Monitoring Real Time Security Attacks for IoT Systems Using DevSecOps: A Systematic Literature Review
Abstract
1. Introduction
2. Research Methodology
2.1. Review Questions (RQs)
2.2. Review Protocol
- using research questions to define major terms through recognizing population, context, intervention, and outcome;
- identifying synonyms and alternative spellings for each major term;
- verifying the search terms in titles, abstracts, and keywords;
- utilizing the Boolean conjunction operator and/or when producing a search string.
- Inclusion criteria:
- written in English;
- related to IoT attack detection;
- published in a journal or conference;
- peer-reviewed papers.
- Exclusion criteria:
- focused on detection methods other than machine learning;
- without empirical analysis or results;
- without surveys;
- the full text is not available.
2.3. Data Extraction
3. Result
3.1. Datasets
3.2. Machine Learning Techniques
3.3. IoT attacks
3.4. Independent Variables
3.5. Evaluation Metrics
3.6. DevSecOps
4. Discussion
Study Limitations
5. Conclusions and Future Work
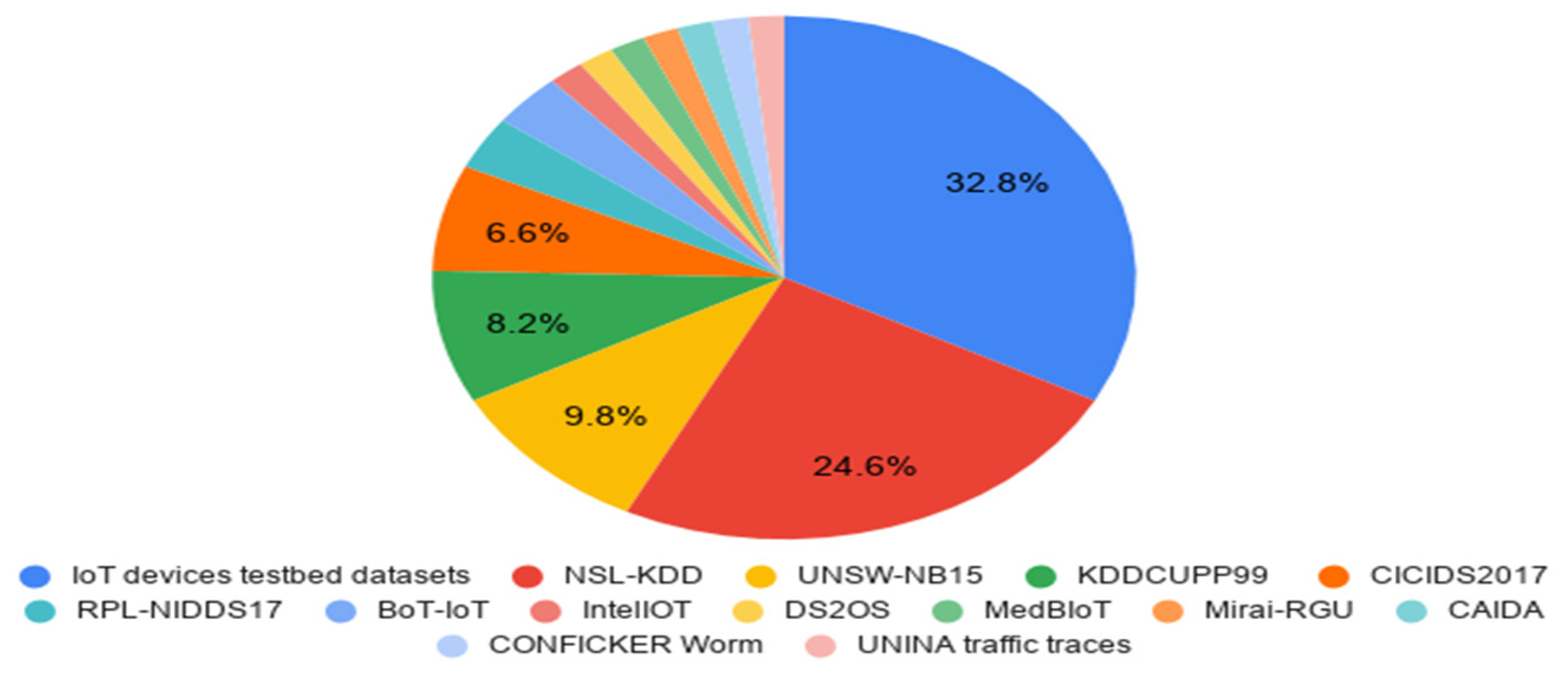
- Most primary studies used IoT device testbed datasets, and others used public datasets. NSL-KDD, UNSW-NB15, and KDDCUP99 repositories were found to be the most frequently used datasets among researchers.
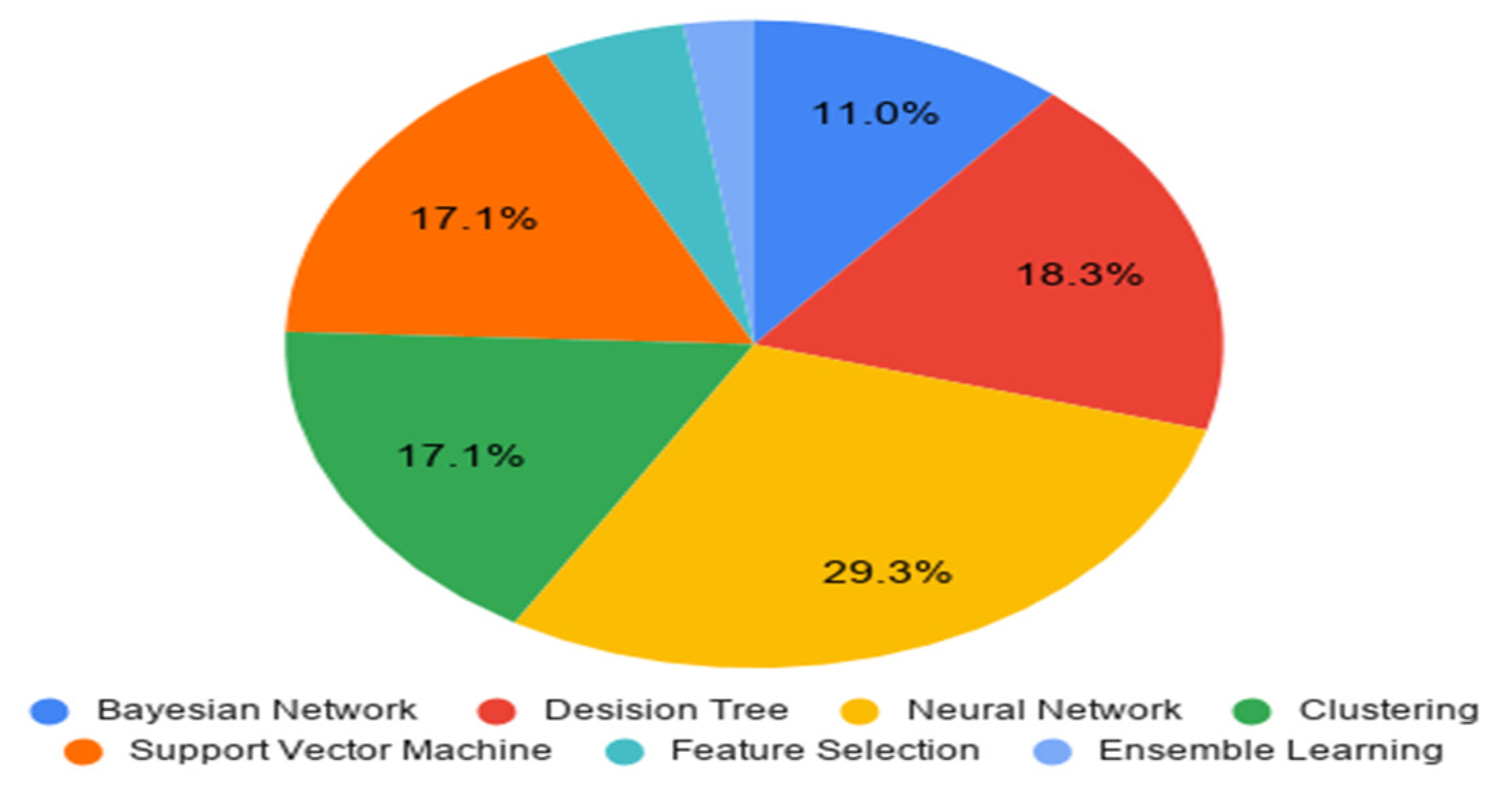
- BN, DT, NN, clustering, SVM, FS, and EL were the ML techniques used in primary studies, and NNs were the most widely used technique for IoT attack detection.
