Diagnostic of Data Processing by Brazilian Organizations—A Low Compliance Issue
Abstract
1. Introduction
2. Background
2.1. Legislation of Personal Data Protection
- Finality, or Transparency in GDPR: the personal data processing must be a legitimate goal, specified and explicitly known by the data owner;
- Adequacy, or Purpose limitation in GDPR: the processing of data must be consistent with its finality requested;
- Need, or Data Minimization in GDPR: the data must be restrained to exactly what is needed by the process;
- Free access: the data owner should be able to consult the form and the duration of its processing as well as the data itself at anytime, free of charge and in an easy way;
- Data quality or accuracy in GDPR: the processed data must be stored, arranged and manipulated with a view to clarity, accuracy, relevance and timeliness of the data;
- Transparency: the information about data processing should be arranged by clarity and objectivity, presenting its purpose;
- Safety, or integrity in GDPR: the data must be safe both technically and administratively (physical and digital data);
- Prevention: adoption of measures to avoid possible damage resulting from data processing;
- Non discrimination: the prohibition of data processing for discrimination or abuse purposes; and
- Accountability: demonstration of the means used to comply with legislation and accountability for the data process.
- Controller: it is a natural or legal person, public or private, who is strategically and tactically responsible for data processing;
- Processor: it is the operational data processing responsible, it executes according to the controller’s determinations;
- Data Protection Officer (DPO): is defined by LGPD as a person nominated by the controller and the processor to act as a communication channel between the controller, data holders and the National Data Protection Authority (ANPD) [1].
2.2. Personal Data Processing
2.3. Data Privacy
2.4. Related Works
3. Research Methodology
3.1. Research Goal
3.2. Research Questions
3.3. Research Methods
- Dimension 1
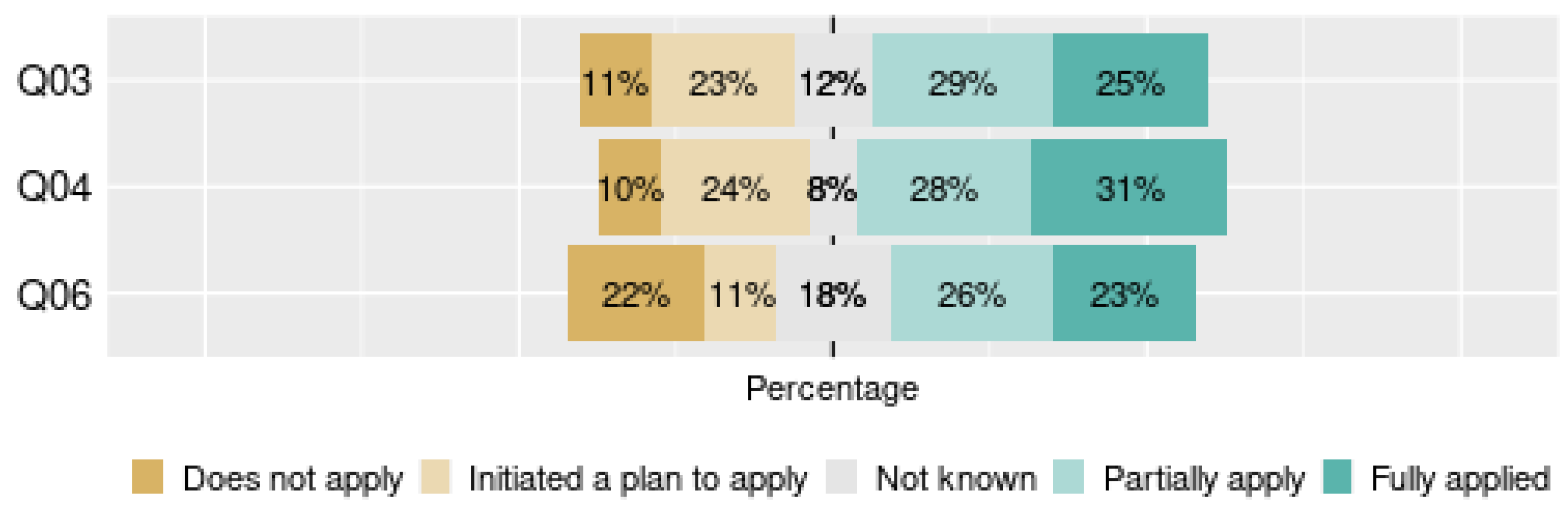
- General Information: In this dimension, we grouped the general information about the audience and their company, taking as an example some questions related to the size of the organization, general actions related to the compliance to LGPD, nature of the organizations activity among others. This dimension contained six questions (1–6).
