improved the overall performance of arithmetic operations, although TFHE does not explicitly provide integer-wise arithmetics. Moreover, the number of bootstrapping operations required is equal to the number of bits. Bourse et al. [14] modified TFHE to enable integer-wise encryption, which only supports homomorphic integer addition and homomorphic evaluation of the sign function.
Contribution
In this paper, we present an approach where an arbitrary function is executed during a bootstrap procedure in the integer-wise TFHE scheme with a generalization of the constant variable “test vector” in the bootstrapping. Our bootstrapping procedure is applicable to homomorphic operations of fundamental arithmetics, where specific settings of the value of test vector are given: We propose the homomorphic equality test (Eq, Algorithm 6) and its variant, which test the equality between a ciphertext and a plaintext (ConstEq, Algorithm 7); the homomorphic multiplication between an integer and a binary number (MultbyBin, Algorithm 8); and homomorphic division, where the dividend is a ciphertext and the divisor is a constant plaintext (DivbyConst, Algorithm 9). Based on these building blocks, we propose a homomorphic algorithm for integer division (Div, Algorithm 10). Our implementation of Divruns approximately times faster than the fastest existing work. We also generalize the Divalgorithm to a homomorphic evaluation of an any 2-variable function.
2. Preliminaries
2.1. Notation
We write the security parameter as . We denote by the torus of real numbers modulo 1, . For any ring , polynomials of the variable X with coefficients in are denoted by . We define , , and their quotient , which are the ring of polynomials of variable X with quotient and real coefficients modulo 1. Let be a set, and we write vectors in bold. We write when is uniformly random sampled from . We denote by the uniform distribution over the set , and we denote by the process of sampling e according to the distribution .
2.2. Background of TFHE
2.2.1. Learning with Errors
The learning with errors (LWE) problem is a computational problem introduced by Regev [29]. We use the torus variant of LWE, as in [6,30]. Let , and let be a statistical distribution on . The torus LWE distribution for a fixed uniformly random secret vector is defined as follows:
The search-LWE problem is to find the secret vector from LWE samples sampled from . The decision-LWE problem is to distinguish whether samples are drawn from or .
TFHE uses a sub-Gaussian distribution for the error distribution. A distribution over such that is called -sub-Gaussian. Let Y and Z be independent random variables that are - and -sub-Gaussian, respectively. Then, for all k, , is -sub-Gaussian.
2.2.2. Bit-Wise LWEEncryption
We briefly explain bit-wise Regev’s encryption [29], which is a building block of the (bit-wise) TFHE. Let be a plaintext. The encryption scheme works as follows:
- : Let the security parameter be . Select and fix public parameters , ; then, samples a secret key and outputs it.
- : a uniformly random vector and a noise are sampled, where is the Gaussian distribution over with a standard deviation . Then, the algorithm outputs a ciphertext , where
- : The decryption algorithm returns . It outputs plaintext correctly if the size of noise e is bounded asSince , , thus .
We explain later in Section 2.4 that this scheme can be extended to integer-wise encryptions.
2.2.3. Torus LWE(TLWE)
The General-LWEproblem (GLWE) proposed by Brakerski, Gentry, and Vaikuntanathan [31] is a general problem that includes the LWE problem, and the Ring-LWE problem proposed by Lyubashevsky, Peikert, and Regev in [32]. TLWE is a torus analogue of the GLWE problem. Let k be a positive integer, N be a power of 2, and be a probability distribution over . A TLWE secret key is a vector of k polynomials over with binary coefficients, denoted as . Given a polynomial message , a “fresh” TLWE ciphertext of under the key is a TLWE sample , where and , where .
Let be a TLWE ciphertext of a polynomial message under a TLWE key . Notice that the coefficients of the TLWE sample is an LWE ciphertext of the constant term of the polynomial message . We define the function SampleExtract that simply extracts the coefficients vector of the TLWE sample, and we denote the vector of coefficients of a polynomial by . Then, we can obtain the extracted LWE ciphertext as , where , …, and is the constant term of the polynomial . This is the ciphertext encrypted with an extracted key .
As mentioned before, TLWE includes the LWE problem and the Ring-LWE problem. When is large and , TLWE is the (binary-secret) Ring-LWE. Conversely, when and k is large, TLWE is the (binary-secret) LWE. Note that, in the TFHE library [33], and by default; thus, TLWE is simply a Ring-LWE in the library, i.e., we can simple consider the TLWE samples as Ring-LWE samples in this paper.
2.2.4. TGSW
TGSW is a generalized variant of the GSW FHE scheme proposed by Gentry, Sahai, and Waters [10]. TGSW can be regarded as the matrix extension of TLWEbecause GSW is the matrix extension of LWE. Each row of a TGSW sample is a TLWE sample. As with TFHE [6], an external product ⊡ that maps can be defined. The product of the TGSW ciphertext of a polynomial message and the TLWE ciphertext of a polynomial message becomes a TLWE ciphertext of a polynomial message . We refer the readers to [6] for more details.
2.3. Overview of TFHE Bootstrapping
We refer to the bootstrapping procedure of the TFHE in [6]. We present the bootstrapping algorithm in Algorithm 1. As we mentioned before, in the default settings of the TFHE library [33], the dimension of the TLWE sample is set as . This means that the TLWE sample is simply the Ring-LWEsample . In the rest of this paper, we set : we also consider the TLWE sample to be the Ring-LWEsample .
| Algorithm 1: TFHE bootstrapping [6] for binary arithmetics. |
| Input: An LWE sample
whose plaintext , a constant , a bootstrapping key , and a keyswitching key , where . Output: An LWE sample , where . 1 , 2 , for each 3 testv 4 5 for to n do // 6 // , 7 return |
2.3.1. Input
The input for the bootstrapping is an LWE ciphertext of message binary message , , where . The noise e is sampled according to the distribution such that to satisfy the condition for correct decryption of the LWE encryption.
2.3.2. Rounding
After the rounding operation in line 2, we obtain an rounded LWE ciphertext , where
and and are rounding errors that are uniformly distributed over . Note that when the coefficients are in ; thus, we can ignore when we use the default parameter setting in the TFHE library of .