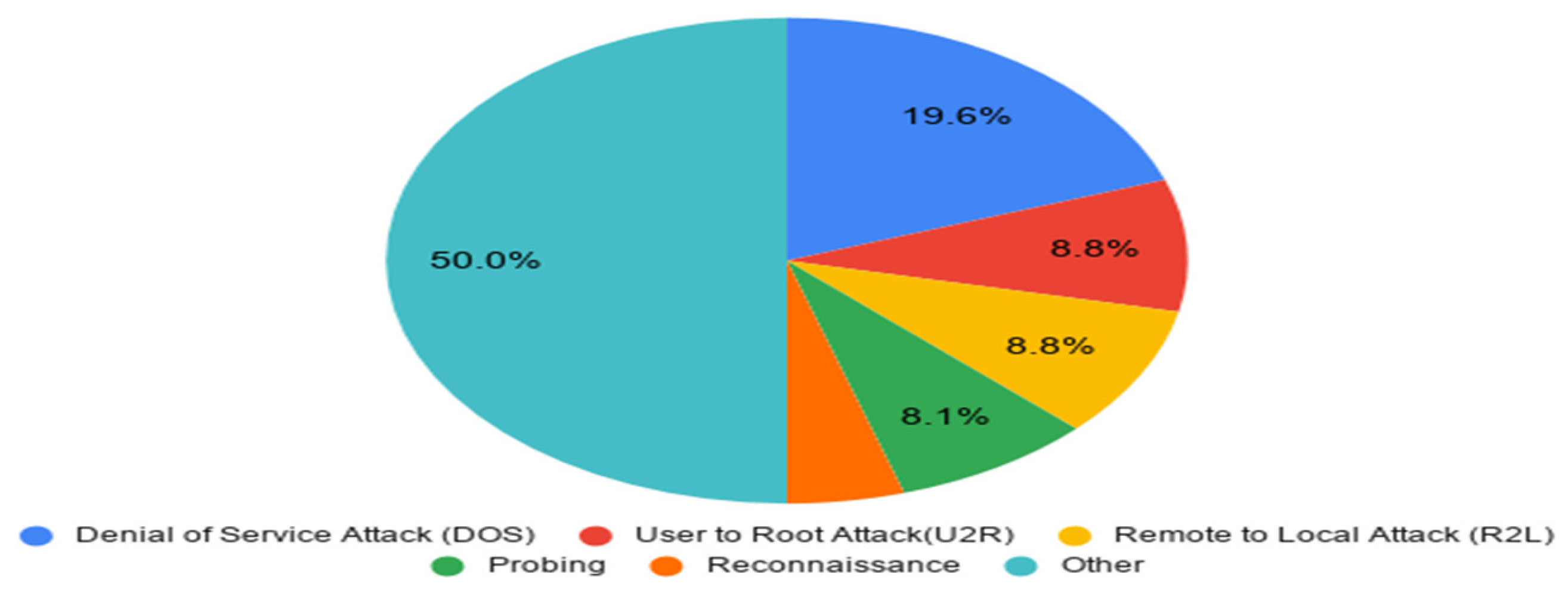
- DOS, U2R, and R2L attacks were most widely considered in the primary studies based on the results we obtained.
- Accuracy, recall, and precision were the most widely used evaluation metrics in the primary studies.
- Few studies analyzed device log traces from IoT devices to identify IoT attacks and monitor infrastructure using DevSecOps pipelines.
- More data preprocessing and data cleaning techniques should be applied to improve the quality of public datasets.
- Using data from real IoT device traffic will enhance the effectiveness of ML techniques.
- The performance of IoT attack detection models should continue to be enhanced through integration with other algorithms.
- Infrastructure configuration should continue to be monitored using methods based on software pipelines.
- Machine learning techniques should be used for advanced supervision and monitoring.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Mehta, R.; Sahni, J.; Khanna, K. Internet of things: Vision, applications and challenges. Procedia Comput. Sci. 2018, 132, 1263–1269. [Google Scholar] [CrossRef]
- ISO/IEC International Standard 20924. Information Technology-Internet of Things-Definition and Vocabulary. 2018. Available online: https://www.iso.org/standard/69470.html. (accessed on 30 March 2021).