- Dimension 2
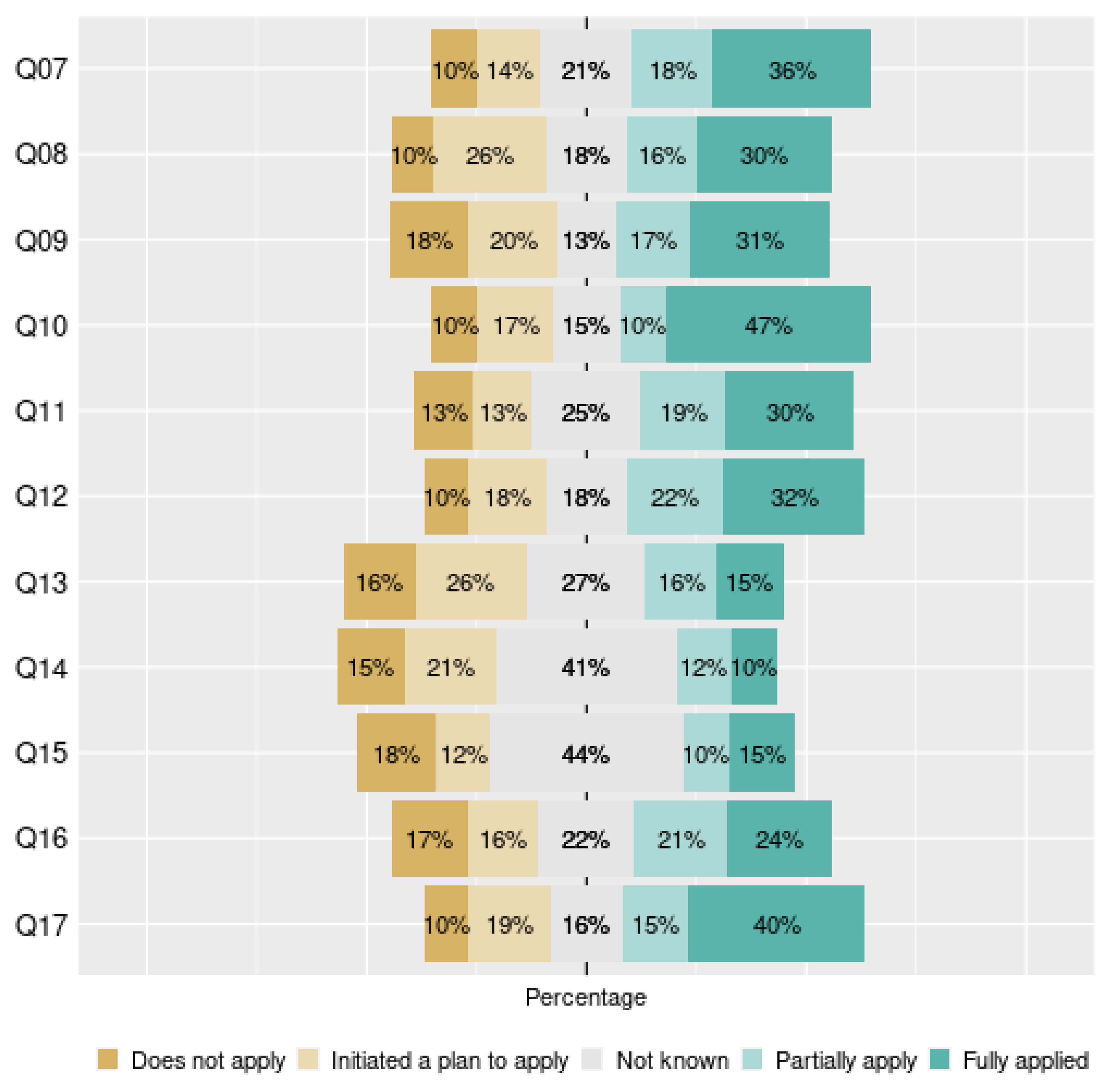
- Governance: About the governance, we listed questions concern the good practices, polices, communication, roles and involvement at a strategic level. This dimension contained eleven questions (7–17).
