Improving Physical Layer Security of Cooperative NOMA System with Wireless-Powered Full-Duplex Relaying
Abstract
:1. Introduction
- We investigate a cooperative NOMA system with wireless-powered FD relaying. In particular, an AN-aided secrecy enhancing scheme is proposed for self-sustained FD relay to reduce the decoding performance of the eavesdropper, where the FD relay can harvest energy from the source and SI signal.
- For the proposed AN-aided secrecy enhancing scheme, the lower bound of the ergodic secrecy sum rate (ESSR) is analyzed with closed-form expressions. In particular, the proposed scheme achieves a positive lower bound of ESSR, indicating that perfect secrecy can be guaranteed.
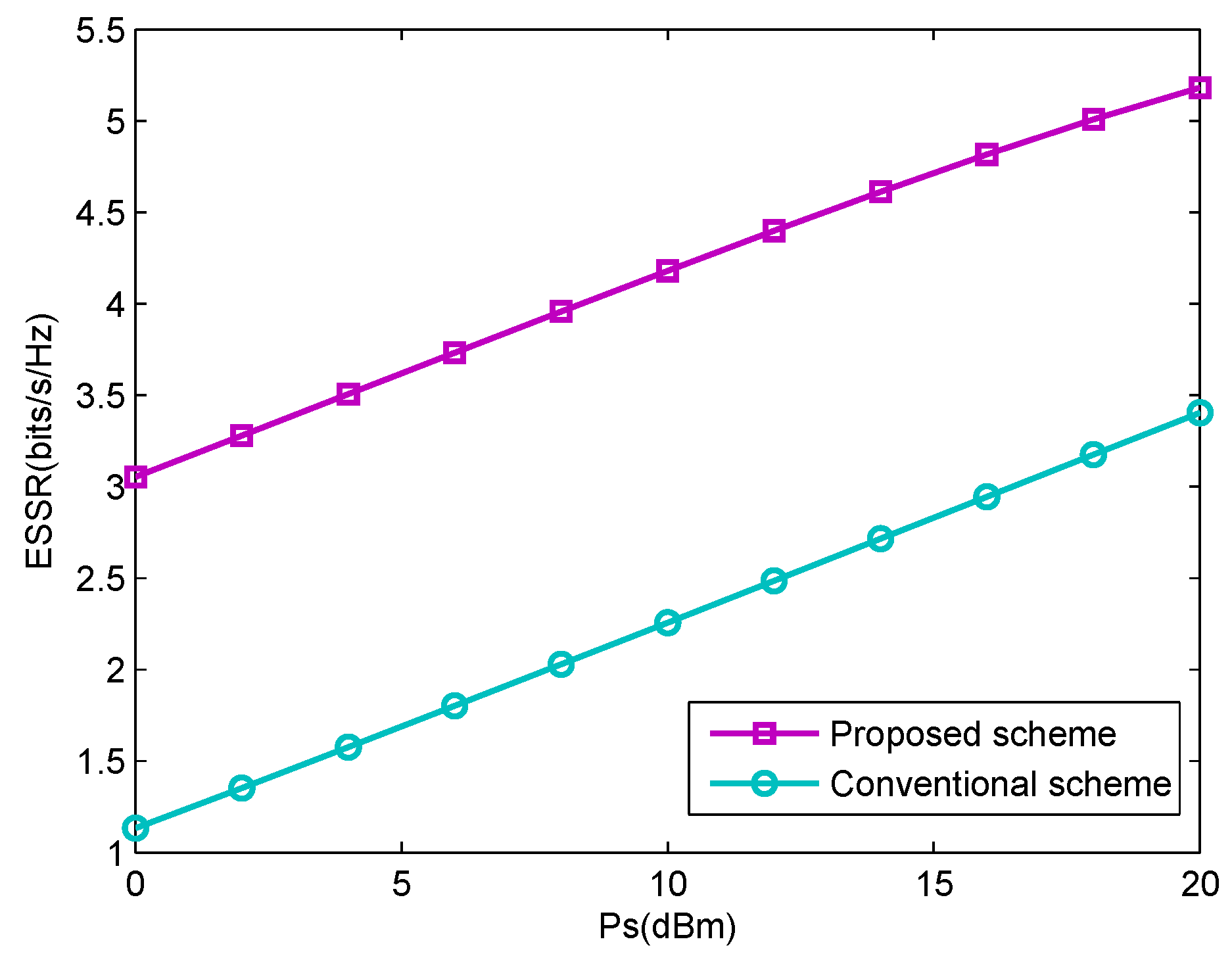
- Monte Carlo simulations are provided to verify the accuracy of the theoretical analysis, and the superiority of the proposed AN-aided secure transmission scheme over the benchmark scheme is also presented. This indicates that adopting AN at the wireless-powered FD relay can significantly improve the secrecy performance in the cooperative NOMA systems.