- Yang, Z.; Liang, B.; Ji, W. An Intelligent end-edge-cloud architecture for visual iot assisted healthcare systems. IEEE Internet Things J. 2021, 8. [Google Scholar] [CrossRef]
- Jiang, X.; Zhang, H.; Yi, E.A.B.; Raghunathan, N.; Mousoulis, C.; Chaterji, S.; Dimitrios, P.; Shakouri, A.; Bagchi, S. Hybrid low-power wide-area mesh network for iot applications. IEEE IoT J. 2020, 8, 901–915. [Google Scholar] [CrossRef]
- Jadhav, A.R.; MPR, S.K.; Pachamuthu, R. Development of a novel iot-enabled power-monitoring architecture with real-time data visualization for use in domestic and industrial scenarios. IEEE Trans. Instrum. Measure. 2020, 70, 1–14. [Google Scholar] [CrossRef]
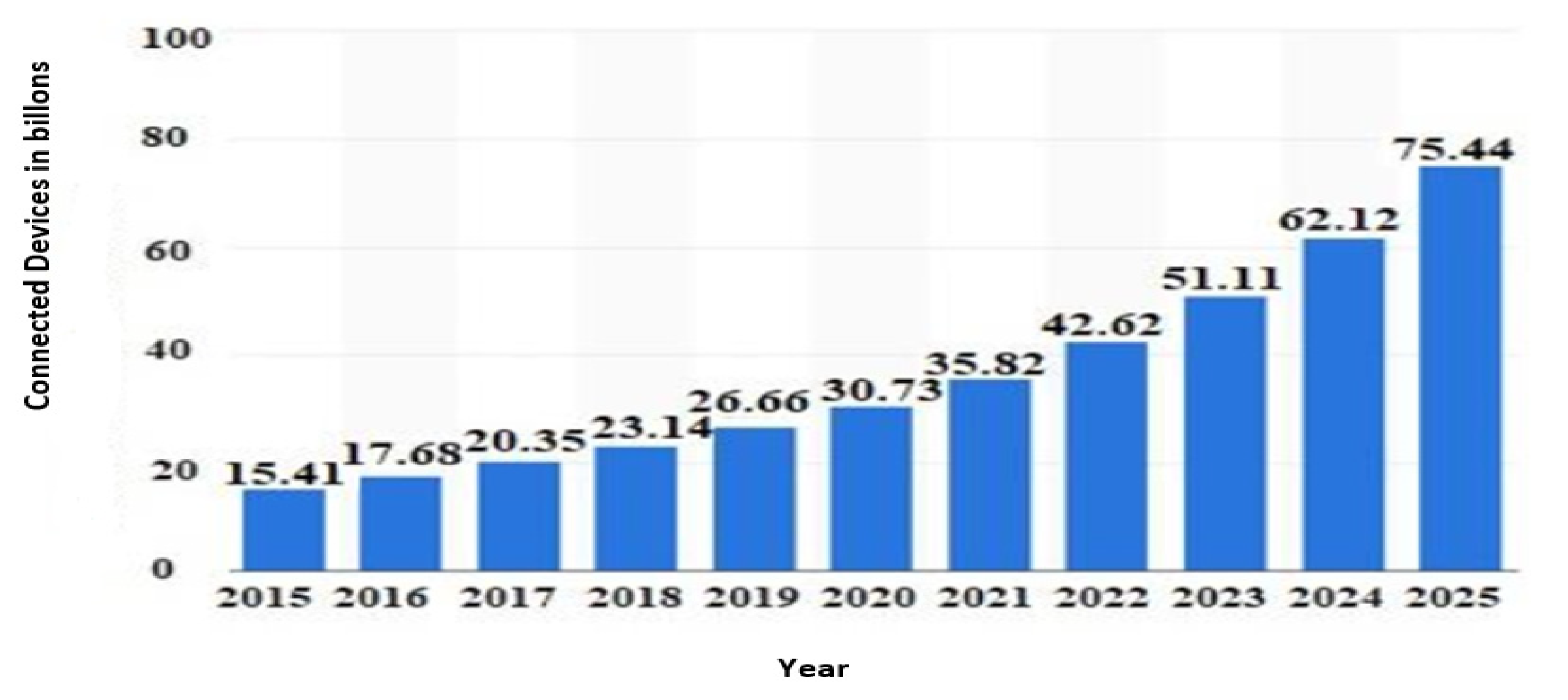
- Statista Report. Available online: https://www.statista.com/statistics/471264/iot number-of-connected-devices-worldwide (accessed on 2 January 2021).
- Alam, T. A reliable communication framework and its use in internet of things (IoT). Int. J. Sci. Res. Comp. Sci. Eng. Inf. Technol. 2018, 3. [Google Scholar] [CrossRef]
- Cyberattack Knocks Out Access to Websites. Available online: https://www.wsj.com/articles/denial-of-service-web-attack-affects-amazon-twitter-others-1477056080 (accessed on 2 January 2021).
- Sajjad, S.M.; Yousaf, M.; Afzal, H.; Muftid, M.R. eMUD: Enhanced manufacturer usage description for IoT botnets prevention on home WiFi routers. IEEE Access 2020, 8, 164200–164213. [Google Scholar] [CrossRef]
- Chen, S.; Xu, H.; Liu, D.; Hu, B.; Wang, H. A vision of IoT: Applications, challenges, and opportunities with china perspective. IEEE IoT J. 2014, 1, 349–359. [Google Scholar]
- Doshi, K.; Yilmaz, Y.; Uludag, S. Timely detection and mitigation of stealthy DDoS attacks via IoT networks. IEEE Trans. Dependable Secur. Comput. 2021, 1. [Google Scholar] [CrossRef]
- McAfee Labs COVID-19 Threats Report. Available online: https://www.mcafee.com/enterprise/en-us/assets/reports/rp-quarterlythreats-july-2020.pdf (accessed on 28 March 2021).