- Dimension 3
- Legal Compliance and LGPD Principles: In this dimension, the level of compliance with the legal aspect of the LGPD and its principles were measured, as the principle of data minimization, or maintaining the purpose/legality of personal data and other aspects. This dimension contained seven questions (18–24).
- Dimension 4
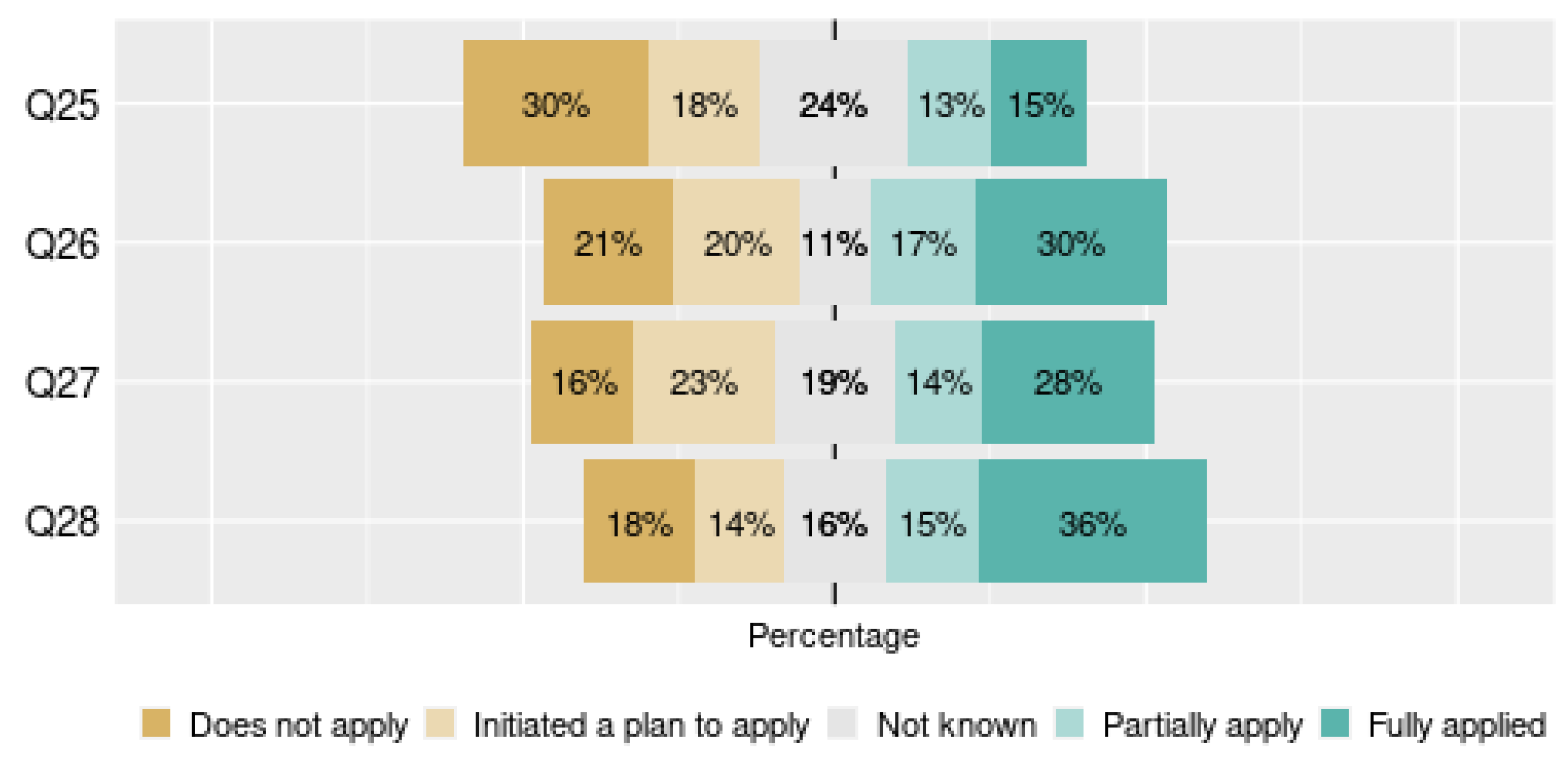
- Transparency and Subject Rights: This dimension assesses the way the company informs its customers about the privacy of their data. This dimension contained four questions (25–28).