2. System Model and the Proposed Scheme
2.1. System Model
2.2. Proposed Scheme
3. Performance Analysis
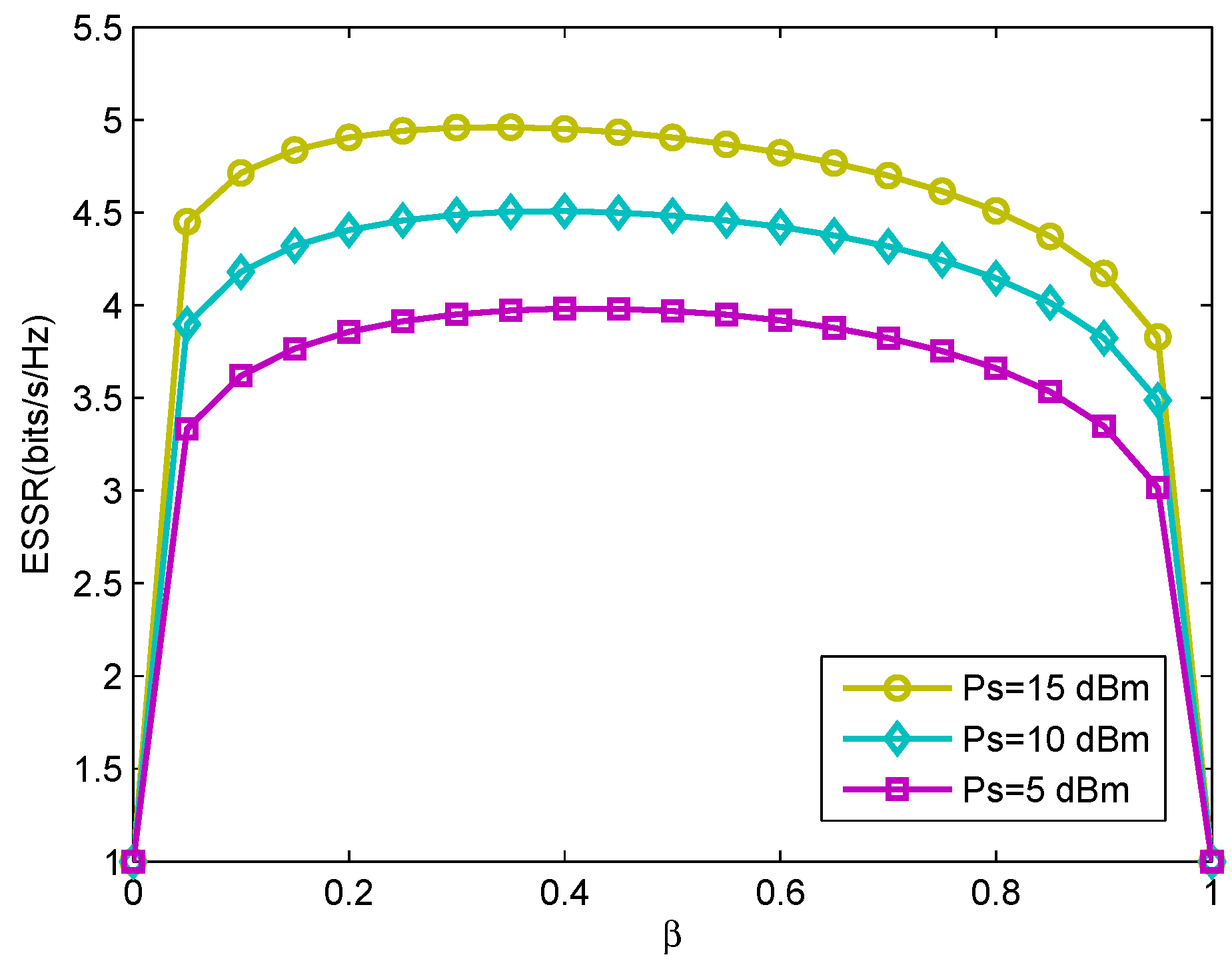
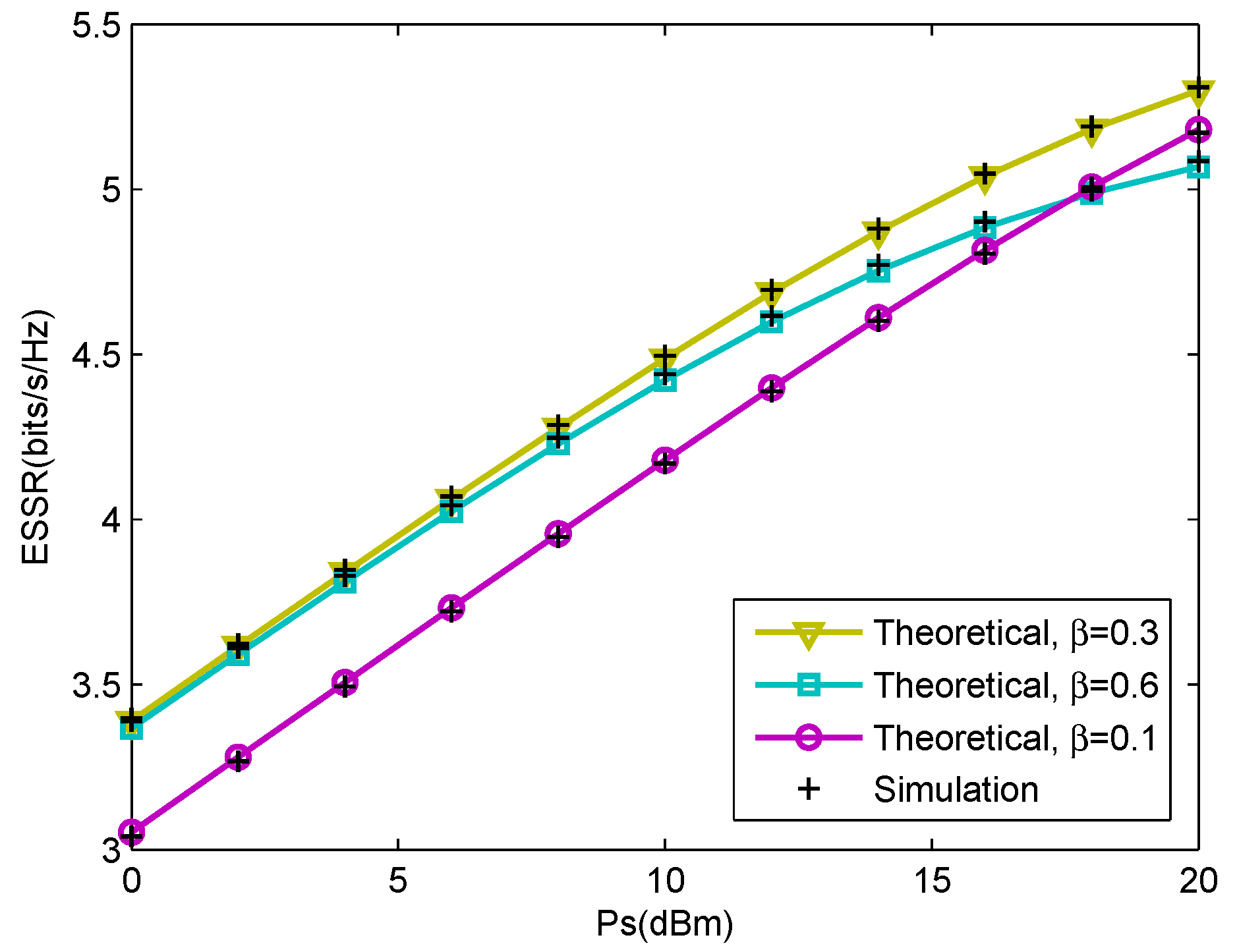
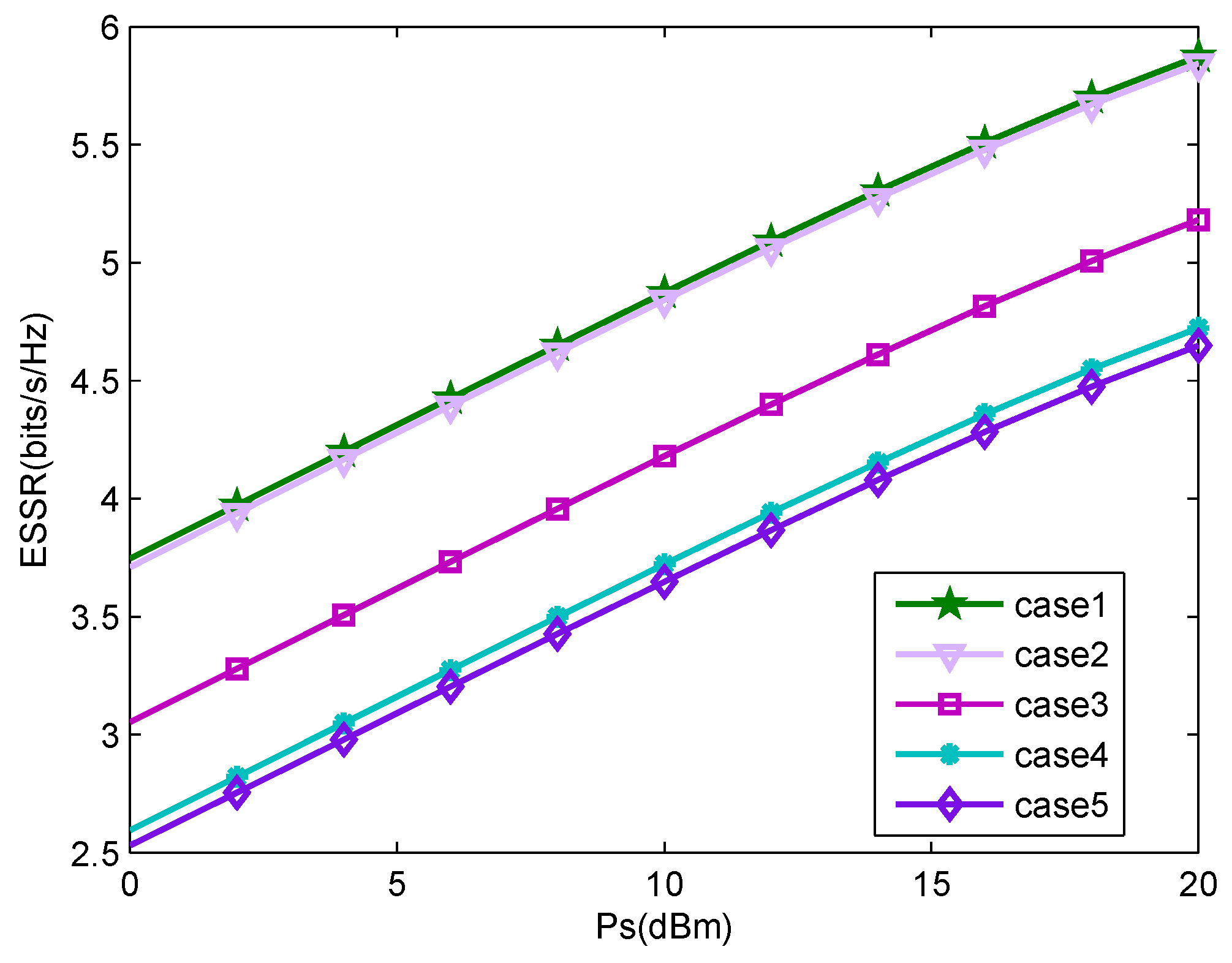
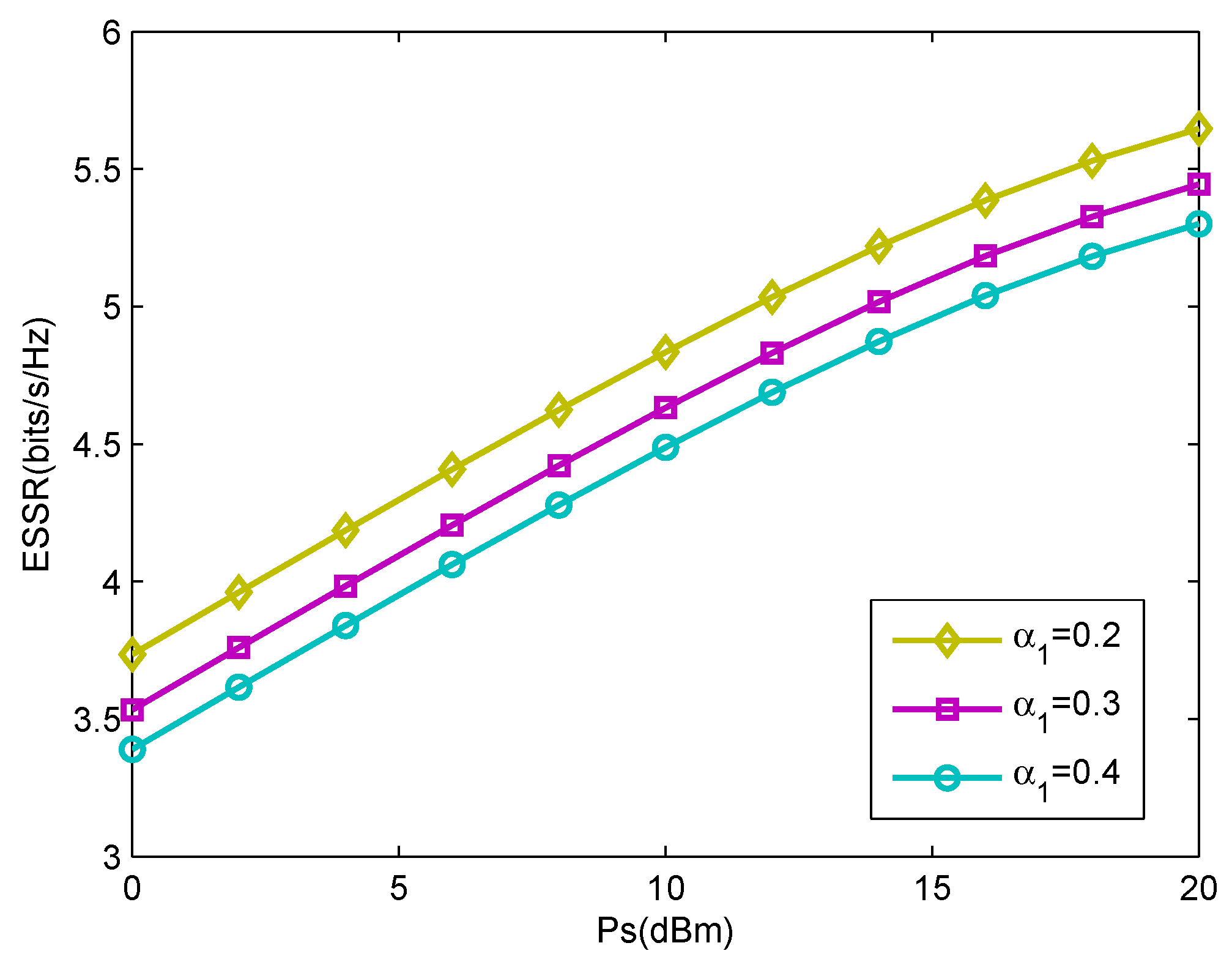
4. Simulations
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Zeng, Y.; Zhang, R. Full-duplex wireless-powered relay with self-energy recycling. IEEE Wirel. Commun. Lett. 2015, 4, 201–204. [Google Scholar] [CrossRef] [Green Version]
- Ding, Z.; Fan, P.; Poor, H.V. On the coexistence between full-duplex and NOMA. IEEE Wirel. Commun. Lett. 2018, 7, 692–695. [Google Scholar] [CrossRef]
- Rauniyar, A.; Engelstad, P.E.; Osterbo, O.N. Performance Analysis of RF Energy Harvesting and Information Transmission Based on NOMA with Interfering Signal for IoT Relay Systems. IEEE Sens. J. 2019, 19, 7668–7682. [Google Scholar] [CrossRef] [Green Version]
