Abstract
In-band full duplex wireless medium access control (MAC) protocol is essential in order to enable higher layers of the protocol stack to exploit the maximum benefits from physical layer full duplex technology. Unlike half duplex wireless local area network, a full duplex MAC protocol has to deal with several unique issues and challenges that arise because of the dynamic nature of the wireless environment. In this paper, we have discussed several existing full duplex MAC protocols and have shown qualitative comparisons among these full duplex MAC protocols. Full duplex in-band wireless communication has the potential to double the capacity of wireless network. Inter-client Interference (ICI) is a hindrance in achieving double spectral efficiency of the in-band full-duplex wireless medium. In this paper, we have classified existing solutions to the ICI problem and compared the solutions with respect to the proposed approaches, their advantages and disadvantages.We have also identified and discussed several issues and challenges of designing a full duplex MAC protocol. Results of qualitative comparisons of various wireless full duplex MAC protocols may be applied to design new protocols as well as researchers may find the identified issues and challenges helpful to solve various problems of a full duplex MAC protocol.
1. Introduction
At present, wireless local area networks (WLANs) are half duplex. The physical layer technologies of current wLANs do not support transmission and reception of wireless signal at the same time in the same frequency band. The main hurdle to making wireless physical layer an in-band full duplex (FD) is the self-interference that results from the transmission signal of the sender’s antenna. The signal strength of self-interference is millions time higher than that of the received signal. But the recent advancement in self-interference cancellation has paved the path to develop full duplex antenna that can transmit and receive wireless signal simultaneously in the same frequency band [1,2]. Previous medium access control strategies for wLANs are developed and implemented taking into consideration that physical layer is half duplex in nature. Those strategies are standardized and integrated in wireless network interface cards. A recent development of an in-band full duplex antenna [3] which can transmit and receive signals at the same time in the same frequency has motivated the researchers to shift the wLANs physical layer technologies to a new paradigm. The authors [3] have shown that this full duplex antenna supports wide band and high power which makes it suitable for deployment in wireless devices to bring FD wireless LANs technologies a reality.
In-band full duplex radio provides several benefits over half duplex because it offers higher throughput and higher spectral efficiency. In addition to usual applications of wireless LANs, full duplex wireless LANs may extend the domain of its applications to smart home, health care, multi-hop relaying and mobile networks in future. These applications generate enormous amount of data traffics. To transmit these high volumes of data through wireless network with the provision of quality of services, the capacity of the wireless network has to be increased.The amount of wireless data traffics are expected to grow exponentially in future [4]. Wireless mesh network is a low cost and easily deployable wireless half-duplex (HD) network. If FD wireless technology is used in wireless mesh network, the increased throughput of the network could make it more suitable for commercial deployment. To provide quality of services (QoS), a fair scheduling algorithm for FD wireless devices has to be re-designed as such an algorithm was designed for HD wireless devices in Reference [5]. However, the upper layers, especially the medium access control (MAC) of the TCP/IP protocol suite have to be modified to maximize the benefits of this in-band FD physical layer technology. In-band FD wireless radio poses few unique issues at the MAC layer and these issues have to be solved by devising suitable solutions which can exploit the pledged advantages of an in-band FD physical layer.
The hidden and exposed nodes [6] are the two well-known problems in carrier sense multiple access (CSMA) based MAC protocols. To mitigate those problems during medium access, overheads that is, request-to-send (RTS) and clear-to-send (CTS) are incurred in IEEE 802.11 distributed coordination function (DCF) protocol which is the de-facto standard for shared medium access in wireless LANs. An FD-MAC protocol must resolve these two issues. Another common issue of wireless communication is the jamming in physical layer. One of the reasons for the occurrence of jamming is because of the scarce and crowded bandwidth of the wireless medium [7]. FD wireless technology has the potential to remove jamming from from the physical layer as it provide higher bandwidth. IEEE 802.11 DCF provides distributed medium access to the wireless nodes based on binary exponential back-off (BEB) and network allocation vector (NAV). Several other issues such as uses of BEB, inter-node interference, inter-operability among half duplex and full duplex nodes, fairness in access time among nodes, synchronization of clocks during FD transmission have to be considered when it comes to design an FD-MAC for wireless LANs.
A number of FD-MAC protocols have been proposed in the literature [3,8,9,10,11,12,13,14,15,16]. Most of these protocols tried to modify the existing IEEE 802.11 DCF MAC to enable it to be operable in in-band FD wireless networks. In-band full duplex wireless transmission itself produces some basic challenges that are not present in half duplex wireless networks. Each of these existing MAC protocol have addressed only a few issues that arise in in-band FD wireless networks. Some researchers proposed centralized FD MAC [3,9,10] and other proposed distributed FD-MAC protocols [3,13,14].
A few survey papers [17,18,19] on FD-MAC protocols have been found in the literature. No review has been carried out so far on the proposed solutions of Inter-Client Interference (ICI) which is a major problem in designing a in-band full-duplex MAC protocols for wireless networks. The authors of Reference [17] have classified and compared self-interference techniques in which most of the works focused on the available physical layer schemes for successful operation of in-band full duplex radios. Only a few in-band FD-MAC protocols have been discussed and classified. In Reference [18], the authors have classified the existing FD-MAC protocols, but a few discussions have been carried out about the problems that persist in designing a FD-MAC protocol.Similar to the previous review works, Dibaei and Ghaffari in Reference [19] have investigated the existing FD-MAC protocols as well as they have classified and made comparisons among these protocols. Although only a few problems related to the design of a FD-MAC are identified in Reference [19], the authors have omitted a large numbers of issues that arise during medium access control in full-duplex wireless radio. Moreover, the paper lacks the discussions about the solutions to ICI problem which significantly reduces the spectral efficiency of the FD wireless medium. The differences between this survey and the previous surveys on FD-MAC protocols are shown in Table 1. Thus, more research on this field are necessary and a comprehensive survey on the existing FD MAC protocols is very essential for understanding the ongoing research.

Table 1.
Comparison among existing surveys and this survey.
The objective of this study is to investigate the existing in-band full duplex MAC protocols and their advantages and disadvantages over half duplex wireless MAC protocols. This exploration includes the identification of future research directions for FD-MAC protocols and formulation of a comprehensive qualitative comparison among the existing FD-MAC protocols. In this study, we have also conducted a survey on the existing solutions to minimize the inter-client interference that emerges during medium access in full-duplex wireless network. This inter-client interference scenario is shown in Figure 1.
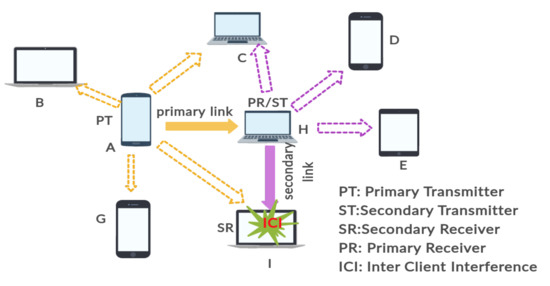
Figure 1.
Inter-Client Interference in Ad hoc Networks.
The contributions of this paper are outlined as follows:
- Identification of in-band wireless full duplex scenarios for the operations of FD-MAC protocols.
- A comprehensive analysis why existing half duplex MAC protocols are not suitable for FD wireless environment.
- Categorization of the existing in-band wireless FD-MAC protocols
- A qualitative comparisons among the existing in-band wireless FD-MAC protocols by considering different performance factors for FD wireless MAC protocols.
- Categorization and comparison of existing solutions proposed in various FD-MAC protocols to minimize the inter-client interference problem with respect to their mode of operations.
- Listing out the problems that should be considered during the design of in-band wireless FD-MAC protocols along with comprehensive discussions of these problems
The rest of the paper is organised as follows. Section 2 explores the common goals of designing a MAC protocols for wireless networks. In Section 3, We describe the reasons of not using existing half duplex MAC protocols in FD wireless LANs. Existing in-band FD-MAC protocols and their approaches to solve different issues in-band full duplex wireless networks are discussed in Section 4. A qualitative comparison among different existing in-band FD-MAC protocols are depicted in Section 5. In Section 5, we have also explained various qualitative metrics that are used for comparing and contrasting among these existing FD-MAC protocols. In Section 8, We have discussed and classified the existing state-of-the art solutions to ICI problem of full-duplex wireless LANs. Section 7 discusses few issues regarding the design of an FD-MAC protocol. In Section 7, we also explore different topological scenarios for the applicability of full duplex MAC. Section 8 concludes this paper with few future research goals.
2. Common Goals of MAC Protocols in Wireless Networks
Unlike Ethernet (IEEE 802.3), the design of medium access control protocol for wireless LANs imposes several challenges due to the dynamically varying nature of the underlying radio channel. As the radio channel in WLAN is broadcast in nature, a controlled and distributed mechanism is required to provide access of the wireless devices to the medium. Carrier sense multiple access [20], which is the most widely used medium access mechanism used in wireless network, paved the way to design MAC protocols by considering various factors of the shared radio channel. There are several common issues that must be resolved to design a MAC protocol for both half duplex and full duplex radios. Apart from those complex issues, there are a few basic issues that are required to be fulfilled by a MAC protocol:
2.1. Throughput
It is quantified as “the fraction of the capacity of a radio link used for data transmission” [21]. It depends on the numerous factors such as spectral efficiency achieved by the MAC protocol, overheads incurred in MAC protocol, Multiple Access Interference (MAI), transmission impairments of the channel and so forth. An FD-MAC protocol should have the potential to double the throughput as compared to other half duplex MAC protocols. An FD-MAC have to deal with the issues that are raised due to the simultaneous transmission and reception of radio signal at the same frequency band.