- Dimension 5
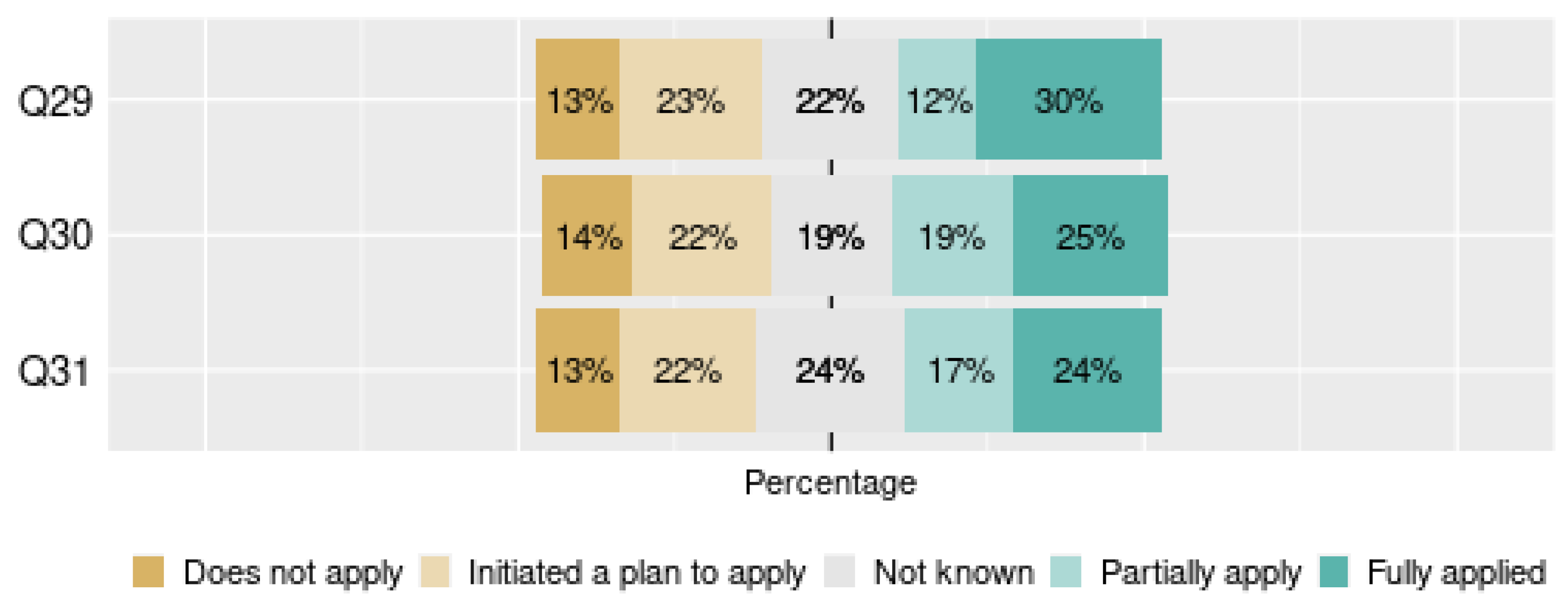
- Data Traceability: This dimension is responsible for grouping questions related to data inventory, data classification and extension of the data format under treatment. This dimension contained three questions (29–31).