- Yang, S.; Ren, Y.; Lu, G.; Wang, J. Optimal resource allocation for full-duplex wireless-powered relaying with self-energy recycling. In Proceedings of the 2019 11th International Conference on Wireless Communications and Signal Processing (WCSP), Xi’an, China, 23–25 October 2019; pp. 1–6. [Google Scholar]
- Liu, Y.; Ding, Z.; Elkashlan, M.; Poor, H.V. Cooperative Non-orthogonal Multiple Access with Simultaneous Wireless Information and Power Transfer. IEEE J. Sel. Areas Commun. 2016, 34, 938–953. [Google Scholar] [CrossRef] [Green Version]
- Do, N.T.; Da Costa, D.B.; Duong, T.Q.; An, B. A BNBF User Selection Scheme for NOMA-Based Cooperative Relaying Systems With SWIPT. IEEE Commun. Lett. 2017, 21, 664–667. [Google Scholar] [CrossRef] [Green Version]
- Guo, C.; Zhao, L.; Feng, C.; Ding, Z.; Chen, H.-H. Energy Harvesting Enabled NOMA Systems with Full-Duplex Relaying. IEEE Trans. Veh. Technol. 2019, 68, 7179–7183. [Google Scholar] [CrossRef] [Green Version]
- Sun, L.; Du, Q. Physical layer security with its applications in 5G networks: A review. China Commun. 2017, 14, 1–14. [Google Scholar] [CrossRef]