2.2. Delay
Delay in MAC layer refers the amount of time a frame has to wait at the sender node before its successful delivery to the receiver node. It is quantified as the difference between the time of en-queue of a frame at the sender’s MAC queue and the time the frame is de-queued from the MAC queue. A FD MAC should have the potential to minimize the average delay of each frame so that time critical applications get better goodput.
2.3. Fairness
Fairness in MAC layer means providing each node equal access time to the medium. A MAC protocol of distributed nature is preferred most in wireless environment. During the design of a distributed MAC protocol, medium access mechanism should be incorporated in such a way that the MAC does not favor any particular node. But different traffics from various time critical applications may have higher priority over normal data traffic. Therefore, applications having same priority traffic class should get equal access time to the medium to maintain application level fairness. A well-designed full duplex MAC should take fairness into consideration during the assignment of radio channel to full duplex nodes. Jain et al. [22] have proposed a fairness index which is widely used in various field of computer science where resource allocation is an important factor.
2.4. Energy Consumption
Energy is a very scarce resource for mobile devices. It is expected that by 2030 global mobile data traffics will be increased to 5016 exabytes per month [23]. Video streaming applications which are more energy hungry than email or http traffic will account for two-third of these mobile data traffic. At a particular time, the network interface of a mobile device can reside in any of the following states: active (transmit/receive), idle, switching, sleep and off. While a device is in the idle state, it continues sensing the medium to detect ongoing activities. A wLAN interface in a mobile device consumes significant portion of the battery power while it stays in the active and idle states [24,25]. In the MAC layer, a device’s energy in wLAN is wasted due to re-transmissions, erroneous frame reception, collisions, overheads transmission, for example, RTS, CTS and sensing the medium for detecting idleness [26]. An in-band FD-MAC protocol must have the characteristics to reduce unnecessary energy usages during data transmission. Therefore, minimizing the energy consumption of the wireless interface of a station is an important design goal of any MAC protocol.
2.5. Lower Overheads and Packet Error Rate
All of the MAC protocols that are present in the literature introduce extra control frames or add extra bytes with data before transmission of original data bits.These overheads consumes much of the wireless bandwidth which lowers the spectral efficiency of the wireless medium [27]. A receipt frame at MAC layer of the receiver could be failed due to collisions that occur during simultaneous transmissions from multiple stations.An erroneous frame has to be re-transmitted by the sender and this re-transmission reduces the bandwidth utilization of the wireless medium [28]. A wireless MAC protocol must address these issues such that it incurs less overheads and lower packet error rate during data transmission.
3. Applicability of HD MAC Protocols for FD Wireless LANs
The design and development of MAC protocol for wireless local area network has received enormous attentions from the research community. Existing MAC protocols for wireless LANs are based on the fact that wireless nodes operates in half duplex mode. MAC protocols found in literature for HD wireless network can be broadly categorized into three classes: contention based protocols, contention free protocols and controlled access protocols [29]. The taxonomy of the existing HD MAC protocols are depicted in Figure 2.
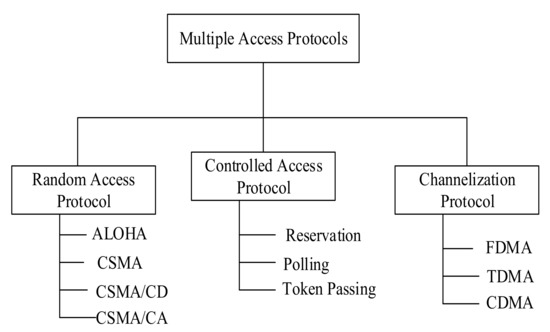
Figure 2.
Taxonomy of existing medium access control (MAC) protocols for wireless local area network (WLAN).
3.1. Contention Based MAC Protocols
These protocols are suitable to make multiple access mechanism a distributed process. In order to access the medium, all nodes contend with each other to gain control of the shared medium. Collisions among the contending nodes are common in these contention based protocols. It is due to the fact that an HD wireless node cannot sense the medium while it is in transmit mode. Binary exponential back-off (BEB) algorithm is widely used by these access schemes. Contention window (CW) size and back-off slot are the two dominant factors that contribute most in all sorts of contention based access scheme. A node chooses back-slots randomly from its current contention window. The node waits until the back-off time reaches to zero. As soon as the back-off time reaches to zero, it starts transmitting a frame. If a collision takes place, a node doubles its contention window for each successive collision until the CW size reaches to a maximum size. If a frame is transmitted successfully, a node resets its contention window to the initial size.
Moreover, in Quality of Service (QoS) supported wLANs, applications with different priorities also contend among themselves. In a dense QoS enabled wLAN, adjustment of the back-off time of a node impacts on the performance of the network. Ali et al. [30] proposed machine learning enabled enhance distributed channel access (MEDCA) mechanism in which the nodes infer the network density and adjust their back-time accordingly. Reference [31] proposed a contention based MAC protocol which exploits the benefits of machine learning in order to provide access of the medium to nodes in internet of things (IoT) based e-health networks. The authors of Reference [32] proposed a cognitive back-off procedure which sets the size of CW dynamically according to the density of nodes in a network. Hidden and exposed terminals are the two common problems in these contention based protocols. An intelligent Q-learning based resource allocation scheme is proposed in Reference [33]. A scaled contention window procedure is proposed in Reference [34] in which the size of CW changed based on the number of collisions and successful transmissions of frames in dense network. Ali et al. [35] proposed observation based scaled back-off procedure to provide coordinated medium access in highly populated wireless networks which operate in unlicensed band.
Because of hidden terminals an ongoing transmission experiences collisions and exposed terminal results in waste of bandwidth utilization. Therefore, the spectral efficiency of the wireless medium remain underutilized. The most widely used medium access protocols is IEEE 802.11 DCF and this protocol is based on carrier sense multiple access with collision avoidance (CSMA/CA) [36]. To mitigate the problem of hidden node, this protocol incurs additional control packets (RTS/CTS) which consume bandwidth. As an FD wireless node can transmit and receive simultaneously in-band, these RTS-CTS overheads are not necessary in FD wireless. When a node initiates a transmission in an infrastructure wLAN, it transmits data to the access point. The FD access point can transmit a busy tone in the same frequency band while it is receiving data from the sender. As other nodes overhear this busy tone, they can suspend their transmissions till the end of the current transmission. In this way it can suppress the hidden terminal problem without sending RTS-CTS control frames. Discarding the transmission of these overheads during channel access period could increase the channel capacity. Thus, existing IEEE 802.11 DCF MAC is not a suitable candidate for in-band FD wireless LANs.
3.2. Contention Free and Controlled Access Protocols
These protocols undergoes specific issues during their respective transmission operations. These protocols have limited flexibility in the presence of dynamic wireless environment. A single point of failure is a major disadvantage of such protocols. The channel efficiency of these protocols are very low while the traffic loads of the network are low. It is because of the fact that these protocols allow the transmitting node to take turns for getting access to the medium. Sometimes the medium may remain idle, but a node that has data to send might have to wait a longer time for its own turn. Applications of these protocols in in-band FD wireless network results the same advantages and disadvantages if these are applied in HD wireless network. To make FD MAC protocol distributed, these protocols are not best candidates as their operations may under-utilize the FD capacity of wireless radio.
4. Existing Full Duplex MAC Protocols
Although in-band full duplex wLAN is in rudimentary state, several works have been carried out to design MAC protocol for in-band full duplex wireless networks. Due to the advancement of self-interference cancellation technologies and promising results of various experiments discussed in Section 1, IEEE 802.11ax working group has considered the adoption of simultaneous transmit and receive mode (STR) for the next generation wLANs [37,38]. In Reference [39] IEEE 802.11 WG have decided that in-band FD technology can yield enormous benefits like increased throughput per station, reduced latency, collision detection and hidden node elimination [40] in a dense infrastructure based wLAN. Some of the protocols have paid attention in modifying the legacy IEEE802.11 DCF protocol, some have modified the back-off procedure and some of the works have exploited the Head of Line (HOL) packet of the MAC and others concentrated on designing a centralized protocol. No full duplex MAC protocol has been standardized yet. Some researchers have proposed that carrier sensing during data transmission could reduce the collision duration as well as the length of a collided data packet [8]. The legacy IEEE CSMA/CA protocol is the most widely deployed medium access protocol in existing wireless devices. Most of the proposed protocols in literature have modified the frame structure either (data frame/control frame) of IEEE 802.11 DCF. If full duplex devices need to co-exist with half duplex devices, these works did not mention how these devices will be compatible with their operations. None of the existing protocols have proposed the back-ward compatibility half duplex wireless devices.
The main job of a MAC protocol is to provide the wireless nodes a coordinated access to the medium through resolving channel contention and minimizing collision among their transmissions. Researchers have devised solutions to make full duplex MAC a reality through effective measures to solve channel contention and collision minimization. Existing FD-MAC protocols can be categorized broadly into two classes according to their modes of operations.These are (i) centralized (ii) distributed. Some of the protocols have taken only topological scenarios for traffic scheduling and others have developed a decentralized methods for transmission scheduling. Carrier sense, contention window, back-off time and re-transmission are the four parameters for a distributed MAC protocol. Most of the existing distributed protocols have exploited these parameters in different manners. A few protocols allow the devices to share the random back-off time among the nodes, some snoops the header of the source packet in determining FD transmission opportunity and some utilizes RTC/CTS exchanges to avoid collision. Carrier sensing imposes hidden and exposed terminal problems in wireless medium access. To alleviate hidden and exposed terminal problems some existing protocols used only busy tone that carries no data. Some protocols are proposed in literature but the authors did not analyze the three basic parameters of the MAC protocol—fairness, throughput and end-to-end delay. A classification of the existing protocols which have considered these three basic parameters are shown in Table 2.

Table 2.
Category of Full Duplex MAC Protocols.
Most of the protocols in Table 2 have considered carrier sensing as the basis of their scheduling operations and these protocols aim to bestow upon the choice of transmission at each wireless node in the network.