2.3.3. BlindRotate
At the line 4, is a trivial TLWE ciphertext ; thus, . After the loop in line 5, from [6] (Theorem 4.6), we have
where and are the precision parameters of the gadget decomposition, , , and is a error size ratio of the bootstrapping key BK. After the loop in line 5, the message of ACC becomes a polynomial . From (3) and , we have Notice that
where , and from (2), we obtain . Therefore, we have the following facts:
Note that, here, we used the fact that , which follows the definition .
2.3.4. Extract
The output of SampleExtract in line 6 is simply the coefficients vector of the TLWE sample over the torus , where is a coefficient vector of and is a constant term of the polynomial . The message of the extracted sample is the constant term of the polynomial . The message is if and if . Therefore,
i.e., . The size of the error of remains since SampleExtract adds no extra noise.
2.3.5. KeySwitch
The output of KeySwitchin line 7 is a TLWE sample of a message , with the secret key . We write this TLWE ciphertext as for simplicity of the notation. The KeySwitchprocedure is the same as that in [6]. We refer to KeySwitch in Algorithm 2 for completeness of this paper. The keyswitching key is defined as , where for and . Here, is a parameter that decides the size of the noise of the key switching key, which satisfies , and is a parameter that decides the precision. From [6] (Lemma 4.3), we obtain
Therefore, we have the bound on the size of the noise as follows:
where the second inequality follows from (4). The bootstrapping outputs a “fresh” LWE ciphertext when the parameters satisfy the following:
| Algorithm 2: KeySwitch. |
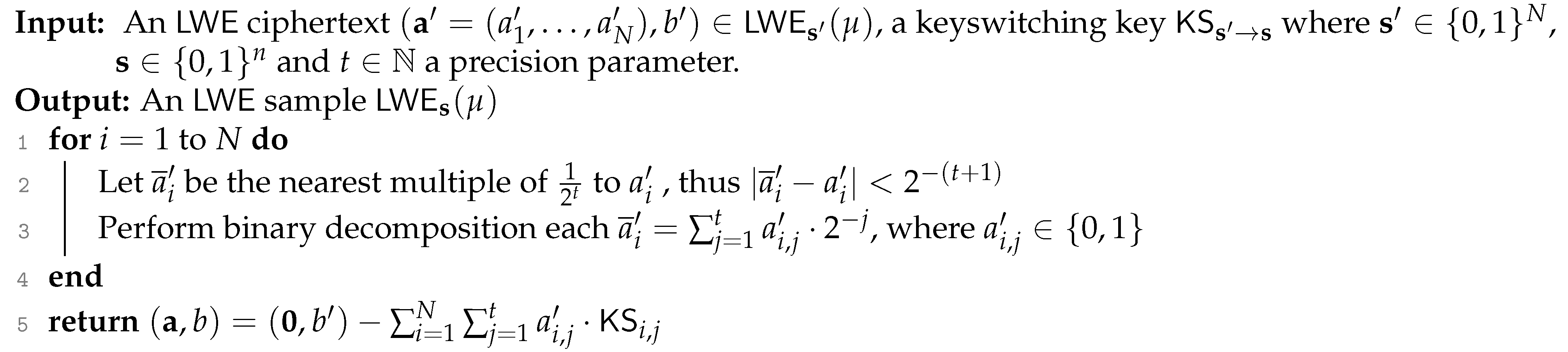 |
This upper bound follows from (2).
2.4. Integer-Wise LWE Encryption
We use a integer-extended variant of Regev’s encryption following the scheme proposed by Bourse et al. in [14]. Let , the message . The integer-wise LWE encryption works as follows:
- : On a input security parameter , and are fixed; a secret key is output.
- : A uniformly random vector and a noise are sampled, where is a Gaussian distribution over with a standard deviation . A ciphertext is output, where
- : The decryption algorithm returns . The decryption works correctly if the size noise is small enough, i.e.,Since and holds from (7).
3. Integer-Wise General Functional Bootstrapping
We modify TFHE to a variant that can encrypt the plaintext of an integer and perform any 1-variable function in only one bootstrapping. We highlight this section as follows:
- We present our general bootstrapping in Algorithm 3 of Section 3.1, which is built upon the integer-wise LWE encryption Section 2.4.
- Our key technique to construct the general bootstrapping is generalizing the setting of the coefficients of the test vector, which is used in the BlindRotate part of the bootstrapping procedure, in Algorithm 4.
- We also discuss the possible security issue that arose after our modification in Section 3.2.
3.1. General Functional Bootstrapping
We present our bootstrapping scheme in Algorithm 3. Our bootstrapping is different from that of Chillotti et al.’s Algorithm 1 in the setting of the test vector used in the BlindRotatepart. Our bootstrapping procedure is constructed over the integer-wise LWE encryption described in Section 2.4, where homomorphic evaluation is performed in an integer-wise manner. We summarize in Table 1 how the input ciphertext is converted line by line for clarity.

Table 1.
Overview of the bootstrapping scheme.
| Algorithm 3: General functional bootstrapping. |
| Input: A ciphertext An LWE sample , such that its plaintext , a bootstrapping key , a keyswitching key , where , a constant function , and a set of coefficients of the test vector that. corresponds to the function f Output: An LWE sample , where 1 , for each 2 Set the test vector as 3 4 for to n do 5 6 return |
3.1.1. Input
The input for our bootstrapping scheme is an LWE ciphertext of an integer message , where . The noise e is sampled according to the distribution such that (7) holds to satisfy the condition for correct decryption of the LWE encryption.
3.1.2. Rounding (Line 1)
The output of the rounding is an rounded LWE ciphertext . Similar to (3), we have
Concretely, we obtain when , as we mentioned in Section 2.3.