- Singh, S.; Hosen, A.S.; Yoon, B. Blockchain Security Attacks, Challenges, and Solutions for the Future Distributed IoT Network. IEEE Access 2021, 9, 13938–13959. [Google Scholar] [CrossRef]
- Chowdhury, M.R.; Tripathi, S.; De, S. Adaptive multivariate data compression in smart metering Internet of Things. IEEE Trans. Ind. Inform. 2020, 17, 1287–1297. [Google Scholar] [CrossRef]
- Makkar, A.; Garg, S.; Kumar, N.; Hossain, M.S.; Ghoneim, A.; Alrashoud, M. An efficient spam detection technique for IoT devices using machine learning. IEEE Trans. Ind. Inform. 2020, 17, 903–912. [Google Scholar] [CrossRef]
- Darko, A.; Vrček, N. Machine learning for the Internet of Things security: A systematic review. In Proceedings of the International Conference on Software Technologies (ICSOFT), Porto, Portugal, 26–28 July 2018; pp. 563–570. [Google Scholar] [CrossRef]
- Kavianpour, S.; Shanmugam, B.; Azam, S.; Zamani, M.; Samy, G.N.; De Boer, F. A systematic literature review of authentication in Internet of Things for heterogeneous devices. J. Comput. Netw. Commun. 2019, 2019, 1–14. [Google Scholar] [CrossRef]
- Meneghello, F.; Calore, M.; Zucchetto, D.; Polese, M.; Zanella, A. IoT: Internet of threats? A survey of practical security vulnerabilities in real IoT devices. IEEE IoT J. 2019, 6, 8182–8201. [Google Scholar] [CrossRef]
- Aly, M.; Khomh, F.; Haoues, M.; Quintero, A.; Yacout, S. Enforcing security in Internet of Things frameworks: A systematic literature review. IoT 2019, 6, 100050. [Google Scholar] [CrossRef]
- Ihsan, A.; Abdelmuttlib, I.A.A.; Almogren, A.; Raza, M.A.; Shah, S.A.; Khan, A.; Gani, A. Systematic literature review on IoT-based botnet attack. IEEE Access 2021, 8, 212220–212232. [Google Scholar]
- Hinderks, A.; José, F.; Mayo, D.; Thomaschewski, J.; Escalona, M.J. An SLR-tool: Search process in practice: A tool to conduct and manage systematic literature review (SLR). In Proceedings of the 2020 IEEE/ACM 42nd International Conference on Software Engineering: Companion Proceedings (ICSE-Companion), Seoul, Korea, 5–11 October 2020; pp. 81–84. [Google Scholar]
- Kitchenham, B.; Charters, S. Guidelines for Performing Systematic Literature Reviews in Software Engineering; School of Computer Science and Mathematics, Keele University: Staffordshire, UK, 2007. [Google Scholar]
- Anthi, E.; Williams, L.; Słowińska, M.; Theodorakopoulos, G.; Burnap, P. Pulse: An Adaptive Intrusion Detection for the Internet of Things, Living in the Internet of Things: Cybersecurity of the IoT. In Proceedings of the Living in the Internet of Things: Cybersecurity of the IoT—2018, London, UK, 28–29 March 2018; pp. 1–4. [Google Scholar]
- Anthi, E.; Williams, L.; Słowińska, M.; Theodorakopoulos, G.; Burnap, P. A supervised intrusion detection system for smart home IoT devices. IEEE IoT J. 2019, 6, 9042–9053. [Google Scholar] [CrossRef]
- Prachi, S. ML-IDS: A Machine Learning Approach to Detect Wormhole Attacks in Internet of Things. In Proceedings of the Intelligent Systems Conference (IntelliSys), London, UK, 7–8 September 2017; pp. 234–240. [Google Scholar]
- Bakhtiar, F.A.; Pramukantoro, E.S.; Nihri, H. A lightweight ids based on J48 algorithm for detecting dos attacks on IoT Middleware. In Proceedings of the IEEE 1st Global Conference on Life Sciences and Technologies (LifeTech), Osaka, Japan, 12–14 March 2019; pp. 41–42. [Google Scholar]
- Yahyaoui, A.; Abdellatif, T.; Attia, R. Hierarchical anomaly-based intrusion detection and localization in IoT. In Proceedings of the 15th International Wireless Communications & Mobile Computing Conference (IWCMC), Tangier, Morocco, 24–28 June 2019; pp. 108–113. [Google Scholar]
- Zolanvari, M.; Teixeira, M.A.; Gupta, L.; Khan, K.M.; Jain, R. Machine learning-based network vulnerability analysis of industrial Internet of Things. IEEE Internet Things J. 2019, 6, 6822–6834. [Google Scholar] [CrossRef]
- Bhatt, P.; Morais, A. HADS: Hybrid anomaly detection system for IoT environments. In Proceedings of the International Conference on Internet of Things, Embedded Systems and Communications (IINTEC), Hamammet, Tunisia, 20–21 December 2018; pp. 191–196. [Google Scholar]
- Ioannou, C.; Vassiliou, V. Classifying security attacks in IoT networks using supervised learning. In Proceedings of the 2019 15th International Conference on Distributed Computing in Sensor Systems (DCOSS), Santorini, Greece, 29–31 May 2019; pp. 652–658. [Google Scholar] [CrossRef]
- Bhunia, S.S.; Gurusamy, M. Dynamic attack detection and mitigation in IoT using SDN. In Proceedings of the 27th International Telecommunication Networks and Applications Conference (ITNAC), Melbourne, VIC, Australia, 22–24 November 2017; pp. 1–6. [Google Scholar]
- Nobakht, M.; Sivaraman, V.; Boreli, R. A host-based intrusion detection and mitigation framework for smart home IoT using OpenFlow. In Proceedings of the 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 147–156. [Google Scholar]
- Díaz, J.; Pérez, J.E.; Lopez-Peña, M.A.; Mena, G.A.; Yagüe, A. Self-service cybersecurity monitoring as enabler for devsecops. IEEE Access 2019, 7, 100283–100295. [Google Scholar] [CrossRef]
- Bhatia, R.; Benno, S.; Esteban, J.; Lakshman, T.V.; Grogan, J. Unsupervised machine learning for net-work-centric anomaly detection in IoT. In Proceedings of the 3rd ACM CoNEXT Workshop on Big DAta, Machine Learning and Artificial Intelligence for Data Communication Networks, New York, NY, USA, 1–5 December 2019. [Google Scholar]
- Chaabouni, N.; Mosbah, M.; Zemmari, A.; Sauvignac, C. An Intrusion Detection System for the OneM2M Service Layer Based on Edge Machine Learning; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Hashimoto, N.; Ozawa, S.; Ban, T.; Nakazato, J.; Shimamura, J. A darknet traffic analysis for IoT malwares using association rule learning. Procedia Comput. Sci. 2018, 144, 118–123. [Google Scholar] [CrossRef]
- Ozawa, S.; Ban, T.; Hashimoto, N.; Nakazato, J.; Shimamura, J. A study of IoT malware activities using association rule learning for darknet sensor data. Int. J. Inform. Secur. 2020, 19, 83–92. [Google Scholar] [CrossRef]
- Maleh, Y. Machine learning techniques for IoT intrusions detection in aerospace cyber-physical systems. In Machine Learning and Data Mining in Aerospace Technology; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Thamilarasu, G.; Chawla, S. Towards deep-learning-driven intrusion detection for the Internet of Things. Sensors 2019, 19, 1977. [Google Scholar] [CrossRef]