- Dimension 6
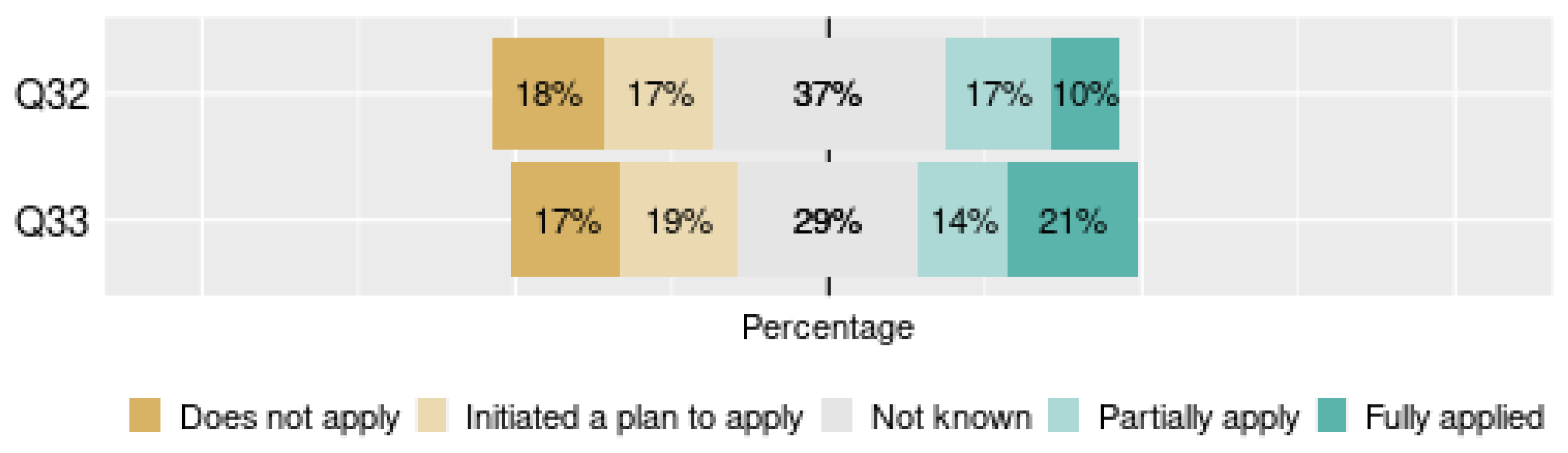
- Contracts and Relations with Collaborators: This is a dimension dedicated to the review of the legal instruments in force and also the future ones to comply with the LGPD regulations. This dimension contained two questions (32 and 33).
- Dimension 7
- Information Security: This dimension assesses aspects of information security related to LGPD such as risk assessment, risk monitoring and technical aspects. This dimension contained five questions (34–38).
- Dimension 8
- Data Breach: This dimension assesses the actions that the company plans to deal with threats of data leakage, such as data leakage communication plan, incident management and external reporting channels. This dimension contained three questions (39–41).
4. Results
4.1. RQ.1. Is the Processing of Personal Data Carried Out by Organizations in Accordance with LGPD Principles?
4.2. RQ.2. Have Organizations Prepared the Personal Data Protection Impact Report (RIPD)?
- Identify the Treatment Agents and the Person in Charge: article 5, Items VI, VII and VIII, of the LGPD;
- Identify the need to prepare the Report;
- Describe the treatment: nature, scope, context and purpose of the treatment;
- Identify the stakeholders consulted;
- Describe how the organization assesses the need and proportionality of personal data;
- Identify and assess risks—classification: low, moderate and high;
- Identify measures to address risks—examples: Logical access control, secure development and Network Security;
- Approve the Report: formalize the approval of the report, by obtaining signatures from the person responsible for preparing the RIPD, the person in charge, the authorities—controller and processor;
- Maintain the Review: the RIPD must be reviewed and updated annually or whenever any type of change occurs that affects the processing of personal data carried out by the organization.
4.3. RQ.3. Have Organizations Established a Procedure or Methodology to Verify That the LGPD Principles Are Being Implemented?
