Design of an Architecture Contributing to the Protection and Privacy of the Data Associated with the Electronic Health Record
Abstract
:1. Introduction
- Constructing an architectural design process that solves the problems proposed by creating the EHR in Colombia by obtaining and analyzing the architectural drivers to formalize the essential requirements.
- Proposal of Blockchain’s use to solve the most crucial quality attributes (QAs) identified through an in-depth systematic literature review.
- Detailed comparison process of different platforms and reference frameworks to select the most appropriate technology stack to instantiate or implement the proposed architectural model, allowing EHR’s exchange in the Colombian context.
- We developed a Poc that demonstrates the resolution of one of the essential attributes of the proposed architecture: Security, by evaluating its robustness against some common attacks within this type of network.
2. Background and Related Work
2.1. Electronic Medical Record in Colombia
2.2. Software Architecture
2.2.1. Architecturally Significant Requirements
2.2.2. Quality Attribute (QA)
2.2.3. Quality Attribute Scenarios
2.2.4. Attribute Driven Design—ADD
2.3. Blockchain
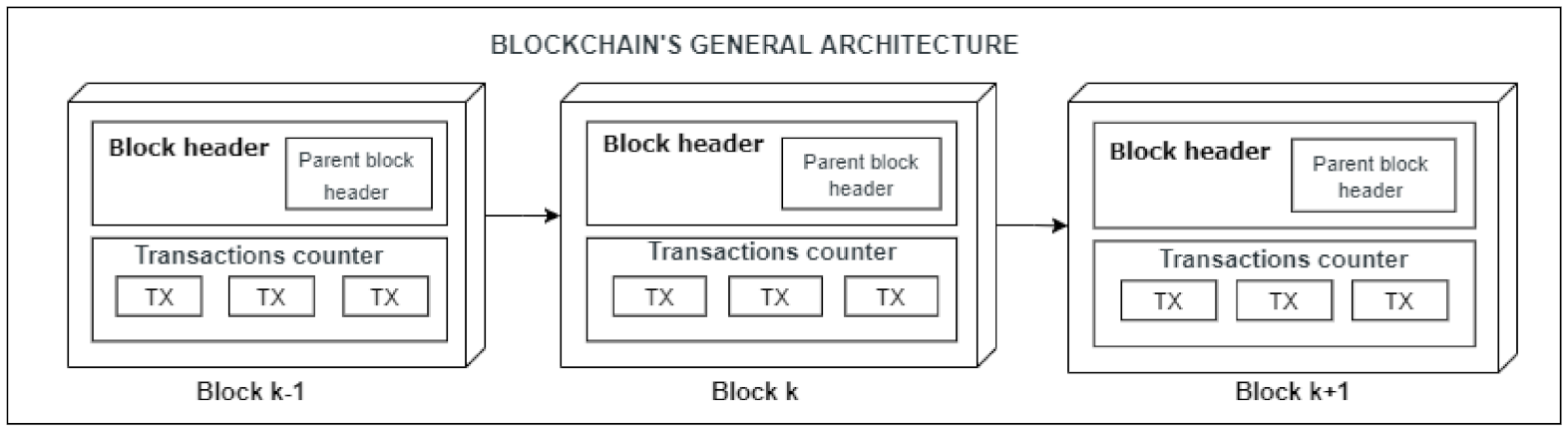
2.4. Blockchain Structure
2.5. Public vs. Private Blockchain
2.6. Hyperledger Fabric
2.6.1. Hyperledger Fabric Architecture
- Consensus manager, responsible for providing the interface to the consensus protocol and receiving transactions and executing them according to the chosen consensus algorithm.
- Distributed ledger, a database used by Smart Contracts to store relevant state information during transaction execution.
- A peer-to-peer protocol.
- Ledger storage
2.6.2. Consensus in Hyperledger Fabric
- Endorsement: It is oriented by a policy where only certain participants take the role of endorsing a transaction.
- Ordering: The ordering phase is in charge of accepting transactions that were previously accepted in the endorsement step. Additionally, an order is agreed upon to confirm transactions in the distributed ledger and delivers the resulting blocks to the committing peers.
- Validation: Obtains a block of ordered transactions and validates the certainty of the results, including verification of the approval policy and ensuring that there is no double-spending.
2.6.3. Nodes in the Fabric Network and Their Roles
- Clients: They are applications in charge of executing transactions in the system by sending them to the endorsing peers or computers.
- Committing peers: This phase is in charge of persisting the chains transmitted in the channels (committing them) in addition to maintaining the general ledger and its status. May have a smart contract (Chaincode).
- Endorsing peers: This phase is responsible for collecting transactions (transaction proposal) from customers and analyzing them using Smart Contracts to enforce their associated rules (endorsing them), e.g., verifying whether an entity is allowed to execute a specific action on the ledger and then signing them.
- Peers or Computing Services: This phase is responsible for approving the inclusion of transaction blocks in the ledger and communicating with peer nodes that commit and endorse to ensure that the ledger is consistent.
- Authentication Authorities: Responsible for ensuring the veracity or authenticity of the identity of users or components, in addition to authenticating users so that they can execute transactions.
2.6.4. Types of Ordering Services
- Solo: Type of service suitable for testing as it does not have fail-safe functionalities such as that of Byzantine Generals failures. It is recommended for moderately reliable environments.
- Kafka-based: Ordering service recommended for productive releases in Fabric versions before 1.4.2 uses Apache Kafka components.