A qualitative comparisons of the existing FD MAC protocols which are available in literature are shown in Table 3 and Table 4. Modes of scheduling mechanisms, applications of the protocol, capability of mitigating hidden and exposed terminal problems, advantages and disadvantages, contention resolutions during three node FD transmission are taken into considerations to compare these protocols. Degree of co-existence with HD devices is also a big factor while evaluating a FD MAC protocol. If an FD MAC protocol is not back-ward compatible with existing HD MAC protocol standards, then nodes of two domains with two different technologies are formed in the same network where neither of them can communicate with each other. These nodes may use the same frequency band for data transmission.

Table 3.
Qualitative comparison of existing full duplex (FD) MAC protocols.

Table 4.
Qualitative comparison of existing full duplex (FD) MAC protocols (continued).
4.1. Centralized FD-MAC Protocols
These centralized FD MAC protocols are operated in infrastructure based networks. Access Point (AP) plays the role of central arbiter that determines which nodes get access to the medium at a specific time and how much time a node can use the medium for transferring its data.
In Janus [10], AP acts as an information collector which sends a probe request to each of the node in its vicinity by asking all of the nodes to send length of data packets that they wish to send. It determines scheduling in cyclic order. Each node also sends the interference information they received from their concurrent counterpart nodes. Janus forms a conflict map. Conflict map and outgoing queue of the AP are used to schedule data transmission. Janus uses Deficit, Round Robin Technique [47] to achieve fairness and control latency. The flow graph of Janus is shown in Figure 3. If the packet sizes of uplink and down link are not equal, AP controls the data rate through adaptation to finish the transmission duration at the same time.
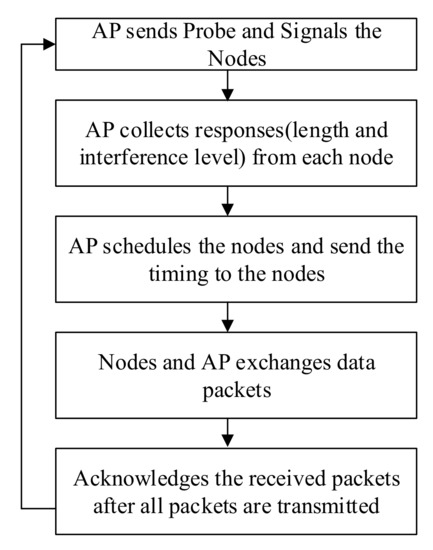
Figure 3.
Janus, A Centralized FD-MAC protocol.
4.2. Contention Based FD MAC Protocols
In Reference [9], a centralized D2D FD-MAC protocol has been proposed, which schedules transmissions by five distinct phases. Access point selects a node that should transmit packet in each time slot. Request, Collect, Schedule, Data and Acknowledgement are the fives phases of the protocol. It uses three types of control packets—Request, Information and Schedule packets. AP sends request packets to each node at the beginning of a time slot. All other nodes which have data to send responds with the information packets. After scheduling all of the requested transmissions, AP sends schedule packets to all of the nodes to inform them about the transmission schedule. During scheduling decision, AP takes neighbors of a node into consideration. It allocates a slot to a transmission which has a destination node with the smallest number of neighbor nodes. It searches for transmission which is symmetric in order to schedule it concurrently with the first transmission in same time slot. Until all of the possible transmissions are scheduled, AP continues to find matches for secondary transmissions. pFD-MAC [11] is an AP based FD MAC protocol that addressed the issues of inter-node interference and asymmetric traffics during medium access. Two timing sequences are defined: contentions free period and contention period.Two distinct operations of pFD-MAC during two contentions periods are depicted in Figure 4. During contention period, network management is carried out such as incoming and outgoing activities of mobile nodes. In contention free period, scheduling process and data transmission process take place simultaneously. During contention free period AP collects relevant info from mobile nodes such as traffic length, interference level. AP updates polling profile accordingly. Workflow diagram of the protocol is depicted in Figure 5. In this protocol, polling profile is used to schedule the transmissions. As generating polling profile is an NP-hard problem, the authors have produced heuristic solution to resolve the contention problem among the nodes. The main goal of this protocol is to minimize the traffic transmission time. Fairness among the nodes is calculated using Deficit Round Robin Algorithm [47]. Polling based scheduler which is the soul of the protocol is used to generate and update polling profiles in each cycle of the protocol is shown in Figure 5. To prevent collision due to inter-node interference, each node reports its interference level to AP. SIR is calculated using the following formula:
where represents signal to interference ratio from node j to node i. is power received from at node i and is power of interference signal receive at node i from node j.
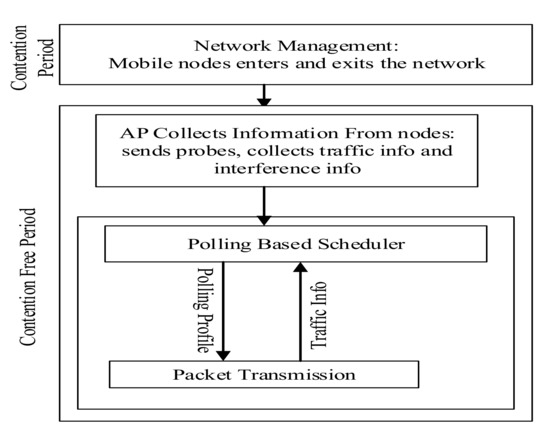
Figure 4.
pFDMAC activity during two different timing periods.
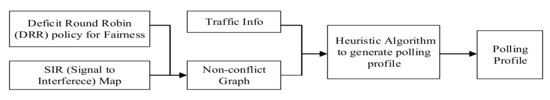
Figure 5.
Polling Based Scheduler of pFD-MAC protocol.
A-Duplex [48] is a centralized contention based FD MAC protocol which is designed for infrastructure based wLANs. AP works as a full-duplex transceiver and other clients are half-duplex. This protocol relies on the capture effect to minimize the ICI problem. Only three node full duplex scenario is supported by this protocol. When a client gets access to the medium, it sends an RTS. Upon receiving the RTS frame, AP sends CTS to the client and if AP has a packet for another client, it immediate sends packet to the second client. If AP does not have a packet for any other client, half-duplex transmission is established. AP maintains a Signal to Interference Ratio (SIR) map about the client pairs. SIR is used to select a second client to construct a three node FD transmission link. If AP gets access to the medium, no in-band full duplex transmission is established. Moreover, maintaining a SIR map about all the client pairs is a complex job.
PoCMAC [49] works in a network scenario where AP has in-band full duplex radio capability and the clients are traditional half-duplex wireless devices. Client that gains access to the medium sends an RTS to AP. Then access point sends a CTS-U frame that includes the address of TX and addresses of eligible down link receivers. These down link clients contend with each other with their newly calculated contention window based on received signal strength (RSSB) from AP to RX and TX to RX. The down link client that has smaller contention window size gets the access to the medium and sends CTS-D frame to AP. Three node full duplex transmission link initiated by the secondary transmitter is established (PT to AP and AP to SR). AP determines the optimal transmit power of primary transmitter and itself such that ICI at SR is minimized. This protocol has introduced several new control frames which are not compatible with existing half-duplex wireless devices. Collision resolution among multiple down link clients with same back-off slots are not discussed. In these scenarios, the protocol operates in half-duplex mode.
FuPlex [50] defines two transmission procedures: primary and secondary. In primary procedure, a client or the AP gets access to the medium after successful contention resolution according to CSMA/CA. If a client starts the primary transmission, AP selects a secondary client and establish a secondary transmission. If AP starts a primary transmission, all of the up-link clients start a secondary contention by choosing a back-off time from each one’s SNIR based contention window. The up-link client with the lowest back-off time starts transmission to AP and AP starts transmission to down link client.Collisions among up-link clients(ST) with same secondary back-off slots reduces the spectrum efficiency of the wireless medium. Asymmetric traffics are made symmetric by adding padding bits.
The proposed FD MAC [51] is suitable for infrastructure wLANs in which both AP and clients operate in full/half duplex mode. Bi-directional(BFD) and Unidirectional (UFD) full duplex transmissions are considered in Reference [51]. The protocol exploited a reserved bit in the legacy CTS control frame to initiate a BFD or UFD transmission. AP uses neighborhood information about the clients to select a suitable SR for enabling a UFD transmission. This protocol lacks a proper ICI cancellation procedure. Moreover, for asymmetric traffics in UFD and BFD transmissions, throughput performance is an issue.
In full duplex transmission, channel under-utilization occurs in infrastructure based wLANs while the time difference between up-link and down link transmission is very large [43]. The author has proposed a secondary contention window for the clients according to the duration field of the overheard RTS and CTS control frames. If time gap is short, symmetric FD transmission takes place without collision. On the other hand, if the uplink transmission time is larger, Station that possesses lower contention window size gets access to the medium and starts its transmission immediately after client→AP TX time is over. The protocol does not offer any ICI cancellation strategy. Stations that are hidden from each other, they receive either an RTS or a CTS. The values of duration fields in RTS and CTS are not the same according to the current standard. Therefore, Clients that receive either an RTS or a CTS might miscalculate the size of its secondary contention window.
4.3. Distributed FD MAC Protocols
Most of the FD MAC protocols in literature are similar to the legacy CSMA/CA protocol. An FD node can overhear collision while it is transmitting/receiving data from its neighbor nodes. If collisions are heard during data transmission session, a node can stop its transmission reducing further collisions in the network. Some of the distributed protocols consider only bidirectional topology depicted in Figure 6a in which FD transmission only occurs while the receiver station also has data for the sender station during the same data transmission session. In this case FD opportunity may happen depending on the availability of a data packet in the head of line (HOL) position of the receiver’s queue for the sender. Other protocols have taken topological scenarios into consideration for scheduling data transmission among nodes depicted in Figure 6b,c. The main objective of these MAC protocols is to maximize the capacity of the wireless network. Some of the protocols have also considered fairness issues in assigning transmission time of the medium to the nodes. These protocols can be classified into three categories according to their scheduling operations which exploits RTS-CTS, back off time and header of the MAC frame.