- Ioannou, C.; Vassiliou, V. Experimentation with local intrusion detection in IoT networks using supervised learning. In Proceedings of the 16th International Conference on Distributed Computing in Sensor Systems (DCOSS), Marina del Rey, CA, USA, 25–27 May 2020; pp. 423–428. [Google Scholar]
- Liu, Z.; Thapa, N.; Shaver, A.; Kaushik, R.; Xiaohong, Y.; Khorsandroo, S. Anomaly detection on loT network intrusion using machine learning. In Proceedings of the International Conference on Artificial Intelligence, Big Data, Computing and Data Communication Systems (icABCD), Durban, South Africa, 6–7 August 2020; pp. 1–5. [Google Scholar]
- Pecori, R.; Tayebi, A.; Vannucci, A.; Veltri, L. IoT Attack detection with deep learning analysis. In Proceedings of the International Joint Conference on Neural Networks (IJCNN), Glasgow, UK, 19–24 July 2020; pp. 1–8. [Google Scholar]
- Liang, C.; Shanmugam, B.; Azam, S.; Jonkman, M.; De Boer, F.; Narayansamy, G. Intrusion detection system for Internet of Things based on a machine learning approach. In Proceedings of the International Conference on Vision Towards Emerging Trends in Communication and Networking (ViTECoN), Vellore, India, 30–31 March 2019. [Google Scholar]
- Illy, P.; Kaddoum, G.; Moreira, C.M.; Kaur, K.; Garg, S. Securing fog-to-things environment using intrusion detection system based on ensemble learning. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Marrakesh, Morocco, 1 April 2019; pp. 1–7. [Google Scholar]
- Pajouh, H.H.; Javidan, R.; Khayami, R.; Dehghantanha, A.; Choo, K.K.R. A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Trans. Emerg. Top. Comp. 2016, 7, 314–323. [Google Scholar] [CrossRef]
- Abeshu, A.; Chilamkurti, N. Deep learning: The frontier for distributed attack detection in fog-to-things computing. IEEE Comm. Mag. 2018, 56, 169–175. [Google Scholar] [CrossRef]
- Shalaginov, A.; Semeniuta, O.; Alazab, M. MEML: Resource-Aware MQTT-Based Machine Learning for Network Atack Detection on IoT Edge Devices. In Proceedings of the 12th IEEE/ACM International Conference on Utility and Cloud Computing Companion (UCC’19 Companion), Auckland, New Zealand, 1–5 December 2019. [Google Scholar]
- Rezvy, S.; Petridis, M.; Lasebae, A.; Zebin, T. Intrusion Detection and Classification with Au-toencoded Deep Neural Network; Springer: Cham, Switzerland, 2019. [Google Scholar]
- Rathore, S.; Park, J.Y. Semi-supervised learning based distributed attack detection framework. Appl. Soft Comp. 2018, 72, 79–89. [Google Scholar] [CrossRef]
- Diro, A.A.; Chilamkurti, N. Distributed attack detection scheme using deep learning approach for Internet of Things. Future Gener. Comp. Syst. 2018, 82, 761–768. [Google Scholar] [CrossRef]
- Fenanir, S.; Semchedine, F.; Baadache, A. A machine learning-based lightweight intrusion detection system for the Internet of Things. Rev. d’Intelligence Artif. 2019, 33, 203–211. [Google Scholar] [CrossRef]
- Verma, A.; Ranga, V. Machine learning based intrusion detection systems for IoT applications. Wireless Pers Commun. 2019, 111, 2287–2310. [Google Scholar] [CrossRef]
- Zhang, J.; Gong, L.R.; Yu, K.; Qi, X.; Wen, Z.; Hua, Q. 3D reconstruction for super-resolution CT images in the Internet of health things using deep learning. IEEE Access 2020, 8, 121513–121525. [Google Scholar] [CrossRef]
- Taghavinejad, S.M.; Taghavinejad, M.; Shahmiri, L.; Zavvar, M.; Zavvar, M.H. Intrusion detection in IoT-based smart grid using hybrid decision tree. In Proceedings of the 6th International Conference on Web Research (ICWR), Tehran, Iran, 22–23 April 2020; pp. 152–156. [Google Scholar]
- Al-Emadi, S.; Al-Mohannadi, A.; Al-Senaid, F. Using deep learning techniques for network intrusion detection. In Proceedings of the IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), Doha, Qatar, 2–5 February2020; pp. 171–176. [Google Scholar]
- de Souzaa, C.A.; Becker Westphalla, C.; Bobsin Machadob, R.; Mangueira Sobrala, B.; dos Santos Vieirab, G. Hybrid approach to intrusion detection in fog-based IoT environments. Comp. Netw. 2020, 180, 107417. [Google Scholar] [CrossRef]
- Rani, D.; Kaushal, N.C. Supervised machine learning based network intrusion detection system for Internet of Things. In Proceedings of the 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Kharagpur, India, 1–3 July 2020; pp. 1–7. [Google Scholar]
- Zhao, S.; Li, W.; Zia, T.; Zomaya, A.Y. A dimension reduction model and classifier for anomaly-based intrusion detection in Internet of Things. In Proceedings of the 2017 IEEE 15th Intl Conf on Dependable, Autonomic and Secure Computing, 15th Intl Conf on Pervasive Intelligence and Computing, 3rd Intl Conf on Big Data Intelligence and Computing and Cyber Science and Technology Congress(DASC/PiCom/DataCom/CyberSciTech), Orlando, FL, USA, 6–10 November 2017; pp. 836–843. [Google Scholar]
- Indre, I.; Lemnaru, C. Detection and prevention system against cyber attacks and botnet malware for information systems and internet of things. In Proceedings of the 12th International Conference on Intelligent Computer Communication and Processing (ICCP), Cluj-Napoca, Romania, 8–10 September 2016; pp. 175–182. [Google Scholar]
- Dwivedi, S.; Vardhan, M.; Tripathi, S. Distributed denial-of-service prediction on IoT framework by learning techniques. Open Comput. Sci. 2020, 10, 220–230. [Google Scholar] [CrossRef]
- Bipraneel, R.; Cheung, H. A deep learning approach for intrusion detectionin internet of things using BI-directional long short-term memory recurrent neural network. In Proceedings of the 28th International Telecommunication Networks and Applications Conference (ITNAC), Sydney, NSW, Australia, 21–23 November 2018. [Google Scholar]
- Hanif, S.; Ilyas, T.; Zeeshan, M. Intrusion detection in IoT using artificial neural networks on UNSW-15 Dataset. In Proceedings of the 2019 IEEE 16th International Conference on Smart Cities: Improving Quality of Life Using ICT & IoT and AI (HONET-ICT), Charlotte, NC, USA, 6–9 October 2019; pp. 152–156. [Google Scholar]
- Latif, S.; Idrees, Z.; Zou, Z.; Ahmad, J. DRaNN: A deep random neural network model for intrusion detection in industrial IoT. In Proceedings of the International Conference on UK-China Emerging Technologies (UCET), Glasgow, UK, 20–21 August 2020; pp. 1–4. [Google Scholar]