- RAFT Emerged from version 1.4.2. It has Byzantine Fault Tolerance (PBFT). It is recommended for unreliable environments.
2.7. Related Works
2.7.1. Benefits of Blockchain in Healthcare Software Architecture
- Improved management in medical records, within which are solutions for secure storage of patient medical records, secure and scalable clinical data exchange, privacy risk management assistance, and EHR’s security or privacy.
- Insurance claims process improvement applications
- Applications that accelerate biomedical research
- Applications that aid in healthcare through Ledgers
2.7.2. Best Suited Blockchain Type in Healthcare
2.7.3. Public or Private Blockchain?
- In a public blockchain, users’ anonymity and inability to verify account owners’ identity could cause data misuse, whereas in a private blockchain, a user or entity must be authenticated or authorized before joining the system.
- Privacy of patient data.
- Fast system response (Throughput).
2.7.4. Best Suited Blockchain Architectures for Clinical Informatics
2.8. Our Proposal’s Features
3. System Architectural Design
3.1. Architectural Drivers
3.1.1. Quality Attributes
3.1.2. Utility Tree
3.1.3. Quality Attribute Scenarios
3.2. System Architecture Design Process
3.2.1. Step 1—Review of Inputs to the Design Process
3.2.2. Iteration 1: Establish an Overall System Structure
3.2.3. Construction
4. The Proposed System—Iteration 2
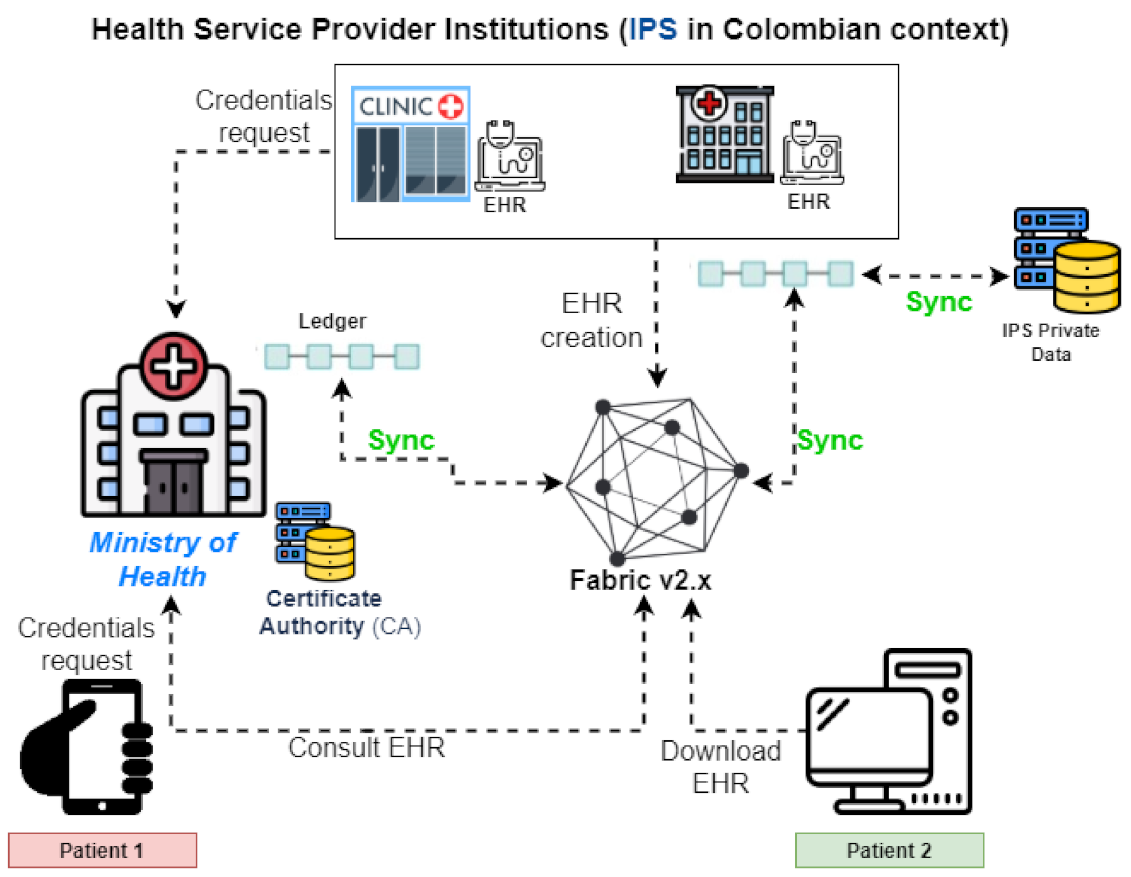
System Architecture
- Store medical history information in the ledger.
- Query the medical history information.