4.4. RQ.4. Do Organizations Have a Service Privacy Policy?
4.5. Work Discussions
5. Research Limitations
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A. Questions of Survey
References
- Da República, P. Lei Geral de Proteção de Dados. 2018. Available online: http://www.planalto.gov.br/ccivil_03/_ato2015-2018/2018/lei/L13709.htm (accessed on 22 July 2020).
- Executivo, P. Medida Provisória 959/2020. 2020. Available online: https://www.camara.leg.br/propostas-legislativas/2250977 (accessed on 12 November 2020).
- Erickson, A. Comparative Analysis of the EU’s GDPR and Brazil’s LGPD: Enforcement Challenges with the LGPD. Brook. J. Int’l L. 2018, 44, 859. [Google Scholar]
- Rodrigues, S. Direito Civil; Number v. 1 in Direito Civil; Editora Saraiva: São Paulo, Brazil, 2003. [Google Scholar]
- Canedo, E.D.; Calazans, A.T.S.; Masson, E.T.S.; Costa, P.H.T.; Lima, F. Perceptions of ICT Practitioners Regarding Software Privacy. Entropy 2020, 22, 429. [Google Scholar] [CrossRef] [PubMed]
- Pessoa, C.R.; Nunes, B.C.; de Oliveira, C.; Marques, M.E. Effects and Projections of the Brazilian General Data Protection Law (LGPD) Application and the Role of the DPO. In Digital Transformation and Challenges to Data Security and Privacy; IGI Global: Hershey, PA, USA, 2021; pp. 195–208. [Google Scholar]
- Federal, G. Guia de Boas Práticas para Implementação na Administração Pública Federal. 2020. Available online: https://www.gov.br/governodigital/pt-br/governanca-de-dados/guia-lgpd.pdf (accessed on 20 October 2020).
- Turn, R. Security and Privacy Requirements in Computing. In Proceedings of the 1986 ACM Fall Joint Computer Conference, ACM ’86, Dallas, TX, USA, 2–6 November 1986; IEEE Computer Society Press: Washington, DC, USA, 1986; pp. 1106–1114. [Google Scholar]
- Schreiber, A. Right to Privacy and Personal Data Protection in Brazilian Law; Springer International Publishing: Cham, Switzerland, 2020; pp. 45–54. [Google Scholar] [CrossRef]
- Standard, International Organization for Standardization. ABNT NBR ISO/IEC 27701:2019—Security Techniques—Extension to ISO/IEC 27001 and ISO/IEC 27002 for Privacy Information Management—Requirements and Guidelines; Standard, International Organization for Standardization: Rio de Janeiro, Brazil, 2019. [Google Scholar]
- Standard, International Organization for Standardization. ABNT NBR ISO/IEC 27002: 2015—Information Technology—Security Techniques—Code of Pratice for Information Security Controls; Standard, International Organization for Standardization: Rio de Janeiro, Brazil, 2015. [Google Scholar]
- Studer, T. A Universal Approach to Guarantee Data Privacy. Log. Universalis 2013, 7, 195–209. [Google Scholar] [CrossRef][Green Version]
- Brito, F.; Machado, J. Preservação de Privacidade de Dados: Fundamentos, Técnicas e Aplicações. J. Atualização Inform. 2017, 3, 40. [Google Scholar]
- Tamburri, D.A. Design principles for the General Data Protection Regulation (GDPR): A formal concept analysis and its evaluation. Inf. Syst. 2020, 91, 101469. [Google Scholar] [CrossRef]
- Jensen, M.; Kapila, S.; Gruschka, N. Towards Aligning GDPR Compliance with Software Development: A Research Agenda. In Proceedings of the 5th International Conference on Information Systems Security and Privacy, Prague, Czech Republic, 23–25 February 2019; SciTePress: Prague, Czech Republic, 2019; Volume 1, ICISSP, INSTICC. pp. 389–396. [Google Scholar] [CrossRef]
- Guamán, D.S.; Del Alamo, J.M.; Caiza, J.C. GDPR Compliance Assessment for Cross-Border Personal Data Transfers in Android Apps. IEEE Access 2021, 9, 15961–15982. [Google Scholar] [CrossRef]
- Daudén-Esmel, C.; Castellà-Roca, J.; Viejo, A.; Domingo-Ferrer, J. Lightweight Blockchain-based Platform for GDPR-Compliant Personal Data Management. In Proceedings of the 2021 IEEE 5th International Conference on Cryptography, Security and Privacy (CSP), Zhuhai, China, 8–10 January 2021; pp. 68–73. [Google Scholar] [CrossRef]
- Daoudagh, S.; Marchetti, E.; Savarino, V.; Bernardo, R.D.; Alessi, M. How to Improve the GDPR Compliance through Consent Management and Access Control. Available online: https://www.scitepress.org/Papers/2021/102602/102602.pdf (accessed on 10 April 2021).