- Chkirbene, Z.; Eltanbouly, S.; Bashendy, M.; Alnaimi, N.; Erbad, A. Hybrid machine learning for network anomaly intrusion detection. In Proceedings of the IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), Doha, Qatar, 2–5 February 2020; pp. 163–170. [Google Scholar]
- Verma, A.; Ranga, V. ELNIDS: Ensemble Learning based Network Intrusion Detection System for RPL based Internet of Things. In Proceedings of the 4th International Conference on Internet of Things: Smart Innovation and Usages (IoT-SIU), Ghaziabad, India, 18–19 April 2019; pp. 1–6. [Google Scholar]
- Shakhov, V.; Ullah Jan, S.; Ahmed, S. On Lightweight method for intrusions detection in the Internet of Things. In Proceedings of the International Black Sea Conference on Communications and Networking (BlackSeaCom), Sochi, Russia, 3–6 June 2019; pp. 1–5. [Google Scholar]
- Ge, M.; Fu, X.; Syed, N.; Baig, Z.; Teo, G.; Robles-Kelly, A. Deep learning-based intrusion detection for IoT networks. In Proceedings of the 24th Pacific Rim International Symposium on Dependable Computing (PRDC), Kyoto, Japan, 1–3 December 2019; pp. 256–266. [Google Scholar]
- Hosseini, M.; Borojeni, H.R.S. A hybrid approach for anomaly detection in the Internet of Things. In Proceedings of the Proceedings of the International Conference on Smart Cities and Internet of Things-SCIOT’18, Mashhad, Iran, 1–3 September 2018. [Google Scholar]
- Latif, S.; Zou, Z.; Idrees, Z.; Ahmad, J. A novel attack detection scheme for the industrial internet of things using a lightweight random neural network. IEEE Access 2020, 8, 89337–89350. [Google Scholar] [CrossRef]
- Roopak, M.; Tian, G.Y.; Chambers, J. Intrusion detection system against ddos attacks in loT networks. In Proceedings of the 10th Annual Computing and Communication Workshop and Conference (CCWC), Las Vegas, NV, USA, 6–8 January 2020; pp. 0562–0567. [Google Scholar]
- Alzahrani, H.; Abulkhair, M.; Alkayal, E. A multi-class neural network model for rapid detection of IoT botnet attacks. Int. J. Adv. Comp. Sci. Appl. 2020. [Google Scholar] [CrossRef]
- Alsaedi, A.; Moustafa, N.; Tari, Z.; Mahmood, A.; Anwar, A. TON_IoT telemetry dataset: A new generation dataset of IoT and IIoT for data-driven intrusion detection systems. IEEE Access 2020, 8, 165130–165150. [Google Scholar] [CrossRef]
- Yahyaoui, A.; Abdellatif, T.; Yangui, S.; Attia, R. “READ-IoT: Reliable anomalies and events detection framework for the Internet of Things. IEEE Access 2021, 9, 24168–24186. [Google Scholar] [CrossRef]
- Wang, Z.; Zeng, Y.; Liu, Y.; Li, D. Deep belief network integrating improved kernel-based extreme learning machine for network intrusion detection. IEEE Access 2021, 9, 16062–16091. [Google Scholar] [CrossRef]
- Maseer, Z.K.; Yusof, R.; Bahaman, N.; Mostafa, S.A.; Foozy, C.F.M. Benchmarking of machine learning for anomaly based intrusion detection systems in the CICIDS2017 dataset. IEEE Access 2021, 9, 22351–22370. [Google Scholar] [CrossRef]
- Pu, G.; Wang, L.; Shen, J.; Dong, F. A hybrid unsupervised clustering-based anomaly detection method. Tsinghua Sci. Technol. 2021, 26, 146–153. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, J.; Li, J.; Song, H.; Yang, T.; Niu, S.; Ming, Z. Zero-bias deep learning for accurate identification of Internet-of-Things (IoT) devices. IEEE Internet Things J. 2021, 8, 2627–2634. [Google Scholar] [CrossRef]
- Nair, R.; Sharma, P.; Kumar Singh, D. Security Attacks in Internet of Things; Wiley Online Library Publishing: Hoboken, NJ, USA, 2020; Chapter 14; pp. 237–261. [Google Scholar] [CrossRef]
- Sharma, P.; Kherajani, M.; Jain, D.; Patel, D. A Study of Routing Protocols, Security Issues and Attacks in Network Layer of Internet of Things Framework. In Proceedings of the 2nd International Conference on Data, Engineering and Applications (IDEA), Bhopal, India, 28–29 February 2020; pp. 1–6. [Google Scholar]
- Raghuprasad, A.; Padmanabhan, S.; Babu, M.A.; Binu, P.K. Security analysis and prevention of attacks on IoT devices. In Proceedings of the International Conference on Communication and Signal Processing (ICCSP), Chennai, India, 28–30 July 2020; pp. 0876–0880. [Google Scholar]
- Rafi, S.; Yu, W.; Akbar, M.A.; AlSanad, A.; Gumaei, A. Prioritization based taxonomy of DevOps security challenges using PROMETHEE. IEEE Access 2020, 8, 105426–105446. [Google Scholar] [CrossRef]
- Mohan, V.; Othmane, L.B. SecDevOps: Is it a marketing buzzword?-Mapping research on security in DevOps. In Proceedings of the 11th International Conference on Availability, Reliability and Security (ARES), Salzburg, Austria, 31 August–2 September 2016; pp. 542–547. [Google Scholar]
- Carter, K. Francois Raynaud on DevSecOps. IEEE Softw. 2017, 34, 93–96. [Google Scholar] [CrossRef]
- Karapantelakis, A.; Liang, H.; Wang, K.; Vandikas, K.; Inam, R.; Fersman, E.; Mulas-Viela, I.; Seyvet, N.; Giannokostas, V. DevOps for IoT Applications using cellular networks and Cloud. In Proceedings of the IEEE 4th International Conference on Future Internet of Things and Cloud (FiCloud), Vienna, Austria, 22–24 August 2016; pp. 340–347. [Google Scholar]
- Lopez-Viana, R.; Diaz, J.; Diaz, V.H.; Martinez, J.-F. Continuous delivery of customized SaaS edge applications in highly distributed IoT systems. IEEE Internet Things J. 2020, 7, 10189–10199. [Google Scholar] [CrossRef]
- López-Peña, M.A.; Díaz, J.; Pérez, J.E.; Humanes, H. DevOps for IoT systems: Fast & continuous monitoring feedback of system availability. IEEE Internet Things J. 2020, 7, 10695–10707. [Google Scholar] [CrossRef]

| Population | IoT Attack Detection |
|---|---|
| Intervention | Machine learning techniques |
| Comparison | Not available |
| Outcomes | Monitoring real-time security attacks for IoT systems using DevSecOps pipelines |
| Context | Review the existing studies monitoring real-time security attacks for IoT systems |
| Resource Name | Total Results | Initial Selection | Final Selection |
|---|---|---|---|
| IEEE Xplore | 248 | 90 | 35 |
| Science Direct | 746 | 84 | 3 |
| Springer Link | 1200 | 150 | 4 |
| ACM | 475 | 53 | 2 |
| Scopus | 229 | 46 | 5 |
| Total | 2898 | 423 | 49 |
| Characteristic | Research Question |
|---|---|