3.1.3. BlindRotate (Line 3 to Line 4)
At line 3, the is a trivial (noiseless) TLWE sample . After the iteration in line 4, the message of ACC becomes a polynomial . Since and from (10), we have . Thus, we obtain from (7) that
Note that we define the test vector in general form , which is the core modification of our scheme. In the following, we explain how to set the value of the coefficients for a homomorphic evaluation of the arbitrary input function f in one bootstrapping. We summarize the setting in Algorithm 4 and show its illustration in Figure 1.
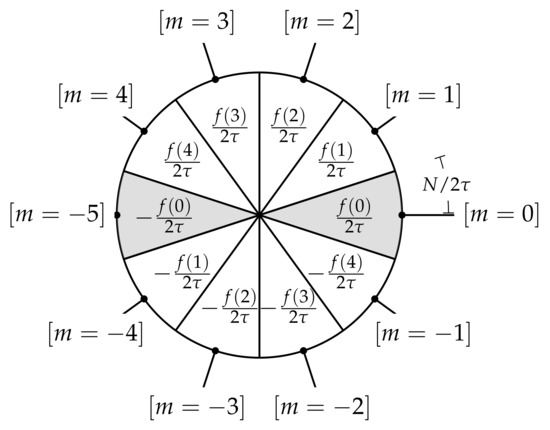
Figure 1.
Illustration of the “slices” for the integer-wise LWEencryption and bootstrapping procedure when .
- When , we have and . Thus, the constant term of the polynomialis inWe define the value of all elements as . Note that, since , we now have or, equivalently, . Similar to this case, when , the constant term of the polynomial is in , …, , , , …, . The elements of this set are the sign inversions of the elements of the set . Therefore, are already defined as .
- When , we have . From (11), we have < << < N. Thus, we obtain and the constant term of the polynomial is inWe define the value of all as . Similarly, when , we have < < < < . Thus, ,…, , and the constant term of the polynomial is in , …, . These values are the sign inversions of the previously defined for .
| Algorithm 4: Our setting of the test vector coefficients defined in (9). |
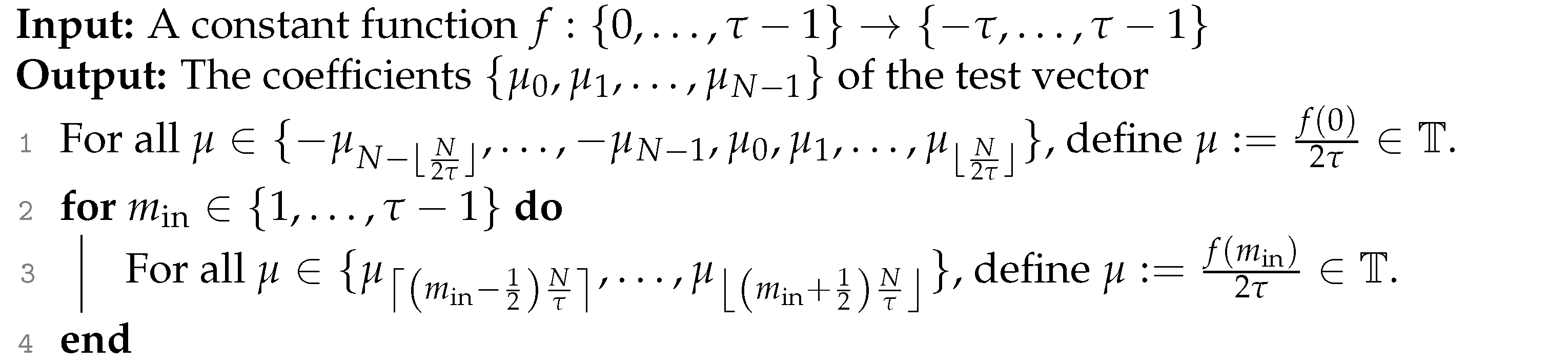 |
3.1.4. Extract (Line 5)
The message of the output in line 5, denoted as , is the constant term of (). By our construction of BlindRotate, it is the coefficient , where is defined in (8).
3.1.5. KeySwitch (Line 7)
Our scheme uses the same KeySwitchprocedure as the original TFHE, which is mentioned in Section 2.3.5. The output of line 6 is a TLWE sample denoted as . The sample is the encryption of the message with the secret key . We denote this TLWE ciphertext as for simplicity of the notation. Only the difference from the original bit-wise TFHE is the upper bound of (5): From (7), we need to choose the parameters that satisfy the upper bound
so that we can obtain a “fresh” LWE sample after the bootstrapping with overwhelming probability.
3.2. Security
The security of our scheme largely relies on the original TFHE scheme because we only modify the test vector, and it changes only the bound of the size of noise given in (12). Although the noise bound of TFHE is fixed to , as in (5), that of our scheme is . Therefore, when we use the larger plaintext space, the bound becomes lower. This means that we need to use the TLWE sample with smaller noise if the bound (12) does not hold. Conversely, we select the security parameters and that satisfy (12); then, the security of our scheme relies solely on the original TFHE scheme. We use the same security parameters and noise as those in the original TFHE scheme and choose a value of that satisfies (12) in our experiments in Section 5. Notably, the bound in (12) is independent of the input function f; therefore, our scheme can run arbitrary functions with the same parameters and running time.
4. Applications
We present several basic applications of our integer-wise general TFHE bootstrapping procedure (Algorithm 3):
- : Homomorphic evaluation of the sign function over a ciphertext (Algorithm 5)
- : Homomorphic evaluation of the equality test (Algorithm 6)
- : Homomorphic evaluation of the equality test with a plaintext (Algorithm 7)
- : Homomorphic evaluation of multiplication by a binary number (Algorithm 8)
- : Homomorphic evaluation of division by a plaintext (Algorithm 9)
- : Homomorphic evaluation of division (Algorithm 10)
The function , which is the homomorphic algorithm of sign, was already presented by Bourse et al. in [14]. For clarity, we describe performed in our scheme to show that our general Bootstrapping schemes includes the sign function. Additionally, the integer-wise TFHE proposed by Bourse et al. [14] can evaluate only bootstrapping; it does not support the homomorphic multiplication of integer ciphertexts.