- Diamantopoulou, V.; Androutsopoulou, A.; Gritzalis, S.; Charalabidis, Y. Preserving Digital Privacy in e-Participation Environments: Towards GDPR Compliance. Information 2020, 11, 117. [Google Scholar] [CrossRef]
- Carauta Ribeiro, R.; Dias Canedo, E. Using MCDA for Selecting Criteria of LGPD Compliant Personal Data Security. In Proceedings of the The 21st Annual International Conference on Digital Government Research, dg.o ’20, Seoul, Korea, 17–19 June 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 175–184. [Google Scholar] [CrossRef]
- Carvalho, A.P.; Canedo, E.D.; Carvalho, F.P.; Carvalho, P.H.P. Anonymisation and Compliance to Protection Data: Impacts and Challenges into Big Data. In Proceedings of the ICEIS (1), SCITEPRESS, Prague, Czech Republic, 5–7 May 2020; pp. 31–41. [Google Scholar] [CrossRef]
- Regulation, G.D.P. EU Data Protection Rules. 2018. Available online: https://ec.europa.eu/commission/priorities/justice-and-fundamental-rights/data-protection/2018-reform-eu-data-protection-rules_en (accessed on 8 March 2021).
- Potiguara Carvalho, A.; Potiguara Carvalho, F.; Dias Canedo, E.; Potiguara Carvalho, P.H. Big Data, Anonymisation and Governance to Personal Data Protection. In Proceedings of the dg.o ’20: The 21st Annual International Conference on Digital Government Research, Aguascalientes, Mexico, 18–21 June 2020; Association for Computing Machinery: New York, NY, USA, 2020; pp. 185–195. [Google Scholar] [CrossRef]
- Oliveira, N.S.d. Segurança da Informação para Internet das Coisas (IoT): Uma Abordagem sobre a Lei Geral de Proteção de Dados (LGPD). Rev. Eletronica De Iniciação Cient. Em Comput. 2019, 17. Available online: https://seer.ufrgs.br/reic/article/view/88790 (accessed on 10 April 2021).
- Silva, J.; Calegari, N.; Gomes, E. After Brazil’s general data protection law: Authorization in decentralized web applications. In Proceedings of the Companion, 2019 World Wide Web Conference, San Francisco, CA, USA, 13–17 May 2019; Association for Computing Machinery: New York, NY, USA, 2019; pp. 819–822. [Google Scholar]
- Pattakou, A.; Mavroeidi, A.; Diamantopoulou, V.; Kalloniatis, C.; Gritzalis, S. Towards the Design of Usable Privacy by Design Methodologies. In Proceedings of the 2018 IEEE 5th International Workshop on Evolving Security Privacy Requirements Engineering (ESPRE), Banff, AB, Canada, 20 August 2018; IEEE: Banff, AB, Canada, 2018; pp. 1–8. [Google Scholar] [CrossRef]
- Carvalho, L.P.; Oliveira, J.; Cappelli, C. Pesquisas em Análise de Redes Sociais e LGPD, análises e recomendações. In Proceedings of the Anais do IX Brazilian Workshop on Social Network Analysis and Mining; SBC: Porto Alegre, RS, Brasil, 2020; pp. 73–84. [Google Scholar] [CrossRef]
- Sabino, R. Gestão da Segurança da Informação Orientado a LGPD: Impactos da Implantação das Normas LGPD nos Processos da ADM SISTEMAS LTDA. 2020. Available online: http://www.riuni.unisul.br/handle/12345/9664 (accessed on 10 April 2021).