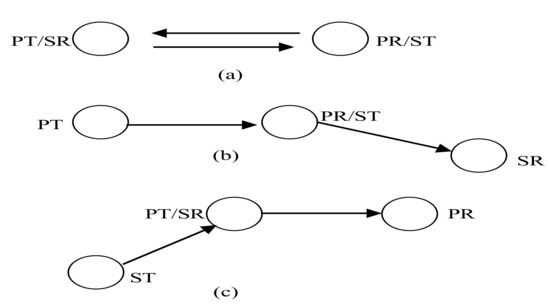
Figure 6.
Full duplex (FD) Opportunity Scenarios.
In FD wireless MAC, proposed in [3] used basic transmission mechanism of IEEE 802.11 DCF. It uses back off procedure and contention window size similar to IEEE 802.11 CSMA. While a receiver receives a frame from the sender, the receiver sends busy tones to its neighbor. This busy tone prevents hidden nodes from interfering with the receiving nodes.
The utility optimal FD MAC [52] operates similarly to the IEEE 802.11 CSMA/CA MAC. It is an RTS-CTS based MAC protocol. In this protocol, a primary node (PT) initiates a transmission session following carrier sensing and binary exponential back off mechanism. The channel contention procedure of this protocol is similar to 802.11 DCF protocol. While the primary receiver (PR) is in receiving mode, it continues to sense the channel status. A bidirectional FD opportunity takes only when both the sender and receivers transmission overlap. Sender sends RTS to the receiver. If receiver has data to send, it sends RTS to its neighbor nodes. Sender which is in transmitting mode decodes RTS and temporarily suspends its transmission. It replies with CTS to the receiver and resumes its transmission. Receiver starts transmission to the sender. This protocols uses RTS/CTS to exploit FD transmission. RTS/CTS imposes exposed terminal problems which can be solved using an offline conflict graph [53]. To solve the asynchronous contention, a shared random back off based FD MAC has been proposed [54]. It exploits the back off and contention mechanism of legacy IEEE 802.11 CSMA/CA protocol but the protocol modifies RTS/CTS structure to incorporate the back off information into frame. Due to node density, the backoff time duration of primary transmitter and primary receiver may not be same. If a PT has more data frames to send to PR and vice-versa. A bidirectional FD transmission is preferred. At first PT wins the contention and initiates a transmission to PR. PT selects a back off time and add this in the RTS frame.
PR upon receiving RTS comes to know that PT has more data to send. PR now sets its back off time proposed by PT for subsequent data transmission. PR can also propose a new back-off time during ACK frame transmission to the PT.
Contraflow [14] is a header snooping based FD MAC protocol which deals with the scenarios depicted in Figure 6a,b. This protocol considered three parameters during medium access: contention resolution among nodes which may cause inter-node interference, efficiency and fairness. As soon as a PR receives a frame from PT, it decodes the header. If PR does not have data for the PT, it can choose a secondary receiver among its neighbor. Only primary receiver is allowed to initiate a secondary transmission. PR chooses an ST from a list which contains the addresses of nodes and the weight of each node. The higher weighted node is selected as the secondary receiver node. The weight represents proportion of successfully secondary transmissions in the past using the same asymmetric dual link. Packet transmission diagram of contraflow for asymmetric link is shown in Figure 7.
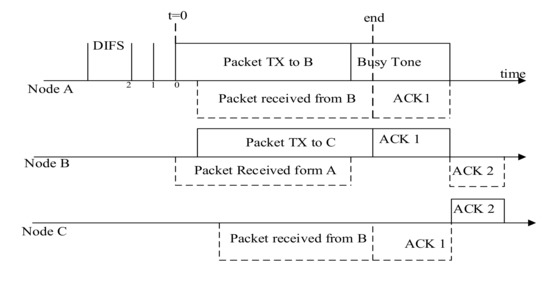
Figure 7.
Frame transmission sequence of contraflow [14] in asymmetric link.
Song et al. [55] proposed an energy efficient MAC protocol in which three new control frames have been introduced like CSMA/CA. The protocol schedules only bi-directional full-duplex transmissions or half-duplex transmission. Initially, A primary transmitter (PT) sends an RTS-SIC which includes self-interference co-efficient (SIC) to a primary receiver. Upon receiving an RTS-SIC, PR calculates whether or not its transmission to PT with maximum TX power exceeds the minimum SINR at PT for successful packet reception.If minimum SINR at PT is not satisfied, PR replies with CTS-P with the minimum desired transmit power from PT and a HD transmission from PT to PR is constructed. Otherwise, PR replies with MTS-SIC control to initiate a bi-directional full duplex transmission.In the case of BFD, PT and PR transmit using optimized power calculated from minimum SINR and received power. In a dense ad-hoc network, collision among the nodes increases as more nodes get access to the medium for transmission. Moreover, three node full-duplex transmission scenario is not considered.
A CSMA/CA based full-duplex MAC is proposed in Reference [45] which tries to increase throughput gain opportunistically allowing only bi-directional full-duplex transmissions. According to the protocol, each node contends for the medium like CSMA/CA.While a nodes (PT) gets access, it starts transmission and as well as overhears if there is other on-going transmission. If PT does not sense any signal, it continues with it on-going transmission. The PR, upon receiving the frame header, starts a secondary transmission (passive) to PT. If PT overhears other signal and it cannot decode it, PT and other transmitting nodes stop their transmission. If PT can decode the overheard signal, three scenarios are possible.
- PR is transmitting to PT
- A third node is sending data to PR
- A third node is sending data to a node other than PR
For the first case, PT continues its transmission. For the second and third case, a priority based approach is adopted in which lower priority node abort its transmission. The protocol does not depict the construction of a three node full duplex transmission. A markov chain based analytical model is proposed in which throughput gain is calculated in these network scenarios. Hidden node problem is not considered to formulate the analytical model of this protocol.
Marlali and Grubuz [56] have proposed a shared random back-off based full duplex MAC protocol in which a PT and PR shares their chosen back-off slots with each other for the next FD transmission. The protocol operates in both HD and FD mode. Two reserved bits of Frame Control (FC) field in a data frame of IEEE 802.11 DCF protocol is used to add this information. These two bits also determines the master and slave role of an FD transmission link. A 10-bit extra field (next_bo) which indicates next random back-off value, is added to the data frame structure. Only bi-directional full-duplex transmission link allowed in this protocol. ICI cancellation is missing in this protocol. The 10-bit next_bo field is the main overhead in this protocol.
5. Qualitative Comparison among Existing FD MAC Protocols
A qualitative comparison of existing FD MAC protocols is shown in Table 3 in page 14 and Table 4 in page 15. Various factors are considered to figure out the differences among these MAC protocols. Some protocols are suitable for specific applications. These also differ from their basic access schemes and solutions to particular problems in FD wireless environment. Different protocols address to solve inter-node interference in different ways. The FD scenarios in which a MAC protocol is operable is also listed in this comparison. Not all protocols addressed all of the FD scenarios. Only a few of the existing MAC protocols are backward compatible with the legacy IEEE 802.11 DCF MAC. Compatibility checks whether an FD MAC changes the basic frame structures of standardized IEEE 802.11 DCF protocol.
5.1. Access Mechanism
In wireless network, the medium is shared among the nodes as these nodes transmit and receive in the same frequency band. Medium access mechanisms plays a significant role in maximizing the throughput of network, minimizing the end-to-end delay of a transmission and providing quality of services to different applications. Existing MAC protocols adhere the approaches of centralized and distributed nature in designing a FD MAC. In centralized approach, a single node controls other wireless devices for accessing the medium. This device collects topological information of the wireless networks. It may poll a device to transmit data for a complete data transmission session [9] or grant time slotted access duration to each node collecting and sending control information and data to the nodes [10]. On the other hand, distributed FD-MAC utilizes modified CSMA/CA access schemes. Most of distributed FD-MAC [14,52] modify either the control frame structures of IEEE802.11 DCF or introduce new control frames for their FD operations [16,54].
5.2. Applications
FD MAC protocols are devised to be operable in particular wireless networks. Each wireless network has its own requirements for medium access. Some of the FD-MAC protocols are deploy-able in infrastructure wireless LANs and some are designed to be operable in D2D (Device to Device communication), ad-hoc and multi-hop wireless networks.A few of the existing mac protocols are designed to be applicable for wireless sensor networks and wireless multi-hop networks.
5.3. HD Compatibility
Existing wireless networks are half duplex(HD) in nature. Standardized half duplex MAC protocols are integrated in half duplex wireless devices.If an FD MAC protocol and an in-band FD wireless device are to be introduced in the industry, these FD devices must be inter-operable with existing HD devices.Otherwise a sudden paradigm shift to FD wireless network would incur loss of billions of dollars in the industry.FD-MAC protocols that have introduced new control frame or have modified the frame structures of IEEE 802.11 DCF protocol are not compatible with the existing HD wireless devices.
5.4. FD Scenario
An FD-MAC must be able to exploit all the full duplex opportunities for data transmission. FD opportunity scenarios are depicted in Figure 6. Three cases are possible: (i) a sender and a receiver may have data for simultaneous transmission, (ii) a primary receiver may not have data for its primary transmitter but it may have data to send to other secondary receiver, and (iii) a primary receiver may not have data for any secondary receiver but a secondary node within the vicinity of the primary transmitter may have data to send to the primary transmitter.Existing FD MAC protocols are compared according to their data transmission operations as well as the FD scenarios these protocols had addressed to solve.