| Authors, study title, publication year, publication title, source, source type | General |
| IoT attack datasets | RQ1 |
| IoT attack detection machine learning techniques | RQ2 |
| Type of IoT attacks | RQ3 |
| Dependent/independent variables | RQ4 |
| Performance measures | RQ5 |
| Monitoring real-time security for IoT systems using DevSecOps pipelines | RQ6 |
| S.No | Reference | ML Techniques | IoT Attacks | Evaluation Metrics | Monitoring Real-Time Security Using DevSecOps |
|---|---|---|---|---|---|
| S1 | (Eirini et al., 2018) [23] | BN. | Probing, and DOS | Precision, recall, and F-measure. | No. |
| S3 | (Eirini et al., 2019) [24] | BN and DT. | DOS, MITM, reconnaissance, and replay. | Precision, recall, and F-measure. | No. |
| S6 | (Prachi et al., 2017) [25] | DT and Clustering. | Wormhole | Detection rate. | No. |
| S7 | (Fariz et al., 2019) [26] | DT | DOS | Accuracy. | No. |
| S8 | (Aymen et al., 2019) [27] | SVM | Selective forwarding attack. | Accuracy. | No. |
| S10 | (Maede et al., 2019) [28] | DT, SVM and NN. | Backdoor, command injection, and SQL injection. | Accuracy, false alarm rate, ROC curve, and sensitivity matric. | No. |
| S17 | (Parth et al., 2018) [29] | NN. | DOS. | Accuracy, true positive rate, and false positive rate. | No. |
| S18 | (Christiana et al., 2019) [30] | SVM. | Selective forwarding, and blackhole. | Accuracy. | No. |
| S20 | (Suman et al., 2017) [31] | SVM. | DOS. | Precision and recall. | No. |
| S21 | (Mehdi et al., 2016) [32] | SVM. | DOS and DDoS. | Precision and recall. | No. |
| S22 | (Jessica et al., 2019) [33] | NN. | DOS | Detection rate. | Yes. |
| S24 | (Randeep et al., 2019) [34] | NN. | DOS | Precision, recall, and F-score. | No. |
| S26 | (Nadia et al., 2019) [35] | BN, DT and NN. | Amplification | Recall, accuracy, precision, and false positive rate. | No. |
| S30 | (Naoki et al., 2018) [36] | NN. | Wormhole | Detection rate. | No. |
| S31 | (Seiichi et al., 2019) [37] | NN. | Wormhole | Detection rate. | No. |
| S32 | (Yassine, 2019) [38] | DT, Clustering and NN. | Wormhole | Accuracy, precision, and recall. | No. |
| S33 | (Geethapriya et al., 2019) [39] | NN. | Wormhole | Precision, recall, and F1 score. | No. |
| S38 | (Christiana et al., 2020) [40] | SVM. | Blackhole and selective forwarding. | Accuracy, precision, negative predictive value (NPV), recall, and the Matthews correlation coefficient (MCC). | No. |
| S41 | (Zhipeng et al., 2020) [41] | SVM, clustering and DT. | DOS, scanning and MITM. | Accuracy, recall, and F1 score | No. |
| S47 | (Riccardo et al., 2020) [42] | BN. | DOS, scanning and MITM | Accuracy, precision, recall, and F-measure | No. |
| S.No | Reference | ML Techniques | IoT Attacks | Evaluation Metrics | Monitoring Real-Time Security Using DevSecOps | Other Datasets Used |
|---|---|---|---|---|---|---|
| S5 | (Chao et al., 2019) [43] | NN. | DOS, U2R and R2L. | Accuracy, precision, and recall. | No. | - |
| S9 | (Poulmanogo et al., 2019) [44] | DT and NB. | Probing, U2R and R2L. | Accuracy. | No. | KDDCUP99. |
| S12 | (Hamed et al., 2019) [45] | Clustering and NB. | U2R and R2L. | Detection rate, and false alarm rate. | No. | - |
| S13 | (Abebe et al., 2018) [46] | NN. | Probing, U2R and R2L. | Accuracy, detection rate, false alarm rate and ROC curve. | No. | - |
| S25 | (Andrii et al., 2019) [47] | NN. | Probing, DOS, U2R and R2L. | Detection rate. | No. | - |
| S27 | (Shahadate et al., 2019) [48] | NN. | Probing. | Accuracy. | No. | - |
| S28 | (Shailendra et al., 2018) [49]. | Clustering. | Probing, DOS, U2R and R2L. | Accuracy, sensitivity, F-score and positive predictive value | No. | - |
| S29 | (Abebe et al., 2018) [50] | NN. | Probing, U2R and R2L. | Accuracy, detection rate, false alarm rate, precision, and recall. | No. | - |
| S34 | (Samir et al., 2019) [51] | BN, DT and Clustering. | DOS, Reconnaissance U2R, R2L., Backdoor, Analysis, generic, fuzzers, and shellcode. | Accuracy, false positive rate, precision, and F1-Score. | No. | UNSW-NB15 and KDDCUP99. |
| S35 | (Abhishek et al., 2019) [52] | DT. | DOS | Accuracy, specificity, sensitivity and false positive rate. | No. | CICIDS2017 and UNSW-NB15. |
| S37 | (AHMED et al., 2020) [53] | NN. | DOS and SQL injection. | Accuracy, precision and recall. | No. | UNSW-NB15, CICIDS2017, RPL-NIDDS17 and BoT-IoT |
| S39 | (Seyedeh et al., 2020) [54] | SVM, DT, Clustering. | DOS, U2R and R2L. | Accuracy, precision, recall, and F1-score | No. | - |
| S44 | (Sara et al., 2020) [55] | NN. | U2R and R2L. | Accuracy, F1-score, precision, and recall. | No. | - |
| S45 | (Cristiano et al., 2020) [56] | NN and clustering. | DOS. | Accuracy, Fl-score, precision, and recall | No. | CICIDS2017 |
| S46 | (Deepa et al., 2020) [57] | DT | Probing, DOS, U2R and R2L. | Accuracy, Fl-score, precision and recall. | No. | KDDCUP99. |
| S.No | Reference | ML Techniques | IoT Attacks | Evaluation Metrics | Monitoring Real-Time Security Using DevSecOps | Other Datasets Used |
|---|---|---|---|---|---|---|
| S4 | (Shengchu et al., 2017) [58] | Clustering. | Probing, DOS, U2R, and R2L. | Detection rate, false alarm rate and Accuracy | No. | - |
| S11 | (Ionut et al., 2016) [59] | DT, SVM and Clustering. | Probing, DOS, U2R, and R2L. | Precision. | No. | - |
| S48 | (Shubhra et al., 2020) [60] | SVM and BN. | DDoS | Accuracy, sensitivity, specificity, precision, f-measure, AUC (Area under curve) and false positive rate | No. | CAIDA, CONFICKER Worm, and UNINA traffic traces. |
| S.No | Reference | ML Techniques | IoT Attacks | Evaluation Metrics | Monitoring Real-Time Security Using DevSecOps | Other Datasets Used |
|---|---|---|---|---|---|---|
| S16 | (Bipraneel et al., 2018) [61] | NN. | Reconnaissance, DOS, wormhole and backdoor. | Accuracy, precision, recall, F-measure, miscalculation rate, and detection rate. | No. | - |
| S19 | (Sohaib et al., 2019) [62] | NN. | Reconnaissance, DOS, probing, wormhole and backdoor. | Accuracy and precision | No. | - |
| S36 | (Shahid et al., 2020) [63] | NN. | Reconnaissance, DOS, wormhole, exploits and backdoor. | Accuracy. | No. | - |
| S42 | (Zina et al., 2020) [64] | DT. | Reconnaissance, DOS, wormhole and backdoor. | Accuracy | No. | - |
| S.No | Reference | ML Techniques | IoT Attacks | Evaluation Metrics | Monitoring Real-Time Security Using DevSecOps | Used Datasets |
|---|---|---|---|---|---|---|