- Celidonio, T.; Neves, P.S.; Doná, C.M. Metodologia para mapeamento dos requisitos listados na LGPD (Lei Geral de Proteção de Dados do Brasil número 13.709/18) e sua adequação perante a lei em uma instituição financeira-Um estudo de caso/Methodology for mapping and adequacy of the requirements listed in LGPD (Brazil Data Protection General Law number 13 709/18) in a financial institution-A case study. Braz. J. Bus. 2020, 2, 3626–3648. [Google Scholar]
- Alves, P.H.C.; Frajhof, I.Z.; Correia, F.A.; de Souza, C.S.; Lopes, H. Second layer data governance for permissioned blockchains: The privacy management challenge. arXiv 2020, arXiv:2010.11677. [Google Scholar]
- Morte, A.B.; Meira, A.; Costa, R.; Mariz, D. Uma Análise Sobre o Uso de DLTs no Tratamento de Dados Pessoais: Aderência aos Princípios e Direitos elencados na LGPD. Available online: https://sol.sbc.org.br/index.php/wblockchain/article/view/12435 (accessed on 10 April 2021).
- Da Silva, M.V.V.; da Luz Scherf, E.; da Silva, J.E. The Right to Data Protection versus “Security”: Contradictions of the Rights-discourse in the Brazilian General Personal Data Protection Act (LGPD). Rev. Direitos Cult. Cult. Rights Rev. 2020, 15, 36. [Google Scholar] [CrossRef]
- Kshetri, N.; DeFranco, F.J. The Economics of Cyberattacks on Brazil. Computer 2020, 53, 85–90. [Google Scholar] [CrossRef]
- Freitas, M.d.C.; Mira da Silva, M. GDPR Compliance in SMEs: There is much to be done. J. Inf. Syst. Eng. Manag. 2018, 3, 30. [Google Scholar] [CrossRef]
- Presthus, W.; Sørum, H.; Andersen, L.R. GDPR Compliance in Norwegian Companies. In Norsk konferanse for organisasjoners bruk at IT; Nokobit: Svalbard, Norway, 2018; Volume 26. [Google Scholar]
- Li, Z.S.; Werner, C.; Ernst, N.; Damian, D. Gdpr compliance in the context of continuous integration. arXiv 2020, arXiv:2002.06830. [Google Scholar]
- Lee, A.; Carver, J.C.; Bosu, A. Understanding the impressions, motivations, and barriers of one time code contributors to FLOSS projects: A survey. In Proceedings of the ICSE, Buenos Aires, Argentina, 20–28 May 2017; IEEE: New York, NY, USA, 2017; pp. 187–197. [Google Scholar] [CrossRef]




Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ferrão, S.É.R.; Carvalho, A.P.; Canedo, E.D.; Mota, A.P.B.; Costa, P.H.T.; Cerqueira, A.J. Diagnostic of Data Processing by Brazilian Organizations—A Low Compliance Issue. Information 2021, 12, 168. https://doi.org/10.3390/info12040168
Ferrão SÉR, Carvalho AP, Canedo ED, Mota APB, Costa PHT, Cerqueira AJ. Diagnostic of Data Processing by Brazilian Organizations—A Low Compliance Issue. Information. 2021; 12(4):168. https://doi.org/10.3390/info12040168
Chicago/Turabian StyleFerrão, Sâmmara Éllen Renner, Artur Potiguara Carvalho, Edna Dias Canedo, Alana Paula Barbosa Mota, Pedro Henrique Teixeira Costa, and Anderson Jefferson Cerqueira. 2021. "Diagnostic of Data Processing by Brazilian Organizations—A Low Compliance Issue" Information 12, no. 4: 168. https://doi.org/10.3390/info12040168
APA StyleFerrão, S. É. R., Carvalho, A. P., Canedo, E. D., Mota, A. P. B., Costa, P. H. T., & Cerqueira, A. J. (2021). Diagnostic of Data Processing by Brazilian Organizations—A Low Compliance Issue. Information, 12(4), 168. https://doi.org/10.3390/info12040168