5. Results
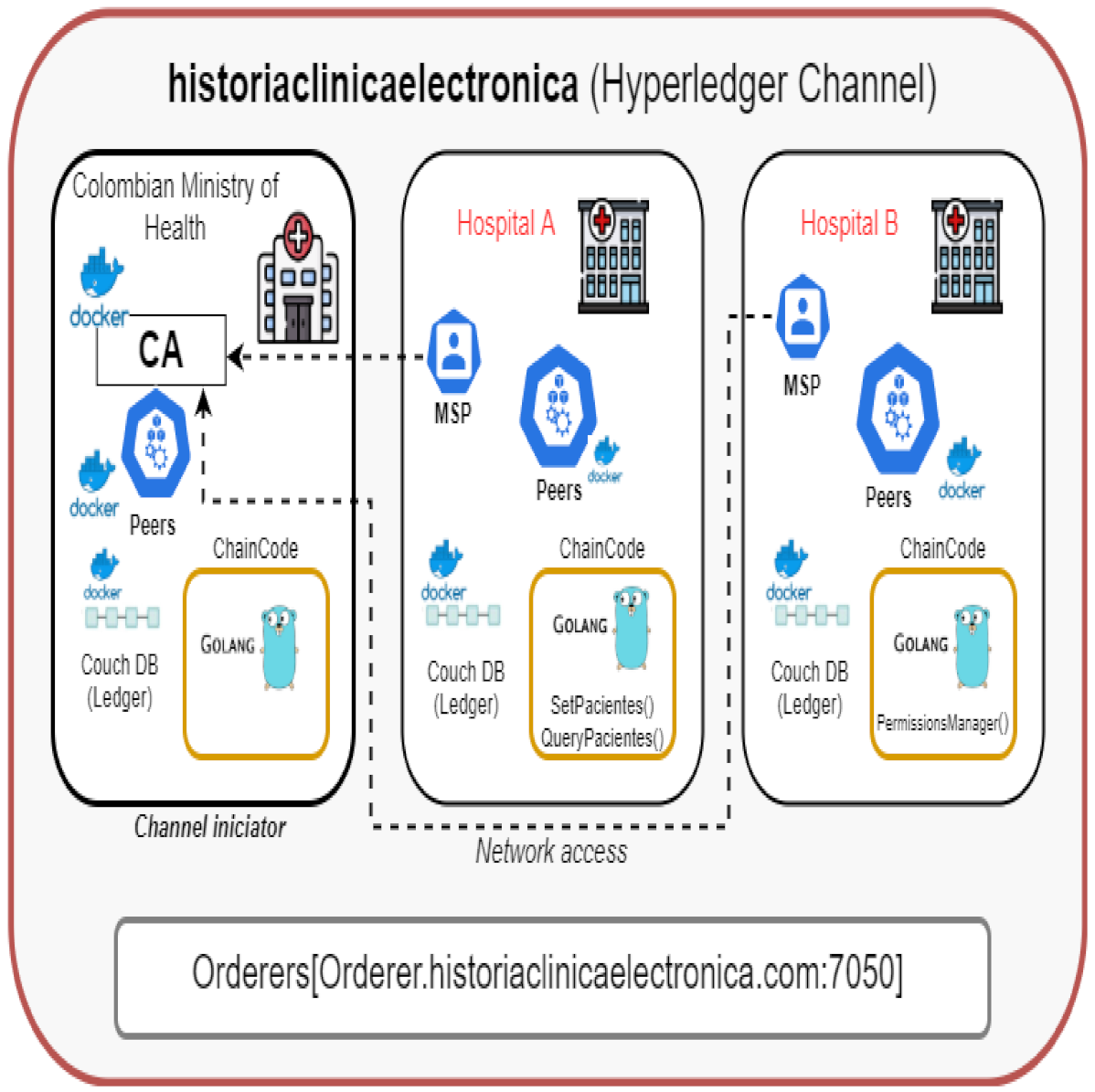
5.1. Hyperledger Installation
5.1.1. Creation of Cryptographic Material
- “OrdererOrgs”, which is the section where we defined the ordering service.
- “PeerOrgs”, which is the section where the health network’s standard organizations are registered.
5.1.2. General Configuration of the Genesis Block and the Channel
5.1.3. Creation of Anchor Transaction Files
5.1.4. Docker Services Definition
5.1.5. Channel Setup
5.2. Smart Contract Deployment
- Packaging the ChainCode
- Installation on each peer (Packaged chaincode)
- Endorsement Policies (Approve a smartcontract definition for your organization)
- Chaincode Commit in the network
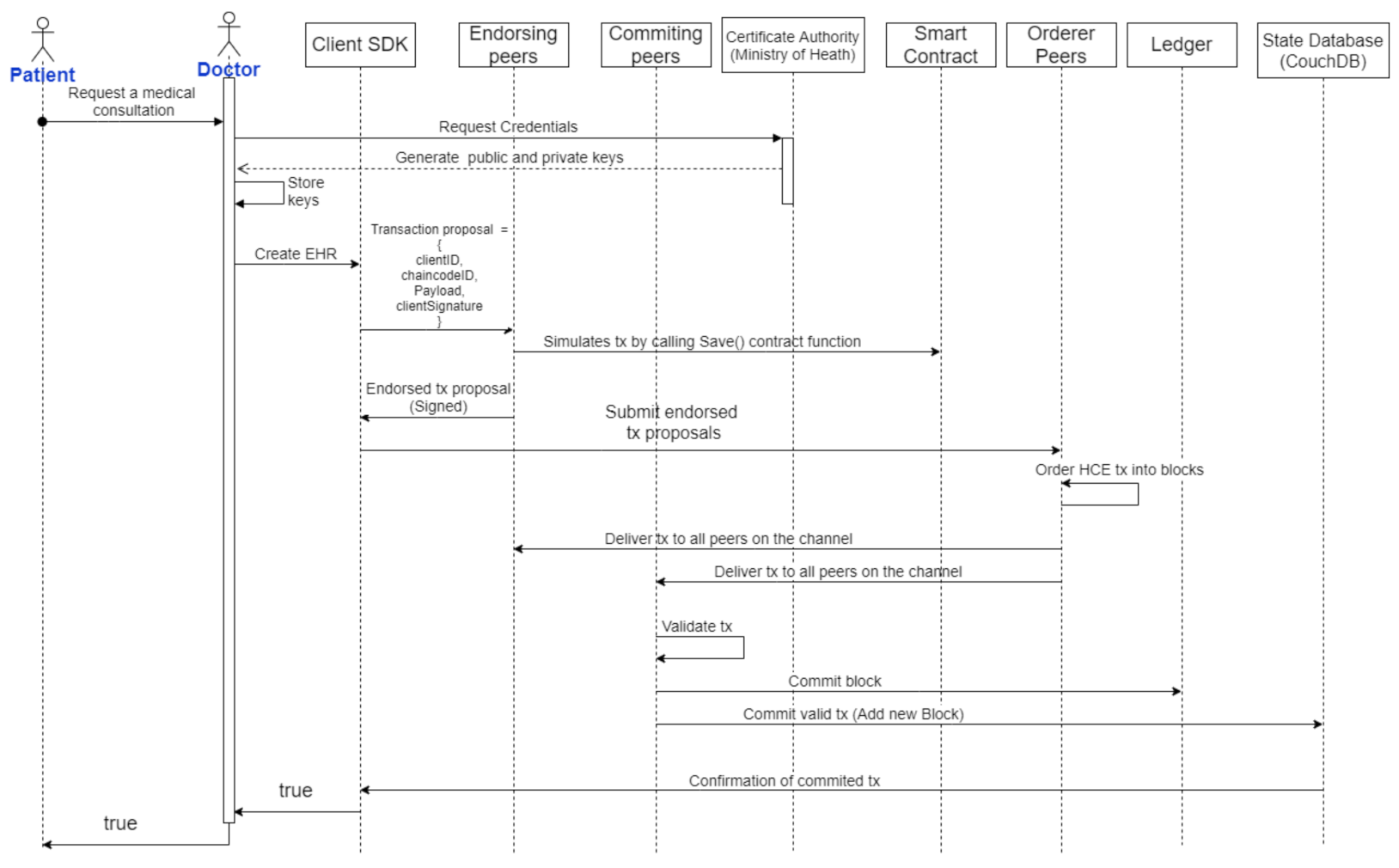
5.3. Execution and Testing of the Smart Contract
6. Security and Privacy Evaluation
- Confidentiality
- Integrity
- Availability
6.1. Confidentiality Assessment
- 1.
- The patient’s identifier during the entire process of exchanging information with the system is the CA’s public key so that the record of their actions does not contain personal information like their identity document.
- 2.
- The Hyperledger Fabric architecture channels allow for segregation of permissions to participants within the network, adding another layer of security over the patient’s EHR.
6.2. Integrity Assessment
6.3. Performance Metrics
6.4. Availability Assessment
6.5. Another Security Characteristics
7. Discussion
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| EHR | Electronic Health Record |
| POC | Proof of Concept |
| EMR | Electronic Medical Records |
| ADD | Attribute Driven Design |
| ASR | Architecturally Significant Requirements |
| QA | Quality Attribute |
| DLT | Distributed Ledger Technology |
References
- Certsuperior. Robos de Datos en el Sector Médico. Available online: https://www.certsuperior.com/robos-de-datos-en-el-sector-medico/ (accessed on 10 September 2020).