| S2 | (Abhishek et al., 2019) [65] | EL | Sinkhole, local repair attacks, blackhole, sybil, DDOS, hello flooding and selective forwarding. | Accuracy and AUC | No. | RPL-NIDDS17 |
| S14 | (Vladimir et al., 2019) [66] | SVM, NN and Clustering. | DOS | Accuracy | No. | CICIDS2017 |
| S15 | (Mengmeng et al., 2019) [67] | NN. | Information theft attacks, DDOS, reconnaissance and DOS. | Accuracy, precision, recall, and F-measure. | No. | BoT-IoT |
| S23 | (Mostafa et al., 2018) [68] | Clustering. | Probing, DOS, U2R and R2L. | Detection rate, False Positive rate and Accuracy. | No. | intelIoT |
| S40 | (SHAHID et al., 2020) [69] | NN. | Probing and DOS. | Accuracy, precision, recall and F1 score. | No. | DS2OS |
| S43 | (Monika et al., 2020) [70] | NN. | DDOS. | Accuracy, Fl-score, precision, and recall | No. | CICIDS2017 |
| S49 | (Haifaa et al., 2020) [71] | NN. | DOS. | F1 score | No. | MedBIoT. |
| IoT Attack | Layer |
|---|---|
| DoS | Network layer and application layer. |
| U2R | Application layer. |
| R2L | Network layer and perception layer. |
| Probing | Network layer. |
| Reconnaissance | Network layer. |
| wormhole | Processing layer. |
| DDoS | Network layer and application layer. |
| backdoor | Application layer. |
| analysis | Application layer. |
| generic | Application Layer. |
| fuzzers | Network layer and perception layer. |
| shellcode | Processing layer. |
| sinkhole | Network layer. |
| blackhole | Perception layer. |
| hello flooding | Network layer. |
| SQL injection | Processing layer. |
| ARP cache poisoning | Network layer. |
| Malformed packets | Application layer. |
| Exploits | Network layer. |
| Scanning | Network layer. |
| Datasets | IoT Attack Type | Features |
|---|---|---|
| NSL-KDD | DoS | back, teardrop, Neptune, land, smurf, and pod. |
| U2R | buffer overflow, perl, rootkit, and load module. | |
| Probing | Satan, ipsweep, portsweep, and nmap. | |
| R2L | multihop, warezmaster, FTP write, guess password, phf, spy, imap, and warezclient. | |
| UNSW-NB15 | Fuzzers, analysis, reconnaissance, backdoors, generic, DoS, exploits, worms, and shellcode | destination, service, source mean, source byte, source to destination time, mean size, source inter-packet arrival time, data transferred, protocol, number of connections, and number of flows. |
| KDDCUPP99 | Probing | nmap, satan, ipsweep, saint, portsweep, and mscan. |
| U2R | perl, sqlattack, Httptunnel, buffer_overflow, ps, rootkit, xterm, and loadmodule. | |
| R2L | Xlock, xsnoop, phf, snmpguess, warezclient, named, warezmaster, tp_write, spy, guess_passwd, imap, snmpgetattack, worm, and multihop. | |
| DoS | Neptune, back, teardrop, mailbomb, land, processtable, apache2, udpstorm, smurf, and pod. | |
| CICIDS2017 | DDoS | Source, time stamps, and destination IP addresses. |
| RPL-NIDDS17 | Sinkhole, Sybil, Clone ID, Blackhole, Hello Flooding, Selective Forwarding, and Local Repair attacks | Destination IP address, protocols used, time of the attack, and size of packets transmitted. |
| BoT-IoT | probing, DOS, and DDOS | frame-related fields, ARP-related fields, IP-related fields, TCP-related fields, and UDP-related fields. |
| S.No | Features |
|---|---|
| S1 | destination IP address, protocols used, time of the attack, and size of packets transmitted. |
| S3 | Frame information and packet type. |
| S6 | Safe distance between any two neighboring routers. |
| S7 | Flags, Ip_len, TCP4_flood, UDP_Flood, TCP6_Flood, UDP6_Low, and IP6_plen. |
| S8 | Packet receiving rate and consumed energy. |
| S10 | mean flow (mean), destination, source bytes, source packets, source port, and total load. |
| S17 | two classes: connection features (e.g., duration of connection, packets per second, average size of data message, and data rate) and traffic features (e.g., active connections on a specific port, active connections on all hosts, rate of active connections on a specific host, rate of active connections for a service, and active connections on a specific host port). |
| S18 | Data packets sent, packets forwarded, packets dropped, announcements received, and data packets received. |
| S20 | bandwidth consumption, source of requests, number of failed authentication attempts, number of sent requests, and device usage at different periods. |
| S21 | the number of bytes in acknowledgment response packets, the number of bytes in command packets, and inter-packet time interval. |
| S22 | level, time, source IP, and packet type. |
| S24 | source bytes, average packet size of traffic, and destination. |
| S26 | request identifier, destination, and response status code. |
| S30 | sequence number, destination port, and window size. |
| S31 | window size, sequence number, and destination port. |
| S32 | duration of connection, rate transmission, and destination. |
| S33 | transmission rate, reception rate, source IP, and destination. |
| S38 | packets forwarded, packets dropped, data packets sent, and announcements received. |
| S41 | destination IP address of the packet, sequence number for the packet, time, source IP address of the packet, protocol, length of the packet, and info. |
| S47 | Duration, total forward packet, total backward packet, total length backward packet, total length forward packet, and idle minimum time. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bahaa, A.; Abdelaziz, A.; Sayed, A.; Elfangary, L.; Fahmy, H. Monitoring Real Time Security Attacks for IoT Systems Using DevSecOps: A Systematic Literature Review. Information 2021, 12, 154. https://doi.org/10.3390/info12040154
Bahaa A, Abdelaziz A, Sayed A, Elfangary L, Fahmy H. Monitoring Real Time Security Attacks for IoT Systems Using DevSecOps: A Systematic Literature Review. Information. 2021; 12(4):154. https://doi.org/10.3390/info12040154
Chicago/Turabian StyleBahaa, Ahmed, Ahmed Abdelaziz, Abdalla Sayed, Laila Elfangary, and Hanan Fahmy. 2021. "Monitoring Real Time Security Attacks for IoT Systems Using DevSecOps: A Systematic Literature Review" Information 12, no. 4: 154. https://doi.org/10.3390/info12040154
APA StyleBahaa, A., Abdelaziz, A., Sayed, A., Elfangary, L., & Fahmy, H. (2021). Monitoring Real Time Security Attacks for IoT Systems Using DevSecOps: A Systematic Literature Review. Information, 12(4), 154. https://doi.org/10.3390/info12040154