6. A Survey on Inter-Client Interference Free FD MAC Protocols for Wireless Networks
Inter-node interference significantly reduces the spectral efficiency of the wireless medium in full duplex wireless LANs. Inter-node interference occurs in both infrastructure based wireless LANs [57,58,59] and ad-hoc wireless networks.In case of infrastructure based wireless network depicted in Figure 8, AP operates in in-band full duplex mode and other stations might work both in HD and FD mode. If an HD station (primary transmitter) initiates a data transmission session and AP has data to send to a secondary receiver, transmission signal from the primary station can corrupt the frame at the secondary receiver. In ad-hoc mode, while a primary transmitter starts a transmission for the primary receiver and the primary receiver does not have data for the primary transmitter but it has to send to a secondary receiver, an interference occurs at the secondary receiver.An in-band full duplex MAC protocol must address this issue and has the capability to keep this interference level in limited range [60]. This scenario is shown in Figure 1, where Node A is the primary transmitter, Node H acts both as primary receiver and secondary transmitter and Node I is the secondary receiver. Due to A’s transmission inter-client interference occurs at node I. To achieve better performances on the parameters described in Section 2, an in-band full duplex MAC protocol must have the capability to minimize the inter-client interference in wireless networks.
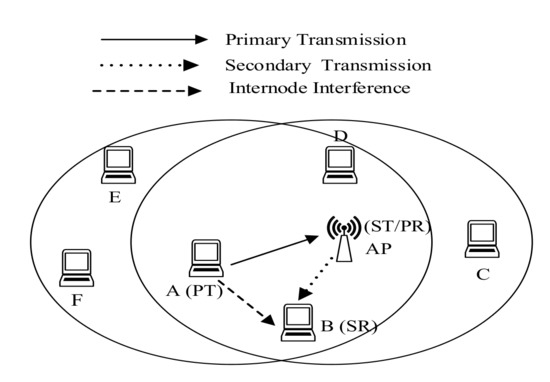
Figure 8.
Inter-node Interference in Infrastructure Wireless Networks.
Existing State of the Art in-Band FD-MAC Protocols with Inter-Client Interference Cancellation
Although nullifying the self-interference in in-band wireless network is still a research issue at the physical layer of the TCP/IP protocol stack, the recent advancement described in the previous sections are very much promising and it is expected that in-band full duplex radio will be available for mass usages in the near future. Inter-client interference is a critical factor that gives rise to conduct research on the MAC sub-layer of the data link in TCP/IP protocol suite.Unless inter-client interference is minimized to 0 dBm, it is not possible to achieve two-fold spectral efficiency of the wireless medium than the current half duplex wireless standards [14,57,58,61]. Some researchers have considered active inter-client interference cancellation by introducing physical layer signaling system and other have cancelled ICI passively utilizing MAC layer properties. In the literature, a few researchers have proposed various techniques for minimizing this inter-node interference issue in FD wireless networks. This section discusses various strategies proposed by the recent in-band FD wireless MAC designers.
Janus [10] proposed a centralized approach suitable for infrastructure based wireless LANs in which a conflict map is maintained by the AP. AP collects information about the pair-wise signal to noise ratio (SNR) among the clients and schedules full duplex transmission on the basis of probability among those pairs. This pair-wise concurrent transmission and reception schedule may limit the throughput performances of in-band full duplex wireless LANs if the clients are located near to each other. In Janus, AP sends periodic control overheads for collecting the CSI from the clients, which consumes bandwidth of the wireless medium.
Goyal et al. [12] have adopted a passive approach to minimize ICI. In this FD MAC protocol, an additional control frame called FD acknowledgement(FDA) is used before initiation of any data transmission. If a primary receiver does not have data for the primary transmitter, it sends data to the secondary receiver (SR). The SR calculate signal to interference and noise ratio (SNIR) of the received signal from ST. If this SNIR is above the required threshold, SR sends FDA to the ST and three node bi-directional transmission takes place. The main drawback of this solution is that SR must have channel state information (CSI) of PT to itself and ST to itself. Moreover, due to dynamic nature of wireless radio, this CSI varies with time and it could lead to miscalculation of SNIR at the secondary transmitter, thereby resulting in erroneous reception at the secondary receiver.
Shai et al. [54] have proposed a passive solution in which AP keeps track of the hidden stations of each half-duplex (HD) clients in an infrastructure based wireless network. While a client node initiates a transmission to the AP, the AP starts a simultaneous transmission to any of the hidden nodes (secondary receiver) of the primary transmitter. Thus it avoids inter-client interference. The weak point of this solution is that if AP does not have data for any of the hidden station then simultaneous full duplex transmission is not taken place.
Tang et al. [48] exploited the capture effect [62] capabilities of the receiver station. But capture effects has some serious dis-advantages because it requires stringent packet-alignment for better performance. At receiver, the packet that arrives first can be decoded easily and the packet that arrives later becomes difficult to decode by the receiver circuitry [63]. Due to asymmetric dual links where one link’s data rate is lower than the other, the throughput performance of this solution is degraded. Moreover, this proposal operates only in network scenarios where AP is full duplex and other clients are half-duplex.
In PoCMAC [49], authors have proposed a Received Signal Strength Based (RSSB) contention window size for all of the down link (DL) receiver clients (RX). A DL client calculates the SNRs from both AP and primary transmitter and sets the size of their contention window according to the calculated RSSBs. DL client(RX) with higher SNR for AP→RX link and lower SNR for PT→RX link usually has smaller size contention window.It indicates that this DL client would undergo lower ICI from the PT’s transmission.AP collects these contention window information about the clients and selects the lower contention windows size station for the DL transmission.After the selection of DL client, AP calculates the optimal transmission power for the PT and itself such ICI is reduced and collision does not occur at DL client.This solution is suitable for infra-structured wireless LANs. Furthermore, if two or more down link clients possess the same RSSB contention window size, this MAC protocol operates in half-duplex mode.
In FD2 [64], each client is equipped with directional antenna in which up-link client transmits its signal towards the AP. This directional transmission does not interfere with the down link clients. Thus, it avoids ICI at the secondary receiver station. Although use of directional antenna can reduce interferences, it also increases number of collisions in a wLAN. Due to increased collisions, packet losses are also higher in wLANs in which nodes are equipped with directional antennas. Moreover, the existing half-duplex wireless terminals have omni-directional antennas.
Hsu et al. [61] have proposed an active ICI cancellation technique for infrastructure based wireless networks. It exploits the AP’s FD capability by transmitting an opposite signal of the received signal from the primary transmitter. AP sends both the nullifying signal and data signal to down link client. The nullifying signal helps the down link client to thwart the interference signal from the primary transmitter. For down link client selection, AP keeps track of the CSI information of all of the client pairs within the wireless network. AP uses this historical CSI information while it starts to initiate a simultaneous down link transmission with the transmission from the primary transmitter. CSIs of each pair of clients vary with the dynamic nature of the wireless medium. CSI may become obsolete with time, thus there are possibilities of selecting an inappropriate down link client. Moreover, as AP has to send two signals, higher power consumption is an issue.
Lee et al. [65] considered the similar approach described in [61], but the authors have proposed a comparatively lower signal processing complexity at the AP by incorporating a large number of antennas. This solution is acceptable in infrastructure based wireless networks, but it cannot be applied to ad-hoc networks where power constraints are very important issues.
In IFFD [41], if a down link client is out of the interference range of the primary transmitter, it sends a control frame through which it informs the AP for the initiation of down link transmission. From the overheard Clear-to-send (CTS) control frame, the down link client calculates distance between primary transmitter and itself and examines whether or not it falls within the interference range of the primary transmitter. This solution only enable FD down link transmission with hidden stations of the primary transmitter.
Hu et al. [57] proposed a hybrid MAC protocol in which the authors demonstrated a two fold contention approach to minimize the ICI among the clients in infrastructure based wireless LAN. In the first phase, a primary transmitter upon getting access to medium sends UE-RTS control frame to the AP. Then AP chooses a random number between 0 and 1 and if the number is greater than a predefined threshold it sends AP-CTS which contains time duration for internal contention among the down link clients. Within this internal contention, station that access the medium first and SNIR requirements is chosen as the down link client. This scheme introduces several overheads which consume much of the bandwidth of the wireless medium. Moreover, if no client accesses the medium within the internal contention duration, half-duplex transmission is followed. In this case, medium remains idle for internal contention duration and affects the performances of the MAC protocol.
Kai et al. [66] proposed a centralized pair wise solution among the up-link and down link clients in which AP selects the down link client for a particular up-link transmission. AP maintains SNIRs of each pair of up-link and down link client links. AP uses hungarian algorithm [67] to select a down link receiver for a particular up-link transmission based on SNIRs. Then AP assigns access intensity adjustment value to the pair to calculate the maximum down link aggregate utility. Based on the up-link data rate requirement, this solution finds the optimal down link client for secondary transmission. In this solution, it is assumed that each node is within the carrier sensing range of each other.
Table 5 and Table 6 depict various MAC protocols which have proposed solutions for ICI and comparisons among those proposed solutions in terms of basic ideas, applications, advantages and drawbacks.

Table 5.
Comparisons among various solutions of inter-client interference cancellation in full duplex MAC protocols and their characteristics.

Table 6.
Comparisons among various solutions of inter-client interference cancellation in full duplex MAC protocols and their characteristics(continued).
7. Issues and Challenges in Full Duplex MAC Protocol
As the physical layer technologies of a full duplex device differ from those of the half duplex devices, an FD MAC protocol has to consider these variations such as self-interference cancellation, carrier signal sensing procedures, full duplex gain, and heterogeneous full duplex transmission scenarios. Interference range and transmission range of a node limits the capacity gain of an FD MAC protocol in a wLAN. As interference range of a transmitter reduces the number of simultaneous active links in a fixed geographic region, it significantly affects the performance gain of an FD MAC [52] protocol. In order to convey the maximum benefits of FD wireless physical layer to the upper layers, an FD MAC protocol must address several unique issues that are not present in half-duplex wireless radio environment. Several challenges pertaining to the design of an FD MAC protocol are described in the following subsections.