- Chen, J.; Yang, L.; Alouini, M.-S. Physical Layer Security for Cooperative NOMA Systems. IEEE Trans. Veh. Technol. 2018, 67, 4645–4649. [Google Scholar] [CrossRef] [Green Version]
- Feng, Y.; Yang, Z.; Yan, S. Non-orthogonal multiple access and artificial-noise aided secure transmission in FD relay networks. In Proceedings of the 2017 IEEE Globecom Workshops (GC Wkshps), Singapore, 4–8 December 2017; pp. 1–6. [Google Scholar]
- Liu, C.; Zhang, L.; Xiao, M.; Chen, Z.; Li, S. Secrecy performance analysis in downlink NOMA systems with cooperative full-duplex relaying. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Lv, L.; Jiang, H.; Ding, Z.; Yang, L.; Chen, J. Secrecy-Enhancing Design for Cooperative Downlink and Uplink NOMA with an Untrusted Relay. IEEE Trans. Commun. 2020, 68, 1698–1715. [Google Scholar] [CrossRef]
- Lei, H.; Yang, Z.; Park, K.-H.; Ansari, I.S.; Guo, Y.; Pan, G.; Alouini, M.-S. Secrecy Outage Analysis for Cooperative NOMA Systems with Relay Selection Schemes. IEEE Trans. Commun. 2019, 67, 6282–6298. [Google Scholar] [CrossRef] [Green Version]