- Coventry, L.; Branley, D. Cybersecurity in healthcare: A narrative review of trends, threats and ways forward. Maturitas 2018, 113, 48–52. [Google Scholar] [CrossRef] [PubMed]
- Lee, H.A.; Kung, H.H.; Udayasankaran, J.; Kijsanayotin, B.; Marcelo, A.B.; Chao, L.; Hsu, C.Y. An Architecture and Management Platform for Blockchain-Based Personal Health Record Exchange: Development and Usability Study. J. Med. Internet Res. 2020, 22, e16748. [Google Scholar] [CrossRef] [PubMed]
- Esmaeilzadeh, P.; Mirzaei, T. The potential of blockchain technology for health information exchange: Experimental study from patients’ perspectives. J. Med. Internet Res. 2019, 21, e14184. [Google Scholar] [CrossRef] [PubMed]
- Salud, M.D. Resolucion 1995 DE 1999. Available online: https://www.minsalud.gov.co/Normatividad_Nuevo/RESOLUCI%C3%93N%201995%20DE%201999.pdf (accessed on 13 March 2020).
- Ministerio de Salud y Protección Social—National Government Enacted the Interoperability Law of Electronic Medical Record. Available online: https://www.minsalud.gov.co/English/Paginas/This-is-How-the-Electronic-Medical-Records-Will-Work-in-Colombia.aspx (accessed on 19 March 2021).
- Bass, L.; Clements, P.; Kazman, R. Software Architecture in Practice, 3rd ed.; Prentice Hall: Hoboken, NJ, USA, 2012. [Google Scholar]
- Cervantes, H.; Kazman, R. Designing Software Architectures: A Practical Approach; Addison-Wesley Professional: Boston, MA, USA, 2016; p. 289. [Google Scholar]
- Sajana, P.; Sindhu, M.; Sethumadhavan, M. On Blockchain Applications: Hyperledger Fabric And Ethereum. Int. J. Pure Appl. Math. 2018, 118, 2965–2970. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Manubot. 2019. Available online: https://git.dhimmel.com/bitcoin-whitepaper/ (accessed on 15 June 2021).