We show Eqand ConstEqin Section 4.2, MultbyBinin Section 4.3, and DivbyConstin Section 4.4. We propose Divin Section 4.5 using DivbyConst, ConstEq, and MultbyBinas building blocks. We also generalize the Divfunction to the homomorphic algorithm that evaluates any 2-variable function in Section 4.5.
| Algorithm 5:: Homomorphic sign evaluation in our bootstrapping scheme. |
| Input: A ciphertext , where . Output: , where 1 return , where if , 0 if . |
| Algorithm 6:: Equality test. |
| Input: Two ciphertexts and , where . Output: , where 1 return , where if , otherwise. |
| Algorithm 7:: Equality test with a constant |
| Input: A ciphertext and plaintext , where . Output: , where 1 Encode to . 2 return , where if , otherwise. |
4.1. Homomorphic Evaluation of the Sign Function:
Algorithm 5 shows that our algorithms homomorphically evaluate the sign function. This algorithm is constructed using Bootstrap with an input function . Specifically, we “express” by defining the coefficients of test vector using Algorithm 4, as follows:
We illustrate the setting of the test vector coefficients in Figure 2. We can confirm from (8) that for , for , for , and for . Note that the plaintext of the output with is the same as that with .
| Algorithm 8:: Homomorphic multiplication by binary number |
| Input: Ciphertexts , where , . Output: 1 // 2 return // |
| Algorithm 9:: Homomorphic division by a constant |
| Input: A ciphertext , where , and a constant plaintext . Output: 1 return |
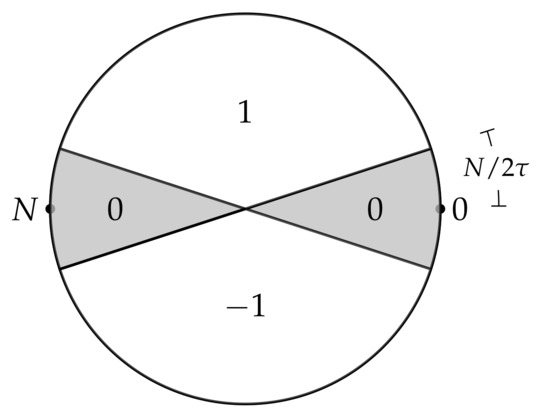
Figure 2.
Illustration of the slices for the test vector coefficients of sign bootstrapping (when ).
| Algorithm 10:: Homomorphic division. |
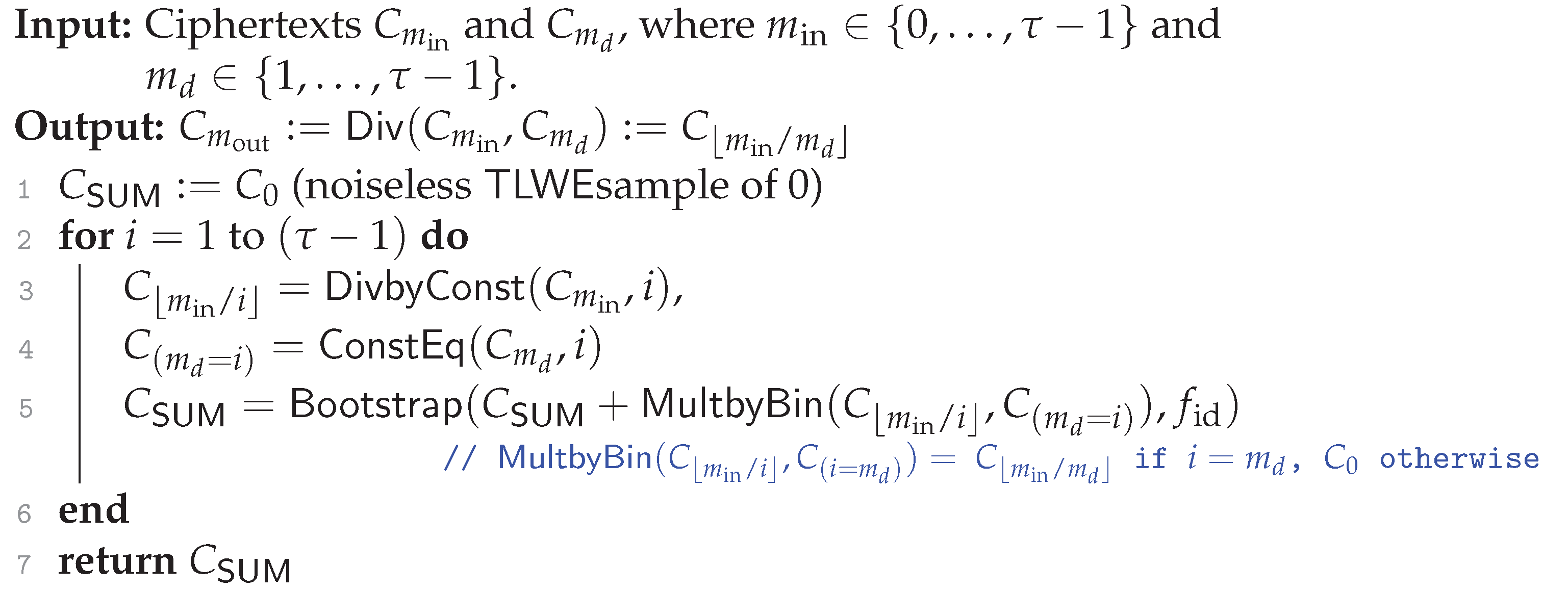 |
4.2. Homomorphic Equality Test: and
For clarity, we present that our bootstrapping scheme includes the homomorphic equality test. This concept is similar to the homomorphic comparison on TFHE proposed by Bourse et al. in [34]. Note that we require the input plaintext space to be in (or in ), for our equality tests Algorithms 6 and 7. This restriction is required since, if we allowed and to be in , we would have and would obtain the trueoutput when , although .