7.1. Residual Self-Interference Cancellation
Physical layer technologies must ensure that an FD node has the capability to transmit and receive in-band signal at the same time. Receiver circuit must be able to detect the amount of interference from its own transmission successfully. Moreover, It must have the capability to disinfect the received signal through cancelling out its own interference perfectly. Otherwise, the number of re-transmissions may increase due to erroneous reception which results from residual self-interference. This can significantly reduce the performance of a MAC protocol. Analog and Digital self-interference cancellation [68,69,70,71] techniques are widely used in in-band FD wireless networks. In order to satiate applications’ growing demand for higher data rate, high power transmitter and wider band channels are necessary for full duplex wireless networks. High power transmitter poses high self-interference on the receiver antenna. But current research are promising towards achieving this requirement such as authors of Reference [72] claim that 110 dB self-interference cancellation is possible with +30 dB of transmit power from an FD wireless node.
7.2. Bidirectional Transmission Mode
In FD wireless local area network, a receiver can be a sender at the same time in the same frequency band. While a sender starts transmission to the receiver, the receiver can initiate a bidirectional transmission with the sender. A MAC protocol should have the potential to adapt to this bidirectional FD transmission property. If the lengths of the data frames in a bi-directional FD mode are asymmetric, then collisions could happen due to transmissions from hidden nodes. As the two transmissions would not be completed at the same time, stations other than PT and PR are not synchronized in this scenario. Figure 6a shows the bidirectional transmission scenario in an FD wLAN.
7.3. Three Node Bidirectional Mode
If the primary receiver does not have data packet in its HOL for the primary transmitted but it has data packet for other node, then three node bidirectional transmission is required to get the maximum benefits out of in-band FD radio. The scenario is shown in Figure 6b. On the other hand, if the primary receiver does not have data packet for other nodes in its vicinity but a node that belongs to the transmission range of the primary transmitter has data packets for the primary transmitter, then the primary transmitter acts as a secondary receiver. In this case, a three node in-band FD transmission is established. This source based in-band FD scenario is depicted in Figure 6c in which one of the neighbors of PT can act as secondary transmitter.
7.4. Asynchronous Contention and Back off Size
In CSMA, it requires that a node senses the medium for idleness before it can send data. Each node has to wait until its back off time reaches to zero. Back-off time and contention window size depend on how a wireless node perceives the medium. More collisions occur in a densely populated network. As the number of collisions a node experiences differ due to the size of its neighborhood, it’s back off time also varies accordingly. In case of bidirectional transmission, if CSMA is employed, the back-off time of two nodes might not reach to zero at the same. While a PT initiates a transmission, the PR maybe in back-off process. This asynchronous back-off time is depicted Figure 9 in which both Rx1 and Tx1 may have different collision domain due to varied density of neighbor nodes.
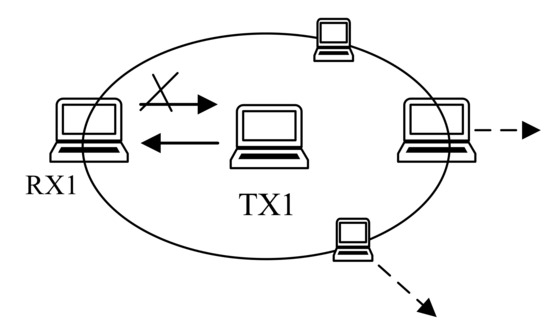
Figure 9.
Asynchronous contention.
7.5. Transmission Region Reuse Factor
In-band FD radio has the potential to double the capacity of a wireless LAN. An FD node can significantly reduce the space reuse region by other nodes for simultaneous transmission. This reduced space reuse factor also decreases number of simultaneous links, it affects the performance of the wireless LAN. This scenarios is shown in Figure 10 for half duplex networks. The neighbor nodes of either the transmitter or receiver can initiate another transmission without mutual interference in half-duplex radio. If an in-band FD radio is applied, the space reuse factor decreases because neighbor nodes of either Tx/Rx are blocked virtually by the transmission from PT or PR. In Figure 11, it is shown that the neighbors those are within the vicinity of an in-band FD node can not initiate a transmission. This reduced transmission region reuse factor is a hindrance towards achieving two folds capacity gain in FD radio than half-duplex radio [52]. Therefore, an FD MAC protocol must employ some measures so that this transmission region reuse factor is maximized to increase the capacity gain of a wireless network.
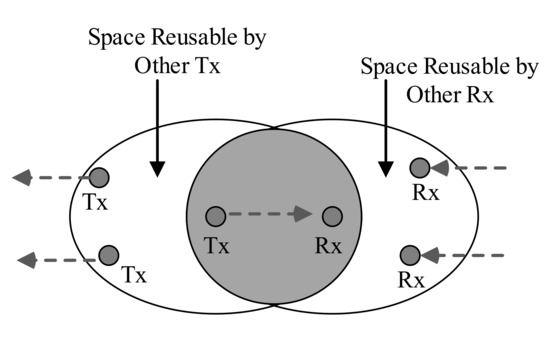
Figure 10.
Half duplex transmission spatial reuse.
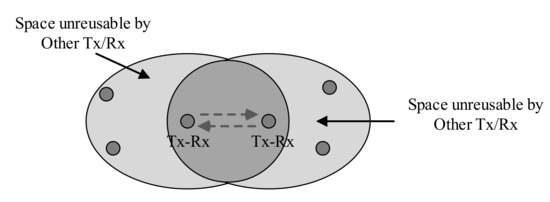
Figure 11.
Full duplex transmission spatial reuse.
7.6. Inter-Operability among HD and FD Nodes
As all of the devices currently deployed in any wLAN are half duplex, replacement of those devices with full duplex wireless interfaces might incur significant loss of investments in the industry. New FD MAC protocols must have the capability to be backward compatible with those existing HD MAC protocols.
7.7. Power Consumption
In in-band FD wireless radio, simultaneous transmission and reception requires more power. Power sources of handled and tiny devices are limited and rapid power drainage could result segmentation in any wLAN. This partition can severely affects the performance of a wireless network. In hostile wireless environment where rapid changes occur in wireless medium, it becomes difficult for a transmitter to measure the idleness of the medium. In this case, a transmission might undergo collisions and re-transmission of the same packet could drain the battery life of an FD node rapidly. Hence an FD MAC should take power consumption into consideration while it operates in dynamically varying wireless environment.
7.8. Inter-Node INTERFERENCE
In an infrastructure WLAN, while a primary transmitter (PT) starts transmission to an AP and AP does not have any data frame for PT, AP can initiate a transmission to an ST. If ST is within the transmission range of the PT, the transmission from PT induces interference at ST. Hence a collision occurs at ST due to the transmissions from both AP and PT. This inter-node interference scenario is depicted in Figure 8. In order to maximize the capacity of the network, An FD MAC protocol must have the potential to minimize this inter-node interference.
8. Conclusions
In-band Full duplex wireless radio has the major potential to double the capacity of the wireless networks. As the need for higher data rate is increasing, doubling the capacity of the wireless network is the main solution to satiate the future needs of wireless communication system. Effective and efficient in-band MAC protocols are essential for various wLANs because different wLANs have different requirements and pose unique challenges. The benefits of in-band full duplex transmissions in wireless network can only be realized by higher layers while both the physical and the MAC layer operate in full duplex mode. Among the challenges and issues identified and discussed in this paper, only a few of them have been addressed by researchers and their proposed solutions have advantages and limitations.
The design of a contention based MAC protocol which can address the three FD transmission scenarios effectively is a challenging task. Most of the solutions found in the literature for the inter-client interference problem are passive in which either hidden stations or SNIRs are taken into consideration. Only a few them have proposed active ICI cancellation techniques but these techniques require higher signaling computations which consume battery power. A combination of both active and passive solutions can reduce the burden of higher signal processing at the clients as well as increase the performance metrics of the wireless network. In-band full duplex radio can be utilized to various application domains, such as cellular networks where base station and clients can transmit and receive simultaneously in the same frequency band, thereby increasing the number users within a cellular tower. Self-interference cancellation in a base station (of the cellular network) is a major concern because the base station transmits with a high power to ensure long distance coverage. In-band FD radio technologies can be very useful for Internet of Things (IoT) devices which require limited transmission power and cover short distances. Reduction of power consumption by in-band FD tiny wireless devices is a future research scope because the uses of hand-held devices are increasing exponentially and those tiny devices possess low powered batteries. The qualitative comparisons and the limitations of various proposed solutions to ICI problem (presented in Table 4 and Table 6, respectively) can be helpful for future research specifically in the field of in-band FD MAC protocols for various wLANs.
Author Contributions
Conceptualization, M.R.A.; methodology, M.R.A., M.S.H. and M.A.; formal analysis, M.R.A.; investigation, M.R.A.; writing—original draft preparation, M.R.A.; writing—review and editing, M.R.A., M.S.H. and M.A.; supervision, M.S.H. and M. Atiquzzaman. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding. This is a part of an ongoing Ph.D work carried out by the first author at the Department of Computer Science and Engineering in Bangladesh University of Engineering and Technology (BUET).