- Salem, A.; Musavian, L.; Jorswieck, E.A.; Aissa, S. Secrecy Outage Probability of Energy-Harvesting Cooperative NOMA Transmissions With Relay Selection. IEEE Trans. Green Commun. Netw. 2020, 4, 1130–1148. [Google Scholar] [CrossRef]
- Guo, C.; Zhao, L.; Feng, C.; Ding, Z.; Wang, H.-M. Secrecy Performance of NOMA Systems With Energy Harvesting and Full-Duplex Relaying. IEEE Trans. Veh. Technol. 2020, 69, 12301–12305. [Google Scholar] [CrossRef]
- Yang, S.; Ren, Y.; Lu, G. Optimal power allocation for wireless-powered full-duplex cooperative NOMA system with partial CSI. In Proceedings of the 2020 IEEE Globecom Workshops (GC Wkshps), Taipei, Taiwan, 7–11 December 2020; pp. 1–5. [Google Scholar]
- Ding, Z.; Yang, Z.; Fan, P.; Poor, H.V. On the Performance of Non-Orthogonal Multiple Access in 5G Systems with Randomly Deployed Users. IEEE Signal Process. Lett. 2014, 21, 1501–1505. [Google Scholar] [CrossRef] [Green Version]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic: New York, NY, USA, 2007. [Google Scholar]