- Jabed Morshed Chowdhury, M.; Ferdous, S.; Biswas, K.; Chowdhury, N.; M Kayes, A.S.; Alazab, M.; Watters, P. A Comparative Analysis of Distributed Ledger Technology Platforms. IEEE Access 2019, 7, 167930–167943. [Google Scholar] [CrossRef]
- Hyperledger Fabric Docs—Documentation Release Master Hyperledger. 2020. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.2/ (accessed on 13 September 2020).
- Kuo, T.T.; Zavaleta Rojas, H.; Ohno-Machado, L. Comparison of blockchain platforms: A systematic review and healthcare examples. J. Am. Med. Inform. Assoc. 2019, 26, 462–478. [Google Scholar] [CrossRef] [PubMed]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-Less Medical Data Sharing among Cloud Service Providers via Blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Dubovitskaya, A.; Xu, Z.; Ryu, S.; Schumacher, M.; Wang, F. Secure and Trustable Electronic Medical Records Sharing using Blockchain. In AMIA Annual Symposium Proceedings; American Medical Informatics Association: Bethesda, MD, USA, 2017. [Google Scholar]
- Fernandes, A.; Rocha, V.; da Conceicao, A.F.; Horita, F. Scalable Architecture for sharing EHR using the Hyperledger Blockchain. In Proceedings of the 2020 IEEE International Conference on Software Architecture Companion (ICSA-C), Salvador, Brazil, 16–20 March 2020; pp. 130–138. [Google Scholar] [CrossRef]
- Areej, S. Which Programming Language Is Best to Use for Fabric’s Chaincode? 2020. Available online: https://www.researchgate.net/post/Which-programming-language-is-best-to-use-for-Fabrics-chaincode (accessed on 20 February 2021).
- Chen, X.; Zhao, S.; Wang, C.; Song, H.; Jiang, J.; Qi, J.; Li, T.O.; Chan, T.H.H.; Wang, S.; Cui, H. Efficient, DoS-resistant Consensus for Permissioned Blockchains. arXiv 2018, arXiv:1808.02252. [Google Scholar]
- Valenta, M.; Sandner, P. Comparison of ethereum, hyperledger fabric and cord. Frankfurt School Blockchain Center 2017, 8, 1–8. [Google Scholar]
- Cachin, C. Architecture of the hyperledger blockchain fabric. In Proceedings of the Workshop on Distributed Cryptocurrencies and Consensus Ledgers, Chicago, IL, USA, 25–29 July 2016; Volume 310, p. 4. [Google Scholar]
- Stamatellis, C.; Papadopoulos, P.; Pitropakis, N.; Katsikas, S.; Buchanan, W.J. A privacy-preserving healthcare framework using hyperledger fabric. Sensors 2020, 20, 6587. [Google Scholar] [CrossRef] [PubMed]
- HYPERLEDGER. Hyperledger Whitepaper. Available online: https://www.hyperledger.org/wp-content/uploads/2018/07/HL_Whitepaper_IntroductiontoHyperledger.pdf (accessed on 4 February 2020).
- McAfee. Informe Sobre Amenazas Contra Blockchain. Available online: https://www.mcafee.com/enterprise/es-es/assets/reports/rp-blockchain-security-risks.pdf (accessed on 24 December 2020).
- Atzei, N.; Bartoletti, M.; Cimoli, T. International Conference on Principles of Security and Trust; Springer: New York, NY, USA, 2017; pp. 164–186. [Google Scholar]
- Nitish, B.; Sugata, S. A Review of Techniques to Mitigate Sybil Attacks. arXiv 2012, arXiv:1207.2617. [Google Scholar]
- Hyperledger-fabric. What’s New in Hyperledger Fabric v2.x —Hyperledger-Fabricdocs Master Documentation. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.2/whatsnew.html (accessed on 30 May 2021).
- Stellabelle. Explain Delegated Proof of Stake Like I’m 5|by Stellabelle|HackerNoon.com|Medium. Available online: https://medium.com/hackernoon/explain-delegated-proof-of-stake-like-im-5-888b2a74897d (accessed on 22 August 2020).
- Tang, Y.; Zou, Q.; Chen, J.; Li, K.; Kamhoua, C.A.; Kwiat, K.; Njilla, L. ChainFS: Blockchain-Secured Cloud Storage. In Proceedings of the IEEE International Conference on Cloud Computing, San Francisco, CA, USA, 2–7 July 2018; pp. 987–990. [Google Scholar] [CrossRef]
- Do, H.G.; Ng, W.K. Blockchain-Based System for Secure Data Storage with Private Keyword Search. In Proceedings of the 2017 IEEE 13th World Congress on Services, Honolulu, HI, USA, 25–30 June 2017; Institute of Electrical and Electronics Engineers Inc.: Piscataway, NJ, USA, 2017; pp. 90–93. [Google Scholar] [CrossRef]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. MedRec: Using blockchain for medical data access and permission management. In Proceedings of the 2016 2nd International Conference on Open and Big Data, Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar] [CrossRef]
- Ichikawa, D.; Kashiyama, M.; Ueno, T. Tamper-resistant mobile health using blockchain technology. JMIR mHealth uHealth 2017, 5, e7938. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Hyperledger. Hyperledger Fabric Docs—Cryptogen. Available online: https://hyperledger-fabric.readthedocs.io/en/release-2.2/commands/cryptogen.html (accessed on 17 March 2021).