Acknowledgments
The first author would like to thank his professional work place “the Department of Computer Science and Engineering of Northern University Bangladesh” where he works as a faculty member. The authors would like to thank the Department of CSE, Bangladesh University of Engineering and Technology for its kind support and cooperation.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Radunovic, B.; Gunawardena, D.; Key, P.; Proutiere, A. Rethinking Indoor Wireless Mesh Design: Low power, Low frequency, Full duplex. In Proceedings of the 5th IEEE Workshop on Wireless Mesh Networks (IEEE WiMesh’10), Boston, MA, USA, 21 June 2010. [Google Scholar]
- Choi, J.I.; Jain, M.; Srinivasan, K.; Levis, P.; Katti, S. Achieving Single Channel, Full Duplex Wireless Communications. In Proceedings of the 16th Annual International conference on Mobile Computing and Networking (ACM MobiCom’10), Chicago, IL, USA, 20–24 September 2010; pp. 1–12. [Google Scholar]
- Jain, M.; Choi, J.I.; Kim, T.; Bharadia, D.; Seth, S.; Srinivasan, K.; Levis, P.; Katti, S.; Sinha, P. Practical, real-time, full duplex wireless. In Proceedings of the 17th annual international conference on Mobile computing and networking(MobiCom’11), Las Vegas, NV, USA, 19–23 September 2011; pp. 301–3012. [Google Scholar]
- Sarret, M.G.; Berardinelli, G.; Mahmood, N.H.; Fleischer, M.; Mogensen, P.; Hein, H. Analyzing the potential of full duplex in 5G ultra-dense small cell networks. EURASIP J. Wirel. Commun. Netw. 2016, 284. [Google Scholar] [CrossRef]
- Ernst, J.B.; Denko, M.K. The design and evaluation of fair scheduling in wireless mesh networks. J. Comput. Syst. Sci. 2011, 77, 652–664. [Google Scholar] [CrossRef]
- Bharghavan, V. Performance Evaluation of Algorithms for Wireless Medium Access. In Proceedings of the IEEE International Computer Performance and Dependability Symposium (IPDS’98), Durham, NC, USA, 9 September 1998; pp. 86–95. [Google Scholar]
- Anantharamu, L.; Chlebus, B.S.; Kowalski, D.R.; Rokicki, M.A. Packet latency of deterministic broadcasting in adversarial multiple access channels. J. Comput. Syst. Sci. 2018, 99, 27–52. [Google Scholar] [CrossRef]
- Liao, Y.; Bian, K.; Song, L.; Han, Z. Full duplex MAC protocol Design and Analysis. IEEE Commun. Lett. 2015, 19, 1185–1188. [Google Scholar] [CrossRef]
- Kim, W.K.; Kim, J.K.; Kim, J.H. Centralized Mac protocol for wireless full duplex network considering D2D communications. In Proceedings of the International Conference on Information and Communication Technology Convergence (ICTC), Jeju, Korea, 19–21 October 2016. [Google Scholar]
- Kim, J.Y.; Mashayekhi, O.; Qu, H.; Kazandjieva, M.; Levis, P. Janus: A Novel MAC Protocol for Full Duplex Radio; Stanford University: Stanford, CA, USA, 2013. [Google Scholar]
- Liu, S.; Han, B.; Peng, W. A Polling-based Traffic-aware MAC Protocol for Centralized Full-duplex Wireless Networks. IEEE Access 2018, 6, 28225–28238. [Google Scholar] [CrossRef]
- Goyal, S.; Liu, P.; Gurbuz, O.; Erkip, E.; Panwar, S. A Distributed MAC protocol for Full duplex radio. In Proceedings of the Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 3–6 November 2013. [Google Scholar]
- Oashi, S.; Bandai, M. Performance of Medium Access Control protocols for full duplex wireless LANs. In Proceedings of the 9th Asia-Pacific Symposium on Information and Telecommunication Technologies (APSITT), Santiago and Valparaiso, Chile, 5–9 November 2012. [Google Scholar]
- Singh, N.; Gunawardena, D.; Proutiere, A.; Radunovic, B.; Balan, H.; Key, P. Efficient and Fair Mac for wireless networks with self—Interference cancellation. In Proceedings of the IEEE international symposium on modeling and optimization in mobile, ad-hoc and wireless networks(WiOpt), Princeton, NJ, USA, 9–13 May 2011. [Google Scholar]
- Tamaki, K.; Raptino, A.; Sugiyama, Y.; Bandai, M.; Saruwatari, S.; Watanabe, T. Full Duplex Media Access control for Wireless multi-hop networks. In Proceedings of the IEEE Vehicular Technology Conference (VTC Spring), Dresden, Germany, 2–5 June 2013. [Google Scholar]
- Cheng, W.; Zhang, X.; Zhang, H. RTS/FCTS mechanism based full-duplex MAC protocol for wireless networks. In Proceedings of the IEEE Global Communication Conference (GLOBECOM), Atlanta, GA, USA, 9–13 December 2013. [Google Scholar]
- Kim, D.; Lee, H.; Hong, D. A Survey of In-Band Full-Duplex Transmission: From the Perspective of PHY and MAC Layers. IEEE Commun. Surv. Tutor. 2015, 17, 2017–2046. [Google Scholar] [CrossRef]
- Thilina, K.M.; Tabassum, H.; Hossain, E.; Kim, D.I. Medium access control design for full duplex wireless systems: Challenges and approaches. IEEE Commun. Mag. 2015, 53, 112–120. [Google Scholar] [CrossRef]
- Dibaei, M.; Ghaffari, A. Full-duplex medium access control protocols in wireless networks: A survey. Wirel. Netw. 2020. [Google Scholar] [CrossRef]
- Kleinrock, L.; Tobagi, F.A. Packet Switching in Radio Channels: Part 1-Carrier Sense Multiple Access Modes and Their Throughput-delay characteristics. IEEE Trans. Commun. 1975, 23, 1400–1416. [Google Scholar] [CrossRef]
- Devi, M.C.; SubbaRao, S.P.V. Performance Evaluation of 802.11 MAC Protocol with QoS Differentiation for Real-Time Control. Int. J. Adv. Res. Electr. Electron. Instrum. Eng. 2016. [Google Scholar] [CrossRef]
- Jain, R.; Chiu, D.; Hawe, W. A quantitative measure of fairness and discrimination for resource allocation in shared systems. In DEC Research Report TR-301; Eastern Research Laboratory, Digital Equipment Corporation: Hudson, MA, USA, 1984. [Google Scholar]
- Report ITU-R M.2370-0.IMT Traffic Estimates for the Years 2020 to 2030. Available online: http://www.itu.int/pub/r-rep-m.2370 (accessed on 17 February 2020).
- Tsao, S.L.; Cheng, E.C. A power saving strategy for cellular/VoWLAN dual-mode mobiles. Wirel. Netw. 2008, 14, 683–698. [Google Scholar] [CrossRef]
- Ebert, J.P.; Aier, S.; Kofahl, G.; Becker, A.; Burns, B.; Wolisz, A. Measurement and Simulation of the Energy Consumption of a WLAN Interface; TKN Technical Report TKN-02-010; Technical University Berlin: Berlin, Germany, 2002; Volume 314. [Google Scholar]
- Tsao, S.L.; Huang, C.H. A survey of energy efficient MAC protocols for IEEE 802.11 WLAN. Comput. Commun. 2011, 34, 54–67. [Google Scholar] [CrossRef]
- So, J.; Eliab, A. N-DCF: MAC overhead reduction using narrow channel contention in wireless networks. EURASIP J. Wirel. Commun. Netw. 2018, 2018, 1–19. [Google Scholar] [CrossRef]
- Bianchi, G. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar] [CrossRef]
- Forouzan, B.A. Multiple Access. In Data Communication and Networking; Mc-Graw Hill: New York, NY, USA, 2007; Chapter 12; pp. 363–394. [Google Scholar]
- Ali, R.; Nauman, A.; Zikria, Y.B.; Kim, B.; Kim, S.W. Performance optimization of QoS-supported dense WLANs using machine-learning-enabled enhanced distributed channel access (MEDCA) mechanism. Neural Comput. Appl. 2019. [Google Scholar] [CrossRef]
- Ali, R.; Qadri, Y.A.; Zikria, Y.B.; Umer, T.; Kim, B.; Kim, S.W. Q-learning-enabled channel access in next-generation dense wireless networks for IoT-based eHealth systems. J. Wirel. Commun. Netw. 2019, 178. [Google Scholar] [CrossRef]
- Shahin, N.; Ali, R.; Kim, S.W.; Kim, Y. Cognitive backoff mechanism for IEEE802.11ax high-efficiency WLANs. J. Commun. Netw. 2019, 21, 158–167. [Google Scholar] [CrossRef]
- Ali, R.; Shahin, N.; Zikria, Y.B.; Kim, B.; Kim, S.W. Deep Reinforcement Learning Paradigm for Performance Optimization of Channel Observation–Based MAC Protocols in Dense WLANs. IEEE Access 2019, 7, 3500–3511. [Google Scholar] [CrossRef]
- Ali, R.; Shahin, N.; Kim, Y.; Kim, B.; Kim, S.W. Channel observation-based scaled backoff mechanism for high-efficiency WLANs. Electron. Lett. 2018, 54, 663–665. [Google Scholar] [CrossRef]
- Ali, R.; Shahin, N.; Bajracharya, R.; Kim, B.; Kim, S.W. A Self-Scrutinized Backoff Mechanism for IEEE 802.11ax in 5G Unlicensed Networks. Sustainability 2018, 10, 1201. [Google Scholar] [CrossRef]
- IEEE. Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE Standard 802.11; IEEE: Piscataway, NJ, USA, 1997. [Google Scholar]
- IEEE. P802.11ax–IEEE Draft Standard for Information Technology – Telecommunications and Information Exchange Between Systems Local and Metropolitan Area Networks – Specific Requirements Part 11:Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment Enhancements for High Efficiency WLAN; IEEE P802.11ax/D4.0; 2019; pp. 1–746. Available online: https://ieeexplore.ieee.org/servlet/opac?punumber=8672641 (accessed on 8 February 2020).