- Abramowitz, M.; Stegun, I. Handbook of Mathematical Functions with Formulas, Graphs, Mathematical Tables; Dover: New York, NY, USA, 1972. [Google Scholar]

Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ren, Y.; Tan, Y.; Makhanbet, M.; Zhang, X. Improving Physical Layer Security of Cooperative NOMA System with Wireless-Powered Full-Duplex Relaying. Information 2021, 12, 279. https://doi.org/10.3390/info12070279
Ren Y, Tan Y, Makhanbet M, Zhang X. Improving Physical Layer Security of Cooperative NOMA System with Wireless-Powered Full-Duplex Relaying. Information. 2021; 12(7):279. https://doi.org/10.3390/info12070279
Chicago/Turabian StyleRen, Yuan, Yixuan Tan, Meruyert Makhanbet, and Xuewei Zhang. 2021. "Improving Physical Layer Security of Cooperative NOMA System with Wireless-Powered Full-Duplex Relaying" Information 12, no. 7: 279. https://doi.org/10.3390/info12070279
APA StyleRen, Y., Tan, Y., Makhanbet, M., & Zhang, X. (2021). Improving Physical Layer Security of Cooperative NOMA System with Wireless-Powered Full-Duplex Relaying. Information, 12(7), 279. https://doi.org/10.3390/info12070279