Some previous integer-wise homomorphic equality tests were performed based on Fermat’s little theorem [35] in other FHE schemes, such as HElib. For example, in HElib (i.e., in the BGV FHE scheme [31]), the plaintext space was for some prime number modulus p, and the equality test was constructed using the fact
However, this approach is not efficient because it calls for homomorphic multiplication many () times, and thus, some additional bootstrapping are required in order to reduce the increase in noise caused by the homomorphic multiplication. Our homomorphic equality test is efficient because it calls only one bootstrapping procedure.
Algorithm 6 shows , the equality test between two ciphertexts. The algorithm is based on the integer-wise “zero test” bootstrapping with the function , where if , 0 otherwise. Concretely, we define the test vector coefficients that correspond to , based on Algorithm 4, as follows:
We show the illustration of the setting of the coefficients of the test vector in Figure 3.
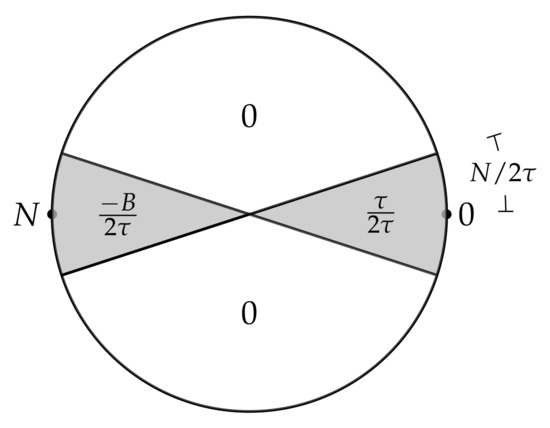
Figure 3.
Illustration of the slices for the test vector coefficients of equality test bootstrapping (when ).
Algorithm 7 shows the variant that is performed between a ciphertext and a plaintext. Notice that the second argument of the algorithm is a plaintext , which is then encoded as a trivial LWE ciphertext in line 1.
4.3. Homomorphic Multiplication by a Binary Number:
Algorithm 8 shows the algorithm used to homomorphically evaluate the multiplication by a binary number (MultbyBin). As mentioned before, integer-wise TFHE cannot perform homomorphic multiplication between integer ciphertexts. MultbyBinhomomorphically multiplies an integer ciphertext by a ciphertext of a binary message. MultbyBinis called as a module in the homomorphic division Div, which we describe later in Algorithm 10. Figure 4 illustrates how the MultbyBinworks. Note that we need restrictions for MultbyBin: (1) to be an odd number and (2) . We explained these restrictions later in this subsection.
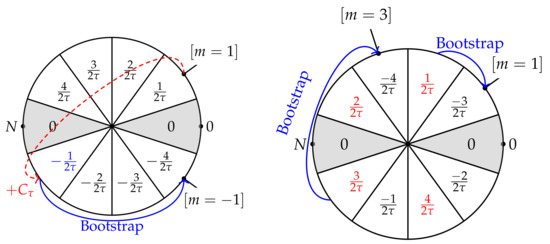
Figure 4.
Illustration of MultbyBinwhen . The left figure illustrates the procedure in line 1, and the right figure illustrates the procedure in line 2.
We define two functions and to be used as inputs of Bootstrapto construct MultbyBin. The function is an identity function defined as . Based on Algorithm 4, we define the test vector coefficients for as follows:
The function is defined as
For , we define the test vector coefficients based on Algorithm 4, as follows:
We now explain Algorithm 8. First, in line 1, we homomorphically multiply a ciphertext of a binary message in , and a constant to . The output of the bootstrapping of the sum with is stored as .
- If is a ciphertext of 0 (which means ), then is (ciphertext of the constant ). Thus, the phase of is rotated to a position symmetrical about the origin, as illustrated in Figure 4 by the dashed arrow in the left image. Then, the phase of the ciphertext is rotated to a position symmetrical about the x-axis. After bootstrapping with , becomes a ciphertext of .
- If is a ciphertext of (which means ), then is (ciphertext of 0). Thus, remains a ciphertext of .
Therefore, in line 2, when , and when . After bootstrapping with , is converted to , and remains , as illustrated in Figure 4. Finally, we obtain when and when .
As noted before, we need to restrict to odd values. If is even, when and , the ciphertext in line 2 is converted to , but we require it to remain as . Therefore, needs to be an odd number to homomorphically evaluate the division by 2 with the function . Additionally, we require the input to be in because we cannot perform multiplication with binary values on negative plaintext with MultbyBin. (Although we can perform binary multiplication on or , which is equivalent to , we omit from the input plaintext space, for simplicity.) For ,
- if (which means ), the message of in line 1 is , and the output becomes because for all while .
- If (which means ), in line 1, the message of is and the output is .
Therefore, for negative inputs , does not work as multiplication with binary values; thus, we need the restriction.
4.4. Homomorphic Division by a Constant:
Algorithm 9 shows that DivbyConsthomomorphically evaluates “division by a constant”. DivbyConsttakes a ciphertext and a plaintext as inputs, and it outputs a ciphertext of . Note that we need to restrict and .
Bit-wise integer division by 2 on TFHE was proposed in [7]. The algorithm was constructed based on a right shift over the bits; therefore, it only supports a power of two dividend. Homomorphic division by a (not only 2) constant was proposed in [23] based on HElib. This algorithm uses polynomial interpolation, which needs to homomorphically calculate all powers of the ciphertexts , where p is the modulus of the plaintext space . Thus, it is not efficient since many () homomorphic multiplications are needed for a homomorphic polynomial interpolation. Contrary to that, our homomorphic division by a constant on the integer-wise TFHE is efficient because it needs only one bootstrapping.
The function is defined as for a constant . We define the test vector coefficients for based on Algorithm 4, as follows:
Note that we need to have a set of for all : we need to store values in before starting the algorithm. Additionally, we need the restriction since we cannot perform divisions for , as the output becomes .
4.5. Homomorphic Division:
As a final application, we construct a homomorphic division Divin Algorithm 10. It calls DivbyConst, ConstEq, and MultbyBinas subalgorithms. As these subalgorithms need the restriction , Divalso follows this restriction.