- Matt, Z.; Brian, W.; Mark, M. Hands-On Smart Contract Development with Hyperledger Fabric V2; O’Reilly Media, Inc.: Newton, MA, USA, 2021. [Google Scholar]
- Ali, M.; Nelson, J.; Shea, R.; Fredman, M.J. Bootstrapping trust in distributed systems with blockchains. USENIX 2016, 41, 52–58. [Google Scholar]
- Nitin, G.; O’Dowd, A.; Novotny, P.; Desrosiers, L.; Venkatraman Ramakrishna, S.A.B. Blockchain—An Enterprise and Industry Perspective— Blockchain with Hyperledger Fabric, 2nd ed.; Packt Publishing Ltd.: San Francisco, CA, USA, 2020. [Google Scholar]


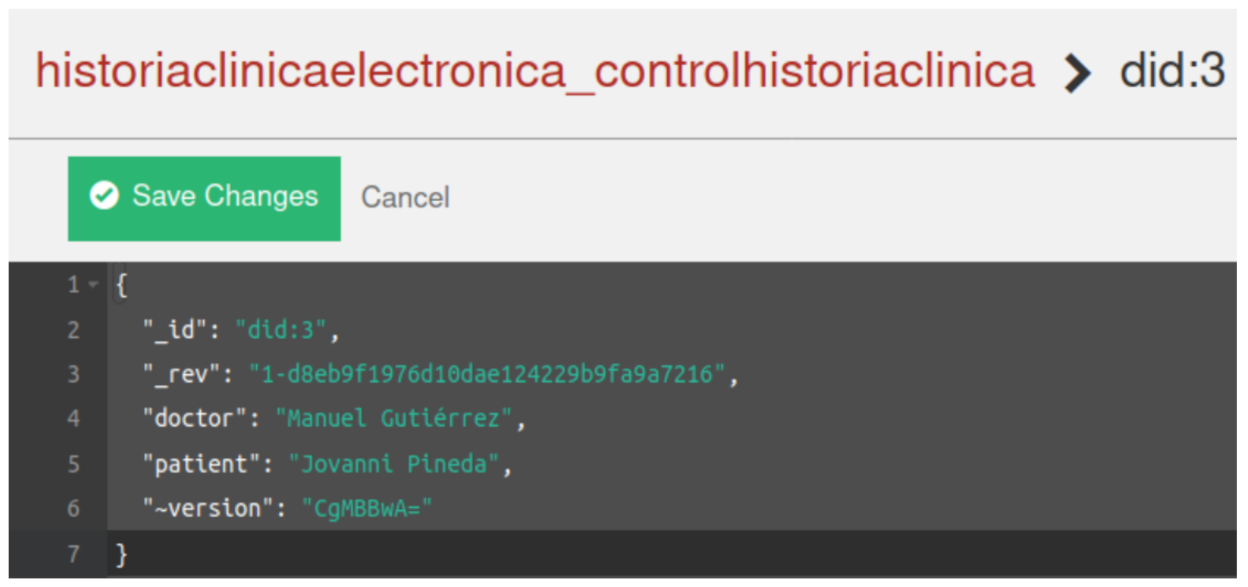


| Public | Private |
|---|---|
| Pseudo-anonymous nodes | Identified nodes |
| Permissions to view all data | Restricted data. |
| Focused on Cryptocurrencies | Focused on enterprise solutions in various industries |
| such as finance, supply chain, etc. | |
| Miners are required | Miners are not needed. |
| Use of PoW as consensus protocol in most cases | Use of different consensus protocols. |
| High power consumption | Low power consumption. |
| Attribute | Public | Private |
|---|---|---|
| Performance | Low | High |
| Latency | Slow | Medium. |
| Number of readers | High | High |
| Number of writers | High | Medium |
| Number of untrusted writers | High | Low. |
| Consensus Mechanism | Mainly PoW, and PoS | Many, BFT protocols. |
| Centrally managed | No | Consortium (Set of participants). |
| Element | Options and Features |
|---|---|
| Permission type in the network | Public (Permissionless): Public participation is required, e.g.,: Applications that rely on patient-managed data. Private (Permissioned): It is required to include only authorized participants, e.g.,: Information exchange networks between hospitals. |
| Consensus Protocol or Algorithm | Proof of Stake: Suitable for healthcare applications. Kafka Based on election process. Finalizes consensus quickly due to a small number of members. |
| Programming language | Bitcoin Script: Smart contracts with simple programming languages. Not useful for healthcare applications. Solidity: Ethereum smart contracts language. It is one of the most popular languages for writing Smart Contracts. Go, Node.js and Java: Hyperledger Fabric Chaincode languages. Widely known and used programming languages. An interesting paper to choose Hyperledger’s Chaincode language can be found in [18]. |
| Software License Type | MIT: Open source, and non-copyleft license. Allows healthcare applications to reuse the source code of the Blockchain platform. GPL: Copyleft license that allows source code use. Its derivative works in some cases must also be open-source. Apache License v2.0: Type of license used by Fabric, it is not a copyleft license but requires a copyright notice retention. |
| Quality Attributes | Design Rationale |
|---|---|
| Throughput, Reliability | Based on healthcare context architectural constraints. The need to pay for transaction execution (As in Ethereum) limits the system’s usability and throughput [16]. Hyperledger Fabric aims to develop distributed ledgers with a particular focus on improving the performance and reliability of such systems [9]. |
| Scalability | Hyperledger Fabric would exponentially improve scalability and storage size in healthcare domain as only specific nodes would be in charge of handling the consensus and addition of blocks to the chain [17]. Having a ledger for each channel allows distributing transactions among several committer nodes, increasing the amount of data and the requests that a node can store and fulfill [17]. Fabric solves some performance, scalability, and privacy issues that some permissionless blockchain architectures such as Ethereum possess thanks to its permissioned blockchain mode of operation, use of BFT consensus algorithm and fine-grained access control [20]. |