- Bellalta, B. IEEE 802.11ax: High-Efficiency WLANs. IEEE Wirel. Commun. 2015. [Google Scholar] [CrossRef]
- Xin, Y. Technical Report on Full Duplex for 802.11. IEEE 802.11-18/0498r6. 2018. Available online: https://www.scribd.com/document/421290505/11-18-0498-07-00fd-fd-tig-report-docx (accessed on 10 February 2020).
- Perahia, E.; Stacey, R. Next Generation Wireless LANs: 802.11n and 802.11ac; Cambridge University Press: Cambridge, UK, 2013. [Google Scholar]
- Chen, Y.; Chen, I.; Shih, K. An In-band full duplex MAC protocol with interference free for next generation WLANs. In Proceedings of the 2018 International Conference on Electronics Technology (ICET), Chengdu, China, 23–27 May 2018; pp. 407–410. [Google Scholar] [CrossRef]
- Zhou, Y.; Zhang, H.; Chen, R.; Zhou, T. Design and performance analysis of two-stage contention MAC protocol for full-duplex wireless networks. Int. J. Sens. Netw. 2018, 26, 115–124. [Google Scholar] [CrossRef]
- Kim, W.; Joo, S.; Pack, S. An opportunistic MAC protocol for full duplex wireless LANs. In Proceedings of the 2018 International Conference on Information Networking(ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 810–812. [Google Scholar] [CrossRef]
- Luvisotto, M.; Sadeghi, A.; Lahouti, F.; Vitturi, S.; Zorzi, M. RCFD: A Novel Channel Access Scheme for Full-Duplex Wireless Networks Based on Contention in Time and Frequency Domains. IEEE Trans. Mob. Comput. 2018, 17, 2381–2395. [Google Scholar] [CrossRef]
- Song, Y.D.; Qi, W.; Zhao, W.; Cheng, W. Full-Duplex MAC Protocol for CSMA/CA-Based Single-Hop Wireless Networks. Sensors 2019, 19, 2413. [Google Scholar] [CrossRef] [PubMed]
- Sanada, K.; Mori, K. Throughput Analysis for Full Duplex Wireless Local Area Networks with Hidden Nodes. In Proceedings of the 2019 16th IEEE Annual Consumer Communications Networking Conference (CCNC), Las Vegas, NV, USA, 11–14 January 2019; pp. 1–4. [Google Scholar] [CrossRef]
- Shreedhar, M.; Varghese, G. Efficient Fair Queuing Using Deficit Round Robin. ACM SIGCOMM Comput. Commun. Rev. 1995, 25, 231–242. [Google Scholar] [CrossRef]
- Tang, A.; Wang, X. A-Duplex: Medium Access Control for Efficient Coexistence Between Full-Duplex and Half-Duplex Communications. IEEE Trans. Wirel. Commun. 2015, 14, 5871–5885. [Google Scholar] [CrossRef]
- Choi, W.; Lim, H.; Sabharwal, A. Power-Controlled Medium Access Control Protocol for Full-Duplex WiFi Networks. IEEE Trans. Wirel. Commun. 2015, 14, 3601–3613. [Google Scholar] [CrossRef]
- Qu, Q.; Li, B.; Yang, M.; Yan, Z.; Zuo, X.; Guan, Q. FuPlex: A full duplex MAC for the next generation WLAN. In Proceedings of the 2015 11th International Conference on Heterogeneous Networking for Quality Reliability Security and Robustness (QSHINE), Taipei, Taiwan, 19–20 August 2015; pp. 239–245. [Google Scholar]
- Aijaz, A.; Kulkarni, P. Simultaneous Transmit and Receive Operation in Next Generation IEEE 802.11 WLANs: A MAC Protocol Design Approach. IEEE Wirel. Commun. 2017, 24, 128–135. [Google Scholar] [CrossRef]
- Xie, X.; Zhang, X. Does full duplex double the capacity of wireless networks? In Proceedings of the IEEE Conference on Computer Communications (IEEE InfoCom’14), Toronto, ON, Canada, 27 April–2 May 2014. [Google Scholar]
- Vutukuru, M.; Jamieson, K.; Balakrishnan, H. Harnessing Exposed Terminals in Wireless Networks. In Proceedings of the 5th USENIX Symposium on Networked Systems Design and Implementation (NSDI’08), San Francisco, CA, USA, 16–18 April 2008; pp. 59–72. [Google Scholar]
- Shai, A.; Patel, G.; Sabharwal, A. Pushing the limits of full duplex: Design and real-time implementation. Rice University Technical report TREE11104. arXiv 2011, arXiv:1107.0607. [Google Scholar]
- Song, Y.; Qi, W.; Cheng, W. Energy efficient MAC protocol for wireless full-duplex networks. China Commun. 2018, 15, 35–44. [Google Scholar] [CrossRef]
- Marlali, D.; Gurbuz, O. Design and Performance Analysis of a Full-Duplex MAC Protocol for Wireless Local Area Networks. Ad Hoc Netw. 2017, 67. [Google Scholar] [CrossRef]
- Hu, J.; Di, B.; Liao, Y.; Bian, K.; Song, L. Hybrid MAC Protocol Design and Optimization for Full Duplex Wi-Fi Networks. IEEE Trans. Wirel. Commun. 2018, 17, 3615–3630. [Google Scholar] [CrossRef]
- Sabharwal, A.; Schniter, P.; Guo, D.; Bliss, D.W.; Rangarajan, S.; Wichman, R. In-Band Full-Duplex Wireless: Challenges and Opportunities. IEEE J. Sel. Areas Commun. 2014, 32, 1637–1652. [Google Scholar] [CrossRef]
- Mohammadi, M.; Suraweera, H.A.; Cao, Y.; Krikidis, I.; Tellambura, C. Full-Duplex Radio for Uplink/Downlink Wireless Access With Spatially Random Nodes. IEEE Trans. Commun. 2015, 63, 5250–5266. [Google Scholar] [CrossRef]
- Alim, M.A.; Watanabe, T. Full Duplex Medium Access Control Protocol for Asymmetric Traffic. In Proceedings of the 2016 IEEE 84th Vehicular Technology Conference (VTC-Fall), Montreal, QC, Canada, 18–21 September 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Hsu, K.; Lin, K.C.; Wei, H. Inter-client interference cancellation for full-duplex networks. In Proceedings of the IEEE INFOCOM 2017—IEEE Conference on Computer Communications, Atlanta, GA, USA, 1–4 May 2017; pp. 1–9. [Google Scholar] [CrossRef]
- Lee, J.; Kim, W.; Lee, S.J.; Jo, D.; Ryu, J.; Kwon, T.; Choi, Y. An experimental study on the capture effect in 802.11a networks. In Proceedings of the 2nd ACM International Workshop On Wireless Network Testbeds, Experimental Evaluation And Characterization, Montreal, QC, Canada, 9–14 September 2007; pp. 19–26. [Google Scholar] [CrossRef]
- Santhapuri, N.; Manweiler, J.; Sen, S.; Nelakuduti, S.; Munagala, K. Message in Message (MIM): A Case for Reordering Transmissions in Wireless Networks. In Proceedings of the Seventh ACM Workshop on Hot Topics in Networks, Calgary, AB, Canada, 6–7 October 2008. [Google Scholar]
- Aryafar, E.; Keshavarz-Haddad, A. FD2: A directional full duplex communication system for indoor wireless networks. In Proceedings of the 2015 IEEE Conference on Computer Communications (INFOCOM), Kowloon, Hong Kong, 26 April–1 May 2015; pp. 1993–2001. [Google Scholar] [CrossRef]
- Lee, Y.; Huang, B. Active Interference Cancellation for Full-Duplex Multiuser Networks With or Without Existence of Self-Interference. IEEE Access 2019, 7, 15056–15068. [Google Scholar] [CrossRef]
- Kai, C.; Huang, T.; Wang, L.; Gu, Y. CSMA-Based Utility-Optimal Scheduling in the WLAN With a Full-Duplex Access Point. IEEE Access 2018, 6, 41399–41409. [Google Scholar] [CrossRef]
- Kuhn, H.W. The Hungarian Method for the Assignment Problem. In 50 Years of Integer Programming; Springer: Berlin/Heidelberg, Germany, 2010. [Google Scholar] [CrossRef]
- Mikhael, M.; van Liempd, B.; Craninckx, J.; Guindi, R.; Debaillie, B. An in-band full-duplex transceiver prototype with an in-system automated tuning for RF self-interference cancellation. In Proceedings of the 1st International Conference on 5G for Ubiquitous Connectivity, Akaslompolo, Finland, 26–28 November 2014; pp. 110–115. [Google Scholar] [CrossRef]
- Yang, H.; Zhang, H.; Zhang, J.; Yang, L. Digital Self-Interference Cancellation Based on Blind Source Separation and Spectral Efficiency Analysis for the Full-Duplex Communication Systems. IEEE Access 2018, 6, 43946–43955. [Google Scholar] [CrossRef]
- Riihonen, T.; Korpi, D.; Rantula, O.; Rantanen, H.; Saarelainen, T.; Valkama, M. Inband Full-Duplex Radio Transceivers: A Paradigm Shift in Tactical Communications and Electronic Warfare? IEEE Commun. Mag. 2017, 55, 30–36. [Google Scholar] [CrossRef]
- Korpi, M.; Choi, Y.; Huusari, T.; Anttila, L.; Talwar, S.; Valkama, M. Adaptive Nonlinear Digital Self-Interference Cancellation for Mobile Inband Full-Duplex Radio: Algorithms and RF Measurements. In Proceedings of the 2015 IEEE Global Communications Conference (GLOBECOM), San Diego, CA, USA, 6–10 December 2015; pp. 1–7. [Google Scholar] [CrossRef]
- Korpi, D.; Turunen, M.; Anttila, L.; Valkama, M. Modeling and Cancellation of Self-Interference in Full-Duplex Radio Transceivers: Volterra Series-Based Approach. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).