We now explain Div. First, in line 1, we set a as a trivial TLWE ciphertext of a message 0. In the iteration on line 2 and 6, we obtain a ciphertext of , denoted as with DivbyConst, and then, we test if with ConstEq, where d is the plaintext of the input . The output is the ciphertext of the Boolean value of the test result . Second, in line 5, we have
Therefore, after this loop, we have .
Generalization to a Two-Variable Function:
We now generalize Divto any two-variable function , in Algorithm 11. The algorithm takes the following inputs: two ciphertexts and ; a two-variable function ; and sets of test vector coefficients , which corresponds to a one-variable function for all fixed . The output of the algorithm is a ciphertext . This algorithm generalizes Divby generalizing the DivbyConstto , which is the homomorphic evaluation of a general one-variable function over a ciphertext .
5. Results of Homomorphic Division
In this section, we present the implementation results of Div. We implemented our bootstrapping procedure and Divby modifying the TFHE library [33]. The parameter values are the same as the defaults of the TFHE library:
- The degree of the polynomials in the ring: .
- The dimensions of the LWE and TLWE: and .
- Decomposition basis and length of TGSWciphertexts: and .
- Decomposition basis and length of KeySwitch: and .
- Standard deviation of the noise of the key-switching keys KS: .
- Standard deviation of the noise of the bootstrapping keys BK: .
These choices of parameters achieve at least 128-bit security [6]. A single bootstrapping procedure takes approximately 10 msec on our PC with a -GHz Intel Core i5 CPU. We implemented Divfor a 4-bit integer, which is the same target as that of existing work on homomorphic division algorithms [16,17,18,23]. Thus, we set to encrypt 4-bit integers.
Table 2 shows our results, including the values taken from the existing works on homomorphic division. We ran Div (Algorithm 10) 1000 times and took the average. Our method is approximately times faster than the fastest method ([23]) shown in the table while achieving a higher level of security () than that of existing methods. For a fair comparison, we also implemented the “non-restorative division algorithm” on the original (bit-wise) TFHE library with the same parameters. The non-restorative division algorithm is a classic bit-wise algorithm for integer division that is used in previous works [16,17,18]. We can confirm from Table 2 that our method is approximately times faster than non-restorative division. In the asymptotic analysis, as shown in the “Complexity” column of the table, our division algorithm and that of [23] take exponential time. Thus, our algorithm and that of [23] are asymptotically slower than other works based on the bit-wise non-restorative division algorithm. The main bottle necks of our algorithm and that in [23] are the exhaustive loop of line 2–6 in Algorithm 10, similar to the part in [23]. However, while the method of [23] needs an calculation, our algorithm is quadratically faster: it takes a smaller calculation. This is due to that our bootstrapping being able to evaluate any one-variable function without extra computational costs over the original TFHE, and in contrast, the bootstrapping in [23] needs an calculation for homomorphic evaluation of the general one-variable function.

Table 2.
Results: comparison with existing homomorphic division implementations. We abbreviate the non-restoring division method as NRD. The “Complexity” column shows the asymptotic complexity for a one-bit-length integer input.
| Algorithm 11:: Homomorphic evaluation of a 2-variable function |
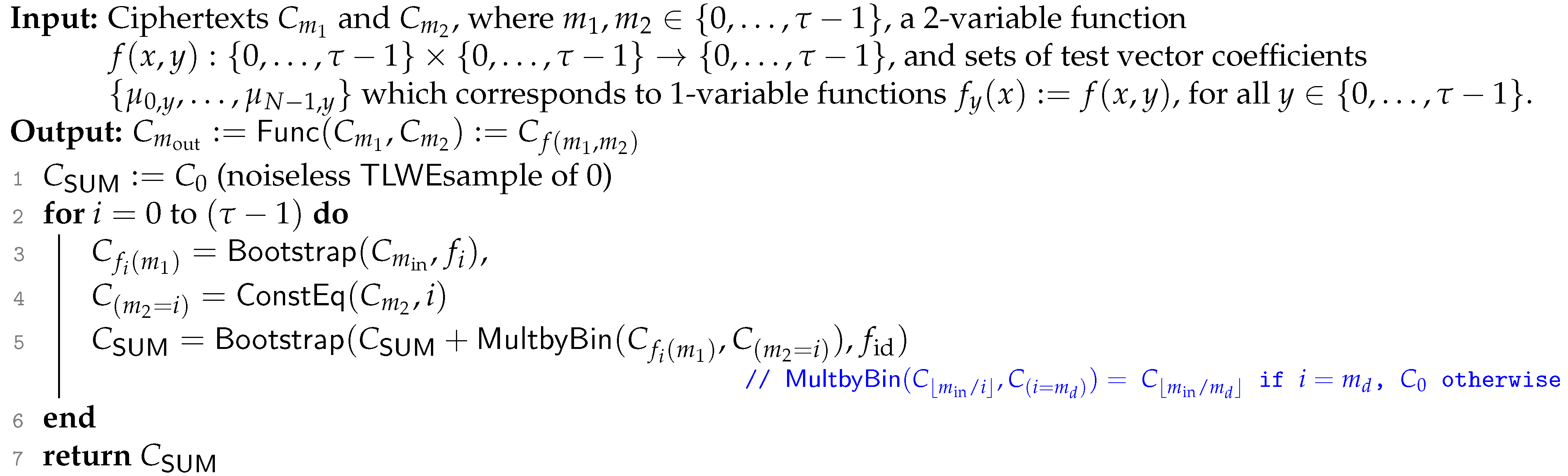 |
We show in Table 3 the breakdown of the run time of our Div, which was completed in 930 msec in total. The run time for each of MultbyBin, ConstEq, DivbyConst, and in line 5 of Algorithm 10 are shown in the table. The run times of these subalgorithms account for almost the entire run time. As the single bootstrapping takes approximately 10 msec on our PC, the cost of these functions is dominated by the run time of bootstrapping, i.e., our functions entail minimal additional costs.

Table 3.
A breakdown of the run time of our Div (Algorithm 10).