| Security: Privacy, Confidentiality, and Reliability | Hyperledger Fabric has a multi-channel architecture where participants cannot access a chain if they do not have access to the channel the chain belongs to [9,17]. Additionally, it is reliable since it will not allow the information to be modified. Fabric has a security infrastructure that includes transaction enrollment and authorization through a public key certificate [9] and achieves a level of confidentiality through in-band encryption (occurs while data are in transit) as described in [21]. In [22] a Hyperledger Fabric-based solution is proposed which stores patient records in an immutable distributed ledger with anonymity and data privacy. Additionally, the use of Idemix cryptographic protocol suite provides patient’s data unlinkability. |
| Auditability | Regulatory compliance and access for regulators to investigate transaction records is required in health context [22]. Fabric’s ledger provides this QA, as it provides authorized entities with the means to link user transactions according to their roles and access a particular user’s activity in the system [23].The authors of [22] created a system that supports secure auditing, and preservation of privacy using Hyperledger Fabric. |
| Modularity | Authors of [12] mentioned that one of the differentiating qualities of Hyperledger Fabric over other DLTs is that it has a highly modular and configurable architecture, which allows it to be used in a wide range of particular use cases, such as EHRs. This modularity is achieved through different types of Pluggable Consensus Protocols, which allows it to be adjusted to particular cases and specific trust models. |
| Flexibility (Modifiability), Resilience | The modular architecture of Hyperledger Fabric delivers a high degree of resilience, flexibility, and confidentiality. This flexibility enables other QAs such as Scalability and Privacy to be achieved [9]. |
| Quality Attributes | Design Rationale |
|---|---|
| Confidentiality, Availability | An Ethereum Blockchain Architecture for clinical records exchange platform integrated with the international standard for health data exchange HL7—FHIR (High Level Seven—Fast Healthcare Interoperability Resource) was built in [3], it manages clinical data exchange authorization to create a private chain. |
| Integrity | Ethereum private chain architecture was used to store the Hash values of patients’ health records (PHRs) in the Southeast Asian health network to ensure their integrity in [3]. |
| Fault Tolerance | The core of Ethereum is its EVM (Ethereum Virtual Machine), which maintains consensus across the entire Blockchain network when executed on each network node. This decentralization of consensus ratifies an extreme level of fault tolerance [9]. |
| Performance | Ethereum Architecture has been used together with the PoA consensus mechanism, which compared to other proof mechanisms, allows faster creation of the blocks since the verification of the new blocks will be done by some verifier nodes using their real identities [3], so the waiting time for information exchange is reduced considerably. |
| Security, Privacy | Ethereum achieves Immutability and Security in part through SHA-256, the default hash algorithm used by the Ethereum architecture to create blocks composed of the block’s content, the hash value of the previous block, and a timestamp. The authors of [14] proposed a data sharing framework to ensure access to sensitive electronic health data records using a blockchain-based data-sharing scheme and the use of smart contracts built upon Solidity to monitor the behavior of data when it is outside the custodians care facilities. |
| Auditability | Authors of [14] implemented a blockchain-based system to provide data provenance, auditing and traceability for medical data among health entities (cloud service providers) mainly through tagging the smart contracts to the data. |