Limitations of Correctness
In the parameter setting of this section, the final standard deviation of the noise after bootstrapping is , as in [6]. The probability of decryption failure, i.e., the probability of the standard deviation of noise after bootstrapping is larger than and is bounded by . The condition suffices for the bit-wise TFHE scheme. However, for our scheme, decryption fails if the size of the noise after bootstrapping is larger than , as shown in (12). The probability of decryption error is bounded by for our scheme. This upper bound appears large, but we empirically observed in our experiment that the decryption error rate is approximately (4 decryption errors in 5000 bootstrappings). In other words, there is a trade-off between the size of the plaintext space and the decryption error rate. For 5-bit integers, i.e., when , the upper bound of the decryption failure probability rapidly increases to approximately . Thus, for the parameter setting in this section, our scheme is practical only for -bit integer input. Notably, although the decryption failure rate of our scheme increases as increases, the security of the scheme is not affected because is independent of the standard deviation of the noise [14].
6. Conclusions
We proposed a technique for performing arbitrary 1-variable functions with only one bootstrapping procedure using the integer-wise variant of TFHE. The core modification is to generalize the test vector used in the bootstrapping and the concrete setting of the values of the test vector coefficients. Based on this general functional bootstrapping procedure, we extended the functionality of the integer-wise TFHE scheme to construct several basic applications, such as homomorphic equality testing, multiplication by a binary number, and a division algorithm. We implemented our homomorphic division algorithm and showed that it can be performed in less than 1 second, which is approximately times faster than the fastest division algorithm. However, as a limitation, our scheme is practical only for ≤4-bit integer inputs, when we use the default parameters of TFHE library. In order to use our scheme for larger integer inputs, we need to use a smaller error rate.
Efficient algorithms for basic arithmetic operations are needed to increase the options for optimizing high-level secure computation applications. We believe our bootstrapping scheme can be used to develop a wide variety of homomorphic calculation algorithms.
Author Contributions
Conceptualization, H.O.; methodology, H.O.; software, H.O.; validation, H.O.; formal analysis, H.O.; writing—original draft preparation, H.O.; writing—review and editing, H.O. and S.K.; visualization, H.O.; supervision, S.K. and C.C.; All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Acknowledgments
We thank Benjamin Curtis and Rachel Player for their comments on the preliminary version of this paper [36].
Conflicts of Interest
The authors declare no conflict of interest.
References
- Gentry, C. A Fully Homomorphic Encryption Scheme. Ph.D. Thesis, Stanford University, Stanford, CA, USA, 2009. [Google Scholar]
- Gentry, C. Fully Homomorphic Encryption Using Ideal Lattices. In STOC 2009; ACM: New York, NY, USA, 2009; pp. 169–178. [Google Scholar] [CrossRef] [Green Version]
- Brakerski, Z.; Vaikuntanathan, V. Efficient Fully Homomorphic Encryption from (Standard) LWE. In FOCS 2011; IEEE: Piscataway, NJ, USA, 2011; pp. 97–106. [Google Scholar] [CrossRef] [Green Version]
- Brakerski, Z.; Vaikuntanathan, V. Fully Homomorphic Encryption from Ring-LWE and Security for Key Dependent Messages. In CRYPTO 2011; Rogaway, P., Ed.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 505–524. [Google Scholar] [CrossRef] [Green Version]
- Brakerski, Z.; Vaikuntanathan, V. Lattice-based FHE As Secure As PKE. In ITCS 2014; ACM: New York, NY, USA, 2014; pp. 1–12. [Google Scholar] [CrossRef] [Green Version]
- Chillotti, I.; Gama, N.; Georgieva, M.; Izabachène, M. Faster Fully Homomorphic Encryption: Bootstrapping in Less Than 0.1 Seconds. In ASIACRYPT 2016; Cheon, J.H., Takagi, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 3–33. [Google Scholar] [CrossRef]
- Chillotti, I.; Gama, N.; Georgieva, M.; Izabachène, M. Faster Packed Homomorphic Operations and Efficient Circuit Bootstrapping for TFHE. In ASIACRYPT 2017; Takagi, T., Peyrin, T., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 377–408. [Google Scholar] [CrossRef]
- Chillotti, I.; Gama, N.; Georgieva, M.; Izabachène, M. TFHE: Fast Fully Homomorphic Encryption Over the Torus. J. Cryptol. 2020, 33, 34–91. [Google Scholar] [CrossRef]
- Gentry, C.; Halevi, S.; Smart, N.P. Homomorphic Evaluation of the AES Circuit. In CRYPTO 2012; Safavi-Naini, R., Canetti, R., Eds.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 850–867. [Google Scholar] [CrossRef] [Green Version]
- Gentry, C.; Sahai, A.; Waters, B. Homomorphic Encryption from Learning with Errors: Conceptually-Simpler, Asymptotically-Faster, Attribute-Based. In CRYPTO 2013; Canetti, R., Garay, J.A., Eds.; Springer: Berlin/Heidelberg, Germany, 2013; pp. 75–92. [Google Scholar] [CrossRef] [Green Version]
- Smart, N.P.; Vercauteren, F. Fully Homomorphic Encryption with Relatively Small Key and Ciphertext Sizes. In PKC 2010; Nguyen, P.Q., Pointcheval, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 420–443. [Google Scholar] [CrossRef] [Green Version]
- Stehlé, D.; Steinfeld, R. Faster Fully Homomorphic Encryption. In ASIACRYPT 2010; Abe, M., Ed.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 377–394. [Google Scholar] [CrossRef] [Green Version]