| Paper | Network | Technology | Privacy | Integrity | Access Control | Latency/Throughput Testing |
|---|---|---|---|---|---|---|
| ChainFS [29] | Private | Ethereum | ✓ | X | X | ✓ / X |
| Block DS [30] | Private | Agnostic | ✓ | X | ✓ | X / X |
| MedRec [31] | Public/Private | Ethereum | ✓ | ✓ | X | X / X |
| Tamper-resistant mHealth [32] | Private | Fabric 0.5 | X | ✓ | X | / X |
| PREHEALTH [22] | Private | Fabric 1.4 | ✓ | ✓ | X | ✓ / X |
| Our work | Private | Fabric 2.2.0 | ✓ | ✓ | ✓ | ✓ / ✓ |
| Id | Quality Attribute | Scenario |
|---|---|---|
| QA-1 | Security | When an electronic medical record is altered in the system, the precise values of the change are recorded 100% of the time. |
| QA-2 | Security | When an intruder alters an electronic medical record in the system, the change’s precise values are recorded 100% of the time. |
| QA-3 | Security | When a user makes a change in the system, it is possible to know who performed a transaction in the system 100% of the time. |
| QA-4 | Interoperability | A hospital with an external health system requests a Patient’s Medical History registration in another system. 100% of the information is understood by the system, processed, and stored according to the archetypes stipulated. |
| QA-5 | Availability | When an error occurs in the system, it must resume its operation in less than 1 min. |
| QA-6 | Availability | When a network failure occurs in one of the EPS or health network entities, the system availability is affected less than 5%. |
| Category | Description |
|---|---|
| Design purpose | We will design a greenfield system (a new system) that is part of a mature domain. The primary purpose is to build a detailed design in order to be able to build a system that contributes to the protection of the data associated with the EHR. |
| Primary Functional Requirements | Based on the context of the EHR and the primary functional requirements obtained from it, we determined that the main Use Cases are:
|
| Scenario ID | Importance for the Health Network | Difficulty of Implementation |
|---|---|---|
| QA-1 | High | Low |
| QA-2 | High | High |
| QA-3 | High | High |
| QA-5 | High | High |
| QA-6 | High | Medium |
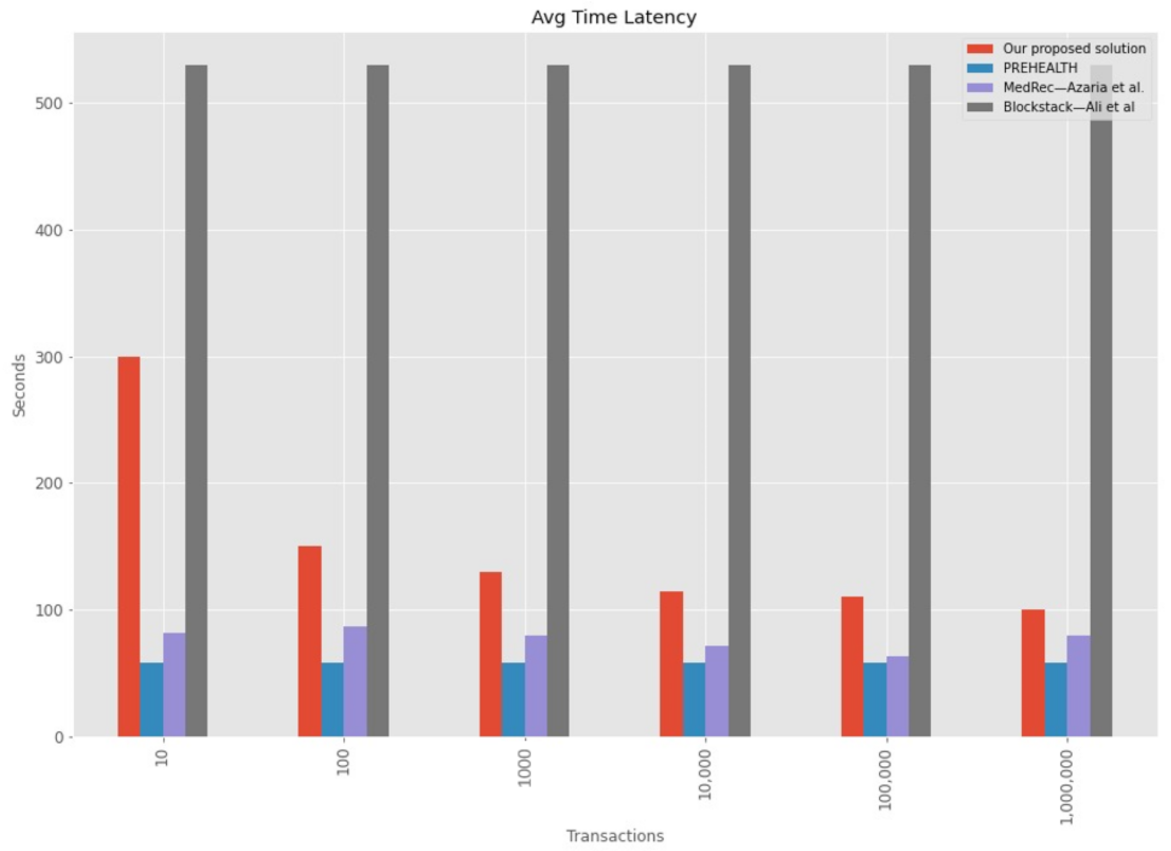
| Stats | Our Proposed Solution | PREHEALTH | MedRec—Azaria et al. | Blockstack—Ali et al. |
|---|---|---|---|---|
| Mean | 150.67 | 58.00 | 77.07 | 530.00 |
| Std | 75.22 | 0.00 | 8.38 | 0.00 |
| Min | 100.00 | 58.00 | 63.20 | 530.00 |
| 25% | 111.00 | 58.00 | 73.60 | 530.00 |
| 50% | 122.00 | 58.00 | 79.60 | 530.00 |
| 75% | 145.00 | 58.00 | 81.02 | 530.00 |
| Max | 300.00 | 58.00 | 86.90 | 530.00 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Pineda Rincón, E.A.; Moreno-Sandoval, L.G. Design of an Architecture Contributing to the Protection and Privacy of the Data Associated with the Electronic Health Record. Information 2021, 12, 313. https://doi.org/10.3390/info12080313
Pineda Rincón EA, Moreno-Sandoval LG. Design of an Architecture Contributing to the Protection and Privacy of the Data Associated with the Electronic Health Record. Information. 2021; 12(8):313. https://doi.org/10.3390/info12080313
Chicago/Turabian StylePineda Rincón, Edwar Andrés, and Luis Gabriel Moreno-Sandoval. 2021. "Design of an Architecture Contributing to the Protection and Privacy of the Data Associated with the Electronic Health Record" Information 12, no. 8: 313. https://doi.org/10.3390/info12080313
APA StylePineda Rincón, E. A., & Moreno-Sandoval, L. G. (2021). Design of an Architecture Contributing to the Protection and Privacy of the Data Associated with the Electronic Health Record. Information, 12(8), 313. https://doi.org/10.3390/info12080313