- van Dijk, M.; Gentry, C.; Halevi, S.; Vaikuntanathan, V. Fully Homomorphic Encryption over the Integers. In EUROCRYPT 2010; Gilbert, H., Ed.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 24–43. [Google Scholar] [CrossRef] [Green Version]
- Bourse, F.; Minelli, M.; Minihold, M.; Paillier, P. Fast Homomorphic Evaluation of Deep Discretized Neural Networks. In CRYPTO 2018; Shacham, H., Boldyreva, A., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 483–512. [Google Scholar] [CrossRef] [Green Version]
- Gilad-Bachrach, R.; Dowlin, N.; Laine, K.; Lauter, K.; Naehrig, M.; Wernsing, J. CryptoNets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy. In Proceedings of the 33rd International Conference on Machine Learning, New York, NY, USA, 19–24 June 2016; Volume 48, pp. 201–210. [Google Scholar] [CrossRef]
- Chen, J.; Feng, Y.; Liu, Y.; Wu, W. Faster Binary Arithmetic Operations on Encrypted Integers. In WCSE 2017; SCIEI: Hong Kong, China, 2017; pp. 956–960. [Google Scholar] [CrossRef]
- Chen, Y.; Gong, G. Integer arithmetic over ciphertext and homomorphic data aggregation. In Proceedings of the IEEE Conference on Communications and Network Security (CNS), Florence, Italy, 28–30 September 2015; pp. 628–632. [Google Scholar] [CrossRef]
- Xu, C.; Chen, J.; Wu, W.; Feng, Y. Homomorphically Encrypted Arithmetic Operations Over the Integer Ring. In ISPEC 2016; Bao, F., Chen, L., Deng, R.H., Wang, G., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 167–181. [Google Scholar] [CrossRef]
- Çetin, G.S.; Doröz, Y.; Sunar, B.; Savaş, E. Depth Optimized Efficient Homomorphic Sorting. In LATINCRYPT 2015; Lauter, K., Rodríguez-Henríquez, F., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 61–80. [Google Scholar] [CrossRef] [Green Version]
- Bost, R.; Popa, R.A.; Tu, S.; Goldwasser, S. Machine Learning Classification over Encrypted Data. In Proceedings of the Network and Distributed System Security (NDSS) Symposium, San Diego, CA, USA, 8–11 February 2015. [Google Scholar] [CrossRef] [Green Version]
- Juvekar, C.; Vaikuntanathan, V.; Chandrakasan, A. GAZELLE: A Low Latency Framework for Secure Neural Network Inference. In USENIX Security 2018; USENIX Association: Baltimore, MD, USA, 2018; pp. 1651–1669. [Google Scholar]
- Narumanchi, H.; Goyal, D.; Emmadi, N.; Gauravaram, P. Performance Analysis of Sorting of FHE Data: Integer-Wise Comparison. In AINA 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 902–908. [Google Scholar] [CrossRef]
- Okada, H.; Cid, C.; Hidano, S.; Kiyomoto, S. Linear Depth Integer-Wise Homomorphic Division. In WISTP 2018; Blazy, O., Yeun, C.Y., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 91–106. [Google Scholar] [CrossRef]
- Halevi, S.; Shoup, V. HElib—An Implementation of Homomorphic Encryption. 2019. Available online: https://github.com/shaih/HElib/ (accessed on 26 July 2020).
- Cheon, J.H.; Han, K.; Kim, A.; Kim, M.; Song, Y. Bootstrapping for Approximate Homomorphic Encryption. In EUROCRYPT 2018; Nielsen, J.B., Rijmen, V., Eds.; Springer International Publishing: Cham, Switzerland, 2018; pp. 360–384. [Google Scholar] [CrossRef]
- New Jersey Institute of Technology. PALISADE. 2019. Available online: https://git.njit.edu/palisade/PALISADE (accessed on 26 July 2020).
- Chen, H.; Dai, W.; Kannepalli, S.; Khanpour, H.; Laine, K.; Lauter, K.; Singh, T.; Song, Y.; Tieman, J. Microsoft SEAL: Fast and Easy-to-Use Homomorphic Encryption Library. 2019. Available online: https://www.microsoft.com/en-us/research/project/microsoftseal/ (accessed on 26 July 2020).
- Ducas, L.; Micciancio, D. FHEW: Bootstrapping Homomorphic Encryption in Less Than a Second. In EUROCRYPT 2015; Oswald, E., Fischlin, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 617–640. [Google Scholar] [CrossRef] [Green Version]
- Regev, O. On Lattices, Learning with Errors, Random Linear Codes, and Cryptography. In STOC ’05; ACM: New York, NY, USA, 2005; pp. 84–93. [Google Scholar] [CrossRef]
- Cheon, J.H.; Stehlé, D. Fully Homomophic Encryption over the Integers Revisited. In EUROCRYPT 2015; Oswald, E., Fischlin, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2015; pp. 513–536. [Google Scholar] [CrossRef] [Green Version]
- Brakerski, Z.; Gentry, C.; Vaikuntanathan, V. (Leveled) Fully Homomorphic EncryptionWithout Bootstrapping. In ITCS 2012; ACM: New York, NY, USA, 2012; pp. 309–325. [Google Scholar] [CrossRef] [Green Version]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On Ideal Lattices and Learning with Errors over Rings. In EUROCRYPT 2010; Gilbert, H., Ed.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 1–23. [Google Scholar] [CrossRef]
- Carpov, S.; Chillotti, I.; Gama, N.; Georgieva, M.; Izabachene, M. TFHE: Fast Fully Homomorphic Encryption over the Torus. 2019. Available online: https://tfhe.github.io/tfhe/ (accessed on 26 July 2020).
- Bourse, F.; Sanders, O.; Traoré, J. Improved Secure Integer Comparison via Homomorphic Encryption. In EUROCRYPT 2020; Jarecki, S., Ed.; Springer International Publishing: Cham, Switzerland, 2020; pp. 391–416. [Google Scholar] [CrossRef]
- Çetin, G.S.; Doröz, Y.; Sunar, B.; Martin, W.J.; Arithmetic Using Word-wise Homomorphic Encryption. Cryptology ePrint Archive, Report 2015/1195. 2015. Available online: https://eprint.iacr.org/2015/1195 (accessed on 26 July 2020).
- Okada, H.; Kiyomoto, S.; Cid, C. Integerwise Functional Bootstrapping on TFHE. In Information Security; Susilo, W., Deng, R.H., Guo, F., Li, Y., Intan, R., Eds.; Springer International Publishing: Cham, Switzerland, 2020; pp. 107–125. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).